Rectification and Super-Resolution Enhancements for Forensic Text Recognition †
Abstract
:1. Introduction
2. Related Work
3. Methodology
3.1. State-of-the-Art Datasets
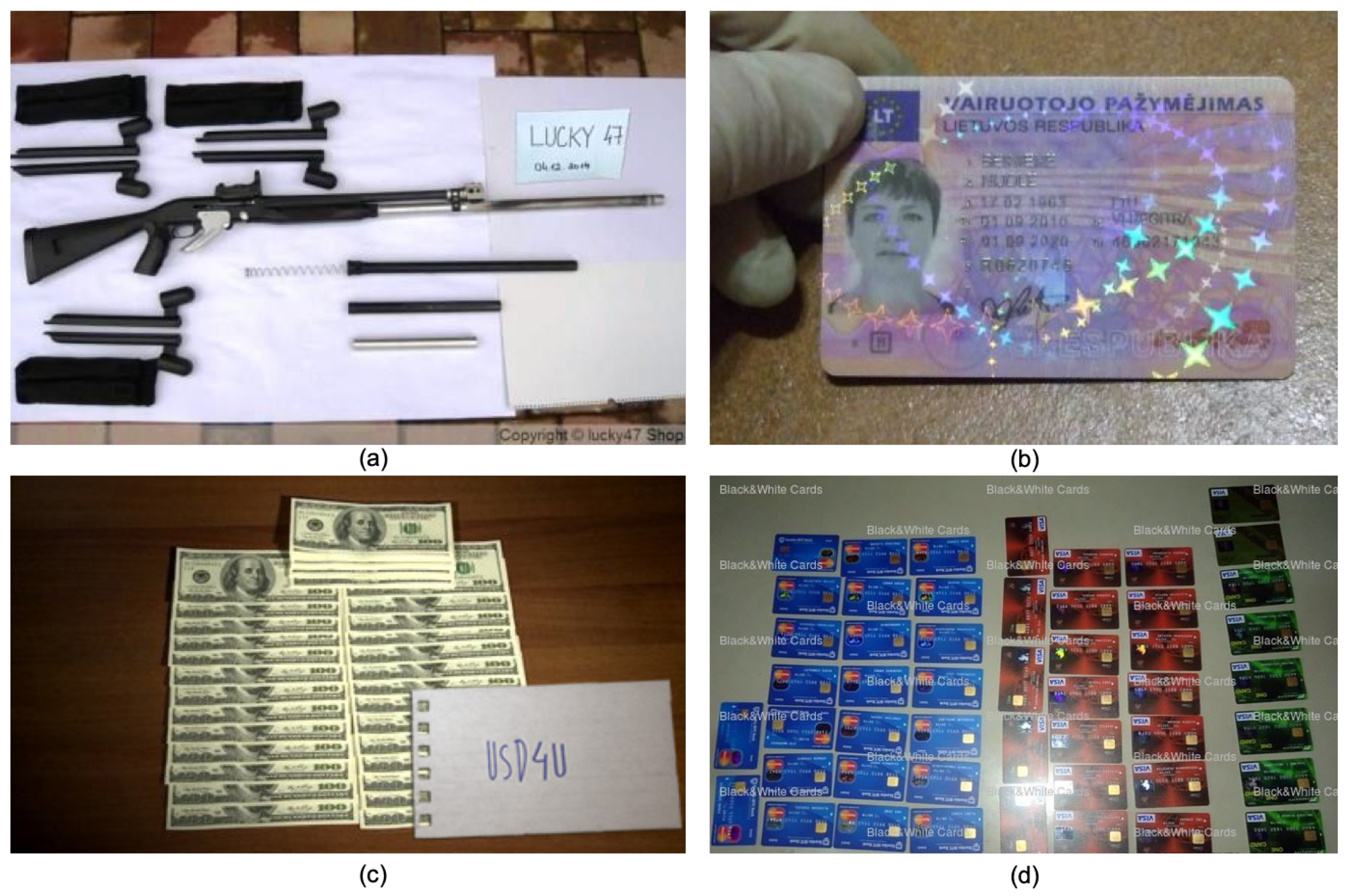
3.2. Toico-1k
3.3. Csa-Text Dataset
3.4. Recognition Methods
3.5. Super-Resolution Approaches
4. Experimental Results and Discussion
4.1. Experimental Setup
4.2. Results and Discussion
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Ye, Q.; Doermann, D. Text detection and recognition in imagery: A survey. Trans. Pattern Anal. Mach. Intell. 2014, 37, 1480–1500. [Google Scholar] [CrossRef] [PubMed]
- Zhu, Y.; Yao, C.; Bai, X. Scene text detection and recognition: Recent advances and future trends. Front. Comput. Sci. 2016, 10, 19–36. [Google Scholar] [CrossRef]
- Liu, X.; Meng, G.; Pan, C. Scene text detection and recognition with advances in deep learning: A survey. Int. J. Doc. Anal. Recognit. 2019, 22, 143–162. [Google Scholar] [CrossRef]
- Carriquiry, A.; Hofmann, H.; Tai, X.H.; VanderPlas, S. Machine learning in forensic applications. Significance 2019, 16, 29–35. [Google Scholar] [CrossRef] [Green Version]
- Rughani, P.H.; Bhatt, P. Machine learning forensics: A new branch of digital forensics. Int. J. Adv. Res. Comput. Sci. 2017, 8, 217–222. [Google Scholar]
- Anda, F.; Lillis, D.; Kanta, A.; Becker, B.A.; Bou-Harb, E.; Le-Khac, N.A.; Scanlon, M. Improving Borderline Adulthood Facial Age Estimation Through Ensemble Learning. In Proceedings of the 14th International Conference on Availability, Reliability and Security (ARES ’19), Canterbury, UK, 26–29 August 2019. [Google Scholar] [CrossRef] [Green Version]
- Nixon, M.; Aguado, A. Feature Extraction and Image Processing for Computer Vision; Academic Press: Cambridge, MA, USA, 2019. [Google Scholar]
- Gangwar, A.; Fidalgo, E.; Alegre, E.; González-Castro, V. Pornography and Child Sexual Abuse Detection in Image and Video: A Comparative Evaluation. In Proceedings of the 8th International Conference on Imaging for Crime Detection and Prevention (ICDP 2017), Madrid, Spain, 13–15 December 2017. [Google Scholar]
- Saikia, S.; Fidalgo, E.; Alegre, E.; Fernández-Robles, L. Object Detection for Crime Scene Evidence Analysis Using Deep Learning. In Proceedings of the Image Analysis and Processing(ICIAP 2017), Catania, Italy, 11–15 September 2017. [Google Scholar]
- Saikia, S.; Fidalgo, E.; Alegre, E.; Fernández-Robles, L. Query Based Object Retrieval Using Neural Codes. In Proceedings of the International Joint Conference SOCO’17-CISIS’17-ICEUTE’17, León, Spain, 6–8 September 2017. [Google Scholar]
- Nadeem, M.S.; Franqueira, V.N.; Zhai, X.; Kurugollu, F. A Survey of Deep Learning Solutions for Multimedia Visual Content Analysis. IEEE Access 2019, 7, 84003–84019. [Google Scholar] [CrossRef]
- Schroff, F.; Kalenichenko, D.; Philbin, J. Facenet: A unified embedding for face recognition and clustering. In Proceedings of the 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Boston, MA, USA, 7–12 June 2015; pp. 815–823. [Google Scholar]
- Singh, S.; Prasad, S. Techniques and Challenges of Face Recognition: A Critical Review. Procedia Comput. Sci. 2018, 143, 536–543. [Google Scholar] [CrossRef]
- Al-Nabki, M.W.; Fidalgo, E.; Alegre, E.; Fernández-Robles, L. ToRank: Identifying the most influential suspicious domains in the Tor network. Expert Syst. Appl. 2019, 123, 212–226. [Google Scholar] [CrossRef]
- He, S.; He, Y.; Li, M. Classification of illegal activities on the dark web. In Proceedings of the 2019 2nd International Conference on Information Science and Systems (ICISS 2019), Tokyo, Japan, 16–19 March 2019; pp. 73–78. [Google Scholar] [CrossRef]
- Joshi, A.; Fidalgo, E.; Alegre, E.; Fernández-Robles, L. SummCoder: An unsupervised framework for extractive text summarization based on deep auto-encoders. Expert Syst. Appl. 2019, 129, 200–215. [Google Scholar] [CrossRef]
- Wang, X.; Peng, P.; Wang, C.; Wang, G. You are your photographs: Detecting multiple identities of vendors in the darknet marketplaces. In Proceedings of the 2018 on Asia Conference on Computer and Communications Security (ASIACCS ’18), Incheon, Korea, 4–8 June 2018; pp. 431–442. [Google Scholar]
- Biswas, R.; Fidalgo, E.; Alegre, E. Recognition of service domains on TOR dark net using perceptual hashing and image classification techniques. In Proceedings of the 8th International Conference on Imaging for Crime Detection and Prevention (ICDP 2017), Madrid, Spain, 13–15 December 2017; pp. 7–12. [Google Scholar]
- Duxbury, S.W.; Haynie, D.L. The Network Structure of Opioid Distribution on a Darknet Cryptomarket. J. Quant. Criminol. 2018, 34, 921–941. [Google Scholar] [CrossRef]
- Wesam, M.; Nabki, A.; Fidalgo, E.; Alegre, E.; González-Castro, V. Detecting Emerging Products in TOR Network Based on K-Shell Graph Decomposition. In Proceedings of the Jornadas Nacionales de Investigación en Ciberseguridad (JNIC2017), Madrid, Spain, 31 May–2 June 2017; pp. 24–30. [Google Scholar]
- Yang, M.; Zhao, W.; Ye, J.; Lei, Z.; Zhao, Z.; Zhang, S. Investigating capsule networks with dynamic routing for text classification. In Proceedings of the 2018 Conference on Empirical Methods in Natural Language Processing, Brussels, Belgium, 31 October–4 November 2018; pp. 3110–3119. [Google Scholar]
- Blanco-Medina, P.; Fidalgo, E.; Alegre, E.; Al-Nabki, M.W. Detecting Textual Information in images from onion domains using Text Spotting. In Proceedings of the Actas de las XXXIX Jornadas de Automática, Badajoz, Spain, 5–7 September 2018; pp. 975–982. [Google Scholar]
- Blanco-Medina, P.; Fidalgo, E.; Alegre, E.; Al-Nabki, M.W.; Chaves, D. Enhancing text recognition on Tor Darknet images. In Proceedings of the XL Jornadas de Automática, Ferrol, Spain, 4–6 September 2019; pp. 828–835. [Google Scholar]
- Baek, J.; Kim, G.; Lee, J.; Park, S.; Han, D.; Yun, S.; Oh, S.J.; Lee, H. What is wrong with scene text recognition model comparisons? Dataset and model analysis. In Proceedings of the 2019 IEEE/CVF International Conference on Computer Vision (ICCV 2019), Seoul, Korea, 27 October–2 November 2019; pp. 4715–4723. [Google Scholar]
- Blanco-Medina, P.; Fidalgo, E.; Alegre, E.; Jánez-Martino, F. Improving Text Recognition in Tor darknet with Rectification and Super-Resolution techniques. In Proceedings of the 9th International Conference on Imaging for Crime Detection and Prevention (ICDP-2019), London, UK, 16–18 December 2019; pp. 32–37. [Google Scholar]
- Shi, B.; Yang, M.; Wang, X.; Lyu, P.; Yao, C.; Bai, X. Aster: An attentional scene text recognizer with flexible rectification. IEEE Trans. Pattern Anal. Mach. Intell. 2018, 41, 2035–2048. [Google Scholar] [CrossRef] [PubMed]
- Luo, C.; Jin, L.; Sun, Z. MORAN: A Multi-Object Rectified Attention Network for scene text recognition. Pattern Recognit. 2019, 90, 109–118. [Google Scholar] [CrossRef]
- Ma, Y.; Peng, H.; Cambria, E. Targeted Aspect-Based Sentiment Analysis via Embedding Commonsense Knowledge into an Attentive LSTM. In Proceedings of the Thirty-Second AAAI Conferenceon Artificial Intelligence (AAAI-18), New Orleans, LA, USA, 2–7 February 2018; pp. 5876–5883. [Google Scholar]
- Shi, B.; Bai, X.; Yao, C. An end-to-end trainable neural network for image-based sequence recognition and its application to scene text recognition. IEEE Trans. Pattern Anal. Mach. Intell. 2016, 39, 2298–2304. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Liu, X.; Liang, D.; Yan, S.; Chen, D.; Qiao, Y.; Yan, J. Fots: Fast oriented text spotting with a unified network. In Proceedings of the 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Salt Lake City, UT, USA, 18–23 June 2018; pp. 5676–5685. [Google Scholar]
- Cheng, Z.; Xu, Y.; Bai, F.; Niu, Y.; Pu, S.; Zhou, S. Aon: Towards arbitrarily-oriented text recognition. In Proceedings of the 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Salt Lake City, UT, USA, 18–23 June 2018; pp. 5571–5579. [Google Scholar]
- Peyrard, C.; Baccouche, M.; Mamalet, F.; Garcia, C. ICDAR2015 competition on text image super-resolution. In Proceedings of the 2015 13th International Conference on Document Analysis and Recognition (ICDAR), Tunis, Tunisia, 23–26 August 2015; pp. 1201–1205. [Google Scholar]
- Dong, C.; Loy, C.C.; He, K.; Tang, X. Learning a deep convolutional network for image super-resolution. In Proceedings of the 13th European conference on computer vision(ECCV 2014), Zurich, Switzerland, 6–12 September 2014; pp. 184–199. [Google Scholar]
- Yamanaka, J.; Kuwashima, S.; Kurita, T. Fast and accurate image super resolution by deep CNN with skip connection and network in network. In Proceedings of the 24th International Conference on Neural Information Processing, Guangzhou, China, 14–18 November 2017; pp. 217–225. [Google Scholar]
- Zhang, Y.; Tian, Y.; Kong, Y.; Zhong, B.; Fu, Y. Residual dense network for image super-resolution. In Proceedings of the 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition, Salt Lake City, UT, USA, 18–23 June 2018; pp. 2472–2481. [Google Scholar]
- Ledig, C.; Theis, L.; Huszár, F.; Caballero, J.; Cunningham, A.; Acosta, A.; Aitken, A.; Tejani, A.; Totz, J.; Wang, Z.; et al. Photo-realistic single image super-resolution using a generative adversarial network. In Proceedings of the 2017 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Honolulu, HI, USA, 21–26 July 2017; pp. 4681–4690. [Google Scholar]
- Wang, K.; Belongie, S. Word spotting in the wild. In Proceedings of the 11th European Conference on Computer Vision (ECCV 2010), Heraklion, Greece, 5–11 September 2010; pp. 591–604. [Google Scholar]
- Karatzas, D.; Gomez-Bigorda, L.; Nicolaou, A.; Ghosh, S.; Bagdanov, A.; Iwamura, M.; Matas, J.; Neumann, L.; Chandrasekhar, V.R.; Lu, S.; et al. ICDAR 2015 competition on robust reading. In Proceedings of the 2015 13th International Conference on Document Analysis and Recognition (ICDAR), Tunis, Tunisia, 23–26 August 2015; pp. 1156–1160. [Google Scholar]
- Karatzas, D.; Shafait, F.; Uchida, S.; Iwamura, M.; I Bigorda, L.G.; Mestre, S.R.; Mas, J.; Mota, D.F.; Almazan, J.A.; De Las Heras, L.P. ICDAR 2013 robust reading competition. In Proceedings of the 2013 12th International Conference on Document Analysis and Recognition, Washington, DC, USA, 25–28 August 2013; pp. 1484–1493. [Google Scholar]
- Mishra, A.; Alahari, K.; Jawahar, C. Scene text recognition using higher order language priors. In Proceedings of the BMVC-British Machine Vision Conference 2012, Surrey, UK, 3–7 September 2012. [Google Scholar]
- Fidalgo, E.; Alegre, E.; Fernández-Robles, L.; González-Castro, V. Classifying suspicious content in tor darknet through Semantic Attention Keypoint Filtering. Dig. Investig. 2019, 30, 12–22. [Google Scholar] [CrossRef]
- Bookstein, F.L. Principal warps: Thin-plate splines and the decomposition of deformations. IEEE Trans. Pattern Anal. Mach. Intell. 1989, 11, 567–585. [Google Scholar] [CrossRef] [Green Version]
- Very Deep Convolutional Networks for Large-Scale Image Recognition. Available online: https://arxiv.org/abs/1409.1556 (accessed on 27 July 2020).
- He, K.; Zhang, X.; Ren, S.; Sun, J. Deep residual learning for image recognition. In Proceedings of the 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar]
- Cohen, W.; Ravikumar, P.; Fienberg, S. A comparison of string metrics for matching names and records. In Proceedings of the Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–27 August 2003; pp. 73–78. [Google Scholar]





| Method | TOICO-1K | CSA-Text | SVT | IC15 | IC13 | IIIT5K |
|---|---|---|---|---|---|---|
| FOTS | 0.2074 | 0.3889 | 0.5255 | 0.2499 | 0.7292 | 0.5700 |
| MORAN | 0.2652 | 0.5355 | 0.8671 | 0.6771 | 0.8573 | 0.9243 |
| ASTER | 0.2830 | 0.6883 | 0.8825 | 0.7235 | 0.8829 | 0.8413 |
| None + ResNet + None + CTC | 0.2163 | 0.5448 | 0.8377 | 0.6283 | 0.8280 | 0.8397 |
| None + VGG + BiLSTM + CTC | 0.2089 | 0.5417 | 0.8207 | 0.6119 | 0.8289 | 0.8273 |
| None + VGG + None + CTC | 0.1319 | 0.3858 | 0.7558 | 0.5060 | 0.7749 | 0.7600 |
| TPS + ResNet + BiLSTM + ATTN | 0.2637 | 0.5417 | 0.8702 | 0.6984 | 0.8545 | 0.8740 |
| TPS + ResNet + BiLSTM + CTC | 0.2385 | 0.5448 | 0.8624 | 0.6733 | 0.8417 | 0.8618 |
| Method | TOICO-1K | CSA-Text | SVT | IC15 | IC13 | IIT5K | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ED | Std | ED | Std | ED | Std | ED | Std | ED | Std | ED | Std | |
| FOTS | 2859 | 5.039 | 957 | 1.635 | 846 | 2.109 | 5346 | 2.221 | 631 | 1.701 | 2918 | 1.709 |
| MORAN | 3197 | 5.367 | 1783 | 4.112 | 203 | 2.034 | 1716 | 2.026 | 277 | 1.200 | 515 | 2.816 |
| ASTER | 2914 | 5.496 | 2530 | 5.405 | 165 | 2.003 | 1522 | 1.971 | 248 | 1.356 | 774 | 1.821 |
| None + ResNet + None + CTC | 3173 | 5.595 | 1386 | 2.678 | 190 | 1.488 | 1752 | 1.731 | 310 | 1.212 | 836 | 1.725 |
| None + VGG + BiLSTM + CTC | 3608 | 6.590 | 1413 | 2.864 | 235 | 1.618 | 1934 | 1.827 | 314 | 1.229 | 978 | 2.083 |
| None + VGG + None + CTC | 3547 | 5.557 | 2059 | 4.446 | 330 | 1.598 | 2439 | 1.703 | 421 | 1.182 | 1376 | 1.851 |
| TPS + ResNet + BiLSTM + ATTN | 3219 | 5.832 | 1568 | 2.991 | 169 | 1.485 | 1579 | 2.051 | 283 | 1.578 | 757 | 2.529 |
| TPS + ResNet + BiLSTM + CTC | 3044 | 5.343 | 1553 | 2.975 | 158 | 1.396 | 1567 | 1.874 | 287 | 1.323 | 701 | 1.808 |
| Method | TOICO-1K | CSA-Text | SVT | IC15 | IC13 | IIIT5K |
|---|---|---|---|---|---|---|
| ASTER (Baseline) | 0.2830 | 0.6883 | 0.8825 | 0.7235 | 0.8829 | 0.8413 |
| ASTER (Baseline) + Rectification | 0.3052 | 0.6914 | 0.9042 | 0.7424 | 0.8984 | 0.8540 |
| RDN | 0.2993 | 0.6898 | 0.8934 | 0.7453 | 0.8957 | 0.8483 |
| RDN + Rectification | 0.3096 | 0.6898 | 0.9042 | 0.7612 | 0.9122 | 0.8557 |
| DCSCN | 0.3037 | 0.6898 | 0.8995 | 0.7414 | 0.8930 | 0.8470 |
| DCSCN + Rectification | 0.3170 | 0.6944 | 0.9104 | 0.7574 | 0.9076 | 0.8560 |
| NE Repair | 0.2933 | 0.6960 | 0.8964 | 0.7351 | 0.8939 | 0.8543 |
| NE Repair + Rectification | 0.3007 | 0.6960 | 0.9042 | 0.7487 | 0.9021 | 0.8620 |
| NE Deblur | 0.2933 | 0.6914 | 0.9011 | 0.7380 | 0.8911 | 0.8540 |
| NE Deblur + Rectification | 0.3007 | 0.6914 | 0.9057 | 0.7477 | 0.9039 | 0.8613 |
| NE Default ×2 | 0.2993 | 0.6898 | 0.8964 | 0.7453 | 0.8939 | 0.8477 |
| NE Default ×2 + Rectification | 0.3126 | 0.6914 | 0.9042 | 0.7598 | 0.9058 | 0.8580 |
| NE Default ×4 | 0.3022 | 0.6898 | 0.8949 | 0.7438 | 0.8893 | 0.8493 |
| NE Default ×4 + Rectification | 0.3096 | 0.6914 | 0.9042 | 0.7593 | 0.9039 | 0.8590 |
| Method | TOICO-1K | CSA-text | SVT | IC15 | IC13 | IIIT5K |
|---|---|---|---|---|---|---|
| MORAN (Baseline) | 0.2652 | 0.5355 | 0.867 | 0.6771 | 0.8573 | 0.9243 |
| MORAN (Baseline) + Rectification | 0.2919 | 0.5370 | 0.8733 | 0.7173 | 0.8774 | 0.9430 |
| RDN | 0.2785 | 0.5417 | 0.8717 | 0.7018 | 0.8664 | 0.9323 |
| RDN + Rectification | 0.2993 | 0.5417 | 0.8764 | 0.7255 | 0.8756 | 0.9450 |
| DCSCN | 0.2785 | 0.5417 | 0.8671 | 0.6936 | 0.8628 | 0.9297 |
| DCSCN + Rectification | 0.2993 | 0.5370 | 0.8764 | 0.7206 | 0.8792 | 0.9443 |
| NE Repair | 0.2711 | 0.5432 | 0.8733 | 0.6984 | 0.8646 | 0.9327 |
| NE Repair + Rectification | 0.2800 | 0.5432 | 0.8794 | 0.7158 | 0.8747 | 0.9430 |
| NE Deblur | 0.2726 | 0.5401 | 0.8748 | 0.6999 | 0.8673 | 0.9347 |
| NE Deblur + Rectification | 0.2800 | 0.5386 | 0.8810 | 0.7115 | 0.8728 | 0.9417 |
| NE Default ×2 | 0.2770 | 0.5448 | 0.8702 | 0.7013 | 0.8692 | 0.9343 |
| NE Default ×2 + Rectification | 0.2889 | 0.5432 | 0.8748 | 0.7255 | 0.8792 | 0.9447 |
| NE Default ×4 | 0.2830 | 0.5432 | 0.8794 | 0.6989 | 0.8701 | 0.9353 |
| NE Default ×4 + Rectification | 0.2933 | 0.5432 | 0.8733 | 0.7250 | 0.8756 | 0.9443 |
| Approach | TOICO-1K | CSA-Text | SVT | IC15 | IC13 | IIIT5K | Avg |
|---|---|---|---|---|---|---|---|
| Rectification | 2.22% | 0.31% | 2.16% | 1.88% | 1.56% | 1.27% | 1.57% |
| RDN | 1.63% | 0.15% | 1.08% | 2.17% | 1.28% | 0.70% | 1.17% |
| RDN + Rectification | 2.67% | 0.15% | 2.16% | 3.77% | 2.93% | 1.43% | 2.19% |
| DCSCN | 2.07% | 0.15% | 1.70% | 1.79% | 1.01% | 0.57% | 1.22% |
| DCSCN + Rectification | 3.41% | 0.62% | 2.78% | 3.38% | 2.47% | 1.47% | 2.36% |
| NE | 1.93% | 0.77% | 1.85% | 2.17% | 1.10% | 1.30% | 1.52% |
| NE + Rectification | 2.96% | 0.77% | 2.32% | 3.62% | 2.29% | 2.07% | 2.34% |
| Average Improvement | 2.45% | 0.44% | 1.98% | 2.82% | 1.85% | 1.26% | / |
| Approach | TOICO-1K | CSA-Text | SVT | IC15 | IC13 | IIIT5K | Avg |
|---|---|---|---|---|---|---|---|
| Rectification | 2.67% | 0.16% | 0.62% | 4.01% | 2.01% | 1.87% | 1.89% |
| RDN | 1.33% | 0.62% | 0.46% | 2.46% | 0.91% | 0.80% | 1.10% |
| RDN + Rectification | 3.41% | 0.62% | 0.93% | 4.83% | 1.83% | 2.07% | 2.28% |
| DCSCN | 1.33% | 0.62% | 0.00% | 1.64% | 0.55% | 0.53% | 0.78% |
| DCSCN + Rectification | 3.41% | 0.15% | 0.93% | 4.35% | 2.20% | 2.00% | 2.17% |
| NE | 1.78% | 0.93% | 0.77% | 2.42% | 1.28% | 1.10% | 1.38% |
| NE + Rectification | 2.81% | 0.77% | 1.39% | 4.83% | 2.20% | 2.03% | 2.34% |
| Average Improvement | 2.35% | 0.62% | 0.75% | 3.42% | 1.50% | 1.42% | / |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Blanco-Medina, P.; Fidalgo, E.; Alegre, E.; Alaiz-Rodríguez, R.; Jáñez-Martino, F.; Bonnici, A. Rectification and Super-Resolution Enhancements for Forensic Text Recognition. Sensors 2020, 20, 5850. https://doi.org/10.3390/s20205850
Blanco-Medina P, Fidalgo E, Alegre E, Alaiz-Rodríguez R, Jáñez-Martino F, Bonnici A. Rectification and Super-Resolution Enhancements for Forensic Text Recognition. Sensors. 2020; 20(20):5850. https://doi.org/10.3390/s20205850
Chicago/Turabian StyleBlanco-Medina, Pablo, Eduardo Fidalgo, Enrique Alegre, Rocío Alaiz-Rodríguez, Francisco Jáñez-Martino, and Alexandra Bonnici. 2020. "Rectification and Super-Resolution Enhancements for Forensic Text Recognition" Sensors 20, no. 20: 5850. https://doi.org/10.3390/s20205850






