Abstract
Focusing on the diversified demands of location privacy in mobile social networks (MSNs), we propose a privacy-enhancing k-nearest neighbors search scheme over MSNs. First, we construct a dual-server architecture that incorporates location privacy and fine-grained access control. Under the above architecture, we design a lightweight location encryption algorithm to achieve a minimal cost to the user. We also propose a location re-encryption protocol and an encrypted location search protocol based on secure multi-party computation and homomorphic encryption mechanism, which achieve accurate and secure k-nearest friends retrieval. Moreover, to satisfy fine-grained access control requirements, we propose a dynamic friends management mechanism based on public-key broadcast encryption. It enables users to grant/revoke others’ search right without updating their friends’ keys, realizing constant-time authentication. Security analysis shows that the proposed scheme satisfies adaptive -semantic security and revocation security under a random oracle model. In terms of performance, compared with the related works with single server architecture, the proposed scheme reduces the leakage of the location information, search pattern and the user–server communication cost. Our results show that a decentralized and end-to-end encrypted k-nearest neighbors search over MSNs is not only possible in theory, but also feasible in real-world MSNs collaboration deployment with resource-constrained mobile devices and highly iterative location update demands.
1. Motivation
With the rapid development of 5G Wireless Communication, mobile social networks (MSNs), represented by instant messaging and location sharing, have become essential parts of people’s everyday lives. According to [1], the number of enrolled users in MSNs worldwide reaches 862 million in 2020, and it is estimated to exceed 900 million by the end of 2021. In particular, the utilization rate of location-based MSN services reaches 96.9% based on the positioning system (e.g., GPS, WiFi, Bluetooth, etc.) embedded in mobile devices, such as Facebook’s “Nearby friends”, Foursquare’s “Swarm”, and Joyrun’s “real-time running competition”, and so forth. In these services, users can broadcast their locations among friends and send location-based queries for nearby friends. Therefore, the location-based services provide a profoundly mobile interface for users’ real-life social networks.
Nevertheless, people are using the enormously popular MSNs services without realizing their privacy concerns: the MSNs services providers can observe and accumulate the geo-location that users transmit through the network. According to the Mobile APP Security Research [2], among the 50 MSN services surveyed, there are 35 services that leak users’ location data to advertisers or data analysis services on purpose without any permission. In recent years, a lot of research also uses data analysis and machine learning technology to extract a large number of their sensitive information from users’ location information over MSNs: by analyzing their search patterns, the matched friends and search similarities and so forth, it is easy to predict the location conversion patterns between users and their friends [3,4]. It is also turned out that Facebook’s historical spatiotemporal trajectory leaks the geographical distance between each user and the spot that he frequently queries, and then the service provider can learn the access probability—whether and when the user will check-in the next time [5].
To avoid illegal access to users’ locations and search patterns by unauthorized service providers and hackers, previous research aimed to encrypt the location information before uploading. However, traditional encryption methods limit the MSNs service provider’s ability to provide location-based services for users. To achieve privacy-preserving location-based query, the straightforward mathematical methods deploy private information retrieval [6], searchable encryption [7] and other crypto primitives to make the encrypted location data searchable. However, these methods come at the huge cost of computation and communication overhead. Moreover, in a privacy-preserving setting, users have their keys embedded in their mobile devices. If a user is allowed to share his/her location encryption key with friends, he/she needs to launch a search request to the platform multiple times when he wants to retrieve his/her friends’ locations. Moreover, when granting or revoking friends’ search rights, a user and his/her friends should update their keys with synchronous locally, which are not suitable for MSNs platforms with highly extensible requirements. To the best of our knowledge, it is fair to say that achieving fine-grained location access control while providing an efficient, secure location-based neighbors search service has become one of the challenging research topics in the field of privacy-enhancing MSNs and still remains open.
In this work, we translate the high-level vision of the above issues and location privacy demand in MSNs into technical requirements and design a privacy-enhancing k-nearest neighbors search scheme containing cryptographic protocols that meet them. The purpose of this work is to protect users’ location data and search patterns privacy, and make it available for users to query for their k-nearest neighbors based on current distances. In terms of technical contribution, our work presents an efficient construction so that the server can effectively compute and sort the encrypted distance between a user and his/her friends without any decryption operation, which is the first to tackle this problem through the lens of secure multi-party computation. It also achieves lightweight friend authentication and authority management by enabling users to grant/revoke their friends’ search rights without updating others’ keys. In terms of security, our scheme satisfies adaptive -semantic secure and revocation secure under random oracle model. We also undertook an extensive experiment that validates our work, showing that the proposed scheme is possible in theory and feasible in practice.
2. Related Works
2.1. MSNs Privacy
In recent decades, researchers have proposed many privacy-preserving approaches for MSNs. Encryption is the most common method for achieving privacy. For example, Flybynight [8] is a Facebook application for encrypting and decrypting sensitive data using client-side JavaScript. However, it is easy to be attacked by an adversary because the server holds users’ keys and takes charge of key management. NOYB (short for none of your business) [9] offers privacy and preserves MSN services’ functionality based on a secret dictionary’s encryption. Besides, there have been many privacy-preserving matching solutions over MSNs proposed with different techniques. Some schemes are based on private set intersection protocols [10,11] to allow two users to compute the intersection of the two private profile sets privately, but leak no useful information of both parties. For example, Niu et al. designed a spatiotemporal matching scheme for privacy-aware users in MSNs based on the profile’s weight or level and the participant’s social strength [10]. Zhang et al. proposed the concept of a fine-grained privacy information matching protocol by giving preference to each profile and using a similarity function to measure the matching degree [11]. To reduce computation cost, some works [12,13] designed non-encryption-based privacy-preserving matching protocols. Fu et al. proposed a privacy-preserving common-friend matching scheme based on a bloom filter [12]. It transmitted the common profiles of two users into an intersection of bloom filters, which ensures the privacy of friend lists against unknown users. However, it will not be able to resist brute-force attacks, resulting in privacy information leakage. Sun et al. [13] proposed a privacy-preserving spatiotemporal profiles matching scheme to let each user periodically record his locations by a geographic cell index among a large set of predefined ones, which can ensure spatiotemporal privacy at the cost of possibly huge communication and computation overhead.
2.2. Location Privacy
With the rapid development and enormous popularity of location-based services, scholars have paid more and more attention to location data’s privacy and security. Many approaches focus on how to perform privacy-preserving location queries: Bamba et al. proposed a k-anonymity-based scheme that relies on a server to construct an anonymous set based on users’ original queries to make query indistinguishable on the server-side [14]. Bordenabe et al. [15] and Shi et al. [16] both integrated differential privacy to realize nearby friends’ queries. Differential privacy provides a rigorous privacy guarantee by adding noise (randomly to choose a set of fake locations ) to make their data and query deferentially private. Jorgensen et al. incorporated a clustering procedure that groups users according to the social network’s natural community structure and significantly reduced noise [17]. The above works [14,15,16,17] can achieve relatively high efficiency. However, the limitations of these works are that it is challenging to achieve provable security guarantees with formal security definitions, since they did not employ well-designed and provable encryption methods. Zhou et al. took advantage of private information retrieval (PIR) to realize nearby friends’ queries [18]. It provides strong cryptographic guarantees but needs complex operations, and it only protects query privacy but not location privacy. Li et al. designed a private location information matching protocol over MSNs based on inner product similarity (IPS) [19], putting users’ map locations into vectors and encrypting the vectors. The similarity function is used to measure the similarity degree of the encrypted vectors of different users. Schlegel et al. designed an encryption method of dynamic location grid index structure [20], achieving neighbor point search on the premise of not revealing location privacy to the third party. In the above encryption-based schemes, the computation efficiencies are not ideal, requiring multi-round interactions at the logarithmic level between user and server.
Many other works are based on higher security assumptions to achieve a trade-off between security and efficiency. For example, some works [21,22] assumed that the service provider is honest and that it has the authority to access the location plaintext without leaking any information to others. Some works [21,23,24] introduced a trusted third party (TTP) to achieve the trade-off between security and efficiency. Unfortunately, there may not exist such a TTP in real MSNs scenarios. Some non-TTP solutions [15,20] are based on approximate measurements (e.g., linear programming and dynamic grid) with no accurate result. Some works [18,25] need complex operations (e.g., sending fake queries or receiving redundant results) to achieve secure guarantees, which incur high communication and computation overhead at the user-side, making them unsuitable for resource-constrained mobile devices.
3. The Proposed Scheme
3.1. Overview
The privacy-enhancing k-nearest neighbors search scheme over MSNs can be viewed as a decentralized system of end-to-end encrypted social network databases, focusing on the diversified demands of location privacy in MSNs. Our design relies on various cryptographic building blocks, including pseudo-random function, homomorphic crypto mechanism, secure multi-party computation and broadcast encryption.
- -
- Aiming at the limited computation power of resource-constrained mobile devices, we design a lightweight end-to-end location encryption algorithm and a server-aid location re-encryption protocol based on Paillier homomorphic encryption to achieve further location sharing. The protocol allows the service provider to transfer friends’ location ciphertexts into the query user’s homomorphic ciphertexts without requiring them to be online to participate in the calculation.
- -
- We build a secure dual-server architecture and design a secure k-nearest neighbors search protocol by secure multi-party computation and a homomorphic encryption mechanism under this architecture. The server can effectively compute and sort the distance between users and their friends without any decryption operation. Compared with the cloud-center model, where a single server holds complete knowledge, the dual-server architecture minimizes the leakage to the servers and reduces the cost of communication between the mobile user and the server.
- -
- To achieve fine-grained access control, we design a dynamic friends management mechanism based on public-key broadcast encryption. It enables users to grant/revoke their friends’ search rights without updating others’ keys, achieving lightweight friend authentication and authority management. Moreover, this mechanism satisfies revocation secure that the adversary cannot obtain the user’s location information through collusion with the server and the revoked friends, thus further improving the scheme’s overall security.
3.2. Architecture and Syntax
Our scheme is designed to be executed among: U, , and . U is a set that contains n mobile users . Each user can connect with others as his friends dynamically. is the primary server that provides a mobile social network service to all users in U. Each user can send a search request to for k-nearest neighbors among friends based on current location. is a collaborated server to conduct secure computation with for k-nearest neighbors search.
The scheme’s architecture is shown in Figure 1. At a high level, users’ information and their relationships are modeled by a direct graph structure . To initialize the system, the primary server executes Initial algorithm to output public parameter and an empty . Any user should use public parameter to generate his symmetric key and public/secret keys locally by executing algorithm and interacts with the primary server for registration by Join protocol. Any enrolled user can grant/revoke ’s location search right by interacting with in Grant/Revoke protocols. holds a friends index that records his granted friends. According to the real-life MSNs’ location service architecture, we deploy trusted location infrastructure to provide tracing service by sending the current location of each user to his local mobile device periodically. executes to encrypt his location data by his symmetric key at local and uploads the location ciphertext to . then can execute Search protocol with by sending k-nearest neighbors search request. performs encrypted search in with the assistance of and returns the search result to , without relying on the presence of any other user. The proposed scheme’s syntax consists of seven polynomial-time algorithms and protocols, which is shown in Syntax below:
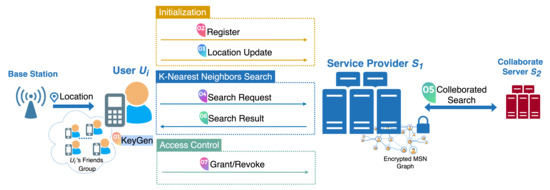
Figure 1.
The architecture.
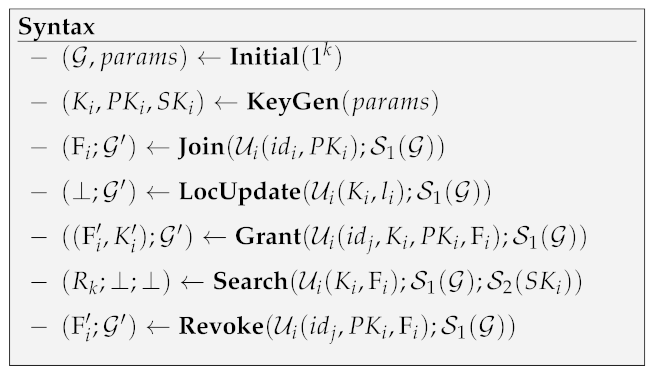
Definition 1
(Correctness). Correctness implies that, for all , all generated by Initial, all generated by KeyGen, all generated by , all generated byKeyGen, and all sequences of LocUpdate, Grant and Revoke protocols, will always output result that: satisfies ; and there does not exist such that and that .
3.3. Security Definition
3.3.1. Adaptive -Semantic Secure
The security definition of adaptive -semantic secure is formalized by an ideal/real-world paradigm [7]. Roughly speaking, we require that the execution of the scheme in the real-world is indistinguishable from an ideal-world. In real-world Real, the protocols between the adversarial servers and the user execute just like in the real scheme. In ideal-world Ideal, there exist two simulators and that can obtain the leakage information from leakage functions and try to simulate the execution of and in Real.
Definition 2 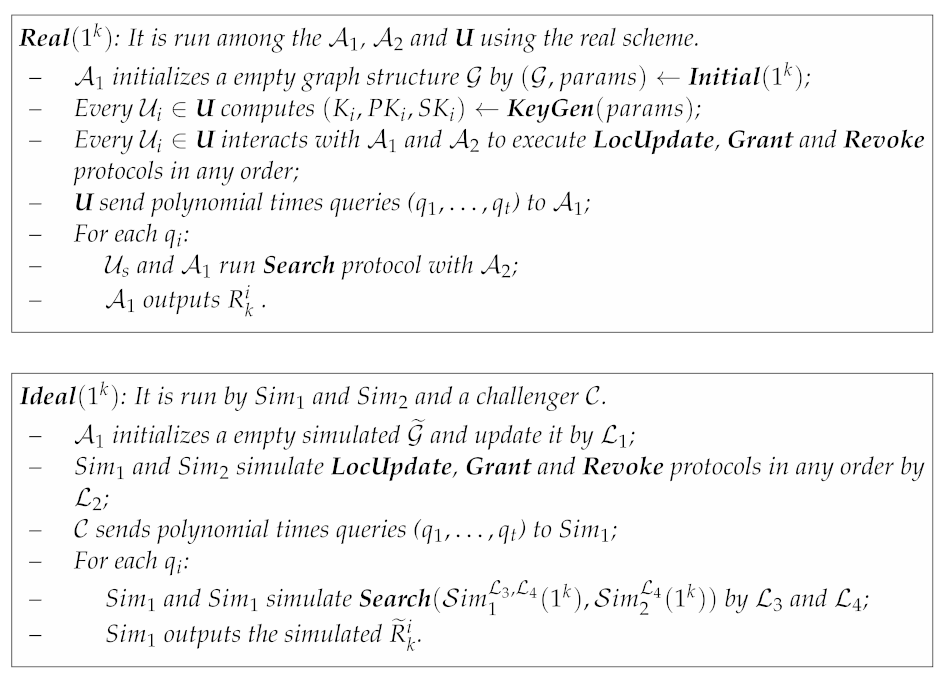
(Adaptive -Semantic Secure). Given the syntax in Section 3.2 and considering the following probabilistic paradigms, where U= is the users’ set, and are two non-colluding adversaries with pseudo-random polynomial time (PPT) computation ability, and are two PPT simulators and to are leakage functions.

The proposed scheme achieves adaptive -semantic security if, for all polynomial time and , there exists polynomial time simulators and such that the following two distribution ensembles are computationally indistinguishable:
3.3.2. Revocation Security
Revocation security guarantees that the scheme satisfies that any user’s revoked friend cannot provide a valid search for his location, even if an adversary illegally steals the revoked friend’s key. We construct the experiment to formalize the revocation security definition. is interactively executed by a challenger and an adversary who has the ability to add friends, perform a search and revoke friends in the real scheme. deletes the user who has been added to the friends index by . continues to generate a search token using the revoked friend’s identity and makes a search request. After a polynomial number of queries, revokes all users that are queried to the Grant oracle but are not subsequently queried to the Revoke oracle (i.e., all users for which holds their valid user keys).
The adversary must then produce a search token which, when used as an input to Search protocol, does not produce null, that is, must produce a valid search request even though it does not hold a non-revoked key. After several rounds of queries, if ’s probability of winning the revocation security experiment with PPT computation ability is negligible, then we can say that the proposed scheme satisfies revocation security.
Definition 3 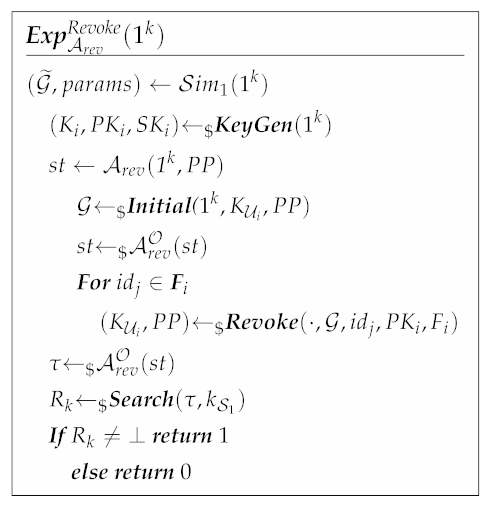
(Revocation Secure). Given the syntax in Section 3.2 and considering , which is executed by a challenger and an adversary :

Specifically, runs to initialize , generates key and state ciphertext by and Join. sends and to . can access to the following oracles, where denotes the parameters that are provided by himself:
- -
- : can send grant friend request to this oracle. If , then the oracle runs Grant by the input provides by . If , then the oracle outputs ⊥.
- -
- : can send revoke friend request to this oracle. If , then the oracle runs by the input provides by . If , then the oracle outputs ⊥.
- -
- : can send a search request in to this oracle. generates a search token and sends it to . Then, the oracle runs by the input provides by , and outputs the search result to .
After polynomial times rounds of queries, revokes all the users that have access to but not . generates a search token τ in protocol. If the output of is not ⊥, then returns 1, otherwise returns 0.
The proposed scheme achieves revocation security if, for all , all , the advantage of to win is negligible:
3.4. The Detailed Construction
Let be a broadcast encryption scheme that retains CPA secure against a coalition of revoked users [26],
be the Pallier encryption scheme [27], be the Goldwasser-Micali encryption scheme [28], and be a pseudo-random function. The detailed construction is given as follows:
3.4.1. Initialization
On input of the security parameter , initializes the global social network graph structure and public parameters . In graph , the maximal number of vertexes in is n, that is , which represents the maximum amount of enrolled users. Each vertex should be attached with the information for an enrolled user that gathered. The existence of a non-zero edge between and represents the friends relationship of and . In other words, if and are strangers to each other, then . is empty at initialization.
3.4.2. Key Generation
If a user is willing to join in the system, he should generate his own keys at local. ’s keys consists of the following parts: the key for the pseudo-random function to encrypt location data, the key pair for the broadcast encryption scheme , the key pairs for the Pallier encryption scheme and the Goldwasser-Micali encryption scheme . first takes as input the binary representation of the public parameters , and randomly selects a k-bit string for his key of . Then he generates by , by and by . Afterwards, he forms his symmetric key as , public key as and secret key as . The lengths of the above keys are determined by the security parameter . Finally, publishes his public key throughout the system.
3.4.3. Join
Before joining in, should generate his friends index with d entries, where d represents the maximum amount of ’s friends. is a key-value data structure, which is empty at first. The key part of will be attached with the granted friends’ identities, the corresponding value part will be attached with the granted friends’ session keys. More precisely, if is a friend of , then stores the session key that has shared with , where represents ’s identity: , where represents ’s identity. To register, should also add the server in by generating ’s session key by and setting . Afterwards, randomly selects a k-bit string as his current state value and encrypts to by . Then sends a registration request . selects an empty vertex in and attaches with .
3.4.4. Location Update
An enrolled user can interact with to update his location by LocUpdate protocol. First, obtains his current geo-location from the trusted location infrastructure that sends ’s geo-location to his local mobile device periodically. maps into an integer from and computes its square . To hide from , needs to encrypt and at local: he chooses two random values and from , uses his key to generate and by pseudo-random function , and hides and into and by and . Finally he forms his current location ciphertext as and sends to . updates the information embedded in vertex in as .
3.4.5. Grant
When connects as his friend, he should grant ’s right to search his location by conducting Grant protocol with . First, adds ’s identity as an entry in ’s friends index , generates ’s session key by , sends to in secure channel. then selects a k-bit string as his updated state value, encrypts to for the updated friends group in that contains by , and boardcasts to the system. After receiving his session key from , he attaches with : . Afterwards, he sends grant request to . first checks whether there is a non-zero direct edge in . If not, it sets and update in with new : .
3.4.6. K-Nearest Neighbors Search
Each enrolled user can send a search request to for retrieving his k-nearest neighbors sorted by distances, shown in Protocol 1. First of all, retrieves his friends’ identities from his friends index , downloads the state ciphertexts for all his friends from the system. For each , decrypts it to by . Afterwards, consolidates the decryption results into search token and sends to . After receiving , extracts from ’s all adjacents in . For each , decrypts it to by . It compares each in with in : if is equal to , then has been granted the right to search for ’s location. Afterwards, for each granted , retrieves the encrypted location attached in . Then, and conduct the following protocols:
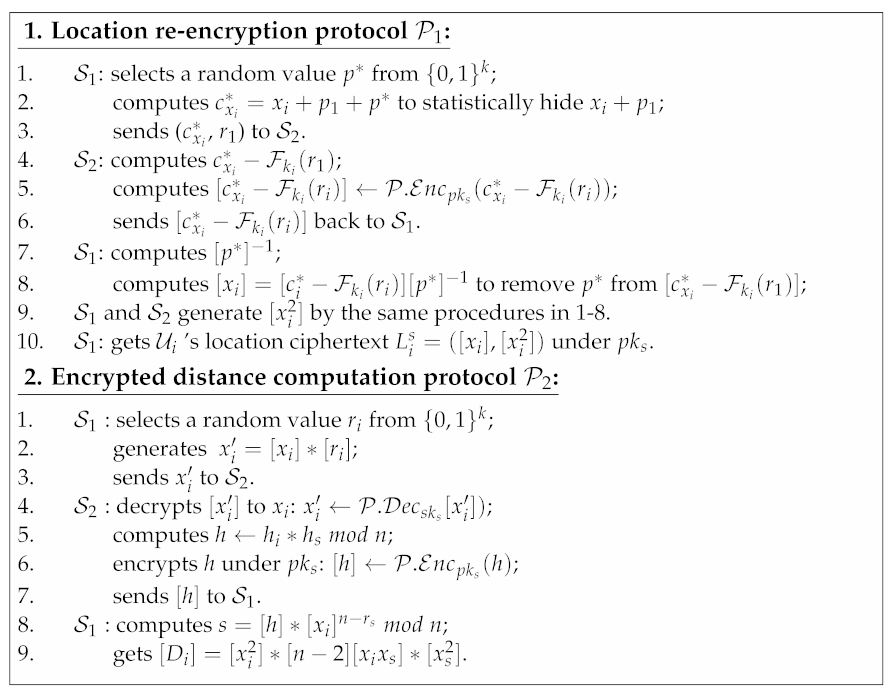
After conducting and for all ’s friends, forms a key-value set that contains all pairs of the encrypted distances between and his friends along with their identities. encrypts each to by , and generates . and perform a secure comparison protocol [29] for and to compare each pair and in based on the distance and . We use as a black-box building block for Search protocol, and pick Batcher’s sorting [30] for performing efficient parallel multi-time comparisons.
Finally, obtains the sorted final result , and sends it back to . can decrypt each to by , then obtain his k-nearest neighbors identities that were sorted by distance.
3.4.7. Revoke
When wants to revoke ’s search right, he should conduct Revoke protocol with . first deletes locally, selects a k-bit string as his updated state value, encrypts to by for the updated group in that excludes . Afterwards, he sends revoke request to . first checks whether there is a non-zero direct edge in . If true, it set and update in with new : .

4. Security Analysis
4.1. Adaptive -Semantic Secure
Theorem 1.
If is a pseudo-random function, , and are CPA secure, and the DGK protocol [31] is proved to be semantically secure in the random oracle model, then the proposed scheme satisfies adaptive -semantic security, which is defined in Definition 2.
Proof.
We construct two simulators that can generate the simulated values in using the information given in the leakage functions to , and prove that is indistinguishable with Real by any PPT adversary.
Given the information leaked from , can learn and . Afterwords, it can choose random value with lengths to simulate . Due to the CPA secure of , is indistinguishable from by any PPT adversary. Therefore, cannot learn extra information from , which satisfies:
Given the information leaked from , can learn and in . Afterwards, it can choose two random values in lengths and to output the simulated . Since is generated by , and are indistinguishable by any PPT adversary due to the randomness of . Therefore, cannot learn extra information from the update history , which satisfies:
Given the information leaked from , can obtain search tokens . Afterwards, it can choose random value in size to simulate each . Moreover, since is generated by by decrypting using keys , and each in is a k-bit random string, each in is indistinguishable from by any PPT adversary. Therefore, cannot learn extra information from , which satisfies:
The sorting network between and contains levels, and each level contains times of protocols. Therefore, the simulation of the sorting network can be reduced to prove and can simulate the secure comparison protocol with leakage functions. Given the information leaked from , can learn the leaked information from each round of and the rounds number . In each round, can learn . and should simulate and with by all pairs with times in sorting protocol to get the final simulation value. At every pairs i, ’s view can be denoted as . Given , we can build in the following phases:
- -
- Randomly choose , compute as ;
- -
- Randomly choose ;
- -
- Encrypt : ;
- -
- Output .
Since , where x is a l-bits integer and r is a -bits integer, the distribution of is indistinguishable from z. We can get . Besides, since the distribution of and z are independent of t, we can get . In a similar way, at every pairs i, ’s view can be denoted as . We can build to simulate in the following phases:
- -
- Choose ;
- -
- Choose two random values , computes ;
- -
- Output .
In both and , r is extracted from uniform distribution , is the ciphertext of which is randomness, so
. We can obtain: and are computational indistinguishable. What is more, since , . Due to the semantic security of DGK, and can obtain d ciphertexts that are unsorted from the leakage function . Then, and can simulate Bathcer’s sorting protocols in times.
Therefore, for all polynomial time and , there exists polynomial time simulators and such that:
We can demonstrate that the proposed scheme satisfies adaptive -semantic security in the random oracle model, which is defined in Definition 2. Theorem 1 proved. □
4.2. Revocation Secure
Theorem 2.
If is CPA secure, then the proposed scheme satisfies revocation secure, which is defined in Definition 3.
Proof.
Assuming the advantage of to win is negligible, we can construct an adversary , who can break the CPA secure of with assist of . We will show that if has a non-negligible advantage in , then we can construct an adversary that uses as a subroutine to break the CPA secure of .
To make the output of as 1, needs to provide a valid search token. To achieve that, must know . A new value of is randomly selected and encrypted by at each time a user is revoked from the system, where is the new friends index. then broadcast this encrypted value to all users. ’s security ensures that only a non-revoked friend of can decrypt this ciphertext to obtain with overwhelming probability. Hence, the adversary can only create a valid search token if he is a valid friend of , or he will break the security of . That is, the probability that a random bit string is valid is . It means that the adversary will not be able to produce a valid token with non-negligible probability.
Let be the challenger for the adversary against , will act as the challenger for :
- runs to generate keys . initializes , randomly chooses a k-bit string , and sends to . runs to generate , and sends it to . runs to generate , runs to generate , where does not include .
- issues a query to for the secret key of . runs to generate , sends to . To fully enroll as a valid friend, the state ciphertext also needs to be updated by . send and a newly generated to , runs to generate new . runs to generate the key of .
- runs Initial to generate graph , and sends and to . can access to oracles and .
- revokes by running , runs Revoke a second time in order to produce two values and for , and sends and to as the challenge value for , along with a set of no revoked friends of .
- selects a bit , uses to encrypt and generates , sends to as the challenge ciphertext for the CPA secure of . sends to as the challenge ciphertext of .
- generates token , and sends to . Since the advantage for to win is non-negligible, the probability of validity of is non-negligible.
- If , then Search stops. According to the following situations, outputs its guess for b:
- -
- If , this tells that was used to generate the token, outputs its guess for b as ;
- -
- Of , this tells that was used to generate the token, outputs its guess for b as .
From the above analysis, the advantage of to break the CPA secure of can be computed as :
Since the advantage of to win is non-negligible, the advantage of to break the CPA security of is non-negligible, which contradicts the CPA security of . Therefore, there exists no , who can win with non-negligible probability, and the proposed scheme satisfies revocation security as defined in Definition 3. Theorem 2 proved. □
5. Theoretical Analysis
The complexity analysis is shown in Table 1, where n is the maximum amount of enrolled users and d is the maximum amount of each user’s friends. We compare our scheme with the related privacy-preserving location-based query schemes [15,18,20] in Table 2. Due to the significant differences among the existing schemes in application scenarios, secure models, evaluation indicators and other factors, we focus on comparing characteristics and security.

Table 1.
Complexity analysis.

Table 2.
Properties comparison.
For result accuracy, [15] achieves differential privacy for location information using linear programming techniques. It is specifically designed for simple computation that cannot provide accurate encrypted distance sorting. Ref. [20] uses a dynamic location grid structure to cluster users close to each other. However, the search results in [15,20] have a specific rate of false positives, which are suitable for similarity search. Our scheme and [18] use Euclidean distance to calculate the encrypted distance to achieve precise secure sorting. Ref. [18] focuses on searching the number of points of interest in a specific location area; our scheme sorts the distances based on the proven-secure comparison protocol. In terms of security, Ref. [18] protects location search privacy by way of private information retrieval (PIR). Although it adopts the anchor technology to improve search efficiency, it still has a certain communication overhead. Ref. [20] achieves sort privacy by assuming the server only performs the search, and the user performs the result sorting. As a result, the above methods each sort privacy but lead to high computation or communication costs.
Besides, compared with other schemes, our scheme also has a flexible access control mechanism. Moreover, our scheme achieves a constant-time computation cost and communication cost when updating friends and encrypting locations, and a user only needs to store key-related information locally. Therefore, we can demonstrate that our proposed scheme has both a very light user workload and a moderate server workload while being secure against the honest-but-curious adversary. In nowadays’s mobile social networking environment, the user-side lightweight device’s storage and computation cost should be minimized as much as possible. As a consequence, the proposed scheme is more suitable for the real-life thin clients MSNs deployment scenario.
6. Implementation
We implement and analyze the performance of our scheme. The experiments were run on several computers with Linux Ubuntu 18.04.2 64-Bit Version with Inter(R) Core(TM) I7-2600 quad-core processor (3.4 ghz) and 8 GB memory, which were installed on VMware Workstation in the LAN in C++ language. One of the computers acted as the server-end and the others acted as user-ends, respectively. We implemented a job allocation mechanism in the server-end that the computer acted as the master server and used threads to simulate the collaborated server that performed the assistant job. Each user-end stored the user’s keys locally and interacted with the server-end. To submit a search request, a user-end only communicated with the master server.
In the simulation experiments, the security parameter k was set to 256 bits. We chose SHA256 in the OpenSSL library [32] for the pseudo-randomness function, and used the Relic library [33] to implement Paillier and GM homomorphic encryption. To implement the scheme more securely, we improved the modulus n of the Paillier and GM to 1024 bits. Besides, we used BGW2 [26] to implement public-key broadcast encryption. The key length in the above public encryption methods was set to be 1024 bits.
We conducted data simulations based on real-world data sets, which came from the newest version of the Enron email dataset [34], where we randomly selected 1000 accounts as the total users set. We represented users’ friendships in the form of linked contacts. We selected a random integer in to simulate the user’s location’ value, which was updated periodically. Moreover, we initialized the social network graph structure with 1000 vertexes and 3831 edges that contained the above data and used a unique value to identify each vertex (user) in . We did not record the network communication time during all the experiments since it depends on the user-end and the server-end’s network connection. Each data point in the experiments was obtained after being repeated 50 times to generate the average value.
6.1. Storage Analysis
We first analyzed the storage overhead of our scheme. Table 3 shows the comparison between the encrypted and unencrypted of the generation time and the server’s storage cost in the trend of the number of users increases. It can be seen that the server’s storage cost increased almost linearly with the increase of the number of users. Since we used symmetric encryption to encrypt location, compared with the Paillier homomorphism ciphertext, the inflation rate of the symmetric ciphertext of the location decreased significantly, which is consistent with the theoretical analysis. Therefore, the proposed scheme achieves the trade-off of users’ location confidentiality and search privacy with the acceptable additional storage cost.

Table 3.
Storage cost.
6.2. Communication
In terms of communication, we mainly analyzed the amount of data transformed between (1) and and (2) and in Search protocol. Theoretically, when requests to search k-nearest neighbors among his d friends, ’s communication overhead increases almost linearly with k. When and interact with each other to compute the distance from the total of d friends’ location ciphertexts, the data size of the communication between them is .
Figure 2a,b shows the relationship between the two types of communication overhead in the experiment with the increasing trends of the friends’ number d and the search parameter k, respectively. In general, the amount of data transmission required by the user in Search protocol is positively related to k. When k increases to a particular value (greater than d), the data transmission volume tends to be stable. The communication overhead between and is mainly positively related to d, but independent of the increase of k. Moreover, the distance computation sub-procedure requires several rounds of interactions, so the amount of communication overhead between servers is relatively large, which is consistent with the theoretical analysis.
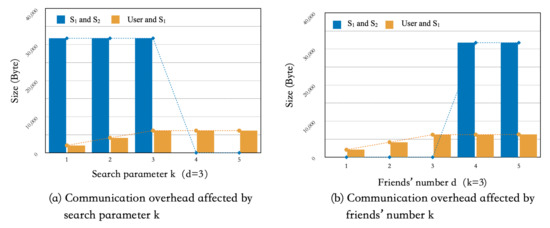
Figure 2.
Communication overhead.
6.3. Search Time
We also analyzed the primary source of the search time overhead for Search protocol. First, we divided the Search protocol at the server-end into two sub-procedures of location search and distance sort. Figure 3 shows the relationship between search time and the number of friends d. In Figure 3, the total time overhead of Search protocol is shown in the blue curve, the time overhead to extract and re-encrypt location ciphertext is shown in the yellow curve, and the time overhead to compute and sort the encrypted distance is shown in the red curve.
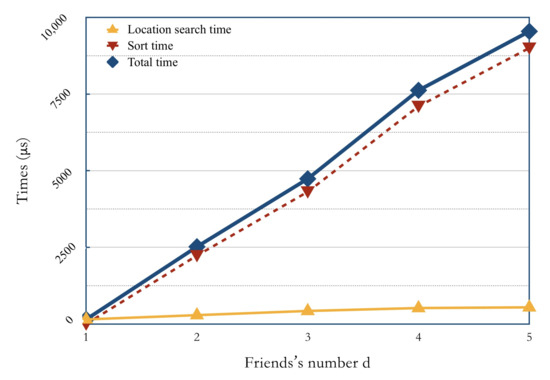
Figure 3.
Search time overhead.
From Figure 3, we can see that the time overhead of the two sub-procedures in the Search protocol generally increases with the increasing trend of d. Specifically, the location search time is far lower than the distance sort time, and with d increases to 4, the curve growth is slowing down. The distance sort time has a stable approximate linear relation with d. Therefore, it can be concluded that the computation and comparison of encrypted distances are two primary time-overhead sources of the Search protocol, which is consistent with the theoretical analysis.
6.4. Scalability
In terms of scalability, we first analyzed the impact of the search users’ number who submit search requests in parallel on the time overhead of the Search protocol. To be specific, we deploy one host to simulate one user to execute the Search protocol and record the total time overhead. Then we deploy six hosts to simulate six users to repeat the same experiment and compare the results. It is worth mentioning that, when recording the time of multi-user search, multiple user-ends simultaneously send the search requests to the server-end. We record the start and end time when the server-end receives the search request until it completes each user’s search. Figure 4 shows the relationship between the parallel search users’ number and Search protocol’s total time. It can be seen that one user’s search time is slightly lower than six parallel users’ search times. The former is approximately in a stable linear relation with d, and the latter slows down to a constant level with the increase of d. From the trend it can be concluded that, with the number of search users d increasing, its impact on search time overhead is weakened, and it further weakens the influence of the increasing number of friends on the search time. Therefore, the multi-user parallelism has a weak impact on search time overhead, which helps the scheme to achieve a certain level of scalability.
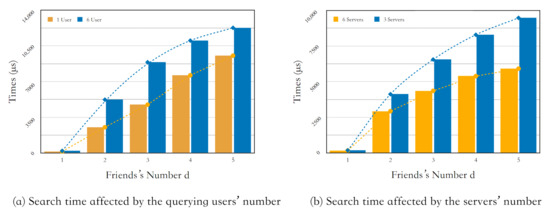
Figure 4.
Scalability.
Besides, we analyzed the influence of the expandable number of remote servers on the search time overhead. First, we deployed three servers to execute the Search protocol for six users simultaneously and recorded the total time overhead. Then we deployed six servers to repeat the same experiment and compare the results. Figure 4 shows the relationship between the number of servers and the search time. It can be seen that the search time of 6-server deployment is significantly lower than the running time with 3-server deployment, and the former’s growth was slowed down to a constant level after d reaches 4, but the latter’s growth takes an approximately linear relationship with the number of friends steadily. Therefore, it can be concluded that deploying multiple servers to perform parallel searches can reduce the search time overhead and further weaken the influence of the increasing number of friends on the search time.
Remark 1.
It is worth pointing out that the search process’s main computation cost is the homomorphic encryption/decryption operation and broadcast decryption operation. The computation efficiency is closely related to the selected parameters of the underlying algorithms. The server-end implementation can also be optimized to reduce the search time by using multiple threads for distance sorting and using approximate sorting algorithms, and so forth. In our experiment, we did not adopt any optimization method. The server was allowed to complete all the computation steps in a single thread in each phase to reflect the scheme’s original execution efficiency faithfully.
7. Conclusions
Aiming at the problem of location privacy disclosure in MSNs, we propose a privacy-enhancing k-nearest neighbors search scheme over MSNs. We deploy a dual-server collaborative architecture and design an encrypted location-oriented k-neighbor search protocol based on secure multi-party computation and homomorphic encryption. Our scheme achieves accurate nearby friends retrieval while protecting the geo-location and the distance order from revealing them to the servers. We propose a lightweight dynamic friends management mechanism based on public-key broadcast encryption to satisfy the fine-grained access control requirement. It enables users to grant/revoke a friend’s location search right without updating others’ keys and achieves constant-time identity authentication. The scheme satisfies adaptive -semantic security and revocation security under the random oracle model. Compared with the works on single server architecture, the proposed scheme reduces the communication cost between users and the server and prevents location information leakage, which achieves a trade-off of the location availability and privacy.
Author Contributions
Conceptualization, Y.L. and F.Z.; Data curation, Y.L.; Formal analysis, Y.L.; Funding acquisition, F.Z.; Methodology, Y.L.; Project administration, F.Z.; Validation, Y.G. and Z.X.; Writing–original draft, Y.L.; Writing–review & editing, Y.L., Y.G. and Z.X. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Northeastern University Annual Basic Scientific Research Funding under Grant 02190022121006 and the Natural Science Foundation of China under Grant 61772127, Grant 61532007 and Grant 61472184.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Global Social Media Stats. Available online: https://datareportal.com/social-media-users (accessed on 10 April 2021).
- Weichbroth, P.; Łysik, Ł. Mobile Security: Threats and Best Practices. Mob. Inf. Syst. 2020. [Google Scholar] [CrossRef]
- Anastasios, N.; Salvatore, S.; Mascolo, C.; Pontil, M. An empirical study of geographic user activity patterns in foursquare. In Proceedings of the Fifth International AAAI Conference on Weblogs and Social Media, Barcelona, Spain, 17–21 July 2011. [Google Scholar]
- Cheng, Z.; Caverlee, J.; Lee, K.; Sui, D. Exploring millions of footprints in location sharing services. In Proceedings of the International Conference on Weblogs and Social Media, Barcelona, Spain, 17–21 July 2011; pp. 81–88. [Google Scholar]
- Preotiuc, P.D.; Cohn, T. Mining user behaviors: A study of check-in patterns in location based social network. In Proceedings of the Conference on ACM Web Science, Paris, France, 2–4 May 2013; pp. 306–315. [Google Scholar]
- Chor, B.; Goldreich, O.; Kushilevitz, E.; Sudan, M. Private information retrieval. In Proceedings of the IEEE 36th Annual Foundations of Computer Science, Milwaukee, Wisconsin, 23–25 October 1995; pp. 41–50. [Google Scholar]
- Curtmola, R.; Garay, J.; Kamara, S.; Ostrovsky, R. Searchable symmetric encryption: Improved definitions and efficient constructions. J. Comput. Secur. 2016, 19, 895–934. [Google Scholar] [CrossRef]
- Lucas, M.M.; Nikita, B. Flybynight: Mitigating the privacy risks of social networking. In Proceedings of the 7th ACM Workshop on Privacy in the Electronic Society, Alexandria, VA, USA, 27 October 2008; pp. 1–8. [Google Scholar]
- Guha, S.; Kevin, T.; Paul, F. NOYB: Privacy in online social networks. In Proceedings of the First Workshop on Online Social Networks, Seattle, WA, USA, 18 August 2008; pp. 49–54. [Google Scholar]
- Niu, B.; Li, X.; Zhu, X.; Li, X.; Li, H. Are you really my friend? Exactly spatiotemporal matching scheme in Privacy-Preserving mobile social networks. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Beijing, China, 24–26 September 2014; pp. 33–40. [Google Scholar]
- Zhang, R.; Zhang, Y.; Sun, J.; Yan, G. Fine-grained private matching for proximity-based mobile social networking. In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 1969–1977. [Google Scholar]
- Fu, Y.; Wang, Y. BCE: A privacy-preserving common-friend estimation method for distributed online social networks without cryptography. In Proceedings of the 7th International Conference on Communications and Networking, Kunming, China, 8–10 August 2012; pp. 212–217. [Google Scholar]
- Sun, J.; Zhang, R.; Zhang, Y. Privacy-preserving spatiotemporal matching. In Proceedings of the IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 800–808. [Google Scholar]
- Bamba, B.; Liu, L.; Pesti, P.; Wang, T. Supporting anonymous location queries in mobile environments with PrivacyGrid. In Proceedings of the 17th international conference on World Wide Web, New York, NY, USA, 21–25 April 2008; pp. 237–246. [Google Scholar]
- Bordenabe, N.E.; Chatzikokolakis, K.; Palamidessi, C. Optimal Geo-Indistinguishable Mechanisms for Location Privacy. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security (CCS ’14), Scottsdale, AZ, USA, 3–7 November 2014; pp. 251–262. [Google Scholar]
- Elaine, S.; Richard, C.; Hubert, C. Privacy-preserving aggregation of time-series data. In Proceedings of the Network and Distributed System Security Symposium (NDSS 2011), San Diego, CA, USA, 6–9 February 2011; pp. 1–17. [Google Scholar]
- Jorgensen, Z.; Yu, T.; Cormode, G. Publishing attributed social graphs with formal privacy guarantees. In Proceedings of the 2016 International Conference on Management of Data, San Francisco, CA, USA, 26 June–1 July 2016; pp. 107–122. [Google Scholar]
- Zhou, C.L.; Chen, Y.H.; Tian, H.; Cai, S.B. Location Privacy and Query Privacy Preserving Method for K-nearest Neighbor Query in Road Networks. J. Softw. 2020, 31, 471–492. [Google Scholar] [CrossRef]
- Li, Z.; Wang, C.; Yang, S.; Jiang, C.; Li, X. Lass: Local-activity and social-similarity based data forwarding in mobile social networks. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 174–184. [Google Scholar] [CrossRef][Green Version]
- Schlegel, R.; Chow, C.; Huang, Q.; Wong, D. User-defined privacy grid system for continuous location-based services. IEEE Trans. Mob. Comput. 2015, 14, 2158–2172. [Google Scholar] [CrossRef]
- Han, M.; Li, L.; Xie, Y.; Wang, J.; Duan, Z.; Li, J.; Yan, M. Cognitive approach for location privacy protection. IEEE Access 2018, 6, 13466–13477. [Google Scholar] [CrossRef]
- Siddula, M.; Li, Y.; Cheng, X.; Tian, Z.; Cai, Z. Privacy-enhancing preferential lbs query for mobile social network users. Wirel. Commun. Mob. Comput. 2020. [Google Scholar] [CrossRef]
- Yang, X.; Yang, M.; Yang, P.; Leng, Q. A multi-authority attribute-based encryption access control for social network. In Proceedings of the 2017 3rd IEEE International Conference on Control Science and Systems Engineering (ICCSSE), Beijing, China, 17–19 August 2017; pp. 671–674. [Google Scholar]
- Luo, E.; Liu, Q.; Wang, G. Hierarchical multi-authority and attribute-based encryption friend discovery scheme in mobile social networks. IEEE Commun. Lett. 2016, 20, 1772–1775. [Google Scholar] [CrossRef]
- Alanwar, A.; Shoukry, Y.; Chakraborty, S.; Martin, P.; Tabuada, P.; Srivastava, M. PrOLoc: Resilient localization with private observers using partial homomorphic encryption. In Proceedings of the 2017 16th ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Pittsburgh, PA, USA, 18–21 April 2017; pp. 41–52. [Google Scholar]
- Boneh, D.; Craig, G.; Brent, W. Collusion resistant broadcast encryption with short ciphertexts and private keys. In Proceedings of the Advances in Cryptology—CRYPTO 2005, Santa Barbara, CA, USA, 14–18 August 2005; pp. 258–275. [Google Scholar]
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 223–238. [Google Scholar]
- Goldwasser, S.; Micali, S. Probabilistic Encryption. J. Comput. Syst. Sci. 1984, 28, 270–299. [Google Scholar] [CrossRef]
- Li, Y.; Zhou, F.; Xu, Z. PPFQ: Privacy-Preserving Friends Query over Online Social Networks. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December–1 January 2021; pp. 1348–1353. [Google Scholar]
- Batcher, K.E. Sorting networks and their applications. In Proceedings of the spring joint computer conference, New York, NY, USA, 30 April–2 May 1968; pp. 307–314. [Google Scholar]
- Veugen, T. Improving the DGK comparison protocol. In Proceedings of the International Workshop on Information Forensics and Security, Tenerife, Spain, 2 December 2012; pp. 49–54. [Google Scholar]
- The OpenSSL Project. OpenSSL: The Open Source Toolkit for SSL/TLS. 2015. Available online: http://www.openssl.org/ (accessed on 26 May 2021).
- Relic-Toolkit. Available online: https://github.com/relic-toolkit (accessed on 26 May 2021).
- Cohen, W.W. Enron Email Dataset. 2015. Available online: https://www.cs.cmu.edu/~enron/ (accessed on 26 May 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).