A Throughput Request Satisfaction Method for Concurrently Communicating Multiple Hosts in Wireless Local Area Network
Abstract
:1. Introduction
- The proper target throughput for each host is derived by measuring the single and concurrent throughput and estimating the required channel occupying time to satisfy the throughput request.
- Then, the traffic shaping is applied using the Linux tc command at the Raspberry Pi AP to control the traffic of every host to satisfy the target throughput without modifying the existing CSMA/CA protocol or the hardware.
2. Related Works
3. Preliminary
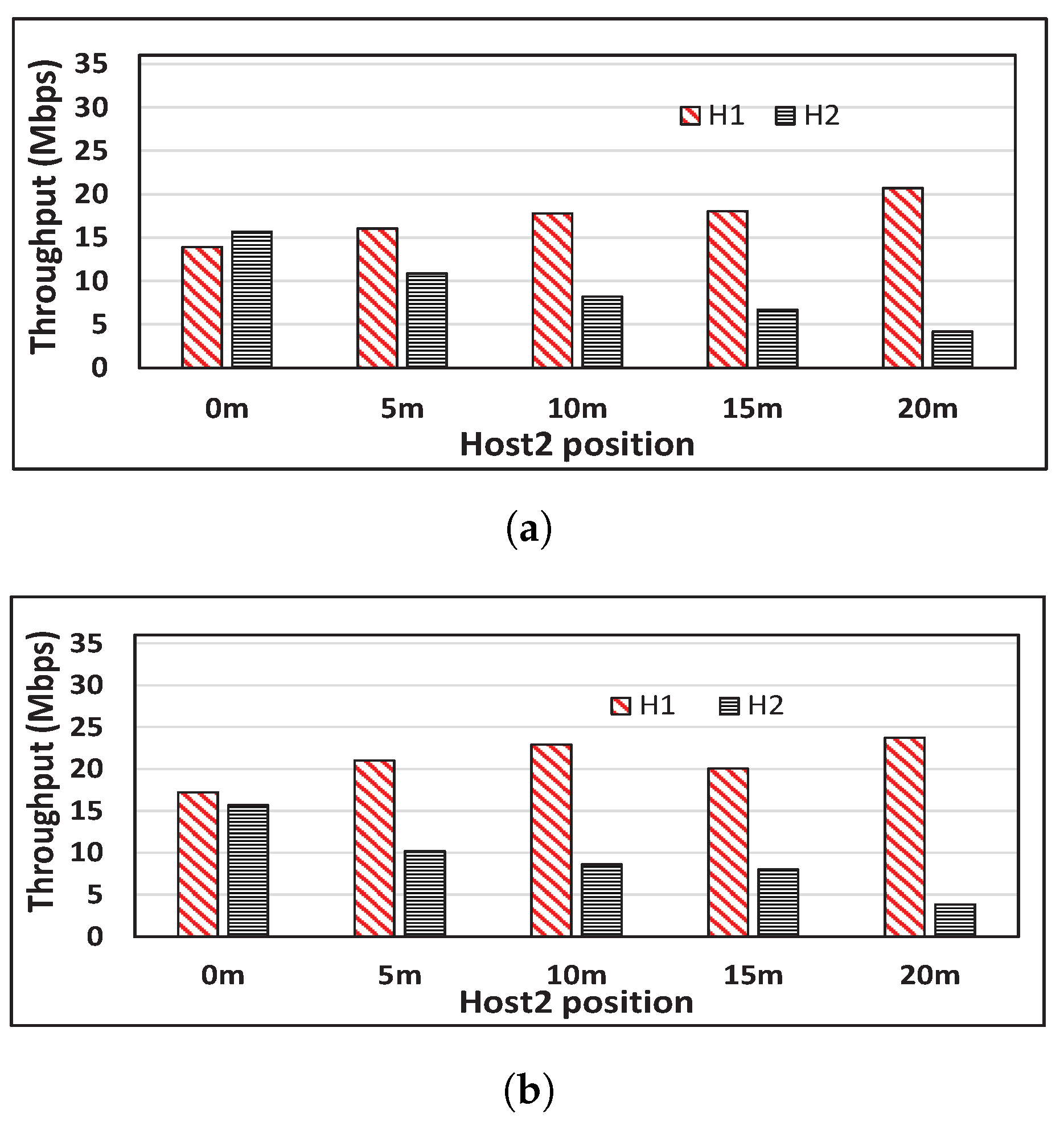
3.1. Throughput Unfairness Observation
3.2. Saturated Host
3.3. Traffic Shaping
3.4. Throughput Measurement Tool
4. Throughput Request Satisfaction Method
4.1. Observations of Proposal
- (1)
- The traffic shaping can control the throughput of each host by applying tc command at the AP.
- (2)
- The single throughput for each host can be measured using iftop when only one host communicates with the AP, which can give the average maximum number of transmitted bits per second (bps).
- (3)
- The concurrent throughput for each host can be measured using iftop when all hosts communicate concurrently with the AP, which can give the average actual number of transmitted bits per second (bps).
- (4)
- The target throughput refers to the number of bits transmitted per second by each host.
- (5)
- The concurrent throughput and single throughput for each host can be used to estimate the average channel occupying time per one second. The concurrent throughput is divided by the single throughput to obtain the average channel occupying time. Then, this relationship is still true if the concurrent throughput is substituted by the target throughput.
- (6)
- The total of the average channel occupying time for all the hosts can be constant (basically, one second).
- (7)
- The single throughput of the host is always higher than the target throughput.
- (8)
- When the target throughput of a host exceeds the concurrent one, the time allocated to this host can be increased by taking the channel occupying time of the other hosts. Thus, a proper target throughput for each host can be determined.
4.2. Single and Concurrent Throughput Measurement
4.3. Channel Occupying Time of Hosts
4.4. Equal Target Throughput Request
4.4.1. Conventional Host Case
4.4.2. Saturated Host Case
4.5. Different Target Throughput Request
4.5.1. Conventional Host Case
4.5.2. Saturated Host Case
4.5.3. Minimum Target Throughput Case
4.6. PI Controller for Rate and Ceil Parameter
4.7. Application of Traffic Shaping
- (1)
- Create the HTB qdisc, generate the required number of classes for each host i, and assign the rate value by:
- –
- $sudo tc qdisc add dev wlan0 root handle 1: htb default.
- –
- $sudo tc class add dev wlan0 parent 1: classid 1:1 htb rate
- –
- $sudo tc class add dev wlan0 parent 1:1 classid 1:i htb rate ceil .
- (2)
- Apply the to the host by specifying the IP address:
- –
- $sudo tc filter add dev wlan0 protocol ip parent 1:0 prio 1 u32 match ip dst flowid 1:i.
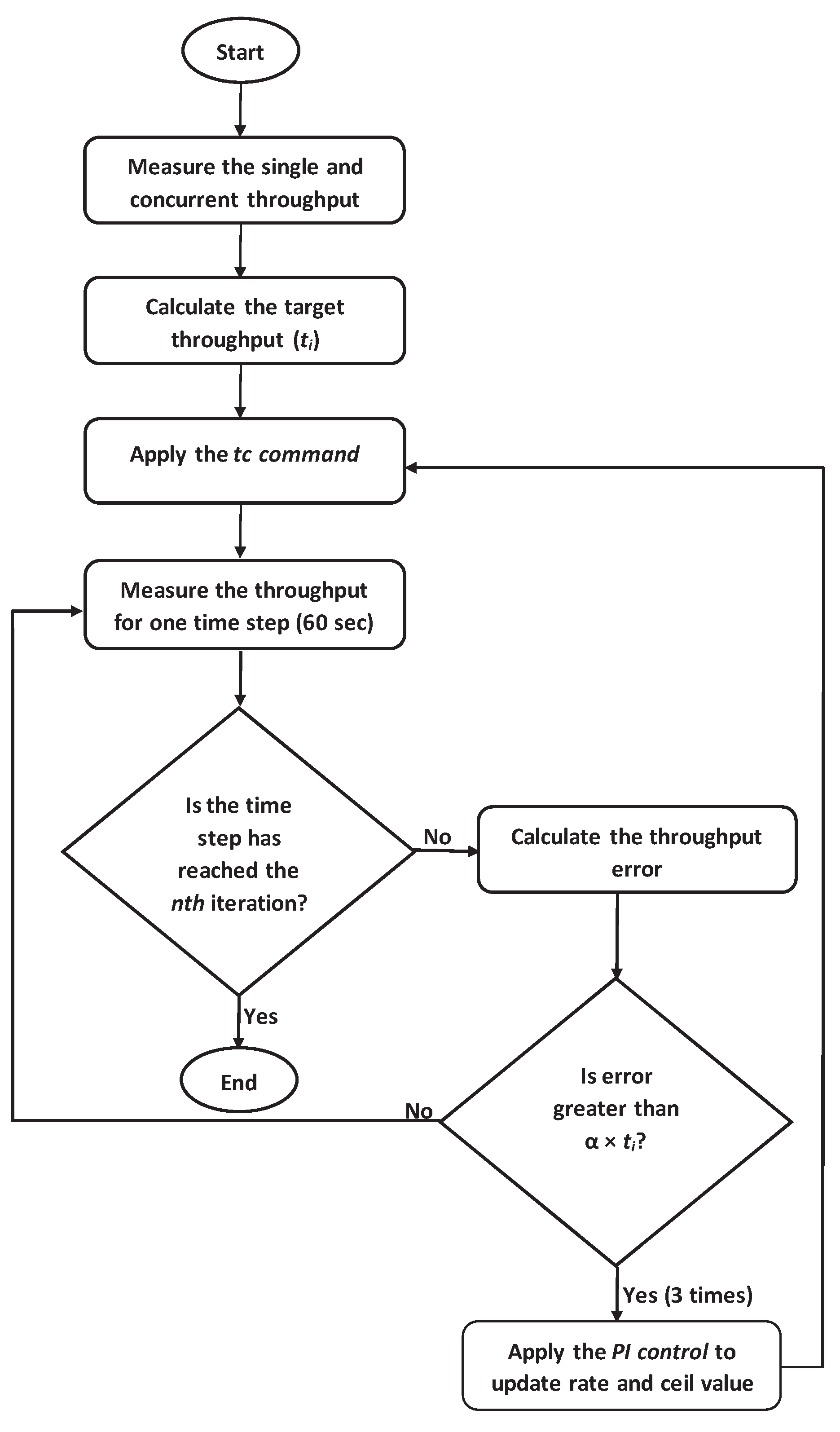
4.8. Procedure of Throughput Request Satisfaction Method
- (1)
- Measure the single throughput for each host using iftop while only the host is communicating.
- (2)
- Measure the concurrent throughput for every host using iftop while all the hosts are communicating simultaneously.
- (3)
- Calculate the target throughput and assign the initial rate and ceil value by = .
- (4)
- Apply the traffic shaping using tc.
- (5)
- Periodically measure the concurrent throughput for every host using iftop while all the hosts are communicating.
- (6)
- Apply the PI control to update .
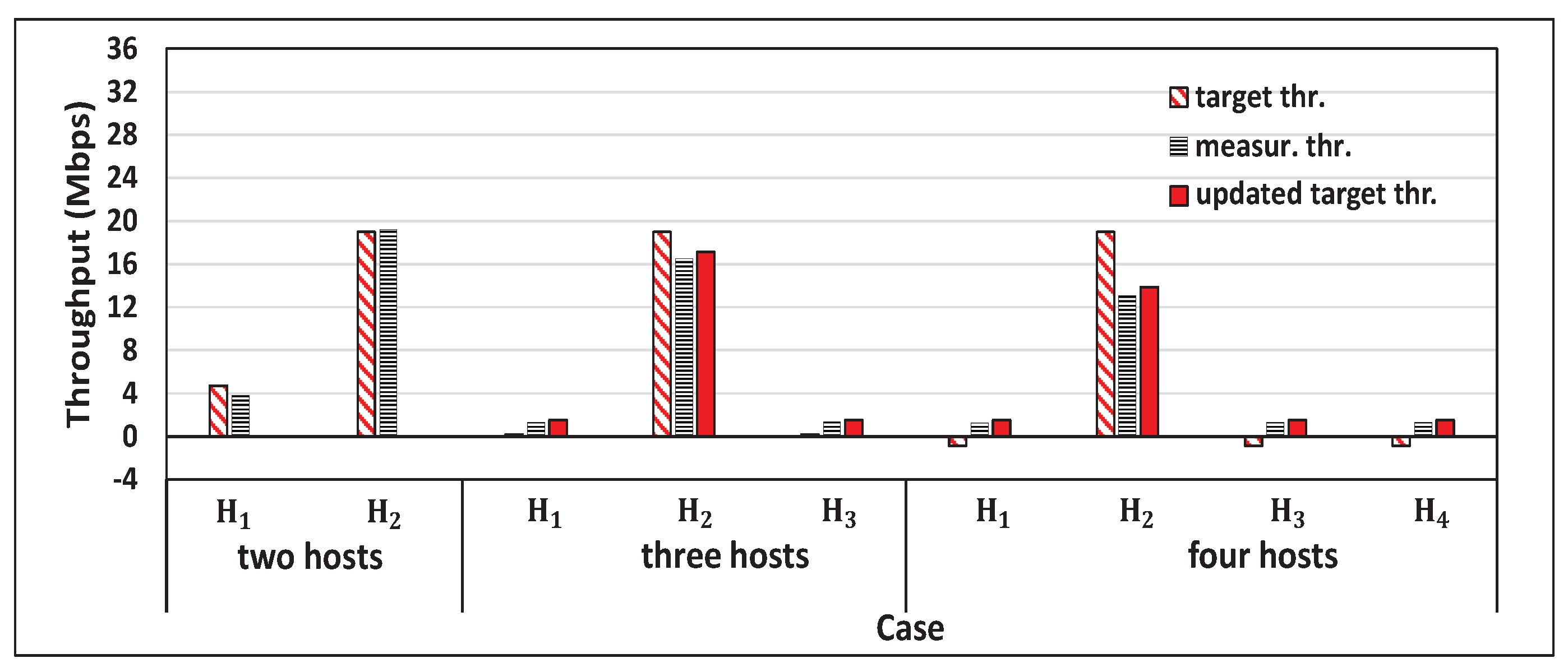
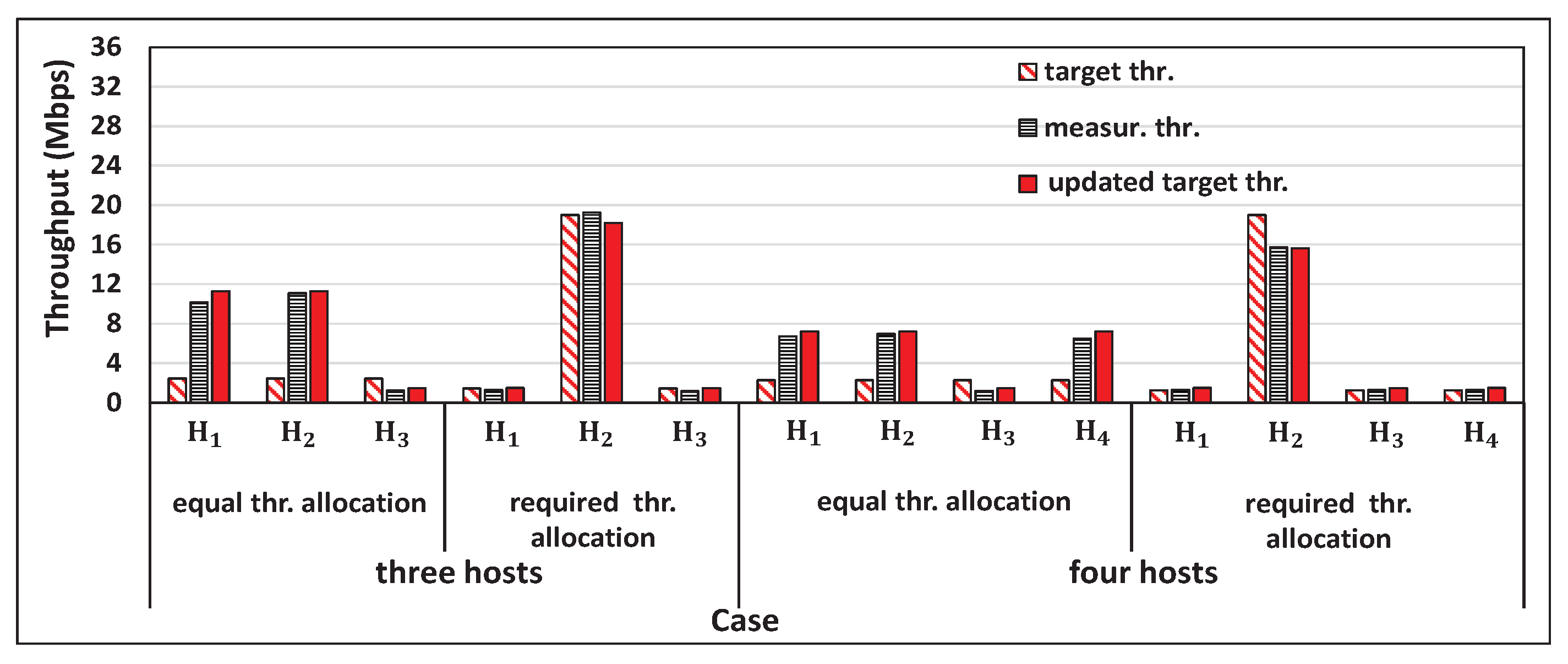
5. Evaluations with iperf Traffic
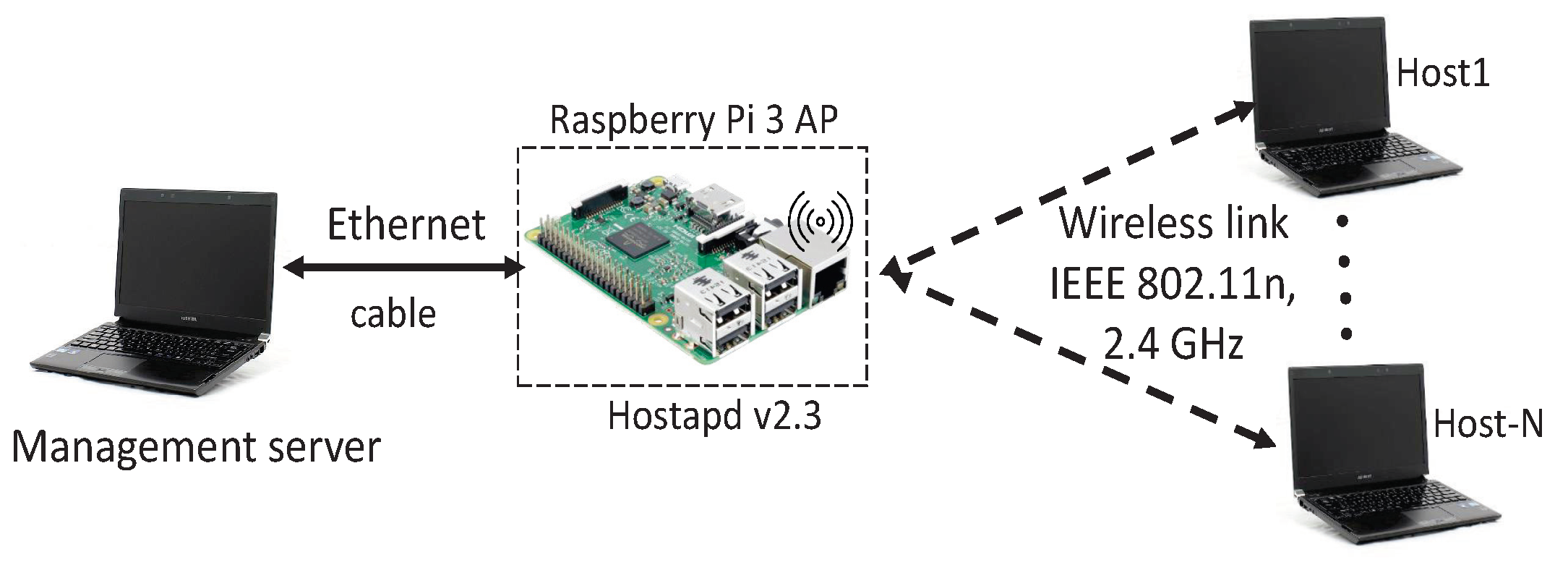
5.1. Experimental Setup
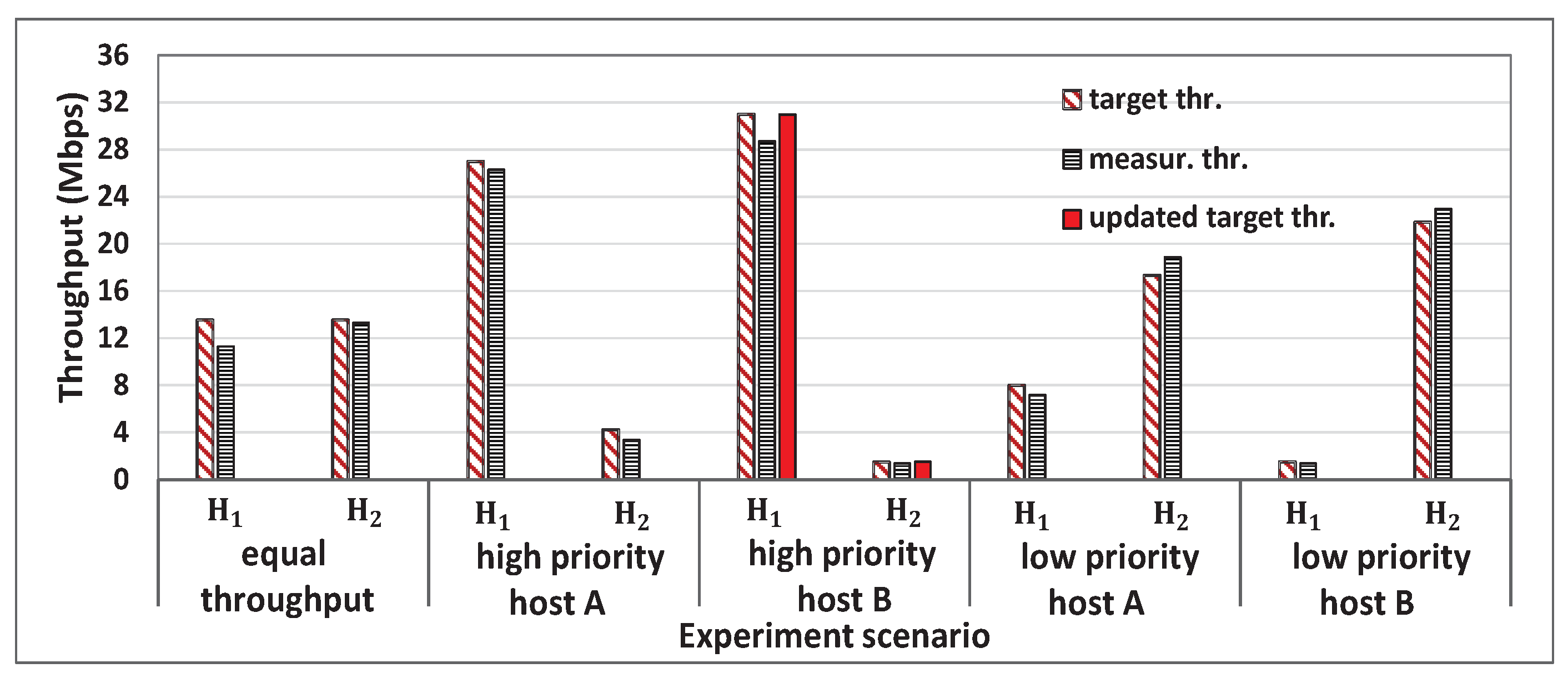
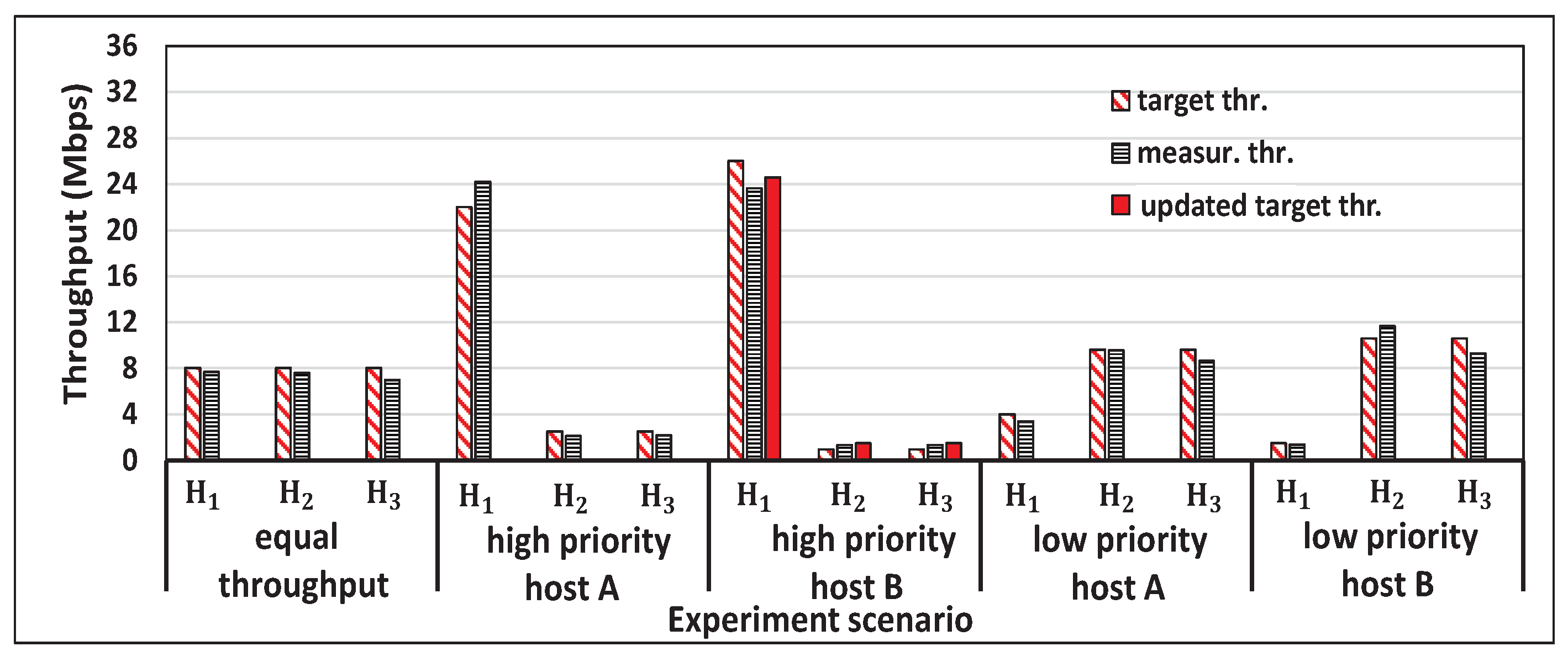
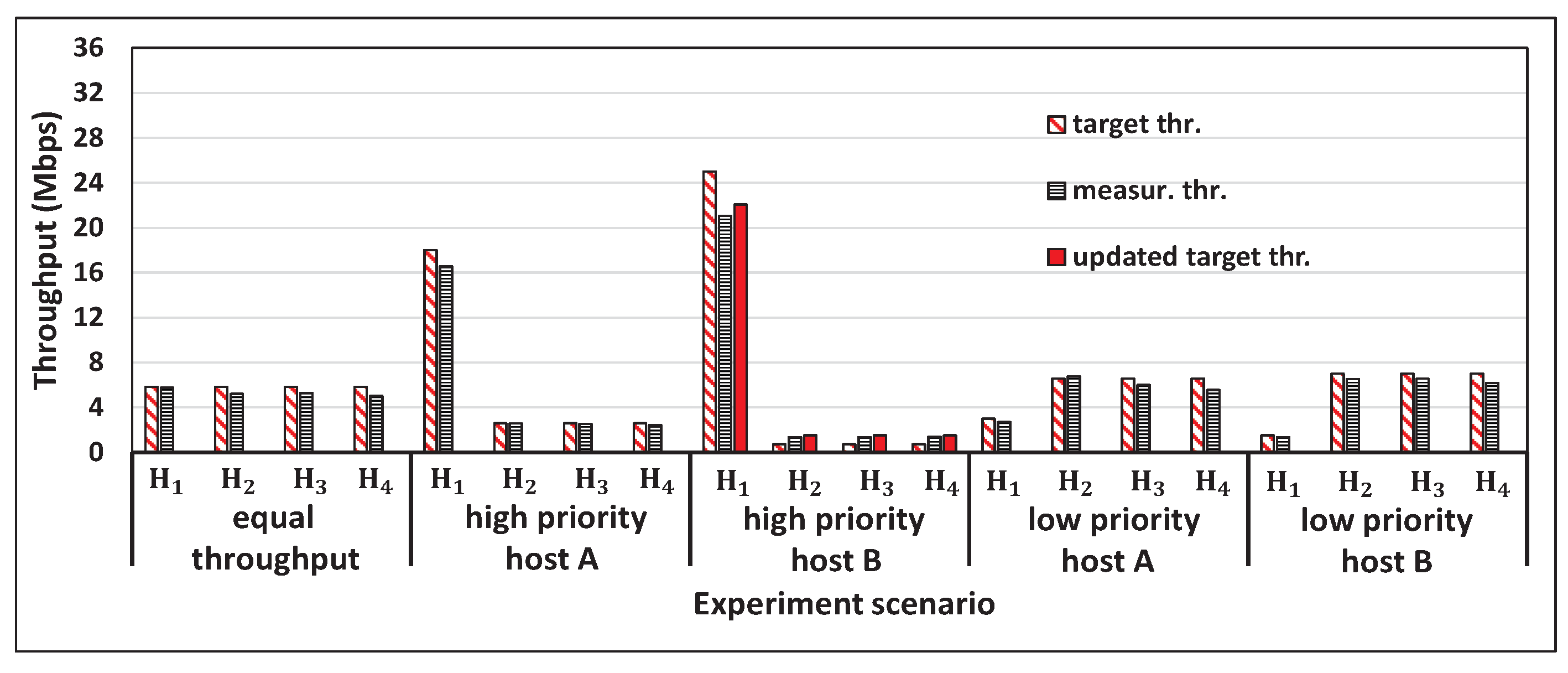
5.2. Experiment Scenarios
5.3. Throughput Results
5.4. Discussions
5.5. Fairness Index
6. Evaluations with Web Traffic
6.1. Experimental Setup
6.2. Results for Equal Throughput Scenario
6.3. Results for Priority Host Scenario
6.4. Results for Saturated Host Scenario
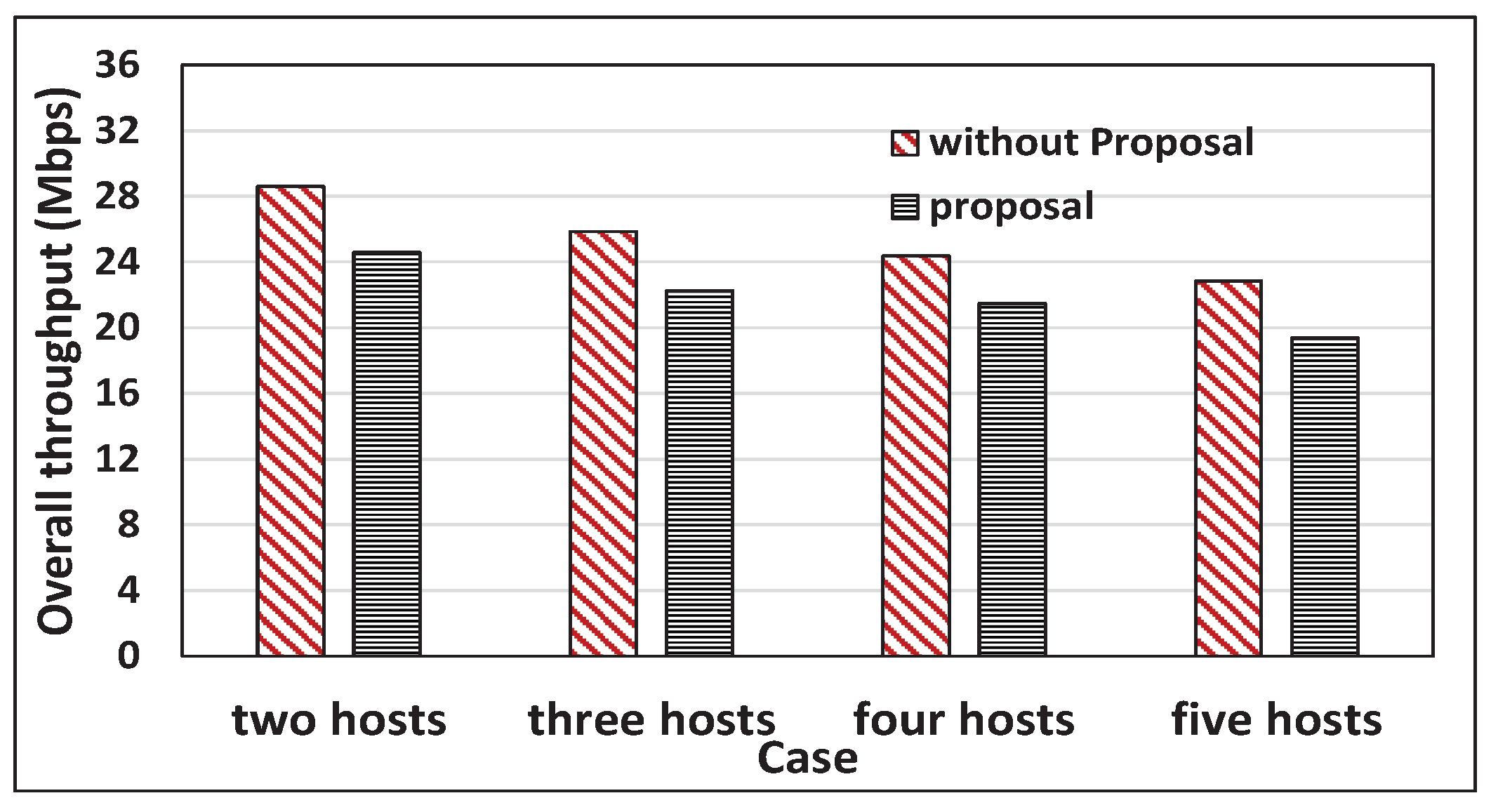
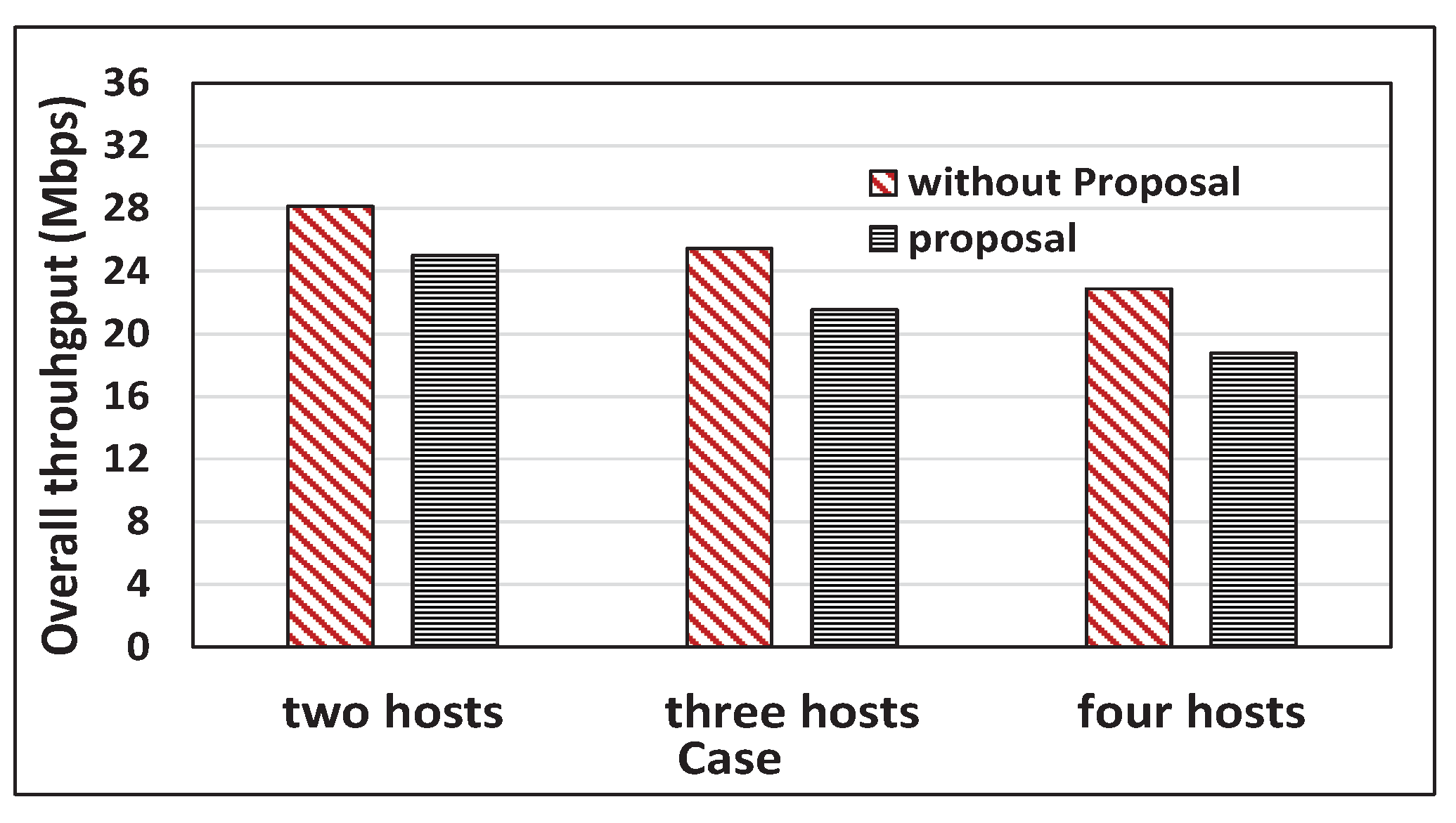
6.5. Throughput Comparison between the Proposal and without Proposal
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Liu, J.; Aoki, T.; Li, Z.; Pei, T.; Choi, Y.; Nguyen, K.; Sekiya, H. Throughput analysis of IEEE 802.11 WLANs with inter-network interference. Appl. Sci. 2020, 10, 2192. [Google Scholar] [CrossRef] [Green Version]
- Pahlavan, K.; Krishnamurthy, P. Evolution and impact of Wi-Fi technology and applications: A historical perspective. Int. J. Wirel. Inf. Netw. 2020, 28, 3–19. [Google Scholar] [CrossRef]
- Dash, S.; Mishra, S.; Mishra, J. Mobile data offloading using opportunistic communication and AP deployment. Int. J. Mob. Comput. Multimed. Commun. 2017, 8, 66–84. [Google Scholar] [CrossRef] [Green Version]
- Oh, H.; Jeong, D.; Jeon, W. Joint radio resource management of channel-assignment and user-association for load balancing in dense WLAN environment. IEEE Access 2020, 8, 69615–69628. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, X.; Cai, L. On Achieving Fair and Throughput-Optimal Scheduling for TCP Flows in Wireless Networks. IEEE Trans. Wirel. Commun. 2016, 15, 7996–8008. [Google Scholar] [CrossRef]
- Moiseenko, I.; Oran, D. TCP/ICN: Carrying TCP over content centric and named data networks. In Proceedings of the 3rd ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; pp. 112–121. [Google Scholar]
- Sudibyo, R.; Funabiki, N.; Kuribayashi, M.; Munene, K.; Briantoro, H.; Islam, M.; Kao, W. A generalized TCP fairness control method for multiple-host concurrent communications in elastic WLAN system using Raspberry Pi access point. Int. J. Mob. Comput. Multimed. Commun. 2020, 11, 18–40. [Google Scholar] [CrossRef]
- Manipulate Traffic Control Settings. Available online: https://linux.die.net/man/8/tc (accessed on 31 August 2022).
- HTB Linux Queuing Discipline Manual—User Guide. Available online: http://luxik.cdi.cz/~devik/qos/htb/manual/userg.htm (accessed on 31 August 2022).
- Kim, J.; Jin, H.; Seo, J.; Kim, S.; Sung, D. Adaptive transmission control for uplink/downlink fairness in unsaturated CSMA networks. IEEE Commun. Lett. 2019, 23, 1879–1882. [Google Scholar] [CrossRef]
- Priya, S.S.; Murugan, K. Enhancing TCP fairness in wireless networks using dual queue approach with optimal queue selection. Wirel. Pers. Commun. 2015, 83, 1359–1372. [Google Scholar] [CrossRef]
- Kim, J.; Kim, S.; Sung, D. Hybrid ARQ-based fairness enhancement in uplink WLAN. IEEE Trans. Wirel. Commun. 2018, 17, 4362–4373. [Google Scholar] [CrossRef]
- Lei, J.; Wu, Y.; Zhang, X. An improved active queue management algorithm for time fairness in multirate 802.11 WLAN. In In Proceedings of the 6th Computer Science Online Conference (CSOC), Prague, Czech Republic, 26–29 April 2017; pp. 161–171. [Google Scholar]
- Kongsili, L.; Fujimoto, A.; Uchio, F. Packet scheduling and access priority control for QoS and fairness in wireless LAN. Procedia Comput. Sci. 2015, 60, 1788–1797. [Google Scholar] [CrossRef]
- Fang, Y.; Doray, B.; Issa, O. A practical air time control strategy for Wi-Fi in diverse environment. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops (WCNCW), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Mansy, A.; Fayed, M.; Ammar, M. Network-layer fairness for adaptive video streams. In Proceedings of the 14th IFIP Networking, Toulouse, France, 20–22 May 2015; pp. 42–48. [Google Scholar]
- Hwang, J.; Lim, H.; Oh, S.; Lee, B. Association scheme with traffic control for IEEE 802.11 wireless LANs. IEICE Trans. Commun. 2015, 98, 1680–1689. [Google Scholar] [CrossRef] [Green Version]
- Høiland-Jørgensen, T.; Kazior, M.; Täht, D.; Hurtig, P.; Brunstrom, A. Ending the anomaly: Achieving low latency and airtime fairness in wifi. In Proceedings of the USENIX Annual Technical Conference, Santa Clara, CA, USA, 12–14 July 2017; pp. 139–151. [Google Scholar]
- Le, Y.; Ma, L.; Cheng, W.; Cheng, X.; Chen, B. A Time fairness-based MAC algorithm for throughput maximization in 802.11 networks. IEEE Trans. Comput. 2015, 64, 19–31. [Google Scholar] [CrossRef]
- Garroppo, R.; Giordano, S.; Lucetti, S.; Tavanti, L. Providing air-time usage fairness in IEEE 802.11 networks with the deficit transmission time (DTT) scheduler. Wirel. Netw. 2006, 13, 481–495. [Google Scholar] [CrossRef]
- Blough, D.; Resta, G.; Santi, P. Interference-aware proportional fairness for multi-rate wireless networks. In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 2733–2741. [Google Scholar]
- Banchs, A.; Serrano, P.; Patras, P.; Natkaniec, M. Providing throughput and fairness guarantees in virtualized WLANs through control theory. Mob. Netw. Appl. 2012, 17, 435–446. [Google Scholar] [CrossRef]
- Akimoto, K.; Kameda, S.; Suematsu, N. Optimum allocation scheme for user fairness of location-based virtual sector method solving hidden terminal problem in WLAN. IEEE Trans. Veh. Technol. 2018, 67, 8363–8371. [Google Scholar] [CrossRef]
- Abuteir, R.M.; Fladenmuller, A.; Fourmaux, O. An SDN approach to adaptive video streaming in wireless home networks. In Proceedings of the IEEE International Wireless Communications and Mobile Computing Conference (IWCMC), Paphos, Cyprus, 5–9 September 2016; pp. 321–326. [Google Scholar]
- Inaba, T.; Sakamoto, S.; Oda, T.; Ikeda, M.; Barolli, L. A testbed for admission control in WLAN: A fuzzy approach and its performance evaluation. In Proceedings of the 11th International Conference On Broad-Band Wireless Computing, Communication and Applications (BWCCA), Asan, Republic of Korea, 5–7 November 2016; pp. 559–571. [Google Scholar]
- Jat, D.S.; Shejwal, A.; Lusilao, G.; Singh, C. A review of the quality of service for time-sensitive applications through admission control in 802.11 WLAN. In In Proceedings of the International Conference on Recent Advancement on Computer and Communication, Singapore, 25–27 April 2018; pp. 665–672. [Google Scholar]
- Capano, D.E.; Vavra, C. Understanding modulation and coding schemes: Industrial wireless tutorials: Modulation and coding schemes (MCS) are used to determine the data rate of a wireless connection using high-throughput orthogonal frequency division multiplexing (HT-OFDM). Control. Eng. 2014, 61, 26–27. [Google Scholar]
- Zoom Rooms System Requirements. Available online: https://support.zoom.us/hc/en-us/articles/204003179-System-Requirements-for-Zoom-Rooms#hb48c2bfd-7da0-4290-aae8-784270d3ab3 (accessed on 31 August 2022).
- iftop: Display Bandwidth Usage on an Interface. Available online: http://www.ex-parrot.com/pdw/iftop/ (accessed on 31 August 2022).
- The Ultimate Speed Test Tool for TCP, UDP and SCTP. Available online: https://iperf.fr/ (accessed on 31 August 2022).
- Jaafar, H.I.; Hussien, S.Y.S.; Selamat, N.A.; Aras, M.S.M.; Rashid, M.Z.A. Development of PID controller for controlling desired level of coupled tank system. Int. J. Innov. Technol. Explor. Eng. 2014, 3, 32–36. [Google Scholar]
- Islam, M.; Funabiki, N.; Sudibyo, R.; Munene, K.; Kao, W. A dynamic access-point transmission power minimization method using PI feedback control in elastic WLAN system for IoT applications. Internet Things 2019, 8, 100089. [Google Scholar] [CrossRef]
- Jain, R.K.; Chiu, D.M.W.; Hawe, W.R. A Quantitative Measure of Fairness and Discrimination; Eastern Research Laboratory, Digital Equipment Corporation: Hudson, MA, USA, 1984. [Google Scholar]
- Ubuntu 20.04.3 LTS Released. Available online: https://www.omgubuntu.co.uk/2021/08/ubuntu-20-04-3-point-release (accessed on 31 August 2022).







| Reference | Goal | Approach and Implementation | Advantage | Disadvantage and Non Solved Problem | Evaluation |
|---|---|---|---|---|---|
| proposal | throughput fairness per host | throughput control by traffic shaping, implemented by the Linux command | does not require any modification of hardware or protocol | reduce the overall throughput | testbed experiment |
| [10] | throughput fairness per flow | uplink/downlink flow control by modified backoff algorithm in MAC layer. | increase the overall throughput | modification of MAC layer protocol and cannot allocate equal or required throughput | simulation |
| [11] | fairness between uplink/downlink TCP flows | dual queue for optimum queue selection in MAC layer | increase the overall throughput | modification of MAC layer protocol and cannot allocate equal or required throughput | simulation |
| [12] | throughput fairness per flow | DCF enhancement by HARQ in MAC layer | increase the overall throughput | modification of MAC layer protocol and cannot allocate equal or required throughput | simulation |
| [13] | airtime fairness | queue management based on data rates, which is implemented in MAC layer | increase the overall throughput | modification of MAC layer protocol and cannot allocate equal or required throughput | simulation |
| [14] | airtime fairness | packet scheduling and channel access control, which is implemented on AP | increase the overall throughput | modification of AP and cannot allocate equal or required throughput | simulation |
| [15] | airtime fairness | airtime control by traffic shaping, implemented by the Linux command | increase the overall throughput | cannot allocate equal or required throughput | testbed experiment |
| [16] | max-min fairness | network-level queueing prioritization, implemented by the Linux command | increase the user level QoS by allocating throughput | cannot allocate equal required throuhgput | testbed experiment |
| [17] | throughput allocation | throughput control by traffic shaping, implemented by ns-2 simulator | provide throughput fairness | cannot allocate necessary throughput, and reduce the overall throughput | simulation |
| [18] | airtime fairness | network-level queue management, implemented in Linux kernel | increase the overall throughput | cannot allocate equal or required throughput | testbed experiement |
| [19] | airtime fairness | changing contention window by modifying MAC protocol | increase the overall throughput | modification of MAC layer protocol and cannot allocate equal or required throughput | simulation |
| [20] | airtime fairness | queueing prioritization, implemented by the Linux command | increase the overall throughput | cannot allocate equal or required throughput and hardware specific approach | testbed experiment |
| [21] | airtime fairness | packet scheduling algorithm in MAC layer | increase the overall throughput | cannot allocate equal or required throughput and modification of scheduler | simulation |
| [22] | fairness among virtual WLANs | contention window adjustment by PI controller | increase the overall throughput | cannot allocate equal or required throughput and modification of hardware | simulation |
| [23] | throughput fairness | DCF enhancement by HARQ, Implemented in MAC layer | increase the overall throughput | cannot allocate equal or required throughput and modification of hardware | simulation |
| [24] | airtime fairness | SDN approach, and bandwidth control by traffic shaping | increase the overall throughput | cannot allocate equal or required throughput | testbed experiment |
| Notations | Definition |
|---|---|
| ith host for , where n is the number of host | |
| measured single throughput of | |
| measured concurrent throughput of | |
| target throughput of | |
| minimum target throughput for any host | |
| rate and ceil parameter value | |
| measured throughput at time step m |
| Server and Hosts | |
|---|---|
| type | 1. Toshiba Dynabook R731/B, |
| 2. Toshiba Dynabook R734/K | |
| operating system | Linux (Ubuntu 14) |
| processor | 1. Intel Core i5-2520M, 2.5 GHz |
| 2. Intel Core i5-4300M @2.6 GHz | |
| RAM | 4GB DDR3-1333 MHz |
| software | iperf 2.0.5 |
| access point | |
| type | Raspberry Pi 3 |
| operating system | Linux (Raspbian) |
| processor | BCM2837 1.2 GHz, Broadcom |
| RAM | LPDDR2 900 MHz 1GB |
| NIC | BCM43438, Broadcom |
| software | hostapd, iftop |
| Case | Device Location | ||
|---|---|---|---|
| D307 | in front of D307 | Refresh Corner | |
| 2 hosts | , | – | |
| 3 hosts | , , | – | |
| 4 hosts | , , | ||
| 5 hosts | , , | , | |
| Scenario | Condition |
|---|---|
| (1) equal throughput | |
| (2) high priority host A | and |
| (3) high priority host B | and |
| (4) low priority host A | and |
| (5) low priority host B | and |
| Case | Fairness Index | |
|---|---|---|
| without Proposal | Proposal | |
| 2 hosts | 0.920 | 0.993 |
| 3 hosts | 0.869 | 0.998 |
| 4 hosts | 0.842 | 0.995 |
| 5 hosts | 0.802 | 0.991 |
| Case | Fairness Index | |
|---|---|---|
| without Proposal | Proposal | |
| 2 hosts | 0.942 | 0.996 |
| 3 hosts | 0.912 | 0.998 |
| 4 hosts | 0.847 | 0.996 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rahman, M.M.; Funabiki, N.; Munene, K.I.; Roy, S.C.; Kuribayashi, M.; Gulo, M.M.; Kao, W.-C. A Throughput Request Satisfaction Method for Concurrently Communicating Multiple Hosts in Wireless Local Area Network. Sensors 2022, 22, 8823. https://doi.org/10.3390/s22228823
Rahman MM, Funabiki N, Munene KI, Roy SC, Kuribayashi M, Gulo MM, Kao W-C. A Throughput Request Satisfaction Method for Concurrently Communicating Multiple Hosts in Wireless Local Area Network. Sensors. 2022; 22(22):8823. https://doi.org/10.3390/s22228823
Chicago/Turabian StyleRahman, Md. Mahbubur, Nobuo Funabiki, Kwenga Ismael Munene, Sujan Chandra Roy, Minoru Kuribayashi, Melki Mario Gulo, and Wen-Chung Kao. 2022. "A Throughput Request Satisfaction Method for Concurrently Communicating Multiple Hosts in Wireless Local Area Network" Sensors 22, no. 22: 8823. https://doi.org/10.3390/s22228823
APA StyleRahman, M. M., Funabiki, N., Munene, K. I., Roy, S. C., Kuribayashi, M., Gulo, M. M., & Kao, W.-C. (2022). A Throughput Request Satisfaction Method for Concurrently Communicating Multiple Hosts in Wireless Local Area Network. Sensors, 22(22), 8823. https://doi.org/10.3390/s22228823










