Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices
Abstract
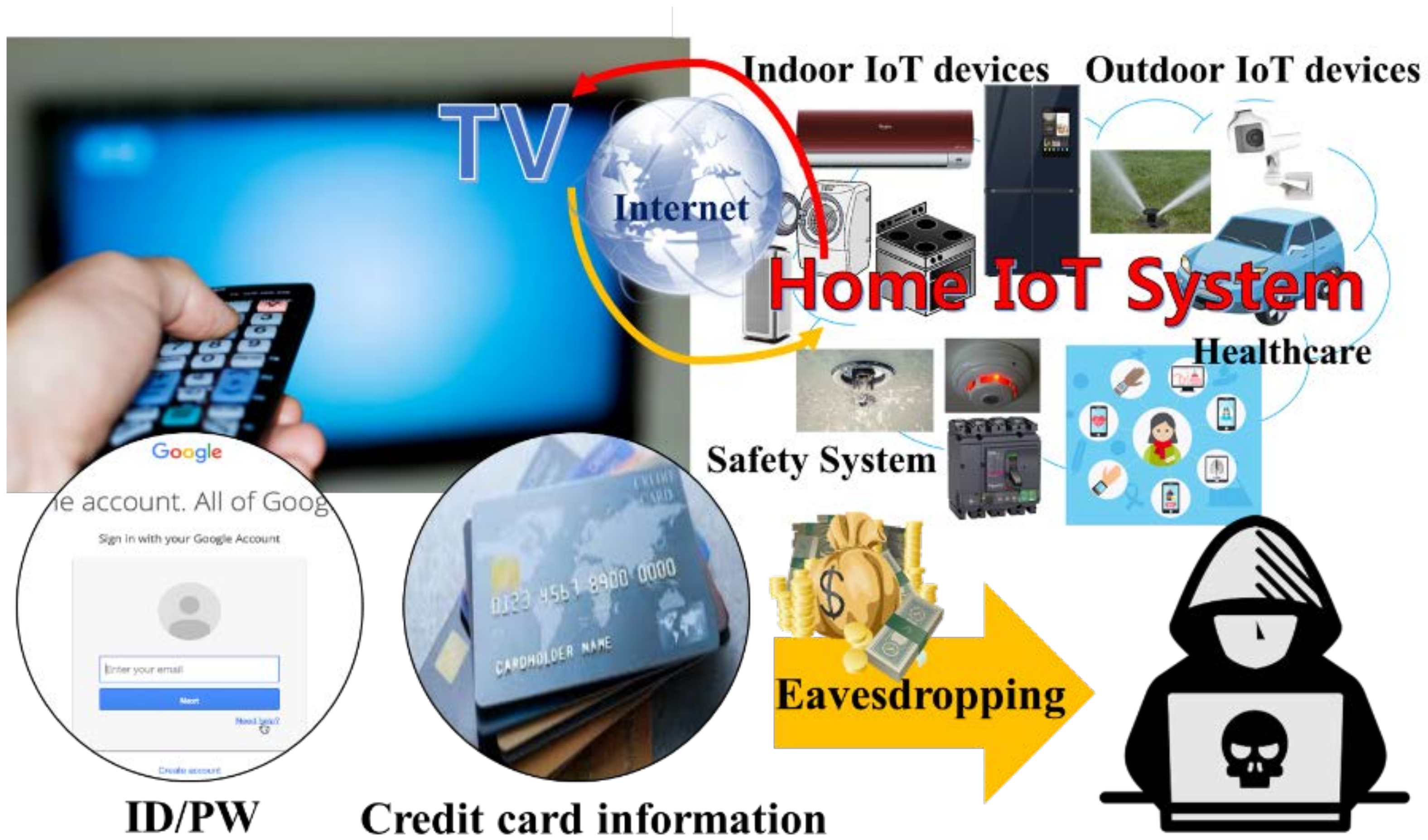
:1. Introduction
2. Related Works
3. Background
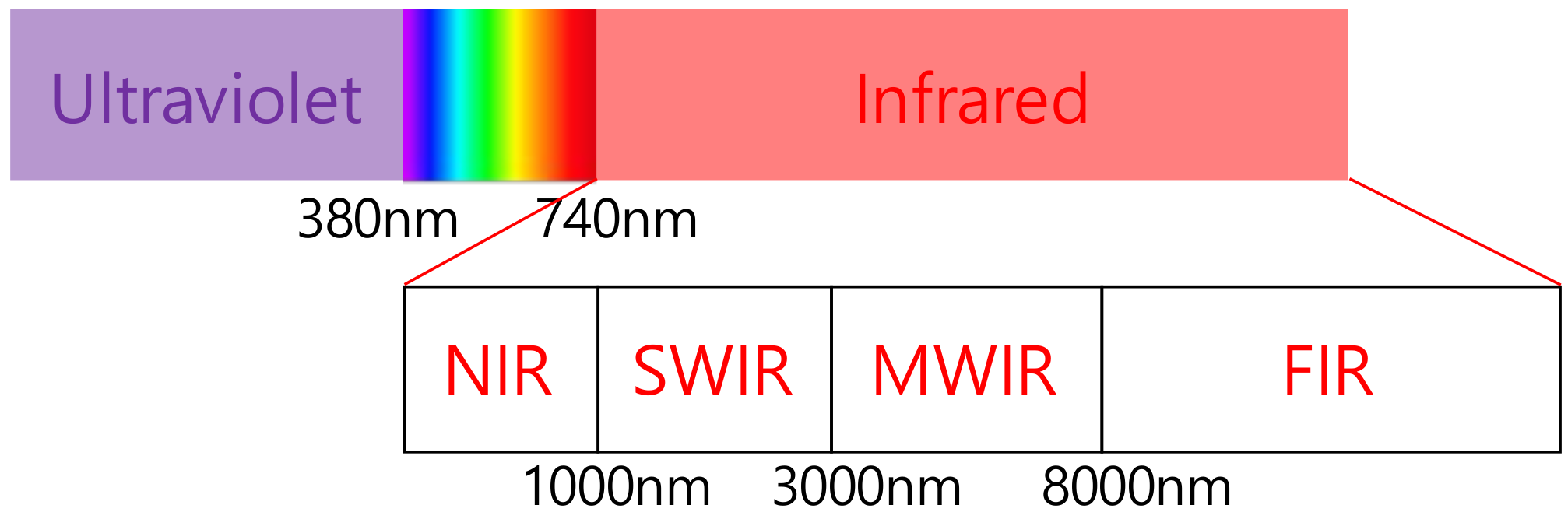
3.1. Infrared Spectrum
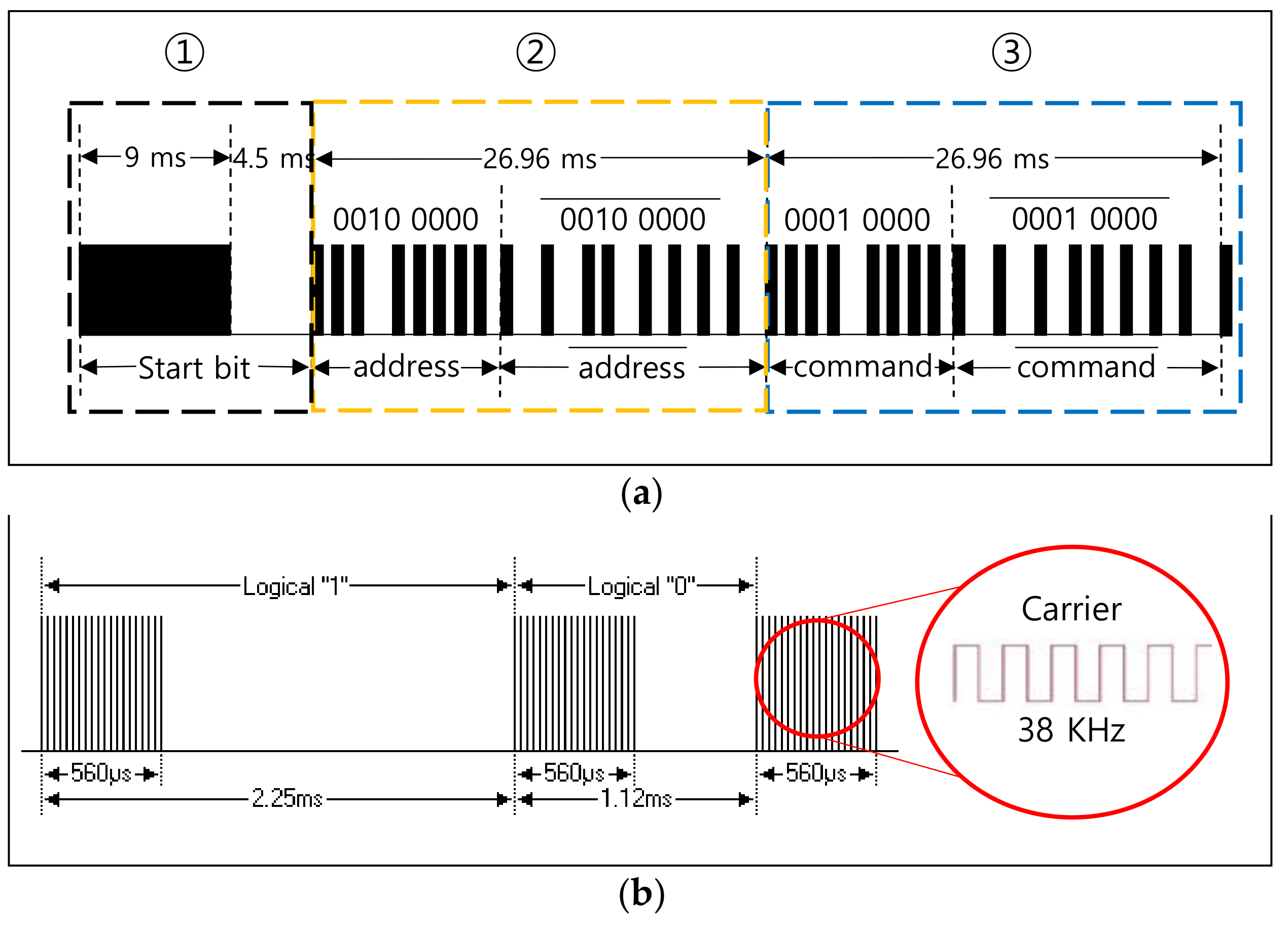
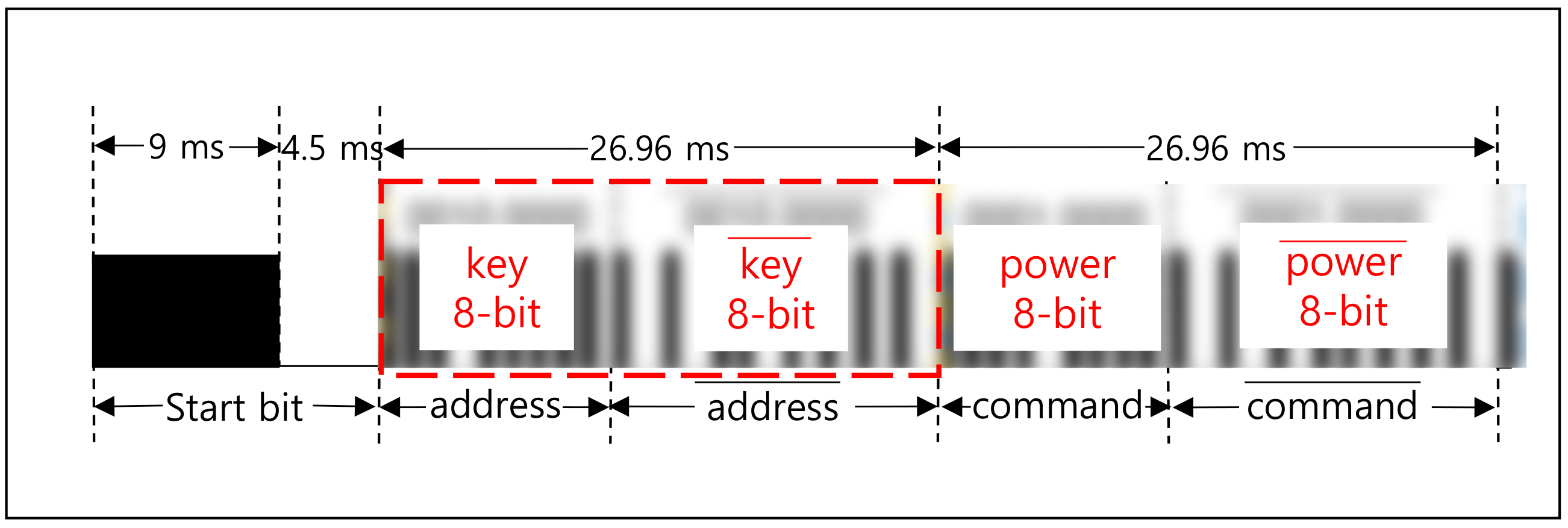
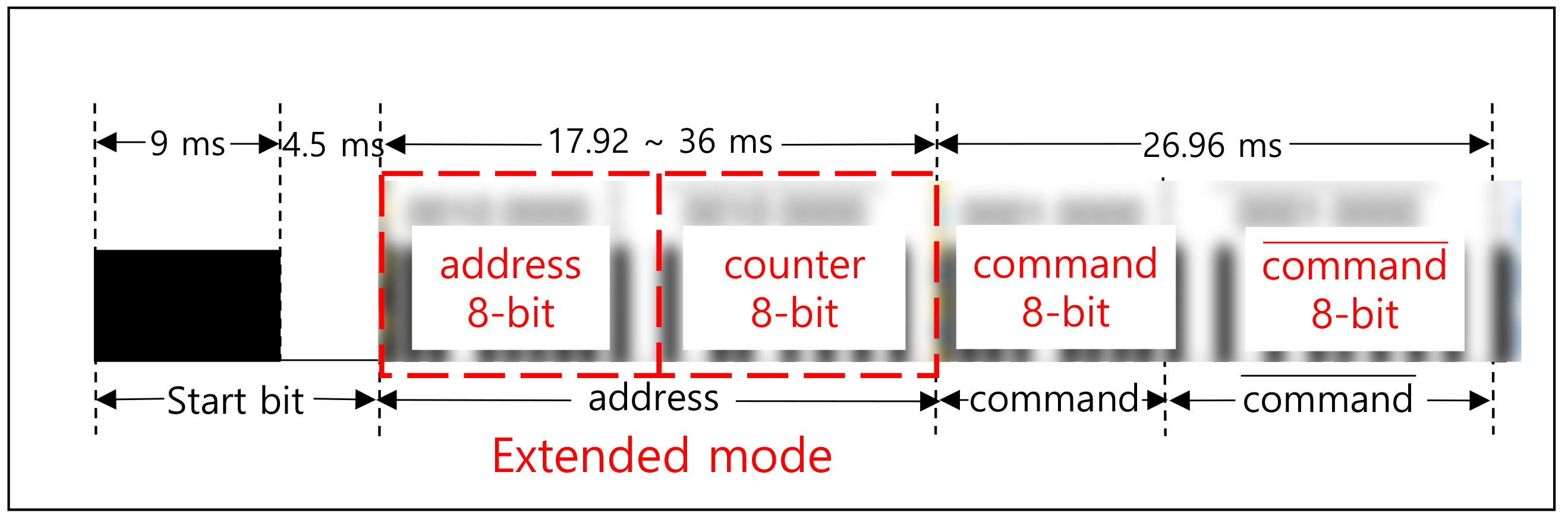
3.2. Communication Protocols Using Infrared
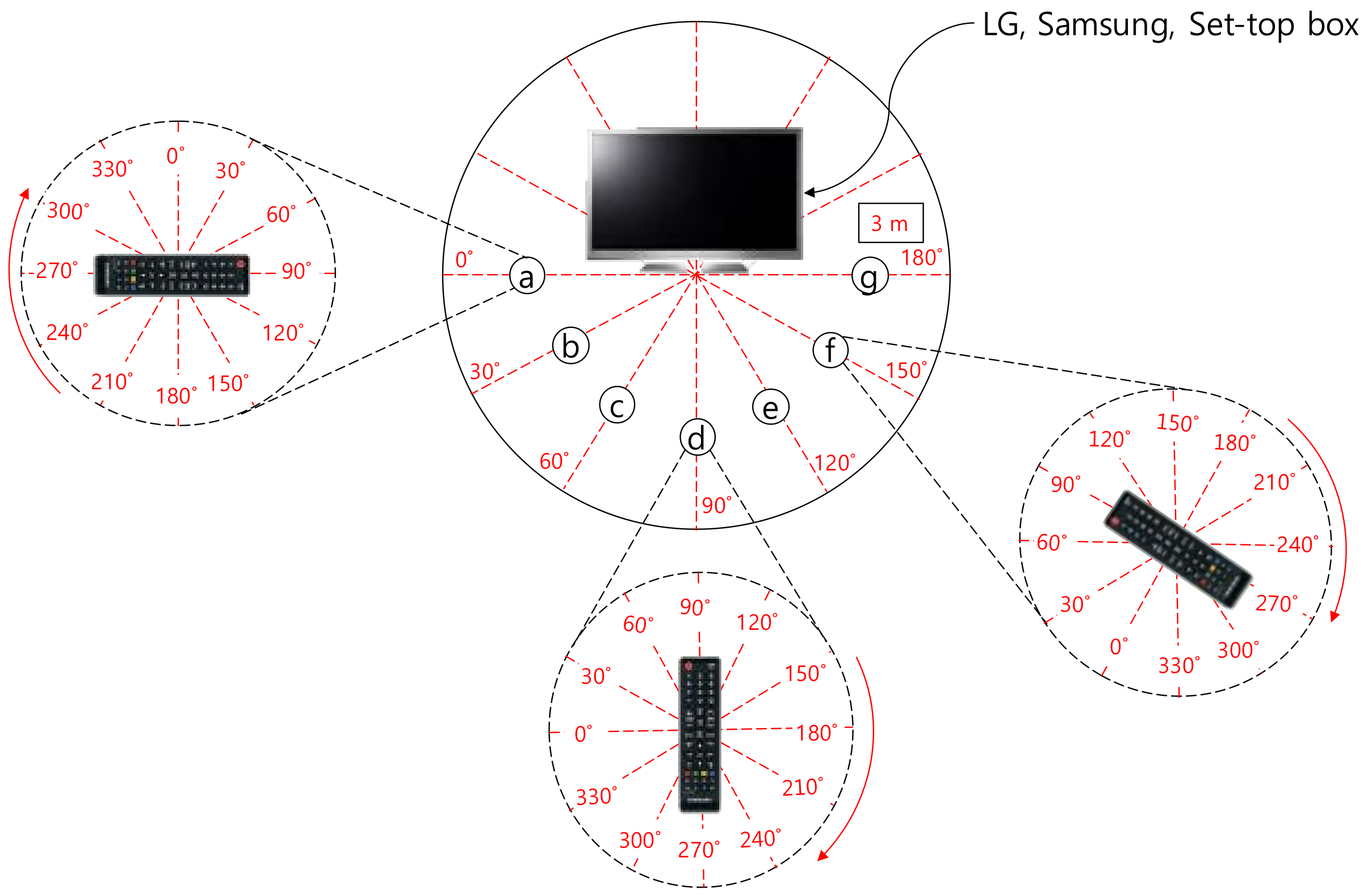
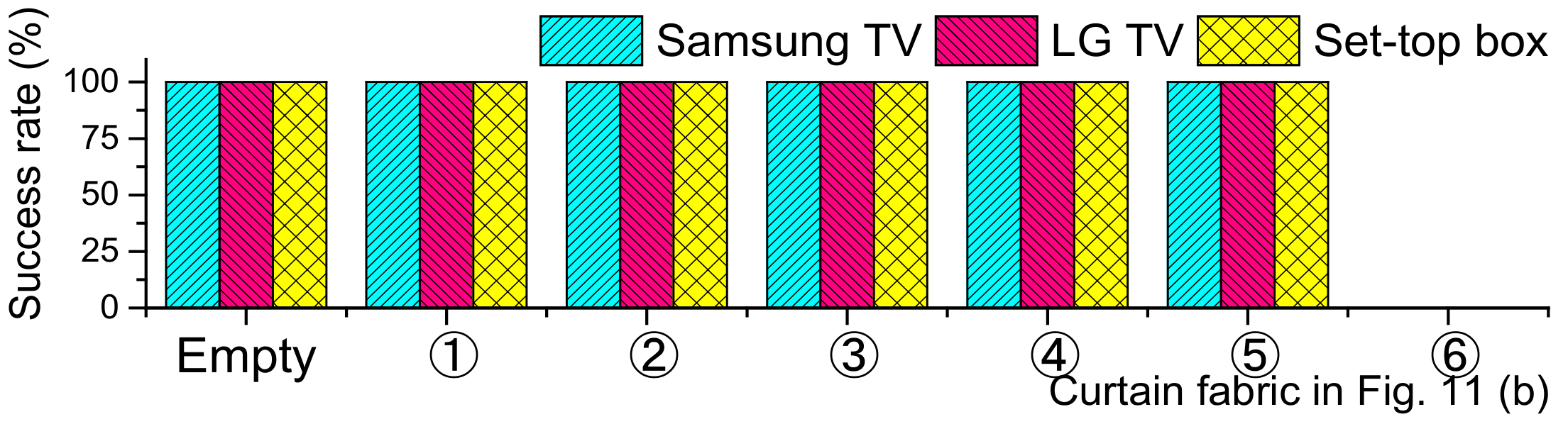
4. IR Reception Sensitivity Experiments
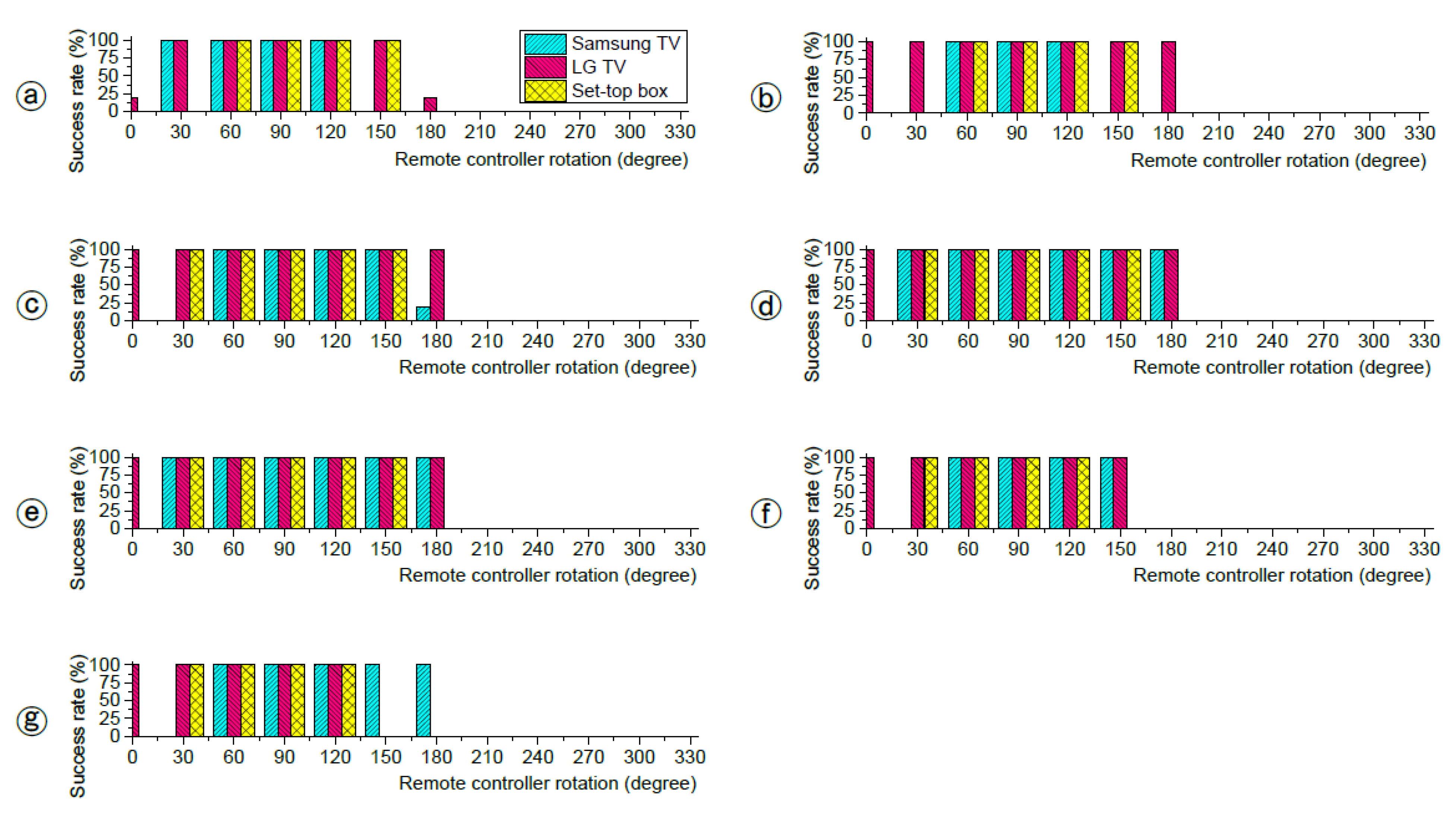
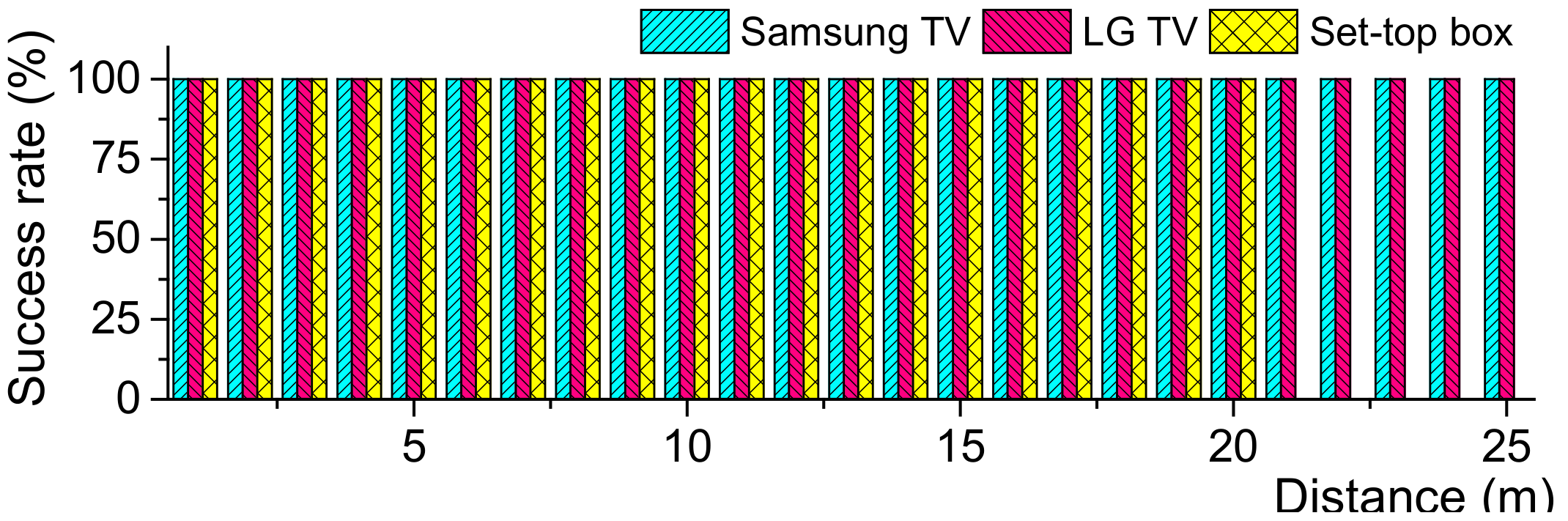
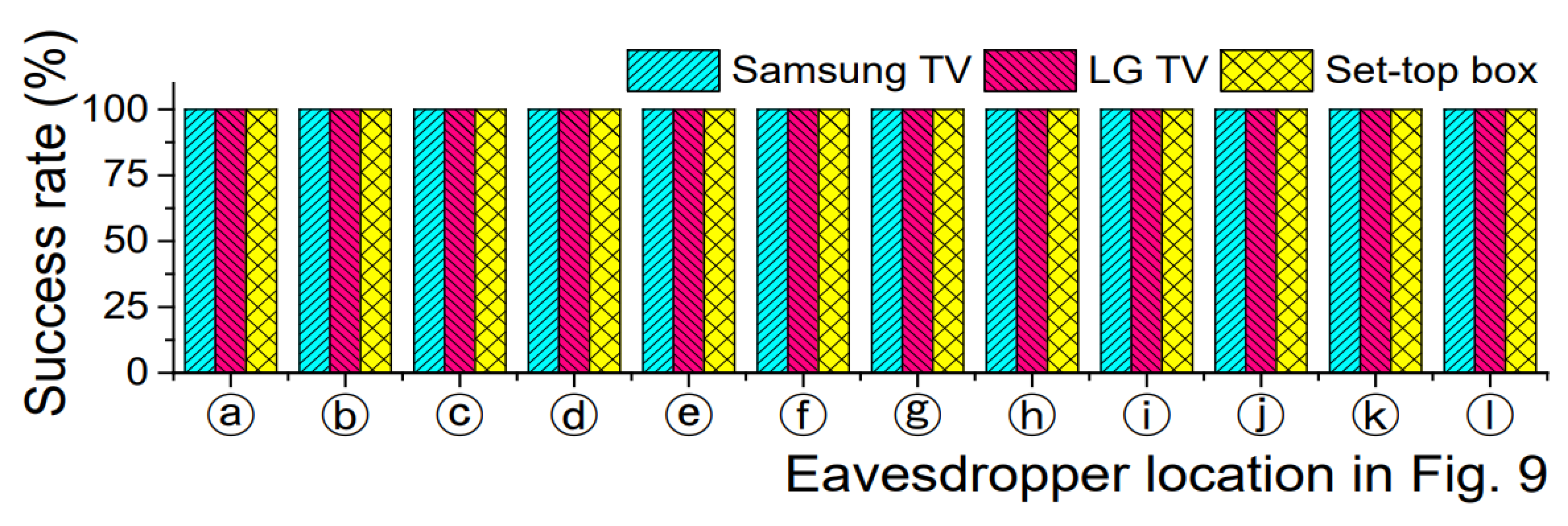
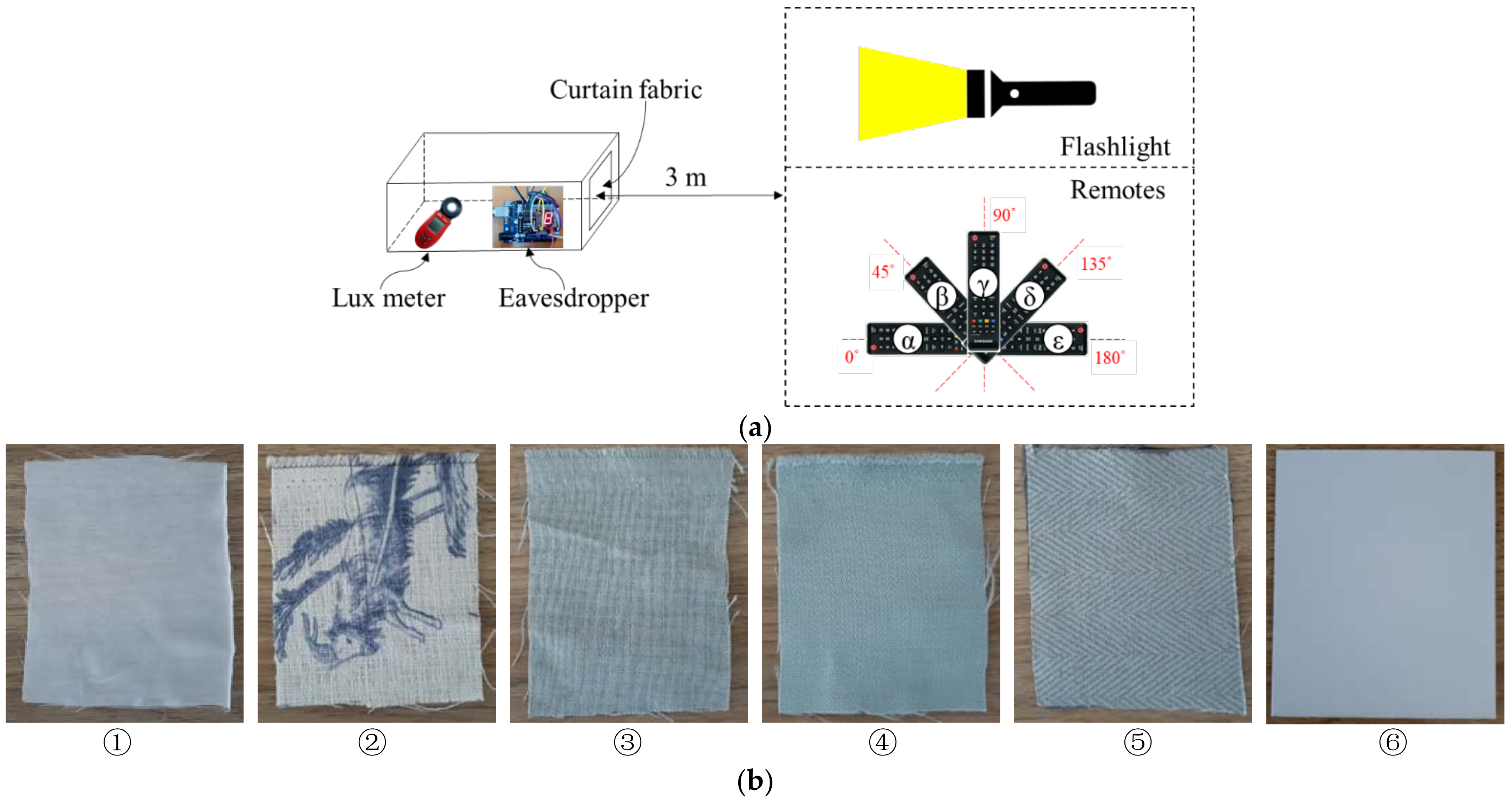
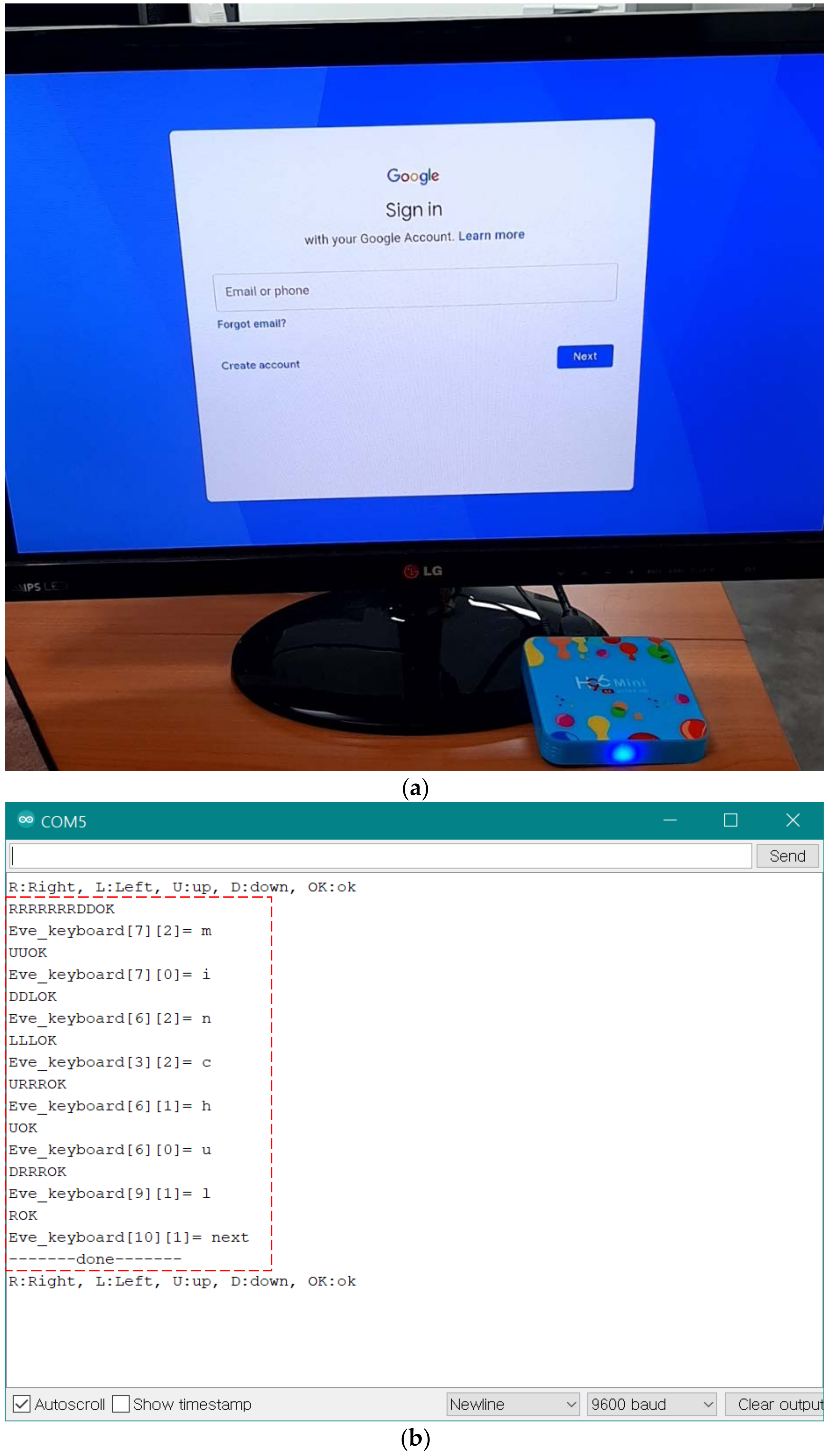
5. Eavesdropping Experiments
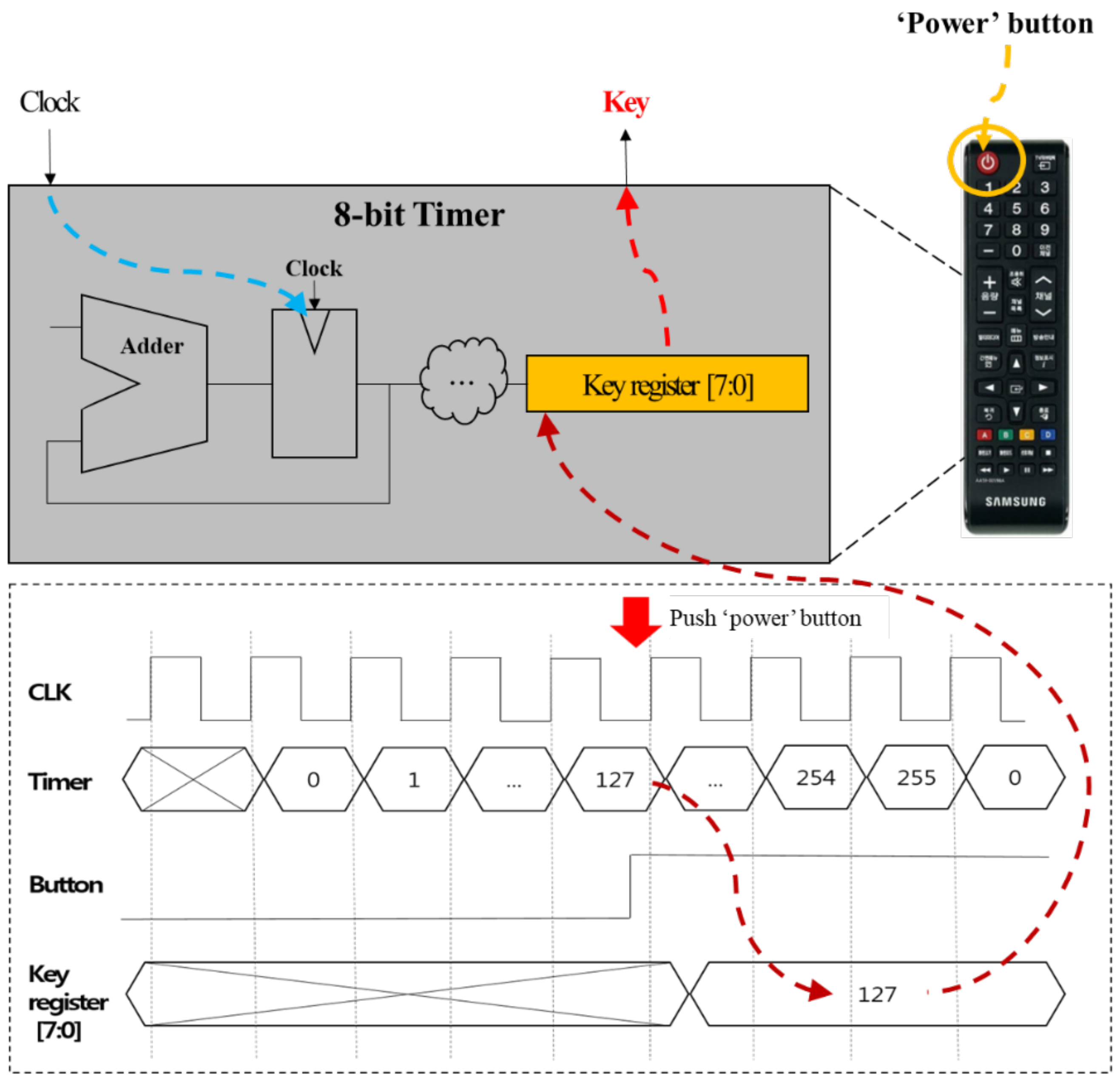
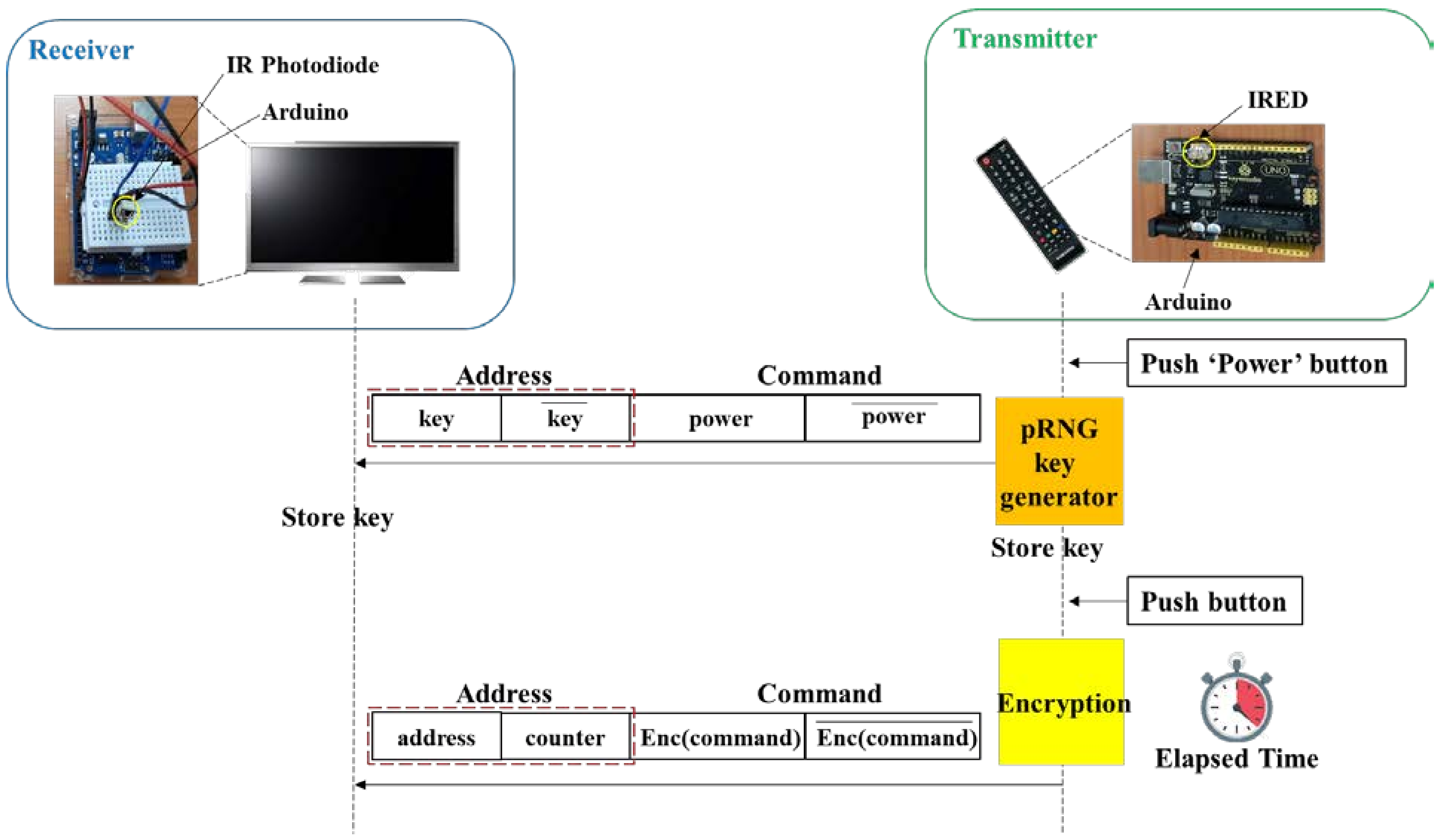
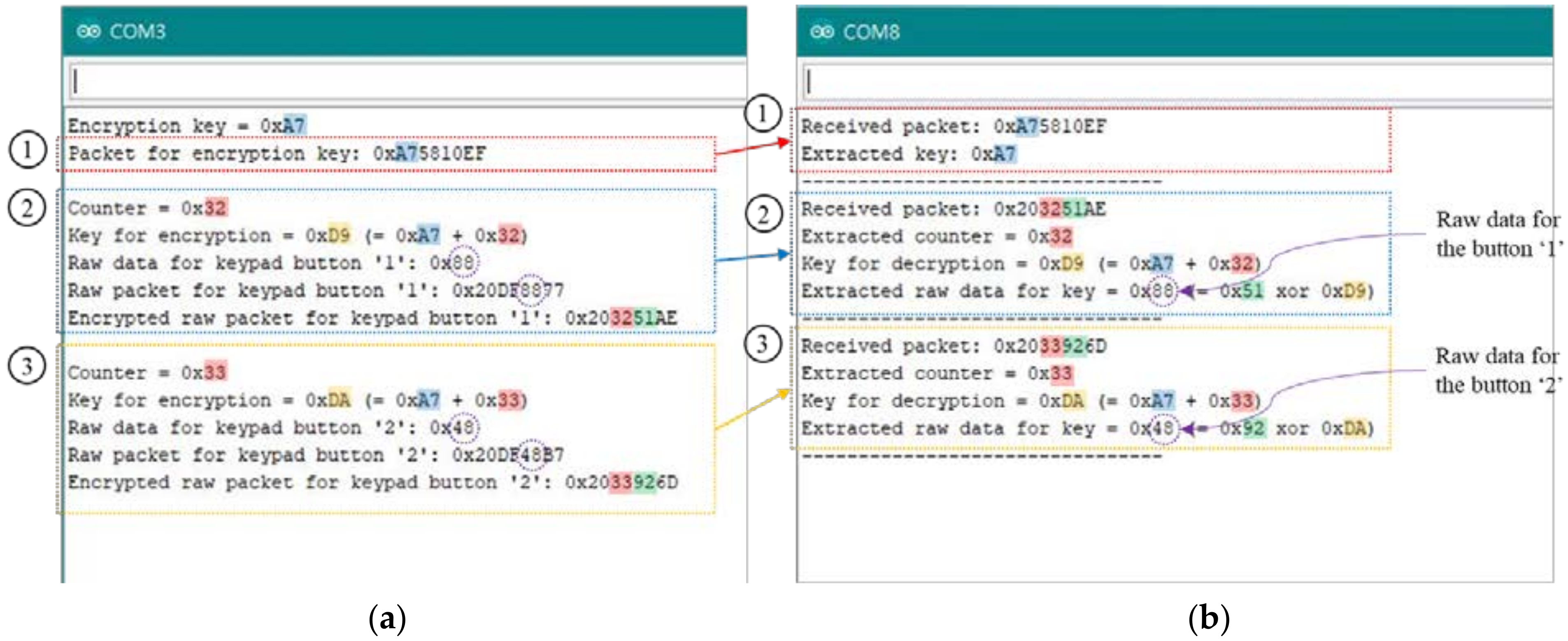
6. Countermeasure
| Code 1. Command encryption using the key and IR packing encoding |
| 1: Procedure |
| 2: |
| 3: key = 8-bit key; |
| 4: addr = 8-bit device_address; |
| 5: cmd = 8-bit command; |
| 6: enc_cmd = key ^ cmd; // encrypted command with XOR |
| 7: |
| 8: // create a 32-bit frame data according to NEC protocol |
| 9: 16-bit_ext_addr = (addr << 8) + ~addr; |
| 10: 16-bit_ext_cmd = (enc_cmd << 8) + ~enc_cmd; |
| 11: 32-bit_addr_cmd = (16-bit_ext_addr << 16) + 16-bit_ext_cmd; |
| 12: |
| 13: // Send the 32-bit frame via IR |
| 14: IR_send (32-bit_addr_cmd) |
| 15: |
| 16: End procedure |
| Code 2. Command encryption using the key and counter |
| 1: Procedure |
| 2: |
| 3: // random based on free-running timer |
| 4: counter = 8-bit random_number; |
| 5: key = 8-bit key; |
| 6: addr = 8-bit device_address; |
| 7: cmd = 8-bit command; |
| 8: key = key + counter; |
| 9: enc_cmd = key ^ cmd; // encrypted command with XOR |
| 10: |
| 11: // create a 32-bit frame data according to NEC protocol |
| 12: 16-bit_ext_addr = (addr << 8) + counter; |
| 13: 16-bit_ext_cmd = (enc_cmd << 8) + ~enc_cmd; |
| 14: 32-bit_addr_cmd = (16-bit_ext_addr << 16) + 16-bit_ext_cmd; |
| 15: |
| 16: // Send the 32-bit frame via IR |
| 17: IR_send (32-bit_addr_cmd) |
| 18: |
| 19: counter++; |
| 20: End procedure |
7. Conclusions
Supplementary Materials
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sharma, N.; Mangla, M.; Mohanty, S.N.; Satpathy, S. In A Gesture based Remote Control for Home Appliances. In Proceedings of the 2021 8th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 17–19 March 2021. [Google Scholar]
- Muthiah, M.; Natesh, A.V. In Low cost smart glove for universal control of IR device. In Proceedings of the 2016 IEEE International Symposium on Technology and Society (ISTAS), Kollam, India, 20–22 October 2016. [Google Scholar]
- Verdadero, M.S.; Martinez-Ojeda, C.O.; Cruz, J.C.D. In Hand Gesture Recognition System as an Alternative Interface for Remote Controlled Home Appliances. In Proceedings of the 2018 IEEE 10th International Conference on Humanoid, Nanotechnology, Information Technology, Communication and Control, Environment and Management (HNICEM), Baguio, Philippines, 29 November–2 December 2018. [Google Scholar]
- Kirsh, I.; Ruser, H. In Phone-pointing remote app: Using smartphones as pointers in gesture-based IoT remote controls. In Proceedings of the International Conference on Human-Computer Interaction, Virtual Event, 2021. [Google Scholar]
- Tonmoy, A.I.; Hossain, M.F.; Hasan, S.Z. In Voice, Gesture and IR Remote Controlled Alphabet Learning Display for Kids Based on 16× 16 LED Dot Matrix Display. In Proceedings of the 2019 International Conference on Electrical, Computer and Communication Engineering (ECCE), Cox’s Bazar, Bangladesh, 7–9 February 2019. [Google Scholar]
- Alghamdi, A.S. In Design a Universal Remote Controlled Thermostat Based on FPGA. In Proceedings of the 2019 6th International Conference on Control, Decision and Information Technologies (CoDIT), Paris, France, 23–26 April 2019. [Google Scholar]
- Ismaeel, A.G.; Kamal, M.Q. In Worldwide auto-mobi: Arduino IoT home automation system for IR devices. In Proceedings of the 2017 International Conference on Current Research in Computer Science and Information Technology (ICCIT), Sulaymaniyah, Iraq, 26–27 April 2017. [Google Scholar]
- Adiono, T.; Anindya, S.F.; Fuada, S.; Fathany, M.Y. In Developing of General IrDa Remote to Wirelessly Control IR-based Home Appliances. In Proceedings of the 2018 IEEE 7th Global Conference on Consumer Electronics (GCCE), Nara, Japan, 9–12 October 2018. [Google Scholar]
- Salichs, J.; Castro-Gonzalez, A.; Salichs, M.A. In Infrared remote control with a social robot. In Proceedings of the FIRA RoboWorld Congress, Incheon, Korea, 16–20 August 2009. [Google Scholar]
- Kubota, N.; Wagatsuma, Y.; Ozawa, S. In Intelligent technologies for edutainment using multiple robots. In Proceedings of the FIRA RoboWorld Congress, Incheon, Korea, 16–20 August 2009. [Google Scholar]
- Kahn, J.M.; Barry, J.R. Wireless infrared communications. Proc. IEEE 1997, 85, 265–298. [Google Scholar] [CrossRef] [Green Version]
- Barry, J.R. Wireless Infrared Communications; Springer Science & Business Media: New York, NY, USA, 2012; Volume 280. [Google Scholar]
- Koonen, T.; Mekonnen, K.; Cao, Z.; Huijskens, F.; Pham, N.Q.; Tangdiongga, E. Ultra-high-capacity wireless communication by means of steered narrow optical beams. Philos. Trans. R. Soc. A 2020, 378, 20190192. [Google Scholar] [CrossRef] [Green Version]
- Wolfe, J.; Morais, M.; Neumann, S.; Schafer, E.; Mülder, H.E.; Wells, N.; John, A.; Hudson, M. Evaluation of speech recognition with personal FM and classroom audio distribution systems. J. Educ. Audiol. 2013, 19, 65–79. [Google Scholar]
- Ling, Z.; Gao, C.; Sano, C.; Toe, C.; Li, Z.; Fu, X. STIR: A Smart and Trustworthy IoT System Interconnecting Legacy IR Devices. IEEE Internet Things J. 2020, 7, 3958–3967. [Google Scholar] [CrossRef]
- Alam, I.; Khusro, S.; Naeem, M. In A review of smart TV: Past, present, and future. In Proceedings of the 2017 International Conference on Open Source Systems & Technologies (ICOSST), Lahore, Pakistan, 18–20 December 2017. [Google Scholar]
- Dhatchayeny, D.R.; Arya, S.; Chung, Y.H. Infrared-Based Multiple-Patient Monitoring in Indoor Optical Wireless Healthcare Systems. IEEE Sens. J. 2019, 19, 5594–5599. [Google Scholar] [CrossRef]
- IEEE. ISO/IEEE International Standard Health Informatics—Point-of-Care Medical Device Communication—Transport Profile—Infrared; ISO/IEEE 11073-30300:2004(E); IEEE: Piscataway, NJ, USA, 2004; pp. 1–73. [Google Scholar] [CrossRef]
- Połap, D. Analysis of skin marks through the use of intelligent things. IEEE Access 2019, 7, 149355–149363. [Google Scholar] [CrossRef]
- Shieh, W.-Y.; Wang, T.-H.; Chou, Y.-H.; Huang, C.-C. Design of the radiation pattern of infrared short-range communication systems for electronic-toll-collection applications. IEEE Trans. Intell. Transp. Syst. 2008, 9, 548–558. [Google Scholar] [CrossRef]
- Al-Mutawa, R.F.; Eassa, F.A. A smart home system based on internet of things. arXiv 2020, arXiv:2009.05328. [Google Scholar] [CrossRef]
- Abu-Tair, M.; Djahel, S.; Perry, P.; Scotney, B.; Zia, U.; Carracedo, J.M.; Sajjad, A. Towards Secure and Privacy-Preserving IoT Enabled Smart Home: Architecture and Experimental Study. Sensors 2020, 20, 6131. [Google Scholar] [CrossRef] [PubMed]
- Ferrara, P.; Mandal, A.K.; Cortesi, A.; Spoto, F. Static analysis for discovering IoT vulnerabilities. Int. J. Softw. Tools Technol. Transf. 2021, 23, 71–88. [Google Scholar] [CrossRef]
- Lei, X.; Tu, G.-H.; Li, C.-Y.; Xie, T.; Zhang, M. In SecWIR: Securing Smart Home IoT Communications via Wifi Routers with Embedded Intelligence. In Proceedings of the 18th International Conference on Mobile Systems, Applications, and Services, Toronto, ON, Canada, 15–19 June 2020. [Google Scholar]
- Zhou, Z.; Zhang, W.; Li, S.; Yu, N. Potential risk of IoT device supporting IR remote control. Comput. Netw. 2019, 148, 307–317. [Google Scholar] [CrossRef] [Green Version]
- Gotschlich, M. Remote Controls—Radio Frequency or Infrared. Whitepaper Infineon Technol. AG. 2010. Available online: https://www.infineon.com/dgdl/RF2ir%20WhitePaper%20V1.0.pdf?fileId=db3a30432b57a660012b5c16272c2e81 (accessed on 8 December 2021).
- Biran, A. In WiFi OFDM and Bluetooth signal collision analysis. In Proceedings of the 2011 IEEE International Conference on Microwaves, Communications, Antennas and Electronic Systems (COMCAS 2011), Hilton Hotel Tel-Aviv, Israel, 7–9 November 2011. [Google Scholar]
- Arduino Library IRremote. Available online: https://www.arduino.cc/reference/en/libraries/irremote/ (accessed on 8 December 2021).
- Hamza, A.S.; Deogun, J.S.; Alexander, D.R. Wireless communication in data centers: A survey. IEEE Commun. Surv. Tutor. 2016, 18, 1572–1595. [Google Scholar] [CrossRef] [Green Version]
- Akhloufi, M.A.; Bendada, A. Fusion of active and passive infrared images for face recognition, Thermosense: Thermal Infrared Applications XXXV. Int. Soc. Opt. Photonics 2013, 8705, 87050B-1–87050B-10. [Google Scholar]
- Vishay Intertechnology Co. High Power Infrared Emitting Diode, TSAL 6100 Datasheet. 2019. Available online: https://www.vishay.com/docs/81009/tsal6100.pdf (accessed on 8 December 2021).
- Kodenshi Co. KSM-60 LM, KSM-70 LM Optic Receiver Modules Datasheet. Available online: http://product.ic114.com/PDF/K/KSM60WLM.pdf (accessed on 8 December 2021).
- Chowdhury, M.S.; Kavehrad, M.; Zhang, W. Cable television transmission over a 1550-nm infrared indoor optical wireless link. Opt. Eng. 2013, 52, 100503. [Google Scholar] [CrossRef]
- Tsai, W.-C.; Zhu, S.-X.; Huang, N.-T.; Chiang, M.-L. An Implementation of Hardware-Accelerated Serial Interface of IoT Gateway for Enabling Machine-Type Communication: A Case Study of Networking IR Controllable Home Appliances. J. Comput. Netw. Commun. 2019, 2019, 13. [Google Scholar] [CrossRef] [Green Version]
- NEC Protocol; SB-Projects. New York, NY, USA. 2017. Available online: https://www.sbprojects.net/knowledge/ir/nec.php (accessed on 8 December 2021).
- Arduino. Available online: https://www.arduino.cc/ (accessed on 8 December 2021).
- ETACHIPS Co. ADAM24PXX 4-bit Single Chip Microcomputers Datasheet. Available online: https://datasheetspdf.com/datasheet/search.php?sWord=ADAM24P20G (accessed on 8 December 2021).
- Philips Semiconductors Co. PCA84C922, PCA84C923 Microcontrollers for Universal Infrared Remote Transmitter Applications Datasheet. 1997. Available online: https://datasheetspdf.com/datasheet/PCA84C922.html (accessed on 8 December 2021).
- Maxim Intergrated Products Inc. MAXQ617 Infrared Remote Control System-on-Chip. 2013. Available online: https://www.maximintegrated.com/en/products/microcontrollers/MAXQ617.html (accessed on 8 December 2021).
- Lipmaa, H.; Rogaway, P.; Wagner, D. Comments to NIST Concerning AES-Modes of Operations: CTR-Mode Encryption. Available online: https://www.researchgate.net/profile/Helger-Lipmaa/publication/2817314_Comments_to_NIST_concerning_AES-modes_of_operations_CTR-mode_encryption/links/0912f51368902f1a87000000/Comments-to-NIST-concerning-AES-modes-of-operations-CTR-mode-encryption.pdf (accessed on 8 December 2021).
- Miliani, L. ”pRNG”. 2016. Available online: https://github.com/leomil72/pRNG (accessed on 8 December 2021).




| IR | RF | |
|---|---|---|
| Frequency | 870 nm and 930–950 nm | 2.4 GHz Worldwide ISM-band |
| Carrier | 38 KHz | 315, 434, or 868 MHz |
| Coverage range | Up to 10 m | Up to 50 m |
| Data rate | 10~1 K bit/s | 100 K bit/s |
| Regulation | No limitations | Regulated in worldwide standards (ETSI, FCC, etc.) |
| Hardware cost | <$1 | >$5 |
| Objects or wall transmittance | Relatively little | High |
| Interference factor | Ambient light | Other communications (2.4 Ghz Wi-Fi, Bluetooth, etc.) |
| Protocol | Keypad Inputs | Raw_Data | Display on 7-Segment | |
|---|---|---|---|---|
| Samsung TV | Samsung | On/Off | 0xE0E040BF (32 bits) | 1 |
| Keypad 1 | 0xE0E020DF (32 bits) | 2 | ||
| LG TV | NEC | On/Off | 0x20DF10EF (32 bits) | 3 |
| Keypad 1 | 0x20DF8877 (32 bits) | 4 | ||
| Set-top box | NEC | On/Off | 0x01FE817E (32 bits) | 5 |
| Keypad OK | 0x01FEC837 (32 bits) | 6 |
| Fabric | Empty | ① | ② | ③ | ④ | ⑤⑥ | |
|---|---|---|---|---|---|---|---|
| Lux | 9800 | 2000 | 860 | 480 | 94 | 0 | |
| Light transmittance | 100% | 20.41% | 8.78% | 4.90% | 0.96% | 0% | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, M.; Suh, T. Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices. Sensors 2021, 21, 8207. https://doi.org/10.3390/s21248207
Kim M, Suh T. Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices. Sensors. 2021; 21(24):8207. https://doi.org/10.3390/s21248207
Chicago/Turabian StyleKim, Minchul, and Taeweon Suh. 2021. "Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices" Sensors 21, no. 24: 8207. https://doi.org/10.3390/s21248207
APA StyleKim, M., & Suh, T. (2021). Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices. Sensors, 21(24), 8207. https://doi.org/10.3390/s21248207






