Towards Improving TSCH Energy Efficiency: An Analytical Approach to a Practical Implementation
Abstract
1. Introduction
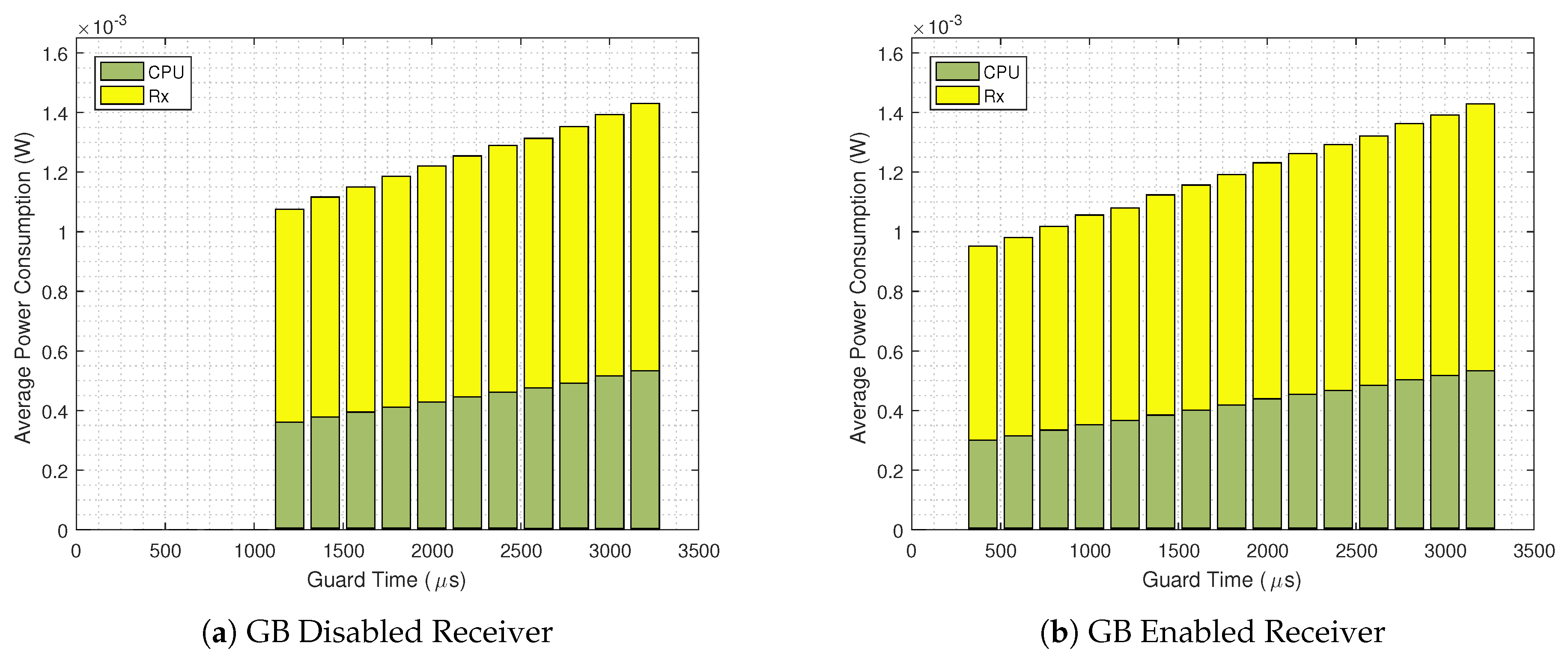
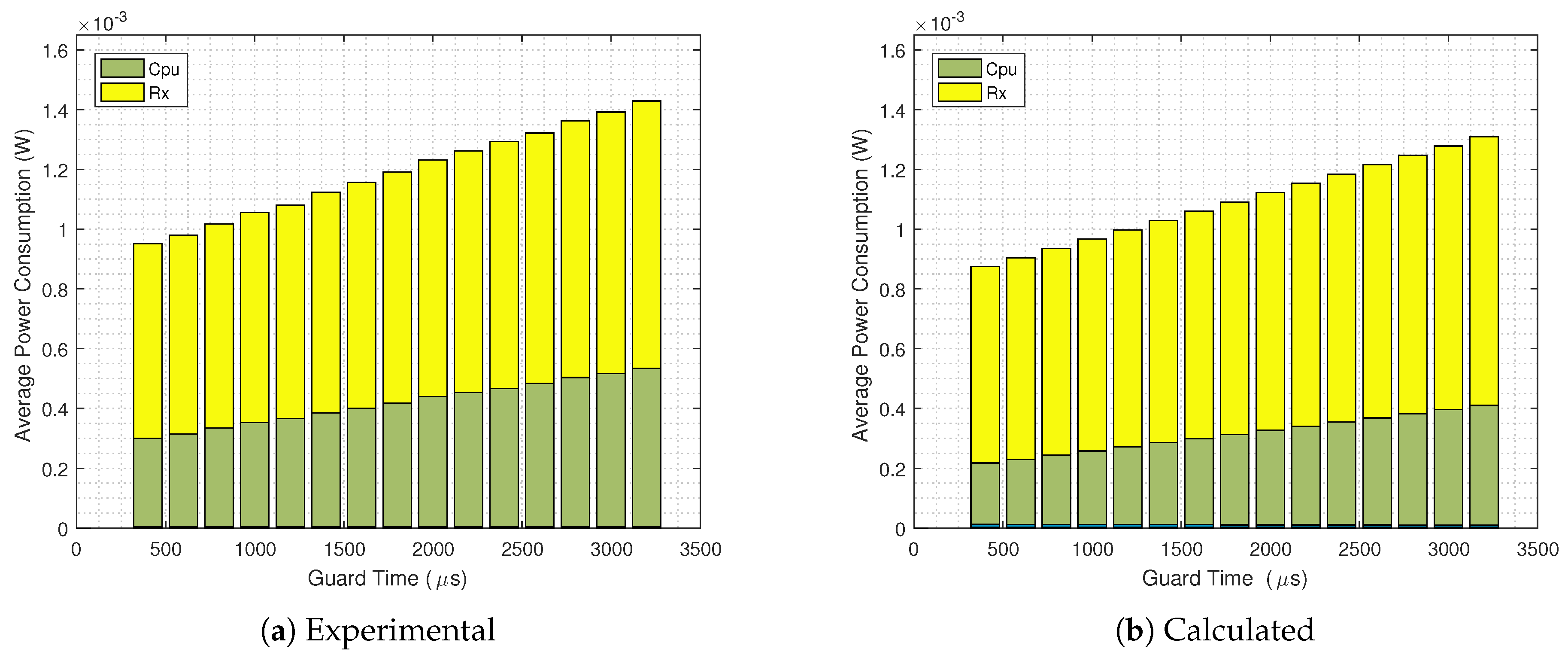
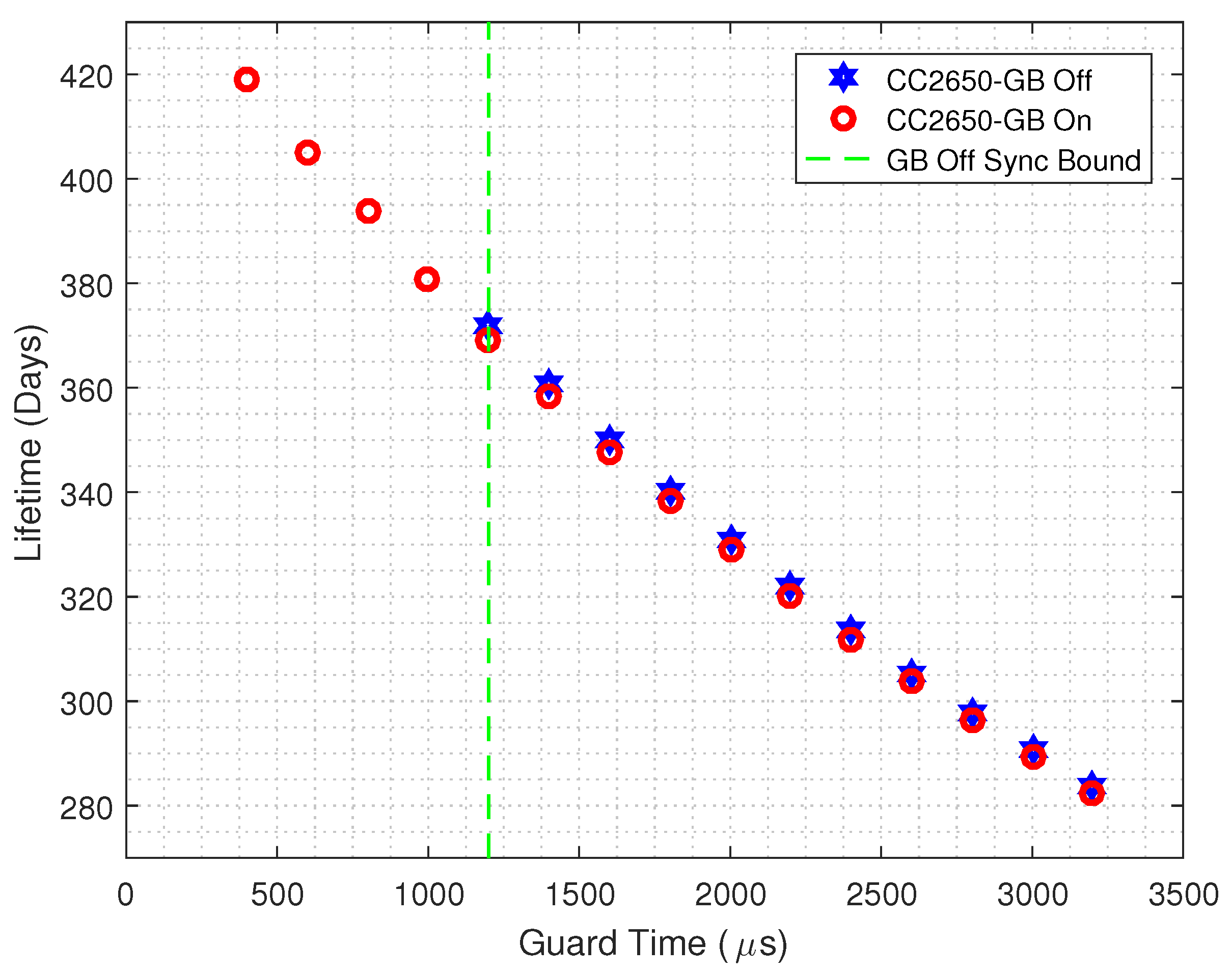
- We resort to the Guard Beacon strategy aiming at reducing the guard time of a TSCH-based network. Our results indicate that the standard Contiki’s TSCH implementation [24] power consumption is up to 13.05% higher than when our scheme is implemented;
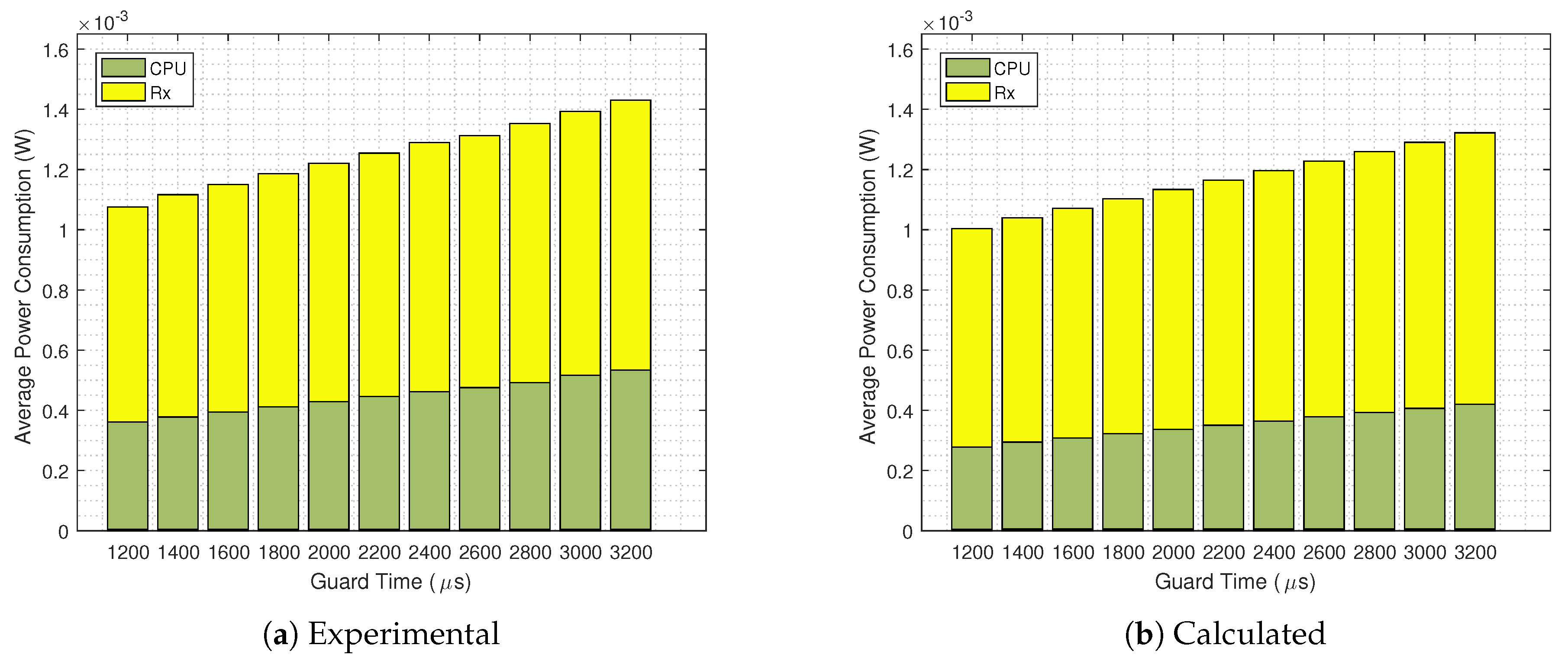
- We perform a set of measurements on the Contiki’s TSCH timing, which allows us to provide a more updated set of time slots and states then the ones from [22], also including the Guard Beacon strategy. The model accuracy is verified by comparing the analytical results to the ones obtained from the Contiki’s Powertrace and Energest tools, which presents a close match regardless of the guard time length or the packet sizes.
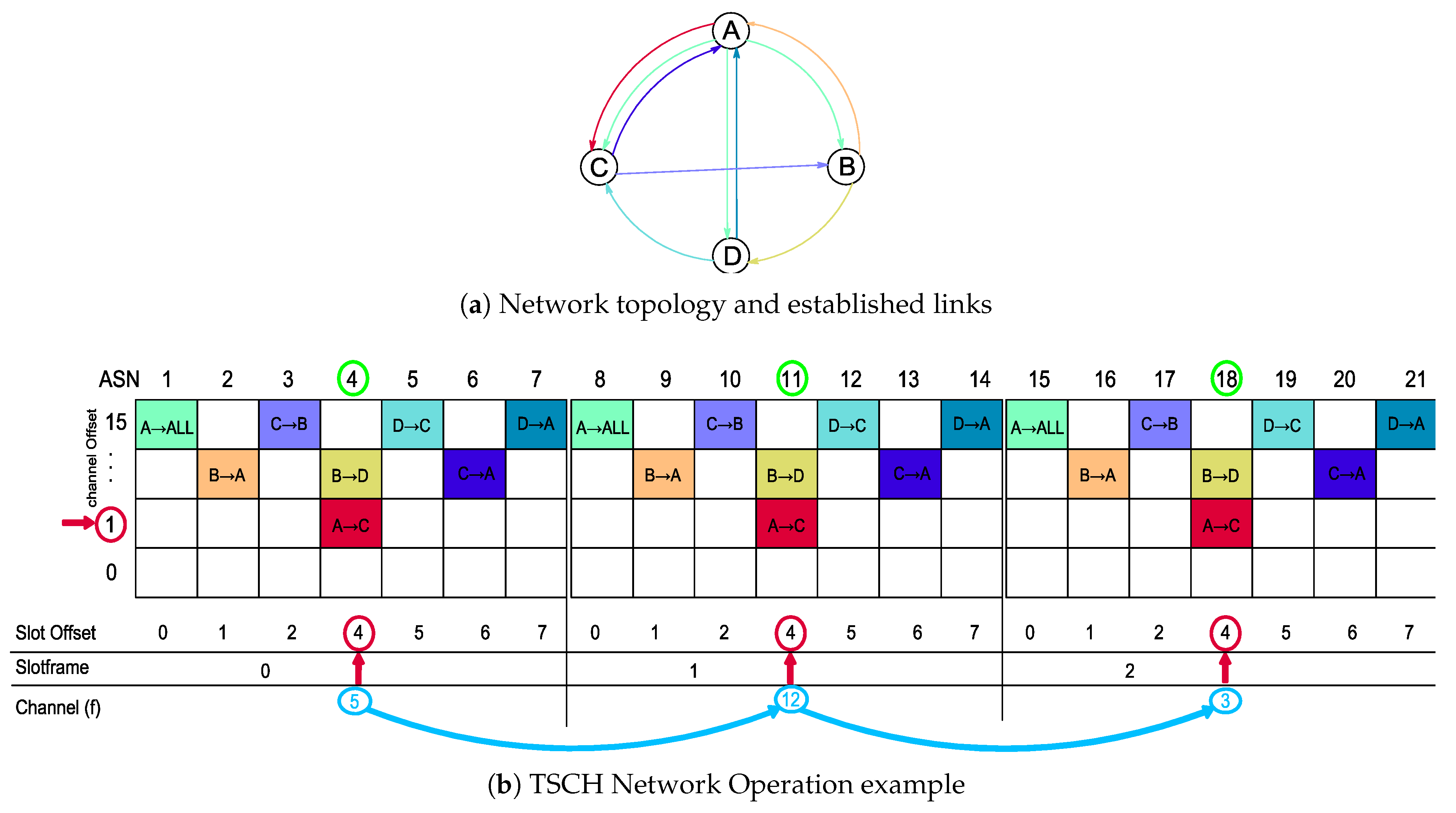
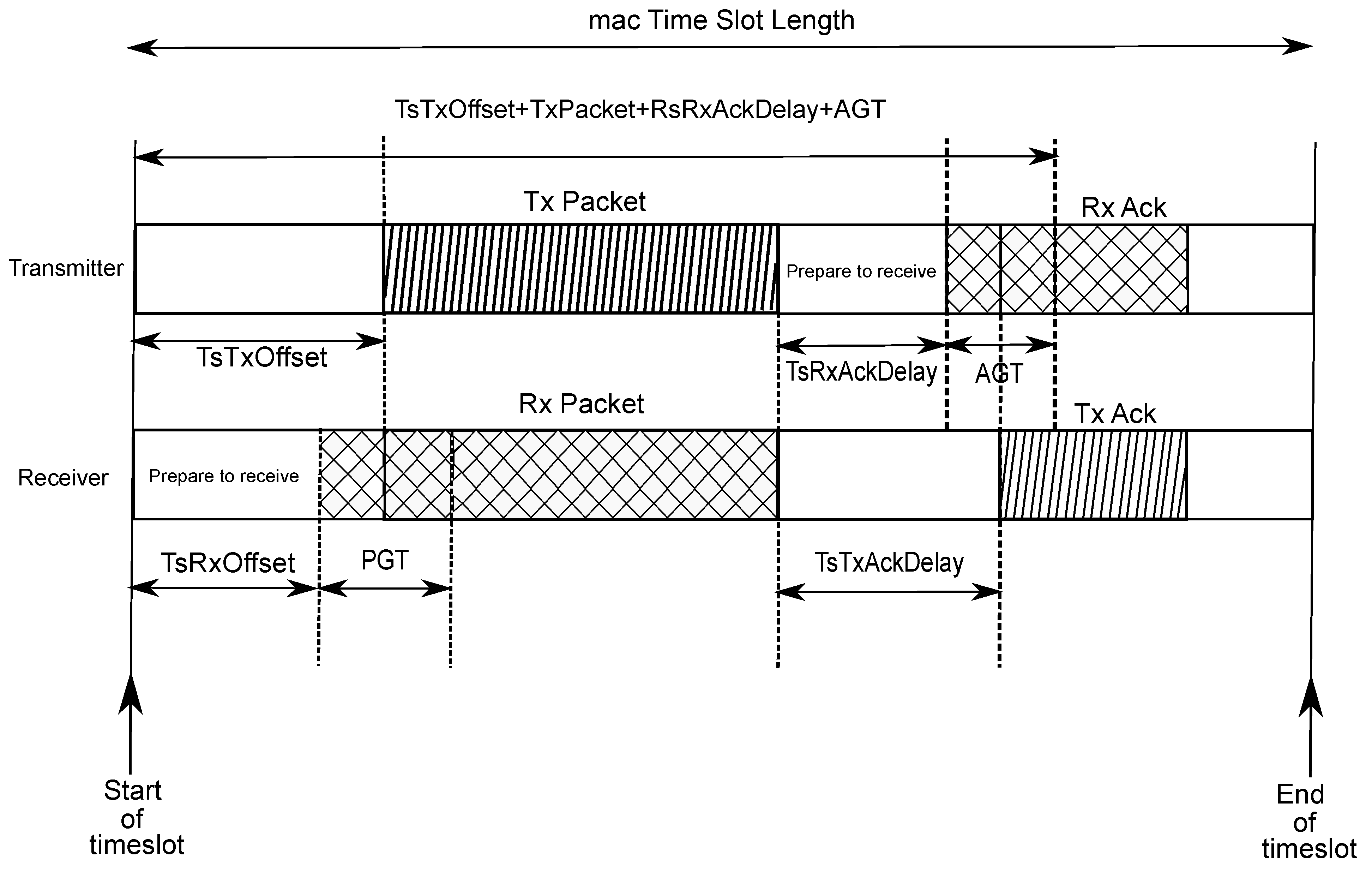
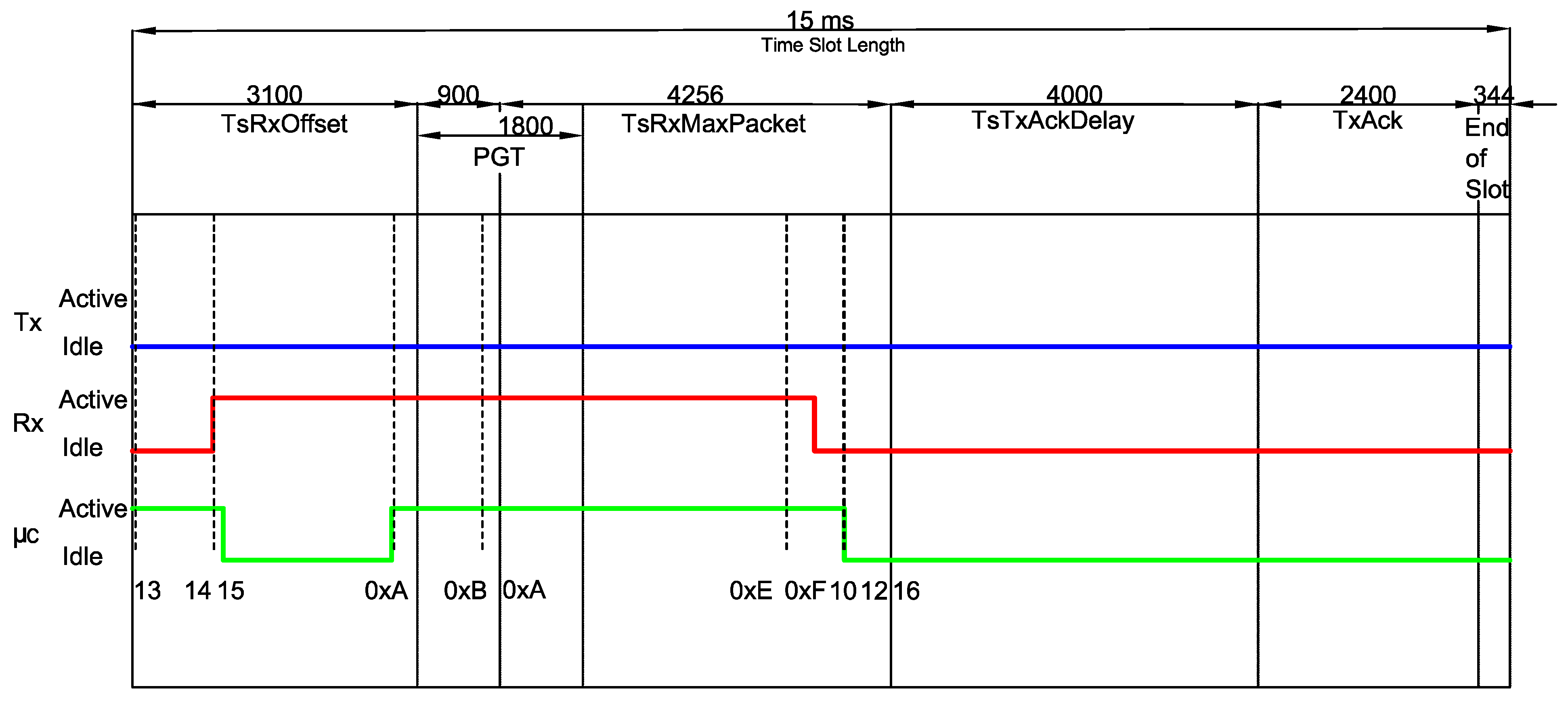
2. Time Slotted Channel Hopping—TSCH
3. Energy Consumption Model
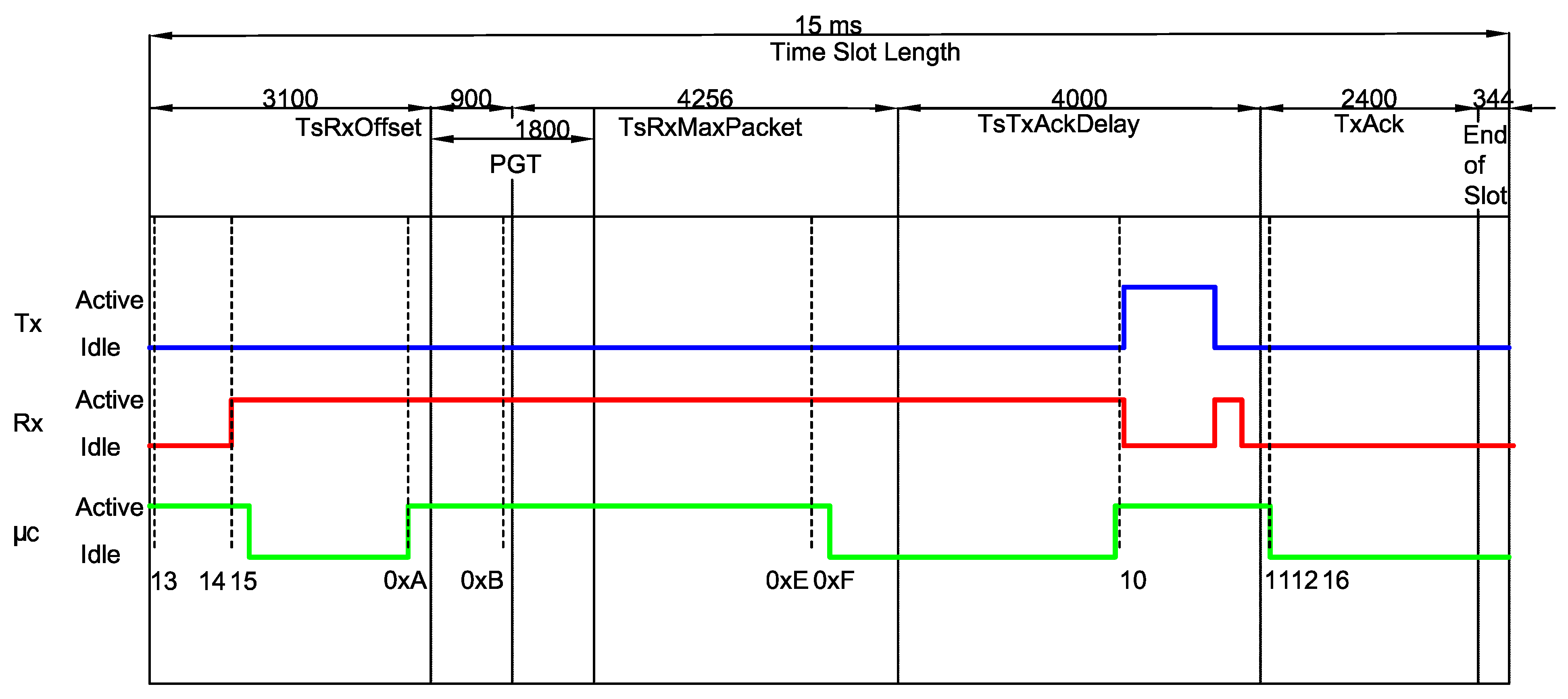
3.1. Energy Consumption of a CC2650 Running Contiki OS
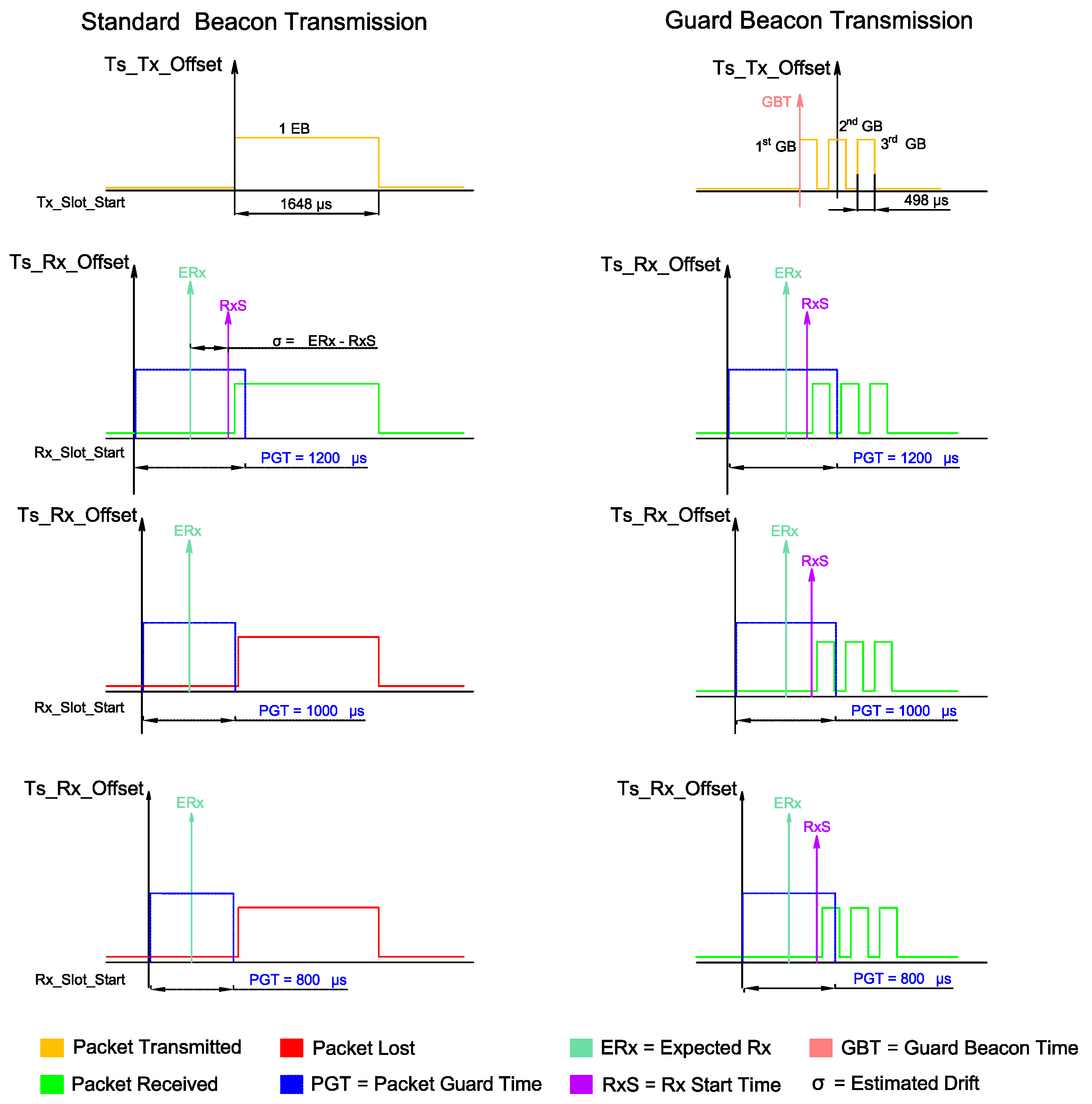
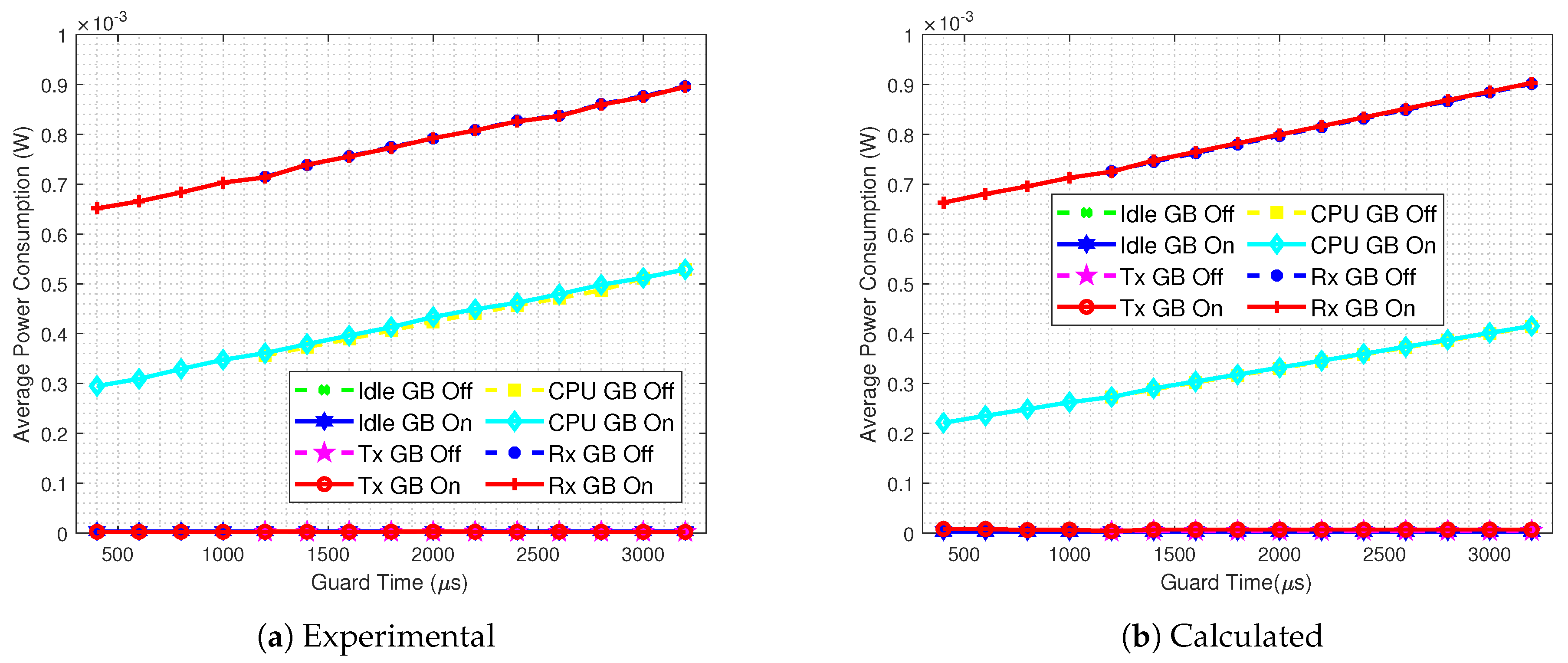
3.2. The Guard Beacon Strategy
- In a TxData or TxDataRxAck slot, the radio was supposed to enter in a sleep mode after finishing the packet transmission; however, it remains active for approximately an additional period of ;
- Although there is no incoming Ack in a TxData slot, the receiver remains active for about ;
- Upon receiving a packet, the receiver unnecessarily remains active for extra ~ in a RxData slot, regardless of the size of the received packet;
- The CPU remains active after the end of the timeslot for approximately in the TxDataRxAck timeslot and about for RxDataTxAck.
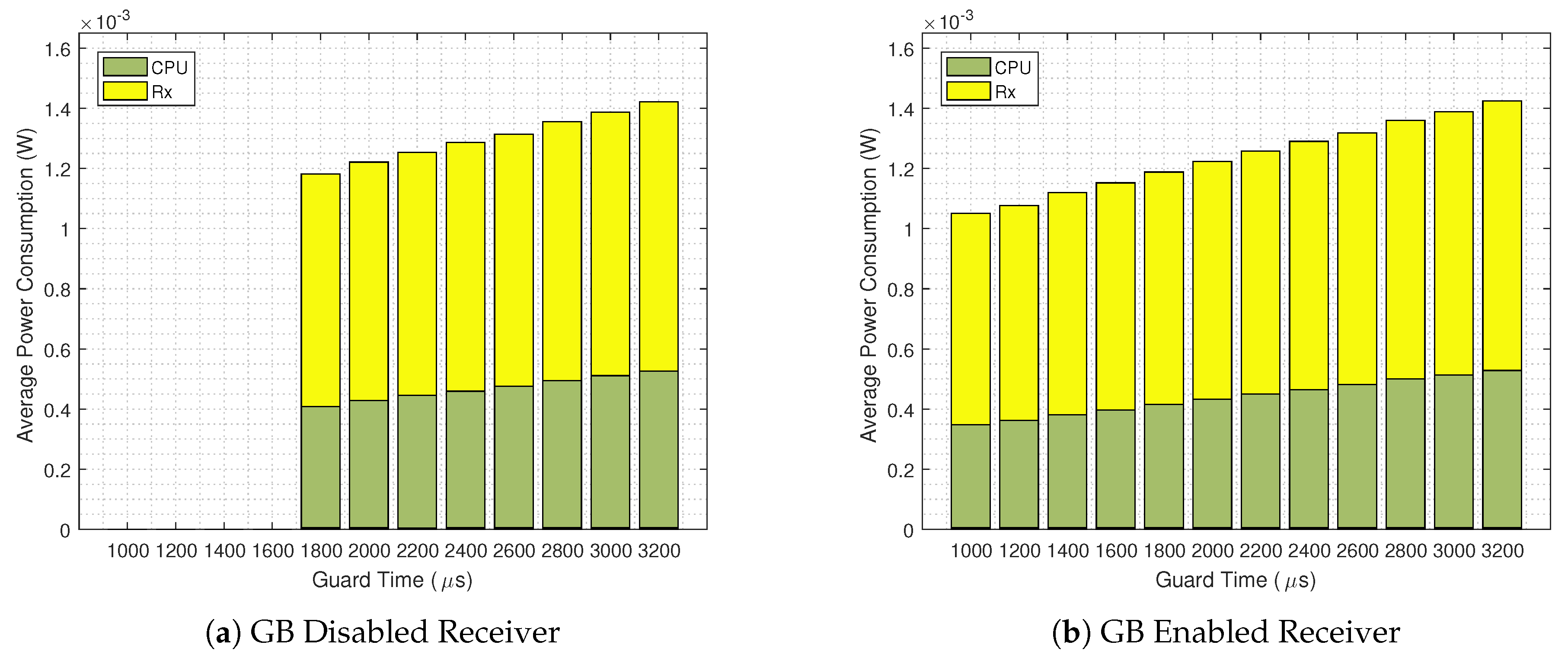
4. Performance Evaluation
- When the Guard Beacon strategy is implemented, energy savings can be achieved by considerably reducing the guard time;
- The difference between experimental and analytical values is mainly due to the CPU power consumption, since the analytical model does not encompass the CPU states outside the TSCH code.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ren, J.; Zhang, Y.; Zhang, K.; Liu, A.; Chen, J.; Shen, X.S. Lifetime and Energy Hole Evolution Analysis in Data-Gathering Wireless Sensor Networks. IEEE Trans. Ind. Informat. 2016, 12, 788–800. [Google Scholar] [CrossRef]
- Yetgin, H.; Cheung, K.T.K.; El-Hajjar, M.; Hanzo, L.H. A Survey of Network Lifetime Maximization Techniques in Wireless Sensor Networks. IEEE Commun. Surveys Tuts. 2017, 19, 828–854. [Google Scholar] [CrossRef]
- Youssef, M.F.; Elsayed, K.M.F.; Zahran, A.H. Contiki-AMAC–The enhanced adaptive radio duty cycling protocol: Proposal and analysis. In Proceedings of the 2016 Int. Conf. on Sel. Topics in Mobile Wireless Netw. (MoWNeT), Cairo, Egypt, 11–13 April 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Texas Instruments. CC2650 SimpleLink™ Multistandard Wireless MCU. Available online: https://www.ti.com/lit/ds/symlink/cc2650.pdf (accessed on 23 October 2020).
- Duquennoy, S.; Elsts, A.; Nahas, B.A.; Oikonomou, G. TSCH and 6TiSCH for Contiki: Challenges, Design and Evaluation. In Proceedings of the 2017 13th International Conference on Distributed Computing in Sensor Systems (DCOSS), Ottawa, ON, Canada, 5–7 June 2017; pp. 11–18. [Google Scholar] [CrossRef]
- IEEE. IEEE Standard for Low-Rate Wireless Personal Area Networks (LRWPANs). Available online: https://standards.ieee.org/standard/802_15_4-2015.html (accessed on 23 October 2020).
- Djenouri, D.; Bagaa, M. Synchronization Protocols and Implementation Issues in Wireless Sensor Networks: A Review. IEEE Syst. J. 2016, 10, 617–627. [Google Scholar] [CrossRef]
- Vera-Pérez, J.; Todolí-Ferrandis, D.; Santonja-Climent, S.; Silvestre-Blanes, J.; Sempere-Payá, V. A Joining Procedure and Synchronization for TSCH-RPL Wireless Sensor Networks. Sensors 2018, 18, 3556. [Google Scholar] [CrossRef] [PubMed]
- Chen, Y.; Qin, F.; Yi, W. Guard Beacon: An Energy-Efficient Beacon Strategy for Time Synchronization in Wireless Sensor Networks. IEEE Commun. Lett. 2014, 18, 987–990. [Google Scholar] [CrossRef]
- Mavromatis, A.; Papadopoulos, G.Z.; Fafoutis, X.; Elsts, A.; Oikonomou, G.; Tryfonas, T. Impact of Guard Time Length on IEEE 802.15.4e TSCH Energy Consumption. In Proceedings of the 2016 13th Annual IEEE International Conference on Sensing, Communication and Networking (SECON), London, UK, 27–30 June 2016; pp. 1–3. [Google Scholar] [CrossRef]
- Papadopoulos, G.Z.; Mavromatis, A.; Fafoutis, X.; Montavont, N.; Piechocki, R.; Tryfonas, T.; Oikonomou, G. Guard time optimisation and adaptation for energy efficient multi-hop TSCH networks. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; pp. 301–306. [Google Scholar] [CrossRef]
- Papadopoulos, G.; Mavromatis, A.; Fafoutis, X.; Piechocki, R.; Tryfonas, T.; Oikonomou, G. Guard Time Optimisation for Energy Efficiency in IEEE 802.15.4-2015 TSCH Links. In Proceedings of the EAI International Conference on Interoperability, Safety and Security in IoT. 2nd InterIoT 2016 and 3rd SaSeIoT 2016, Paris, France, 26–27 October 2016; pp. 56–63. [Google Scholar] [CrossRef]
- Mavromatis, A.; Papadopoulos, G.Z.; Elsts, A.; Montavont, N.; Piechocki, R.; Tryfonas, T.; Oikonomou, G.; Fafoutis, X. Adaptive Guard Time for Energy-Efficient IEEE 802.15.4 TSCH Networks. In Proceedings of the 17th IFIP WG 6.2 International Conference on Wired/Wireless Internet Communication (WWIC), Bologna, Italy, 17–18 June 2019; pp. 15–26. [Google Scholar] [CrossRef]
- Vera-Pérez, J.; Todolí-Ferrandis, D.; Silvestre-Blanes, J.; Sempere-Payá, V. Bell-X, An Opportunistic Time Synchronization Mechanism for Scheduled Wireless Sensor Networks. Sensors 2019, 19, 4128. [Google Scholar] [CrossRef] [PubMed]
- Karalis, A.; Zorbas, D.; Douligeris, C. Collision-Free Advertisement Scheduling for IEEE 802.15.4-TSCH Networks. Sensors 2019, 19, 1789. [Google Scholar] [CrossRef] [PubMed]
- Papadopoulos, G.Z.; Fafoutis, X.; Thubert, P. Multi-Source Time Synchronization in IEEE Std 802.15.4-2015 TSCH Networks. Internet Technol. Lett. 2020, 3, 148. [Google Scholar] [CrossRef]
- Dunkels, A.; Gronvall, B.; Voigt, T. Contiki-a lightweight and flexible operating system for tiny networked sensors. In Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks (LCN), Tampa, FL, USA, 16–18 November 2004; pp. 455–462. [Google Scholar] [CrossRef]
- Levis, P. TinyOS: An Operating System for Sensor Networks. In Ambient Intelligence; Weber, W., Rabaey, J.M., Aarts, E., Eds.; Springer: Berlin, Germany, 2005; pp. 115–148. [Google Scholar] [CrossRef]
- Baccelli, E.; Hahm, O.; Gunes, M.; Wahlisch, M.; Schmidt, T.C. RIOT OS: Towards an OS for the Internet of Things. In Proceedings of the 2013 IEEE Conference on Computer Communication Workshops (INFOCOM WKSHPS), Turin, Italy, 14–19 April 2013; pp. 79–80. [Google Scholar] [CrossRef]
- Watteyne, T.; Vilajosana, X.; Kerkez, B.; Chraim, F.; Weekly, K.; Wang, Q.; Glaser, S.; Pister, K. OpenWSN: A standards-based low-power wireless development environment. Trans. Emerging Tel. Tech. 2012, 23, 480–493. [Google Scholar] [CrossRef]
- The Zephyr Project. An RTOS for IoT. Available online: http://www.zephyrproject.org (accessed on 23 October 2020).
- Daneels, G.; Municio, E.; Van de Velde, B.; Ergeerts, G.; Weyn, M.; Latré, S.; Famaey, J. Accurate Energy Consumption Modeling of IEEE 802.15.4e TSCH Using Dual-Band OpenMote Hardware. Sensors 2018, 18, 437. [Google Scholar] [CrossRef] [PubMed]
- Vilajosana, X.; Wang, Q.; Chraim, F.; Watteyne, T.; Chang, T.; Pister, K.S.J. A Realistic Energy Consumption Model for TSCH Networks. IEEE Sens. J. 2014, 14, 482–489. [Google Scholar] [CrossRef]
- Dunkels, A. Contiki, the open source OS for the Internet of Things. Available online: https://github.com/contiki-os/contiki (accessed on 23 October 2020).
- Dunkels, A.; Eriksson, J.; Finne, N.; Tsiftes, N. Powertrace: Network-level Power Profiling for Low-power Wireless Networks. Available online: http://soda.swedishict.se/4112/ (accessed on 23 October 2020).
- Kovatsch, M.; Duquennoy, S.; Dunkels, A. A Low-Power CoAP for Contiki. In Proceedings of the 2011 IEEE 8th International Conference on Mobile Ad-Hoc and Sensor Syst. (MASS), Valencia, Spain, 17–22 October 2011; pp. 855–860. [Google Scholar] [CrossRef]
- Rayel, O.K.; de Sordi, M.A. Contiki’s TSCH Guard Beacon Implementation. Available online: https://zenodo.org/record/3268707 (accessed on 23 October 2020).




| Number | Number | ||
|---|---|---|---|
| TX_INIT | 0x01 | RX_IDLE_RX_OFF | 0x0D |
| TS_TX_OFFSET_AFTER_TRANSMIT | 0x03 | PACKET_DETECTED | 0x0E |
| TS_RX_ACK_DELAY | 0x04 | PACKET_RECEIVED | 0x0F |
| TS_ACK_WAIT | 0x05 | RX_OFF_AFTER_PACKET_RECEIVED | 0x10 |
| ACK_RECEIVED | 0x06 | RX_ACK_SEND | 0x11 |
| RADIO_OFF_AFTER_ACK_RECEIVED | 0x07 | RX_END | 0x12 |
| RADIO_OFF_END_TX_SLOT | 0x08 | SLOT_START | 0x13 |
| TX_END | 0x09 | SLOT_START_TURN_RADIO_ON | 0x14 |
| RX_INIT | 0x0A | SLOT_START_RADIO_IS_ON | 0x15 |
| TS_RX_OFFSET | 0x0B | SLOT_END | 0x16 |
| RX_IDLE | 0x0C | SLOT_OPERATION_END | 0x18 |
| RxDataTxAck | RxData | RxGB | RxIdle | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| CPU | Tx | Rx | CPU | Tx | Rx | CPU | Tx | Rx | CPU | Tx | Rx | ||
| 0x0A | 0 | PGT | 0 | PGT | 0 | PGT | 0 | PGT | |||||
| 0x0B | PGT | 0 | PGT | PGT | 0 | PGT | 0 | PGT | 0 | PGT | |||
| 0x0C | - | - | - | - | - | - | - | - | - | 0 | |||
| 0x0D | - | - | - | - | - | - | - | - | - | 0 | 0 | ||
| 0x0E | 0 | 0 | 0 | - | - | - | |||||||
| 0x0F | 0 | 0 | 0 | - | - | - | |||||||
| 0x10 | 0 | 0 | - | - | - | ||||||||
| 0x11 | - | - | - | - | - | - | - | - | - | ||||
| 0x12 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |||||
| 0x13 | 0 | 0 | 0 | 0 | 29 | 0 | 0 | 0 | 0 | ||||
| 0x14 | 0 | 0 | 0 | 0 | |||||||||
| 0x15 | 0 | 6 | 0 | 6 | 6 | 0 | 6 | 6 | 0 | 6 | |||
| 0x16 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |||||
| TxDataRxAck | TxData | TxGB | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| CPU | Tx | Rx | CPU | Tx | Rx | CPU | Tx | Rx | ||
| 0x01 | ||||||||||
| 0x03 | 0 | 0 | 0 | |||||||
| 0x04 | 0 | - | - | - | - | - | - | |||
| 0x05 | 0 | - | - | - | - | - | - | |||
| 0x06 | 0 | - | - | - | - | - | - | |||
| 0x07 | 0 | - | - | - | - | - | - | |||
| 0x08 | 0 | 0 | 0 | 0 | 0 | 0 | ||||
| 0x09 | 0 | 0 | 0 | 0 | 0 | 0 | ||||
| 0x13 | 32 | 0 | 0 | 26 | 0 | 0 | 26 | 0 | 0 | |
| 0x14 | 0 | 0 | 0 | |||||||
| 0x15 | 0 | 0 | 0 | |||||||
| 0x16 | 0 | 0 | 0 | 0 | 0 | 0 | ||||
| Set of States | |
|---|---|
| RxDataTxAck | 0x13, 0x14, 0x15, 0x0A, 0x0B, 0x0E, 0x0F, 0x10, 0x11, 0x12, 0x16 |
| RxData | 0x13, 0x14, 0x15, 0x0A, 0x0B, 0x0E, 0x0F, 0x10, 0x12, 0x16 |
| RxIdle | 0x13, 0x14, 0x15, 0x0A, 0x0B, 0x0C, 0x0D, 0x12, 0x16 |
| TxDataRxAck | 0x13, 0x14, 0x15, 0x01, 0x03, 0x04, 0x05, 0x06, 0x07, 0x08, 0x09, 0x16 |
| TxData | 0x13, 0x14, 0x15, 0x01, 0x03, 0x08, 0x09, 0x16 |
| RxGB | 0x13, 0x14, 0x15, 0x0A, 0x0B, 0x0E, 0x0F, 0x10, 0x12, 0x16 |
| TxGB | 0x13, 0x14, 0x15, 0x01, 0x03, 0x08, 0x09, 0x16 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sordi, M.A.; K. Rayel, O.; Moritz, G.L.; Rebelatto, J.L. Towards Improving TSCH Energy Efficiency: An Analytical Approach to a Practical Implementation. Sensors 2020, 20, 6047. https://doi.org/10.3390/s20216047
Sordi MA, K. Rayel O, Moritz GL, Rebelatto JL. Towards Improving TSCH Energy Efficiency: An Analytical Approach to a Practical Implementation. Sensors. 2020; 20(21):6047. https://doi.org/10.3390/s20216047
Chicago/Turabian StyleSordi, Marcos A., Ohara K. Rayel, Guilherme L. Moritz, and João L. Rebelatto. 2020. "Towards Improving TSCH Energy Efficiency: An Analytical Approach to a Practical Implementation" Sensors 20, no. 21: 6047. https://doi.org/10.3390/s20216047
APA StyleSordi, M. A., K. Rayel, O., Moritz, G. L., & Rebelatto, J. L. (2020). Towards Improving TSCH Energy Efficiency: An Analytical Approach to a Practical Implementation. Sensors, 20(21), 6047. https://doi.org/10.3390/s20216047






