Encryption Based Image Watermarking Algorithm in 2DWT-DCT Domains
Abstract
:1. Introduction
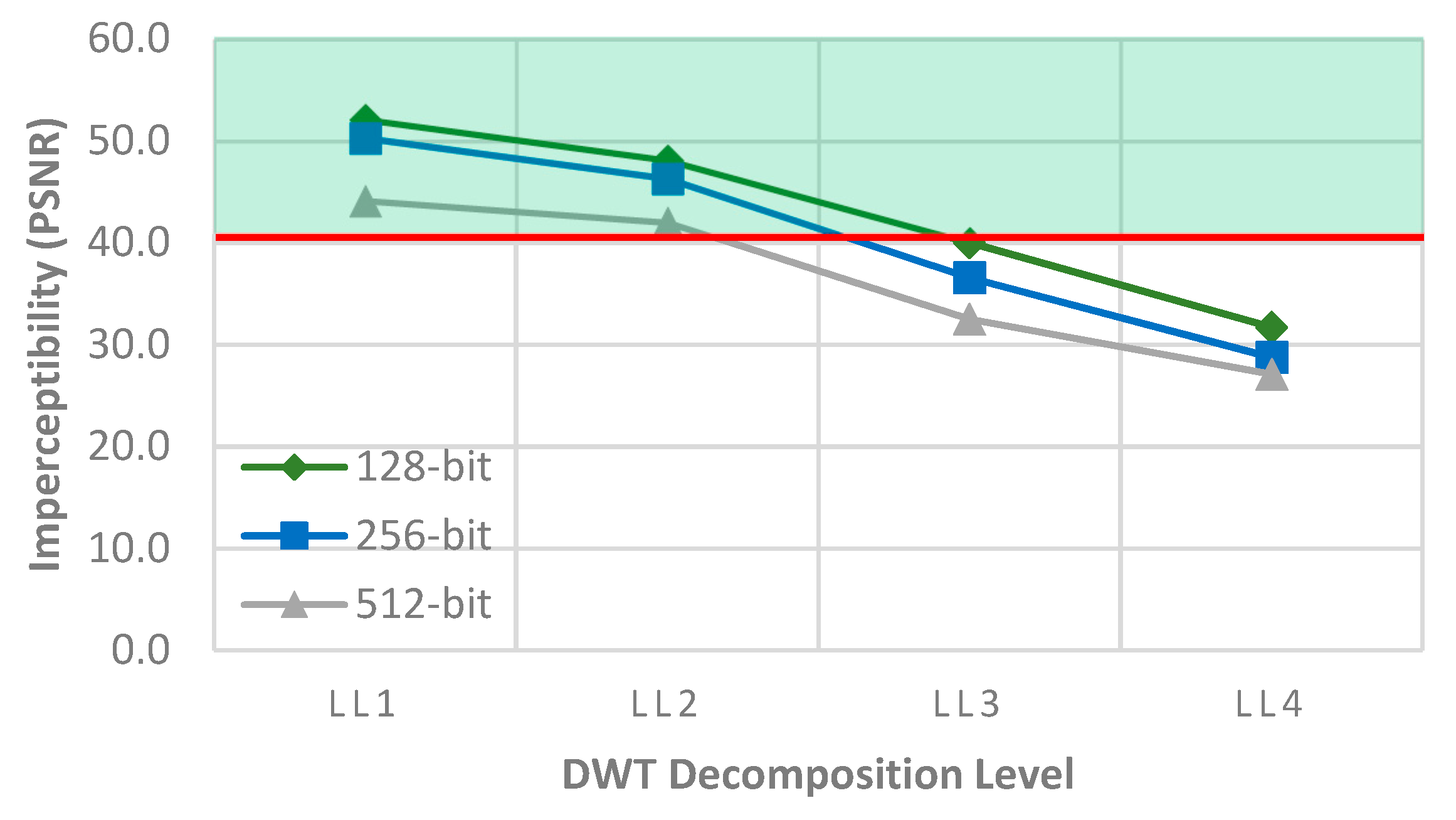
- In the proposed scheme, the 2DWT is selected based on the analysis of the trade-off between the imperceptibility and embedding capacity at various levels of decomposition. A large enough embedding capacity for the acceptable security of the watermarked image is also ensured.
- A technique is introduced to utilize the same random bit sequence as the cryptographic key and watermark for better security and convenience.
- The bit correction rate outperforms those of existing methods under different types of image-processing attacks on watermarked images.
2. Related Work
3. Proposed Scheme
3.1. Selection of the Distinct Embedding Region
3.2. Watermark Embedding Process
- Step 1
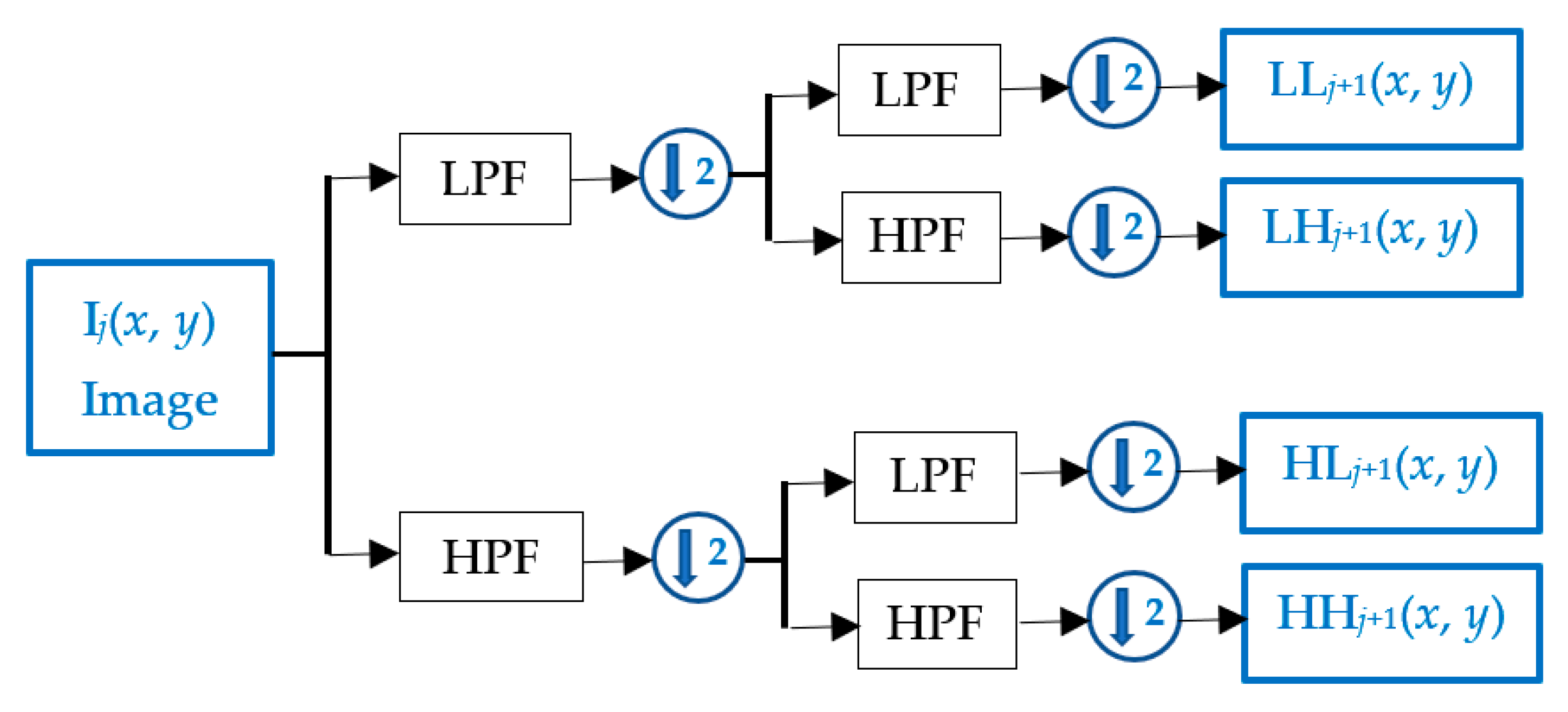
- 2DWT of the host image (I) could be obtained by two subsequent DWT decompositions. The first DWT is applied to I to create four different frequency sub-bands: LL1, LH1, HL1, and HH1. DWT is then applied again to the LL1 frequency coefficients matrix to obtain a lower frequency sub-band (LL2). The size of the LL2 sub-band is m/4 × m/4. The transformation is defined as follows:
- Step 2
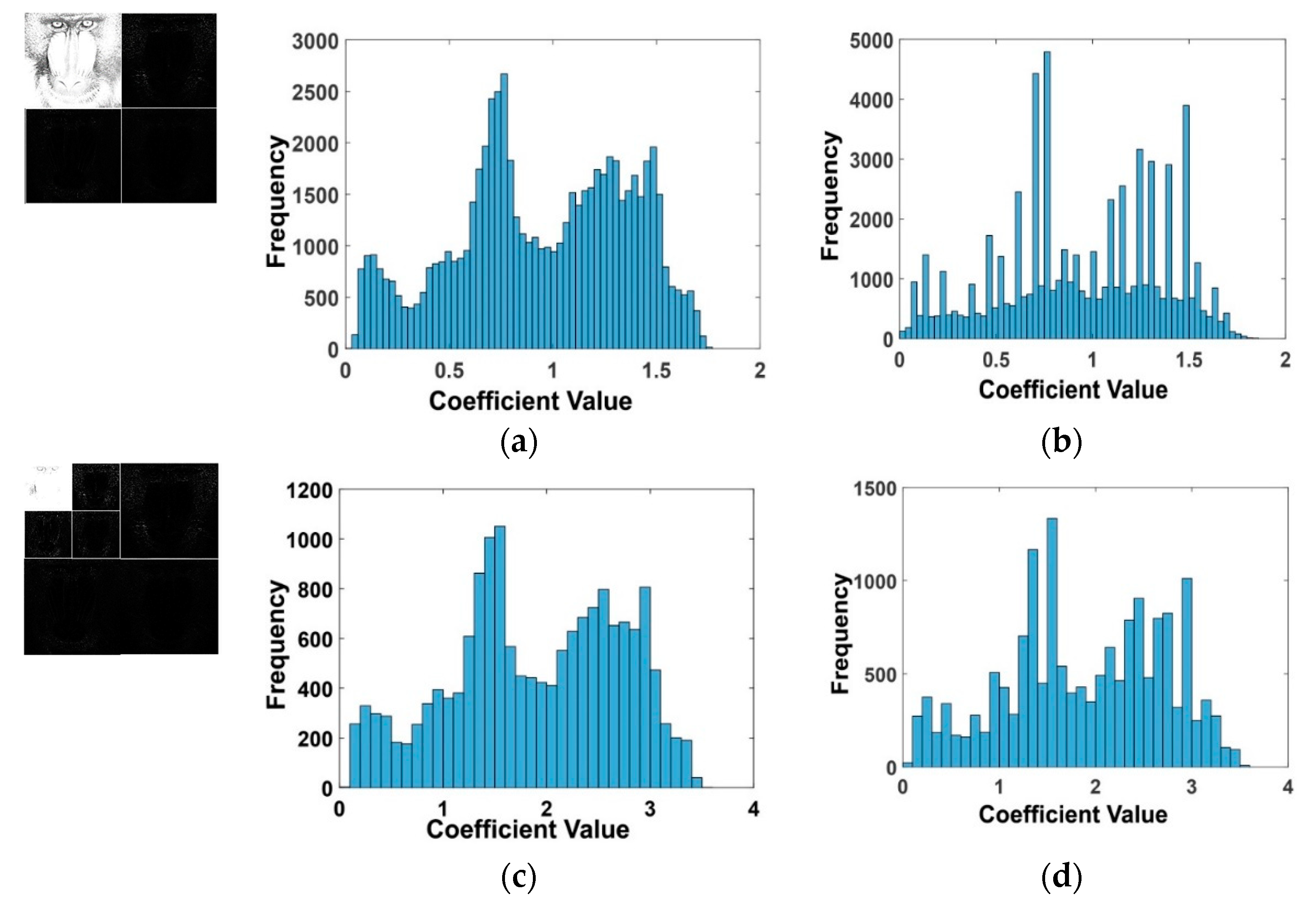
- The lowest frequency sub-band (LL2) is selected to carry the watermark bits. Here, a vector is generated from the sub-band coefficient by using the zig-zag scanning operation [51]. The resultant vector coefficient is denoted vn, where n ≤ m/4; n × n is the size of the LL2 sub-band.
- Step 3
- Vector vn is split into two parallel vectors v1 and v2 according to their positions on vector coefficients. Here, odd coefficients are stored in vector v1, and even coefficients are stored in vector v2:where k = 1,..., n.
- Step 4
- DCT is applied to each split vector (v1, v2) to produce two corresponding vectors v1dct = DCT(v1) and v2dct = DCT(v2), respectively.
- Step 5
- A unified random bit sequence is created for watermarking and random position selection. The length of the sequence W = {1, −1}z is z, which is less than or equal to the size of the LL2 matrix (i.e., z ≤ m/4). To embed the i-th bit of the sequence, a random position j(1 ≤ j ≤ m/4) is selected using W as a seed. The watermark is embedded as follows:
- Step 6
- Inverse DCT is applied to vectors v1w and v2w to obtain v′1w = DCT−1 (v1w) and v′2w = DCT−1 (v2w), respectively. The two vectors are merged to a single vector, which is the inverse operation of Step 3 (i.e., embedding). Finally, the inverse zig-zig operation is applied to create a two-dimensional image matrix from a one-dimensional vector. This process is expressed as follows:
- Step 7
- To reconstruct the final watermarked image, two of the inverse DWT operations are applied using LL2w (in place of LL2) with other sub-band sets. The operations for the final watermarked image Iw are expressed as follows:
3.3. Extraction Process
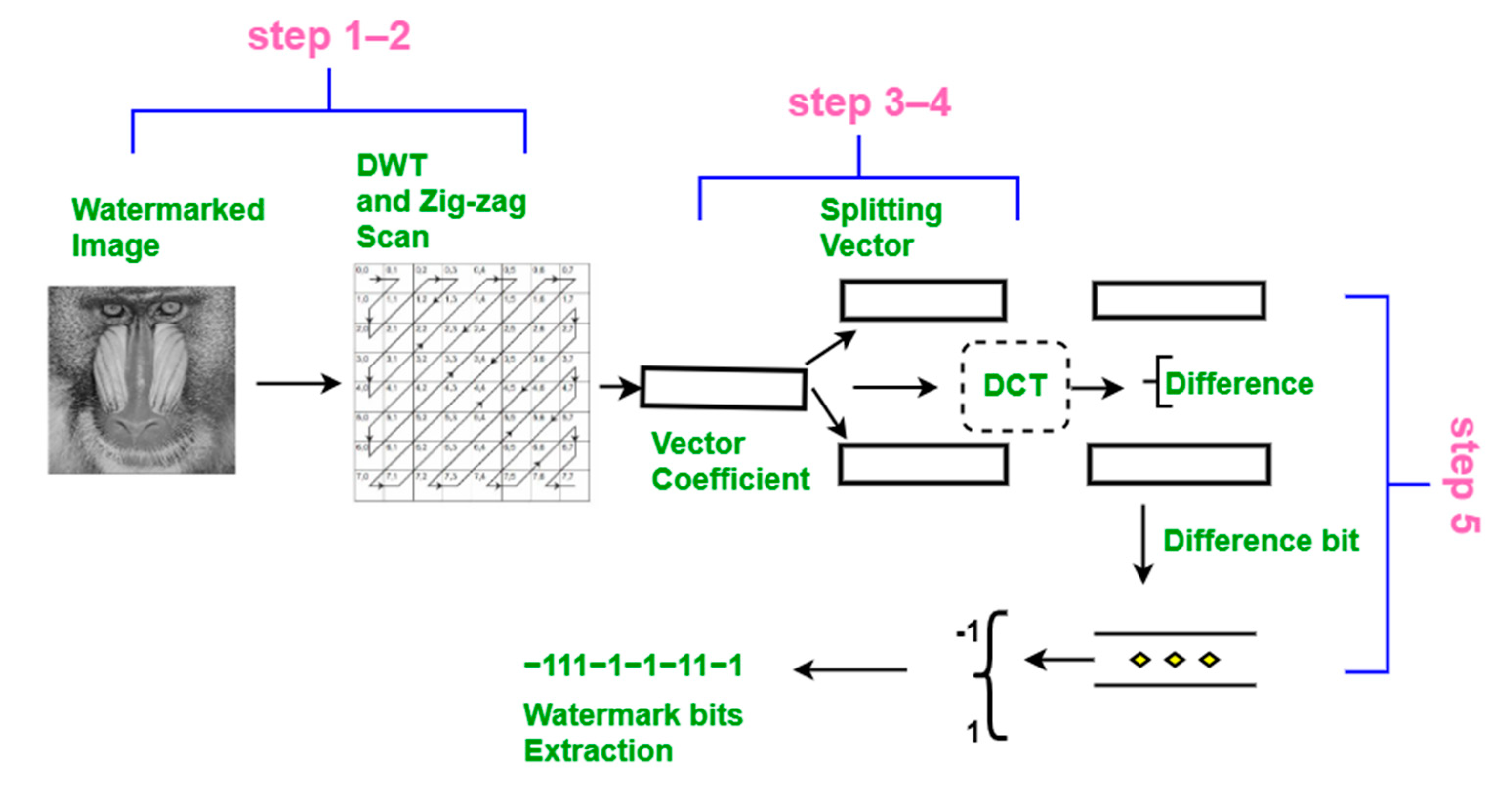
- Steps 1–4
- These steps are the same as the embedding process (Steps 1–4). Here, sub-vectors v1w and v2w are obtained after completing Step 4.
- Step 5
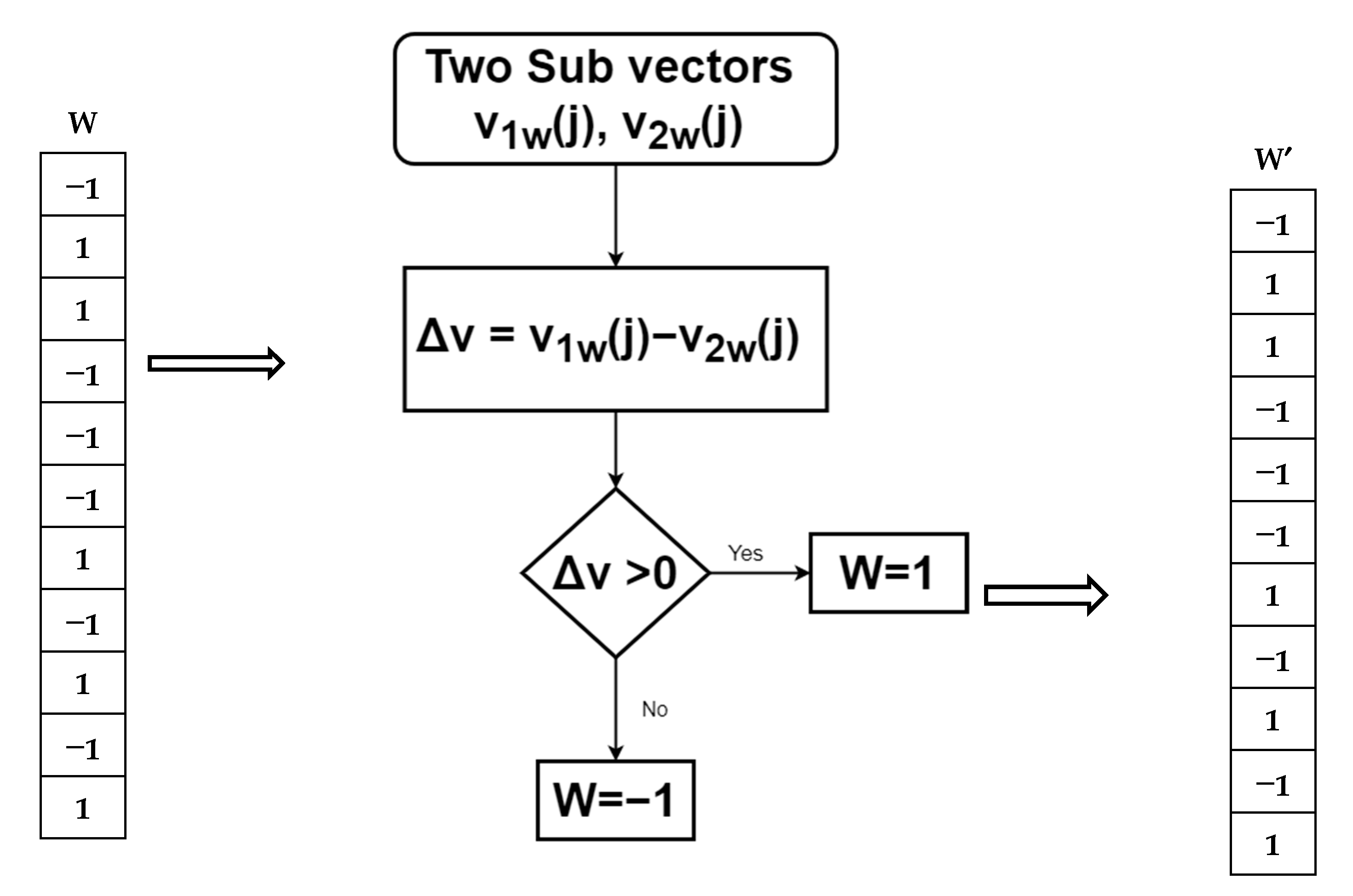
- The two sub-vectors are subtracted from each other, and the difference is denoted Δv, where Δv = v1w(j) − v2w(j) = 2W. As seed (W) is known, we can calculate the random position (j) from the seed. Using a threshold on Δv, we can then extract the watermark bits W’ (Figure 6). Here, values less than 0 are extracted as −1, and the positive values are extracted as 1. Note that this extraction process is blind and does not require the original host image to recover the watermarked bits.
3.4. Computing Complexity
4. Experiments
4.1. Performance Metrics
4.2. Effect of Gain Factor
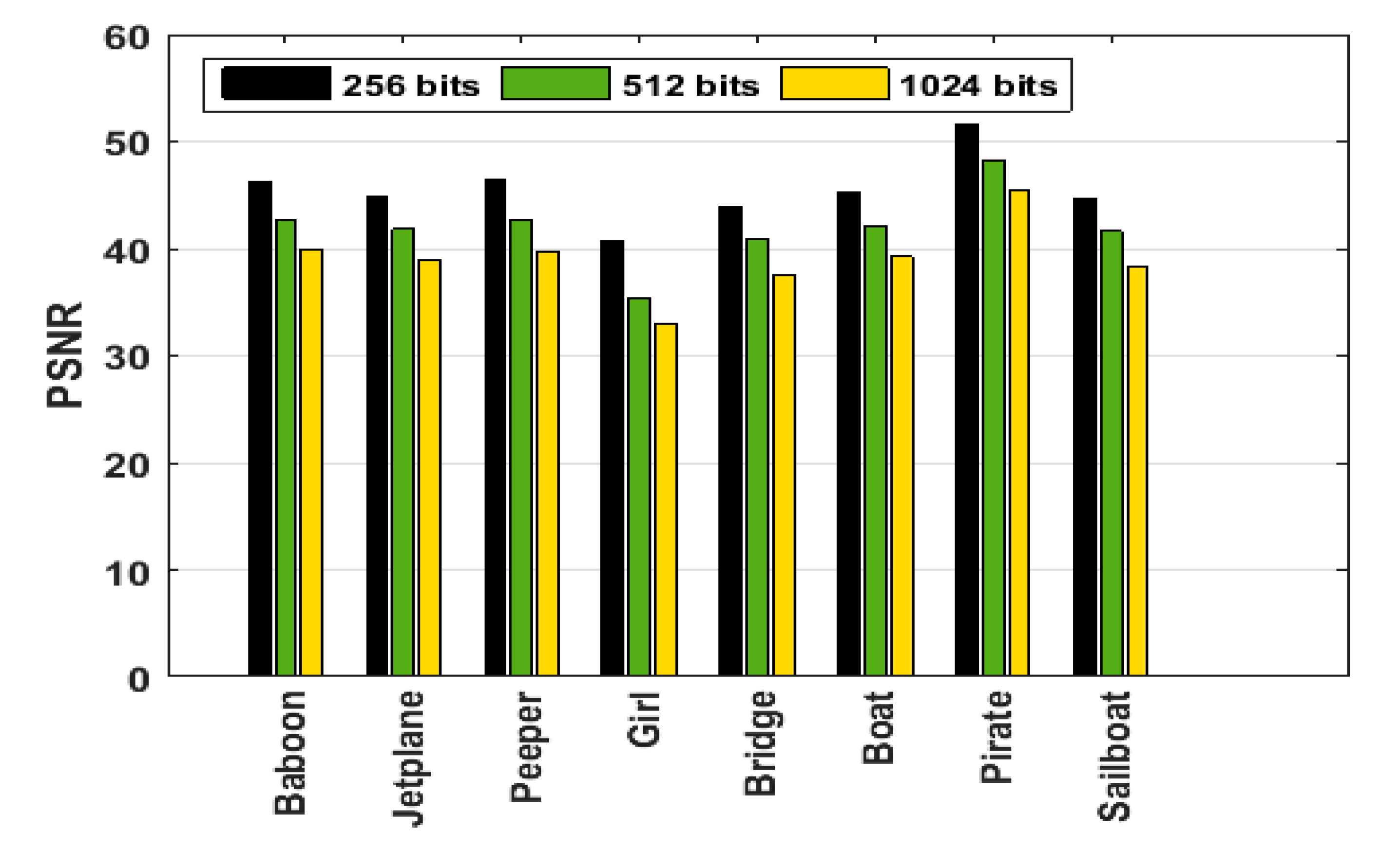
4.3. Embedding Capacity
5. Results and Discussions
5.1. Resistance to JPEG Compression Attacks
5.2. Robustness against Common Noise Attacks
5.3. Robustness against Image Enhancement Processes
5.4. Robustness against Cropping and Geometrical Attacks
5.5. Robustness against Different Filtering Operations
5.6. Comparison with Other Methods
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Giri, K.J.; Quadri SM, K.; Bashir, R.; Bhat, J.I. DWT Based Color Image Watermarking: A Review. Multimed. Tools Appl. 2020, 79, 32881–32895. [Google Scholar] [CrossRef]
- Soltani Panah, A.; Van Schyndel, R.; Sellis, T.; Bertino, E. On the Properties of Non-Media Digital Watermarking: A Review of State of the Art Techniques. IEEE Access 2016, 4, 2670–2704. [Google Scholar] [CrossRef]
- Tao, H.; Chongmin, L.; Mohamad Zain, J.; Abdalla, A.N. Robust Image Watermarking Theories and Techniques: A Review. J. Appl. Res. Technol. 2014, 12, 122–138. [Google Scholar] [CrossRef] [Green Version]
- Chetan, K.R.; Nirmala, S. An Efficient and Secure Robust Watermarking Scheme for Document Images Using Integer Wavelets and Block Coding of Binary Watermarks. J. Inf. Secur. Appl. 2015, 24–25, 13–24. [Google Scholar] [CrossRef]
- Hsu, L.-Y.; Hu, H.-T. Blind Image Watermarking via Exploitation of Inter-Block Prediction and Visibility Threshold in DCT Domain. J. Vis. Commun. Image Represent. 2015, 32, 130–143. [Google Scholar] [CrossRef]
- Hernandez, J.R.; Amado, M.; Perez-Gonzalez, F. DCT-Domain Watermarking Techniques for Still Images: Detector Performance Analysis and a New Structure. IEEE Trans. Image Process. 2000, 9, 55–68. [Google Scholar] [CrossRef] [Green Version]
- Cox, I.J.; Miller, M.L.; Bloom, J.A.; Fridrich, J.; Kalker, T. Watermarking with Side Information. In Digital Watermarking and Steganography; Elsevier: Amsterdam, The Netherlands, 2008; pp. 137–182. ISBN 978-0-12-372585-1. [Google Scholar]
- Roy, S.; Pal, A.K. A Blind DCT Based Color Watermarking Algorithm for Embedding Multiple Watermarks. AEU Int. J. Electron. Commun. 2017, 72, 149–161. [Google Scholar] [CrossRef]
- Moosazadeha, M.; Ekbatanifard, G. An Improved Robust Image Watermarking Method Using DCT and YCoCg-R Color Space. Optik 2017, 140, 975–988. [Google Scholar] [CrossRef]
- Su, Q.; Niu, Y.; Wang, G.; Jia, S.; Yue, J. Color Image Blind Watermarking Scheme Based on QR Decomposition. Signal. Process. 2014, 94, 219–235. [Google Scholar] [CrossRef]
- Chen, S.T.; Huang, H.N.; Kung, W.M.; Hsu, C.Y. Optimization-Based Image Watermarking with Integrat-Edquantization Embedding in the Wavelet-Domain. Multimed. Tools Appl. 2016, 75, 5493–5511. [Google Scholar] [CrossRef]
- Hsieh, M.-S.; Tseng, D.-C.; Huang, Y.-H. Hiding Digital Watermarks Using Multiresolution Wavelettransform. IEEE Trans Indust. Electron. 2001, 48, 875–882. [Google Scholar] [CrossRef] [Green Version]
- Kalra, G.S.; Talwar, R.; Sadawarti, H. Adaptive Digital Image Watermarking for Color Images In-Frequency Domain. Multimed. Tools Appl. 2015, 74, 6849–6869. [Google Scholar] [CrossRef]
- Patra, J.C.; Phua, J.E.; Bornand, C. A Novel DCT Domain CRT-Based Watermarking Scheme for Image Authentication Surviving JPEG Compression. Digit. Signal. Process. 2010, 20, 1597–1611. [Google Scholar] [CrossRef]
- Lin, S.D.; Chen, C.-F. A Robust DCT-Based Watermarking for Copyright Protection. IEEE Trans. Consum. Electron. 2000, 46, 415–421. [Google Scholar] [CrossRef]
- Lin, S.D.; Shie, S.-C.; Guo, J.Y. Improving the Robustness of DCT-Based Image Watermarking against JPEG Compression. Comput. Stand. Interfaces 2010, 32, 54–60. [Google Scholar] [CrossRef]
- Bao, P.; Ma, X. Image Adaptive Watermarking Using Wavelet Domain Singular Value Decomposition. IEEE Trans. Circuits Syst. Video Technol. 2005, 15, 96–102. [Google Scholar] [CrossRef]
- Chang, C.-C.; Hu, Y.-S.; Lin, C.-C. A Digital Watermarking Scheme Based on Singular Value Decomposition. In Combinatorics, Algorithms, Probabilistic and Experimental Methodologies; Chen, B., Paterson, M., Zhang, G., Eds.; Lecture Notes in Computer Science; Springer: Berlin, Heidelberg, Germany, 2007; Volume 4614, pp. 82–93. ISBN 978-3-540-74449-8. [Google Scholar]
- Tao, P.; Eskicioglu, A.M. An Adaptive Method for Image Recovery in the DFT Domain. JMM 2006, 1, 36–45. [Google Scholar] [CrossRef]
- Mohammad, A.A. A New Digital Image Watermarking Scheme Based on Schur Decomposition. Multimed. Tools Appl. 2012, 59, 851–883. [Google Scholar] [CrossRef]
- Naderahmadian, Y.; Hosseini-Khayat, S. Fast and Robust Watermarking in Still Images Based on QR Decomposition. Multimed. Tools Appl. 2014, 72, 2597–2618. [Google Scholar] [CrossRef]
- Benoraira, A.; Benmahammed, K.; Boucenna, N. Blind Image Watermarking Technique Based on Differential Embedding in DWT and DCT Domains. EURASIP J. Adv. Signal. Process. 2015, 2015, 55. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Y.; Campisi, P.; Kundur, D. Dual Domain Watermarking for Authentication and Compression of Cultural Heritage Images. IEEE Trans. Image Process. 2004, 13, 430–448. [Google Scholar] [CrossRef]
- Yaghmaee, F.; Jamzad, M. Estimating Watermarking Capacity in Gray Scale Images Based on Image Complexity. EURASIP J. Adv. Signal. Process. 2010, 2010, 851920. [Google Scholar] [CrossRef] [Green Version]
- Qadir, G.; Zhao, X.; Ho, A.T.S. Estimating JPEG2000 Compression for Image Forensics Using Benford’s Law; Schelkens, P., Ebrahimi, T., Cristóbal, G., Truchetet, F., Saarikko, P., Eds.; International Society for Optics and Photonics: Brussels, Belgium, 2010; p. 77230J. [Google Scholar]
- Su, Q.; Niu, Y.; Wang, Q.; Sheng, G. A Blind Color Image Watermarking Based on DC Component in the Spatial Domain. Optik 2013, 124, 6255–6260. [Google Scholar] [CrossRef]
- Loan, N.A.; Hurrah, N.N.; Parah, S.A.; Lee, J.W.; Sheikh, J.A.; Bhat, G.M. Secure and Robust Digital Image Watermarking Using Coefficient Differencing and Chaotic Encryption. IEEE Access 2018, 6, 19876–19897. [Google Scholar] [CrossRef]
- Ahmad, J.; Khan, M.A.; Hwang, S.O.; Khan, J.S. A Compression Sensing and Noise-Tolerant Image Encryption Scheme Based on Chaotic Maps and Orthogonal Matrices. Neural Comput Applic. 2017, 28, 953–967. [Google Scholar] [CrossRef]
- Dowling, J.; Planitz, B.M.; Maeder, A.J.; Du, J.; Pham, B.; Boyd, C.; Chen, S.; Bradley, A.P.; Crozier, S. A Comparison of DCT and DWT Block Based Watermarking on Medical Image Quality. In Digital Watermarking; Shi, Y.Q., Kim, H.-J., Katzenbeisser, S., Eds.; Lecture Notes in Computer Science; Springer: Berlin, Heidelberg, Germany, 2008; Volume 5041, pp. 454–466. ISBN 978-3-540-92237-7. [Google Scholar]
- Kahlessenane, F.; Khaldi, A.; Kafi, R.; Euschi, S. A DWT Based Watermarking Approach for Medical Image Protection. J. Ambient Intell. Hum. Comput 2021, 12, 2931–2938. [Google Scholar] [CrossRef]
- Fares, K.; Khaldi, A.; Redouane, K.; Salah, E. DCT & DWT Based Watermarking Scheme for Medical Information Security. Biomed. Signal. Process. Control. 2021, 66, 102403. [Google Scholar] [CrossRef]
- Yap, P.-T.; Paramesran, R. Local Watermarks Based on Krawtchouk Moments. In Proceedings of the 2004 IEEE Region 10 Conference TENCON 2004, Chiang Mai, Thailand, 21–24 November 2004; IEEE: New York, NY, USA, 2004; Volume 2, pp. 73–76. [Google Scholar]
- Radeaf, H.S.; Mahmmod, B.M.; Abdulhussain, S.H.; Al-Jumaeily, D. A Steganography Based on Orthogonal Moments. In Proceedings of the International Conference on Information and Communication Technology, Baghdad, Iraq, 15–16 April 2019; ACM Press: New York, NY, USA, 2019; pp. 147–153. [Google Scholar]
- Qi, W.; Liu, Y.; Guo, S.; Wang, X.; Guo, Z. An Adaptive Visible Watermark Embedding Method Based on Region Selection. Secur. Commun. Netw. 2021, 2021, 1–11. [Google Scholar] [CrossRef]
- Vahedi, E.; Zoroofi, R.A.; Shiva, M. Toward a New Wavelet-Based Watermarking Approach for Color Images Using Bio-Inspired Optimization Principles. Digit. Signal. Process. 2012, 22, 153–162. [Google Scholar] [CrossRef]
- Mohananthini, N.; Yamuna, G. Comparison of Multiple Watermarking Techniques Using Genetic Algorithms. J. Electr. Syst. Inf. Technol. 2016, 3, 68–80. [Google Scholar] [CrossRef]
- Dong, C.; Li, J.; Huang, M.; Bai, Y. The Medical Image Watermarking Algorithm with Encryption by DCT and Logistic. In Proceedings of the 2012 Ninth Web Information Systems and Applications Conference, Haikou, China, 16–18 November 2012; IEEE: New York, NY, USA, 2012; pp. 119–124. [Google Scholar]
- Golabi, S.; Sadegh Helfroush, M.; Danyali, H.; Owjimehr, M. Robust Watermarking against Geometric Attacks Using Partial Calculation of Radial Moments and Interval Phase Modulation. Inf. Sci. 2014, 269, 94–105. [Google Scholar] [CrossRef]
- Fares, K.; Amine, K.; Salah, E. A Robust Blind Color Image Watermarking Based on Fourier Transform Domain. Optik 2020, 208, 164562. [Google Scholar] [CrossRef]
- Zhang, X.; Su, Q.; Yuan, Z.; Liu, D. An Efficient Blind Color Image Watermarking Algorithm in Spatial Domain Combining Discrete Fourier Transform. Optik 2020, 219, 165272. [Google Scholar] [CrossRef]
- Singh, D.; Singh, S.K. DWT-SVD and DCT Based Robust and Blind Watermarking Scheme for Copyright Protection. Multimed Tools Appl 2017, 76, 13001–13024. [Google Scholar] [CrossRef]
- Fan, D.; Li, Y.; Gao, S.; Chi, W.; Lv, C. A Novel Zero Watermark Optimization Algorithm Based on Gabor Transform and Discrete Cosine Transform. Concurr. Comput. Pr. Exper 2020, e5689. [Google Scholar] [CrossRef]
- Luo, Y.; Li, L.; Liu, J.; Tang, S.; Cao, L.; Zhang, S.; Qiu, S.; Cao, Y. A Multi-Scale Image Watermarking Based on Integer Wavelet Transform and Singular Value Decomposition. Expert Syst. Appl. 2021, 168, 114272. [Google Scholar] [CrossRef]
- Barker, E. Recommendation for Key Management: Part. 1—General; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020. [Google Scholar] [CrossRef]
- Abdulrahman, A.K.; Ozturk, S. A Novel Hybrid DCT and DWT Based Robust Watermarking Algorithm for Color Images. Multimed. Tools Appl. 2019, 78, 17027–17049. [Google Scholar] [CrossRef]
- Proakis, J.G.; Manolakis, D.G. Digital Signal. Processing: Principles, Algorithms, and Applications, 3rd ed.; Prentice Hall: Upper Saddle River, NJ, USA, 1996; ISBN 978-0-13-373762-2. [Google Scholar]
- Proakis, J.G.; Manolakis, D.G. Digital Signal. Processing, 4th ed.; Pearson Prentice Hall: Upper Saddle River, NJ, USA, 2007; ISBN 978-0-13-187374-2. [Google Scholar]
- Nikolaidis, A.; Pitas, I. Asymptotically Optimal Detection for Additive Watermarking in the DCT and DWT Domains. IEEE Trans. Image Process. 2003, 12, 563–571. [Google Scholar] [CrossRef]
- Parah, S.A.; Sheikh, J.A.; Loan, N.A.; Bhat, G.M. Robust and Blind Watermarking Technique in DCT Domain Using Inter-Block Coefficient Differencing. Digit. Signal. Process. 2016, 53, 11–24. [Google Scholar] [CrossRef]
- Chang, T.-J.; Pan, I.-H.; Huang, P.-S.; Hu, C.-H. A Robust DCT-2DLDA Watermark for Color Images. Multimed. Tools Appl. 2019, 78, 9169–9191. [Google Scholar] [CrossRef]
- Bhatnagar, G.; Wu, Q.M.J. A New Robust and Efficient Multiple Watermarking Scheme. Multimed. Tools Appl. 2015, 74, 8421–8444. [Google Scholar] [CrossRef]
- Huang, H.-C.; Chu, S.-C.; Pan, J.-S.; Huang, C.-Y.; Liao, B.-Y. Tabu Search Based Multi-Watermarks Embedding Algorithm with Multiple Description Coding. Inf. Sci. 2011, 181, 3379–3396. [Google Scholar] [CrossRef]
- Roimela, K.; Aarnio, T.; Itäranta, J. Efficient High Dynamic Range Texture Compression. In Proceedings of the 2008 Symposium on Interactive 3D Graphics and Games, Redwood City, CA, USA, 15–17 February 2008; ACM Press: New York, NY, USA, 2008; p. 207. [Google Scholar]
- Ernawan, F.; Kabir, M.N. A Robust Image Watermarking Technique with an Optimal DCT-Psychovisual Threshold. IEEE Access 2018, 6, 20464–20480. [Google Scholar] [CrossRef]
- Feng, L.P.; Zheng, L.B.; Cao, P. A DWT-DCT Based Blind Watermarking Algorithm for Copyright Protection. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; IEEE: New York, NY, USA, 2010; pp. 455–458. [Google Scholar]
- Jiang, Y.; Zhang, Y.; Pei, W.; Wang, K. Adaptive Spread Transform QIM Watermarking Algorithm Based on Improved Perceptual Models. AEU Int. J. Electron. Commun. 2013, 67, 690–696. [Google Scholar] [CrossRef]
- Lin, W.-H.; Horng, S.-J.; Kao, T.-W.; Fan, P.; Lee, C.-L.; Pan, Y. An Efficient Watermarking Method Based on Significant Difference of Wavelet Coefficient Quantization. IEEE Trans. Multimed. 2008, 10, 746–757. [Google Scholar] [CrossRef]
- Zermi, N.; Khaldi, A.; Kafi, R.; Kahlessenane, F.; Euschi, S. A DWT-SVD Based Robust Digital Watermarking for Medical Image Security. Forensic Sci. Int. 2021, 320, 110691. [Google Scholar] [CrossRef]
- Mardolkar, S.B.; Shenvi, N. A Blind Digital Watermarking Algorithm Based on DWT-DCT Transformation. Int. J. Innov. Res. Electr. Electron. Instrum. Control. Eng. 2016, 4, 212–216. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, Y.; Sun, Y. Digital Watermarking Based on Joint DWT–DCT and OMP Reconstruction. Circuits Syst Signal. Process. 2019, 38, 5135–5148. [Google Scholar] [CrossRef]
- Lang, J.; Zhang, Z. Blind Digital Watermarking Method in the Fractional Fourier Transform Domain. Opt. Lasers Eng. 2014, 53, 112–121. [Google Scholar] [CrossRef]
- Guo, J.; Zheng, P.; Huang, J. Secure Watermarking Scheme against Watermark Attacks in the Encrypted Domain. J. Vis. Commun. Image Represent. 2015, 30, 125–135. [Google Scholar] [CrossRef]
- Moosazadeh, M.; Ekbatanifard, G. A New DCT-Based Robust Image Watermarking Method Using Teaching-Learning-Based Optimization. J. Inf. Secur. Appl. 2019, 47, 28–38. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. An Improved DWT-SVD Domain Watermarking for Medical Information Security. Comput. Commun. 2020, 152, 72–80. [Google Scholar] [CrossRef]
- Hu, H.-T.; Chang, J.-R.; Hsu, L.-Y. Robust Blind Image Watermarking by Modulating the Mean of Partly Sign-Altered DCT Coefficients Guided by Human Visual Perception. AEU Int. J. Electron. Commun. 2016, 70, 1374–1381. [Google Scholar] [CrossRef]
- Islam, M.S. Heartbeat Biometrics for Remote Authentication Using Sensor Embedded Computing Devices. Int. J. Distrib. Sens. Netw. 2015, 11, 549134. [Google Scholar] [CrossRef] [Green Version]
- Alharbi, S.; Islam, M.S.; Alahmadi, S. Time-Invariant Cryptographic Key Generation from Cardiac Signals. In Proceedings of the Future Technologies Conference (FTC), San Francisco, CA, USA, 24–25 October 2019; Arai, K., Bhatia, R., Kapoor, S., Eds.; Advances in Intelligent Systems and Computing; Springer International Publishing: Cham, Switzerland, 2020; Volume 1070, pp. 338–352, ISBN 978-3-030-32522-0. [Google Scholar]




| Step | Main Operation | Embedding Process | Extraction Process |
|---|---|---|---|
| 1 | DWT | O(n) | O(n) |
| 2 | Zig-zag | O(n) | O(n) |
| 3 | Split vector | O(n) | O(n) |
| 4 | DCT | O(n) | O(n) |
| 5 | Watermark embedding/extraction | O(z) | O(z) |
| 6 | Inverse DCT & Zig-zag | O(n) | - |
| 7 | Inverse DWT | O(n) | - |
| Total | O(n) + O(z) | O(n) + O(z) | |
| Image | Image Size | Embedding Time (s) | Extraction Time (s) |
|---|---|---|---|
| Girl | 256 × 256 | 0.1716 | 0.1223 |
| Peeper | 512 × 512 | 0.2265 | 0.1448 |
| Jet-plane | 512 × 512 | 0.2267 | 0.1488 |
| Baboon | 512 × 512 | 0.2313 | 0.1479 |
| Sailboat | 512 × 512 | 0.2251 | 0.1471 |
| Boat | 512 × 512 | 0.2311 | 0.1471 |
| Pirate | 1024 × 1024 | 0.4455 | 0.2457 |
| Average | 0.2511 | 0.1577 |
| α = 0.1 | α = 0.2 | α = 0.3 | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Image | PSNR | SSIM | BCR | PSNR | SSIM | BCR | PSNR | SSIM | BCR |
| Peeper | 46.8532 | 0.9903 | 100 | 41.0763 | 0.9637 | 100 | 37.5991 | 0.9276 | 100 |
| Jet-plane | 44.9943 | 0.9877 | 100 | 41.2936 | 0.9603 | 100 | 37.4736 | 0.9153 | 100 |
| Baboon | 45.6986 | 0.9960 | 100 | 40.0648 | 0.9834 | 100 | 37.3289 | 0.9712 | 100 |
| Girl | 40.6585 | 0.9583 | 100 | 35.2580 | 0.8834 | 100 | 31.4715 | 0.7825 | 100 |
| Sailboat | 46.7466 | 0.9917 | 100 | 40.9721 | 0.9723 | 100 | 37.3362 | 0.9418 | 100 |
| Boat | 46.5594 | 0.9921 | 100 | 41.1118 | 0.9731 | 100 | 37.5301 | 0.9457 | 100 |
| Pirate | 52.7633 | 0.9978 | 100 | 47.1427 | 0.9921 | 100 | 43.5626 | 0.9829 | 100 |
| Image | Q 10 | Q 20 | Q 30 | Q 40 | Q 50 | Q 60 | Q 70 |
|---|---|---|---|---|---|---|---|
| Girl | 77.451 | 95.686 | 100 | 100 | 100 | 100 | 100 |
| Peeper | 89.124 | 85.458 | 99.986 | 100 | 100 | 100 | 100 |
| Jet-plane | 84.256 | 87.213 | 100 | 100 | 100 | 100 | 100 |
| Bridge | 90.945 | 100 | 100 | 100 | 100 | 100 | 100 |
| Baboon | 87.2541 | 99.845 | 100 | 100 | 100 | 100 | 100 |
| Pirate | 88.4575 | 98.356 | 100 | 100 | 100 | 100 | 100 |
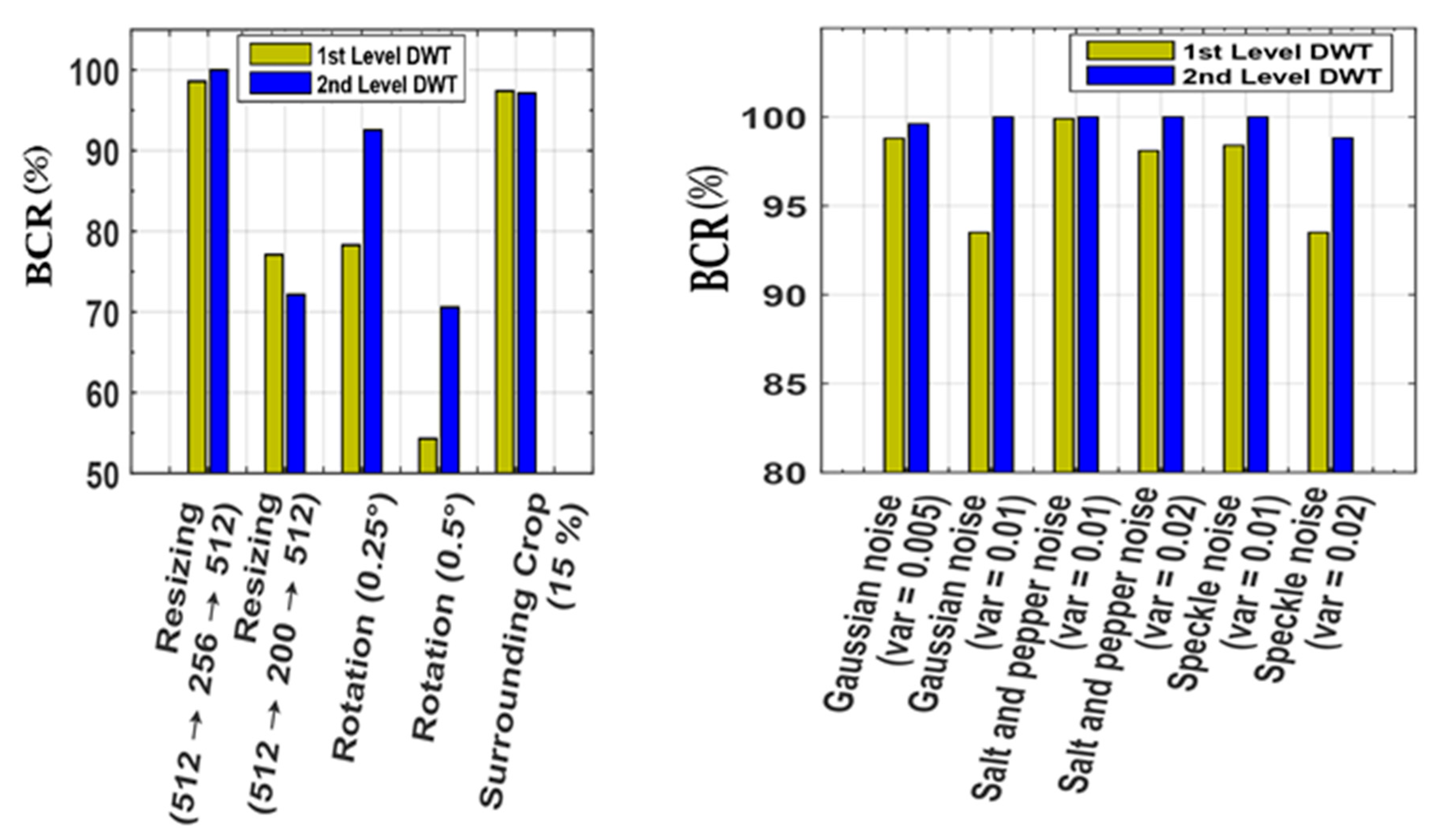
| Image | Gaussian Noise (var = 0.0005) | Gaussian Noise (var = 0.001) | Speckle Noise (var = 0.01) | Speckle Noise (var = 0.02) | Salt and Pepper Noise (var = 0.01) | Salt and Pepper Noise (var = 0.02) |
|---|---|---|---|---|---|---|
| Baboon | 99.6078 | 100 | 100 | 100 | 100 | 100 |
| Jet-plane | 99.5078 | 99.6142 | 100 | 98.82 | 100 | 100 |
| Bridge | 99.2157 | 100 | 100 | 100 | 100 | 100 |
| Pirate | 99.8876 | 100 | 100 | 100 | 100 | 100 |
| Peppers | 100 | 99.6125 | 100 | 100 | 100 | 100 |
| Image | Bit-Plane Removal (5 bits) | Bit-Plane Removal (6 bits) | Gamma Correction (0.5) | Gamma Correction (1.5) | Histogram Equalization | Laplacian Sharpening |
|---|---|---|---|---|---|---|
| Baboon | 99.5464 | 97.1247 | 100 | 100 | 100 | 100 |
| Jet-plane | 99.2154 | 95.2451 | 100 | 100 | 100 | 100 |
| Bridge | 100 | 93.1212 | 100 | 100 | 100 | 100 |
| Pirate | 100 | 96.6647 | 100 | 100 | 100 | 100 |
| Peppers | 99.987 | 100 | 100 | 100 | 100 | 100 |
| Boat | 98.451 | 99.4545 | 100 | 100 | 100 | 100 |
| Image | Rotation (0.25°) | Rotation (0.5°) | Resizing (512 → 256 → 512) | Resizing (512 → 200 → 512) | Surrounding Crop (15%) |
|---|---|---|---|---|---|
| Baboon | 92.549 | 70.588 | 100 | 72.1569 | 97.1201 |
| Jet-plane | 99.607 | 80.784 | 100 | 60.3922 | 97.0214 |
| Bridge | 97.647 | 75.686 | 100 | 69.3725 | 99.1041 |
| Peppers | 100 | 83.529 | 100 | 71.3725 | 98.5102 |
| Boat | 97.254 | 77.647 | 100 | 72.1569 | 98.8564 |
| Tree | 100 | 90.5882 | 100 | 65.1245 | 96.6548 |
| SSIM | BCR | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Images | Gaussian Filter (5 × 5) var = 1.5 | Gaussian Filter (5 × 5) var = 1 | Median Filter (3 × 3) | Wiener Filter (3 × 3) | Average Filter (3 × 3) | Gaussian Filter (5 × 5) var = 1.5 | Gaussian Filter (5 × 5) var = 1 | Median Filter (3 × 3) | Wiener Filter (3 × 3) | Average Filter (3 × 3) |
| Girl | 0.8848 | 0.8843 | 0.8785 | 0.8809 | 0.8769 | 100 | 100 | 100 | 100 | 100 |
| Baboon | 0.988 | 0.9861 | 0.9873 | 0.9875 | 0.9875 | 100 | 100 | 100 | 100 | 100 |
| Jet | 0.9645 | 0.957 | 0.9589 | 0.9567 | 0.9574 | 100 | 100 | 100 | 100 | 100 |
| Bridge | 0.9853 | 0.9828 | 0.986 | 0.984 | 0.9842 | 100 | 100 | 100 | 100 | 100 |
| Pirate | 0.9912 | 0.9906 | 0.9911 | 0.9898 | 0.9906 | 100 | 100 | 100 | 100 | 100 |
| Pepper | 0.9658 | 0.966 | 0.9673 | 0.9681 | 0.9668 | 100 | 100 | 100 | 100 | 100 |
| Boat | 0.9698 | 0.9666 | 0.9683 | 0.9711 | 0.9695 | 99.216 | 100 | 100 | 100 | 100 |
| Tree | 0.8965 | 0.9666 | 0.9034 | 0.8964 | 0.8952 | 99.216 | 99.2157 | 100 | 100 | 99.608 |
| Attack | 1DWT | 2DWT | Attack | 1DWT | 2DWT | Attack | 1DWT | 2DWT |
|---|---|---|---|---|---|---|---|---|
| Average filter [5 × 5] | 51.0763 | 99.6086 | Wiener filter [5 × 5] | 79.4521 | 100 | Median Filter [5 × 5] | 57.1429 | 97.456 |
| Average filter [7 × 7] | 17.2211 | 89.0196 | Wiener filter [6 × 6] | 73.1898 | 98.4344 | Median Filter [6 × 6] | 38.7476 | 91.9765 |
| Average filter [6 × 6] | 31.5068 | 90.6067 | Wiener filter [7 × 7] | 70.6458 | 95.3033 | Median Filter [7 × 7] | 24.0705 | 82.5832 |
| Attack | Zermi et al., 2021 [58] | Fares et al., 2021 [31] | Ferda et al., 2018 [54] | Feng et al., 2010 [55] | Lin et al., 2008 [57] | Jiang et al., 2013 [56] | Mardolkar et al., 2016 [59] | Zhang et al., 2019 [60] | Fan et al., 2020 [42] | Proposed Method |
|---|---|---|---|---|---|---|---|---|---|---|
| JPEG compression 20 | 49.80 | 69.80 | 94.50 | 50.88 | 59.37 | 99.83 | 99.87 | 99.85 | ||
| JPEG compression 30 | 98 | 71.97 | 78.40 | 98.40 | 99.87 | 100 | ||||
| JPEG compression 40 | 92 | 83.50 | 89.20 | 100 | 76.95 | 69.85 | 99.97 | 99.90 | 100 | |
| Gamma Correction | 97 | 99.20 | 76.10 | 100 | ||||||
| Gaussian noise (0.01) | 99.06 | 87.50 | 79.50 | 70.41 | 68.26 | 99.65 | 100 | |||
| Salt and Pepper (0.01) | 99 | 99.17 | 79.98 | 81.74 | 99.84 | 100 | ||||
| Salt and Pepper (0.02) | 91 | 93.30 | 93.30 | 69.04 | 67.19 | 99.69 | 100 | |||
| Median Filter (3 × 3) | 99.01 | 97.10 | 99.20 | 99.87 | 100 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hasan, N.; Islam, M.S.; Chen, W.; Kabir, M.A.; Al-Ahmadi, S. Encryption Based Image Watermarking Algorithm in 2DWT-DCT Domains. Sensors 2021, 21, 5540. https://doi.org/10.3390/s21165540
Hasan N, Islam MS, Chen W, Kabir MA, Al-Ahmadi S. Encryption Based Image Watermarking Algorithm in 2DWT-DCT Domains. Sensors. 2021; 21(16):5540. https://doi.org/10.3390/s21165540
Chicago/Turabian StyleHasan, Nayeem, Md Saiful Islam, Wenyu Chen, Muhammad Ashad Kabir, and Saad Al-Ahmadi. 2021. "Encryption Based Image Watermarking Algorithm in 2DWT-DCT Domains" Sensors 21, no. 16: 5540. https://doi.org/10.3390/s21165540
APA StyleHasan, N., Islam, M. S., Chen, W., Kabir, M. A., & Al-Ahmadi, S. (2021). Encryption Based Image Watermarking Algorithm in 2DWT-DCT Domains. Sensors, 21(16), 5540. https://doi.org/10.3390/s21165540









