Abstract
The paper presents a novel data-embedding method based on the Periodic Haar Piecewise-Linear (PHL) transform. The theoretical background behind the PHL transform concept is introduced. The proposed watermarking method assumes embedding hidden information in the PHL transform domain using the luminance channel of the original image. The watermark is embedded by modifying the coefficients with relatively low values. The proposed method was verified based on the measurement of the visual quality of an image with a watermark with respect to the length of the embedded information. In addition, the bit error rate (BER) is also considered for different sizes of a watermark. Furthermore, a method for the detection of image manipulation is presented. The elaborated technique seems to be suitable for applications in digital signal and image processing where high imperceptibility and low BER are required, and information security is of high importance. In particular, this method can be applied in systems where the sensitive data is transmitted or stored and needs to be protected appropriately (e.g., in medical image processing).
1. Introduction
There is a large number of areas where the security of multimedia content is crucial for ensuring privacy and citizens’ rights in general. Digital watermarking is an efficient and versatile technical means for embedding secret information into multimedia objects, such as still images, videos, and audio files. An example of such secret, sensitive information can be medical data related to patients. Watermarking technology can assure protection of the digital content against unauthorized access, tampering, sensitive information disclosure, or copyright infringement. Methods based on watermarking may be also used for such applications as steganography and pseudonymization of private data. A graphic or audio file marked in this way can help locate websites or FTP servers where these files are unlawfully shared. As a result, a digital watermark now has high hopes for an effective fight against fraud.
The efficient watermark should be characterized by the following features: Impercep-tibility—the watermark should be imperceptible to the human eye, and the inserted information should not deteriorate the visual quality of an original image. Robustness—the watermark is detectable even after the original image transformation and is difficult to be removed. Consideration of local image properties—the watermark is inserted with varying intensity in different areas, depending on the characteristics of the area (e.g., brightness) Watermark decoding method—the watermark can be read based on the watermarked image only, without the need to verify against the original image.
Image watermarking can be performed in the spatial or transform domain. Spatial domain methods usually result in direct modifications of image data, such as color bands, and brightness. The common method for embedding a watermark in the spatial domain is the Least Significant Bit (LSB) method where the secret information is inserted into the original image by modifying or replacing the least significant bits of pixels. On the other hand, transform-based techniques rely on changing spectral factors in the domain of a specific transform. To retrieve the image with an embedded watermark one needs to perform the corresponding inverse transform operation. Watermarks embedded in the transform domains are typically more reliable in comparison with the watermarks inserted in the spatial domain [1,2].
The most widely used transforms used in digital watermarking include discrete cosine transform (DCT) [3,4,5,6], discrete wavelet transforms (DWT) [7,8] and discrete Fourier transform (DFT) [9,10]. Combination of different transform methods can be implemented, (e.g., DCT and DWT transform) [11,12,13]. Additionally, transform-based techniques can be used jointly with other methods, such as, (e.g., singular value decomposition (SVD) [14] or discrete fractional random transform (DFRNT)) [2]. There are also new approaches that apply novel types of transforms that are orthogonal and can be parameterized [15].
In [16], Yan et al. presented a data hiding scheme based on LSB modification in the Piecewise-Linear Haar transform for audio signals. Yang et al. in [17] proposed a reversible data hiding method dedicated to images using symmetrical histogram expansion also in the domain of this transform.
However, Periodic Haar Piecewise-Linear (PHL) transform is only mentioned in the literature with regard to image compression tasks [18].
For obvious reasons medical images are private to the patient and authorized medical personnel and should be protected from unauthorized viewers. One method to protect such images is using cryptography including traditional symmetric cryptosystems and biometrics [19,20,21]. Digital content, in particular this related to medical images, is more and more often protected by a combination of tools, such as encryption and watermarking. As defined in [22] encryption algorithms can be considered as an “a priori” protection mechanism since once data is decrypted, it is no longer protected. A complement to “a priori” mechanism is “a posteriori” protection, which can be provided by watermarking.
Apart from unauthorized access to sensitive content, another potential threat to medical multimedia content is possible manipulations. Existing, widely available, image editing software and image altering tools allow us to easily manipulate a digital image nowadays. Studies of various image manipulation detection techniques are available in the literature. Numerous image forgeries that can be performed on the image and different image manipulation detection and localization methods were presented in [23]. Image manipulation can also concern biomedical sciences where the use of images to depict laboratory results is widely disseminated. Results published in [24] have shown an alarming level of image manipulation in the published record. A dedicated tool was used to detect some of the most common misbehaviors, running tests on a random set of papers and the full publishing record of a journal.
Currently, image tampering detection can be also realized with the use of Convolutional Neural Networks [25]. Image protection and manipulation detection are extremely relevant in all applications where the sensitive data is transmitted from the imaging sensor to a remote destination where it is further processed and analyzed [26]. Such protection can be realized in aerial photography, area monitoring, and satellite imagery [27]. The same applies to medical applications of remote sensing where electromagnetic radiation is most commonly the sensing medium and the sensors of diagnostic devices, which are exterior to the body of a patient, can detect various features of human tissues in a noninvasive way [28].
The paper is organized as follows. The next section is dedicated to Periodic Haar Piecewise-Linear Transform. Section 3 introduces a new method for data embedding. Section 4 presents the potential application of the proposed algorithm for the detection of image manipulations. In Section 5 the experimental results are presented and the comparison between the proposed solution and the DCT approach is discussed. Finally, Section 6 contains the conclusions and future work.
2. Periodic Haar Piecewise-Linear PHL Transform
This section covers the most important theoretical aspects related to Periodic Haar Piecewise-Linear (PHL) transform. The thorough description and further information are presented in detail in [29]. The Haar functions are defined by the following formulas:
where , .
In turn, the PHL functions can be calculated by performing the integration of these Haar functions. It can be realized by using the below formulas:
where ;
k—index of group of PHL functions;
m—number of period.
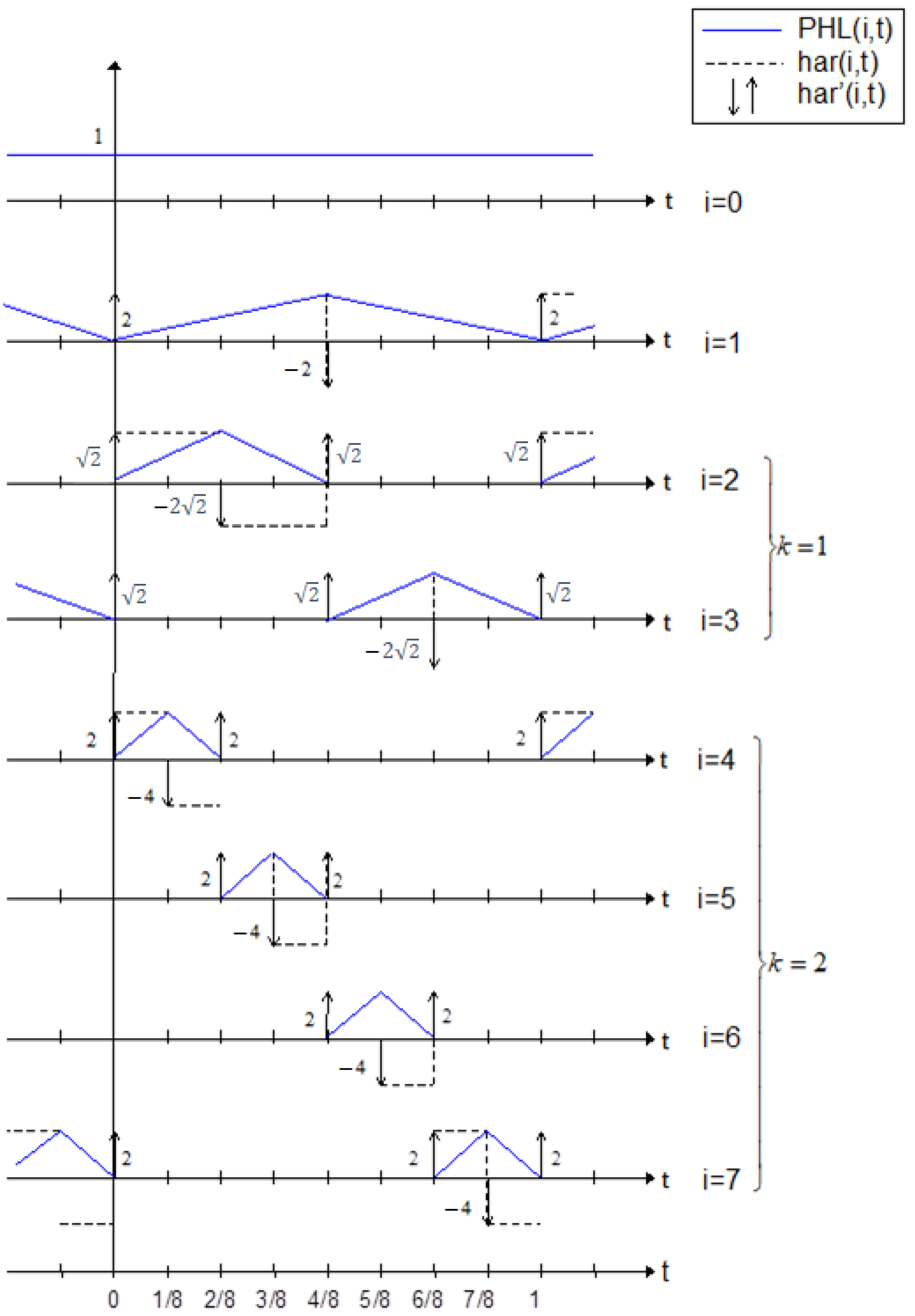
Figure 1 depicts the derivatives (in distributive sense) of Haar functions. The PHL functions are linearly independent but they do not satisfy the orthogonality condition.
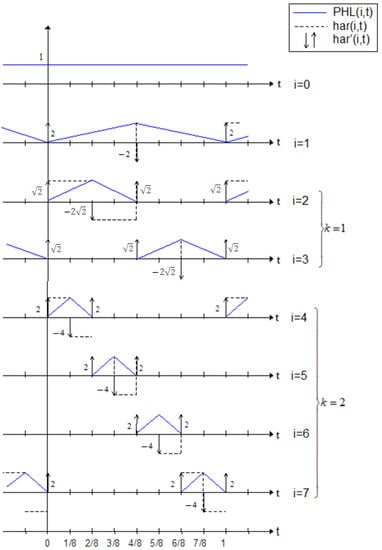
Figure 1.
Set of PHL functions for N = 8.
2.1. One-Dimensional PHL Transform
To perform forward and inverse PHL transform, the following matrix equations can be used:
- a.
- Forward transform
- b.
- Inverse transform
where [C(N)]—vector of PHL coefficients (PHL spectrum);
[X(N)]—vector of sampled signal;
[PHL(N)]—matrix of forward transform;
[IPHL(N)]—matrix of inverse transform;
—diagonal matrix of normalization.
The first row of the forward transform matrix consists of number one at the first position and the remaining elements are equal to zero. Other rows are composed of derivatives (in a distributive sense) of periodic Haar functions. The matrix for the inverse transform [IPHL(N)] is constructed in such a way that particular rows consist of PHL function values calculated for the same argument. For instance, the [PHL(N)] and [IPHL(N)] matrices, for N = 8, are presented below:
In this case, according to Equation (5), the diagonal matrix of normalization takes the following form:
It can be observed that:
where [I(N)] is the identity matrix.
2.2. Two-Dimensional PHL Functions and Transform
The 2D PHL transform can be formulated in the following way:
- a.
- Forward transform
- b.
- Inverse transform
where —matrix of 2D signal;
—matrix of coefficients (2D PHL spectrum);
—matrices of 1D PHL forward transform;
—matrices of 1D PHL inverse transform;
—diagonal matrices of normalization.
The non-periodic Haar Piecewise-Linear Transforms have an order () while the PHL Transforms have an order (N). Due to this fact, PHL transforms can be applied in digital signal and image processing since the data usually has a dimension that is a power of 2.
3. Data Embedding in PHL Spectrum
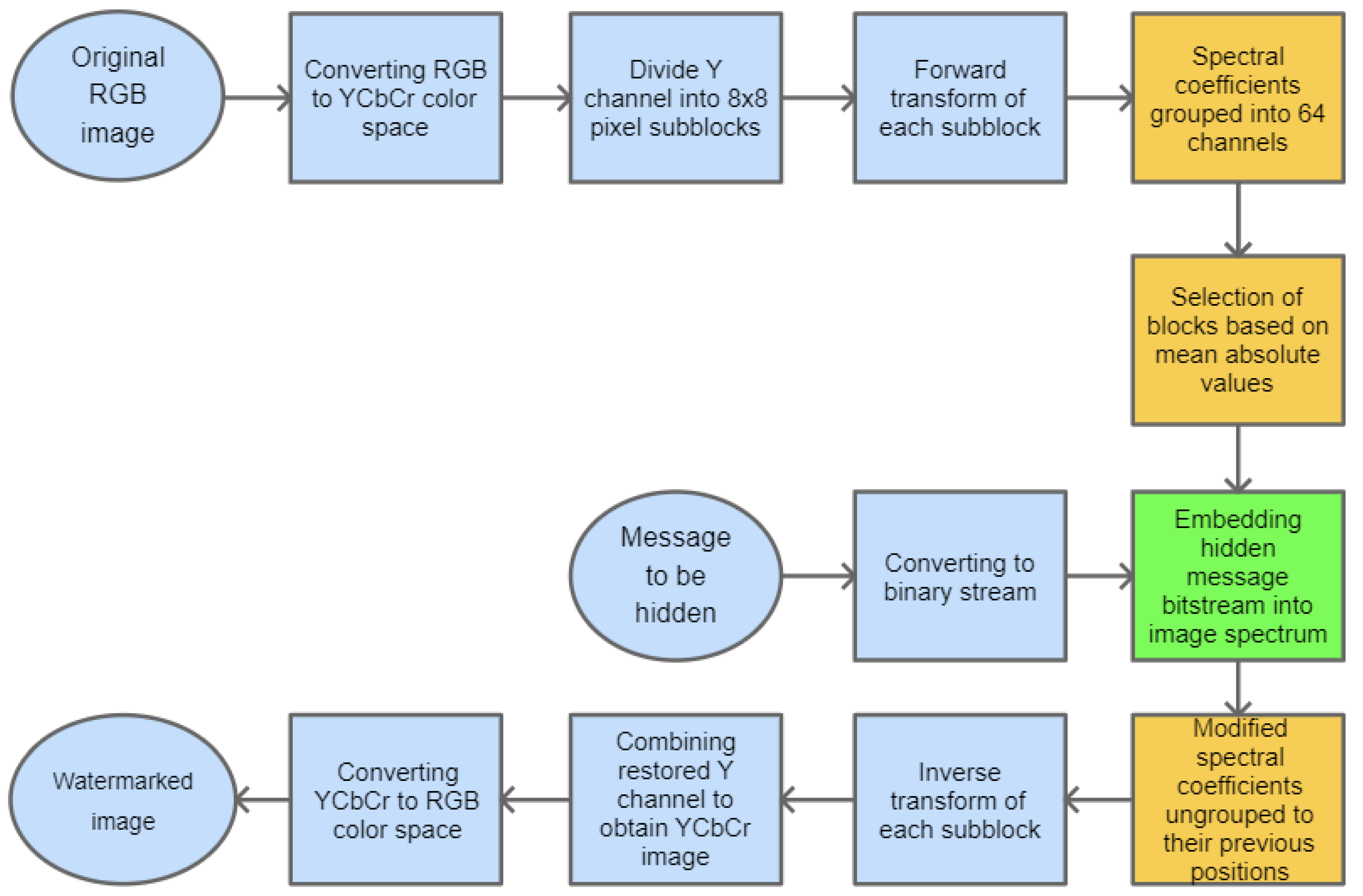
The watermarking approach, presented in this paper, is based on inserting secret information in the PHL transform domain. The method assumes that the PHL spectrum is calculated only for the luminance channel of the given image, representing its grayscale version. To speed up the computations, the forward transform operation is performed on smaller subimages, i.e., blocks with the size: 8 × 8 pixels, using Equation (10) and the matrices (6) and (7).
As a result, after performing the above process to the input signal, we get its spectral coefficients in the PHL domain. Typically, a limited number of these coefficients carry most of the signal energy [30,31].
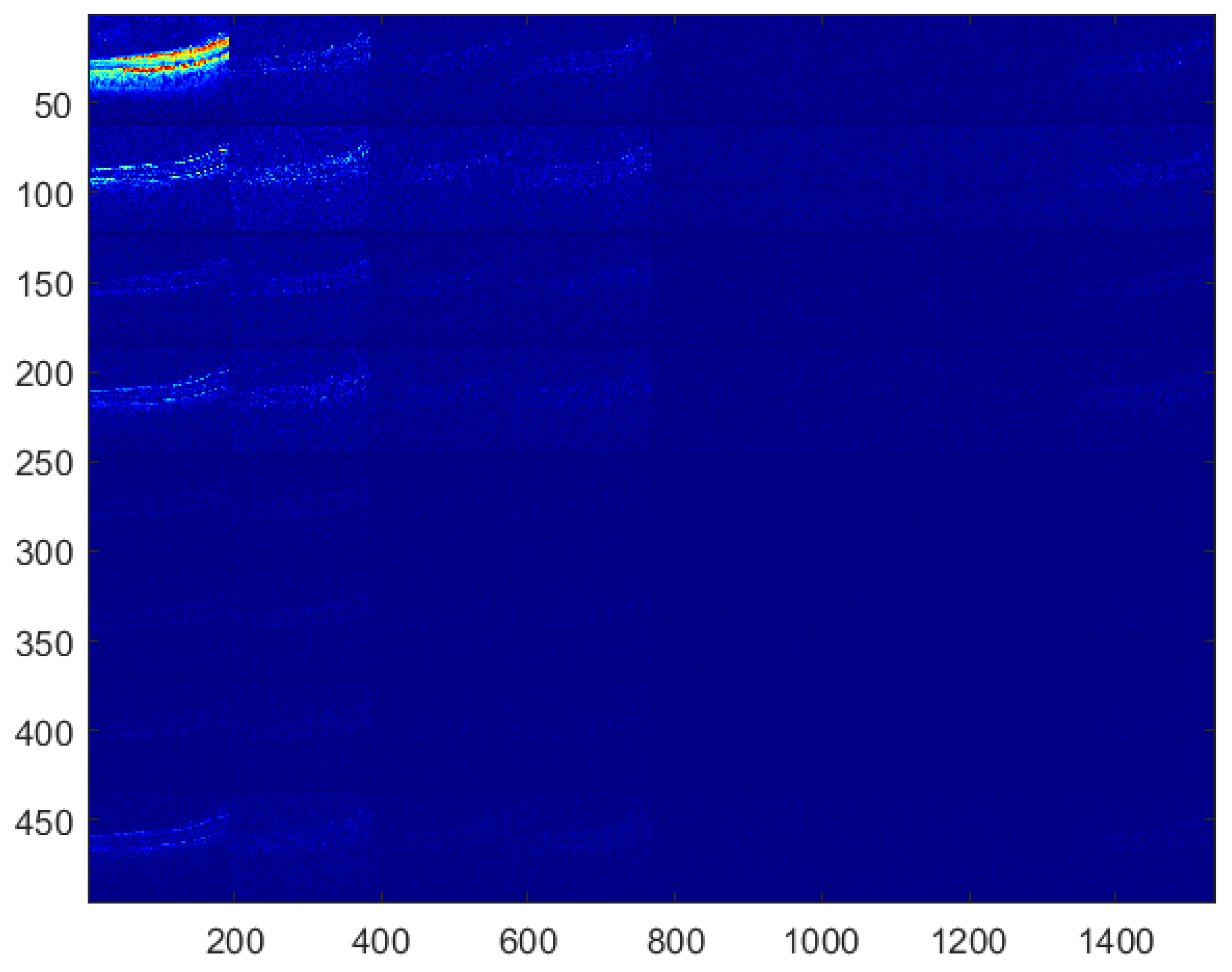
The PHL transform may be used for image compression purposes [32]. In this task, the spectral coefficients that are above a given threshold are kept while the remaining ones are set to zero. Following this approach, our method assumes embedding of the watermark by modification of the coefficients having relatively low values. To perform this operation, the PHL coefficients are split into channels. Each channel groups the spectral coefficients with the same indices from each block processed in the forward transform step. This way, we obtain 64 PHL transform channels. The study of a set of various images and their spectra indicates that the top-left channel cumulates most of the signal energy. It is well depicted in Figure 2 which shows the PHL spectrum coefficients after grouping into 64 channels.
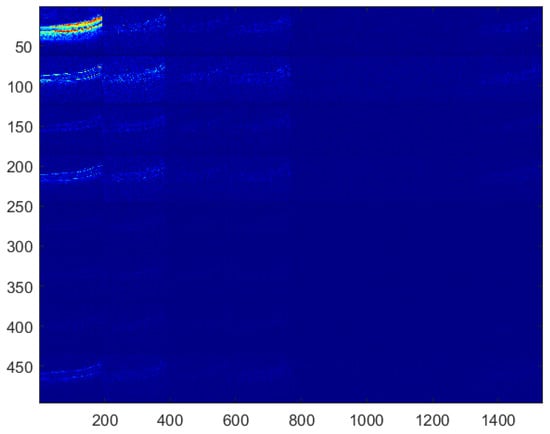
Figure 2.
PHL spectrum coefficients grouped into channels.
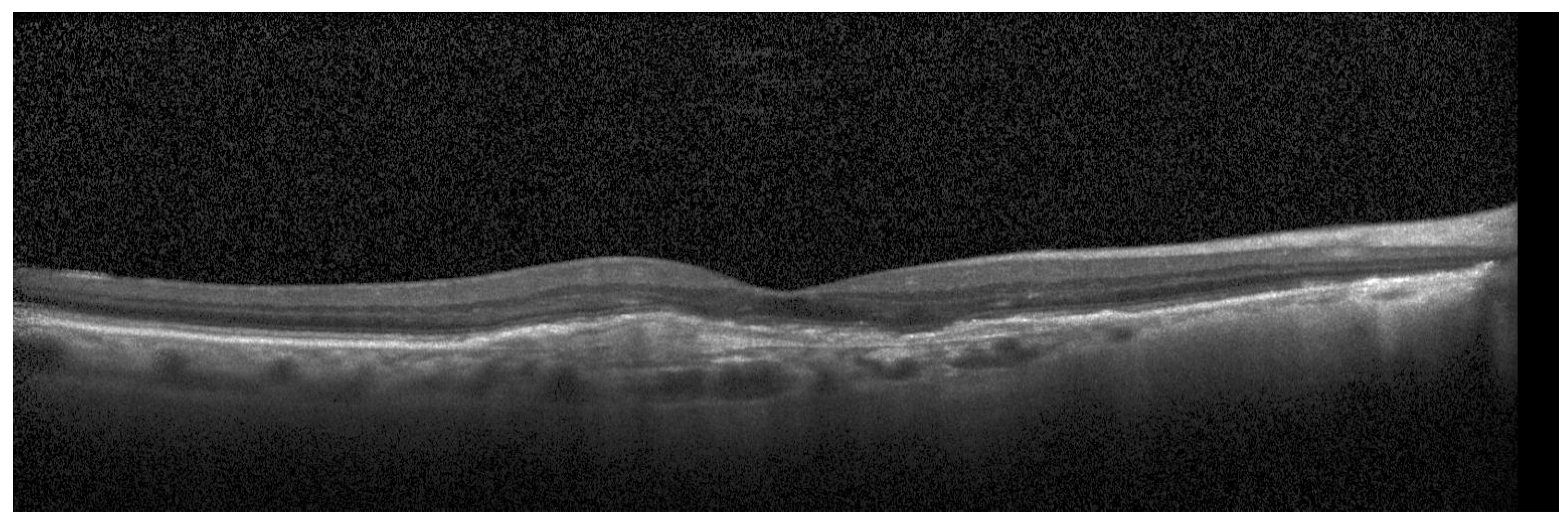
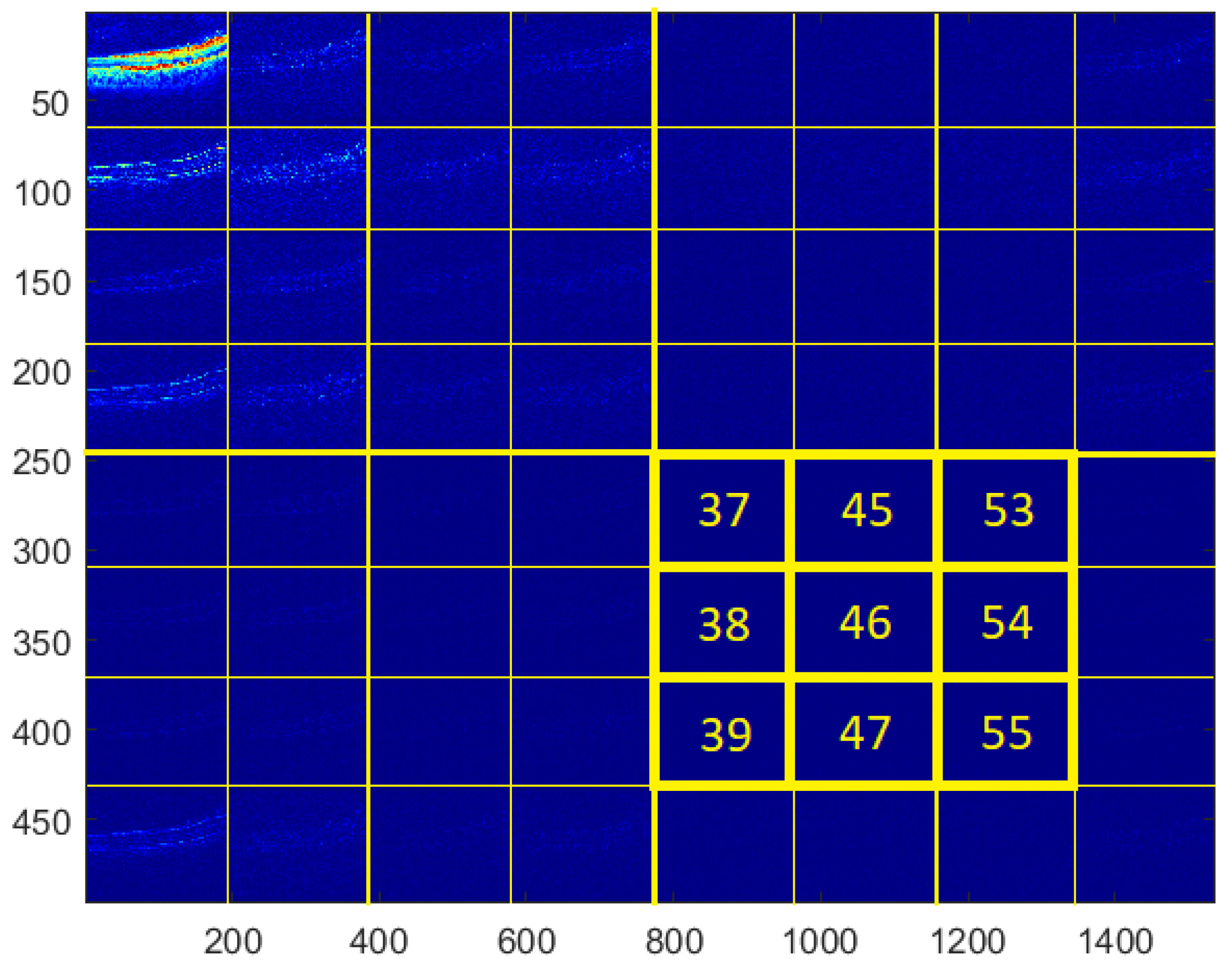
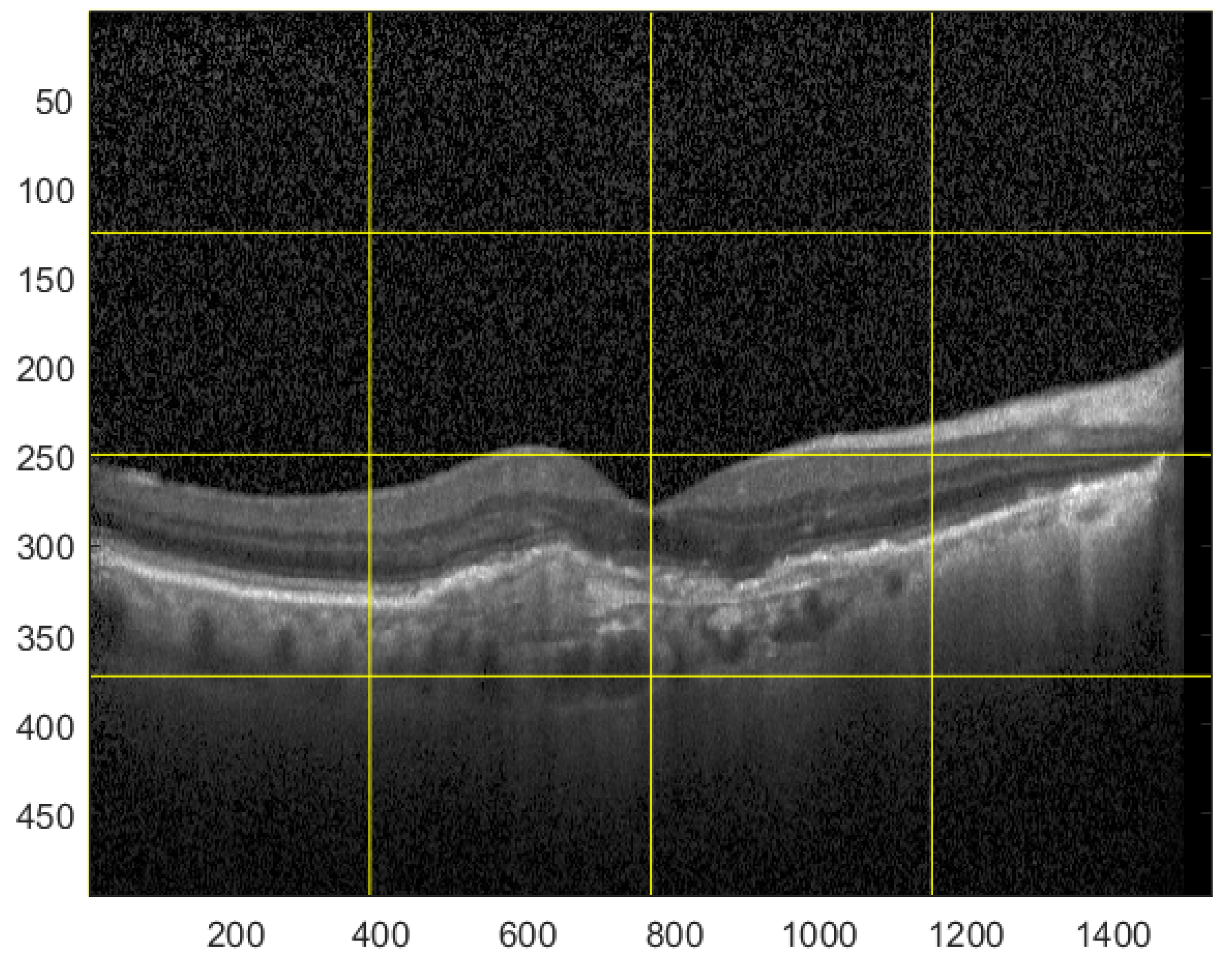
For the testing purpose and the presentation of the image manipulation detection method in the following section, the Optical Coherence Tomography (OCT) images, having the resolution of 1536 × 496 pixels, were used [33]. The OCT is a non-invasive imaging examination that uses light waves to take cross-section pictures of the human retina. One sample image of this type is shown in Figure 3. The tests show that the blocks: 37–39, 45–47, and 53–55, marked in Figure 4, should be usually selected for the process of inserting secret information. This conclusion is based on the analysis of spectra of diverse images with varying content and characteristics. For the selection of the best channel for watermark embedding, the mean of all absolute values from each block is calculated. The channel with the lowest mean is chosen as the first candidate for the subsequent data embedding operation. To increase the capacity of the watermark, other blocks can be selected afterward, considering their mean values sorted in ascending order.
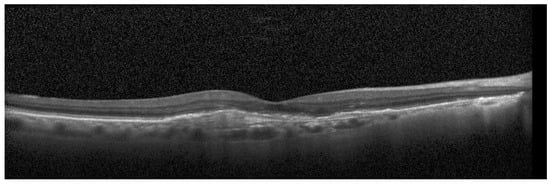
Figure 3.
Sample OCT image.
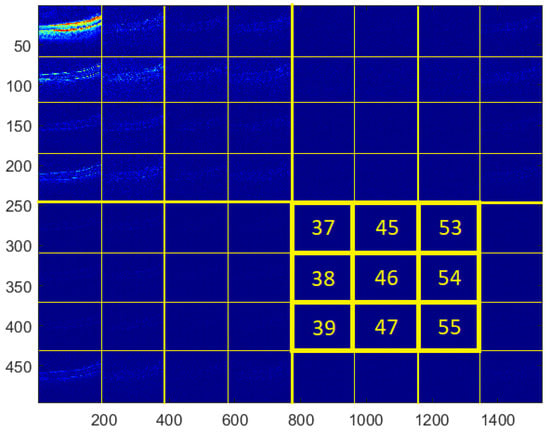
Figure 4.
Blocks selected for data embedding.
The selected channel coefficients are replaced with the consecutive bits of the message that is to be hidden in the image. Subsequently, the channel coefficients need to be relocated back to their previous positions. The final step is the inverse PHL transform of the modified image spectrum that results in the image with an inserted watermark. The stages of the whole embedding process are presented in Figure 5.
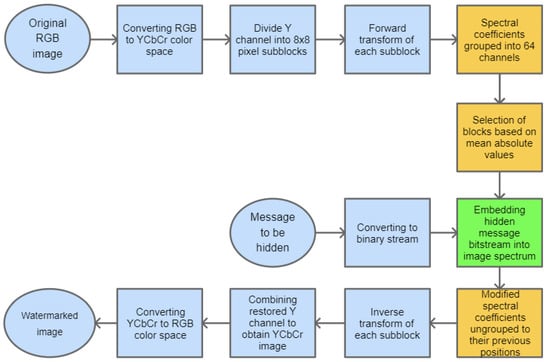
Figure 5.
Block diagram for the base process of watermark embedding.
For the recovery of the embedded information, the same steps as previously need to be performed—the forward transform, the grouping of PHL coefficients, and finally extracting information from the selected channel or channels.
The selection of nine blocks for watermark embedding can be performed adaptively, as described previously, or arbitrarily. In this way, the chosen order can be used as an additional key at the watermark extraction phase.
4. Image Manipulation Detection
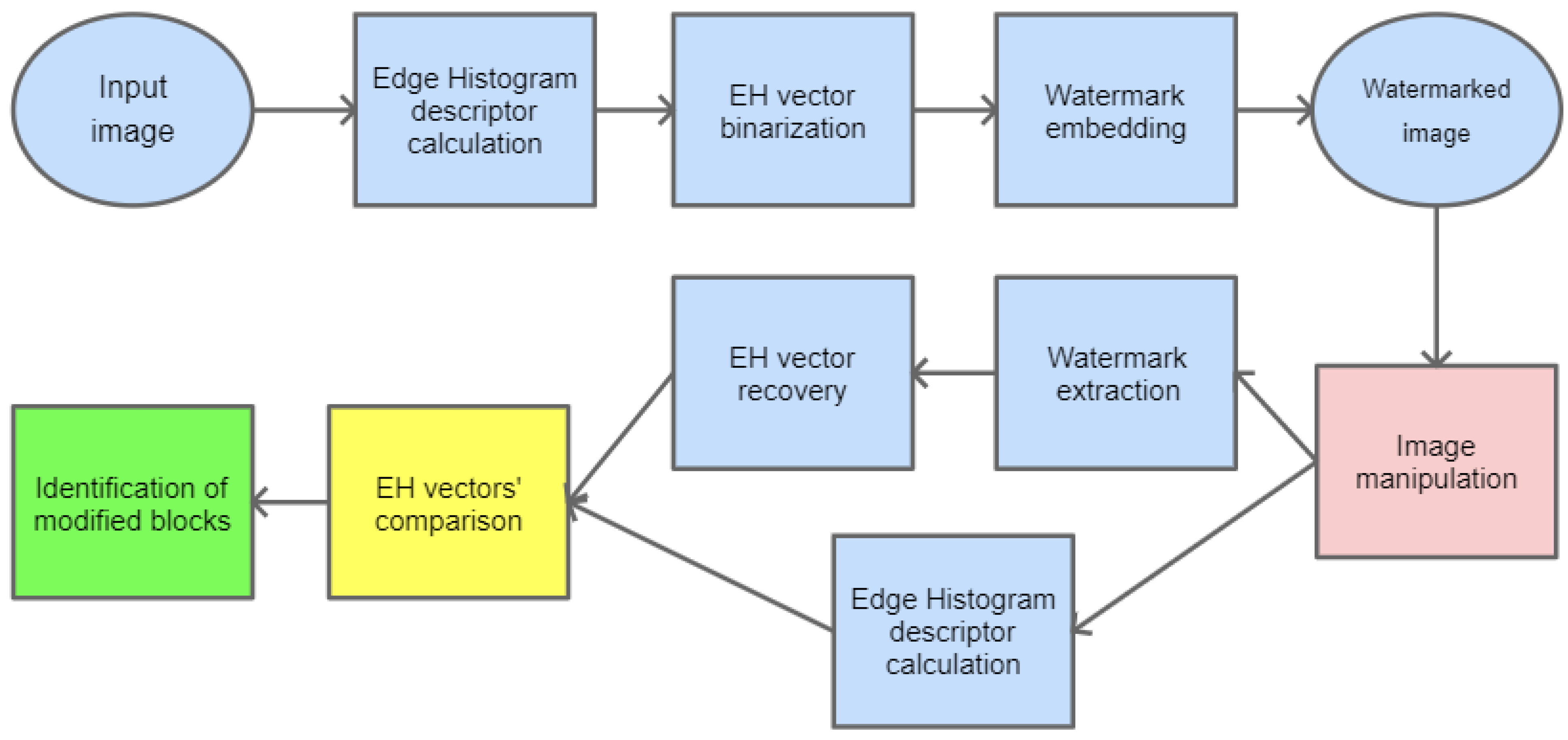
The information embedded as a watermark can be used to detect potential manipulations of the image. It would be beneficial if the hidden message could somehow describe the content of the image so that later, during the recovery phase, it could be compared with a newly generated description for the watermarked image. In case these two descriptions differ significantly, it could be stated that the watermarked image has been tampered with.
In this paper, as a method for image description, MPEG-7 Edge Histogram descriptor (EHD) has been selected. It is a visual texture descriptor that captures the spatial distribution of five types of edges in an image: vertical, horizontal, two diagonals, and non-directional edge. It is created by dividing an input image into 16 (4 × 4) blocks, which is depicted in Figure 6. For each block, a histogram of all the above-mentioned types of edges is calculated. Therefore, it consists of values that compose this descriptor [34].
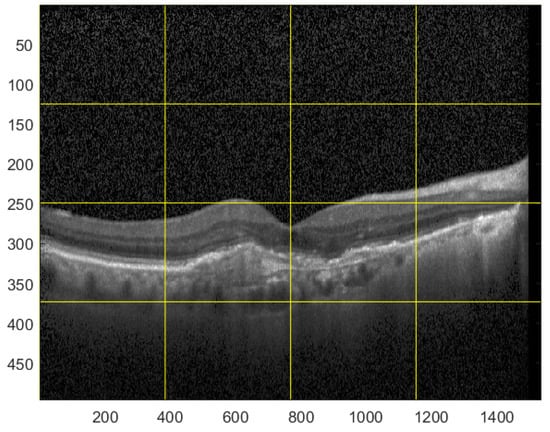
Figure 6.
Blocks for which EHD descriptor is calculated.
In the first stage, the Edge Histogram descriptor is calculated for the given image. Its values are binarized to create a message bitstream which is then embedded into the image.
To detect potential manipulation of the watermarked image, it is necessary to calculate the EHD descriptor again and compare it with the one recovered from the watermark. The particular steps for image manipulation detection are shown in Figure 7.
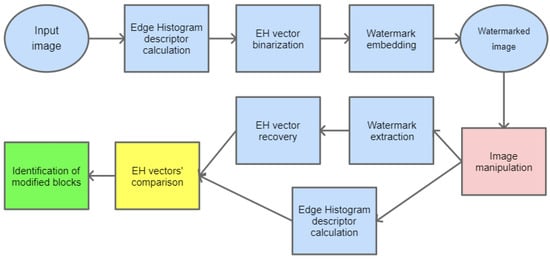
Figure 7.
Block diagram for image manipulation detection process.
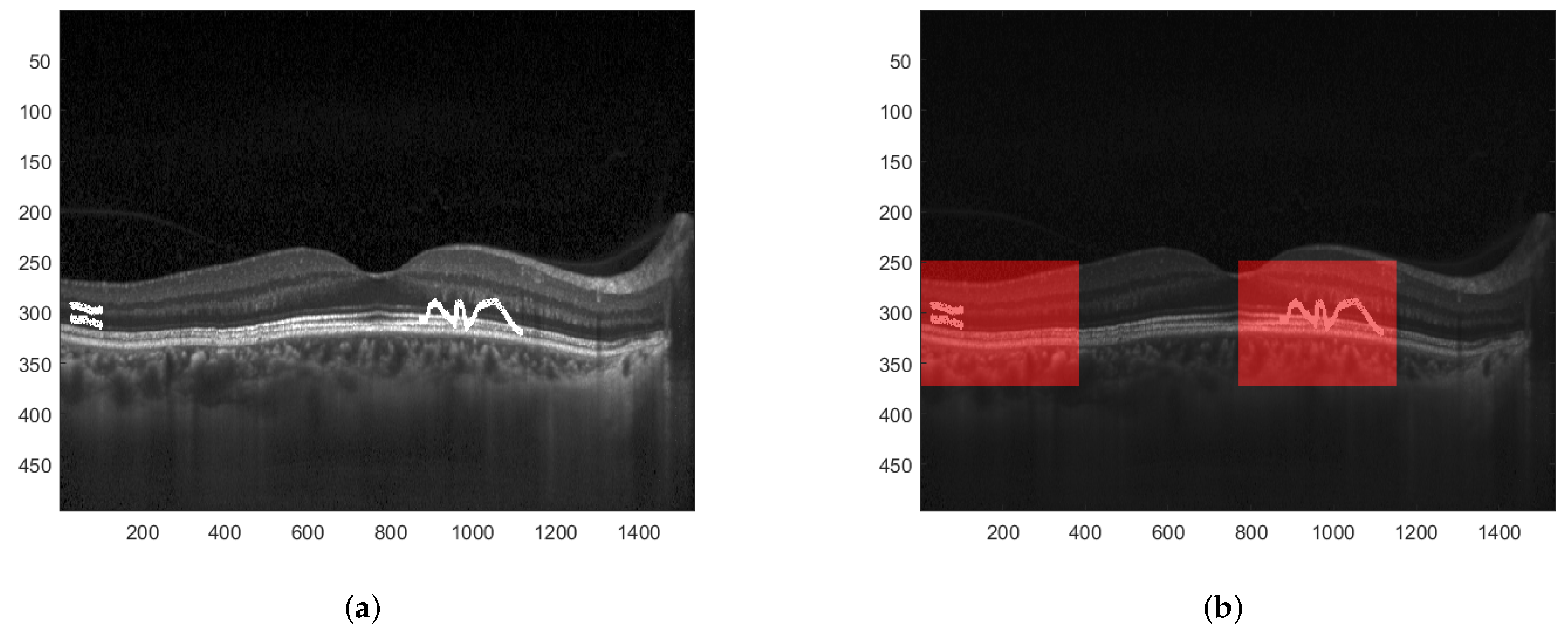
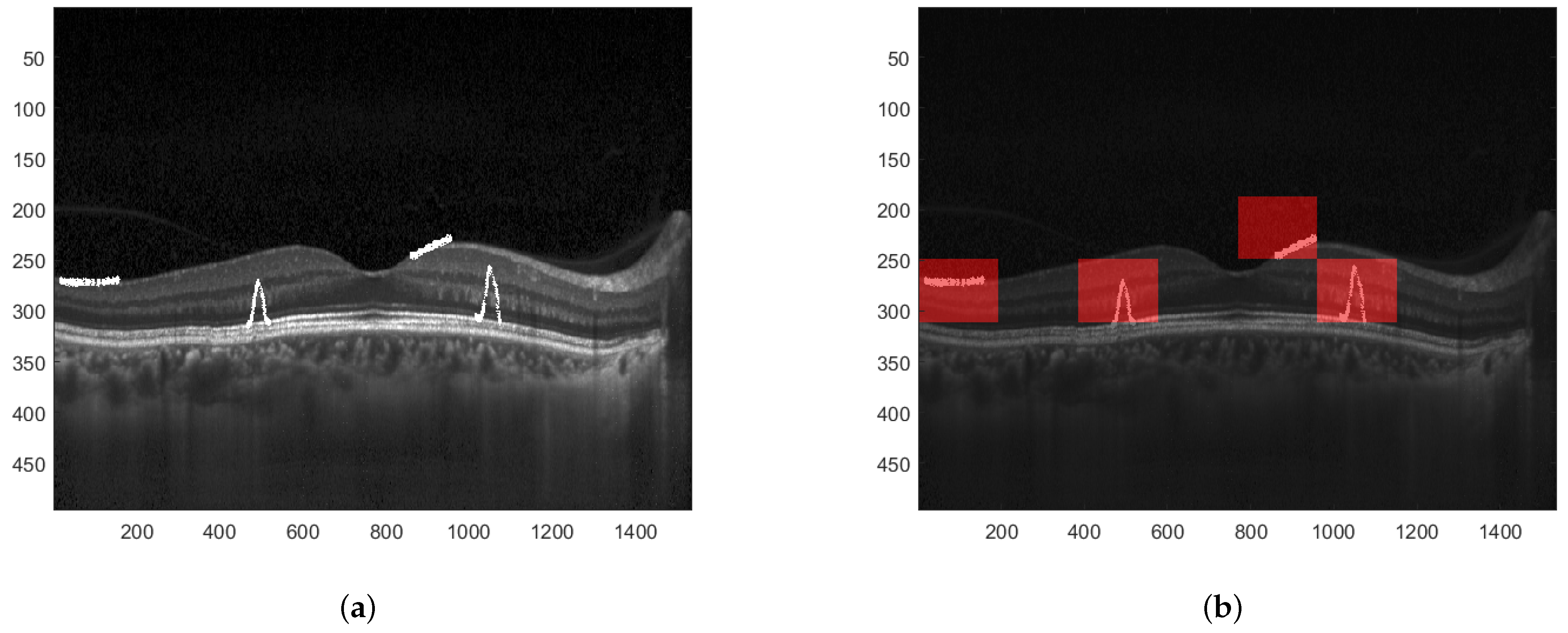
When the difference between particular values of both descriptors is significant, one can determine that the image has been modified. Furthermore, since the EHD descriptor returns 5 values for each of the 16 blocks, the proper analysis of differences at the given positions can precisely indicate which of these 16 blocks have been tampered with. This is presented in Figure 8. A sample tampered image is presented in Figure 8a and the image with selected blocks that have been modified is shown in Figure 8b.
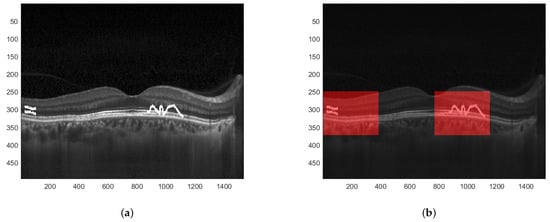
Figure 8.
Result of image manipulation detection. (a) Tampered watermarked image. (b) Detected regions where the image has been manipulated.
To obtain better precision for image manipulation detection the image can be initially divided into smaller sub-images which are then further processed following the same steps as in the previous example. In such a way, the blocks that are identified to have been tampered with are of smaller dimensions. This is depicted in Figure 9.
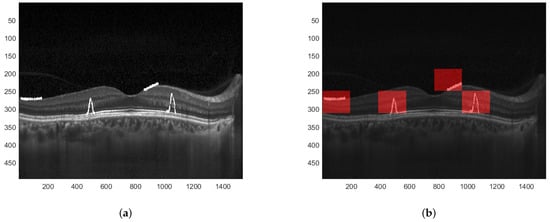
Figure 9.
Result of image manipulation detection with greater precision. (a) Tampered watermarked image. (b) Detected regions with greater precision.
5. Experimental Results
The verification of the proposed algorithm is performed by measuring of Peak Signal to Noise Ratio (PSNR), which represents the visual quality of a watermarked image in relation to the total size of a watermark. Additionally, to consider the human visual system (HVS), Structural Similarity (SSIM) metric [35] and Universal Quality Image (UQI) index [36] are measured to assess the quality of the image with an embedded watermark. Furthermore, the bit error rate (BER) is also analyzed, for different lengths of the hidden message. The measurements of these ratios were performed for watermarks inserted in DCT and PHL transform domains so that the performance of both approaches may be compared. For test purposes, a random bit stream is used as a watermark message. The tests were carried out in a MATLAB environment. The referenced DCT method originates from the one described in [3].
For test purposes, 23 images from ‘Images 4k’ dataset [37] have been selected. The dataset contains 2057 files. The test images were selected in such a way that they represent different visual characteristics, i.e., low and high contrast and brightness as well as various color distributions. The dimensions of the images were reduced by half to 1920 × 1080 size so that the calculations and the watermark embedding process are speeded up.
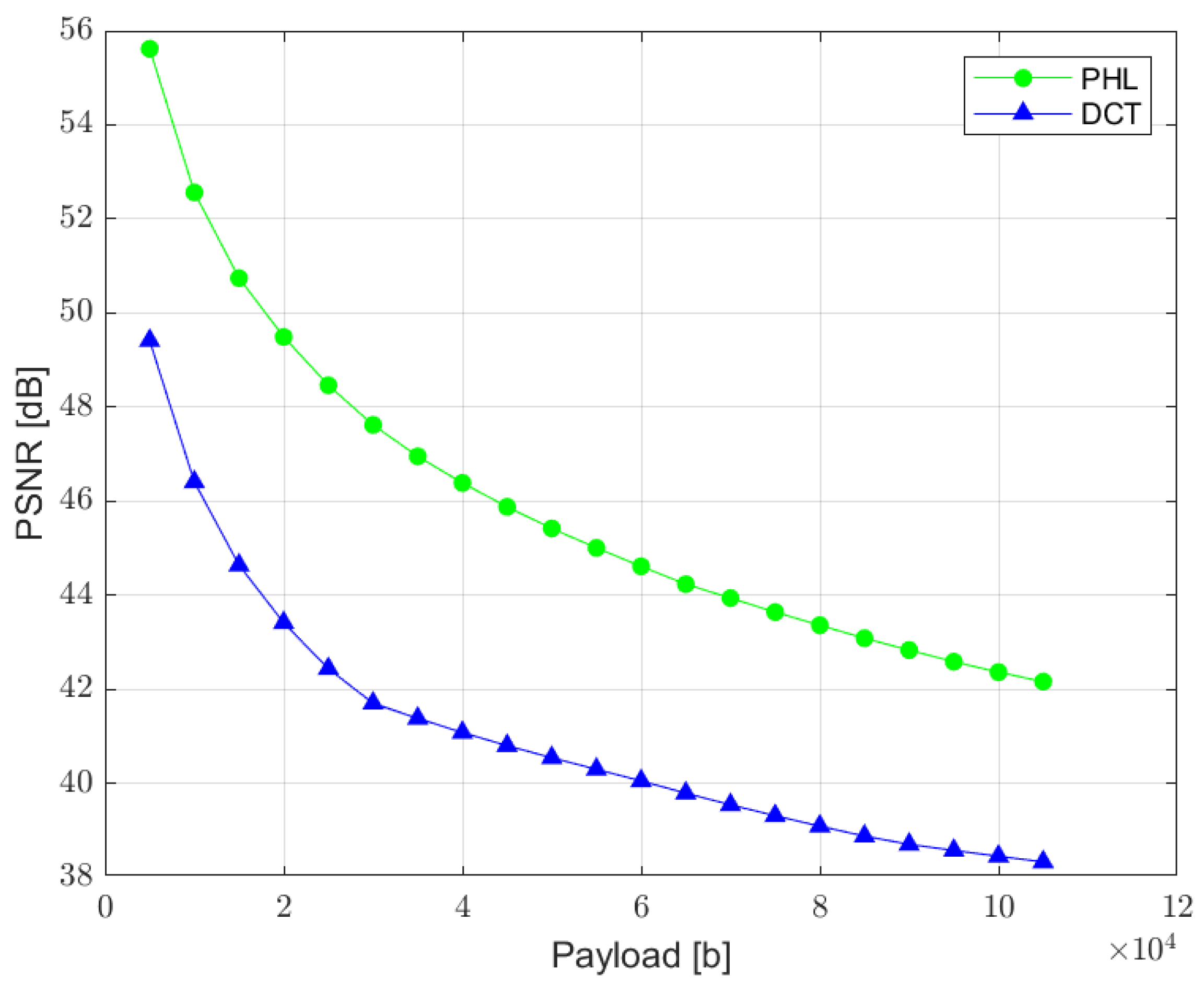
The relation between the PSNR ratio and the length of a hidden bit stream is presented in Figure 10. It can be observed that a perceptual quality of an image with a watermark inserted in the PHL spectrum is consistently better than in the case of a watermark embedded in the DCT domain. It is assumed that the PSNR above 35 dB indicates that the two images being compared are visually identical, with no perceptual loss of quality [38]. Therefore, both techniques provide satisfying results as far as the imperceptibility of a watermark is concerned, for the size of a watermark exceeding even 100,000 bits.
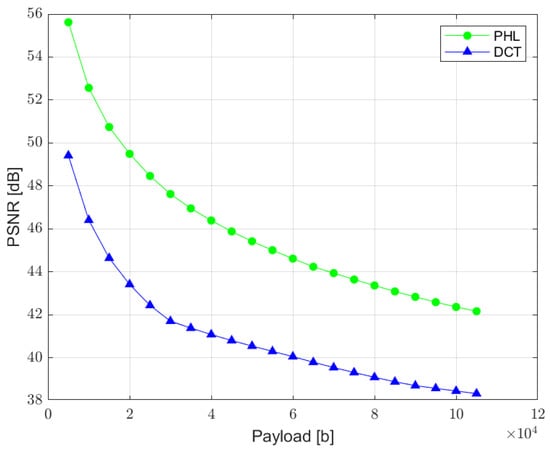
Figure 10.
Relation between PSNR ratio and the watermark capacity (PHL vs. DCT).
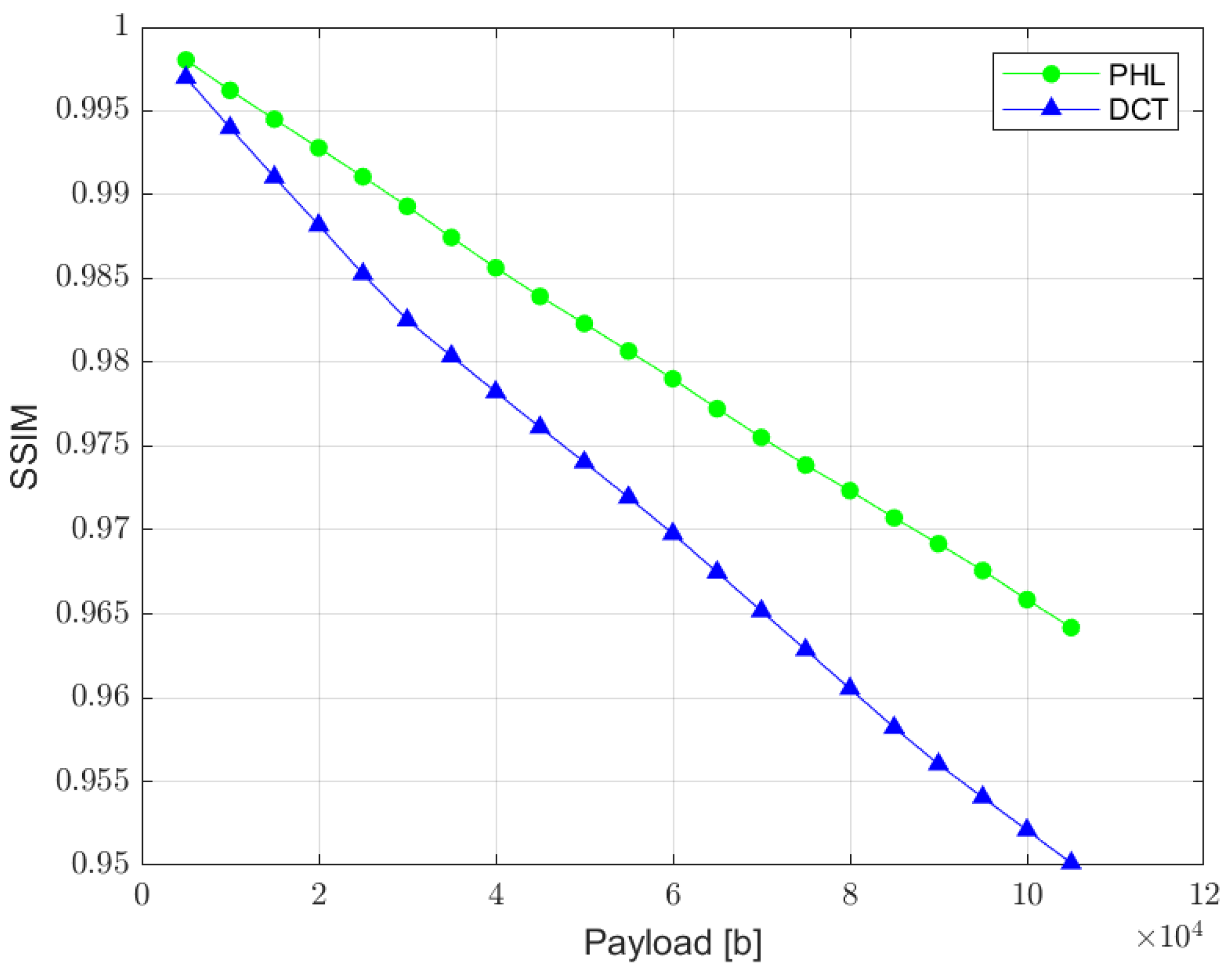
SSIM is a quality assessment metric based on the visual changes in local structure and contrast between two images. It provides a good approximation of human visual perception. The metric values can range from 0 to 1, where 1 indicates perfect similarity [35]. The relation between SSIM and the total size of a watermark is presented in Figure 11. The results measured for the PHL method are slightly better than the ones achieved in the DCT approach. However, both methods according to this metric provide satisfying results.
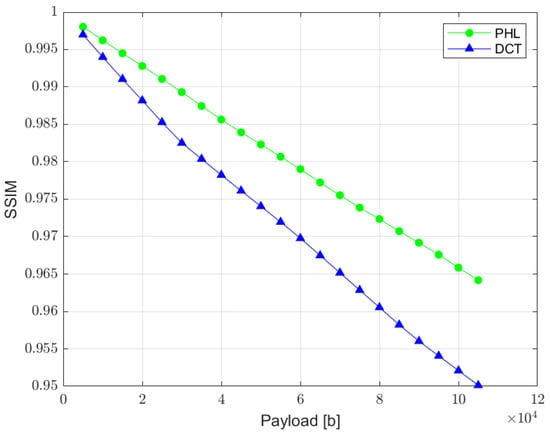
Figure 11.
Relation between SSIM metric and the watermark capacity (PHL vs. DCT).
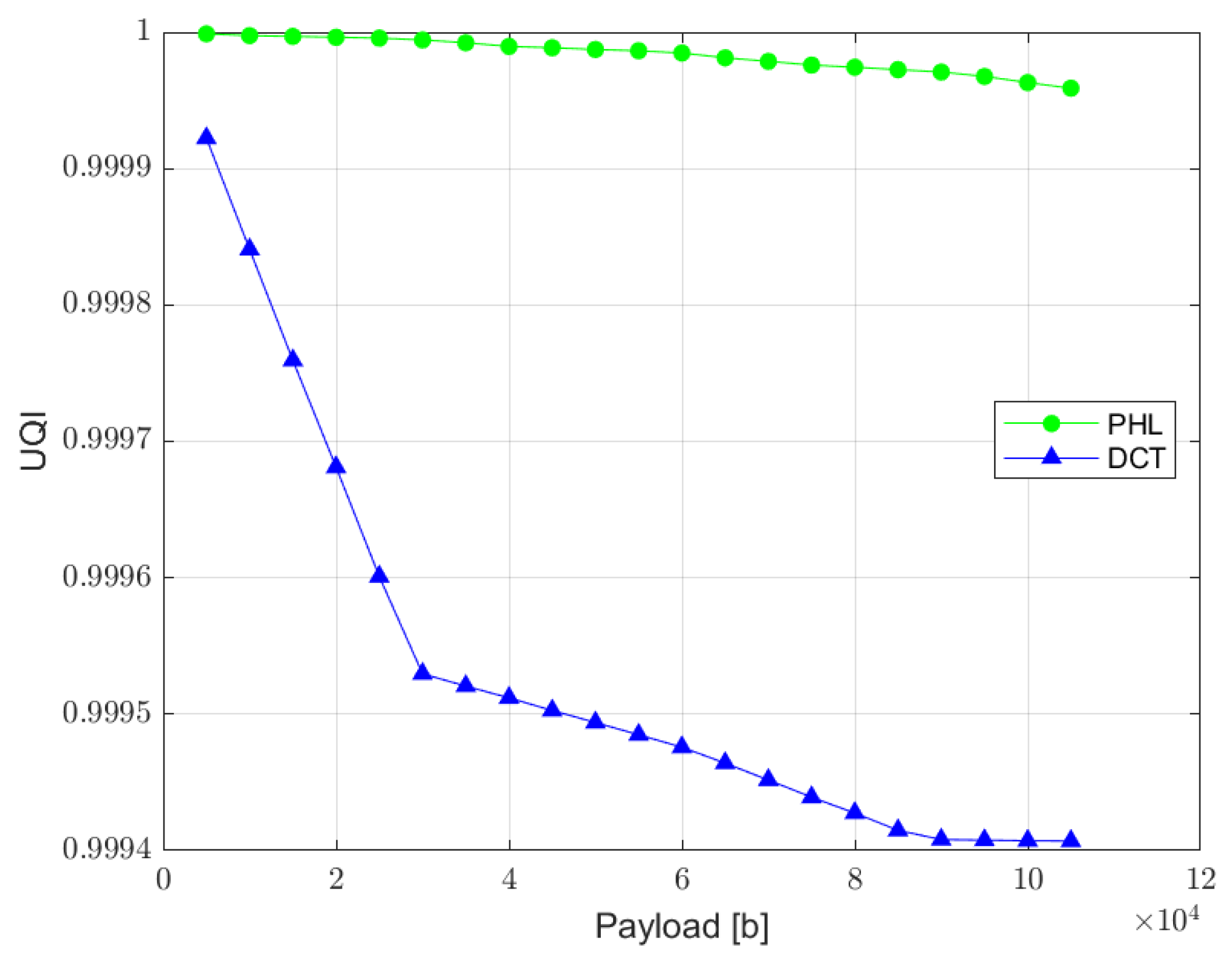
UQI index is designed to model image distortion as a combination of three factors: loss of correlation, luminance distortion, and contrast distortion. Although it does not employ any human visual system model, it was proved to be consistent with subjective quality assessment [36]. UQI index can vary between −1 and 1, where value 1 indicates no distortion present in the image. The relation between UQI and the length of a hidden message is presented in Figure 12.
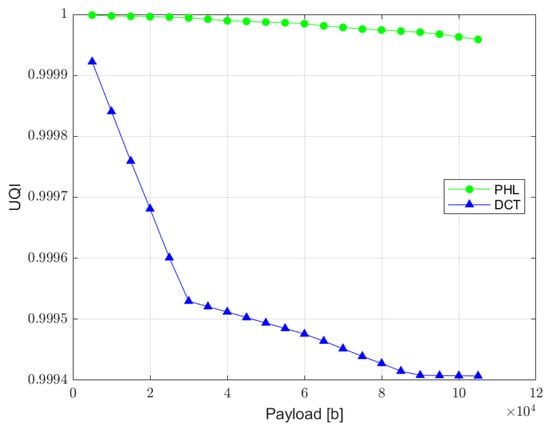
Figure 12.
Relation between UQI index and the watermark capacity (PHL vs. DCT).
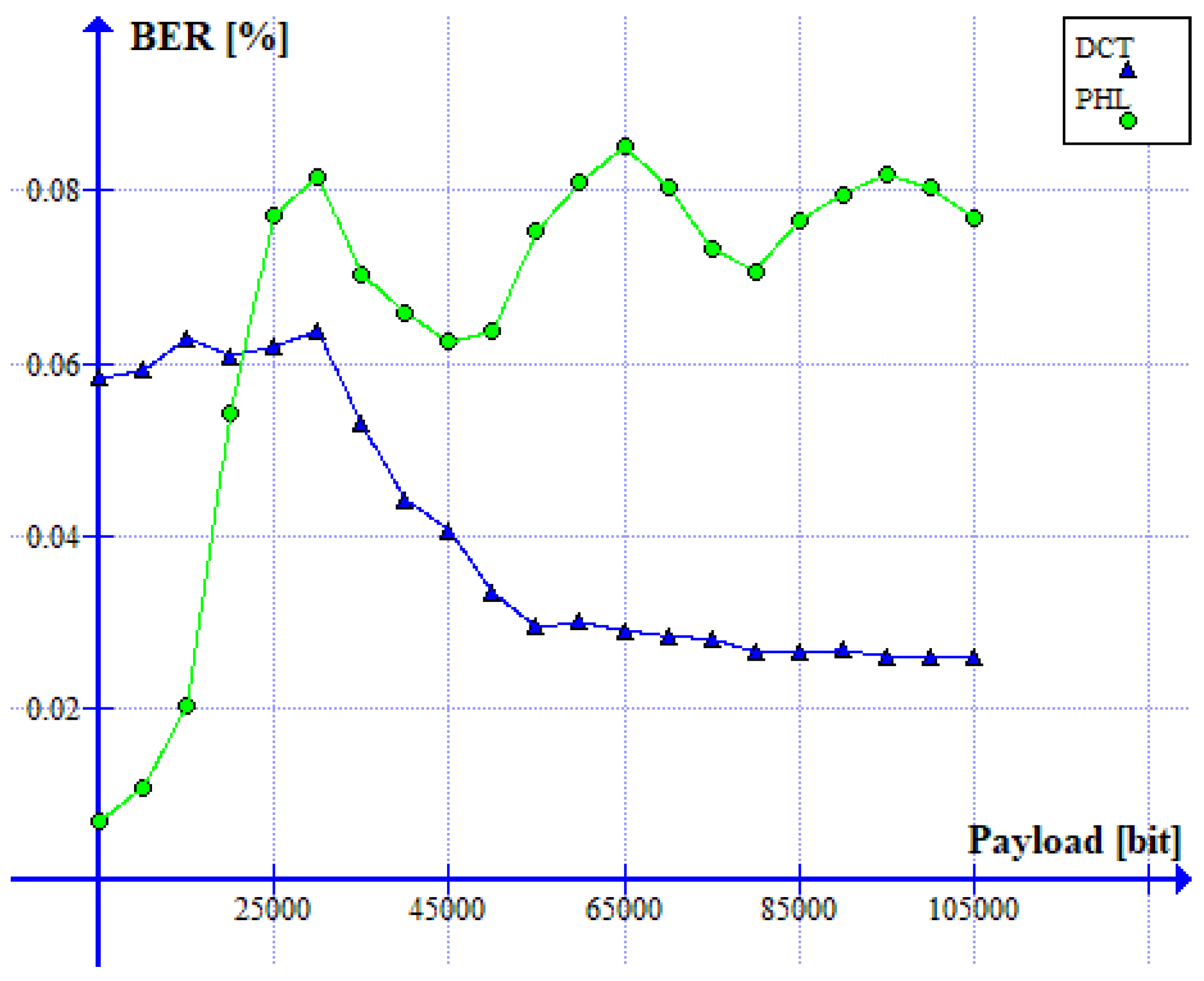
The relation between the BER ratio and the size of a watermark is shown in Figure 13. It can be noticed that both methods guarantee a low bit error rate (<0.1%) for the watermark size ranging from 5000 to 105,000 bits. Therefore, both solutions are useful when a limited, but still, in most applications, sufficient, amount of information needs to be hidden in an image.
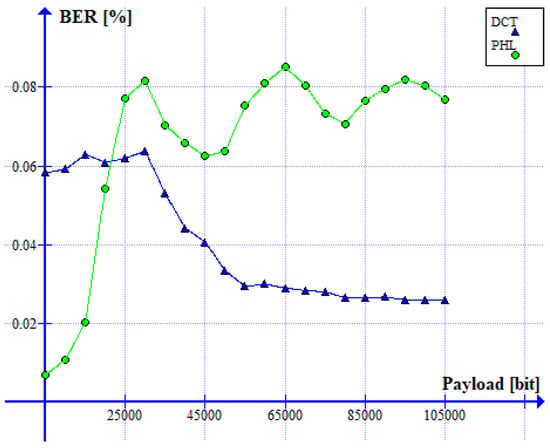
Figure 13.
Relation between BER ratio and the watermark capacity (PHL vs. DCT).
6. Conclusions and Future Work
We have presented a new watermarking scheme that is based on inserting a message bitstream in the PHL transform domain. The method offers a high capacity for hidden information and simultaneously satisfies the initial requirements of low image distortion and high accuracy during the watermark recovery stage. Therefore, it is a promising technique that can be used in a wide range of multimedia systems and services with emphasis put on medical applications where the aforementioned conditions need to be met. In addition, a method for the detection of image manipulation has been presented.
Further investigations will cover potential enhancements so that the method could be robust to various types of attacks. Finally, we plan to apply our solution in many applications in the upcoming future.
Author Contributions
Conceptualization, P.B. and A.D.; methodology, P.B. and A.D.; software, P.B.; validation, P.B. and J.D.; formal analysis, P.B. and J.D.; investigation, P.B.; writing—original draft preparation, P.B.; writing—review and editing, J.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the European Union’s Horizon 2020 Research and Innovation Programme, under Grant Agreement no. 830943, the ECHO project.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Sharma, P.K.; Sau, P.C.; Sharma, D. Digital image watermarking: An approach by different transforms using level indicator. In Proceedings of the 2015 Communication, Control and Intelligent Systems (CCIS), Mathura, India, 7–8 November 2015; pp. 259–263. [Google Scholar]
- Zhou, N.R.; Hou, W.M.X.; Wen, R.H.; Zou, W.P. Imperceptible digital watermarking scheme in multiple transform domains. Multimed Tools Appl. 2018, 77, 30251–30267. [Google Scholar] [CrossRef]
- Lan, T.-H.; Tewfik, A.H. A novel high-capacity data-embedding system. IEEE Trans. Image Process. 2006, 15, 2431–2440. [Google Scholar]
- Kim, W.-H.; Hou, J.-U.; Jang, H.-U.; Lee, H.-K. Robust Template-Based Watermarking for DIBR 3D Images. Appl. Sci. 2018, 8, 911. [Google Scholar] [CrossRef]
- Li, H.; Guo, X. Embedding and Extracting Digital Watermark Based on DCT Algorithm. J. Comput. Commun. 2018, 6, 287–298. [Google Scholar] [CrossRef]
- Xu, Z.J.; Wang, Z.Z.; Lu, Q. Research on Image Watermarking Algorithm Based on DCT. Procedia Environ. Sci. 2011, 10, 1129–1135. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, H.; Wang, C. A Robust Image Watermarking Technique Based on DWT, APDCBT, and SVD. Symmetry 2018, 10, 77. [Google Scholar] [CrossRef]
- Narang, M.; Vashisth, S. Digital Watermarking using Discrete Wavelet Transform. Int. J. Comput. Appl. 2013, 74, 34–38. [Google Scholar] [CrossRef]
- Li, L.; Bai, R.; Lu, J.; Zhang, S.; Chang, C.-C. A Watermarking Scheme for Color Image Using Quaternion Discrete Fourier Transform and Tensor Decomposition. Appl. Sci. 2021, 11, 5006. [Google Scholar] [CrossRef]
- Liao, X.; Li, K.; Yin, J. Separable data hiding in encrypted image based on compressive sensing and discrete fourier transform. Multimed Tools Appl. 2017, 76, 20739–20753. [Google Scholar] [CrossRef]
- Hasan, N.; Islam, M.S.; Chen, W.; Kabir, M.A.; Al-Ahmadi, S. Encryption Based Image Watermarking Algorithm in 2DWT-DCT Domains. Sensors 2021, 21, 5540. [Google Scholar] [CrossRef]
- Hazim, N.; Saeb, Z.; Hameed, K. Digital Watermarking Based on DWT (Discrete Wavelet Transform) and DCT (Discrete Cosine Transform). Int. J. Eng. Technol. 2019, 7, 4825–4829. [Google Scholar]
- Akter, A.; Nur-E-Tajnina; Ullah, M. Digital image watermarking based on DWT-DCT: Evaluate for a new embedding algorithm. In Proceedings of the 2014 International Conference on Informatics, Electronics & Vision (ICIEV), Dhaka, Bangladesh, 23–24 May 2014. [Google Scholar] [CrossRef]
- He, Y.; Hu, Y. A Proposed Digital Image Watermarking Based on DWT-DCT-SVD. In Proceedings of the 2018 2nd IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Xi’an, China, 25–27 May 2018; pp. 1214–1218. [Google Scholar]
- Bogacki, P.; Dziech, A. Analysis of New Orthogonal Transforms for Digital Watermarking. Sensors 2022, 22, 2628. [Google Scholar] [CrossRef]
- Yan, D.; Wang, R. Data Hiding for Audio Based on Piecewise Linear Haar Transform. In Proceedings of the 2008 Congress on Image and Signal Processing, Sanya, China, 27–30 May 2008; pp. 688–691. [Google Scholar]
- Yang, L.; Hao, P.; Zhang, C. Progressive Reversible Data Hiding by Symmetrical Histogram Expansion with Piecewise-Linear Haar Transform. In Proceedings of the 2007 IEEE International Conference on Acoustics, Speech and Signal Processing—ICASSP ’07, Honolulu, HI, USA, 15–20 April 2007; pp. II-265–II-268. [Google Scholar]
- Dziech, A.; Tibken, B.; Slusarczyk, P. Image compression using periodic Haar piecewise-linear PHL transform. In Proceedings of the 2002 14th International Conference on Digital Signal Processing Proceedings, Santorini, Greece, 1–3 July 2002; Volume 2, pp. 1333–1336. [Google Scholar]
- Abdallah, H.A.; ElKamchouchi, D.H. Signing and Verifying Encrypted Medical Images Using Double Random Phase Encryption. Entropy 2022, 24, 538. [Google Scholar] [CrossRef] [PubMed]
- Lim, E.Y.S. Data security and protection for medical images. Biomed. Inf. Technol. 2008, 249–257. [Google Scholar] [CrossRef]
- Fornazin, M.; Netto, D.B.; Cavenaghi, M.A.; Marana, A.N. Protecting Medical Images with Biometric Information. In Advances in Computer and Information Sciences and Engineering; Springer: Dordrecht, The Netherlands, 2008. [Google Scholar]
- Bouslimi, D.; Coatrieux, G. Encryption and Watermarking for medical Image Protection. In Medical Data Privacy Handbook; Springer: Cham, Switzerland, 2015. [Google Scholar]
- Thakur, R.; Rohilla, R. Recent advances in digital image manipulation detection techniques: A brief review. Forensic Sci. Int. 2020, 312, 110311. [Google Scholar] [CrossRef] [PubMed]
- Bucci, E.M. Automatic detection of image manipulations in the biomedical literature. Cell Death Dis. 2018, 9, 400. [Google Scholar] [CrossRef]
- Wei, X.; Wu, Y.; Dong, F.; Zhang, J.; Sun, S. Developing an Image Manipulation Detection Algorithm Based on Edge Detection and Faster R-CNN. Symmetry 2019, 11, 1223. [Google Scholar] [CrossRef]
- Yuan, G.; Hao, Q. Digital watermarking secure scheme for remote sensing image protection. China Commun. 2020, 17, 88–98. [Google Scholar] [CrossRef]
- Zhu, P.; Jiang, Z.; Zhang, J.; Zhang, Y.J.; Wu, P. Remote Sensing Image Watermarking Based on Motion Blur Degeneration and Restoration Model. Optik 2021, 248, 168018. [Google Scholar] [CrossRef]
- Short, N.M. Remote Sensing Tutorial: Medical Applications of Remote Sensing. Available online: https://drr.ikcest.org/remote-sensing-tutorial/introduction/Part2_26b.html (accessed on 15 September 2022).
- Dziech, A.; Bogacki, P.; Derkacz, J. A Novel Watermark Method for Image Protection Based on Periodic Haar Piecewise-Linear Transform. In Proceedings of the International Conference on Multimedia Communications, Services and Security, Communications in Computer and Information Science, Kraków, Poland, 8–9 October 2020; Volume 1284. [Google Scholar]
- Dziech, A.; Belgassem, F.; Nern, H.J. Image Data Compression using Zonal Sampling and Piecewise-Linear Transforms. J. Intell. Robot. Syst. 2000, 28, 61–68. [Google Scholar] [CrossRef]
- Baran, R.; Wiraszka, D. Application of Piecewise-Linear Transforms in Threshold Compression of Contours. Logistyka 2015, 4, 2341–2348. [Google Scholar]
- Dziech, A.; Ślusarczyk, P.; Tibken, B.R. Methods of Image Compression by PHL Transform. J. Intell. Robot. Syst. 2004, 39, 447–458. [Google Scholar] [CrossRef]
- Kermany, D.; Goldbaum, M.; Cai, W. Identifying Medical Diagnoses and Treatable Diseases by Image-Based Deep Learning. Cell 2018, 172, 1122–1131. [Google Scholar] [CrossRef]
- Won, C.; Park, D.; Park, S. Efficient Use of MPEG7 Edge Histogram Descriptor. Etri J. 2002, 24, 23–30. [Google Scholar] [CrossRef]
- Wang, Z.; Bovik, A.; Sheikh, H.; Simoncelli, E. Image Quality Assessment: From Error Visibility to Structural Similarity. IEEE Trans. Image Process. 2004, 13, 600–612. [Google Scholar] [CrossRef] [PubMed]
- Wang, Z.; Bovik, A.C. A universal image quality index. IEEE Signal Process. Lett. 2002, 9, 81–84. [Google Scholar] [CrossRef]
- ‘Images 4k’ Dataset from Kaggle. Available online: https://www.kaggle.com/evgeniumakov/images4k (accessed on 19 September 2022).
- Aherrahrou, N.; Tairi, H. PDE based scheme for multi-modal medical image watermarking. Biomed Eng. Online 2015, 14, 108. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).