Exploiting Capture Diversity for Performance Enhancement of ALOHA-Based Multi-Static Backscattering Systems in the 6G Perspective
Abstract
:1. Introduction
1.1. Paper Contributions
- We present a framework that describes propagation phenomena and their impact on medium access control protocol dynamics. Specifically, the channel abstraction considers log-normal fading statistics and includes cascade communication links that affect both nodes’ powering and backscattering signals’ detection. To mitigate multiple access interference, we assume that channel contention is driven by a Framed Slotted ALOHA (FSA) [13] protocol and we show how propagation impairments affect detection probability and collision occurrence.
- We characterize the statistical properties of the multiple access interference in terms of Signal-to-Interference Ratio (SIR), which does not admit a closed-form representation in terms of Probability Density Function (PDF) in the proposed settings. To this aim, we approximate the SIR by means of a log-normal random variable for which we determine the unknown parameters via moment matching. The proposed approximation rationale is based on the technique described in [14] and here extended to the peculiar features of the backscattering propagation cascade channel, including nodes’ powering.
- By exploiting the proposed approximation, we are able to study the capture effect at a given receiver in terms of capture distribution. Furthermore, when exploiting the spatial diversity offered by multiple detection points we describe the concept of capture diversity that was first introduced in our prior work [11] in the context of RFID systems. In particular, we show how different samples of fading and interference processes available at different receivers can be exploited in multi-static systems to resolve simultaneous nodes’ transmissions during collision events.
- Based on the proposed framework, we study the performance of the considered multi-static architecture with focus on different parameters such as fading severity, number of deployed receivers and network topology. Moreover, we discuss the impact of FSA settings on the optimal achievable performance in the presence of capture diversity and propagation channel impairments. Specifically, we show how the capability of multi-static systems to resolve simultaneously transmitted data packets substantially reduces the optimal frame length of the FSA and definitely improves channel access performance.
1.2. Related Works
1.3. Notation
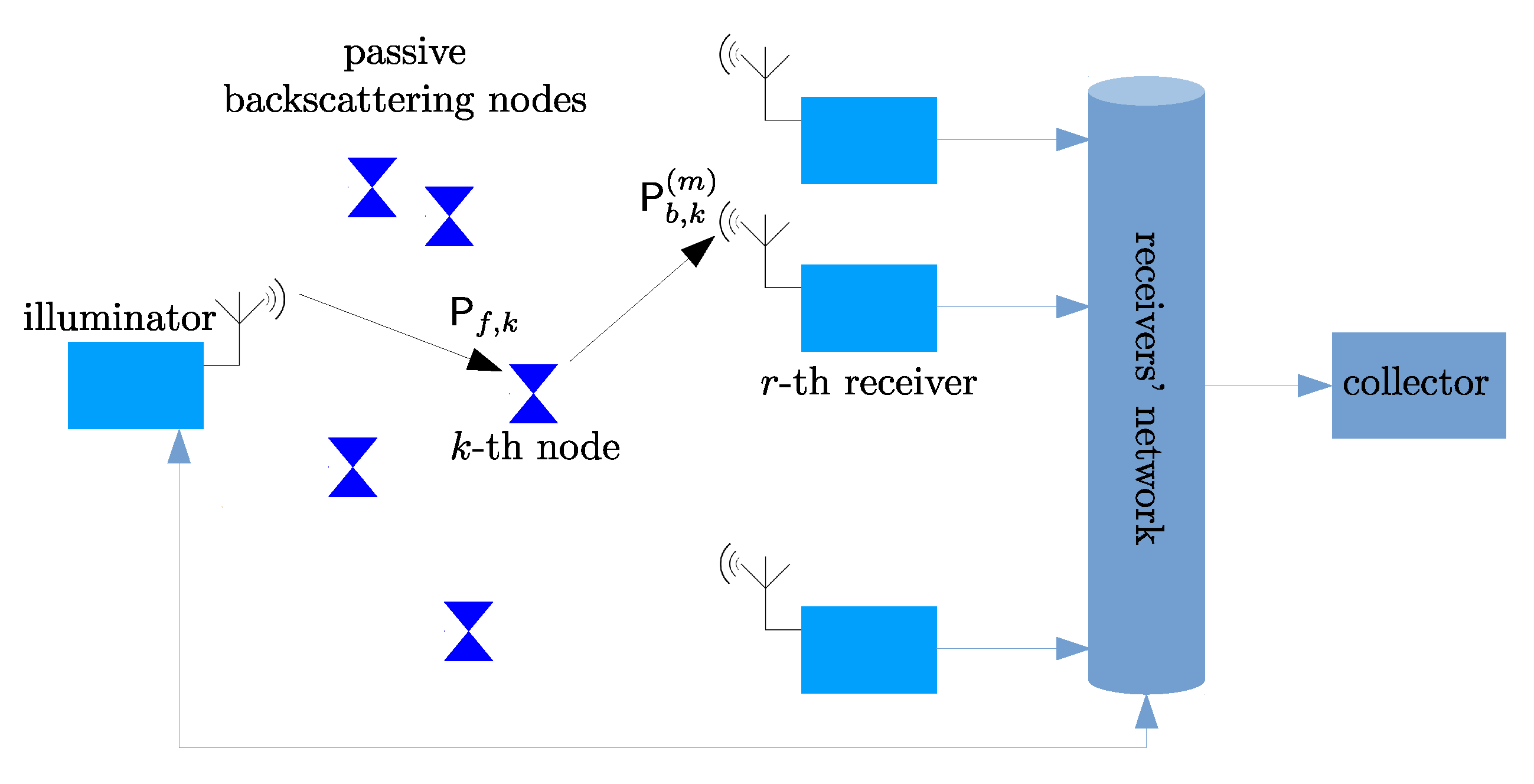
2. System Model
2.1. System Architecture
- A1
- information about the successful detection of a node’s data is available immediately at the illuminator. This can be achieved by a high speed network between the receivers and the illuminator. Nonetheless, the characterization of this high speed network is beyond the scope of this paper and is not explicitly included here;
- A2
- communication occurs over a slow varying channel, where fading is time invariant within a sufficiently long time interval;
- A3
- fading components are log-normally distributed. Although it may appear limiting, this assumption is well suited to describe different propagation phenomena, such as shadow fading and, in several indoor scenarios, even multipath fading [44].
- A4
- fading components do not exhibit spatial correlation;
- A5
- the network operates in saturation conditions, where each node has always data to send.
- A6
- buffering and/or re-transmission policies are not included in our framework, so as data packets are dropped if not successfully delivered in a slot.
2.2. Propagation Channel Abstraction
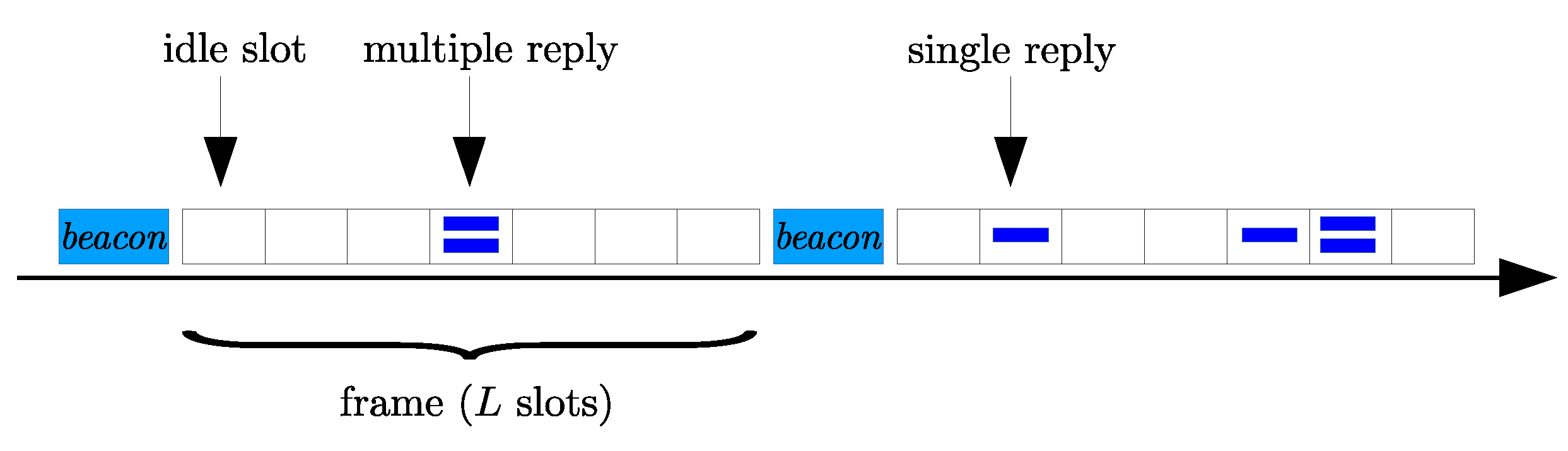
2.3. Random Channel Access Model
- Idle Slot: , that corresponds to the case where no node has a null slot counter, and thus no transmission occurs;
- Single transmission slot: , that corresponds to the event where only one node has a slot counter equal to zero. In this case, the received signal is correctly detected by the m-th receiver if the backscattered power is larger than the receiver sensitivity threshold, which we denote as . Then, conditioned to the event , the probability for the single transmitted packet to be successfully detected can be expressed aswhere we exploited the independence among fading components. Then, it may happen that the power at the m-th receiver input is below the receiver sensitivity threshold, thus yielding a data packet loss.
- Multiple transmission slot: , that corresponds to the case where multiple nodes gain access to the channel in the same slot. In this case, the received backscattered signal at the generic receiver consists of the superimposition of multiple interfering transmissions. This event is typically interpreted as a collision, nevertheless, due to the so-called capture effect, a node’s data packet can be successfully detected at the m-th receiver despite the interference. A successful packet detection can occur when the backscattered power from a node is sufficiently large if compared to the power of the interfering signals. More precisely, this occurs when the SIR measured at a given receiver for a given node’s packet is larger than the so-called SIR threshold (or capture ratio), which we denote as . Formally, by defining the SIR for the k-th tag at the m-th receiver asthe k-th nodes’s packet is successfully detected at the m-th receiver with probabilitythen, the probability of having a successful packet detection at the m-th receiver is given asA collision occurs when the SIR associated to all the replying nodes is below the SIR threshold, and the collision probability at the m-th receiver can be trivially determined as
3. Multiple Access Interference Characterization and Capture Diversity
Capture Diversity
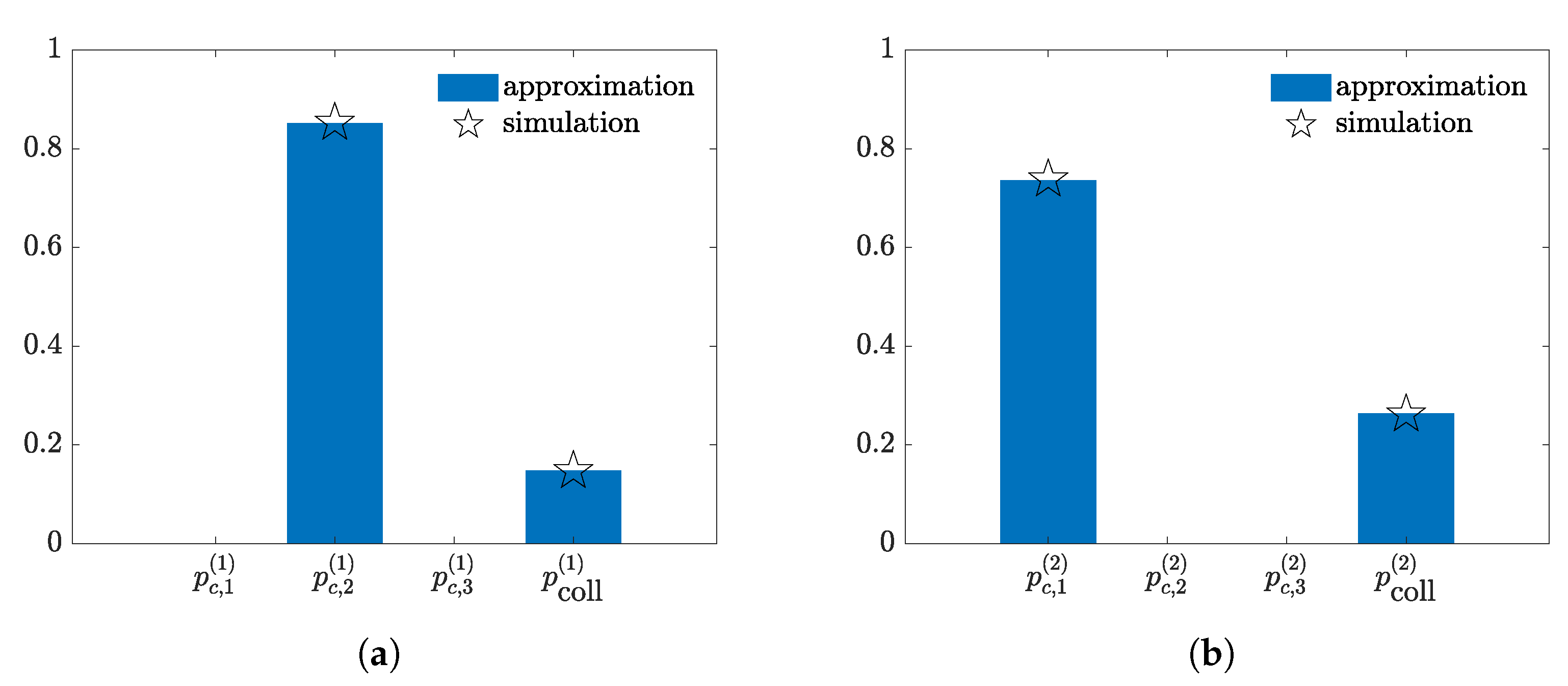
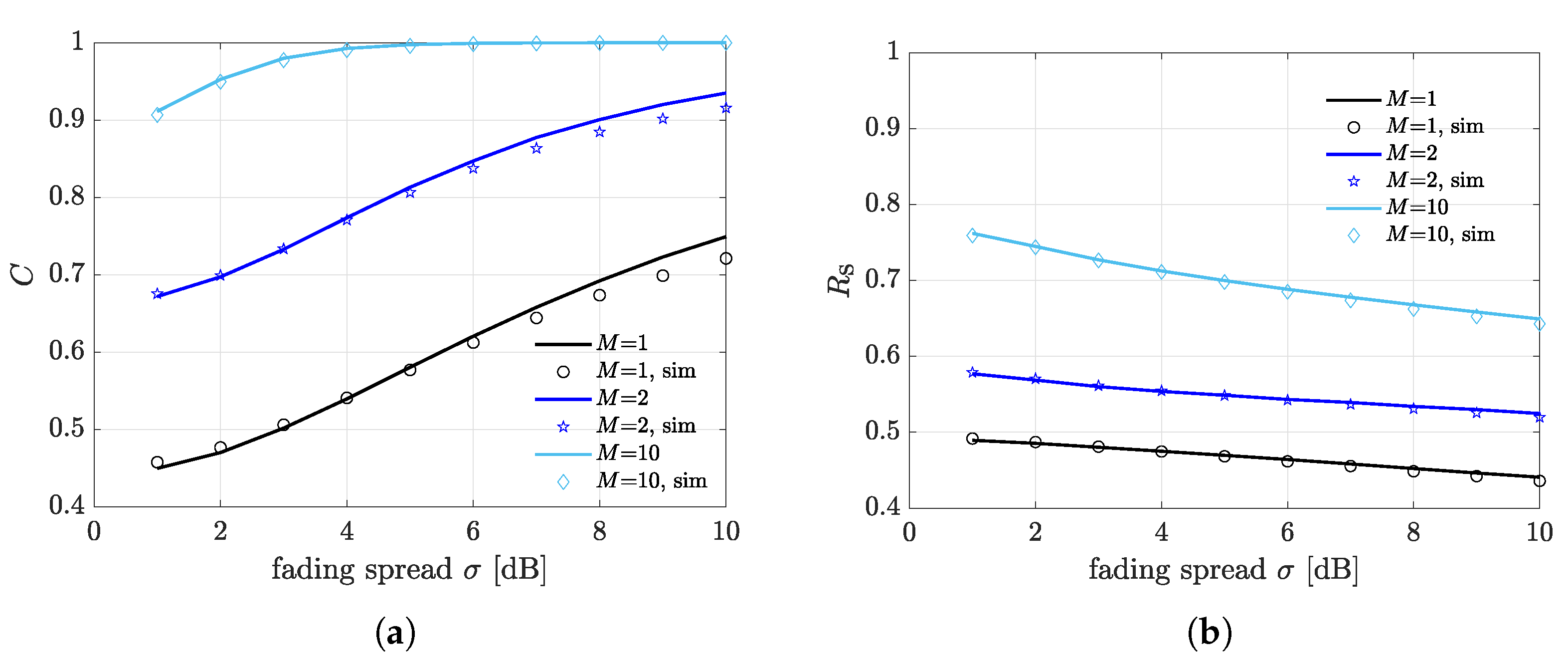
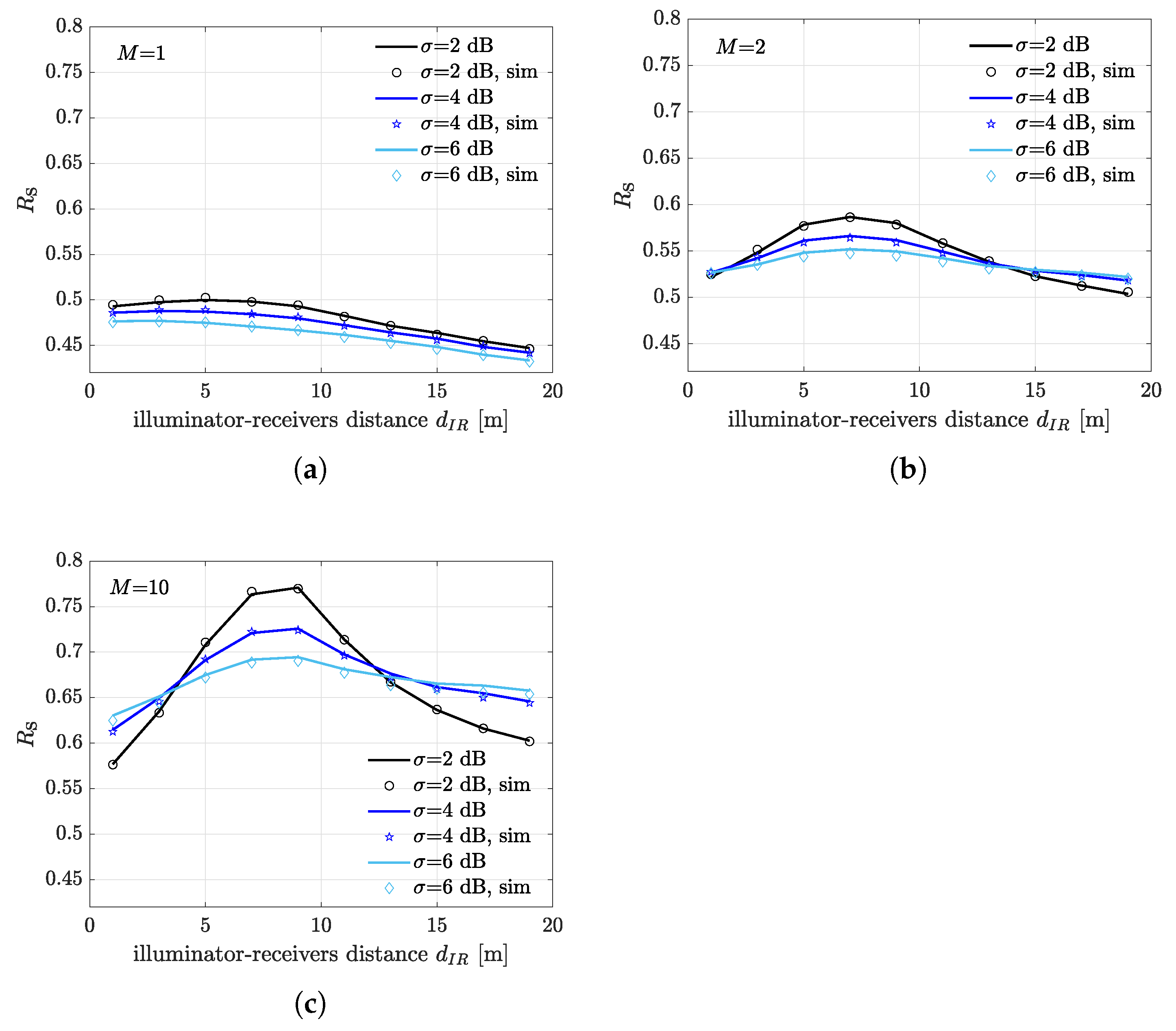
4. Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Duan, R.; Wang, X.; Yigitler, H.; Sheikh, M.U.; Jantti, R.; Han, Z. Ambient Backscatter Communications for Future Ultra-Low-Power Machine Type Communications: Challenges, Solutions, Opportunities, and Future Research Trends. IEEE Commun. Mag. 2020, 58, 42–47. [Google Scholar] [CrossRef]
- Wu, Y.; Gao, X.; Zhou, S.; Yang, W.; Polyanskiy, Y.; Caire, G. Massive Access for Future Wireless Communication Systems. IEEE Wirel. Commun. 2020, 27, 148–156. [Google Scholar] [CrossRef] [Green Version]
- Babich, F.; Buttazzoni, G.; Vatta, F.; Comisso, M. Energy-Constrained Uncoordinated Multiple Access for Next-Generation Networks. IEEE Open J. Commun. Soc. 2020, 1, 1808–1819. [Google Scholar] [CrossRef]
- Ma, Y.; Yuan, Z.; Li, W.; Li, Z. Novel Solutions to NOMA based Modern Random Access for 6G Enabled IoT. IEEE Internet Things J. 2021, 1. [Google Scholar] [CrossRef]
- Munari, A.; Clazzer, F.; Liva, G.; Heindlmaier, M. Multiple-Relay Slotted ALOHA: Performance Analysis and Bounds. IEEE Trans. Commun. 2021, 69, 1578–1594. [Google Scholar] [CrossRef]
- Khan, W.U.; Li, X.; Zeng, M.; Dobre, O.A. Backscatter-Enabled NOMA for Future 6G Systems: A New Optimization Framework Under Imperfect SIC. IEEE Commun. Lett. 2021, 25, 1669–1672. [Google Scholar] [CrossRef]
- Zheng, F.; Kaiser, T. Digital Signal Processing for RFID; John Wiley & Sons: Hoboken, NJ, USA, 2016. [Google Scholar]
- Nikitin, P.V.; Rao, K.V.S. Performance limitations of passive UHF RFID systems. In Proceedings of the 2006 IEEE Antennas and Propagation Society International Symposium, Albuquerque, NM, USA, 9–14 July 2006; pp. 1011–1014. [Google Scholar]
- Alevizos, P.N.; Tountas, K.; Bletsas, A. Multistatic Scatter Radio Sensor Networks for Extended Coverage. IEEE Trans. Wirel. Commun. 2018, 17, 4522–4535. [Google Scholar] [CrossRef] [Green Version]
- Van Huynh, N.; Hoang, D.T.; Lu, X.; Niyato, D.; Wang, P.; Kim, D.I. Ambient Backscatter Communications: A Contemporary Survey. IEEE Commun. Surv. Tutor. 2018, 20, 2889–2922. [Google Scholar] [CrossRef] [Green Version]
- Valentini, R.; di Marco, P.; Alesii, R.; Santucci, F. Exploiting Capture Diversity in Distributed Passive RFID Systems. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 0996–1000. [Google Scholar]
- Valentini, R.; Di Marco, P.; Alesii, R.; Santucci, F. Cross-Layer Analysis of Multi-Static RFID Systems Exploiting Capture Diversity. IEEE Trans. Commun. 2021. [Google Scholar] [CrossRef]
- Lam, S.; Kleinrock, L. Packet Switching in a Multiaccess Broadcast Channel: Dynamic Control Procedures. IEEE Trans. Commun. 1975, 23, 891–904. [Google Scholar] [CrossRef]
- Pratesi, M.; Santucci, F.; Graziosi, F. Generalized moment matching for the linear combination of lognormal RVs: Application to outage analysis in wireless systems. IEEE Trans. Wirel. Commun. 2006, 5, 1122–1132. [Google Scholar] [CrossRef]
- Salah, H.; Ahmed, H.A.; Robert, J.; Heuberger, A. A Time and Capture Probability Aware Closed Form Frame Slotted ALOHA Frame Length Optimization. IEEE Commun. Lett. 2015, 19, 2009–2012. [Google Scholar] [CrossRef]
- Alcaraz, J.J.; Vales-Alonso, J.; Egea-Lopez, E.; Garcia-Haro, J. A Stochastic Shortest Path Model to Minimize the Reading Time in DFSA-Based RFID Systems. IEEE Commun. Lett. 2013, 17, 341–344. [Google Scholar] [CrossRef]
- Li, B.; Wang, J. Efficient Anti-Collision Algorithm Utilizing the Capture Effect for ISO 18000-6C RFID Protocol. IEEE Commun. Lett. 2011, 15, 352–354. [Google Scholar] [CrossRef]
- Wu, H.; Zeng, Y. Passive RFID Tag Anticollision Algorithm for Capture Effect. IEEE Sens. J. 2015, 15, 218–226. [Google Scholar] [CrossRef]
- Lau, C.; Leung, C. Capture models for mobile packet radio networks. IEEE Trans. Commun. 1992, 40, 917–925. [Google Scholar] [CrossRef]
- Valentini, R.; Alesii, R.; Levorato, M.; Santucci, F. Cross-Layer Analysis of RFID Systems with Correlated Shadowing and Random Radiation Efficiency. In Proceedings of the ICC 2019—2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Di Marco, P.; Santucci, F.; Fischione, C. Modeling anti-collision protocols for RFID Systems with multiple access interference. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 5938–5944. [Google Scholar] [CrossRef]
- Al-Badarneh, Y.H.; Alouini, M.S.; Georghiades, C.N. Performance Analysis of Monostatic Multi-Tag Backscatter Systems with General Order Tag Selection. IEEE Wireless Commun. Lett. 2020, 9, 1201–1205. [Google Scholar] [CrossRef]
- Babich, F.; Comisso, M. Impact of Segmentation and Capture on Slotted Aloha Systems Exploiting Interference Cancellation. IEEE Trans. Veh. Technol. 2019, 68, 2878–2892. [Google Scholar] [CrossRef] [Green Version]
- Tang, S.; Yuan, J.; Li, X.Y.; Chen, G.; Liu, Y.; Zhao, J. RASPberry: A stable reader activation scheduling protocol in multi-reader RFID systems. In Proceedings of the 2009 17th IEEE International Conference on Network Protocols, Princeton, NJ, USA, 13–16 October 2009; pp. 304–313. [Google Scholar] [CrossRef]
- Tang, S.; Wang, C.; Li, X.Y.; Jiang, C. Reader Activation Scheduling in Multi-reader RFID Systems: A Study of General Case. In Proceedings of the 2011 IEEE International Parallel Distributed Processing Symposium, Anchorage, AK, USA, 16–20 May 2011; pp. 1147–1155. [Google Scholar] [CrossRef]
- Zhou, Z.; Gupta, H.; Das, S.R.; Zhu, X. Slotted Scheduled Tag Access in Multi-Reader RFID Systems. In Proceedings of the 2007 IEEE International Conference on Network Protocols, Beijing, China, 16–19 October 2007; pp. 61–70. [Google Scholar] [CrossRef] [Green Version]
- Mohsenian-Rad, A.H.; Shah-Mansouri, V.; Wong, V.W.; Schober, R. Distributed channel selection and randomized interrogation algorithms for large-scale and dense RFID systems. IEEE Trans. Wirel. Commun. 2010, 9, 1402–1413. [Google Scholar] [CrossRef]
- Yang, L.; Qi, Y.; Han, J.; Wang, C.; Liu, Y. Shelving Interference and Joint Identification in Large-Scale RFID Systems. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 3149–3159. [Google Scholar] [CrossRef]
- Liu, X.; Yin, J.; Zhang, S.; Xiao, B.; Ou, B. Time-Efficient Target Tags Information Collection in Large-scale RFID Systems. IEEE Trans. Mob. Comput. 2020, 1. [Google Scholar] [CrossRef]
- Hui, X.; Kan, E.C. Collaborative Reader Code Division Multiple Access in the Harmonic RFID System. IEEE J. Radio Freq. Identif. 2018, 2, 86–92. [Google Scholar] [CrossRef]
- Ouroutzoglou, M.; Vougioukas, G.; Alevizos, P.N.; Dimitriou, A.G.; Bletsas, A. Multistatic Gen2 RFID over Ethernet with Commodity SDRs. In Proceedings of the 2019 IEEE International Conference on RFID Technology and Applications (RFID-TA), Pisa, Italy, 25–27 September 2019; pp. 393–398. [Google Scholar] [CrossRef]
- Babich, F.; Comisso, M.; Cuttin, A.; Ricciato, F. Exploiting capture and interference cancellation for uplink random multiple access in 5G millimeter-wave networks. Ann. Telecommun. 2020, 75, 1–15. [Google Scholar] [CrossRef]
- Babich, F.; Comisso, M. Coded Slotted Aloha (CSA) with Capture. In Proceedings of the 24th European Wireless Conference, European Wireless 2018, Catania, Italy, 2–4 May 2018; pp. 1–6. [Google Scholar]
- Babich, F.; Buttazzoni, G.; Vatta, F.; Comisso, M. Energy-Constrained NOMA with Packet Diversity for Slotted Aloha Systems. In Proceedings of the 2020 Mediterranean Communication and Computer Networking Conference (MedComNet), Arona, Italy, 17–19 June 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Guo, J.; Zhou, X.; Durrani, S.; Yanikomeroglu, H. Design of Non-Orthogonal Multiple Access Enhanced Backscatter Communication. IEEE Trans. Wirel. Commun. 2018, 17, 6837–6852. [Google Scholar] [CrossRef] [Green Version]
- Zhu, G.; Ko, S.W.; Huang, K. Inference From Randomized Transmissions by Many Backscatter Sensors. IEEE Trans. Wirel. Commun. 2018, 17, 3111–3127. [Google Scholar] [CrossRef]
- Nazar, A.W.; Hassan, S.A.; Jung, H.; Mahmood, A.; Gidlund, M. BER Analysis of a Backscatter Communication System with Non-Orthogonal Multiple Access. IEEE Trans. Green Commun. Netw. 2021, 5, 574–586. [Google Scholar] [CrossRef]
- Boyer, C.; Roy, S. Space Time Coding for Backscatter RFID. IEEE Trans. Wirel. Commun. 2013, 12, 2272–2280. [Google Scholar] [CrossRef]
- He, C.; Wang, Z.J.; Leung, V.C.M. Unitary Query for the M × L × N MIMO Backscatter RFID Channel. IEEE Trans. Wirel. Commun. 2015, 14, 2613–2625. [Google Scholar] [CrossRef] [Green Version]
- He, C.; Wang, Z.J.; Miao, C.; Leung, V.C.M. Block-Level Unitary Query: Enabling Orthogonal-Like Space-Time Code with Query Diversity for MIMO Backscatter RFID. IEEE Trans. Wirel. Commun. 2016, 15, 1937–1949. [Google Scholar] [CrossRef]
- He, C.; Wang, Z.J.; Miao, C. Query Diversity Schemes for Backscatter RFID Communications with Single-Antenna Tags. IEEE Trans. Veh. Technol. 2017, 66, 6932–6941. [Google Scholar] [CrossRef]
- Mishra, D.; Larsson, E.G. Monostatic Backscattering Detection by Multiantenna Reader. In Proceedings of the 2019 53rd Asilomar Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 3–6 November 2019; pp. 697–701. [Google Scholar] [CrossRef]
- Mishra, D.; Larsson, E.G. Multi-Tag Backscattering to MIMO Reader: Channel Estimation and Throughput Fairness. IEEE Trans. Wirel. Commun. 2019, 18, 5584–5599. [Google Scholar] [CrossRef] [Green Version]
- Jeruchim, M.C.; Balaban, P.; Shanmugan, K.S. Simulation of Communication Systems: Modeling, Methodology and Techniques; Springer Science & Business Media: New York, NY, USA, 2006. [Google Scholar]
- Alevizos, P.N.; Bletsas, A. Sensitive and Nonlinear Far-Field RF Energy Harvesting in Wireless Communications. IEEE Trans. Wirel. Commun. 2018, 17, 3670–3685. [Google Scholar] [CrossRef] [Green Version]
- Alhassoun, M.; Durgin, G.D. Spatial Fading in Backscatter Channels: Theory and Models. In Proceedings of the 2019 16th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Genz, A. Numerical Computation of Multivariate Normal Probabilities. J. Comput. Graph. Stat. 1992, 1, 141–149. [Google Scholar] [CrossRef]
- Schwartz, S.C.; Yeh, Y.S. On the distribution function and moments of power sums with log-normal components. Bell Syst. Tech. J. 1982, 61, 1441–1462. [Google Scholar] [CrossRef]
- Stüber, G.L. Principles of Mobile Communication; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2. [Google Scholar]
- EPCglobal Inc. EPC Radio-Frequency Identity Protocols Generation-2 UHF RFID; EPCglobal Inc.: Lawrenceville, NJ, USA, 2018. [Google Scholar]





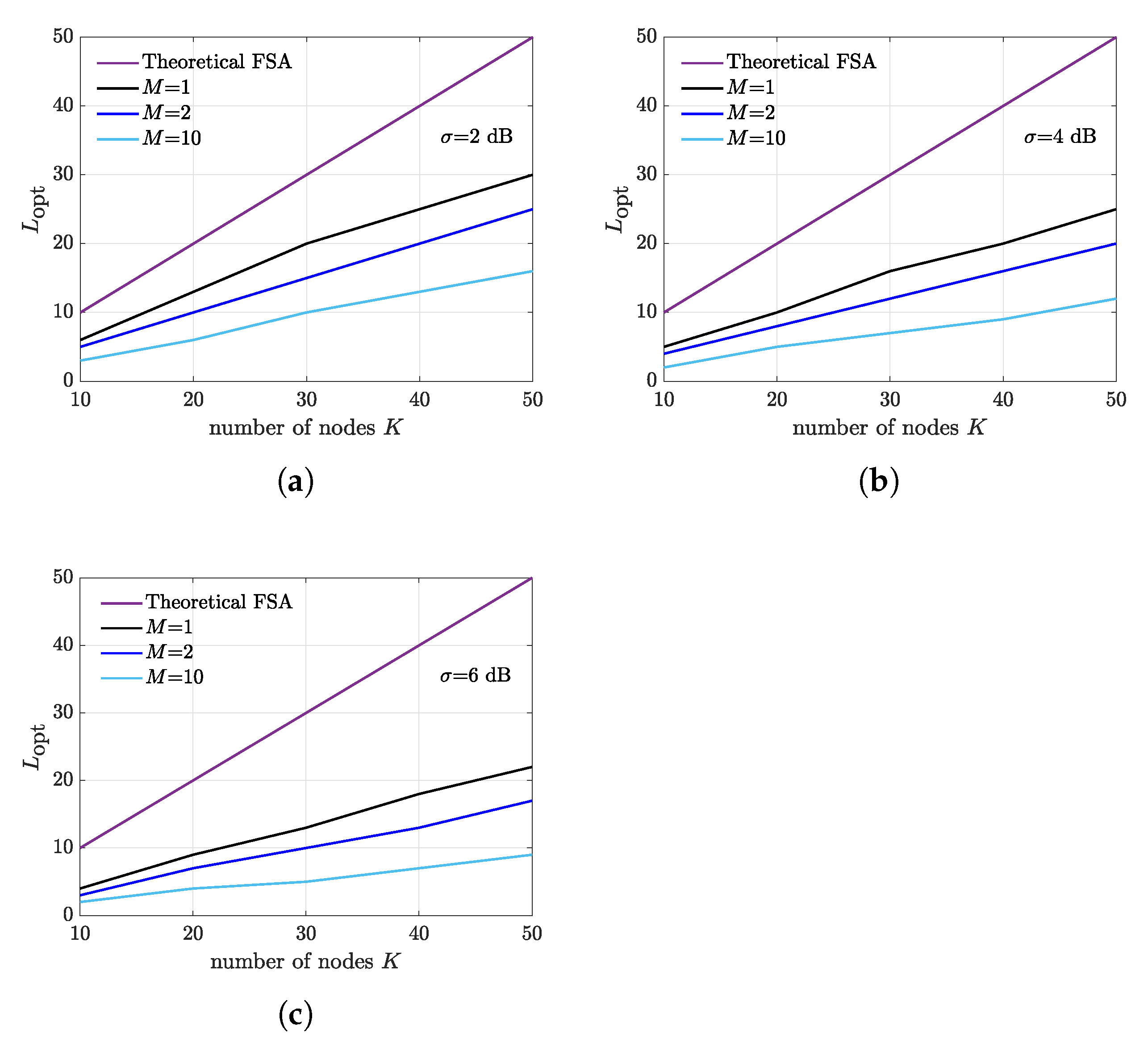
| Parameter | Value | Unit |
|---|---|---|
| 33 | dBm | |
| dBm | ||
| dBm | ||
| f | 915 | Mhz |
| 2 | - | |
| 6 | dB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Valentini, R.; Di Marco, P.; Santucci, F. Exploiting Capture Diversity for Performance Enhancement of ALOHA-Based Multi-Static Backscattering Systems in the 6G Perspective. Sensors 2021, 21, 5070. https://doi.org/10.3390/s21155070
Valentini R, Di Marco P, Santucci F. Exploiting Capture Diversity for Performance Enhancement of ALOHA-Based Multi-Static Backscattering Systems in the 6G Perspective. Sensors. 2021; 21(15):5070. https://doi.org/10.3390/s21155070
Chicago/Turabian StyleValentini, Roberto, Piergiuseppe Di Marco, and Fortunato Santucci. 2021. "Exploiting Capture Diversity for Performance Enhancement of ALOHA-Based Multi-Static Backscattering Systems in the 6G Perspective" Sensors 21, no. 15: 5070. https://doi.org/10.3390/s21155070
APA StyleValentini, R., Di Marco, P., & Santucci, F. (2021). Exploiting Capture Diversity for Performance Enhancement of ALOHA-Based Multi-Static Backscattering Systems in the 6G Perspective. Sensors, 21(15), 5070. https://doi.org/10.3390/s21155070






