A Spatiotemporal-Oriented Deep Ensemble Learning Model to Defend Link Flooding Attacks in IoT Network
Abstract
1. Introduction
2. Related Work
2.1. LFA and Countermeasures
| No. | SDN | Detection | Mitigation | ||||
|---|---|---|---|---|---|---|---|
| Detect Target/All Links | Flow/Packet Based | Method | Time Series | Method | Related to * of TLs | ||
| [1] | Y | Target | Flow | Measure TL U | N | 1.Rerouting 2.Drop malicious flows | N |
| [3] | Y | All | Flow | Consumed Bandwidth Rate > T | N | NA | N |
| [4] | Y | All | Flow | Traffic rate > T | N | Broadcast block route message to all routers | N |
| [5] | Y | All | Flow | Rate of link U changes > T | N | 1.Max-min fairness packet dropping 2.Drop flows based BL | N |
| [6] | N | All | Flow | Available Bandwidth > T | N | NA | N |
| [7] | N | All | Packet | Randomized Traffic rate > T | N | NA | N |
| [8] | Y | All | Packet | Traffic rate > T | N | Random dropping | N |
| [9] | N | All | Packet | Monitor the traceroute packet | N | NA | N |
| [10] | Y | All | Packet | Monitor the traceroute packet | N | MTD | N |
| [11] | Y | All | Flow | ANN | N | Null routing | N |
| [12] | Y | All | Flow | CNN | N | 1.Drop packets based BL 2. Max-min fairness packet dropping | N |
| [13] | N | NA | NA | NA | N | Tail drop | N |
| [26, 27, 28, 29, 30] | Y | All | Flow | Stacking based Deep Learning method | Y | NA | N |
2.2. Deep Learning
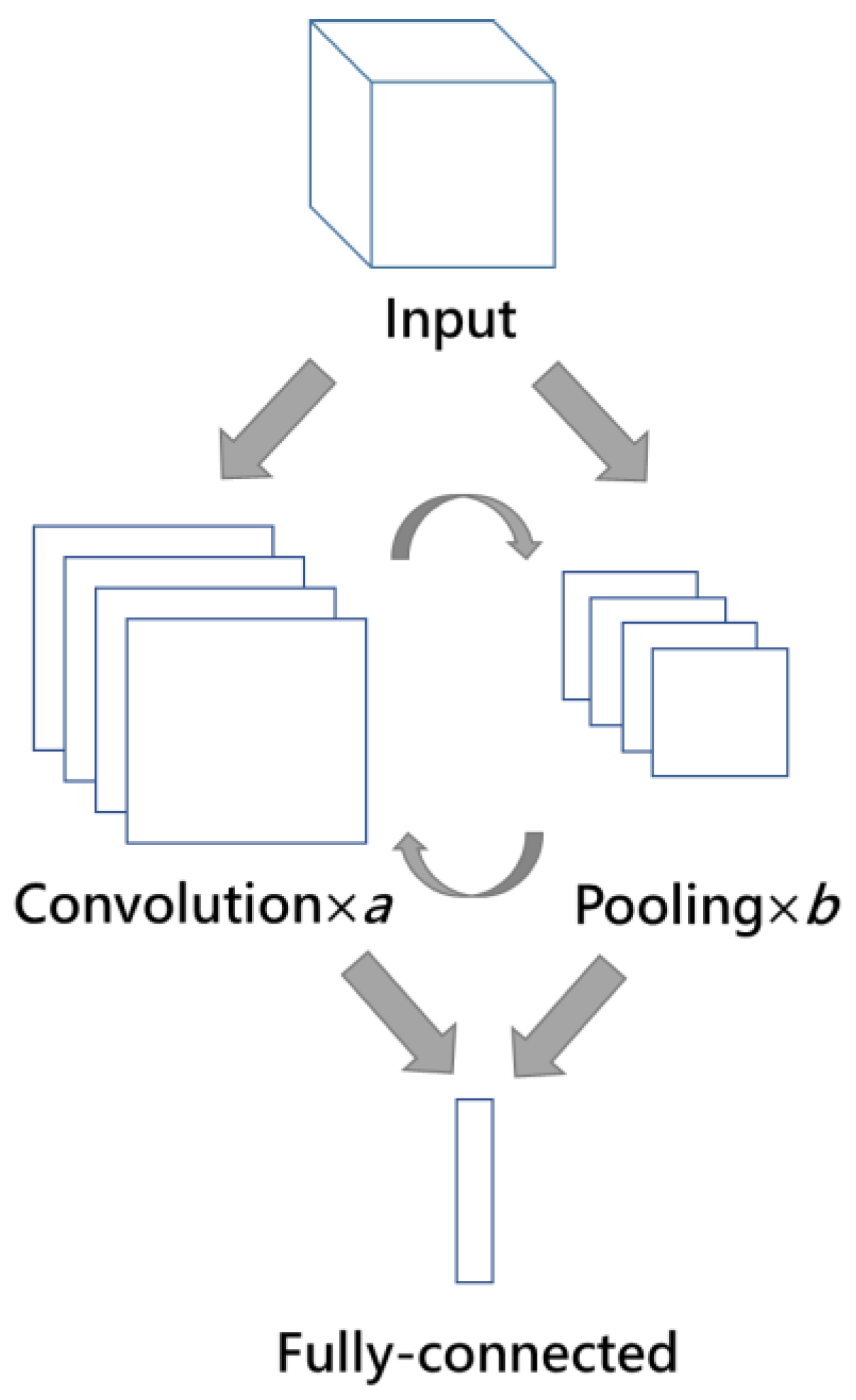
2.2.1. CNN
- A.
- Convolutional layer
- B.
- Pooling layer
- C.
- Fully Connected layer
2.2.2. LSTM
- A.
- Memory cell
- B.
- Forget gate
- C.
- Input gate
- D.
- Output gate
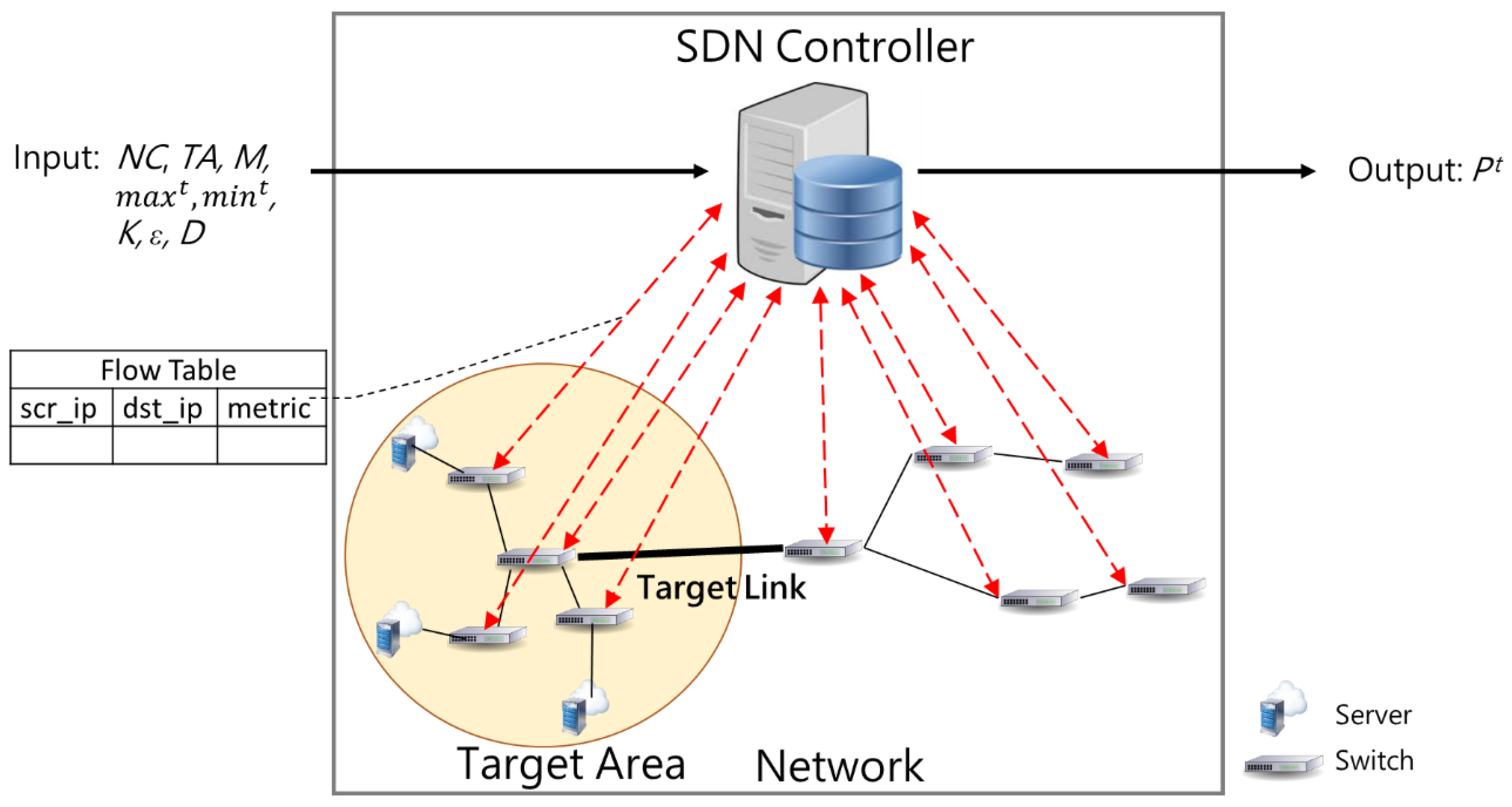
3. Problem Statement
- Given:C, TA, M, maxt, mint, K, ε, and D
- Output: dropping probabilities in target links at time t: Pt
- Objective: maximize MAt
4. Stacking-Based CNN and STM(SCL)
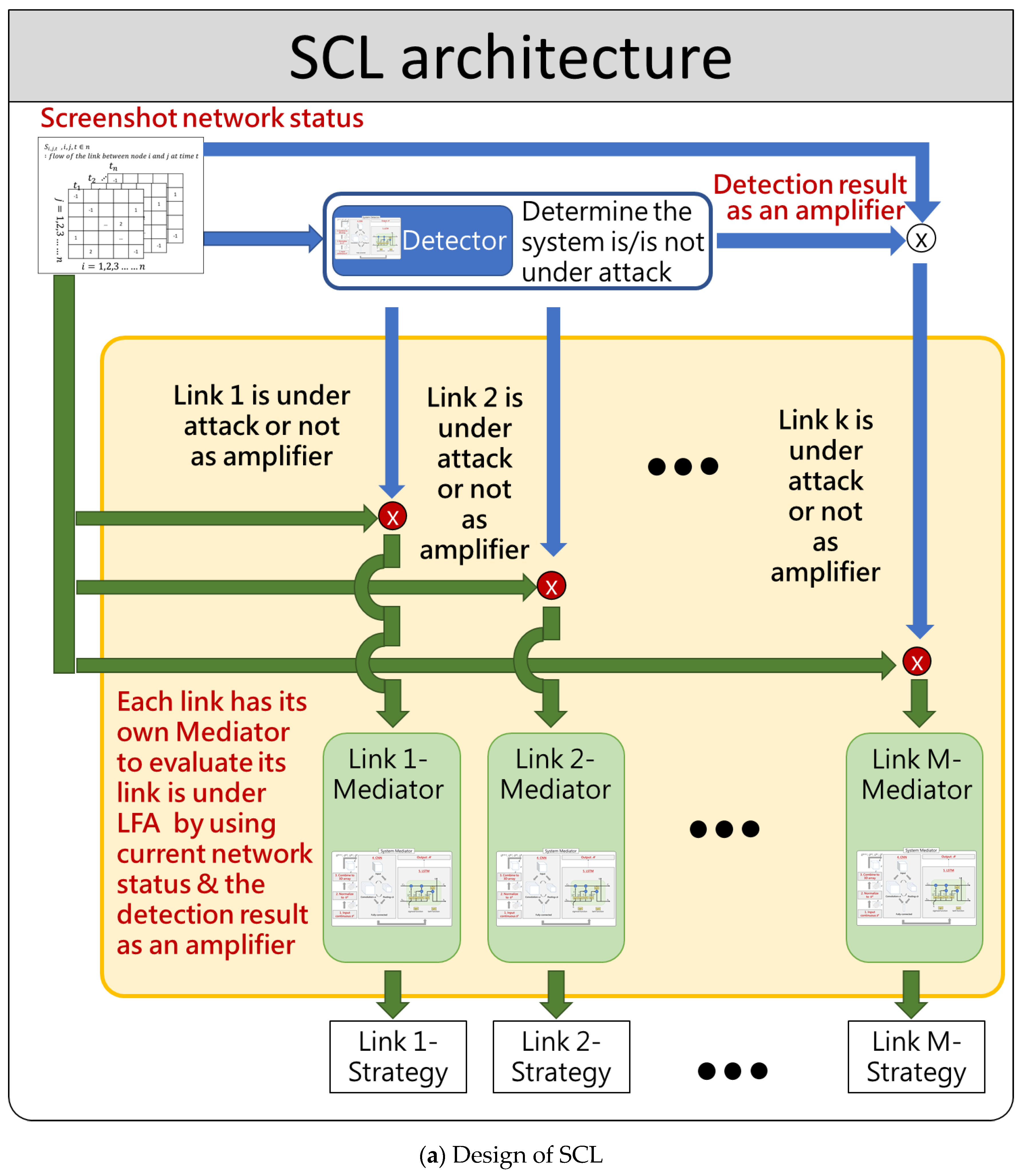
4.1. SCL Overall Architecture
4.2. System Detector Module
4.3. LFA Mitigator Module
5. Evaluation
5.1. Scenario and Parameter Setting
5.1.1. Scenarios Setting
5.1.2. SCL Parameter Setting
5.1.3. Performance Evaluation Metric
5.2. Architecture Investigation
5.2.1. The Effects of the Number of Convolution Layers
5.2.2. The Effects of the Number of Pooling Layers
5.2.3. The Effects of Different Orders of Pooling in CNN
- (1)
- Pooling -> Convolution -> Convolution -> Convolution -> Fully Connected;
- (2)
- Convolution -> Pooling -> Convolution -> Convolution -> Fully Connected;
- (3)
- Convolution -> Convolution -> Pooling -> Convolution -> Fully Connected;
- (4)
- Convolution -> Convolution -> Convolution -> Pooling -> Fully Connected.
5.2.4. The Effects of Different Activation Functions in CNN
5.2.5. Performance of SCL
5.3. Parameter Investigation
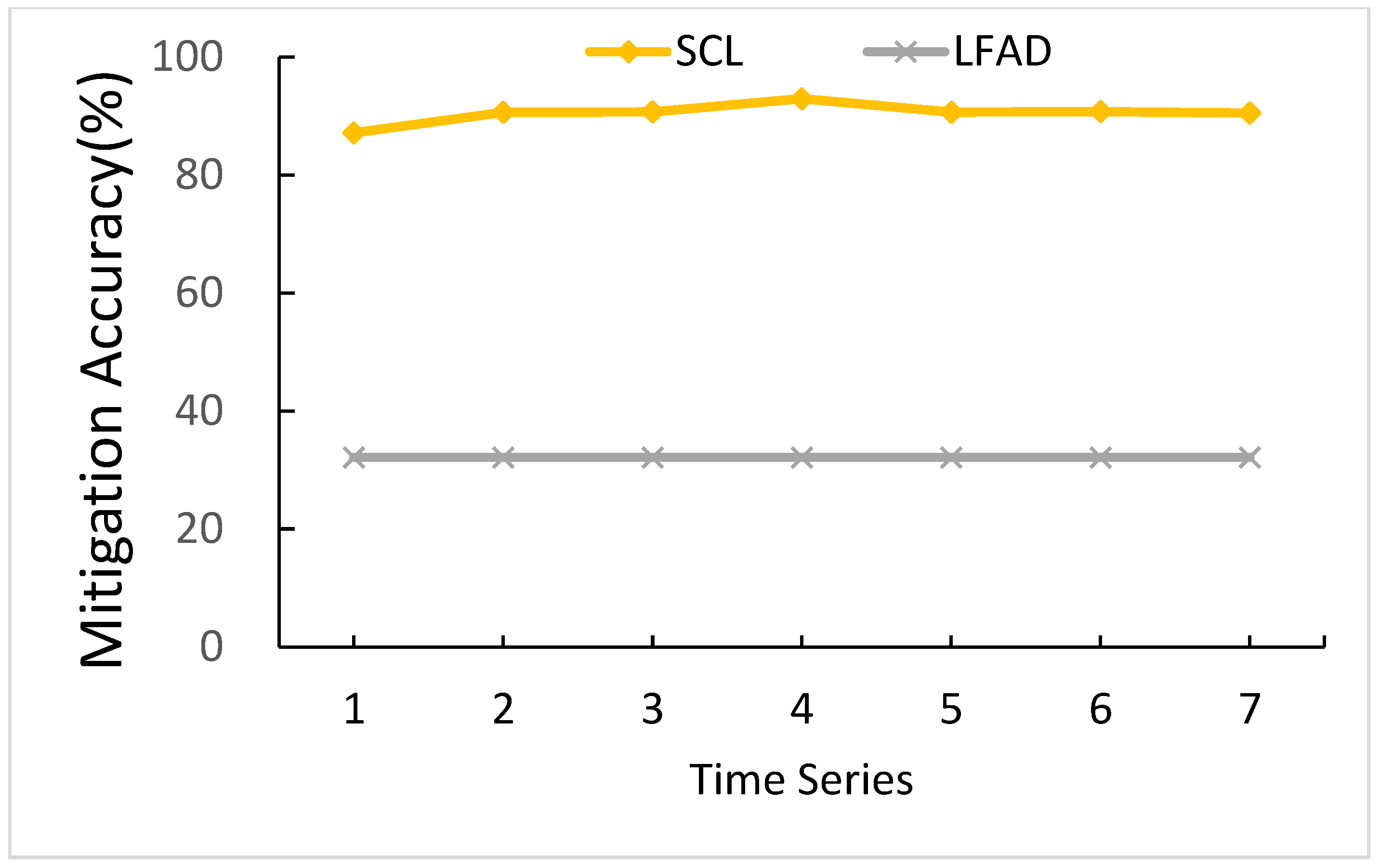
5.3.1. The Effects of Time Series
5.3.2. The effects of the Number of Target Links
5.3.3. The Effects of the Number of Input Nodes
5.3.4. The Effects of the Number of Bots
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wang, J.; Wen, R.; Li, J.; Yan, F.; Zhao, B.; Yu, F. Detecting and mitigating target link-flooding attacks using SDN. IEEE Trans. Dependable Secur. Comput. 2018, 16, 944–956. [Google Scholar] [CrossRef]
- Kang, M.S.; Lee, S.B.; Gligor, V.D. The Crossfire Attack. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 127–141. [Google Scholar] [CrossRef]
- Kim, J.; Shin, S. Software-Defined HoneyNet: Towards Mitigating Link Flooding Attacks. In Proceedings of the 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshop (DSN-W), Denver, CO, USA, 26–29 June 2017; pp. 99–100. [Google Scholar]
- Gajbhiye, A.; Sen, D.; Bhatt, A.; Soni, G. DPLPLN: Detection and Prevention from Flooding Attack in IoT. In Proceedings of the 2020 International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 10–12 September 2020; pp. 704–709. [Google Scholar] [CrossRef]
- Zheng, J.; Li, Q.; Gu, G.; Cao, J.; Yau, D.K.; Wu, J. Realtime DDoS defense using COTS SDN switches via adaptive correlation analysis. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1838–1853. [Google Scholar] [CrossRef]
- Xue, L.; Ma, X.; Luo, X.; Chan, E.W.; Miu, T.T.; Gu, G. LinkScope: Toward detecting target link flooding attacks. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2423–2438. [Google Scholar] [CrossRef]
- Ma, X.; An, B.; Zhao, M.; Luo, X.; Xue, L.; Li, Z.; Miu, T.T.N.; Guan, X. Randomized security patrolling for link flooding attack detection. IEEE Trans. Dependable Secur. Comput. 2019, 17, 795–812. [Google Scholar] [CrossRef]
- Ravi, N.; Shalinie, S.M.; Theres, J.D.D. BALANCE: Link flooding attack detection and mitigation via Hybrid-SDN. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1715–1729. [Google Scholar] [CrossRef]
- Sakuma, K.; Asahina, H.; Haruta, S.; Sasase, I. Traceroute-based Target Link Flooding Attack Detection Scheme by Analyzing Hop Count to the Destination. In Proceedings of the 23rd Asia-Pacific Conference on Communications (APCC), Perth, WA, Australia, 11–13 December 2017; pp. 1–6. [Google Scholar]
- Aydeger, A.; Saputro, N.; Akkaya, K.; Rahman, M. Mitigating Crossfire Attacks Using SDN-Based Moving Target Defense. In Proceedings of the IEEE 41st Conference on Local Computer Networks, Dubai, United Arab Emirates, 7–10 November 2016; pp. 627–630. [Google Scholar]
- Rasool, R.U.; Ashraf, U.; Ahmed, K.; Wang, H.; Rafique, W.; Anwar, Z. Cyberpulse: A machine learning based link flooding attack mitigation system for software defined networks. IEEE Access 2019, 7, 34885–34899. [Google Scholar] [CrossRef]
- Xing, J.; Cai, J.; Zhou, B.; Wu, C. A Deep ConvNet-Based Countermeasure to Mitigate Link Flooding Attacks Using Software-Defined Networks. In Proceedings of the 2019 IEEE Symposium on Computers and Communications (ISCC), Barcelona, Spain, 29 June–3 July 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Yang, G.; Hosseini, H.; Sahabandu, D.; Clark, A.; Hespanha, J.; Poovendran, R. Modeling and Mitigating the Coremelt Attack. In Proceedings of the 2018 Annual American Control Conference (ACC), Milwaukee, WA, USA, 27–29 June 2018; pp. 3410–3416. [Google Scholar]
- Deep Neural Network (DNN) Is an Artificial Neural Network (ANN). Available online: https://bangaloreai.com/blog/meet-the-bitcoin-cash-hyper-mini-sprint-car/ (accessed on 27 June 2020).
- What Is a Botnet Attack? Available online: https://www.akamai.com/us/en/resources/what-is-a-botnet.jsp (accessed on 25 May 2020).
- Mahajan, N.V.; Deshpande, A.S.; Satpute, S.S. Prediction of Fault in Gas Chromatograph using Convolutional Neural Network. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 930–933. [Google Scholar]
- Pai, K.; Giridharan, A. Convolutional Neural Networks for classifying skin lesions. In Proceedings of the TENCON 2019—2019 IEEE Region 10 Conference (TENCON), Kochi, India, 17–20 October 2019; pp. 1794–1796. [Google Scholar] [CrossRef]
- Guo, T.; Dong, J.; Li, H.; Gao, Y. Simple convolutional neural network on image classification. In Proceedings of the 2017 IEEE 2nd International Conference on Big Data Analysis (ICBDA), Beijing, China, 10–12 March 2017; pp. 721–724. [Google Scholar] [CrossRef]
- A Comprehensive Guide to Convolutional Neural Networks—The ELI5 Way. Available online: https://towardsdatascience.com/a-comprehensive-guide-to-convolutional-neural-networks-the-eli5-way-3bd2b1164a53 (accessed on 25 May 2020).
- Fully Connected Layers in Convolutional Neural Networks: The Complete Guide. Available online: https://missinglink.ai/guides/convolutional-neural-networks/fully-connected-layers-convolutional-neural-networks-complete-guide/ (accessed on 21 March 2020).
- Yu, S. Residual Learning and LSTM Networks for Wearable Human Activity Recognition Problem. In Proceedings of the 2018 37th Chinese Control Conference (CCC), Wuhan, China, 25–27 July 2018; pp. 9440–9447. [Google Scholar]
- Kopetz, H. Real-Time Systems: Design Principles for Distributed Embedded Applications; Springer Publishing Company: New York, NY, USA, 2011. [Google Scholar]
- Zhang, Z.; Chen, H.; Hua, M.; Li, C.; Huang, Y.; Yang, L. Double coded caching in ultra dense networks: Caching and multicast scheduling via deep reinforcement learning. IEEE Trans. Commun. 2020, 68, 1071–1086. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef] [PubMed]
- Schmidhuber, J. Deep learning in neural networks: An overview. Neural Netw. 2015, 61, 85–117. [Google Scholar] [CrossRef] [PubMed]
- Alotaibi, B.; Alotaibi, M. A stacked deep learning approach for IoT cyberattack detection. J. Sens. 2020. [Google Scholar] [CrossRef]
- Dutta, V.; Choras, M.; Pawlicki, M.; Kozik, R. A deep learning ensemble for network anomaly and cyber-attack detection. Sensors 2020, 20, 4583. [Google Scholar] [CrossRef] [PubMed]
- Roopak, M.; Tian, G.Y.; Chambers, J. Deep Learning Models for Cyber Security in IoT Networks. In Proceeding of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 0452–0457. [Google Scholar] [CrossRef]
- Khan, M.A.; Kim, J. Toward developing efficient Conv-AE-based intrusion detection system using heterogeneous dataset. Electronics 2020, 9, 1771. [Google Scholar] [CrossRef]
- Alqahtani, M.; Mathkour, H.; Ismail, M.M.B. IoT botnet attack detection based on optimized extreme gradient boosting and feature selection. Sensors 2020, 20, 6336. [Google Scholar] [CrossRef] [PubMed]
- Lever, J.; Krzywinski, M.; Altman, N. Model selection and overfitting. Nat. Method 2016, 13, 703–704. [Google Scholar] [CrossRef]
- Nusrat, I.; Jang, S.-B. A comparison of regularization techniques in deep neural networks. Symmetry 2018, 10, 648. [Google Scholar] [CrossRef]
- Hernández-Blanco, A.; Herrera-Flores, B.; Tomás, D.; Navarro-Colorado, B. A systematic review of deep learning approaches to educational data mining. Complexity 2019. [Google Scholar] [CrossRef]
- Yang, X.; Xue, Q.; Ding, M.; Wu, J.; Gao, Z. Short-term prediction of passenger volume for urban rail systems: A deep learning approach based on smart-card data. Int. J. Prod. Econ. 2021, 231. [Google Scholar] [CrossRef]
- Khan, M.A.; Ki, Y. Cardiac arrhythmia disease classification using LSTM deep learning approach. Comput. Mater. Contin. 2021, 67, 427–443. [Google Scholar] [CrossRef]
- Yadav, B.; Tokekar, S. Deep Learning in Malware Identification and Classification. In Malware Analysis Using Artificial Intelligence and Deep Learning; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Andreopoulos, W.B. Malware Detection with Sequence-Based Machine Learning and Deep Learning. In Malware Analysis Using Artificial Intelligence and Deep Learning; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Yuan, Y.; Cai, X. A human-machine interaction scheme based on background knowledge in 6G-enabled IoT environment. IEEE Int. Things J. 2021. [Google Scholar] [CrossRef]


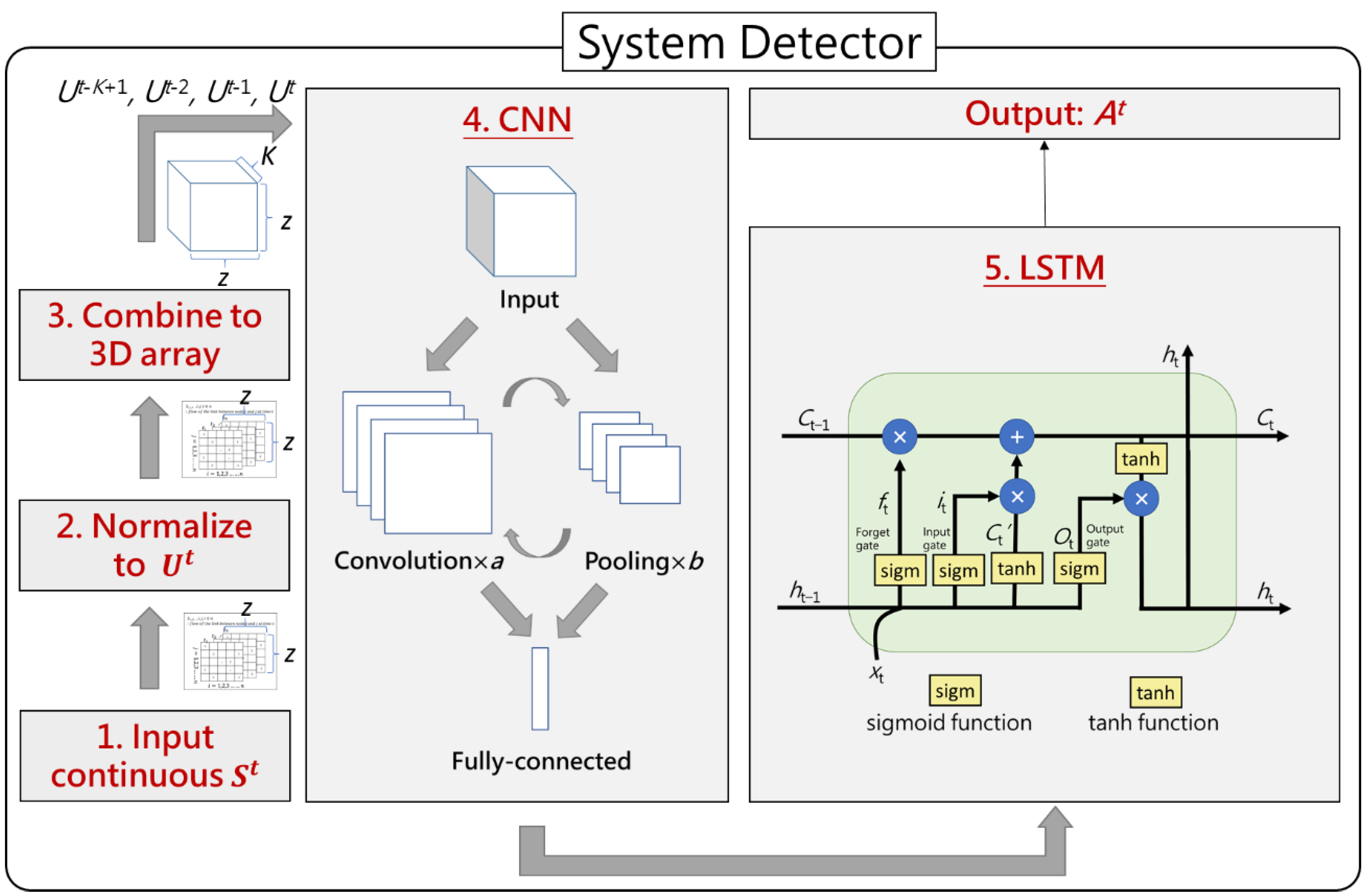











| Notations | Descriptions | Property |
|---|---|---|
| C | Network capacity matrix C, where the ci,j is the link capacity from node i to j | Input |
| TA | Target area | Input |
| M | Number of target links in the topology | Input |
| maxt | Maximum threshold of link utilization at time t | Input |
| mint | Minimum threshold of link utilization at time t | Input |
| K | Number of continuous inputs for deep learning | Input |
| ε | When detection accuracy less than ε for several times, the training ends. Specifically, and and … , the training of System Detector ends | Input |
| D | The accumulated times reaches D when , the training of System Detector ends | Input |
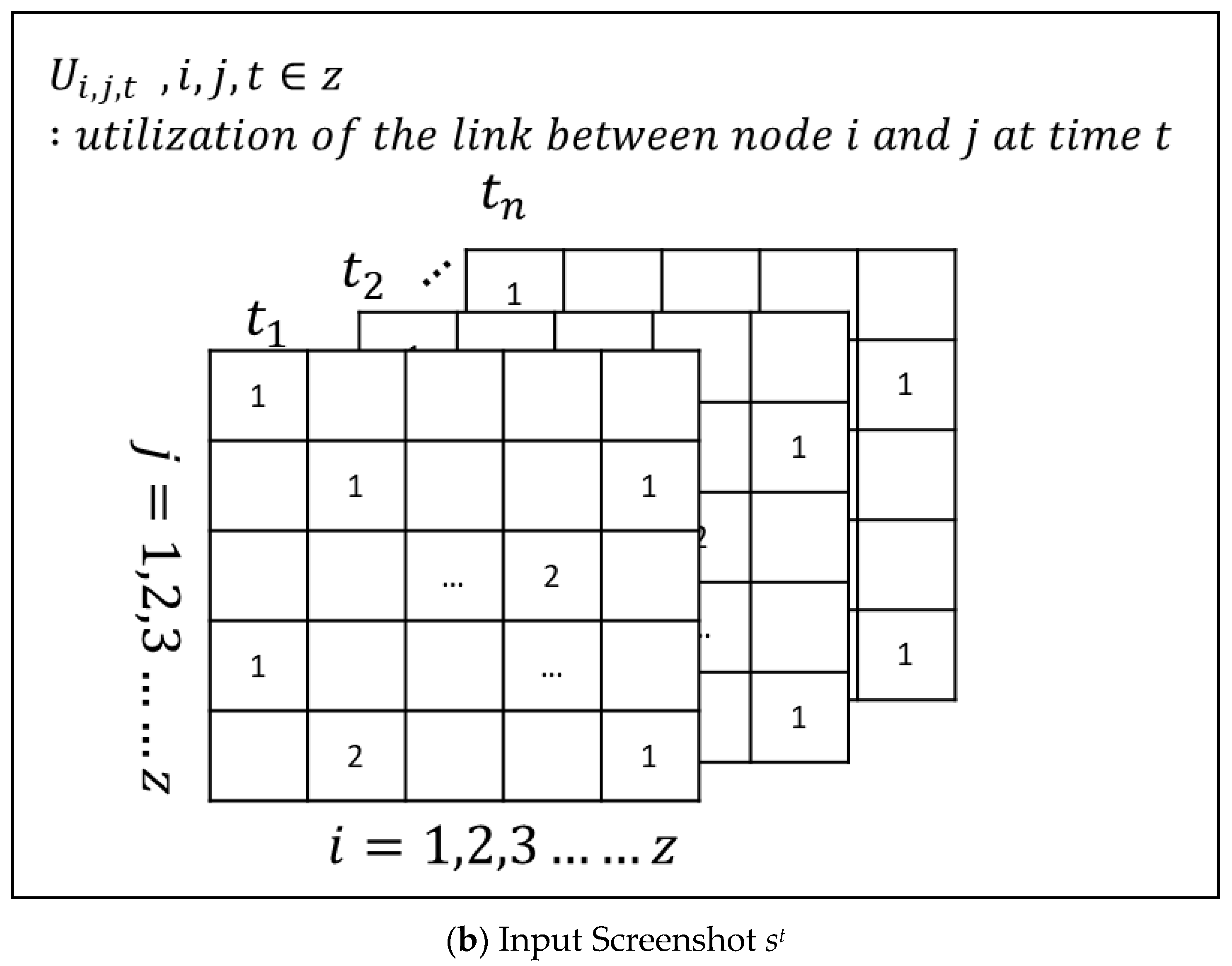
| St | Network traffic matrix St, where the si,j is the amount of traffic from node i to j at time t | Variable |
| Ut | Network utilization matrix Ut, where the Ui,j is the link utilization from node i to j. Specifically, | Variable |
| Bt | The vector of target links under attack or not at time t. Specifically, , where is under attack or not in the i-th target link at time t | Variable |
| Nt | Number of attacked target links at time t. The total number of attacked target links in Bt | Variable |
| PATt | The probability of attacked target links at time t. Specifically, | Variable |
| DTPt | The number of true positive in detection, which means the number of identified attacks and actual attacks | Variable |
| DTNt | The number of true negative in detection, which means the number of identified non-attacks and actual non-attacks | Variable |
| DFPt | The number of false positive in detection, which means the number of identified attacks but actual non-attacks | Variable |
| DFNt | The number of false negative in detection, which means the number of identified non-attacks but actual attacks | Variable |
| DAt | Detection accuracy of system under attack or not, which is the performance of System Detector. Specifically, | Variable |
| MTPt | The number of true positive in mitigation, which means the number of flows should be blocked and actually be blocked | Variable |
| MTNt | The number of true negative in mitigation, which means the number of flows should not be blocked and actually not be blocked | Variable |
| MFPt | The number of false positive in mitigation, which means the number of flows should be blocked but actually not be blocked | Variable |
| MFNt | The number of false negative in mitigation, which means the number of flows should not be blocked but actually be blocked | Variable |
| MAt | Mitigation accuracy of successfully blocking LFA, which is the performance of LFA Mitigator module. Specifically, | Variable |
| NT | Number of training times | Variable |
| ET | The time that deep learning spends in each training time | Variable |
| OTT | The overall training time in deep learning. Specifically, | Variable |
| A2O | The measure of the relationship between DAt and OTT. Specifically, | Variable |
| FRR | False rejection rate of system under attack or not, which means it should be recognized as non-attack, but it is determine as an attack. Specifically, | Variable |
| FAR | False acceptance rate of system under attack or not, which means it should be recognized as an attack, but it is determine as non-attack. Specifically, | Variable |
| Pt | The vector of dropping probability of target links at time t. Specifically, , where is the dropping probability in the i-th target link at time t | Output |
| Parameter | Default Value |
|---|---|
| Number of nodes | 80 |
| The way to decide target links | All links get into TA |
| Link capacity | 60 Mbps |
| Routing method | Shortest path |
| Normal | Default Value |
| Number of traffic | 1–50 |
| Source and destination | Node -> Node |
| Flow traffic | 1–60 Mbps |
| Lasted time | All the time |
| Launch interval | Random |
| Attack | Default Value |
| Number of bots | 10 |
| Source and destination | Bot -> Decoy server |
| Flow traffic | 4 Kbps per flow |
| Launch interval | 3 min |
| Parameter | Default Value |
|---|---|
| Network capacity matrix (C) | Five-hop (75 75) |
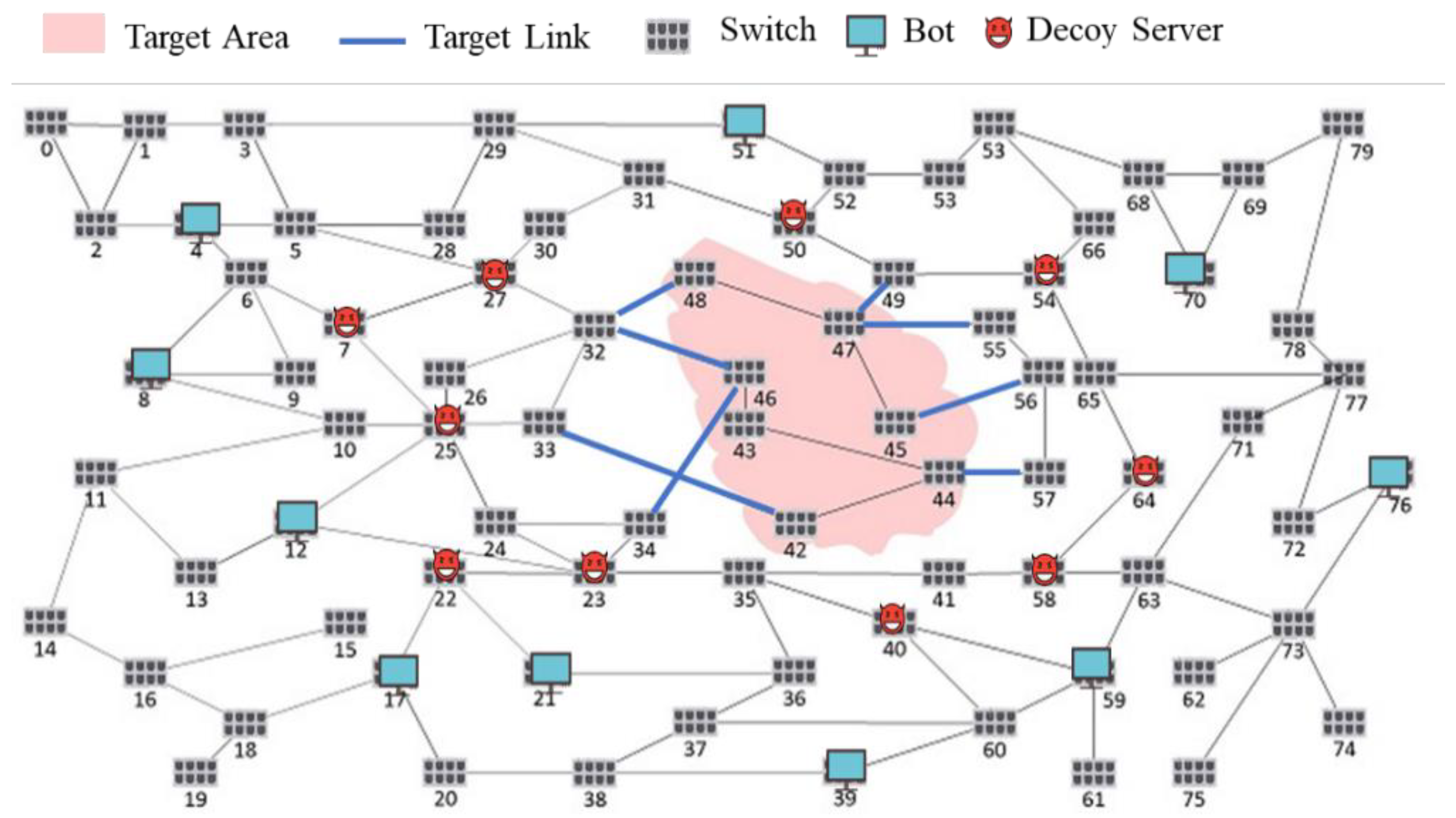
| Target area (TA) | Area in the Figure 8 |
| Number of target links (M) | 6 |
| Maximum thresholds of link utilization at time t (maxt) | 0.6 |
| Minimum thresholds of link utilization at time t (mint) | 0.3 |
| Number of continuous inputs for deep learning (K) | 4 |
| When detection accuracy less than ε for several times, the training ends (ε) | 002 |
| The accumulated times which , the training of System Detector ends (D) | 15 |
| Parameter | Default Value |
|---|---|
| 1st Convolution Layer | 32 filters (shape 8 × 8 × 4), with stride = 4 and ReLU (Rectified Linear Unit) function. |
| 2nd Convolution Layer | 64 filters (shape 4 × 4 × 32), with stride = 2 and ReLU function |
| 3rd Convolution Layer | 64 filters (shape 3 × 3 × 64), with stride = 2 and ReLU function |
| Pooling Layer | Max pool function, with stride = 2 |
| Fully Connected layer | Flatten and transform to one-dimension vector (1 × 512) |
| Convolutions order | Convolution -> Pooling -> Convolution -> Convolution -> Fully Connected |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Y.-H.; Lai, Y.-C.; Jan, P.-T.; Tsai, T.-Y. A Spatiotemporal-Oriented Deep Ensemble Learning Model to Defend Link Flooding Attacks in IoT Network. Sensors 2021, 21, 1027. https://doi.org/10.3390/s21041027
Chen Y-H, Lai Y-C, Jan P-T, Tsai T-Y. A Spatiotemporal-Oriented Deep Ensemble Learning Model to Defend Link Flooding Attacks in IoT Network. Sensors. 2021; 21(4):1027. https://doi.org/10.3390/s21041027
Chicago/Turabian StyleChen, Yen-Hung, Yuan-Cheng Lai, Pi-Tzong Jan, and Ting-Yi Tsai. 2021. "A Spatiotemporal-Oriented Deep Ensemble Learning Model to Defend Link Flooding Attacks in IoT Network" Sensors 21, no. 4: 1027. https://doi.org/10.3390/s21041027
APA StyleChen, Y.-H., Lai, Y.-C., Jan, P.-T., & Tsai, T.-Y. (2021). A Spatiotemporal-Oriented Deep Ensemble Learning Model to Defend Link Flooding Attacks in IoT Network. Sensors, 21(4), 1027. https://doi.org/10.3390/s21041027






