PUFTAP-IoT: PUF-Based Three-Factor Authentication Protocol in IoT Environment Focused on Sensing Devices
Abstract
:1. Introduction
- Informal (non-mathematical) analysis and formal analysis are performed to prove the security of the proposed PUFTAP-IoT. Formal analysis uses the widely adopted Burrows Abadi Needham (BAN) logic [32] and Real-Or-Random (ROR) model [33]. We also use the scyther simulation tool [34] to show that PUFTAP-IoT is secure in networks over public channels.
- We compare PUFTAP-IoT with other authentication protocols in terms of computation cost, communication cost, and security to analyze its efficiency.
2. Related Works
3. Preliminaries
3.1. The Proposed System Model
- User: The user requests communication to the gateway to use the sensing device. Only registered users can use IoT services by requesting communication to the gateway.
- Sensing device: Sensing devices are smart devices deployed in various IoT environments. Examples in Figure 1 include smart agriculture, vehicles, smart doors, and smart watches. They collect data and provide it to users, and users can use the data to execute any commands they want. Sensing devices also have limited computational power.
- Gateway: All service users and sensing devices must be registered with the gateway. A gateway is a trusted entity that is responsible for the process and regulates authentication requests between users and sensing devices.
3.2. The Adversary Model
- The adversary can learn messages by intercepting messages delivered over insecure, public wireless channels. Through the learned message, the adversary can create a valid message and insert and modify it.
- The adversary can obtain stored values by stealing a valid user’s smart card and sensing device [37].
- The adversary can guess the user’s ID/password pair in polynomial time [21].
- The adversary can perform guessing, impersonation, known session-specific temporary information, and session key disclosure attacks using the acquired values.
3.3. Physical Unclonable Function
- It is impossible to clone PUF to create the same device [38].
- Any attempt to change the device containing the PUF will change the PUF’s behavior and destroy the PUF [39].
- In real-world manufacturing circuits, the difference between mapping input and output functions is fixed and unpredictable. In this respect, the hardware is equivalent to a one-way function [40].
3.4. Fuzzy Extraction
3.5. Honey List
4. Cryptanalysis of Authentication Protocols
4.1. Cryptanalysis of Chunka et al.’s Protocol
4.1.1. Known Session-Specific Temporary Information Attacks
4.1.2. Off-Line Guessing Attacks
4.1.3. Impersonation Attacks
4.2. Cryptanalysis of Amintoosi et al.’s Protocol
4.2.1. Off-line Guessing Attacks
4.2.2. Impersonation Attacks
4.3. Cryptanalysis of Hajian et al.’s Protocol
4.3.1. Device Impersonation Attacks
4.3.2. Session Key Disclosure Attacks
5. The Proposed PUFTAP-IoT
5.1. Registration Phase
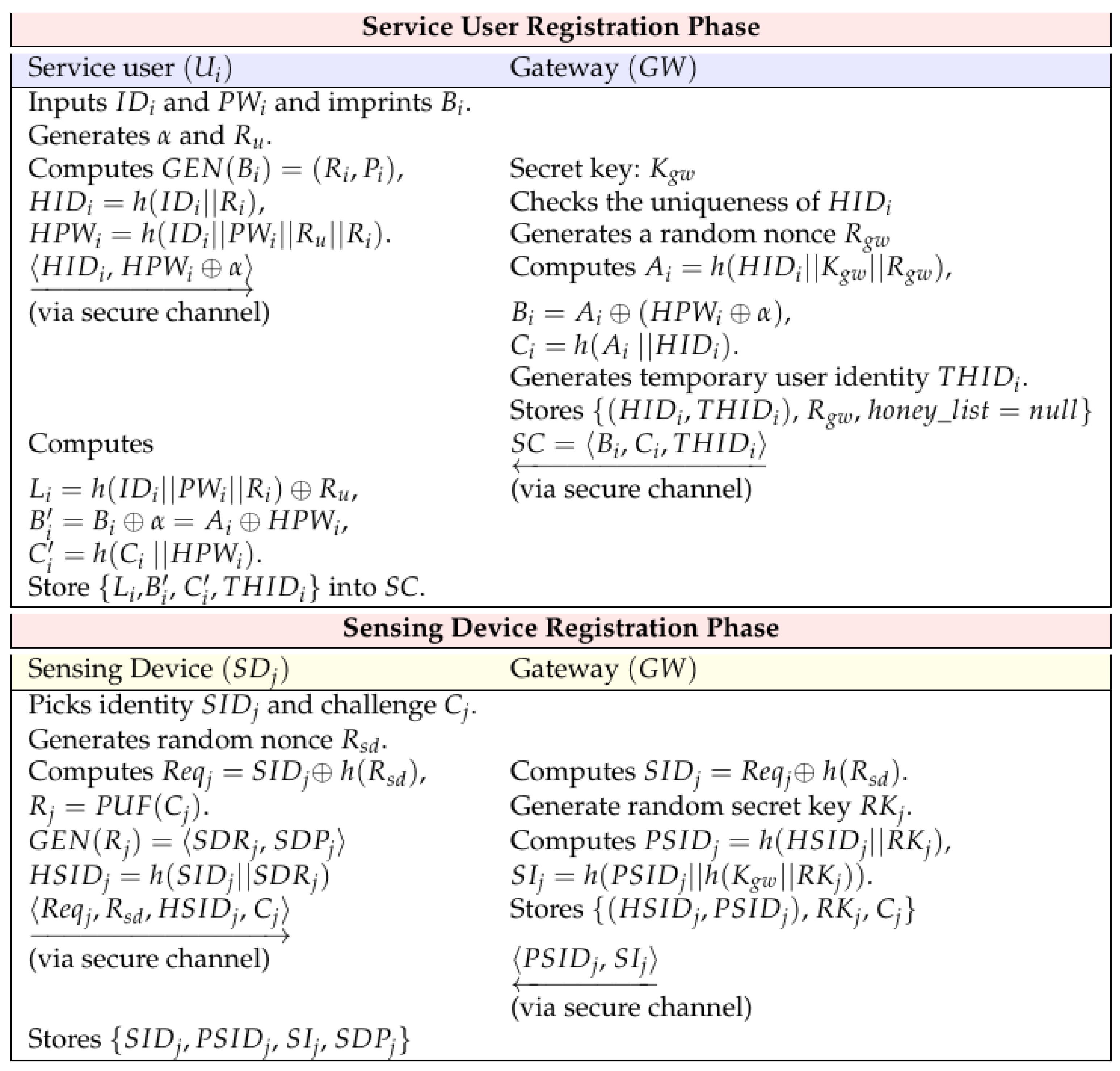
5.1.1. Service User Registration Phase
5.1.2. Sensing Device Registration Phase
5.2. Login and Authentication Phase
5.3. Service User Password and Biometrics Update Phase
6. Security Analysis
6.1. Informal Security Analysis
6.1.1. Offline and Online-Guessing Attacks
6.1.2. Service User Anonymity
6.1.3. Impersonation Attack
6.1.4. Sensing Device Physical Capture Attack
6.1.5. Replay and Man-in-the-Middle Attack
6.1.6. Stolen Verifier Attack
6.1.7. Perfect Forward Secrecy
6.1.8. Session-Specific Random Number Leakage Attack
6.1.9. Session Key Disclosure Attack
6.1.10. Mutual Authentication
6.2. BAN Logic
- 1.
- Jurisdiction rule:
- 2.
- Message meaning rule:
- 3.
- Nonce verification rule:
- 4.
- Belief rule:
- 5.
- Freshness rule:
6.2.1. Goals
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- Goal 5:
- Goal 6:
- Goal 7:
- Goal 8:
6.2.2. Idealized Forms
- :
- :
- :
- :
6.2.3. Assumptions
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
6.2.4. Proof
- Step 1:
- can be obtained from .
- Step 2:
- can be obtained by applying the with .
- Step 3:
- can be gained from the with and .
- Step 4:
- can be acquired by applying the with and .
- Step 5:
- can be obtained from .
- Step 6:
- can be gained from with and .
- Step 7:
- can be obtained by applying with and .
- Step 8:
- can be obtained from with and .
- Step 9:
- can be obtained from .
- Step 10:
- can be gained from with and .
- Step 11:
- can be obtained by applying with and .
- Step 12:
- can be obtained from with and .
- Step 13:
- can be obtained from .
- Step 14:
- can be obtained from with and .
- Step 15:
- can be obtained from with and , since .
- Step 16:
- can be obtained from with and .
- Step 17:
- and can be obtained from and since .
- Step 18:
- and can be obtained by applying from , , , and .
- Step 19:
- and can be obtained from and since .
- Step 20:
- and can be obtained by applying from , , , and .
6.3. ROR
- : conducts query to obtain messages sent over insecure channels between , , and .
- : indicates that can obtain information stored in the smart card of .
- : is that returns the session key between , , and . is safe if reveals using the query.
- : query allows to transmit the M message to and receive a response.
- : A fair coin is tossed before the game starts, and the result is known only to . uses this result to determine query. If conducts this query and is fresh, will return for = 1 or a random nonce for = 0. Otherwise, returns a null (⊥).
Security Proof
- : can execute a real attack on PUFTAP-IoT through this game. selects at the beginning of . Then, according to this game, we obtain:
- : conducts the query through this game and eavesdrops transmitted messages , , , and . then checks whether the derived is real to execute and queries. In PUFTAP-IoT, the session key consists of . To derive , must know the ID and random numbers of , , and . As a result, never increases the probability of winning . Thus, and can be considered indistinguishable, and we obtain:
- : To obtain , conducts and queries. can modify exchanged messages to carry out active attacks. However, all exchanged messages are protected using the one-way hash function and consist of secret credentials and random numbers. Moreover, it is difficult for to derive secret credentials and a random nonce because it is a computationally infeasible problem depending on the properties of . So, using the birthday paradox, we obtain:
- : It is similar to . conducts and queries. As described in Section 3.3, has security properties. So, we can obtain the following result:
- : In , can try to obtain with the query. By the query, can extract sensitive values stored on the smart card of . , , and are expressed as , , and . Since has no knowledge of identity and password , must guess these parameters from the extracted values. However, it is computationally infeasible for to guess ID, password, and simultaneously. Thus, and are indistinguishable. By utilizing Zipf’s law, we can obtain:Now that all the games were run, has to guess the bit to win the game. Thus, we can obtain following results:From Equations (1) and (2), we obtain the result as follows:With Equations (5) and (6), we derive the below equation:Using the trigonometric inequality, we can obtain the results of Equations (4), (5), and (7).Finally, multiply both sides of Equation (8) by 2 to obtain the desired result.
6.4. Scyther Tool Simulation
- Scyther tool checks security attack classes and possible protocol behaviors of the proposed protocol based on a pattern refinement algorithm.
- Scyther tool traces the most efficient and optimal security attacks through the “Find best attacks” setting.
- Scyther tool analyzes the security of the proposed protocol using claim events, including “Secret”, “Alive”, “Weakagree”, “Niagree”, and “Nisynch”.
- To support multiple executions of protocols in the scyther tool, the “Maximum number of run” and “Maximum number of patterns per claim” parameters are set to 5 and 10, respectively.
6.4.1. Scyther Framework
6.4.2. SPDL Specification
6.4.3. Simulation Result
7. Efficiency Analysis
7.1. Security and Functionality Features Comparison
7.2. Computation Cost Comparison
7.3. Communication Cost Comparison
7.4. Results of Comparison
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhang, Y.; Zhao, H.; Xiang, Y.; Huang, X.; Chen, X. A key agreement scheme for smart homes using the secret mismatch problem. IEEE Internet Things J. 2019, 6, 10251–10260. [Google Scholar] [CrossRef]
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 2016, 60, 192–219. [Google Scholar] [CrossRef]
- Pierce, F.J.; Elliott, T.V. Regional and on-farm wireless sensor networks for agricultural systems in Eastern Washington. Comput. Electron. Agric. 2008, 61, 32–43. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.P.C.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based Internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Kwon, D.; Yu, S.; Lee, J.; Son, S.; Park, Y. WSN-SLAP: Secure and lightweight mutual authentication protocol for wireless sensor networks. Sensors 2021, 21, 936. [Google Scholar] [CrossRef]
- Fu, X.; Wang, Y.; Yang, Y.; Postolache, O. Analysis on cascading reliability of edge-assisted Internet of Things. Reliab. Eng. Syst. Saf. 2022, 223, 108463. [Google Scholar] [CrossRef]
- Fu, X.; Pace, P.; Aloi, G.; Li, W.; Fortino, G. Cascade Failures Analysis of Internet of Things under Global/Local Routing Mode. IEEE Sensors J. 2021, 22, 1705–1719. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sensor Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Kumar, P.; Lee, H.J. Cryptanalysis on two user authentication protocols using smart card for wireless sensor networks. In Proceedings of the Wireless Advanced, London, UK, 20–22 June 2011; pp. 241–245. [Google Scholar]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G.P. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 81, 72–85. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Zou, S.; Cao, Q.; Wang, C.; Huang, Z.; Xu, G. A Robust Two-Factor User Authentication Scheme-Based ECC for Smart Home in IoT. IEEE Syst. J. 2021, 16, 4938–4949. [Google Scholar] [CrossRef]
- Chunka, C.; Banerjee, S.; Goswami, R.S. An efficient user authentication and session key agreement in wireless sensor network using smart card. Wirel. Pers. Commun. 2021, 117, 1361–1385. [Google Scholar] [CrossRef]
- Kalra, S.; Sood, S.K. Advanced password based authentication scheme for wireless sensor networks. J. Inf. Secur. Appl. 2015, 20, 37–46. [Google Scholar] [CrossRef]
- Amintoosi, H.; Nikooghadam, M.; Shojafar, M.; Kumari, S.; Alazab, M. Slight: A lightweight authentication scheme for smart healthcare services. Comput. Elec. Eng. 2022, 99, 107803. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chen, J.; Lee, C.-C.; Chilamkurti, N.; Yeo, S.-S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Syst. 2015, 21, 49–60. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. An improved and anonymous twofactor authentication protocol for health-care applications with wireless medical sensor networks. Multimedia Syst. 2017, 23, 195–205. [Google Scholar] [CrossRef]
- Wang, C.; Xu, G.; Li, W. A secure and anonymous two-factor authentication protocol in multiserver environment. Secur. Commun. Netw. 2018, 2018, 1–15. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Arshad, H.; Nikooghadam, M.; Abbasinezhad-Mood, D. Three party secure data transmission in IoT networks through design of a lightweight authenticated key agreement scheme. Future Gener. Comput. Syst. 2019, 100, 882–892. [Google Scholar] [CrossRef]
- Mo, J.; Chen, H. A lightweight secure user authentication and key agreement protocol for wireless sensor networks. Secur. Commun. Netw. 2019, 2019, 1–17. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. SLUA-WSN: Secure and lightweight three-factor-based user authentication protocol for wireless sensor networks. Sensors 2020, 20, 4143. [Google Scholar] [CrossRef]
- Hajian, R.; Erfani, S.H.; Kumari, S. A lightweight authentication and key agreement protocol for heterogeneous IoT with special attention to sensing devices and gateway. J. Supercomput. 2022, 1–43. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Shojafar, M.; Peris-Lopez, P. LACO: Lightweight three-factor authentication, access control and ownership transfer scheme for e-health systems in IoT. Future Gener. Comput. Syst. 2019, 96, 410–424. [Google Scholar]
- Maes, R. Physically unclonable functions: Properties. In Physically Unclonable Functions; Springer: Berlin/Heidelberg, Germany, 2013; pp. 49–80. [Google Scholar]
- Juels, A.; Ristenpart, T. Honey encryption: Encryption beyond the brute-force barrier. IEEE Secur. Privacy 2014, 12, 59–62. [Google Scholar] [CrossRef]
- Juels, A.; Ristenpart, T. Honey encryption: Security beyond the brute-force bound. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, 11–15 May 2014; pp. 293–310. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar]
- Abdalla, M.; Fouque, P.-A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Lecture Notes in Computer Science, Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography (PKC’05), Les Diablerets, Switzerland, 23–26 January 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Scyther Tool—Cas Cremers. Available online: https://people.cispa.io/cas.cremers/scyther/ (accessed on 23 July 2022).
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology; Springer Science+Business Media: Berlin, Germany; New York, NY, USA, 1999; pp. 388–397. [Google Scholar]
- Aman, M.N.; Chua, K.C.; Sikdar, B. Mutual authentication in IoT systems using physical unclonable functions. IEEE Internet Things J. 2017, 4, 1327–1340. [Google Scholar] [CrossRef]
- Frikken, K.B.; Blantonm, M.; Atallahm, M.J. Robust authentication using physically unclonable functions. In Proceedings of the International Conference on Information Security, Pisa, Italy, 7–9 September 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 262–277. [Google Scholar]
- Chatterjee, U.; Chakraborty, R.S.; Mukhopadhyay, D. A PUF-based secure communication protocol for IoT. ACM Trans. Embedded Comput. Syst. 2017, 16, 1–25. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Lecture Notes in Computer Science, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Juels, A.; Rivest, R.L. Honeywords: Making password cracking detectable. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 145–160. [Google Scholar]
- Lee, J.; Yu, S.; Park, K.; Park, Y.; Park, Y. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Oh, J.; Yu, S.; Lee, J.; Son, S.; Kim, M.; Park, Y. A secure and lightweight authentication protocol for IoT-based smart homes. Sensors 2021, 21, 1488. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. A Robust Authentication Protocol for Wireless Medical Sensor Networks Using Blockchain and Physically Unclonable Functions. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Kim, M.; Lee, J.; Oh, J.; Park, K.; Park, Y.; Park, K. Blockchain based energy trading scheme for vehicle-to-vehicle using decentralized identifiers. Appl. Energy 2022, 322, 119445. [Google Scholar] [CrossRef]
- Lee, J.; Kim, G.; Das, A.K.; Park, Y. Secure and efficient honey list-based authentication protocol for vehicular ad hoc networks. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2412–2425. [Google Scholar] [CrossRef]
- Cremers, C.J. The scyther tool: Verification, falsification, and analysis of security protocols. In Proceedings of the International Conference on Computer Aided Verification, Princeton, NJ, USA, 7–14 July 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 414–418. [Google Scholar]
- Kilinc, H.H.; Yanik, T. A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 2013, 16, 1005–1023. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J. 2019, 6, 580–589. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.; Park, Y. Physically secure lightweight anonymous user authentication protocol for internet of things using physically unclonable functions. IEEE Access 2019, 7, 85627–85644. [Google Scholar] [CrossRef]





| Notations | Meanings |
|---|---|
| i-th user | |
| j-th sensing device | |
| Gateway node | |
| SC | Smartcard |
| Identity of | |
| Identity of | |
| Password of | |
| The hidden password of i-th user | |
| Biometrics of | |
| The Physical Unclonable Function | |
| The challenge/response pair | |
| Generation and reproduction algorithm of fuzzy extractor | |
| Secret key of | |
| , | Random nonces |
| Timestamps | |
| Pseudo-identity of and | |
| Temporary user identity | |
| Session key | |
| Data concatenation operator | |
| ⊕ | Bitwise exclusive-or operator |
| Collision-resistant one-way hash function |
| Notations | Description |
|---|---|
| The session key in PUFTAP-IoT | |
| The statement S is fresh | |
| believes the statement | |
| sees the statement | |
| once said | |
| is combined with formula F | |
| Encrypt with | |
| controls | |
| and shard and use for communication |
| Security Properties | PUFTAP-IoT | Chunka et al. [16] | Amintoosi et al. [18] | Hajian et al. [27] |
|---|---|---|---|---|
| Replay attack | o | o | o | o |
| Man-in-the-middle attack | o | o | o | o |
| Guessing attack | o | x | x | o |
| Impersonation attack | o | x | x | x |
| KSSTI attack | o | x | o | x |
| Smart card stolen attack | o | x | x | o |
| Device capture attack | o | o | o | x |
| Anonymity | o | x | x | o |
| Perfect forward secrecy | o | o | o | o |
| Using three factors | o | x | x | o |
| Using PUF | o | x | x | x |
| Using | o | x | x | x |
| Secure mutual | o | x | x | x |
| authentication |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.; Oh, J.; Kwon, D.; Kim, M.; Yu, S.; Jho, N.-S.; Park, Y. PUFTAP-IoT: PUF-Based Three-Factor Authentication Protocol in IoT Environment Focused on Sensing Devices. Sensors 2022, 22, 7075. https://doi.org/10.3390/s22187075
Lee J, Oh J, Kwon D, Kim M, Yu S, Jho N-S, Park Y. PUFTAP-IoT: PUF-Based Three-Factor Authentication Protocol in IoT Environment Focused on Sensing Devices. Sensors. 2022; 22(18):7075. https://doi.org/10.3390/s22187075
Chicago/Turabian StyleLee, JoonYoung, JiHyeon Oh, DeokKyu Kwon, MyeongHyun Kim, SungJin Yu, Nam-Su Jho, and Youngho Park. 2022. "PUFTAP-IoT: PUF-Based Three-Factor Authentication Protocol in IoT Environment Focused on Sensing Devices" Sensors 22, no. 18: 7075. https://doi.org/10.3390/s22187075
APA StyleLee, J., Oh, J., Kwon, D., Kim, M., Yu, S., Jho, N.-S., & Park, Y. (2022). PUFTAP-IoT: PUF-Based Three-Factor Authentication Protocol in IoT Environment Focused on Sensing Devices. Sensors, 22(18), 7075. https://doi.org/10.3390/s22187075






