Biometrics for Internet-of-Things Security: A Review
Abstract
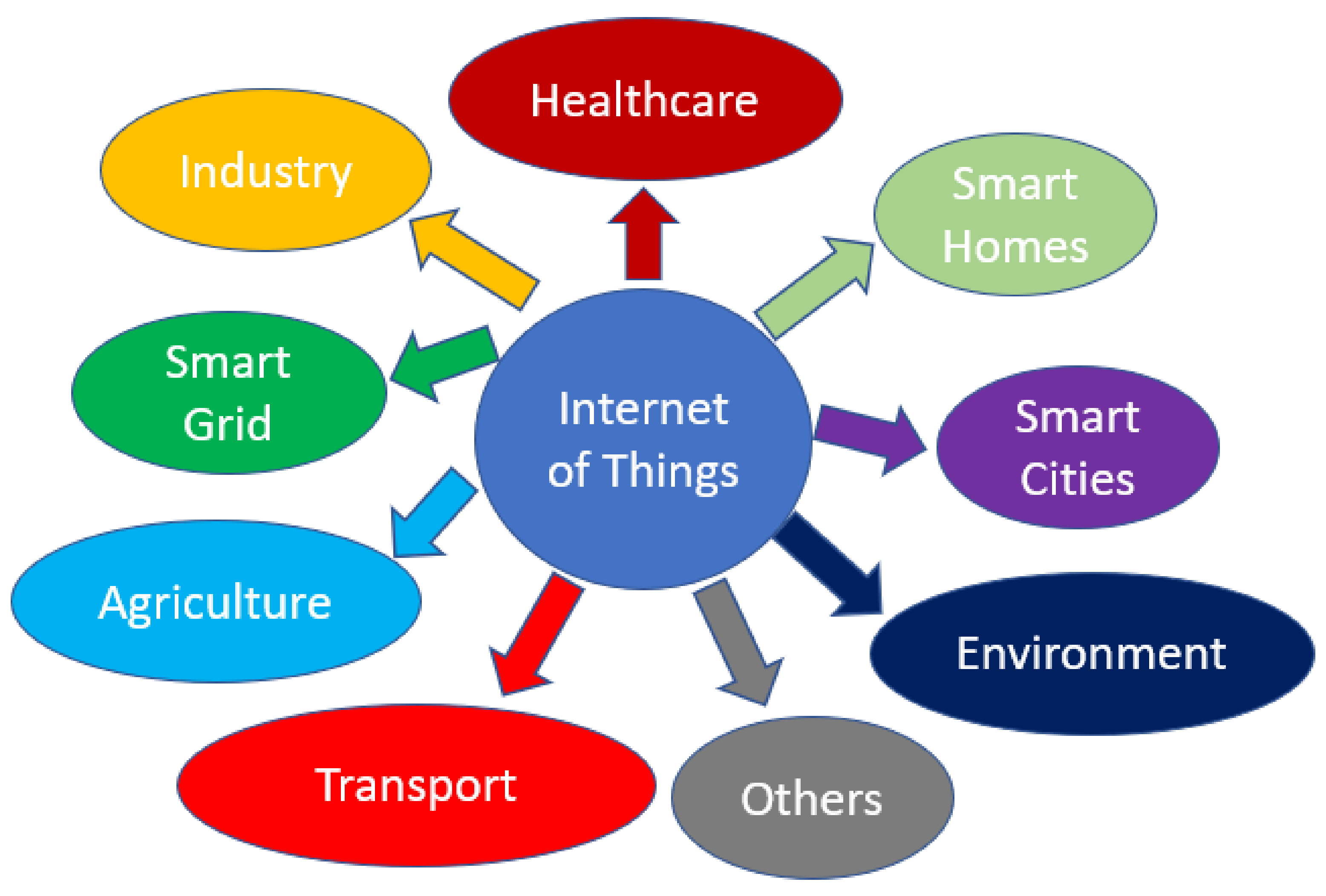
:1. Introduction
- To the best of our knowledge, there has been little survey which adequately considers biometric authentication and encryption simultaneously for the IoT environment prior to this review paper. This paper gives a comprehensive review of the contemporary biometric-based systems that provide authentication and encryption for the IoT;
- Regarding authentication, we classify and analyze IoT-related biometric authentication systems based on different biometric traits and the number of biometric traits used in the biometric systems. Following this, we investigate biometric-cryptographic systems that integrate biometrics with cryptography for data encryption. The study of these systems sheds light on the latest development in handling IoT-related security vulnerabilities or possible attacks targeting the IoT;
- Challenges brought by the deployment of biometric systems in the IoT are identified and potential solutions are discussed and highlighted;
- Several insights into future research directions concerning biometrics for IoT security are provided in this paper.
2. Security Challenges and Vulnerabilities of the IoT
- (i)
- The weakest parts of a system. As the number of IoT devices is rapidly growing, the resource limitations of IoT devices lead to the use of lightweight security algorithms and the security of certain devices is likely neglected. These devices become the weakest parts of an IoT network;
- (ii)
- Low control over updates. Often, users have a shallow understanding of the internal mechanisms of IoT devices and little knowledge about how to handle online updates, opening up opportunities for security attacks by various malware;
- (iii)
- Data privacy. Smart sensors in IoT networks collect large amounts of data from different sources, and a certain amount of data may be related to users’ personal and sensitive information. The leakage of these data endangers the privacy of users.
2.1. Vulnerabilities of the Perception Layer
2.2. Vulnerabilities of the Network Layer
2.3. Vulnerabilities of the Application Layer
3. Biometrics Overview
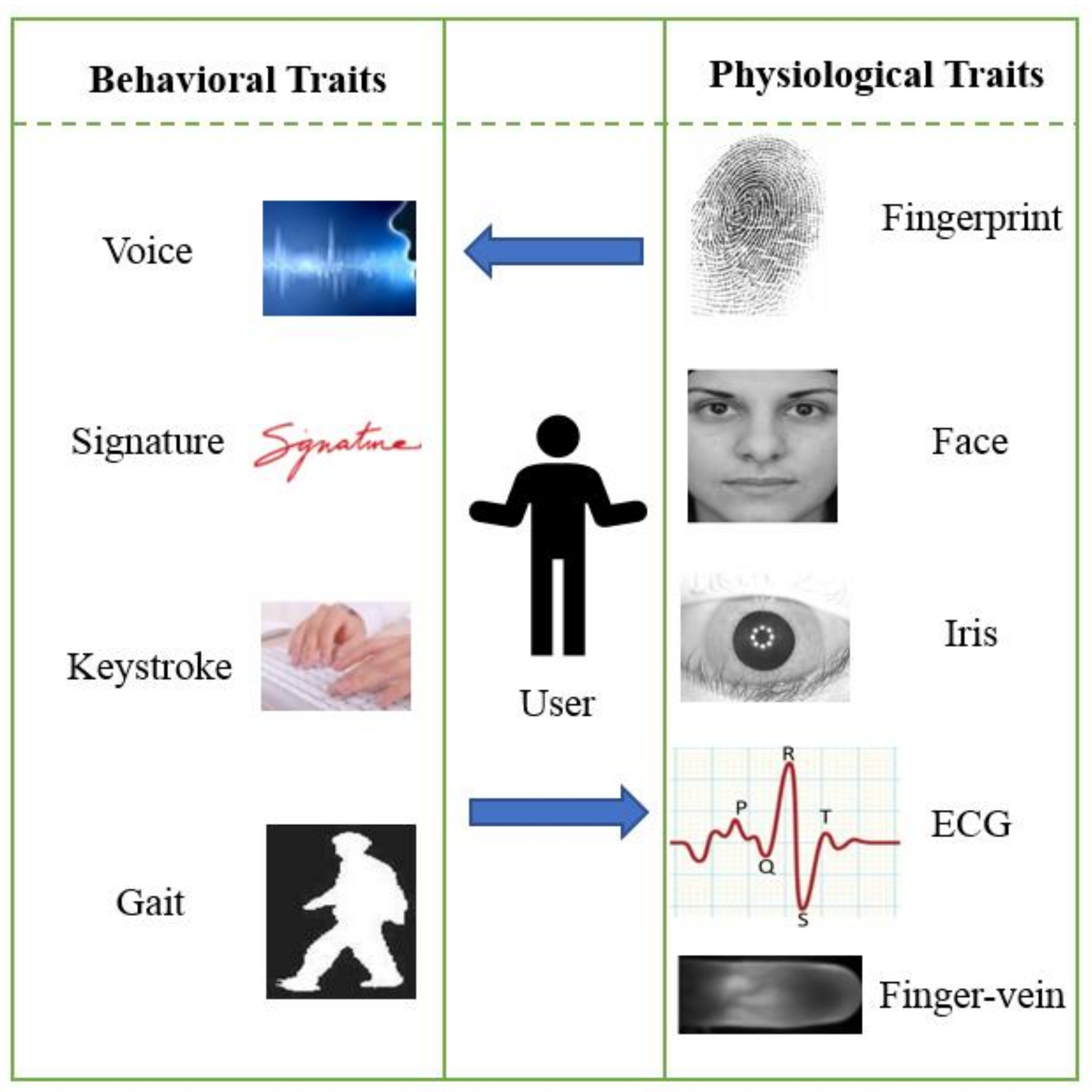
3.1. Classification of Biometrics
3.1.1. Fingerprint
3.1.2. Face
3.1.3. Electrocardiogram (ECG)
3.1.4. Voice
3.1.5. Others
3.2. Evaluation of Biometric Authentication
- False acceptance rate (FAR): The FAR is the probability of mistaking biometric samples from different subjects to be from the same subject [56].
- False rejection rate (FRR): The FRR is the probability of mistaking biometric samples from the same subject to be from different subjects [56].
- Equal error rate (EER): The EER is the error rate when FAR and FRR have the same value [56]. The FAR and FRR are inversely related, which means that when one increases, the other should decrease.
- Recognition accuracy (RA): RA is computed as the percentage of correct predictions out of the total number of observations. This metric is a common performance measure in machine and deep learning-based schemes [57].
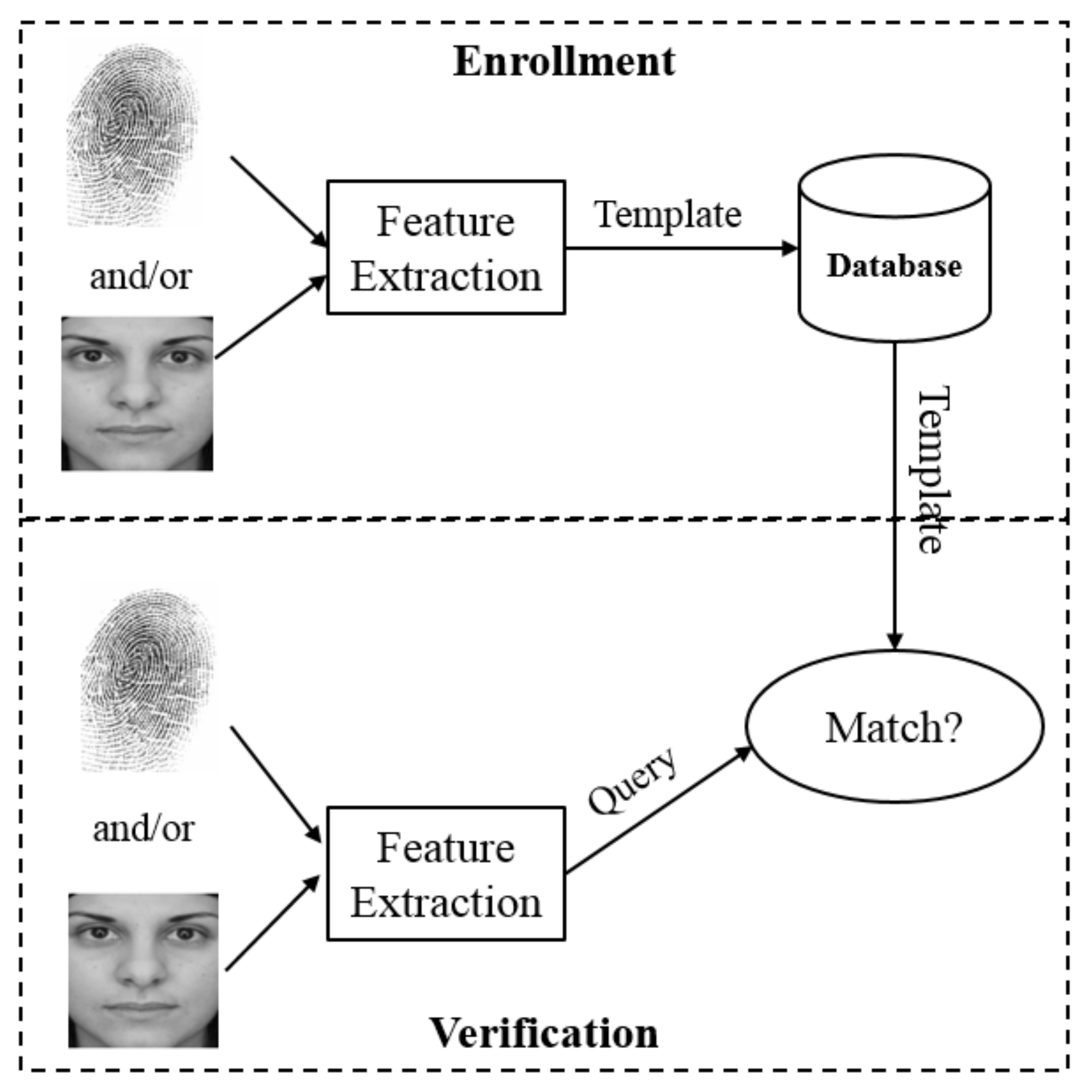
4. Biometric-Based Systems for IoT-Oriented Authentication
4.1. Single-Modal Versus Multi-Modal Biometric Authentication Systems
4.1.1. Single-Modal Biometric Authentication Systems
4.1.2. Multi-Modal Biometric Authentication Systems
4.1.3. Comparison of Single-Modal and Multi-Modal Biometric Authentication Systems
4.1.4. Continuous Biometric Authentication
4.1.5. Biometric Authentication versus Password- and Token-Based Authentication
4.2. Biometric Authentication and Key Agreement
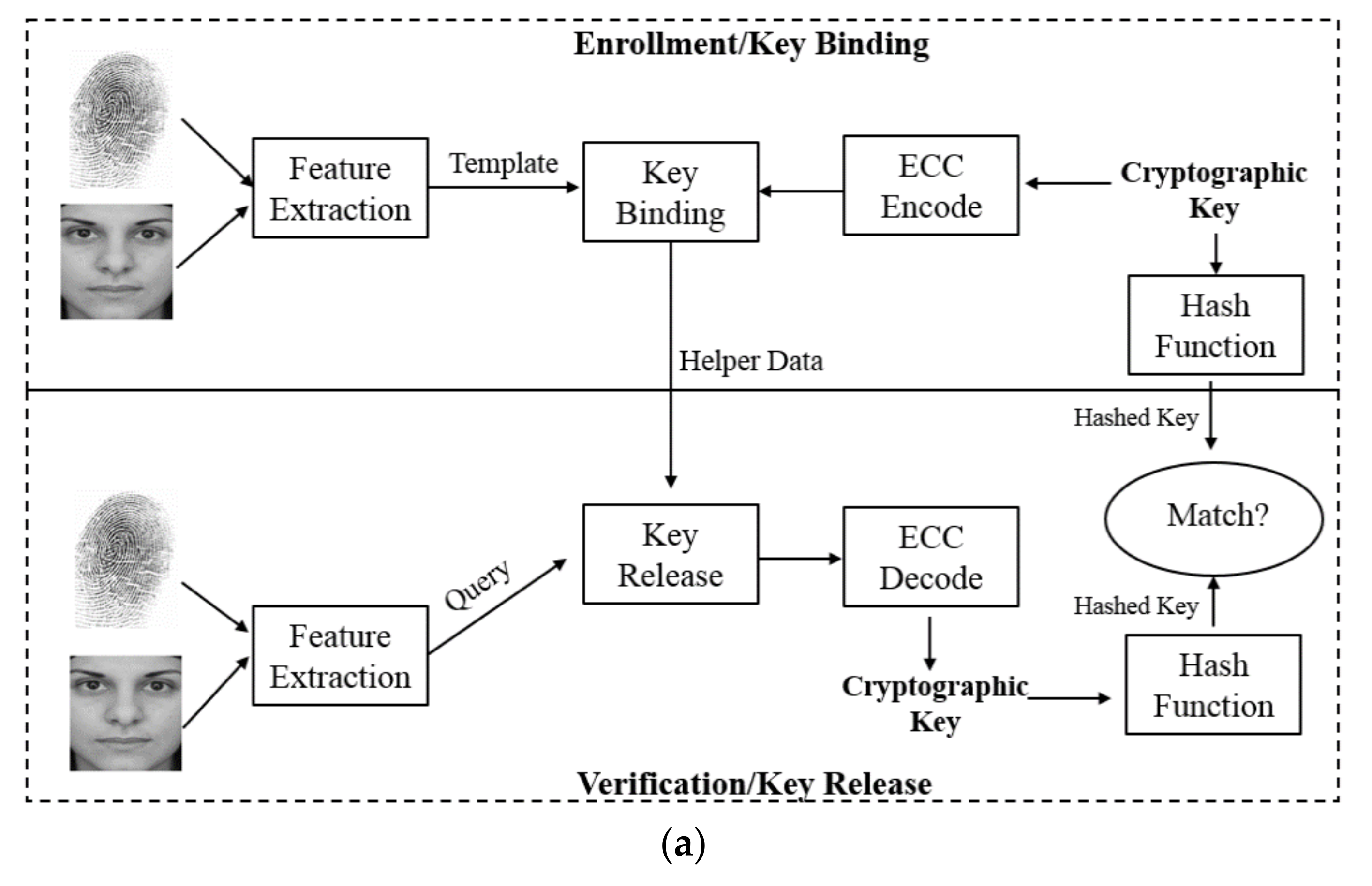
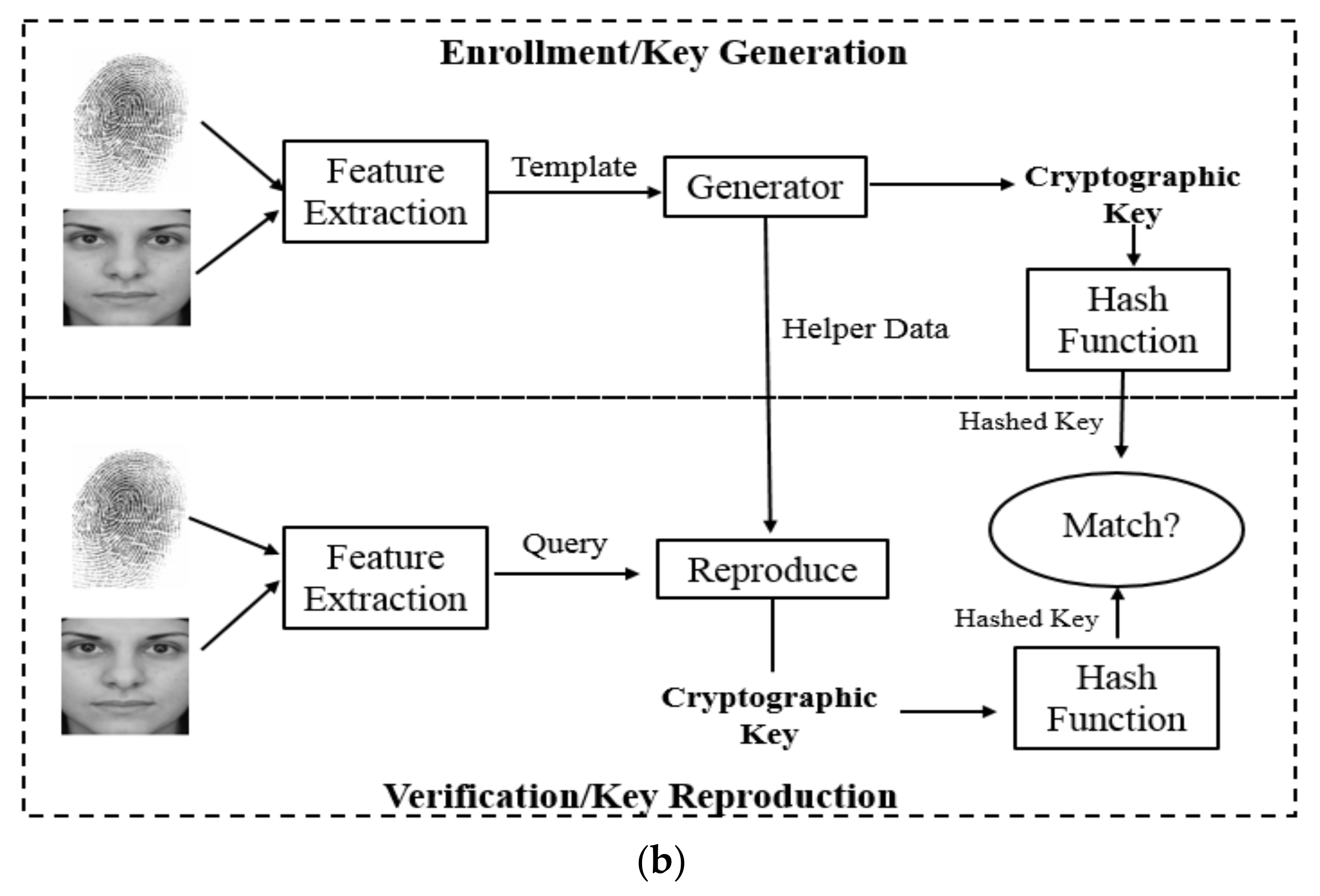
5. Biometric-Cryptographic Systems for IoT Data Encryption/Decryption
6. Present Challenges
6.1. Vulnerabilities of Biometric Systems and Their Impact on IoT Security
6.2. Selection of Biometric Traits for IoT-oriented Authentication
6.3. Limitations of Applying Biometric-Cryptographic Techniques to IoT Data Encryption/Decryption
6.4. Uncertainty of Biometric Data
6.5. Limited Resources of IoT Devices
7. Potential Solutions and Opportunities
7.1. Protecting Biometric Template Data
7.2. Reducing the Impact of Biometric Uncertainty
7.3. Lightweight Algorithm Design
7.4. Biometrics with Other Technologies
8. Threats to the Validity of This Survey
9. Conclusions
- Because no single biometric trait can satisfy the needs of all IoT applications, how to select suitable biometric traits for IoT-oriented biometric authentication is a nontrivial task, calling for more research attention. Moreover, although multi-modal biometric systems can reduce the effect of biometric uncertainty and bring about higher authentication accuracy than single-modal biometric systems, the extra cost incurred (e.g., additional processing and computing time) should be taken into consideration. Due to the resource limitations of IoT devices, how to design efficient and cost-effective multi-modal biometric systems is a much-needed research topic. For example, capturing iris and face biometrics simultaneously saves data collection time and brings convenience to users;
- The implementation of biometric-cryptographic techniques (e.g., fuzzy vault and fuzzy commitment) can provide both authentication and data encryption/decryption for IoT, but the large computing cost of the cryptographic key binding or generation operation and possible performance degradation are certain drawbacks of bio-cryptosystems. Therefore, more research effort should be directed to the development of new biometric-cryptographic techniques which can save cost, while providing satisfactory authentication performance in the IoT environment;
- The spoofing attack to the user interface is a serious security issue concerning biometric systems in the IoT, and the situation is made worse due to IoT’s automatization requirement. To the best of our knowledge thus far, there has been little study on this issue in the IoT field; thus, urgent research activities are required to defy spoofing attacks to IoT devices, especially in IoT applications with no human intervention;
- Despite its importance, biometrics for IoT security is a relatively new research area, evidenced by the limited number of articles that can be found in the literature. Given the resource constraints of IoT devices and the issue of user acceptability and/or convenience of collecting biometrics, it is necessary to develop lightweight authentication schemes, preferably with functions such as template data protection or key management so as to strengthen system security. Moreover, a user-friendly course of action is another critical factor to encourage public acceptance of biometrics in the IoT. We believe that the key to the widespread deployment of biometric systems in the IoT is to strike the right balance between privacy and convenience.
Author Contributions
Funding
Conflicts of Interest
References
- Karie, N.M.; Sahri, N.M.; Haskell-Dowland, P. IoT threat detection advances, challenges and future directions. In Proceedings of the 2020 Workshop on Emerging Technologies for Security in IoT (ETSecIoT), Sydney, NSW, Australia, 21–21 April 2020; pp. 22–29. [Google Scholar]
- Deogirikar, J.; Vidhate, A. Security attacks in IoT: A survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 32–37. [Google Scholar]
- Gurunath, R.; Agarwal, M.; Nandi, A.; Samanta, D. An overview: Security issue in IoT network. In Proceedings of the 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Tirunelveli, India, 29–30 October 2020; pp. 104–107. [Google Scholar]
- Yang, W.; Wang, S.; Hu, J.; Ibrahim, A.; Zheng, G.; Macedo, M.; Johnstone, M.; Valli, C. A Cancelable Iris- and Steganography-based User Authentication System for the Internet of Things. Sensors 2019, 19, 2985. [Google Scholar] [CrossRef] [Green Version]
- Cherapau, I.; Muslukhov, I.; Asanka, N.; Beznosov, K. On the Impact of Touch ID on iPhone Passcodes. In Proceedings of the Eleventh Symposium On Usable Privacy and Security, Pittsburgh, Pennsylvania, 20–22 July 2011; pp. 257–276. [Google Scholar]
- ABI Research Forecasts 95% of Smartphones to Feature Fingerprint Sensors by 2022. Available online: http://www.biometricupdate.com/201705/abi-research-forecasts-95-of-smartphones-to-feature-fingerprint-sensors-by-2022 (accessed on 1 July 2021).
- Rehman, H.U.; Asif, M.; Ahmad, M. Future applications and research challenges of IoT. In Proceedings of the 2017 International Conference on Information and Communication Technologies (ICICT), Karachi, Pakistan, 30–31 December 2017; pp. 68–74. [Google Scholar]
- Yang, W.; Hu, J.; Wang, S. A Delaunay triangle group based fuzzy vault with cancellability. In Proceedings of the 2013 6th International Congress on Image and Signal Processing (CISP), Hangzhou, China, 16–18 December 2013; pp. 1676–1681. [Google Scholar]
- Ren, C.; Gong, Y.; Hao, F.; Cai, X.; Wu, Y. When biometrics meet iot: A survey. In Proceedings of the 6th International Asia Conference on Industrial Engineering and Management Innovation; Springer: Paris, France, 2015; pp. 635–643. [Google Scholar]
- Subha, R. Biometrics in Internet of Things (IoT) Security. Int. J. Eng. Res. Gen. Sci. 2017, 5, 37–42. [Google Scholar]
- Blasco, J.; Chen, T.M.; Tapiador, J.; Peris-Lopez, P. A survey of wearable biometric recognition systems. ACM Comput. Surv. (CSUR) 2016, 49, 1–35. [Google Scholar] [CrossRef]
- Obaidat, M.S.; Rana, S.P.; Maitra, T.; Giri, D.; Dutta, S. Biometric Security and Internet of Things (IoT). In Biometric-Based Physical and Cybersecurity Systems; Springer: Cham, Switzerland, 2019; pp. 477–509. [Google Scholar]
- Petersen, K.; Vakkalanka, S.; Kuzniarz, L. Guidelines for conducting systematic mapping studies in software engineering: An update. Inf. Softw. Technol. 2015, 64, 1–18. [Google Scholar] [CrossRef]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 336–341. [Google Scholar]
- Bures, M.; Klima, M.; Rechtberger, V.; Ahmed, B.S.; Hindy, H.; Bellekens, X. Review of Specific Features and Challenges in the Current Internet of Things Systems Impacting their Security and Reliability. arXiv 2021, arXiv:2101.02631. [Google Scholar]
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- Sethi, P.; Sarangi, S.R. Internet of things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017, 9324035. [Google Scholar] [CrossRef] [Green Version]
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Hu, J.; Zheng, G.; Chaudhry, J.; Adi, E.; Valli, C. Securing Mobile Healthcare Data: A Smart Card based Cancelable Finger-vein Bio-Cryptosystem. IEEE Access 2018, 6, 36939–36947. [Google Scholar] [CrossRef]
- Jain, A.K.; Ross, A.; Prabhakar, S. An introduction to biometric recognition. IEEE Trans. Circ. Syst. Video Technol. 2004, 14, 4–20. [Google Scholar] [CrossRef] [Green Version]
- Yang, W.; Wang, S.; Hu, J.; Zheng, G.; Valli, C. Security and Accuracy of Fingerprint-based Biometrics: A Review. Symmetry 2019, 11, 141. [Google Scholar] [CrossRef] [Green Version]
- Jain, A.K.; Li, S.Z. Handbook of Face Recognition; Springer: London, UK, 2011; Volume 1. [Google Scholar]
- Odinaka, I.; Lai, P.-H.; Kaplan, A.D.; O’Sullivan, J.A.; Sirevaag, E.J.; Rohrbaugh, J.W. ECG biometric recognition: A comparative analysis. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1812–1824. [Google Scholar] [CrossRef]
- Devikar, P.; Krishnamoorthy, A.; Bhanage, A.; Chauhan, M.S. IoT based biometric attendance system. Int. J. Adv. Res. Comput. Commun. Eng. 2016, 11, 156–161. [Google Scholar]
- Shad, D.; Bharadi, V. IoT based biometrics implementation on Raspberry Pi. Procedia Comput. Sci. 2016, 79, 328–336. [Google Scholar] [CrossRef] [Green Version]
- Prakash, N.S.; Venkatram, N. Establishing efficient security scheme in home IOT devices through biometric finger print technique. Indian J. Sci. Technol. 2016, 9, 1–8. [Google Scholar] [CrossRef] [Green Version]
- Taheri, S.; Yuan, J.-S. A cross-layer biometric recognition system for mobile IoT devices. Electronics 2018, 7, 26. [Google Scholar] [CrossRef] [Green Version]
- Sarika, C.; Malakreddy, A.B.; Harinath, H. Iot-based smart login using biometrics. In International Conference on Computer Networks and Communication Technologies; Springer: Singapore, 2018; pp. 589–597. [Google Scholar]
- Yang, W.; Wang, S.; Zheng, G.; Yang, J.; Valli, C. A Privacy-Preserving Lightweight Biometric System for Internet-of-Things Security. IEEE Commun. Mag. 2019, 57, 84–89. [Google Scholar] [CrossRef]
- Golec, M.; Gill, S.S.; Bahsoon, R.; Rana, O. BioSec: A Biometric Authentication Framework for Secure and Private Communication among Edge Devices in IoT and Industry 4.0. IEEE Consum. Electron. Mag. 2020, 1. [Google Scholar] [CrossRef]
- Hossain, M.S.; Muhammad, G.; Rahman, S.M.M.; Abdul, W.; Alelaiwi, A.; Alamri, A. Toward end-to-end biometrics-based security for IoT infrastructure. IEEE Wirel. Commun. 2016, 23, 44–51. [Google Scholar] [CrossRef]
- Thilagavathi, B.; Suthendran, K. Boosting Based Implementation of Biometric Authentication in IoT. J. Cyber Secur. Mobil. 2018, 7, 131–144. [Google Scholar] [CrossRef]
- Gayathri, M.; Malathy, C.; Singh, S. MARK42: The secured personal assistant using biometric traits integrated with green IOT. J. Green Eng. 2020, 10, 255–267. [Google Scholar]
- Kolhar, M.; Al-Turjman, F.; Alameen, A.; Abualhaj, M.M. A three layered decentralized IoT biometric architecture for city lockdown during COVID-19 outbreak. IEEE Access 2020, 8, 163608–163617. [Google Scholar] [CrossRef]
- Karimian, N.; Wortman, P.A.; Tehranipoor, F. Evolving authentication design considerations for the internet of biometric things (IoBT). In Proceedings of the Eleventh IEEE/ACM/IFIP International Conference on Hardware/Software Codesign and System Synthesis, Pittsburgh, PA, USA, 2–7 October 2016; p. 10. [Google Scholar]
- Hussein, A.F.; AlZubaidi, A.K.; Al-Bayaty, A.; Habash, Q.A. An IoT real-time biometric authentication system based on ECG fiducial extracted features using discrete cosine transform. arXiv 2017, arXiv:1708.08189. [Google Scholar]
- Barros, A.; Rosário, D.; Resque, P.; Cerqueira, E. Heart of IoT: ECG as biometric sign for authentication and identification. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 307–312. [Google Scholar]
- Karimian, N.; Tehranipoor, M.; Woodard, D.; Forte, D. Unlock your heart: Next generation biometric in resource-constrained healthcare systems and IoT. IEEE Access 2019, 7, 49135–49149. [Google Scholar] [CrossRef]
- Shin, D.-G.; Jun, M.-S. Home IoT device certification through speaker recognition. In Proceedings of the 2015 17th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 1–3 July 2015; pp. 600–603. [Google Scholar]
- Duraibi, S. Voice Biometric Identity Authentication Model for IoT Devices. Int. J. Secur. Priv. Trust Manag. (IJSPTM) 2020, 9. [Google Scholar] [CrossRef]
- Lu, Y.; Wu, S.; Fang, Z.; Xiong, N.; Yoon, S.; Park, D.S. Exploring finger vein based personal authentication for secure IoT. Future Gener. Comput. Syst. 2017, 77, 149–160. [Google Scholar] [CrossRef]
- Gad, R.; Abd El-Latif, A.A.; Elseuofi, S.; Ibrahim, H.M.; Elmezain, M.; Said, W. IoT security based on iris verification using multi-algorithm feature level fusion scheme. In Proceedings of the 2019 2nd international conference on computer applications & information security (ICCAIS), Riyadh, Saudi Arabia, 1–3 May 2019; pp. 1–6. [Google Scholar]
- Maček, N.; Franc, I.; Bogdanoski, M.; Mirković, A. Multimodal Biometric Authentication in IoT: Single Camera Case Study. In Proceedings of the 8th International Conference on Business Information Security, Belgrade, Serbia, 15 October 2016; pp. 33–38. [Google Scholar]
- Shahim, L.-P.; Snyman, D.; du Toit, T.; Kruger, H. Cost-Effective Biometric Authentication using Leap Motion and IoT Devices. In Proceedings of the Tenth International Conference on Emerging Security Information, Systems and Technologies (SECURWARE 2016), Nice, France, 24–28 July 2016; pp. 10–13. [Google Scholar]
- Olazabal, O.; Gofman, M.; Bai, Y.; Choi, Y.; Sandico, N.; Mitra, S.; Pham, K. Multimodal biometrics for enhanced iot security. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 886–893. [Google Scholar]
- Hassen, O.A.; Abdulhussein, A.A.; Darwish, S.M.; Othman, Z.A.; Tiun, S.; A Lotfy, Y. Towards a Secure Signature Scheme Based on Multimodal Biometric Technology: Application for IOT Blockchain Network. Symmetry 2020, 12, 1699. [Google Scholar] [CrossRef]
- Cherifi, F.; Amroun, K.; Omar, M. Robust multimodal biometric authentication on IoT device through ear shape and arm gesture. Multimed. Tools Appl. 2021, 14807–14827. [Google Scholar] [CrossRef]
- Daugman, J. How Iris Recognition Works. IEEE Trans. Circuits Syst. Video Technol. 2004, 14, 21. [Google Scholar] [CrossRef]
- Li, H.; Qiu, J.; Teoh, A.B.J. Palmprint template protection scheme based on randomized cuckoo hashing and MinHash. Multimed. Tools Appl. 2020, 79, 11947–11971. [Google Scholar] [CrossRef]
- Yang, W.; Hu, J.; Wang, S. A Finger-Vein Based Cancellable Bio-cryptosystem. In Proceedings of the International Conference on Network and System Security, Madrid, Spain, 3–4 June 2013; pp. 784–790. [Google Scholar]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.-J.; Yoo, K.-Y. Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Chang, T.Y. Dynamically generate a long-lived private key based on password keystroke features and neural network. Inf. Sci. 2012, 211, 36–47. [Google Scholar] [CrossRef]
- Moorfield, J.; Wang, S.; Yang, W.; Bedari, A.; Van Der Kamp, P. A Möbius transformation based model for fingerprint minutiae variations. Pattern Recognit. 2019, 98, 107054. [Google Scholar] [CrossRef]
- Natgunanathan, I.; Mehmood, A.; Xiang, Y.; Beliakov, G.; Yearwood, J. Protection of Privacy in Biometric Data. IEEE Access 2016, 4, 880–892. [Google Scholar] [CrossRef] [Green Version]
- Shahzad, M.; Wang, S.; Deng, G.; Yang, W. Alignment-free Cancelable Fingerprint Templates with Dual Protection. Pattern Recognit. 2020, 111, 107735. [Google Scholar] [CrossRef]
- Srivastva, R.; Singh, A.; Singh, Y.N. PlexNet: A fast and robust ECG biometric system for human recognition. Inf. Sci. 2021, 558, 208–228. [Google Scholar] [CrossRef]
- Habib, K.; Torjusen, A.; Leister, W. A novel authentication framework based on biometric and radio fingerprinting for the IoT in eHealth. In Proceedings of the 2014 International Conference on Smart Systems, Devices and Technologies (SMART), Paris, France, 20–24 July 2014; pp. 32–37. [Google Scholar]
- Albalawi, A.; Almrshed, A.; Badhib, A.; Alshehri, S. A survey on authentication techniques for the internet of things. In Proceedings of the 2019 International Conference on Computer and Information Sciences (ICCIS), Sakaka, Saudi Arabia, 3–4 April 2019; pp. 1–5. [Google Scholar]
- Kantarci, B.; Erol-Kantarci, M.; Schuckers, S. Towards secure cloud-centric internet of biometric things. In Proceedings of the 2015 IEEE 4th International Conference on Cloud Networking (CloudNet), Niagara Falls, ON, Canada, 5–7 October 2015; pp. 81–83. [Google Scholar]
- Karimian, N.; Guo, Z.; Tehranipoor, F.; Woodard, D.; Tehranipoor, M.; Forte, D. Secure and reliable biometric access control for resource-constrained systems and IoT. arXiv 2018, arXiv:1803.09710. [Google Scholar]
- Meena, G.; Choudhary, S. Biometric authentication in internet of things: A conceptual view. J. Stat. Manag. Syst. 2019, 22, 643–652. [Google Scholar] [CrossRef]
- Lip, C.C.; Ramli, D.A. Comparative Study on Feature, Score and Decision Level Fusion Schemes for Robust Multibiometric Systems. In Frontiers in Computer Education; Springer: Cham, Switzerland, 2012; pp. 941–948. [Google Scholar]
- Yang, W.; Wang, S.; Hu, J.; Zheng, G.; Valli, C. A Fingerprint and Finger-vein Based Cancelable Multi-biometric System. Pattern Recognit. 2018, 78, 242–251. [Google Scholar] [CrossRef]
- Ross, A. Multibiometrics. In Encyclopedia of Biometrics; Li, S.Z., Jain, A., Eds.; Springer: Boston, MA, USA, 2009; pp. 967–973. [Google Scholar] [CrossRef]
- Rathgeb, C.; Busch, C. Multi-Biometric Template Protection: Issues and Challenges. New Trends and Developments in Biometrics. 2012, pp. 173–190. Available online: https://www.intechopen.com/chapters/40310 (accessed on 1 July 2021).
- Zahoor, S.; Mir, R.N. Resource management in pervasive Internet of Things: A survey. J. King Saud Univ. Comput. Inf. Sci. 2018, in press. [Google Scholar] [CrossRef]
- Bours, P. Continuous keystroke dynamics: A different perspective towards biometric evaluation. Inf. Secur. Tech. Rep. 2012, 17, 36–43. [Google Scholar] [CrossRef]
- Mondal, S.; Bours, P. Continuous authentication using mouse dynamics. In Proceedings of the 2013 International Conference of the BIOSIG Special Interest Group (BIOSIG), Darmstadt, Germany, 5–6 September 2013; pp. 1–12. [Google Scholar]
- Temper, M.; Tjoa, S.; Kaiser, M. Touch to authenticate—Continuous biometric authentication on mobile devices. In Proceedings of the 2015 1st International Conference on Software Security and Assurance (ICSSA), Suwon, Korea, 27 July 2015; pp. 30–35. [Google Scholar]
- Traoré, I.; Nakkabi, Y.; Saad, S.; Sayed, B.; Ardigo, J.D.; de Faria Quinan, P.M. Ensuring online exam integrity through continuous biometric authentication. In Information Security Practices; Springer: Cham, Switzerland, 2017; pp. 73–81. [Google Scholar]
- O’Gorman, L. Comparing passwords, tokens, and biometrics for user authentication. Proc. IEEE 2003, 91, 2021–2040. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Zheng, G.; Chaudhry, J.; Valli, C. ECB4CI: An enhanced cancelable biometric system for securing critical infrastructures. J. Supercomput. 2018, 74, 4893–4909. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Zheng, G.; Valli, C. Impact of feature proportion on matching performance of multi-biometric systems. ICT Express 2018, 5, 37–40. [Google Scholar] [CrossRef]
- Ometov, A.; Petrov, V.; Bezzateev, S.; Andreev, S.; Koucheryavy, Y.; Gerla, M. Challenges of multi-factor authentication for securing advanced IoT applications. IEEE Netw. 2019, 33, 82–88. [Google Scholar] [CrossRef]
- Xie, Q.; Dong, N.; Wong, D.S.; Hu, B. Cryptanalysis and security enhancement of a robust two-factor authentication and key agreement protocol. Int. J. Commun. Syst. 2016, 29, 478–487. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. Robust anonymous two-factor authenticated key exchange scheme for mobile client-server environment. Secur. Commun. Netw. 2016, 9, 1331–1339. [Google Scholar] [CrossRef] [Green Version]
- Yoon, E.-J.; Yoo, K.-Y. Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. J. Supercomput. 2013, 63, 235–255. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumari, S.; Li, X.; Wu, F. Provably secure biometric-based user authentication and key agreement scheme in cloud computing. Secur. Commun. Netw. 2016, 9, 4103–4119. [Google Scholar] [CrossRef] [Green Version]
- Chuang, M.-C.; Chen, M.C. An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst. Appl. 2014, 41, 1411–1418. [Google Scholar] [CrossRef]
- Mishra, D.; Das, A.K.; Mukhopadhyay, S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst. Appl. 2014, 41, 8129–8143. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Y.; Tang, S.; Luo, H. Privacy protection for e-health systems by means of dynamic authentication and three-factor key agreement. IEEE Trans. Ind. Electron. 2017, 65, 2795–2805. [Google Scholar] [CrossRef] [Green Version]
- Kakarla, G.; Singamsetty, P. A Secure and light-weighted Group based Authentication and Key Agreement Protocol involving ECDH for Machine Type Communications in 3GPP Networks. Indian J. Comput. Sci. Eng. 2020, 11, 670–693. [Google Scholar] [CrossRef]
- Modiri, M.; Mohajeri, J.; Salmasizadeh, M. A Novel Group-based Secure Lightweight Authentication and Key Agreement Protocol forMachine-Type Communication. Sci. Iran. 2021. [Google Scholar] [CrossRef]
- Adhikari, M.; Panda, P.K.; Chattopadhyay, S.; Majumdar, S. A Novel Group-Based Authentication and Key Agreement Protocol for IoT Enabled LTE/LTE–A Network. In Proceedings of the 2020 International Conference on Wireless Communications Signal Processing and Networking (WiSPNET), Chennai, India, 16 September 2020; pp. 168–172. [Google Scholar]
- Chuang, Y.H.; Lei, C.L. An independent three-factor mutual authentication and key agreement scheme with privacy preserving for multiserver environment and a survey. Int. J. Commun. Syst. 2021, 34, e4660. [Google Scholar]
- Sandhya, M.; Prasad, M.V. A bio-cryptosystem for fingerprints using Delaunay neighbor structures (dns) and fuzzy commitment scheme. In Advances in Signal Processing and Intelligent Recognition Systems; Springer: Cham, Switzerland, 2016; pp. 159–171. [Google Scholar]
- Uludag, U.; Pankanti, S.; Jain, A.K. Fuzzy vault for fingerprints. In Proceedings of the Audio-and Video-Based Biometric Person Authentication, Hilton Rye Town, NY, USA, 20–22 July 2005; pp. 310–319. [Google Scholar]
- Zheng, G.; Shankaran, R.; Yang, W.; Valli, C.; Qiao, L.; Orgun, M.A.; Mukhopadhyay, S.C. A Critical Analysis of ECG-based Key Distribution for Securing Wearable and Implantable Medical Devices. IEEE Sens. J. 2018, 19, 1186–1198. [Google Scholar] [CrossRef]
- Choi, D.; Seo, S.-H.; Oh, Y.-S.; Kang, Y. Two-factor fuzzy commitment for unmanned IoT devices security. IEEE Internet Things J. 2018, 6, 335–348. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Bhat, V.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Ebrahimi, S.; Bayat-Sarmadi, S. Lightweight Fuzzy Extractor Based on LPN for Device and Biometric Authentication in IoT. IEEE Internet Things J. 2021, 8, 10706–10713. [Google Scholar] [CrossRef]
- Rathgeb, C.; Uhl, A. A survey on biometric cryptosystems and cancelable biometrics. EURASIP J. Inf. Secur. 2011, 2011, 3. [Google Scholar] [CrossRef] [Green Version]
- Ratha, N.K.; Connell, J.H.; Bolle, R.M. An analysis of minutiae matching strength. In Proceedings of the International Conference on Audio-and Video-Based Biometric Person Authentication, Guildford, UK, 9–11 June 2003; pp. 223–228. [Google Scholar]
- Yang, W.; Hu, J.; Fernandes, C.; Sivaraman, V.; Wu, Q. Vulnerability analysis of iPhone 6. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 457–463. [Google Scholar]
- Hammad, M.; Liu, Y.; Wang, K. Multimodal biometric authentication systems using convolution neural network based on different level fusion of ECG and fingerprint. IEEE Access 2018, 7, 26527–26542. [Google Scholar] [CrossRef]
- Selvi, P.T.; Radha, N. Multimodal biometrics based authentication against dictionary attacks. Int. J. Comput. Sci. Eng. 2010, 2, 2652–2658. [Google Scholar]
- Banafa, A. Three major challenges facing iot. Newsletter, IEEE Internet of Things. 2017. Available online: https://iot.ieee.org/newsletter/march-2017/three-major-challenges-facing-iot.html/ (accessed on 1 July 2021).
- Li, C.; Hu, J. A security-enhanced alignment-free fuzzy vault-based fingerprint cryptosystem using pair-polar minutiae structures. IEEE Trans. Inf. Forensics Secur. 2016, 11, 543–555. [Google Scholar] [CrossRef]
- Ferrara, M.; Maltoni, D.; Cappelli, R. Non-invertible Minutia Cylinder-Code Representation. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1727–1737. [Google Scholar] [CrossRef]
- Gao, Q.; Zhang, X. A study of distortion effects on fingerprint matching. Comput. Sci. Eng. 2012, 2, 37–42. [Google Scholar] [CrossRef] [Green Version]
- Yang, T.; Zhang, G.; Liu, L.; Yang, Y.; Zhao, S.; Sun, H.; Wang, W. New features of authentication scheme for the IoT: A survey. In Proceedings of the 2nd International ACM Workshop on Security and Privacy for the Internet-of-Things; Association for Computing Machinery: New York, NY, USA; pp. 44–49.
- Yang, W.; Wang, S.; Shahzad, M.; Zhou, W. A cancelable biometric authentication system based on feature-adaptive random projection. J. Inf. Secur. Appl. 2021, 58, 102704. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Yu, K.; Kang, J.J.; Johnstone, M.N. Secure Fingerprint Authentication with Homomorphic Encryption. In Proceedings of the 2020 Digital Image Computing: Techniques and Applications, Melbourne, Australia, 29 November–2 December 2020. [Google Scholar]
- Bedari, A.; Wang, S.; Yang, W. Design of Cancelable MCC-Based Fingerprint Templates Using Dyno-Key Model. Pattern Recognit. 2021, 119, 108074. [Google Scholar] [CrossRef]
- Mandal, A.; Roy, A.; Yasuda, M. Comprehensive and improved secure biometric system using homomorphic encryption. In Data Privacy Management, And Security Assurance; Springer: Cham, Switzerland, 2015; pp. 183–198. [Google Scholar]
- Punithavathi, P.; Geetha, S.; Karuppiah, M.; Islam, S.H.; Hassan, M.M.; Choo, K.-K.R. A Lightweight Machine Learning-based Authentication Framework for Smart IoT Devices. Inf. Sci. 2019. [CrossRef]
- Punithavathi, P.; Geetha, S. Partial DCT-based cancelable biometric authentication with security and privacy preservation for IoT applications. Multimed. Tools Appl. 2019, 78, 25487–25514. [Google Scholar] [CrossRef]
- Farid, F.; Elkhodr, M.; Sabrina, F.; Ahamed, F.; Gide, E. A Smart Biometric Identity Management Framework for Personalised IoT and Cloud Computing-Based Healthcare Services. Sensors 2021, 21, 552. [Google Scholar] [CrossRef]
- Zheng, G.; Yang, W.; Valli, C.; Qiao, L.; Shankaran, R.; Orgun, M.A.; Mukhopadhyay, S.C. Finger-to-Heart (F2H): Authentication for Wireless Implantable Medical Devices. IEEE J. Biomed. Health Inform. 2018, 23, 1546–1557. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Q. Deep learning of electrocardiography dynamics for biometric human identification in era of IoT. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 885–888. [Google Scholar]
- Yang, W.; Wang, S.; Hu, J.; Zheng, G.; Yang, J.; Valli, C. Securing Deep Learning Based Edge Finger-vein Biometrics with Binary Decision Diagram. IEEE Trans. Ind. Inform. 2019, 15, 11. [Google Scholar] [CrossRef]
- Dhillon, P.K.; Kalra, S. A lightweight biometrics based remote user authentication scheme for IoT services. J. Inf. Secur. Appl. 2017, 34, 255–270. [Google Scholar] [CrossRef]
- Taher, B.H.; Jiang, S.; Yassin, A.A.; Lu, H. Low-overhead remote user authentication protocol for IoT based on a fuzzy extractor and feature extraction. IEEE Access 2019, 7, 148950–148966. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Gao, Z.; Xu, L.; Turner, G.; Patel, B.; Diallo, N.; Chen, L.; Shi, W. Blockchain-based identity management with mobile device. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems, Munich, Germany, 15 June 2018; pp. 66–70. [Google Scholar]
- Kaga, Y.; Fujio, M.; Naganuma, K.; Takahashi, K.; Murakami, T.; Ohki, T.; Nishigaki, M. A secure and practical signature scheme for blockchain based on biometrics. In Proceedings of the International Conference on Information Security Practice and Experience, Melbourne, Australia, 12–13 September 2017; pp. 877–891. [Google Scholar]
- Yahuza, M.; Idris, M.Y.I.B.; Wahab, A.W.B.A.; Ho, A.T.; Khan, S.; Musa, S.N.B.; Taha, A.Z.B. Systematic review on security and privacy requirements in edge computing: State of the art and future research opportunities. IEEE Access 2020, 8, 76541–76567. [Google Scholar] [CrossRef]
- Sjøberg, D.I.; Hannay, J.E.; Hansen, O.; Kampenes, V.B.; Karahasanovic, A.; Liborg, N.-K.; Rekdal, A.C. A survey of controlled experiments in software engineering. IEEE Trans. Softw. Eng. 2005, 31, 733–753. [Google Scholar] [CrossRef] [Green Version]

| Layers | Attacks | Description | Security Requirements |
|---|---|---|---|
| Perception Layer | Node Tampering | The attacker physically alters the node to obtain sensitive information. | Authentication, Data Confidentiality, Lightweight Encryption, Key Agreement |
| RF Interference | The attacker sends noise signals in the radio frequency spectrum. | ||
| Node Jamming | The attacker disturbs the wireless communication using jammers. | ||
| Malicious Node Injection | The attacker injects malicious nodes in the network, which can modify data and pass wrong data to other nodes. | ||
| Physical Damage | The attacker physically harms components of IoT. | ||
| Malicious Code Injection | The attacker introduces malicious code into the nodes of IoT to obtain control of the IoT system. | ||
| Network Layer | Traffic Analysis Attacks | The attacker intercepts and examines messages to obtain network data. | Authentication, Key Management, Intrusion Detection, Communication Security, Routing Security |
| RFID Spoofing and Cloning | The attacker spoofs RFID signals, copies data from a pre-existing RFID tag to another RFID tag. | ||
| Man-in-the-middle Attacks | The attacker intercepts the communication between two nodes in the wireless channel. | ||
| Routing Information Attacks | The attacker spoofs, modifies or sends wrong routing information to complicate the network. | ||
| Denial of Service | The attacker creates a large amount of traffic to flood the network such that the intended users cannot access services. | ||
| Sybil Attacks | The malicious node takes the identifies of multiple nodes and acts as them. | ||
| Application Layer | Phishing Attacks | The attacker obtains private information through spoofing. | Authentication, Information Security Management, Privacy protection |
| Viruses, Worms, Trojan Horses | The attacker undermines the system using malicious code such as viruses, worms and trojan horses. | ||
| Denial of Service | The attacker blocks users from the application layer by denying services. |
| Method for IoT Security | Year of Publication | Type of Biometric Traits | Databases | Performance | Hardware/Platform |
|---|---|---|---|---|---|
| Single-Modal Biometrics | |||||
| Devikar et al. [25] | 2016 | Fingerprint | - | - | ESP8266 NodeMCU |
| Shah and Bharadi [26] | 2016 | Fingerprint | - | - | Raspberry Pi |
| Prakash and Venkatram [27] | 2016 | Fingerprint | - | - | Raspberry Pi 2 |
| Taheri and Yuan [28] | 2018 | Fingerprint | - | - | Simulator on PC |
| Sarika et al. [29] | 2019 | Fingerprint | - | - | Arduino board |
| Yang et al. [30] | 2019 | Fingerprint | FVC2002DB3 | EER = 3% | Simulator |
| Golec et al. [31] | 2020 | Fingerprint | Private | EER = 30% | Raspberry Pi |
| Hossain et al. [32] | 2016 | Face | FERET | RA = 99.5% | Simulator |
| Thilagavathi and Suthendran [33] | 2018 | Face | - | - | Simulator on Web Server (Apache) |
| Gayathri et al. [34] | 2020 | Face | - | - | Simulator on PC |
| Kolhar et al. [35] | 2020 | Face | WIDER FACE | RA = 60.7% | Raspberry Pi |
| Karimian et al. [36] | 2016 | ECG | - | - | - |
| Hussein et al. [37] | 2017 | ECG | MIT-BIH | RA = 97.78% | Raspberry Pi 3 |
| Barros et al. [38] | 2019 | ECG | NIH PhysioBank | RA = 98.2% | Simulator on PC |
| Karimian et al. [39] | 2019 | ECG | PTB | RA = 98.76% | Simulator |
| Shin and Jun [40] | 2015 | Voice | - | - | - |
| Duraibi et al. [41] | 2020 | Voice | - | - | - |
| Lu et al. [42] | 2017 | Finger-vein | MMCBNU_6000 | EER = 0.36% | Simulator |
| Yang et al. [4] | 2019 | Iris | CASIA-Iris v.3 | EER = 0.22% | Simulator |
| Gad et al. [43] | 2019 | Iris | CASIA-Iris v.4 | EER = 0.20% | Simulator |
| Multi-Modal Biometrics | |||||
| Macek et al. [44] | 2016 | Face & Iris | CASIA-Face v.5 CASIA-Iris v.4 | RA = 99.1% | Simulator |
| Shahim et al. [45] | 2016 | Hand & Gesture | - | - | - |
| Olazabal et al. [46] | 2019 | Face & Voice | CSUF-SG5 | Fused: EER = 8.04% Face: EER = 14.05% Voice: EER = 43.76% | Raspberry Pi 3 Model B |
| Hassen et al. [47] | 2020 | Fingerprint & Finger-vein | - | - | Simulator on PC |
| Cherifi et al. [48] | 2021 | Ear & Arm Gestures | AWE HMOG | Fused: EER = 5.15% Ear: EER = 20.80% Arm: EER = 10.60% | Simulator |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, W.; Wang, S.; Sahri, N.M.; Karie, N.M.; Ahmed, M.; Valli, C. Biometrics for Internet-of-Things Security: A Review. Sensors 2021, 21, 6163. https://doi.org/10.3390/s21186163
Yang W, Wang S, Sahri NM, Karie NM, Ahmed M, Valli C. Biometrics for Internet-of-Things Security: A Review. Sensors. 2021; 21(18):6163. https://doi.org/10.3390/s21186163
Chicago/Turabian StyleYang, Wencheng, Song Wang, Nor Masri Sahri, Nickson M. Karie, Mohiuddin Ahmed, and Craig Valli. 2021. "Biometrics for Internet-of-Things Security: A Review" Sensors 21, no. 18: 6163. https://doi.org/10.3390/s21186163
APA StyleYang, W., Wang, S., Sahri, N. M., Karie, N. M., Ahmed, M., & Valli, C. (2021). Biometrics for Internet-of-Things Security: A Review. Sensors, 21(18), 6163. https://doi.org/10.3390/s21186163








