ACD: An Adaptable Approach for RFID Cloning Attack Detection
Abstract
1. Introduction
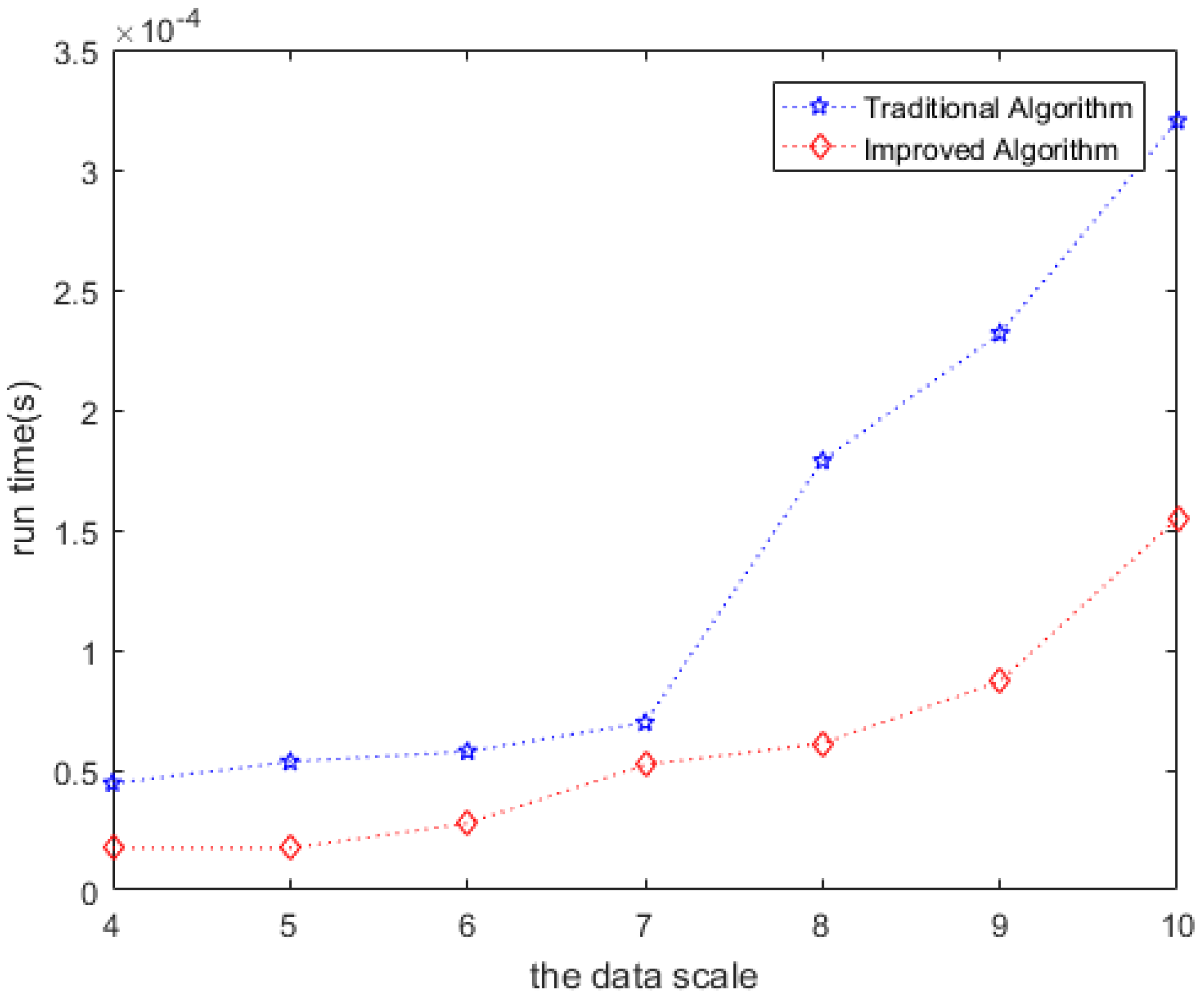
- Utilizing the spatiotemporal collision in spatiotemporal correlations, we propose a clone tag detection method, ACD, based on an improved version of the Floyd-Warshall algorithm. This method can establish the spatiotemporal relationship between nodes when the trajectory is incomplete, and reduce the number of training samples. The improved Floyd-Warshall algorithm can significantly reduce the detection delay.
- ACD has good applicability and portability. There is no need to add equipment for different types of RFID commercial systems, and only the trajectory log is used to model and analyze clone detection. The method can be applied to RFID systems in different frequency bands.
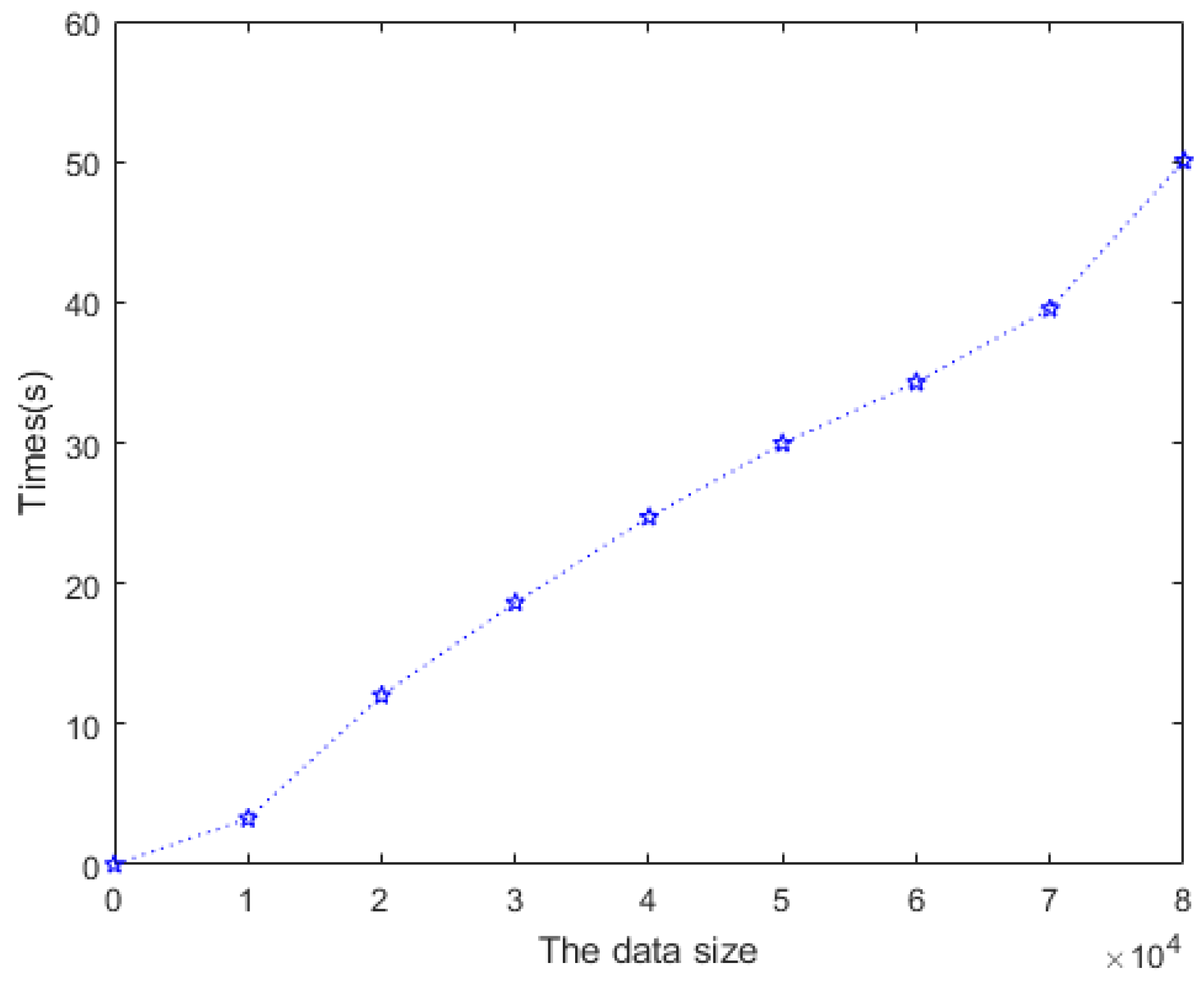
- ACD has real-time performance. The algorithm analyzes trajectory logs in real time, and can detect clone tags in real time. Through experiments, it is found that the detection delay of 10,000 data points is only 3.273 s.
2. Related Work
2.1. Trajectory-Based RFID Clone Detection
2.2. Shortest Path Algorithm
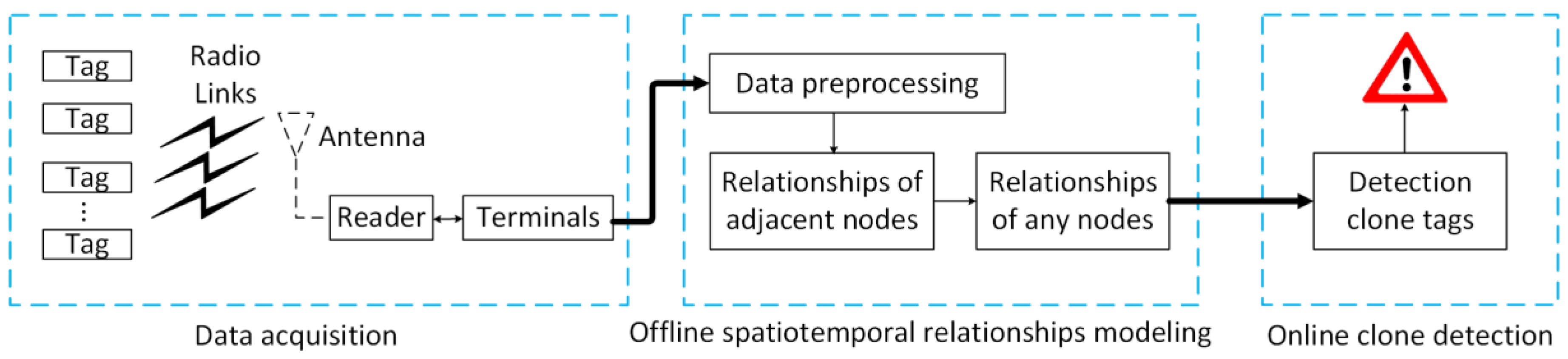
3. Clone Tag Detection Algorithm
3.1. Method Overview and Problem Definition
3.2. Data Structure Definition
3.3. Data Preprocessing
3.4. Offline Spatiotemporal Relationship Modeling
3.4.1. Relationships of Adjacent Nodes

3.4.2. Relationships of Nodes
| Algorithm 1 The Floyd-Warshall’s shortest path algorithm |
| Input: |
| The initial weights of the graph: |
| The number of vertices: |
| Output: |
| The final matrix of the shortest paths: |
| 1: for to do |
| 2: for to do |
| 3: ; |
| 4: end for |
| 5: end for |
| 6: for to do |
| 7: for to do |
| 8: for to do |
| 9: ; |
| 10: end for |
| 11: end for |
| 12: end for |
| 13: return ; |
| Algorithm 2 The improved Floyd-Warshall’s shortest path algorithm |
| Input: |
| The initial weights of the graph: |
| The number of vertices: |
| Output: |
| The final matrix of the shortest paths: |
| 1: for to do |
| 2: for to do |
| 3: ; |
| 4: end for |
| 5: end for |
| 6: for to do |
| 7: for to do |
| 8: |
| 9: for to do |
| 10: ; |
| 11: ; |
| 12: end for |
| 13: end for |
| 14: end for |
| 15: return ; |
3.5. Online Clone Detection
4. Implementation and Evaluation
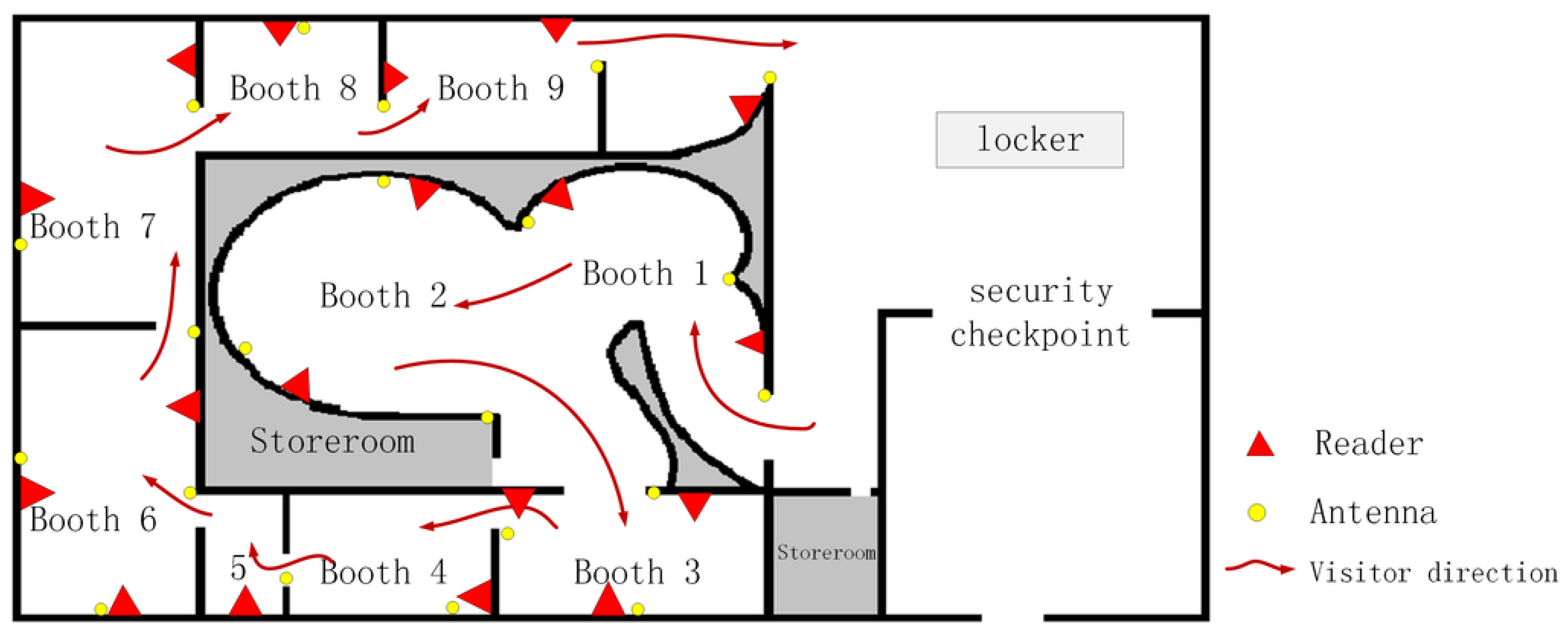
4.1. Experiment Deployment
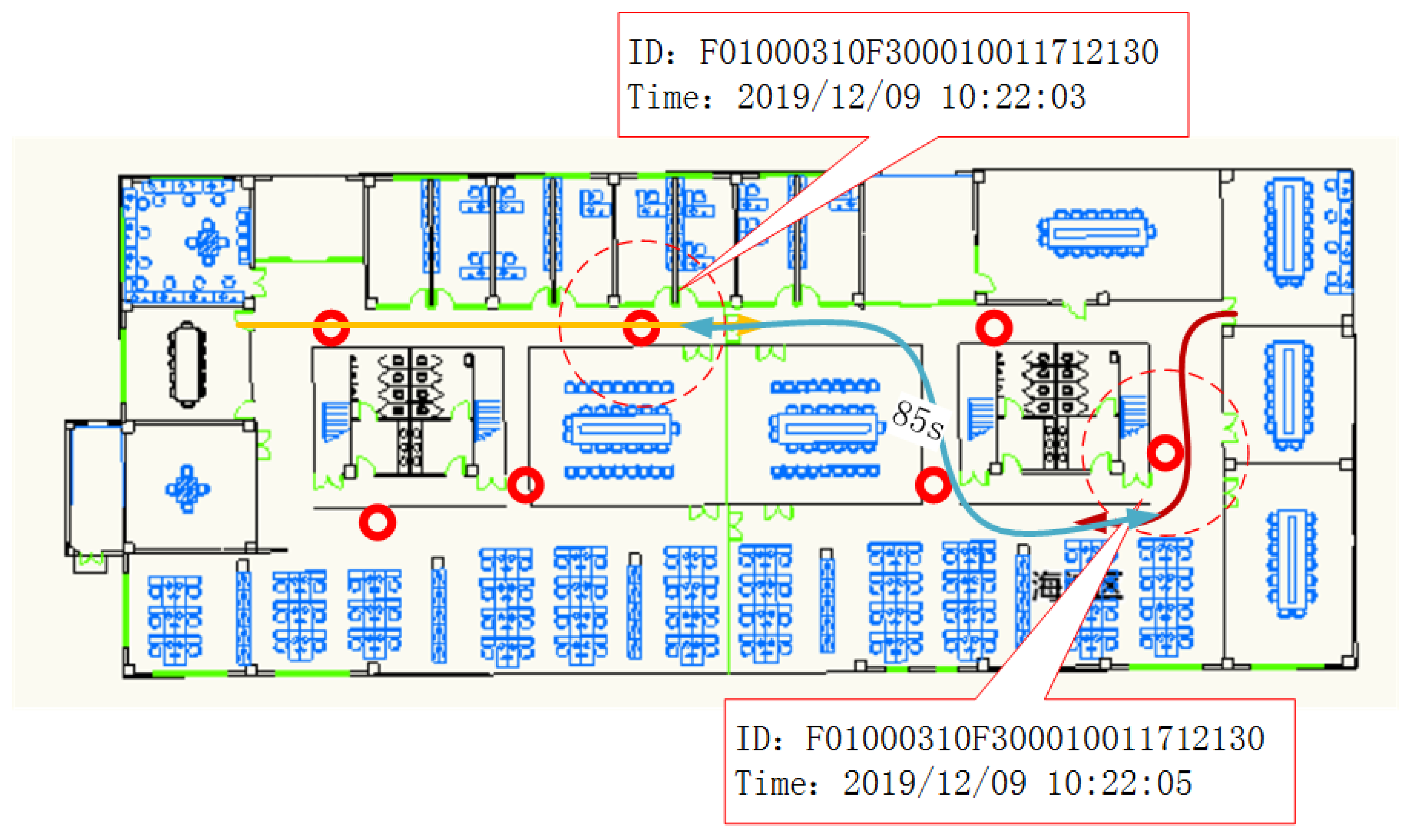
4.2. Clone Detection
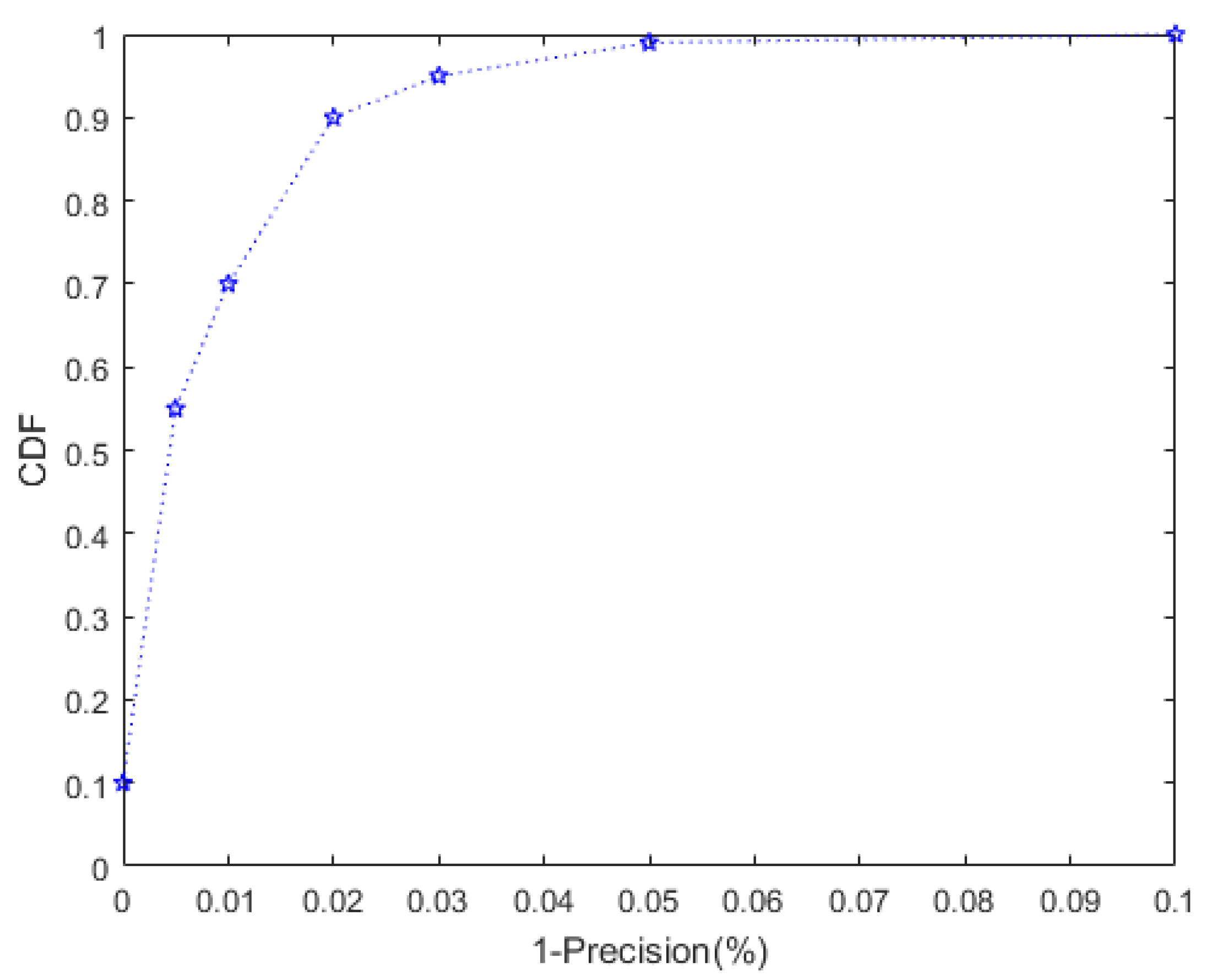
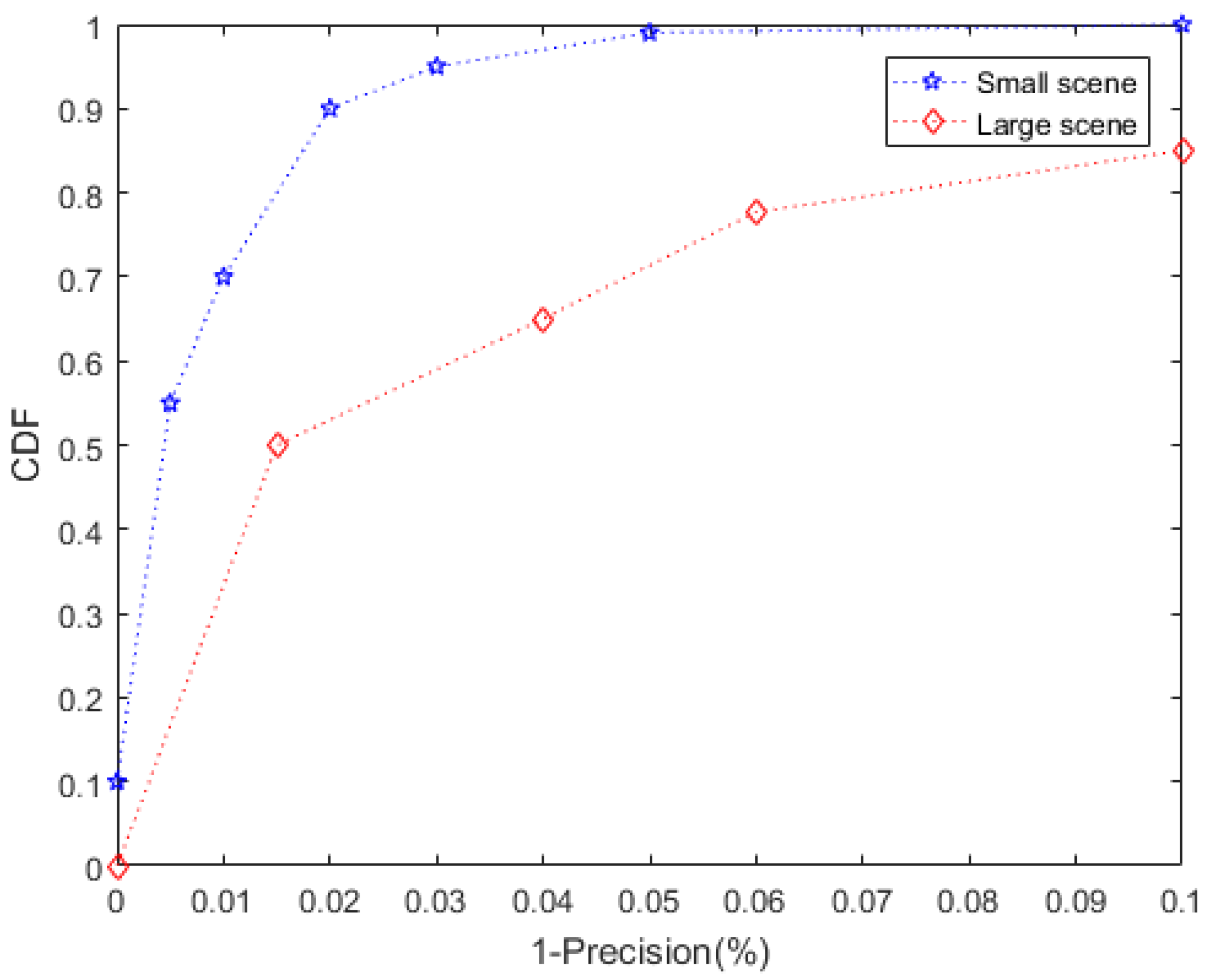
4.2.1. Detection Accuracy of the Clone Event
4.2.2. Real-Time Detection of Clone Event
4.2.3. Effectiveness of the Clone Method
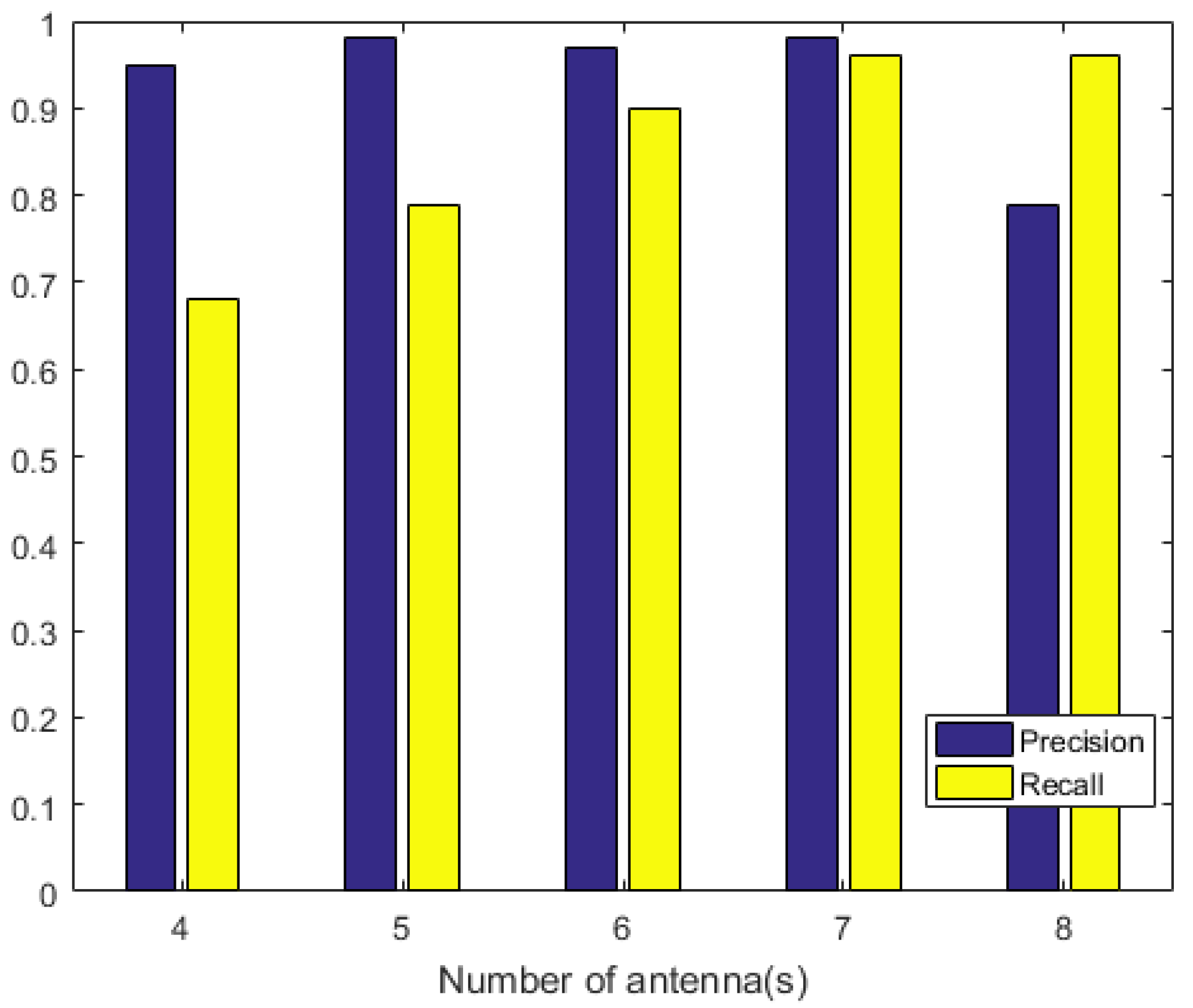
4.3. Adaptivity of the Proposed Scheme
4.4. Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Chen, J.-L.; Chen, M.-C.; Chen, C.-W.; Chang, Y.-C. Architecture design and performance evaluation of RFID object tracking systems. Comput. Commun. 2007, 30, 2070–2086. [Google Scholar] [CrossRef]
- Lee, Y.K.; Batina, L.; Verbauwhede, I. EC-RAC (ECDLP Based Randomized Access Control): Provably Secure RFID authentication protocol. In Proceedings of the 2008 IEEE International Conference on RFID, Las Vegas, NV, USA, 16–17 April 2008; pp. 97–104. [Google Scholar]
- Salleh, A.; Hashim, N.M.Z.; Mohamad, N.R.; Hadi, N.A.A.; Ab Aziz, M. Development of high performance and low cost automatic toll payment system using rfid technology for malaysia environment. Int. J. Adv. Res. Eng. Technol. 2014, 2, 1–7. [Google Scholar]
- Hahnel, D.; Burgard, W.; Fox, D.; Fishkin, K.; Philipose, M. Mapping and localization with RFID technology. In Proceedings of the 2004 IEEE International Conference on Robotics and Automation, New Orleans, LA, USA, 26 April–1 May 2004; pp. 1015–1020. [Google Scholar]
- Wu, D.-L.; Ng, W.W.; Yeung, D.S.; Ding, H.-L. A brief survey on current RFID applications. In Proceedings of the 2009 International Conference on Machine Learning and Cybernetics, Baoding, China, 12–15 July 2009; pp. 2330–2335. [Google Scholar]
- Garcia, F.D.; de Koning Gans, G.; Verdult, R. Tutorial: Proxmark, the swiss army knife for rfid security research. In Proceedings of the 8th Workshop on RFID Security and Privacy (RFIDSec 2012), Nijmegen, The Netherlands, 2–3 July 2012. [Google Scholar]
- Bono, S.C.; Green, M.; Stubblefield, A.; Juels, A.; Rubin, A.D.; Szydlo, M. Security Analysis of a Cryptographically-Enabled RFID Device. In Proceedings of the 14th Conference on USENIX Security Symposium, Baltimore, MD, USA, 31 July–5 August 2005. [Google Scholar]
- Garcia, F.D.; de Koning Gans, G.; Muijrers, R.; van Rossum, P.; Verdult, R.; Schreur, R.W.; Jacobs, B. Dismantling mifare classic. In Proceedings of the Computer Security—ESORICS 2008, 13th European Symposium on Research in Computer Security, Málaga, Spain, 6–8 October 2008. [Google Scholar]
- Oswald, D.; Paar, C. Breaking Mifare DESFire MF3ICD40: Power Analysis and Templates in the Real World. In Proceedings of the 13th International Workshop on Cryptographic Hardware and Embedded Systems, Nara, Japan, 28 September–1 October 2011; pp. 207–222. [Google Scholar]
- Chen, X.; Liu, J.; Wang, X.; Zhang, X.; Wang, Y.; Chen, L. Combating Tag Cloning with COTS RFID Devices. In Proceedings of the 2018 15th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Hong Kong, China, 11–13 June 2018; pp. 1–9. [Google Scholar]
- Krumnikl, M.; Moravec, P.; Olivka, P.; Seidl, D. EM410x RFID Cloned Card Detection System. In Proceedings of the 2015 International Conference on Pervasive and Embedded Computing and Communication Systems (PECCS), Angers, France, 11–13 February 2015; pp. 76–82. [Google Scholar]
- Zhang, G.; Xia, L.; Jia, S.; Ji, Y. Identification of cloned hf rfid proximity cards based on rf fingerprinting. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; pp. 292–300. [Google Scholar]
- Tan, C.; Sheng, B.; Li, Q. Secure and Serverless RFID Authentication and Search Protocols. IEEE Trans. Wirel. Commun. 2008, 7, 1400–1407. [Google Scholar] [CrossRef]
- Yang, L.; Han, J.; Qi, Y.; Liu, Y. Identification-free batch authentication for RFID tags. In Proceedings of the 18th IEEE International Conference on Network Protocols, Kyoto, Japan, 5–8 October 2010; pp. 154–163. [Google Scholar]
- Lehtonen, M.; Ostojic, D.; Ilic, A.; Michahelles, F. Securing RFID Systems by Detecting Tag Cloning. Pervasive Comput. 2009, 5538, 291–308. [Google Scholar] [CrossRef]
- Okpara, S. Detecting Cloning Attack in Low-Cost Passive RFID Tags. An Analytic Comparison between KILL Passwords and Synchronized Secrets Obinna. 2015. [Google Scholar] [CrossRef]
- Babaie, M.; Rahimov, H. Efficient detecting of RFID tag cloning attacks using chaos theory. In Proceedings of the 1st International Conference on Communications Engineering, 22–24 December 2010. pp. 1–6. Available online: http://seminars.usb.ac.ir/Files/iccome/en-us/Document/1597_Babaie.pdf (accessed on 21 April 2020).
- Zanetti, D.; Capkun, S.; Juels, A. Tailing RFID tags for clone detection. In Proceedings of the NDSS Symposium 2013, San Diego, CA, USA, 24–27 February 2013. [Google Scholar]
- Blass, E.-O.; Elkhiyaoui, K.; Molva, R.; Antipolis, E.S. Tracker: Security and privacy for rfid-based supply chains. In Proceedings of the NDSS11, 18th Annual Network and Distributed System Security Symposium, San Diego, CA, USA, 6–9 February 2011. [Google Scholar]
- Shi, J.; Kywe, S.M.; Li, Y. Batch Clone Detection in RFID-enabled supply chain. In Proceedings of the 2014 IEEE International Conference on RFID (IEEE RFID), Orlando, FL, USA, 8–10 April 2014; pp. 118–125. [Google Scholar]
- Maleki, H.; Rahaeimehr, R.; van Dijk, M. Lightsource: Ultra lightweight clone detection of rfid tags from software unclonable responses. Cryptol. ePrint Arch. 2016. Available online: https://eprint.iacr.org/2016/608.pdf (accessed on 21 April 2020).
- Gope, P.; Lee, J.; Quek, T.Q.S. Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J. 2018, 6, 580–589. [Google Scholar] [CrossRef]
- Kamaludin, H.; Mahdin, H.; Abawajy, J.H. Clone tag detection in distributed RFID systems. PLoS ONE 2018, 13, e0193951. [Google Scholar] [CrossRef] [PubMed]
- Wang, P.; Zhou, Y.; Zhu, C.; Huang, J.; Zhang, W. Analysis on abnormal behavior of insider threats based on accesslog mining. CAAI Trans. Intell. Syst. 2017, 12, 781–789. [Google Scholar]
- Mirowski, L.; Hartnett, J. Deckard: A system to detect change of RFID tag ownership. Int. J. Comput. Sci. Netw. Secur. 2007, 7, 89–98. [Google Scholar]
- Ouafi, K.; Vaudenay, S. Pathchecker: An rfid application for tracing products in supply-chains. In Proceedings of the RFIDSec 2009, Leuven, Belgium, 30 June 30–2 July 2009. [Google Scholar]
- Deng, Y.; Chen, Y.; Zhang, Y.; Mahadevan, S. Fuzzy Dijkstra algorithm for shortest path problem under uncertain environment. Appl. Soft Comput. 2012, 12, 1231–1237. [Google Scholar] [CrossRef]
- Hougardy, S. The Floyd–Warshall algorithm on graphs with negative cycles. Inf. Proc. Lett. 2010, 110, 279–281. [Google Scholar] [CrossRef]
- Manaf, K.; Uriawan, W.; Agustian, W.; Gerhana, Y.A.; Jumadi, J.; Ramdhani, M.A. Designing futsal match finder application with floyd-warshall algorithm. J. Phys. Conf. Ser. IOP Publ. 2019, 1280, 022024. [Google Scholar] [CrossRef]
- Wolfram, M.; Schlegel, S.; Westermann, D. Closed loop flow detection in power systems based on Floyd-Warshall algorithm. In Proceedings of the 2017 IEEE Manchester PowerTech, Manchester, UK, 18–22 June 2017; pp. 1–6. [Google Scholar]
- Aziz, A.; Farid, M.M.; Suryani, E. Floyd warshall algorithm with FIS Sugeno for search evacuation route optimization. In Proceedings of the 2017 International Seminar on Application for Technology of Information and Communication (iSemantic), Semarang, Indonesia, 7–8 October 2017; pp. 147–151. [Google Scholar]
- Nikitin, P.; Rao, K.; Lazar, S. An Overview of Near Field UHF RFID. In Proceedings of the 2007 IEEE International Conference on RFID, Grapevine, TX, USA, 26–28 March 2007; pp. 167–174. [Google Scholar]
- Aini, A.; Salehipour, A. Speeding up the Floyd–Warshall algorithm for the cycled shortest path problem. Appl. Math. Lett. 2012, 25, 1–5. [Google Scholar] [CrossRef]
- Elkhiyaoui, K.; Blass, E.O.; Molva, R. CHECKER: On-site checking in RFID-based supply chains. In Proceedings of the Fifth ACM Conference on Security and Privacy in Wireless and Mobile Networks, Tucson, AZ, USA, 16–18 April 2012; pp. 173–184. [Google Scholar]



| Tag ID. | Node ID | Recording Time |
|---|---|---|
| 00B07A13E010A24800000266 | 003 | 2019/12/4 14:16:07 |
| 00B07A13E010A24800000266 | 001 | 2019/12/4 14:06:23 |
| F01000310F30010011712011 | 003 | 2019/12/4 14:07:34 |
| F01000310F30010011712011 | 002 | 2019/12/4 14:04:12 |
| 00B07A13E010A24800000266 | 002 | 2019/12/4 14:10:12 |
| F01000310F30010011712011 | 004 | 2019/12/4 14:40:28 |
| F01000310F30010011712011 | 001 | 2019/12/4 14:25:00 |
| … | … | … |
| Number of Nodes | Node Sequence Number | Dataset Size (Normal Datasets\Test Set) |
|---|---|---|
| 4 | a, d, g, h | 34,076\36,034 |
| 5 | a, c, d, g, h | 45,043\53,724 |
| 6 | a, c, d, f, g, h | 50,419\57,812 |
| 7 | a, b, c, d, f, g, h | 63,032\68,102 |
| 8 | a, b, c, d, e, f, g, h | 78,939\90,176 |
| Name of Methods | Deterministic | Probabilistic | COTS | Not Add Communication Delay | Real-Time |
|---|---|---|---|---|---|
| Pathchecker | √ | √ | |||
| Tracker | √ | √ | |||
| Lightsource | √ | √ | |||
| CHECKER | √ | √ | √ | ||
| ACD | √ | √ | √ | √ |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, W.; Zhang, Y.; Feng, Y. ACD: An Adaptable Approach for RFID Cloning Attack Detection. Sensors 2020, 20, 2378. https://doi.org/10.3390/s20082378
Huang W, Zhang Y, Feng Y. ACD: An Adaptable Approach for RFID Cloning Attack Detection. Sensors. 2020; 20(8):2378. https://doi.org/10.3390/s20082378
Chicago/Turabian StyleHuang, Weiqing, Yanfang Zhang, and Yue Feng. 2020. "ACD: An Adaptable Approach for RFID Cloning Attack Detection" Sensors 20, no. 8: 2378. https://doi.org/10.3390/s20082378
APA StyleHuang, W., Zhang, Y., & Feng, Y. (2020). ACD: An Adaptable Approach for RFID Cloning Attack Detection. Sensors, 20(8), 2378. https://doi.org/10.3390/s20082378





