Abstract
The underwater wireless sensor networks (UWSNs) have been applied in lots of fields such as environment monitoring, military surveillance, data collection, etc. Deployment of sensor nodes in 3D UWSNs is a crucial issue, however, it is a challenging problem due to the complex underwater environment. This paper proposes a growth ring style uneven node depth-adjustment self-deployment optimization algorithm (GRSUNDSOA) to improve the coverage and reliability of UWSNs, meanwhile, and to solve the problem of energy holes. In detail, a growth ring style-based scheme is proposed for constructing the connective tree structure of sensor nodes and a global optimal depth-adjustment algorithm with the goal of comprehensive optimization of both maximizing coverage utilization and energy balance is proposed. Initially, the nodes are scattered to the water surface to form a connected network on this 2D plane. Then, starting from sink node, a growth ring style increment strategy is presented to organize the common nodes as tree structures and each root of subtree is determined. Meanwhile, with the goal of global maximizing coverage utilization and energy balance, all nodes depths are computed iteratively. Finally, all the nodes dive to the computed position once and a 3D underwater connected network with non-uniform distribution and balanced energy is constructed. A series of simulation experiments are performed. The simulation results show that the coverage and reliability of UWSN are improved greatly under the condition of full connectivity and energy balance, and the issue of energy hole can be avoided effectively. Therefore, GRSUNDSOA can prolong the lifetime of UWSN significantly.
1. Introduction
Acoustic communication is the main mode for UWSNs [1,2,3]. In recent years, acoustic-based UWSNs have been applied in lots of fields such as environment monitoring, military surveillance, data collection, etc [4,5,6]. Research on UWSNs mainly involves node deployment [7,8,9,10], node localization [11], network protocol design [3,12], simulation [13,14,15], etc. Deployment of sensor nodes in 3D UWSNs is a crucial issue, which directly affects the performance of networks. However, there is still a large gap between the current research and practical application for this problem [16]. According to the mobility characteristics of sensor nodes, the current deployment schemes can be classified into three categories in general: static deployment, self-deployment and movement-assisted deployment [8]. Static deployment is one of the main deployment approaches, in which sensors are fixed one-by-one manually to their precomputed positions [17]. Although this deployment method reduces the complexity in some special scenarios, its process is very time consuming and costly, especially for a large volume monitored area. Moreover, static deployment is infeasible for some inaccessible regions during military surveillance and pollution detection applications. Movement-assisted deployment is another main mode of deployment for UWSNs. The sensors are embedded in mobile platforms such as autonomous underwater vehicles (AUVs). Driven by these devices, the sensors can move to their final locations after they are dropped randomly onto the water surface [18,19,20]. Assisted by these mobile devices, sensors can move freely to any location in the underwater region [21,22] to improve network coverage and connectivity. However, this deployment method is not practical because these types of sensors are always large and costly. Therefore, finding the low-cost and high-coverage rapid deployment approach for UWSNs has attracted attention from lots of scholars and engineers in recent years.
In order to tackle the problem mentioned above, one of the feasible solutions is the self-deployment method, that is, autonomous depth-adjustment deployment for sensors which have the restricted vertical moving capability [23]. For this scheme, the sensor nodes are dropped randomly onto the water surface initially, so that the coverage is highly uncertain. Then, the sensors dive to their final positions adjusting their depths by themselves. Compared with the AUV-assisted node deployment mentioned above, this depth-adjustment node self-deployment is practical because it relatively simple, readily available, and economic in engineering application. However, due to the complex underwater environment, it is challenging to achieve the optimal depth-adjustment deployment with the goal of maximized coverage, minimized energy consumption and guaranteed connectivity to sink nodes.
Thus, a growth ring style uneven node depth-adjustment self-deployment optimization algorithm (GRSUNDSOA) for UWSNs is proposed in this paper. Initially, the sensors are scattered to the water surface to form a connected network on this 2D plane. Then, starting from the sink node, a growth ring (GR) style increment strategy is utilized to organize the common nodes as tree structures and the depths for all nodes are computed based on the global maximizing coverage utilization and energy balance iteratively. Finally, all the nodes dive to the new positions once according to the computed depths and a 3D connected UWSN with uneven distribution nodes and balanced energy is constructed. Our contributions in this paper are described as follows:
- (1)
- A growth ring style-based scheme is proposed for constructing a connective tree structure. In this scheme, an incremental broadcast radius calculation is utilized to determine the GRs and construct the connective tree structure. It means that the radial distance between the GRs increases with its distance to sink node increasing. The nodes of UWSNs constructed by this deployment method are non-uniformly distributed ring by ring. That is, the network deployed by this strategy has the following characteristics: The number of nodes near sink node is large and the nodes distribution is dense, on the contrary, the number of nodes far from sink node is small and the nodes distribution is sparse. This conforms to the hot spot characteristics near the sink node. Thus, it has better network reliability, and its energy consumption is more balanced. It can avoid the energy hole [24,25] effectively.
- (2)
- A novel depth-adjustment self-deployment algorithm based on growth ring style is proposed. This algorithm strives to obtain the optimal network coverage rate on the basis of ensuring energy consumption balance and connectivity. Different from the recent approaches in the literature such as CDA [26,27], Cacc [28], VODA [29], and DODA [30], the proposed algorithm searches the global optimal dive position based on the basic nodes for depth calculation rather than the local optimal dive position. Furthermore, the proposed depth calculation method is with the goal of comprehensive optimization of both maximizing coverage utilization and energy balance, rather than just coverage only. Therefore, the coverage rate and energy balance of UWSN deployed by GRSUNDSOA is improved greatly.
The rest of the paper is organized as follows: Related works are addressed in Section 2. Section 3 describes our problem definition, model and proposal. The proposed algorithm is presented in Section 4 in detail. Simulation and analysis are provided in Section 5. Finally, conclusions are given in Section 6.
2. Related Research
As mentioned above, in recent years, research on UWSNs mainly involves topics like node deployment [7,8,9,10], node localization [11], network protocol design [3,12], simulation [13,14,15], etc. Specially, the issue of node deployment has attracted attention from lots of scholars and engineers.
For static node deployment scheme, Alam [31] studied a series of node placement strategies with the minimum number of nodes to obtain 100% sensing coverage. In this scheme, a matric called volumetric quotient was defined. The higher the volumetric quotient is, the smaller the number of nodes requires for full 3D coverage. The simulation results show that the truncated octahedral cell has the best coverage. This method is a deterministic rule deployment, which requires precise location of sensors. However, node localization [11] is a tedious process calculated by GPS, which is very time consuming and costly.
Senouci et al. [18] presented a survey and classification about the movement-assisted sensor deployment algorithms. Six classes of approaches are identified based on relocation schemes. Each of these approaches adopts a specific principle to relocate the nodes from their initial position to a new target position. These mobile sensors driven by mobile device, such as AUV, are always costly. Therefore, it is unrealistic to use many mobile nodes for network deployment. In practice, the mobile sensors are always applied to patch the coverage holes. Wang et al. [19] proposed a mobile assisted hole patching scheme for hybrid WSNs based on particle swarm optimization (PSO). Some mobile nodes are utilized to repair coverage holes, and PSO algorithm is used to calculate moving position of mobile nodes. Kadu [20] proposed a movement-assisted coverage improvement approach for hole healing called Modified Hole Detection and Healing (MHDH) to recover the coverage holes.
Recently, move-restricted node self-deployment has been studied by many scholars. Detweiler et al. [23] developed a depth adjustment platform called AQUANODE. The system nodes are deployed on the water surface and connected to the water AQUANODE sensor node. A series of experiments are performed in 50 m water depth to validate this system effectiveness. Two special applications are also discussed to introduce the utilization of this system. In its experiments, the communication between sensor nodes must be through the buoys on the water surface, not the underwater acoustic communication method.
Senel et al. [26,27] proposed a self-deployment scheme named as Depth Computation Approach (CDA). In this approach, the connected paths of network are constructed using a node set called connected dominating set (CDS) to adjust the node depths. The CDS is determined based on a connected backbone constructing. The depths of dominator and non-dominator nodes are then optimized iteratively. This algorithm has relatively good performance on coverage and connectivity. However, this algorithm has poor energy consumption balance performance especially in the situation of sparse node distribution. Moreover, in the process of determining the depth of nodes, CDA can only find the local optimal solution instead of the global optimal solution due to its limitation when considering coverage redundancy; hence the coverage rate of UWSNs can be improved furtherly.
Senel [28] also proposed a self-deployment scheme named coverage-aware connectivity-constrained (Cacc) unattended sensor deployment. In this algorithm, the ground control station initially forms a 2D connected tree structure for all nodes. Then, the ground control station calculates the depth of each node one by one to reduce the coverage overlap between adjacent nodes while maintaining the network connectivity. Similarly, this depth-adjustment algorithm always calculates a local optimum for the diving depth, not the global optimum.
Su et al. [29] proposed a Voronoi-based Optimized Depth Adjustment (VODA) deployment scheme to deploy sensor nodes in a target water space. This algorithm has the goal of coverage and connectivity joint optimization. Some leader nodes are chosen to remain on the water surface based on a Voronoi diagram; on the contrary, the other nodes calculate their depths aiming to optimize coverage overlap between the nodes. This algorithm can achieve good coverage and connectivity performance. However, it needs to collect accurate position coordinates of sensor nodes when establishing the Voronoi diagram. The node localization process is always tedious and costly as mentioned above. Moreover, it does not consider the issue of energy balance and energy holes. Jin et al. [30] proposed a deployment optimization algorithm using depth adjustable nodes in underwater acoustic networks (DODA). This algorithm considers node drift situations when optimizing the node position. With the goal of maximizing network coverage, and combining the location information of neighboring nodes, this paper uses a greedy algorithm to solve the problem of node deployment optimization under the premise of keeping network connectivity. Similarly, this algorithm does not consider the issue of energy balance.
Jiang [32] presented a node self-deployment algorithm based on an uneven cluster with radius adjusting. Firstly, the nodes randomly scattered on the water surface are non-uniformly clustered according to the distance from the sink node. Each cluster head node then constructs a connected path to sink node. Finally, the depths of each node are adjusted with the goal of minimizing the coverage redundancy. This method takes the issues such as network reliability and energy consumption balance into account, however, its depth adjustment strategy cannot reach the global optimum.
Wang [33] presented a depth-adjustment scheme based on Voronoi diagrams. All move-restricted sensor nodes are firstly placed randomly on water surface. Then the special nodes with adjustable depth are found out based on Voronoi diagrams and moved vertically to the determined depth. Therefore, the deployment process is simplified due to the divided different layers with this scheme. However, the construction process of Voronoi diagrams is complicated and costly. Pompili et al. [34] proposed different deployment strategies for 2D and 3D communication architectures for UWSN. Jiang [35] proposed a depth adjustment deployment algorithm based on a 2D convex hull and spanning tree for achieving full network connectivity. Akkaya et al. [36] presented a distributed self-deployment approach in UWSNs to find its maximum coverage rate. On the contrary, in [33] the move-restricted nodes are placed on the water bottom firstly. The graph coloring-based strategy is utilized when the nodes depths are determined. This algorithm can achieve relatively good coverage and connectivity performance with appropriate parameter values. Nevertheless, its energy consumption for node deployment is too large.
Du [37] presented the approach based on virtual force for depth-adjustment of sensor nodes. This algorithm simplifies virtual force as the repulsion force only between neighbor nodes and utilizes the virtual force to adjust the node to the position where the resultant force is zero. It only considers the coverage rate of network but ignores the connectivity rate for network performance.
3. Preliminaries for GRSUNDSOA
As mentioned in Section 2, most of the recent depth-adjust self-deployment algorithms only regard coverage or connectivity as the main performance indicators for network deployment. The network formed by these methods is a generally uniformly distributed 3D topology of nodes. In UWSN, the data collected by sensor nodes are transmitted to sinks via one or multi-hops from bottom to top. Hence, the nodes near the sink have a heavier data transmission load and more energy consumption than that of the other nodes. Thus, the energy non-replenishment of underwater nodes [38,39] leads to faster energy exhaustion and faster failure for nodes near sink than that of the other nodes. As a result, the data uploaded from remote nodes which have longer lifetime cannot be transferred to sinks. This will lead to an early end of the whole network life although lots of remote nodes are still in working mode. Therefore, in order to improve the quality of service (QoS) of UWSN, solving this energy hole problem caused by the imbalance of node energy consumption is also an important indicator for nodes deployment.
Based on the above analysis, a scheme of uneven distribution node deployment, which has higher density nodes near sink and lower density nodes far from sink, is helpful to avoid the issue of energy consumption imbalance. For this scheme, there are more nodes near sink to complete data transmission and share the communication energy consumption, so that the communication energy consumption for each node in this area will be relatively reduced. Thus, the communication energy consumption of each node in the entire UWSN tends to be balanced. According to the above analysis, in this paper, a growth ring style uneven node depth-adjustment self-deployment optimization algorithm for UWSNs is proposed.
3.1. Network Scenario
It is assumed that the nodes are scattered to the water surface and initially form a connected network on this 2D plane. These nodes have perception capabilities and restricted mobility, i.e., moving only in vertical direction by adjusting their depth via a mechanism described in [28]. This depth adjustment system is a mechanism which is composed of a motor, gearhead, timing belt and a magnetic coupler [28]. The timing belt is attached to an underwater sensor node and the magnetic coupler turns a spool of anchor line. The considered network scenario in this paper is shown in Figure 1.
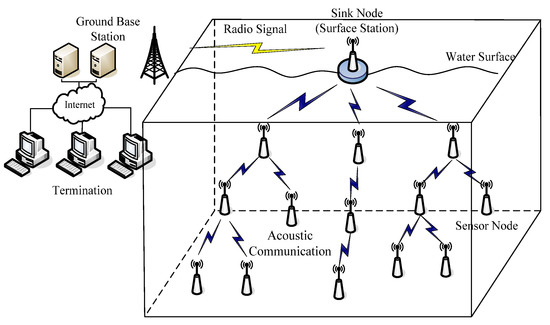
Figure 1.
Considered 3D network scenario.
Each sensor node on the water surface is moved vertically to form this 3D network and probes its vicinity in the sensing range. These nodes send their collecting data to the sink node, which is fixed on the surface station, via a one or multi-hop path through acoustic communication channels. On the contrary, the sink node maintains connectivity with the ground base station through radio.
Some assumptions are considered:
- (1)
- In the initial phase, sensors are dropped randomly to water surface of the monitoring area, the volume of which is denoted as Length × Width × Height (m3), so that a densely populated 2D connected network is formed. The number of sensors is denoted as N. All nodes are in sleep mode. For each node, its coordinate position on water surface can be calculated using location algorithm.
- (2)
- The energy of sink node is considered that can be replenished. And in this system, it is always located in the center of the monitoring area. There is only one sink node in this scenario.
- (3)
- Each node has a unique ID. Its communication radius is denoted as Rb which can be adjusted but must meet the condition Rb ≤ Rcmax, where Rcmax is denoted as the maximum communication radius. The sensing radius of each sensor is denoted as Rs.
3.2. Coverage Model
Let each sensor node in this system be denoted as Nsi, I = 1, 2, …, N, and its position coordinate in monitoring area is X(Nsi) = (xi,yi,zi ). Let U(x,y,z) be a pixel in monitoring area. The probability that U(x,y,z) is covered by node Nsi is denoted as Pcov(x,y,z,Nsi ), which can be calculated with Equation (1) according to the Boolean perception model:
where, U represents a pixel in monitoring area, dist(U,Nsi) represents the Euclidean distance between U and Nsi.
That is, in this coverage model, the perception space of node Nsi is a sphere whose center is X(Nsi) = (xi,yi,zi) and radius is Rs as Figure 2 shows. The pixel that is in the perception sphere like U1 is covered by Nsi; on the contrary, the pixel that is out the perception sphere like U2 cannot be covered by Nsi.
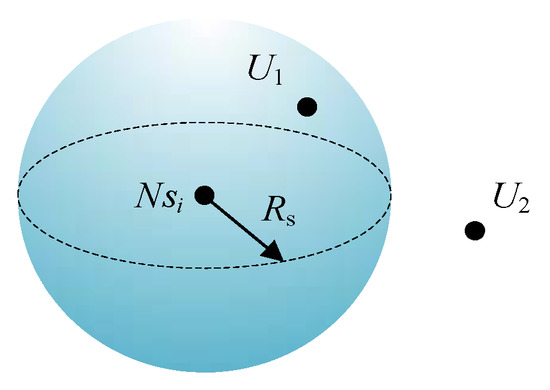
Figure 2.
Coverage model.
Let Ns = {Ns1,Ns2,Ns3,…NsN} represents the nodes set of monitoring area. In this 3D network model as Figure 1, each sensor coverage is considered independent, and thus Equation (2) is utilized as follow to acquire the probability that U is covered by Ns.
3.3. Coverage Rate Calculation
For the Boolean perception model as Equation (1), if at least one node of Ns can perceive the pixel U, it can be considered that U is covered by sensor nodes set Ns. The coverage rate is defined as Equation (3), which is the ratio of the volume of the effective monitoring area formed by all sensor nodes to the volume of the entire monitoring area M.
where, η is the coverage rate, Volume (.) is the volume of area, and Qi is the monitoring area of sensor node Nsi. Due to the irregular shape of the effective monitoring area, it is a NP-hard problem to accurately calculate the volume of the effective monitoring area using Equation (3). In practice, the mesh-grid based approach is a feasible method to estimate the covered volume. Dividing the monitoring area M into l × w × h grids, the intersections or center point of these grids can be denoted as U(x,y,z). The method mentioned above can be used to determine whether U is covered by Ns. Then, all covered grids are identified and their volumes are summed up, which is regarded as the approximation of the effective covered area. High-resolution mesh grid is helpful for improving the calculation accuracy of the covered volume; however, it will cause too long calculation time. In order to improve computing efficiency, the random sampling method such as Monte Carlo method can be adopted in practice.
3.4. Connectivity Definition
In this system, the connectivity rate is defined as follows:
where Nconnect represents the number of sensors connecting to sink node.
3.5. Coverage Utilization
Let the probability that the node Nsi is covered by the neighboring node Nsj overlap be as Equation (5):
where, V(Nsi, Nsj) is the volume of the overlapping area covered by two nodes. Then, the probability that Nsi is not covered by neighbor node Nsj is expressed as Equation (6):
The coverage utilization of Nsi is defined as the probability that it is not covered by all m neighbor nodes:
It reflects the ratio of the area volume of the node Nsi that does not overlap with its neighbors to the volume of its own perception space.
3.6. Growth Ring and Forward Subtree Root Nodes
According to this proposed growth-ring based deployment strategy, in the connected tree rooted with sink node, the g-th ring of subtree root nodes (SRNs) set is called the g-th growth ring (GR).
When the nodes in Rootg collects and transmits data during the network deployment phase, the collected messages are forwarded by one or multiple hops to the previous ring of SRNs. Thus, the nodes in Rootg are called the forward subtree root nodes (FSRNs).
3.7. Basic Node Set
During the network deployment process, the node set whose dive depth has been calculated in the current GR is called the basic node set (BNS), which is denoted as basenodes. It is a reference benchmark for depth calculation of unprocessed nodes, and initially basenodes = {Sink}. With the deployment process, the current nodes whose dive depths have been calculated are added to the BNS dynamically.
3.8. Horizontal Distance, Expect Distance and Offset Distance
For any two nodes Nsi and Nsj, the horizontal distance (HD) between them is defined as the distance between Nsi and Nsj when both are placed on the same horizontal plane (that is, Nsi.Z = Nsj.Z). Let HD between Nsi and Nsj be denoted as d(Nsi,Nsj).
The expect distance (ED) between nodes Nsi and Nsj is defined as the distance to guarantee the connectivity between Nsi and Nsj during depth adjustment. Let ED between Nsi and Nsj be denoted as Edist(Nsi,Nsj). Its maximum value is Rcmax, and the minimum value is d(Nsi,Nsj). In the practical depth adjustment, its value takes any element value in the set {Rcmax, Rcmax-∆r, …., d(Nsi,Nsj)}, where ∆r is the step length.
The offset distance (OD) between nodes Nsi and Nsj is defined as the possible maximum offset distance between them in the vertical direction when guaranteeing connectivity between Nsi and Nsj. Let OD between Nsi and Nsj be denoted as DivNs(Nsi,Nsj). The relationship between these three distances is shown as Equation (8):
3.9. Network Reliability Definition
Let the numbers of nodes within Rcmax from the sink node be denoted as Nsin. Let the average number of neighbor nodes for all sensors be denoted as Navg. Nsin and Navg are calculated as Equation (9) and Equation (10), respectively:
where is the numbers of nodes within Rcmax from the sink node, and is the numbers of nodes within Rcmax from node Nsi, i.e., the degree of Nsi.
The high values of these indicators mean that some other optional transmission paths can be selected to maintain the network connectivity. Therefore, the higher these two indicators are, the greater the reliability of the network is.
3.10. Deployment Energy Consumption
The mobile energy consumption of nodes moving from the water surface to a specified location represents the main energy consumption during self-deployment. To simplify calculations, the energy consumption for network deployment is expressed as follows:
where, D is the total distance that all nodes move during the deployment process, and v is the moving speed of nodes, and p is power.
3.11. Problem Definition
The problem of this paper is defined as follows:
N sensors are dropped to water surface of monitoring area initially and a 2D connective network is formed. What is the optimal depth of each sensor so that the coverage of network reaches the maximum under the condition of energy consumption balance and guarantees connectivity to surface station?
4. Description of the Proposed Algorithm
4.1. The Whole Strategy for the Proposed Algorithm
Considering the sink node as the root node, the nodes that are scattered randomly on the water surface are organized as a tree structure. Then the depths of all nodes are computed iteratively with the goal of the maximized coverage utilization and energy balance. Finally, all the nodes dive to the new position once according to the computed depths. The whole strategy has three phases as follows:
- (1)
- The 1st GR is determined. The 1st ring of connected tree is constructed rooted with sink node and the depths of the nodes within the 1st GR are computed.
The sink node broadcasts a message to the other nodes to identify its one-hop nodes with a variable communication radius Rb. The set of all these one-hop nodes which are identified by replying to this message is regarded as the subtree nodes attached to sink node and denoted as S1. The nodes in S1 are sorted by the distance to sink node from far and near. Selecting from these sorted nodes in S1, a SRNs set is made with a certain probability based on the principle that the distance between each other is roughly uniform. This set is called the 1st GR and denoted as Root1. On the contrary, the other nodes in S1 are regarded as common child nodes of sink node. S1 is called the nodes within the 1st GR (1st NGR). So far, a connected tree is constructed rooted with sink node. Meanwhile, the optimized depths of the nodes in S1 are computed with the goal of maximizing coverage utilization and energy balance.
- (2)
- Ring by ring, each ring of connected tree is constructed rooted with the previous GR and the depths of all nodes are calculated.
Each node in Root1 broadcasts a message to the other nodes to identify its next hop nodes with the increased broadcast radius Rb which is larger than that of the previous iteration. The set of these next-hop nodes which are identified by replying to this message is regarded as the subtree nodes attached to each respective node in Root1 and all these next-hop nodes are called the nodes within the 2nd GR (2nd NGR) denoted as S2. Then, these nodes in S2 are sorted by the distance to sink from far and near so that the SRNs set of the second ring is determined using the similar method with the first phase. The SRNs set of the second ring is denoted with Root2 and called the 2nd GR. On the contrary, the other nodes in S2 are regarded as common child nodes of their corresponding subtree. Starting from each node in Root1, the optimized depths of the nodes in S2 are computed. So far, a series of connected trees are constructed rooted with the corresponding nodes in Root1. The above process is performed iteratively until all nodes are added into their corresponding subtree and the depths of all the nodes are computed.
- (3)
- Sink node distributes the depths to the nodes so that all the nodes dive to the new position once.
This strategy finally forms a growth ring like network layout. The radius of the growth ring increases with the distance to sink node increasing. The flow chart of the whole strategy is shown in Figure 3.
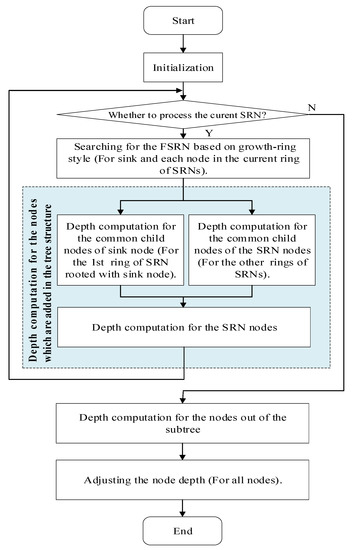
Figure 3.
The flow chart of the whole strategy.
Figure 4 shows an illustration of this deployment strategy. The sensor nodes are dropped randomly to the water surface of the monitoring area initially as shown in Figure 4a, where the red node denotes the sink node. The connected tree which is rooted with sink node in the first phase of the strategy is shown in Figure 4b, where the yellow nodes denote Root1, i.e., the 1st GR. The 2nd NGRs and the connected trees which are rooted with the corresponding the nodes in Root1 are shown in Figure 4c, where the green nodes denote Root2, i.e., the 2nd GR.
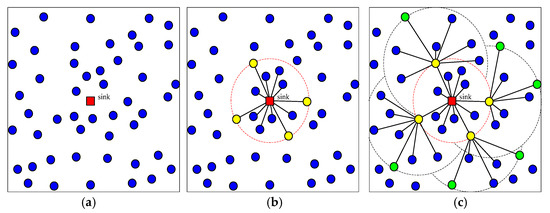
Figure 4.
The overall strategy of autonomous depth-adjustment deployment method in this paper. (a) Initialization. (b) The first growth ring. (c) The second growth ring.
According to this proposed deployment strategy, the connected trees in which the nodes are farther from the sink node have a larger communication distance, thus the node layout is sparse. On the contrary, the connected trees in which the nodes are nearer to the sink node have a smaller communication distance and the node layout is dense. Therefore, there are more nodes in hot-spots area near the sink node, so that network reliability is improved and network transmission energy consumption is balanced. Moreover, the network coverage is improved and the connectivity is guaranteed with the process of optimizing the nodes depth in the connected trees.
4.2. Initialization
N sensor nodes are dropped randomly to the water surface with sink node as the central node. Let the coordinate of the sink node in 3D space be (Length/2, Width/2, 0), and its id be 0. The relative coordinates of the other nodes are denoted as X(Nsi) = (xi, yi, 0). Each node is initialized with the following attributes:
where, id is the unique identification of each node, tree indicates that whether the node joins the tree structure, father is the id of the parent node and its initial value is set with N + 1, root is the root node of the tree to which the node is attached and its initial value is set with Inf, processed indicates whether the current node has calculated the diving depth. If leaf = 1, it means that the node is a leaf node of tree.
< id = i, tree = 0, leaf = 1, father = N + 1, root = Inf, processed = 0 >
Let the number of GR g = 0, the g-th ring of SRNs set Rootg = Φ. The distances between each node and the sink node are calculated and denoted as dist(Nsi, Sink). An ordered node set is then constructed according to these distances from largest to smallest using Equation (12):
4.3. Searching for the FSRN Based on Growth Ring Style
The algorithm for searching the FSRN based on ring style is described by Algorithm 1 as follows.
| Algorithm 1 The algorithm for searching the FSRN based on growth ring style. |
| Step 1. The sink node broadcasts a message including < id = 0, g = 0 > to the other nodes with the broadcasting radius Rb, which is calculated by Equation (13): |
| where, α, β are parameters. The broadcast radius increases with the growth ring number g increasing, which makes the radial distance between GRs increasing gradually. |
| Each node Nsi that receives the broadcast message responses to the sink node with a message including < id = i, dist(Nsi,Sink) >. Then, the sink node sets Nsi.tree = 1, Nsi.root = 0, that is, Nsi is regarded as the subtree node of the sink node. |
| Step 2. According to the order of nodes in distnodes, each node Nsi that Nsi.tree = 1and Nsi. processed = 0 is processed and the SRNs set Rootg is constructed as follows. |
| If Rootg = Φ: A random number is generated as r = rand(). If r > th, where th is a threshold, the farthest node Nsi in distnodes that Nsi.tree = 1 and Nsi. processed = 0 is immediately added into Rootg. Then let Nsi.father be set with the id of the root of the subtree to which it belongs. Let Nsi. leaf = 0, that is, the node Nsi is a non-leaf node; otherwise, the next far node in distnodes that meets the candidate conditions continues to be considered. |
| If Rootg ≠ Φ: The node Nsi is determined whether to join in the subtree according to the following method. Let Nsj be an arbitrary node in Rootg. If both Nsi and Nsj satisfy the condition of Equation (14): |
| where, α, γ are parameters and the value of α is same with that of Equation (13), Nsi will be added into the Rootg. |
| The distribution of these nodes in Rootg acquired with this method is roughly uniform. Furthermore, this method can reduce the coverage overlap between subtree nodes and it is also good for improving the node utilization ratio. |
| Step 3. The depths of each SRN and its children are calculated and a connected tree is constructed with the method mentioned in Section 4.4. Then, these children nodes send their collected message to their corresponding parents, i.e., the FSRNs. The parent nodes aggregate these messages from the children in the subtree and forward the messages to FSRNs. The above procedure is performed repeatedly until sink node receives those collected messages. |
| Step 4. Each node in Rootg is denoted as FSRNs for the next GR. g ← g + 1. Then, these FSRNs broadcast messages including < id = i, g > to the next-hop nodes synchronously with the broadcasting radius Rb, which is calculated as Equation (13). Each node Nsi that receives the broadcast message and Nsi.tree = 0 responses to the nearest FSRN node Nsj with a message including < id = i >. Then, set Nsi.tree = 1 and Nsi.root = Nsj.id. |
| Step 5. Go to step 2 and execute step2–4 repeatedly until g > δ or all nodes are added to the tree structures, where δ is the maximum of GR and it can be calculated as Equation (15): |
4.4. Depth Computation for the Nodes Which Are Added in the Tree Structure
4.4.1. Depth Computation for the Common Child Nodes of Sink Node
For each common child nodes Nsi of sink node, its depth is calculated with the goal of maximizing coverage utilization and energy balance, meanwhile, and guaranteeing connectivity to the sink node. This paper firstly uses each node in the BNS as a benchmark to calculate the local optimal dive depth. Then, with the goal of improving coverage and energy balance, find the global optimal dive depth from all local optimal dive depths:
Calculation of local optimal dive depth based on basic node
Let the current BNS be basenodes, and the common child node to be calculated depth be Nsi. For each node Nsj in basenodes, if d(Nsi,Nsj) < Rcmax, where d(Nsi,Nsj) is the HD between Nsi and Nsj, Nsj is regarded as the basic node to calculate the optimal depth of Nsi. Otherwise, the other nodes in basenodes are selected to determine the basic node under the condition of d(Nsi,Nsj) < Rcmax. Let the basic node of Nsi be selected as Nsj. Then, according to the definition of Section 3.8, the dive candidate positions that Nsi may choose are the positions of the discrete points whose depth is in [ZNs(j) − DivNs, ZNs(j) + DivNs], as Figure 5 showing, where ZNs(j) is the calculated depth of the basic node Nsj.
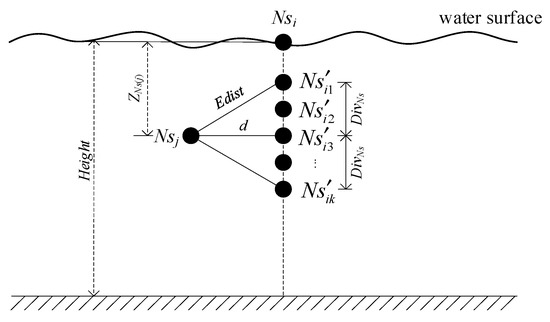
Figure 5.
The set of dive candidate positions for Nsi.
Let the dive candidate position points set of Nsi based on basic node Nsj be . If the coverage area of is above the water surface or below the water bottom, that is, or , the coverage area is invalid. Hence the depth of the candidate position of is revised as Equation (16).
where, random(a,b) represents a random number in [a,b], and Height is the depth of water bottom as Figure 5 showing. Then, the current node Nsi is virtually placed at each candidate position and its overlap area with other nodes whose depth has been calculated (processed = 1) is calculated as Equation (17):
where dist(Nsi, Nsj) is the Euclidean distance between Nsi and Nsj. The smaller the overlap area is, the higher the coverage utilization of the node is at this position. Because the distance between Nsi and Nsj is smaller than 2Rs, there must be an overlap area between them.
Considering Nsj as the basic node, the local optimal dive candidate position of Nsi is the position where the coverage utilization is the largest according to the definition in Section 3.5. It can be represented by Equation (18):
Figure 6 shows the calculation process of the optimal dive depth based on Nsj using Equation (18). When the dive candidate positions of Nsi are selected with respectively, the volumes for the overlap areas between (k = 1, 2, …, 6) and Nsj1, Nsj2, Nsj3, Nsj4, whose depths have been calculated, are shown as Figure 6a–f, where the shadow areas indicate the overlap areas. Assuming Figure 6b has the largest coverage utilization in all candidate positions of Nsi, is then the local optimal dive candidate positions for Nsi based on Nsj.
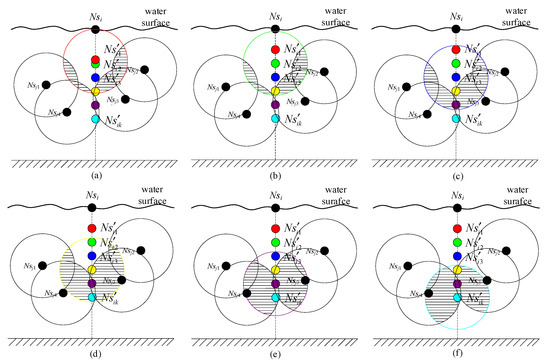
Figure 6.
The optimal depth computation for Nsi based on Nsj. (a) The overlap for . (b) The overlap for .(c) The overlap for . (d) The overlap for . (e) The overlap for . (f) The overlap for .
The Model Based on Coverage Utilization and Energy Balance
In order to improve the coverage rate while guaranteeing the energy balance in the network deployment, the model based on coverage utilization and energy balance (MBCUEB) is constructed when calculating the global optimal dive depth. This model is described as Equation (19):
where, is the coverage utilization of Nsi defined as Equation (7), dist(Nsi, Sink) is the Euclidean distance between Nsi and sink node, and distmax is the maximum distance of all nodes from the sink node. The smaller the distance between the node Nsi and the sink node is, the larger the value of will be, on the contrary, the large distance between Nsi and sink node means the small value of this ratio. Thus, this ratio reflects the characteristics of node distribution when energy is balanced. The parameters a, b are the weights, and a + b = 1. Hence, f(Nsi) reflects the comprehensive performance of Nsi on coverage utilization and energy balance.
The Global Optimization Frame for Depth-Adjustment
Based on the analysis above, the global optimization model of depth-adjustment for node Nsi can be set up as Equation (20):
This is a constrained optimization problem. The constraint C1 indicates that the global optimal position Nsi is selected from all local optimal positions based on each basic node. The constraint C2 means that Nsi must always be within the monitoring area. The constraint C3 means that the depth of candidate node should guarantee the connectivity with its basic node.
According to this optimization model, the global optimal dive depth of Nsi is solved as follows. Firstly, each node in basenodes is utilized as a basic node to calculate the local optimal dive candidate position of Nsi adopting the previous section method. Then, for each candidate position of Nsi, the MBCUEB defined as Equation (19) is adopted to calculate the corresponding f(.) value. The position with the maximum value of f(.) is the global optimal position of Nsi.
The flow chart of calculation of local optimal dive depth based on basic node and global optimal dive depth is shown in Figure 7 with Nsi as an example.
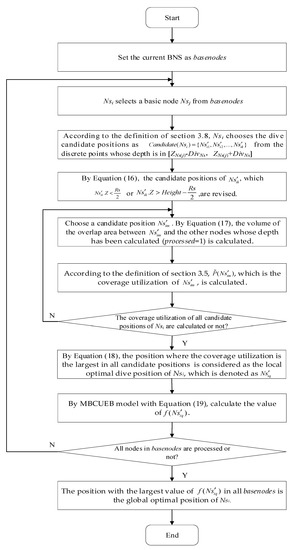
Figure 7.
Flow chart of calculation optimal dive depth with Nsi as an example.
Description of the Algorithm
The algorithm of depth computation for the common child nodes of sink node is described by Algorithm 2 as follows.
| Algorithm 2 Depth computation for the common child nodes of sink node |
| Step 1. Let basenodes be the BNS. Initially, set basenodes = {Sink}. |
| Step 2. For each common node Nsi, the method mentioned in Section “Calculation of local optimal dive depth based on basic node” above is adopted to select the basic node Nsj and calculate the local optimal dive depth based on this basic node Nsj. |
| Step 3. Taking each node in basenodes as the basic node, calculate the corresponding local optimal dive depth. Then the method mentioned in Section “The model based on coverage utilization and energy balance” and Section “The global optimization frame for depth-adjustment” above is adopted to calculate global optimal dive depth of Nsi. The current basic node corresponding to the global optimal depth is the parent node of Nsi. Set Nsi.father with the id of the basic node, Nsi.processed = 1. Add Nsi to basenodes. |
| Step 4. Go to step 2 and execute step2–3 repeatedly until the depths of all common children of sink node are calculated. |
4.4.2. Depth Computation for the SRN Nodes
For the SRN nodes of Rootg, if Nsi. processed = 0, its depth is calculated as Equation (21).
NSi.Z = Rs
4.4.3. Depth Computation for the Common Child Nodes of the SRN Nodes
The depth computation for the common child nodes of the SRN nodes is similar with the method mentioned above using Equations (16)–(20). Meanwhile, the connection paths to the sink node are guaranteed.
4.5. Depth Computation for the Nodes out of the Subtree
For some nodes that are not yet added in the connective tree structure through the above process, especially on the border of the monitoring area, the process is performed as Algorithm 3 until all nodes are added in the tree structures.
| Algorithm 3 Depth computation for the nodes out of the subtree |
| Step 1. Select a node Nsj from the nodes whose depth has been calculated under the condition that d(Nsi,Nsj) < Rcmax, where d(Nsi,Nsj) is the HD between Nsi and Nsj. Then, Nsj is considered as the neighbor node of Nsi on the horizontal plane. |
| Step 2. Nsi is added to the tree structure rooted with Nsj. If d(Nsi, Nsj) ≥ α* Rs, the depth of Nsi is set the same with that of Nsj. Otherwise, the local optimal dive depth of Nsi is calculated using Equations (16)–(18) considering Nsj as the basic node. |
| When selecting the node Nsj, its degree (i.e., the number of its children) should be inspected. If the degree of Nsj is greater than μ, where μ is a non-negative integer threshold, it means that Nsj is overloaded for network transmission. In order to balance the energy consumption, another node is selected from the nodes whose dive depth has been calculated. |
| Step 3. The above process is performed repeatedly until all nodes are added in the tree structures and their depths are calculated. |
4.6. Adjusting the Node Depth
This process is performed based on the connected tree structure. Firstly, the sink node broadcasts the depths of all nodes to the first ring of SRNs and its common child nodes. Then, the first ring of SRNs forwards these depths message to the second ring of SRNs. This process is performed in turn until all SRNs received the depths messages. After that, each ring of SRNs broadcast the depths to their common child nodes until the leaf nodes. Finally, all the nodes dive to the new position once.
4.7. Algorithm Flow
The flow chart of GRSUNDSOA is shown in Figure 8. Initially, the network is initialized which is rooted with the sink node using the method mentioned in Section 4.2. Then, a connected subtree is constructed regarding the sink node as the root node and every ring of SRNs (i.e., GR) constructs the connected subtrees rooted with itself using the method in Section 4.3. The global optimal depths of the common child nodes of sink node and SRNs are calculated using the method in Section 4.4.1 and Section 4.4.3. The depths of SRNs are calculated using the method in Section 4.4.2. This procedure is performed repeatedly until g > δ or all nodes are added to the tree structures and their depths are calculated. Next, the remaining nodes that have not been added to the tree structure are processed and their depths are calculated using the method mentioned in Section 4.5. Finally, all nodes are adjusted to the positions of the calculated dive depth using the method of Section 4.6.
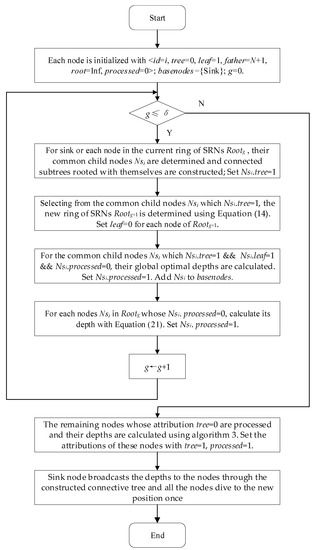
Figure 8.
Flow chart of GRSUNDSOA.
In practice, the mobility of node in the underwater environment can result in the change of horizontal position due to waves and water current. These factors can decrease the network performance. This problem is addressed with the method described in [29] in this paper.
5. Algorithm Simulation and Analysis
5.1. Theory Analysis
5.1.1. Feasibility Analysis
In the environment of 3D underwater, the superposition of all nodes covering perception sphere is an irregular shape. Thus, it is a NP-hard problem to use Equation (3) to accurately calculate the coverage volume of node set Ns. This proposed algorithm does not require the underwater coordinate position information of the node calculated by GPS; moreover, it only requires the relative coordinate positions of nodes on the water surface. This is feasible for 3D UWSN deployment.
5.1.2. Connectivity Analysis
The sink node or SRN broadcasts a message to the other nodes to identify their one-hop nodes with a variable communication radius Rb, where , thus nodes belonging to sink or SRN are connected with each other in horizontal plane. Moreover, as mentioned in Section 3.8, when calculating OD, the maximum ED is taken with Rcmax, thus the node whose depth is to be calculated and its basic node are always connected as known from Equation (8). Therefore, the process of depth-adjustment guarantees that the network is always connected.
5.1.3. Energy Balance Analysis
According to this proposed deployment strategy, the deployed SRNs far from sink node have a larger communication radius, thus the corresponding sub-trees far from sink node have a larger communication distance and they have a large vertical adjustment space. Therefore, the node density in this area far from sink node is small. On the contrary, the sub-trees near the sink node have smaller communication distances and they have a small vertical adjustment space. Therefore, the node density and the number of leaf nodes in this area near the sink node are large. The node distribution deployed with GRSUNDSOA is non-uniform. Moreover, when calculating the dive depth of nodes, it not only considers the local optimal dive depth based on basic nodes with the goal of maximizing the coverage utilization, but also considers the global optimal dive depth from all local optimal dive depths with the goal of improving coverage utilization and energy balance. Therefore, according to this proposed deployment strategy, there are more nodes in hot-spots area near sink node and the node density is different in different under water areas. So that network transmission energy consumption is balanced and it can avoid the energy hole problem effectively.
5.1.4. Complexity Analysis
Message Complexity
The algorithm mainly includes the following aspects of message transmission when deploying the network. Initially, the sink node broadcasts a message to the other nodes with a variable communication radius and the nodes which receive this message reply to sink. Ring by ring, the nodes in each GR broadcast a message to the other nodes with a variable communication radius and the nodes receiving this message send a response message to the corresponding node in GR. Finally, the sink node sends the calculated depths to each node through the connected tree. Therefore, the message complexity of each node is O(1). For UWSNs composed of n nodes, the total message complexity is O(n).
Time Complexity
For UWSNs composed of n nodes, the time consumption of GRSUNDSOA is mainly in the calculation of the dive depths. The proposed algorithm needs to calculate the depths of n nodes one by one. For the depth calculation of each node, let the maximum number of nodes in BNS be d, and then the local optimal dive depth of each basic node is to be calculated. For the local optimal depth calculation of each basic node, it needs to calculate the overlap area between each candidate best position and the nodes whose depths have been calculated. Let the maximum number of candidate best position be k. Therefore, the time complexity of GRSUNDSOA is O(ndk).
5.2. Simulation and Experimental Analysis
5.2.1. Simulation Scenario and Parameter Settings
In order to verify the effectiveness of GRSUNDSOA, the proposed algorithms are implemented and the nodes deployment process are simulated by a MatLab program. The simulation experiments are performed on a computer equipped with an Intel Core i7-8550U 1.8 GHz CPU and 8.0 G RAM. GRSUNDSOA is compared with four approaches— Cacc [28], CDA [26,27], VODA [29]—and the random based deployment approach in this simulation. To fully verify the algorithms performance, each simulation is conducted 20 times. The monitoring area is set to 200 m × 200 m × 500 m. Some parameter settings used in the simulations are shown in Table 1. The definitions of these parameters are shown in glossary section.

Table 1.
Simulation parameter settings.
5.2.2. Analysis of the Effect of Parameter α on the Algorithm
In this experiment, the number of nodes N is fixed to 120 and α value is varied from 1.4 to 1.8 with the step length 0.1. The effects of α on three indicators, namely, coverage rate, average node degree Navg and the sink node degree Nsin in Rcmax are compared and analyzed.
As shown from Figure 9, with the increase of α value, both the broadcast radius and the distances between SRNs increase. The number of SRNs in the 1st GR increases during the execution of GRSUNDSOA, that is, the number of constructed sub-trees increases, and meanwhile, the number of the nodes in each sub-tree also increases. Therefore, the average node degree and the sink node degree in Rcmax increase obviously, on the contrary, the change in coverage rate is relatively slight.
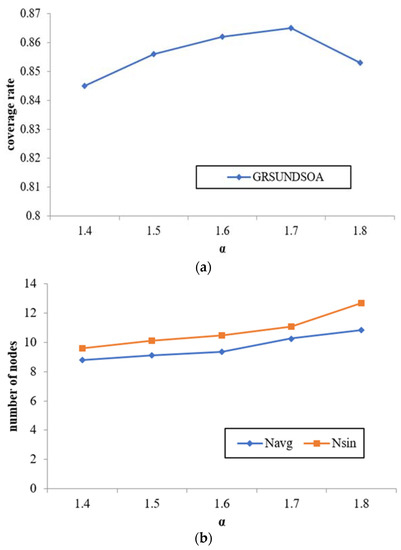
Figure 9.
Effect of parameter α value on network performance. (a) The effects of α on coverage rate. (b) The effects of α on node degree.
In the following experiments, α value is fixed to 1.4, and the number of nodes N varies from 80 to 160.
5.2.3. Coverage Rate Comparison
The coverage rate comparison among five algorithms with various number of nodes is shown in Figure 10.
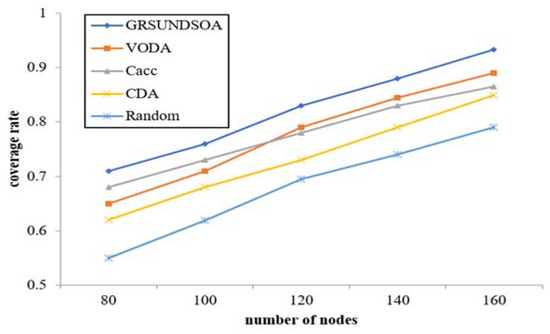
Figure 10.
Coverage rate analysis for varying number of nodes.
This figure shows that the coverage rate of five algorithms increases with the increasing of the number of nodes, but the trend slows down. GRSUNDSOA shows better coverage rate than that of the other four deployment approaches with the same number of nodes. Compared with the random based deployment approach, the coverage rate of GRSUNDSOA is increased by about 15%–30%. The coverage rate of GRSUNDSOA is also significantly improved compared to Cacc, CDA, and VODA algorithms. When selecting the dive position of nodes, CDA only compares the coverage redundancy rates on the position where the distance between the node and each of its basic nodes is Rcmax but does not consider the situation where the distance between them is less than Rcmax. Similarly, VODA only calculates the dive depth on the position with a special ratio of the communication radius to the sensing radius. The dive positions calculated by both methods are often the local optimal dive positions rather than the global optimal positions. Different from CDA and VODA, GRSUNDSOA not only searches the local optimal dive position based on a certain basic node, but also searches the global optimal dive position based on the basic nodes whose depths have been calculated in the previous process. Therefore, the coverage rate of GRSUNDSOA is improved greatly.
5.2.4. Connectivity Comparison
For GRSUNDSOA, the maximum communication radius Rcmax is always considered in the process of constructing connected tree structure, which guarantees the connectivity of the generated network topology. Therefore, like the Cacc, CDA, VODA algorithms, GRSUNDSOA guarantees the connection path from the sensors to sink node, that is, Con = 100% calculated with Equation (4). However, that random based deployment approach cannot guarantee the network connectivity.
5.2.5. Analysis of the Average Node Degree, the node degree near Sink Node and Energy Balance
The indicators Navg and Nsin mentioned in Section 3.9 reflect not only the reliability but also the load balance performance of network. Because the load of the nodes near the sink node is always greater, it is helpful for increasing routing and reducing energy consumption that increases the number of nodes near the sink node. Therefore, it can effectively balance the load of nodes and prevent nodes failure from energy exhausting prematurely. Thus, it can extend the lifecycle of network.
As shown in Figure 11 and Figure 12, the average node degree Navg and the sink node degree Nsin in Rcmax of GRSUNDSOA are significantly higher than that of Cacc, CDA, and VODA for the varying number of nodes. It indicates that the network deployed by GRSUNDSOA can achieve better load balance between routing and higher reliability. As the broadcast radius of GRSUNDSOA increases gradually, the distances between SRNs increase gradually and the number of each ring of SRNs is roughly uniform. Therefore, the nodes distribution deployed by GRSUNDSOA is non-uniform. The nodes number near sink node is large and their distribution is dense. On the contrary, the nodes number far from sink node is small and their distribution is relative sparse. This conforms to the hot spot characteristics near the sink node and its energy consumption is more balanced. In addition, the proposed algorithm constructs the MBCUEB model and constrainted optimization model when calculating the global optimal dive depth. These models reflect the comprehensive performance of node on coverage utilization and energy balance.
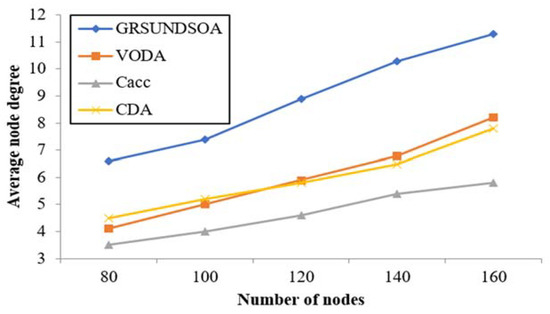
Figure 11.
Comparison of the average node degree.
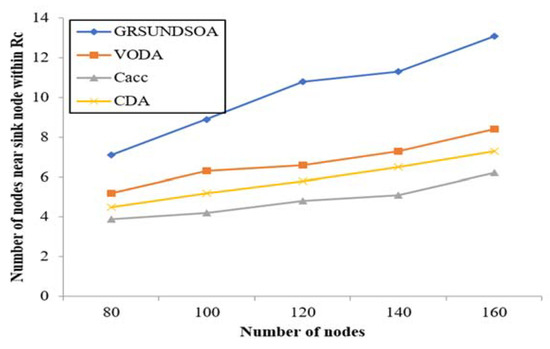
Figure 12.
Comparison of the number of nodes near sink node within radius Rcmax.
In a word, GRSUNDSOA can avoid the energy hole phenomenon effectively and extend the lifecycle of the network.
5.2.6. Average Path Length
The average path length for each sensor to the sink node shows the average hops number for information transmission via nodes. In GRSUNDSOA, because the number of nodes near sink node is large, one hop distance is shorter. On the contrary, one hop distance is larger for the nodes far from the sink node especially on the border of monitoring area. Thus, as shown in Figure 13, with the number of nodes increasing, the change of average path length of GRSUNDSOA is slight and it is always lower than that of CDA and VODA.
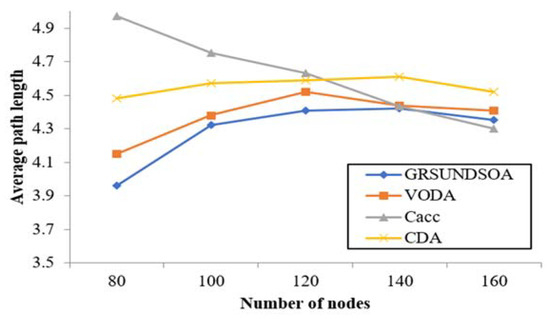
Figure 13.
Comparison of average path length.
5.2.7. Deployment Energy Consumption
To estimate the energy consumption of network deployment, the deployment energy consumption model is utilized as Equation (11), where the diving speed of nodes v is set at 2.4 m/min, and the power p is set with 0.6 W in this experiment. As shown in Figure 14, the energy consumption for deployment of GRSUNDSOA is not much different from that of the other three algorithms, CDA, Cacc, and VODA.
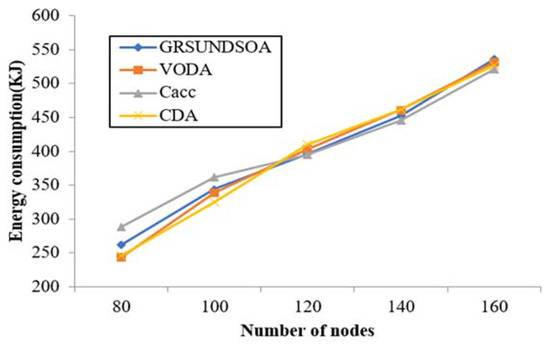
Figure 14.
Comparison of energy consumption for network deployment.
6. Conclusions
In this paper, a growth ring style uneven node depth-adjustment self-deployment optimization algorithm for UWSNs is proposed. Through a series of simulation experiments, the proposed GRSUNDSOA algorithm is compared with the CDA, Cacc and VODA algorithms in terms of several performance indicators such as coverage rate, connectivity, average node degree, average path length, energy balance, and deployment energy consumption. The simulation results with varying number of nodes indicate that GRSUNDSOA has better coverage, network reliability and energy balance performance than those of CDA, Cacc and VODA. It can avoid the energy hole problem effectively. Moreover, GRSUNDSOA also guarantees the full connectivity of network like the other three algorithms. Thus, GRSUNDSOA can improve the network lifecycle on the whole.
In practical UWSN environments, the free-floating sensors tend to change the network topology gradually due to factors such as waves, wind, and vorticity. As future work, we plan to study the effect of dynamic network topology changes on network coverage and connectivity. We also plan to further improve the deployment strategy of underwater wireless sensor network.
Author Contributions
Conceptualization, L.Y. and Y.H.; methodology, L.Y.; software, Z.H.; validation, L.Y., and Z.H.; formal analysis, L.Y.; investigation, L.Y.; resources, Y.H.; data curation, L.Y.; writing—original draft preparation, L.Y.; writing—review and editing, Y.H.; visualization, Z.H.; supervision, Y.H.; project administration, Y.H.; funding acquisition, Y.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China, grant number 61271143, and the Key Science and Research Project of Henan Province University of China, grant number 20A520023.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Glossary
| Nomenclature | Definition |
| GRSUNDSOA | Growth Ring Style based Uneven Node Depth-adjustment Self-deployment Optimization Algorithm |
| GR | Growth Ring |
| SRNs | Subtree Root Nodes |
| FSRNs | Forward Subtree Root Nodes |
| BNS | Basic Node Set |
| HD | Horizontal Distance |
| ED | Expect Distance |
| OD | Offset Distance |
| MBCUEB | Model Based on Coverage Utilization and Energy Balance |
| Symbols | Definition |
| N | The number of sensors deployed in network |
| Nconnect | The number of sensors that connect with sink node |
| Rb | The communication radius of the sensor nodes |
| Rs | The sensing radius of the sensor nodes |
| Rcmax | The maximum communication radius of the sensor nodes |
| Nsi | The sensor node with ID i |
| Nsi.Z | The depth of Nsi under water |
| Ns | The sensor nodes set deployed in network |
| M | The entire monitoring area of UWSN |
| Length,Width,Height | Length—The length of the monitoring area; Width—The width of the monitoring area; Height—The height of the monitoring area |
| U(x,y,z) | A pixel in monitoring area |
| Pcov(x,y,z,Nsi ) | The probability that U(x,y,z) is covered by node Nsi |
| dist(Nsi,Nsj) | The Euclidean distance between Nsi and Nsj |
| d(Nsi,Nsj) | The HD between Nsi and Nsj |
| Edist(Nsi,Nsj) | The ED between Nsi and Nsj |
| DivNs(Nsi,Nsj) | The OD between Nsi and Nsj |
| distmax | The maximum Euclidean distance of all nodes from sink node |
| Pcov(U, Ns) | The probability that U is covered by Ns |
| Qi | The monitoring area of sensor node Nsi |
| η | The coverage rate of UWSN |
| Con | The connectivity rate of UWSN |
| V(Nsi, Nsj) | The volume of the overlapping area covered by Nsi and Nsj |
| The coverage utilization of Nsi | |
| g | The number of GR |
| Rootg | The g-th GR |
| basenodes | The current BNS |
| ∆r | The step length for the set {Rcmax, Rcmax-∆r, …., d(Nsi,Nsj)} |
| Nsin | The numbers of nodes within Rcmax from the sink node |
| Navg. | The average number of neighbor nodes for all sensors |
| W | The energy consumption for network deployment |
| D | The total distance that all nodes move during the deployment process |
| v | The moving speed of nodes |
| p | The power of nodes |
| Sg | The nodes within the g-th GR |
| Nsi.<id, tree, leaf, fathe, root, processed> | The attributions of Nsi. Nsi.id: ID of Nsi; Nsi.tree indicates whether Nsi joins the tree structure (1—Yes, 0—No); Nsi.father: the id of its parent node; Nsi.root: the root node of the tree to which Nsi is attached; Nsi. processed indicates whether Nsi has been calculated the diving depth (1—Yes, 0—No); Nsi.leaf indicates whether Nsi is a leaf node (1—Yes, 0—No). |
| distnodes | The ordered node set of Sg according to dist(Nsi, Sink) from largest to smallest |
| α | The adjustment parameter for communication radius |
| β | The adjustment parameter for communication radius |
| γ | The adjustment parameter for constructing Rootg from Sg |
| r | The random number |
| th | A threshold for constructing Rootg from Sg |
| μ | A non-negative integer threshold |
| δ | The set maximum of GR |
| ZNs(j) | The calculated depth of the basic node Nsj |
| Candidate(Nsi) | The dive candidate position points set of Nsi |
| One of candidate position points in Candidate(Nsi) | |
| a, b | The weights for MBCUEB, a+b = 1 |
| f(Nsi) | The comprehensive optimal model of Nsi on coverage utilization and energy balance |
References
- Li, S.; Qu, W.; Liu, C.; Qiu, T.; Zhao, Z. Survey on high reliability wireless communication for under water sensor networks. J. Netw. Comput. Appl. 2019, 148, 102446. [Google Scholar] [CrossRef]
- Sunhyo, K.; Jee, W.C. Optimal deployment of vector sensor nodes in underwater acoustic sensor networks. Sensors 2019, 19, 1–10. [Google Scholar]
- Wei, X.; Guo, H.; Wang, X.; Wang, X.; Wang, C.; Guizani, M.; Du, X. A co-design-based reliable low-latency and energy-efficient transmission protocol for UWSNs. Sensors 2020, 20, 6370. [Google Scholar] [CrossRef] [PubMed]
- Yang, G.; Dai, L.; Si, G.; Wang, X.; Wang, X. Challenges and security issues in under water wireless sensor networks. In Proceedings of the 2018 International Conference on Identification, Information and Knowledge in the Internet of Things, Beijing, China, 19–21 October 2018; pp. 210–216. [Google Scholar]
- Felemban, E.; Shaikh, F.K.; Qureshi, U.M. Underwater Sensor Network Applications: A Comprehensive Survey. Int. J. Distrib. Sens. Netw. 2015, 2015, 1–14. [Google Scholar] [CrossRef]
- Gupta, O.; Goyal, N. The evolution of data gathering static and mobility models in underwater wireless sensor networks: A survey. J. Ambient. Intell. Humaniz. Comput. 2021, 1–17. [Google Scholar] [CrossRef]
- Wang, Y.; Wu, S.; Chen, Z.; Gao, X.; Chen, G. Coverage Problem with Uncertain Properties in Wireless Sensor Networks: A Survey. Comput. Netw. 2017, 123, 200–232. [Google Scholar] [CrossRef]
- Tuna, G.; Gungor, V.C. A survey on deployment techniques, localization algorithms, and research challenges for underwater acoustic sensor networks. Int. J. Commun. Syst. 2017, 30, e3350. [Google Scholar] [CrossRef]
- Wang, W.; Huang, H.; He, F.; Xiao, F.; Jiang, X.; Sha, C. An enhanced virtual force algorithm for diverse k-Coverage deployment of 3D underwater wireless sensor networks. Sensors 2019, 19, 3496. [Google Scholar] [CrossRef]
- Song, X.; Gong, Y.; Jin, D.; Li, Q. Nodes deployment optimization algorithm based on improved evidence theory of underwater wireless sensor networks. Photonic Netw. Commun. 2019, 37, 224–232. [Google Scholar] [CrossRef]
- Wang, X.; Qin, D.; Zhao, M.; Guo, R.; Berhane, T.M. UWSNs positioning technology based on iterative optimization and data position correction. J. Wirel. Com. Netw. 2020, 158, 2020. [Google Scholar] [CrossRef]
- Chen, L.; Hu, Y.; Sun, Y.; Liu, H.; Lv, B.; Chen, J. An underwater layered protocol based on cooperative communication for underwater sensor network. In Proceedings of the 2020 Chinese Control and Decision Conference (CCDC), Hefei, China, 23–25 May 2020; pp. 2014–2019. [Google Scholar]
- Kim, B.-S.; Sung, T.-E.; Kim, K.-I. An NS-3 implementation and experimental performance analysis of IEEE 802.15.6 standard under different deployment Scenarios. Int. J. Environ. Res. Public Health 2020, 17, 4007. [Google Scholar] [CrossRef]
- Campanile, L.; Gribaudo, M.; Iacono, M.; Marulli, F.; Mastroianni, M. Computer network simulation with ns-3: A systematic literature review. Electronics 2020, 9, 272. [Google Scholar] [CrossRef]
- Nobre, M.; Silva, I.; Guedes, L.A.; Portugal, P. Towards a WirelessHART module for the ns-3 simulator. In Proceedings of the 2010 IEEE 15th Conference on Emerging Technologies & Factory Automation (ETFA 2010), Bilbao, Spain, 13–16 September 2010; pp. 1–4. [Google Scholar]
- Han, F.; Liu, X.; Mohamed, I.I.; Ghazali, K.H.; Zhao, Y. A survey on deployment and coverage strategies in three-dimensional wireless sensor networks. In Proceedings of the 8th International Conference on Software and Computer Applications, ICSCA 2019, Penang, Malaysia, 19–21 February 2019; pp. 544–549. [Google Scholar]
- Shahanaghi, A.; Yang, Y.L.; Buehrer, R.M. Stochastic Link Modeling of Static Wireless Sensor Networks Over the Ocean Surface. IEEE Trans. Wirel. Commun. 2020, 19, 4154–4169. [Google Scholar] [CrossRef]
- Senouci, M.R.; Mellouk, A.; Asnoune, K.; Bouhidel, F.Y. Movement-assisted sensor deployment algorithms: A survey and taxonomy. IEEE Commun. Surv. Tutor. 2015, 17, 2493–2510. [Google Scholar] [CrossRef]
- Wang, J.; Ju, C.; Kim, H.-J.; Sherratt, R.S.; Lee, S. A mobile assisted coverage hole patching scheme based on particle swarm optimization for WSNs. Clust. Comput. 2019, 22, 1787–1795. [Google Scholar] [CrossRef]
- Kadu, R.; Malpe, K. Movement-assisted coverage improvement approach for hole healing in wireless sensor networks. In Proceedings of the 2017 2nd IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT), Tamil Nadu, India, 22–24 February 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–4. [Google Scholar]
- Wang, X.; Li, N.; Liu, F.; Ding, Y. The double-coverage algorithm for mobile node deployment in underwater sensor network. In Proceedings of the 5th International Conference on Geo-Spatial Knowledge and Intelligence, Chiang Mai, Thailand, 8–10 December 2017. [Google Scholar]
- Ding, Y.; Li, N.; Song, B.; Yang, Y. The mobile node deployment algorithm for underwater wireless sensor networks. In Proceedings of the 2017 Chinese Automation Congress, Jinan, China, 20–22 October 2017; pp. 456–460. [Google Scholar]
- Detweiler, C.; Doniec, M.; Vasilescu, I. Autonomous Depth Adjustment for Underwater Sensor Networks: Design and Applications. IEEE ASME Trans. Mechatron. 2012, 17, 16–24. [Google Scholar] [CrossRef]
- Chen, S.X.; Huang, Q.Z.; Zhang, Y.; Li, X. Double sink energy hole avoidance strategy for wireless sensor network. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 226. [Google Scholar] [CrossRef]
- Kamran, L.; Nadeem, J.; Ashfaq, A.; Khan, Z.A.; Alrajeh, N.; Khan, M.I. On energy hole and coverage hole avoidance in underwater wireless sensor networks. IEEE Sens. J. 2016, 16, 4431–4442. [Google Scholar]
- Senel, F.; Akkaya, K.; Yilmaz, T. Autonomous deployment of sensors for maximized coverage and guaranteed connectivity in underwater acoustic sensor networks. In Proceedings of the IEEE 38th Conference on Local Computer Networks (LCN), Sydney, Australia, 21–24 October 2013. [Google Scholar]
- Senel, F.; Akkaya, K.; Erol-Kantarci, M.; Yilmaz, T. Self-deployment of mobile underwater acoustic sensor networks for maximized coverage and guaranteed connectivity. Ad. Hoc. Netw. 2015, 34, 170–183. [Google Scholar] [CrossRef]
- Senel, F. Coverage-aware connectivity-constrained unattended sensor deployment in underwater acoustic sensor networks. Wirel. Commun. Mob. Comput. 2016, 30, 70–77. [Google Scholar] [CrossRef]
- Su, Y.; Guo, L.; Jin, Z.; Fu, X. A Voronoi-Based Optimized Depth Adjustment Deployment Scheme for Underwater Acoustic Sensor Networks. IEEE Sens. J. 2020, 20, 13849–13860. [Google Scholar] [CrossRef]
- Jin, Z.; Ji, Z.; Su, Y. Deployment optimization algorithm using depth adjustable nodes in underwater acoustic networks. Syst. Eng. Electron. 2019, 41, 203–207. [Google Scholar]
- Nazrul Alam, S.M.; Haas, Z.J. Coverage and connectivity in three-dimensional networks. In Proceedings of the 12th Annual International Conference on Mobile Computing and Networking (MOBICOM ’06), Los Angeles, CA, USA, 23–29 September 2006; pp. 346–357. [Google Scholar]
- Jiang, P.; Xu, Y.; Wu, F. Node self-deployment algorithm based on an uneven cluster with radius adjusting for underwater sensor networks. Sensors 2016, 16, 98. [Google Scholar] [CrossRef]
- Wang, H.; Liu, M.; Zhang, S. An efficient depth-adjustment deployment scheme for underwater wireless sensor networks. In Proceedings of the 34th Chinese Control Conference, Hangzhou, China, 28–30 July 2015. [Google Scholar]
- Pompili, D.; Melodia, T.; Akyildiz, I.F. Deployment analysis in underwater acoustic wireless sensor networks. In Proceedings of the 1st ACM International Workshop on Underwater Networks, Los Angeles, CA, USA, September 2006; ACM: Los Angeles, CA, USA, 2006; pp. 48–55. [Google Scholar]
- Jiang, P.; Shuai, L.; Jun, L.; Wu, F.; Zhang, L. A depth-adjustment deployment algorithm based on two-dimensional convex hull and spanning tree for underwater wireless sensor networks. Sensors 2016, 16, 1087. [Google Scholar] [CrossRef] [PubMed]
- Akkaya, K.; Newell, A. Self-deployment of sensors for maximized coverage in underwater acoustic sensor networks. Comput. Commun. 2009, 32, 1233–1244. [Google Scholar] [CrossRef]
- Dux, Y.; Hui, L.I.; Lin, Z. Coverage algorithm based on fixed-directional movement for underwater sensor network. Comput. Eng. 2015, 41, 76–80. [Google Scholar]
- Javaid, N.; Ahmad, Z.; Sher, A.; Wadud, Z.; Khan, Z.A.; Ahmedn, S.H. Fair energy management with void hole avoidance in intelligent heterogeneous underwater WSNs. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 4225–4241. [Google Scholar] [CrossRef]
- Erdem Emre, H.; Gungor Cagri, V. Analyzing lifetime of energy harvesting underwater wireless sensor nodes. Int. J. Commun. Syst. 2020, 33, e4214. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).