A Survey on the Security of Low Power Wide Area Networks: Threats, Challenges, and Potential Solutions
Abstract
:1. Introduction
- We present a comprehensive review of the security and privacy issues and attacks that affect LPWAN. The attacks are categorized under the prominent information security requirements known as Confidentiality, Integrity, and Availability (CIA triad);
- a detailed analysis of the different techniques and security solutions that have been proposed in the literature for securing LPWAN are extensively discussed. The analysis entails a comparison of the mitigation methodologies, the types of attacks mitigated, the security requirements and limitations; and
- challenges and research gap in existing LPWAN security methods and the direction for future works are broadly analyzed.
2. Related Survey Papers
3. Overview of LPWAN
3.1. Low Power Consumption
3.2. Wide or Extended Coverage
3.3. Scalability
3.4. Security and Privacy
4. LPWAN Technologies
4.1. LoRa
4.2. Sigfox
4.3. Weightless
4.4. Ingenu RPMA
4.5. Narrowband Internet of Things
5. LPWAN Security Analysis
5.1. Confidentiality
5.2. Integrity
5.3. Availability
6. Comparison and Discussion
7. Research Challenges and Recommendations for Future Works
7.1. Key Management and Storage
7.2. Encryption Factors
7.3. Bootstrapping and Authentication Issue
7.4. Jamming
7.5. Compromised IoT Device and Open Environment
7.6. Untrusted Gateways
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| AppSkey | Application Key |
| BPSK | Binary Phase-Shift Keying |
| CDMA | Code Division Multiple access |
| CKA | Compromised Key Attack |
| CSS | Chirp-spread-spectrum |
| DBPSK | Differential Binary Phase Shift Keying |
| DL | Downlink |
| DoS | Denial of Service |
| DSSS | Direct Sequence Spread Spectrum |
| EDHOC | Ephemeral Diffie-Hellman Over COSE |
| EEPROM | Erasable Programmable ROM |
| FEC | Forward Error Correction |
| FHMA | Frequency Hop Multiple Access |
| FSK | Frequency-shift keying |
| GFSK | Gaussian Frequency-Shift Keying |
| GMSK | Gaussian Minimum Shift Keying |
| HD | Hamming Distance |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| ICMP | Internet Control Protocol |
| ICT | Information Communication and Technology |
| ISM | Industrial Scientific and Medical |
| Kbps | Kilobits Per Second |
| KDF | Key Derivation Function |
| KLD | Kullback Leibler Divergence |
| LoRa | Long-Range |
| LoRaWAN | Long Range Wide Area Network |
| LoS | Line of Sight |
| LPWAN | Low Power Wide Area Network |
| MITM | Man-in-the-middle |
| M2M | Machine-to-Machine |
| NB-IoT | Narrow Band-Internet of Thing |
| NwkSkey | Network Key |
| OFDMA | Orthogonal Frequency Division Multiple Access |
| OTA | Over-The-Air |
| PKI | Public Key Infrastructure |
| QPSK | Quadrature Phase Shift Keying |
| RPMA | Random Phase Multiple Access |
| RSA | Rivest–Shamir–Adleman |
| R-FDMA | Random Frequency Division Multiple Access |
| SE | Secure Elements |
| SeLPC | Secure Low Power Communication |
| TDD | Time Division Duplex |
| UL | Uplink |
| UNB | Ultra-Narrowband |
References
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Future Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Jose, D.V.; Vijyalakshmi, A. An overview of security in Internet of Things. Procedia Comput. Sci. 2018, 143, 744–748. [Google Scholar] [CrossRef]
- Grammatikis, P.I.; Sarigiannidis, P.; Moscholios, I.D. Securing the Internet of Things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar] [CrossRef]
- Zeadally, S.; Das, A.K.; Klavos, N. Cryptographic technologies and protocol standards for Internet of Things. Internet Things 2019, 100075. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.; Du, X.; Guizani, M. A survey of machine and deep learning methods for Internet of Things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef] [Green Version]
- Tsague, H.D.; Twala, B. Practical techniques for securing the Internet of Things (IoT) against side channel attacks. In Internet of Things and Big Data Analytics toward Next-Generation Intelligence 2018; Springer: Cham, Switzerland, 2018; pp. 439–481. [Google Scholar]
- Garrity, J. Harnessing the Internet of Things for Global Development. Available at SSRN 2588129. 2015. Available online: https://www.itu.int/en/action/broadband/Documents/Harnessing-IoT-Global-Development.pdf (accessed on 16 July 2019).
- Evans, D. The Internet of Things: How the next evolution of the Internet is changing everything. CISCO White Pap. 2011, 1, 1–11. [Google Scholar]
- Ray, S.; Jin, Y.; Raychowdhury, A. The changing computing paradigm with Internet of Things: A tutorial introduction. IEEE Des. Test 2016, 33, 76–96. [Google Scholar] [CrossRef]
- Qadir, Q.M.; Rashid, T.A.; Al-Salihi, N.K.; Ismael, B.; Kist, A.A.; Zhang, Z. Low power wide area networks: A survey of enabling technologies, applications and interoperability needs. IEEE Access 2018, 6, 77454–77473. [Google Scholar] [CrossRef]
- Al-Kashoash, H.A.; Kemp, A.H. Comparison of 6LoWPAN and LPWAN for the Internet of Things. Aust. J. Electr. Electr. Eng. 2016, 13, 268–274. [Google Scholar] [CrossRef]
- Kabalcı, Y.; Ali, M. Emerging LPWAN Technologies for Smart Environments: An Outlook. In Proceedings of the 1st Global Power, Energy and Communication Conference (GPECOM), Nevsehir, Turkey, 12 June 2019; pp. 24–29. [Google Scholar]
- Chaudhari, B.; Borkar, S. Design considerations and network architectures for low-power wide-area networks. In LPWAN Technologies for IoT and M2M Applications; Academic Press: Oxford, UK, 2020; pp. 15–35. [Google Scholar]
- Kumar, S.A.; Vealey, T.; Srivastava, H. Security in Internet of Things: Challenges, solutions and future directions. In Proceedings of the 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5 January 2016; pp. 5772–5781. [Google Scholar]
- Chacko, S.; Job, M.D. Security mechanisms and Vulnerabilities in LPWAN. IOP Conf. Ser. Mater. Sci. Eng. 2018, 396, 012027. [Google Scholar] [CrossRef]
- Butun, I.; Pereira, N.; Gidlund, M. Security risk analysis of LoRaWAN and future directions. Future Internet 2019, 1, 3. [Google Scholar] [CrossRef] [Green Version]
- Kail, E.; Banati, A.; Lászlo, E.; Kozlovszky, M. Security Survey of Dedicated IoT Networks in the Unlicensed ISM Bands. In Proceedings of the IEEE 12th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 17 May 2018; pp. 000449–000454. [Google Scholar]
- Yang, X.; Karampatzakis, E.; Doerr, C.; Kuipers, F. Security Vulnerabilities in LoRaWAN. In Proceedings of the IEEE/ACM Third International Conference on Internet-of-Things Design and Implementation (IoTDI), Orlando, FL, USA, 17 April 2018; pp. 129–140. [Google Scholar]
- Danish, S.M.; Nasir, A.; Qureshi, H.K.; Ashfaq, A.B.; Mumtaz, S.; Rodriguez, J. Network intrusion detection system for jamming attack in lorawan join procedure. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20 May 2018; pp. 1–6. [Google Scholar]
- Chatzigiannakis, I.; Liagkou, V.; Spirakis, P.G. Brief announcement: Providing end-to-end secure communication in low-power wide area networks. In Proceedings of the International Symposium on Cyber Security Cryptography and Machine Learning, Be’er Sheva, Israel, 21 June 2018; pp. 101–104. [Google Scholar]
- Kim, J.; Song, J. A simple and efficient replay attack prevention scheme for LoRaWAN. In Proceedings of the 7th International Conference on Communication and Network Security, Tokyo, Japan, 24 November 2017; pp. 32–36. [Google Scholar]
- Tsai, K.L.; Huang, Y.L.; Leu, F.Y.; You, I.; Huang, Y.L.; Tsai, C.H. AES-128 based secure low power communication for LoRaWAN IoT environments. IEEE Access 2018, 6, 45325–45334. [Google Scholar] [CrossRef]
- Miller, R. MWR Labs Whitepaper, LoRa Security Building a Secure LoRa Solution. Available online: https://labs.f-secure.com/assets/BlogFiles/mwri-LoRa-security-guide-1.2-2016-03-22.pdf (accessed on 2 April 2019).
- Haxhibeqiri, J.; De Poorter, E.; Moerman, I.; Hoebeke, J. A survey of lorawan for iot: From technology to application. Sensors 2018, 11, 3995. [Google Scholar] [CrossRef] [Green Version]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of Things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef] [Green Version]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Kaur, B.; Pateriya, P.K. A Survey on Security Concerns in Internet of Things. In Proceedings of the 2018 Second International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 14 June 2018; pp. 27–34. [Google Scholar]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Gulzar, M.; Abbas, G. Internet of Things Security: A Survey and Taxonomy. In Proceedings of the 2019 International Conference on Engineering and Emerging Technologies (ICEET), Lahore, Pakistan, 21 February 2019; pp. 1–6. [Google Scholar]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.S. IoT elements, layered architectures and security issues: A comprehensive survey. Sensors 2018, 9, 2796. [Google Scholar] [CrossRef] [Green Version]
- Centenaro, M.; Vangelista, L.; Zanella, A.; Zorzi, M. Long-range communications in unlicensed bands: The rising stars in the IoT and smart city scenarios. IEEE Wirel. Commun. 2016, 23, 60–67. [Google Scholar] [CrossRef] [Green Version]
- Vangelista, L.; Zanella, A.; Zorzi, M. Long-range IoT technologies: The dawn of LoRa™. In Future Access Enablers of Ubiquitous and Intelligent Infrastructures; Springer: Cham, Switzerland; Ohrid, Republic of Macedonia, 2015; pp. 51–58. [Google Scholar]
- Mikhaylov, K.; Petaejaejaervi, J.; Haenninen, T. Analysis of capacity and scalability of the LoRa low power wide area network technology. In Proceedings of the 22nd European Wireless Conference, Oulu, Finland, 18 May 2016; pp. 1–6. [Google Scholar]
- Farrell, S. LPWAN Overview: Draft-ietf-lpwan-overview-01. Available online: https://tools.ietf.org/html/draft-ietf-lpwan-overview-01 (accessed on 2 April 2019).
- Patel, D.; Won, M. Experimental study on low power wide area networks (LPWAN) for mobile Internet of Things. In Proceedings of the IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 4 June 2017; pp. 1–5. [Google Scholar]
- Mekki, K.; Bajic, E.; Chaxel, F.; Meyer, F. A comparative study of LPWAN technologies for large-scale IoT deployment. ICT Express 2019, 5, 1–7. [Google Scholar] [CrossRef]
- Petäjäjärvi, J.; Mikhaylov, K.; Hämäläinen, M.; Iinatti, J. Evaluation of LoRa LPWAN technology for remote health and wellbeing monitoring. In Proceedings of the 10th International Symposium on Medical Information and Communication Technology (ISMICT), Worchester, MA, USA, 20 March 2016; pp. 1–5. [Google Scholar]
- Pasolini, G.; Buratti, C.; Feltrin, L.; Zabini, F.; De Castro, C.; Verdone, R.; Andrisano, O. Smart city pilot projects using LoRa and IEEE802. 15.4 technologies. Sensors 2018, 18, 1118. [Google Scholar] [CrossRef] [Green Version]
- Mudumbe, M.J.; Abu-Mahfouz, A.M. Smart water meter system for user-centric consumption measurement. In Proceedings of the IEEE 13th International Conference on Industrial Informatics (INDIN), Cambridgeshire, UK, 22 July 2015; pp. 993–998. [Google Scholar]
- Yaqoob, I.; Hashem, I.A.T.; Ahmed, A.; Kazmi, S.A.; Hong, C.S. Internet of Things forensics: Recent advances, taxonomy, requirements, and open challenges. Future Gener. Comput. Syst. 2019, 92, 265–275. [Google Scholar] [CrossRef]
- Mosenia, A.; Jha, N.K. A comprehensive study of security of Internet-of-things. IEEE Trans. Emerg. Top. Comput. 2017, 4, 586–602. [Google Scholar] [CrossRef]
- Yasmin, R.; Petäjäjärvi, J.; Mikhaylov, K.; Pouttu, A. On the integration of LoRaWAN with the 5G test network. In Proceedings of the IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8 October 2017; pp. 1–6. [Google Scholar]
- Raza, U.; Kulkarni, P.; Sooriyabandara, M. Low power wide area networks: An overview. IEEE Commun. Surv. Tutor. 2017, 19, 855–873. [Google Scholar] [CrossRef] [Green Version]
- Ram, P. LPWAN LoRa LoRaWAN and the Internet of Things. Coinmonks 2019. Available online: https://medium.com/coinmonks/lpwan-lora-lorawan-and-the-internet-of-things-aed7d5975d5d (accessed on 2 March 2020).
- Liao, C.H.; Zhu, G.; Kuwabara, D.; Suzuki, M.; Morikawa, H. Multi-hop LoRa networks enabled by concurrent transmission. IEEE Access 2017, 5, 21430–21446. [Google Scholar] [CrossRef]
- Akpakwu, G.A.; Silva, B.J.; Hancke, G.P.; Abu-Mahfouz, A.M. A survey on 5G networks for the Internet of Things: Communication technologies and challenges. IEEE Access 2017, 6, 3619–3647. [Google Scholar] [CrossRef]
- SIGFOX. Available online: https://www.sigfox.com/en (accessed on 12 August 2019).
- Di Gennaro, P.; Lofú, D.; Vitanio, D.; Tedeschi, P.; Boccadoro, P. WaterS: A Sigfox–compliant prototype for water monitoring. Internet Technol. Lett. 2019, 2, e74. [Google Scholar] [CrossRef] [Green Version]
- Lavric, A.; Petrariu, A.I.; Popa, V. Long range sigfox communication protocol scalability analysis under large-scale, high-density conditions. IEEE Access 2019, 7, 35816–35825. [Google Scholar] [CrossRef]
- WEIGHTLESS. Available online: http://www.weightless.org/about/weightless-specification (accessed on 12 August 2019).
- Singh, R.K.; Singh, R. 4G LTE cellular technology: Network architecture and mobile standards. Int. J. Emerg. Res. Manag. Technol. 2016, 5, 212482531. [Google Scholar]
- Kumar, V.; Jha, R.K.; Jain, S. NB-IoT Security: A Survey. Wirel. Pers. Commun. 2020, 1–48. [Google Scholar] [CrossRef]
- Ismail, D.; Rahman, M.; Saifullah, A. Low-power wide-area networks: Opportunities, challenges, and directions. In Proceedings of the Workshop Program of the 19th International Conference on Distributed Computing and Networking, Varanasi, India, 4 January 2018; p. 8. [Google Scholar]
- Sonar, K.; Upadhyay, H. A survey: DDOS attack on Internet of Things. Int. J. Eng. Res. Dev. 2014, 10, 58–63. [Google Scholar]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K. Security Assessment of the Smart Grid: A Review focusing on the NAN Architecture. In Proceedings of the IEEE 7th International Conference on Adaptive Science & Technology (ICAST), Accra, Ghana, 22 August 2018; pp. 1–8. [Google Scholar]
- Rehman, S.U.; Gruhn, V. An effective security requirement engineering framework for cyber-physical systems. Technologies 2018, 6, 65. [Google Scholar] [CrossRef] [Green Version]
- Antipolis, S.; Girard, P. Low Power Wide Area Networks Security. In White Paper; Gemalto Inc.: Amsterdam, The Netherlands, 2015. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Enhancing the security of the IoT LoraWAN architecture. In Proceedings of the International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 22 November 2016; pp. 1–7. [Google Scholar]
- Sanchez-Iborra, R.; Sánchez-Gómez, J.; Pérez, S.; Fernández, P.J.; Santa, J.; Hernández-Ramos, J.L.; Skarmeta, A.F. Enhancing lorawan security through a lightweight and authenticated key management approach. Sensors 2018, 18, 1833. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Han, J.; Wang, J. An enhanced key management scheme for LoRaWAN. Cryptography 2018, 2, 34. [Google Scholar] [CrossRef] [Green Version]
- Kumar, G.; Kaur, A.; Sethi, S. Computer network attacks-a study. Int. J. Comput. Sci. Mob. Appl. 2014, 2, 24–32. [Google Scholar]
- Baker, A.; River, W. A Survey of Information Security Implementations for the Internet of Things; Technical Report 2017; Wind River Systems: Alameda, CA, USA, 2017. [Google Scholar]
- Rughoobur, P.; Nagowah, L. A lightweight replay attack detection framework for battery depended IoT devices designed for healthcare. In Proceedings of the International Conference on Infocom Technologies and Unmanned Systems (Trends and Future Directions) (ICTUS), Dubai, UAE, 18 December 2017; pp. 811–817. [Google Scholar]
- Meghdadi, M.; Ozdemir, S.; Güler, I. A survey of wormhole-based attacks and their countermeasures in wireless sensor networks. IETE Tech. Rev. 2011, 28, 89–102. [Google Scholar] [CrossRef]
- Aras, E.; Small, N.; Ramachandran, G.S.; Delbruel, S.; Joosen, W.; Hughes, D. Selective jamming of LoRaWAN using commodity hardware. In Proceedings of the 14th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Melbourne, Australia, 7 November 2017; pp. 363–372. [Google Scholar]
- Rajan, A.; Jithish, J.; Sankaran, S. Sybil attack in IOT: Modelling and defenses. In Proceedings of the International Conference on Advances in Computing, Communications and Informatics (ICACCI), Karnataka, India, 13 September 2017; pp. 2323–2327. [Google Scholar]
- Coman, F.L.; Malarski, K.M.; Petersen, M.N.; Ruepp, S. Security issues in Internet of Things: Vulnerability analysis of LoRaWAN, sigfox and NB-IoT. In Proceedings of the Global IoT Summit (GIoTS), Aarhus, Denmark, 17 June 2019; pp. 1–6. [Google Scholar]
- You, I.; Kwon, S.; Choudhary, G.; Sharma, V.; Seo, J.T. An enhanced LoRaWAN security protocol for privacy preservation in IoT with a case study on a smart factory-enabled parking system. Sensors 2018, 18, 1888. [Google Scholar] [CrossRef] [Green Version]
- Na, S.; Hwang, D.; Shin, W.; Kim, K.H. Scenario and countermeasure for replay attack using join request messages in LoRaWAN. In Proceedings of the International Conference on Information Networking (ICOIN), Da-Nang, Vietnam, 11 January 2017; pp. 718–720. [Google Scholar]
- Avoine, G.; Ferreira, L. Rescuing LoRaWAN 1.0. In Proceedings of the International Conference on Financial Cryptography and Data Security, Nieuwpoort, Curaçao, 26 February–2 March 2018; pp. 253–271. [Google Scholar]
- Zulian, S. Security Threat Analysis and Countermeasures for Lorawan Join Procedure. 2016. Available online: http://tesi.cab.unipd.it/53210/1/zulian_simone_tesi.pdf (accessed on 4 October 2019).
- Lee, J.; Hwang, D.; Park, J.; Kim, K.H. Risk analysis and countermeasure for bit-flipping attack in LoRaWAN. In Proceedings of the International conference on information networking (ICOIN), Da-Nang, Vietnam, 11 January 2017; pp. 549–551. [Google Scholar]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network intrusion detection for IoT security based on learning techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Fraga, D.; Bankovic, Z.; Moya, J.M. A taxonomy of trust and reputation system attacks. In Proceedings of the IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25 June 2012; pp. 41–50. [Google Scholar]
- Kozushko, H. Intrusion Detection: Host-Based and Network-Based Intrusion Detection Systems. Indep. Study 2003. Available online: https://www.semanticscholar.org/paper/Intrusion-Detection-%3A-Host-Based-and-Network-Based-Kozushko/471b6047150e82d5b94cbcf1fed36586dcf929c1?p2df (accessed on 15 September 2020).
- Elrawy, M.F.; Awad, A.I.; Hamed, H.F. Intrusion detection systems for IoT-based smart environments: A survey. J. Cloud Comput. 2018, 7, 21. [Google Scholar] [CrossRef] [Green Version]
- Singh, A.P.; Singh, M.D. Analysis of host-based and network-based intrusion detection system. IJ Comput. Netw. Inf. Secur. 2014, 8, 41–47. [Google Scholar]
- Host- vs. Network-Based Intrusion Detection Systems. Available online: https://cyber-defense.sans.org/resources/papers/gsec/host-vs-network-based-intrusion-detection-systems-102574 (accessed on 30 July 2020).
- Das, N.; Sarkar, T. Survey on host and network-based intrusion detection system. Int. J. Adv. Netw. Appl. 2014, 6, 2266. [Google Scholar]
- Verma, A.; Ranga, V. ELNIDS: Ensemble learning based network intrusion detection system for RPL based Internet of Things. In Proceedings of the 4th International conference on Internet of Things: Smart innovation and usages (IoT-SIU), Ghaziabad, India, 18 April 2019; pp. 1–6. [Google Scholar]
- Thamilarasu, G.; Chawla, S. Towards deep-learning-driven intrusion detection for the Internet of Things. Sensors 2019, 19, 1977. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Roopak, M.; Tian, G.Y.; Chambers, J. An Intrusion Detection System against DDoS Attacks in IoT Networks. In Proceedings of the 10th Annual Computing and Communication Workshop and Conference (CCWC), Las-Vegas, NV, USA, 6 January 2020; pp. 0562–0567. [Google Scholar]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. Threat analysis of IoT networks using artificial neural network intrusion detection system. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC), Hammamet, Tunisia, 11 May 2016; pp. 1–6. [Google Scholar]
- Dönmez, T.C.; Nigussie, E. Security of LoRaWAN v1. 1 in Backward Compatibility Scenarios. Procedia Comput. Sci. 2018, 134, 51–58. [Google Scholar] [CrossRef]
- Islam, M.R.; Aktheruzzaman, K.M. An Analysis of Cybersecurity Attacks against Internet of Things and Security Solutions. J. Comput. Commun. 2020, 8, 11–25. [Google Scholar] [CrossRef] [Green Version]
- Andrea, I.; Chrysostomou, C.; Hadjichristofi, G. Internet of Things: Security Vulnerabilities and Challenges. In Proceedings of the IEEE Symposium on Computers and Communication (ISCC), Larnaca, Cyprus, 6–9 July 2015; pp. 180–187. [Google Scholar]
- Jeon, Y.; Ju, H.I.; Yoon, S. Design of an LPWAN communication module based on secure element for smart parking application. In Proceedings of the IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 12–14 January 2018; pp. 1–2. [Google Scholar]
- Urien, P. Towards secure elements for the Internet of Things: The eLock use case: Work in progress. In Proceedings of the Second International Conference on Mobile and Secure Services (MobiSecServ), Gainesville, FL, USA, 26 February 2016; pp. 1–5. [Google Scholar]
- Navarro-Ortiz, J.; Chinchilla-Romero, N.; Ramos-Munoz, J.J.; Munoz-Luengo, P. Improving Hardware Security for LoRaWAN. In Proceedings of the IEEE Conference on Standards for Communications and Networking (CSCN), Granada, Spain, 28 October 2019; pp. 1–6. [Google Scholar]
- Jeon, Y.; Kang, Y. Implementation of a LoRaWAN protocol processing module on an embedded device using Secure Element. In Proceedings of the 34th International Technical Conference on Circuits/Systems, Computers and Communications (ITC-CSCC), Jeju Shinhwa World, Korea, 23 June 2019; pp. 1–3. [Google Scholar]
- Durand, A.; Gremaud, P.; Pasquier, J.; Gerber, U. Trusted Lightweight Communication for IoT Systems Using Hardware Security. In Proceedings of the 9th International Conference on the Internet of Things, Bilbao, Spain, 22 October 2019; pp. 1–4. [Google Scholar]
- Schläpfer, T.; Rüst, A. Security on IoT devices with secure elements. In Proceedings of the Embedded World Conference, Nuremberg, Germany, 26–28 February 2019. [Google Scholar]
- Liagkou, V.; Stylios, C.; Salmas, D. VR training model for exploiting security in LPWAN. Procedia Cirp 2019, 79, 724–729. [Google Scholar] [CrossRef]
- Sanchez-Gomez, J.; Garcia-Carrillo, D.; Marin-Perez, R.; Skarmeta, A.F. Secure Authentication and Credential Establishment in Narrowband IoT and 5G. Sensors 2020, 3, 882. [Google Scholar] [CrossRef] [Green Version]
- Oniga, B.; Dadarlat, V.; De Poorter, E.; Munteanu, A. Analysis, design and implementation of secure LoRaWAN sensor networks. In Proceedings of the 13th IEEE International Conference on Intelligent Computer Communication and Processing (ICCP), Cluj-Napoca, Romania, 7 September 2017; pp. 421–428. [Google Scholar]
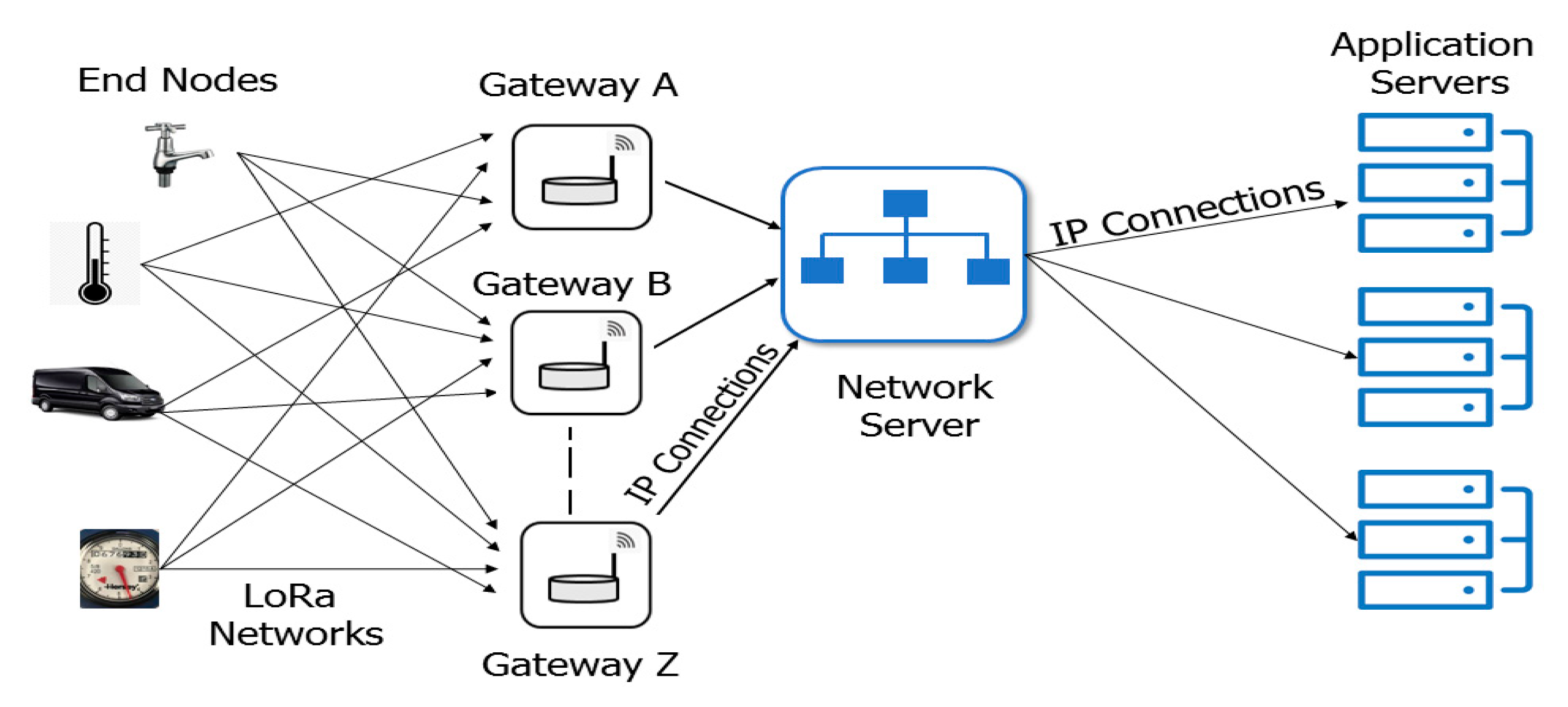
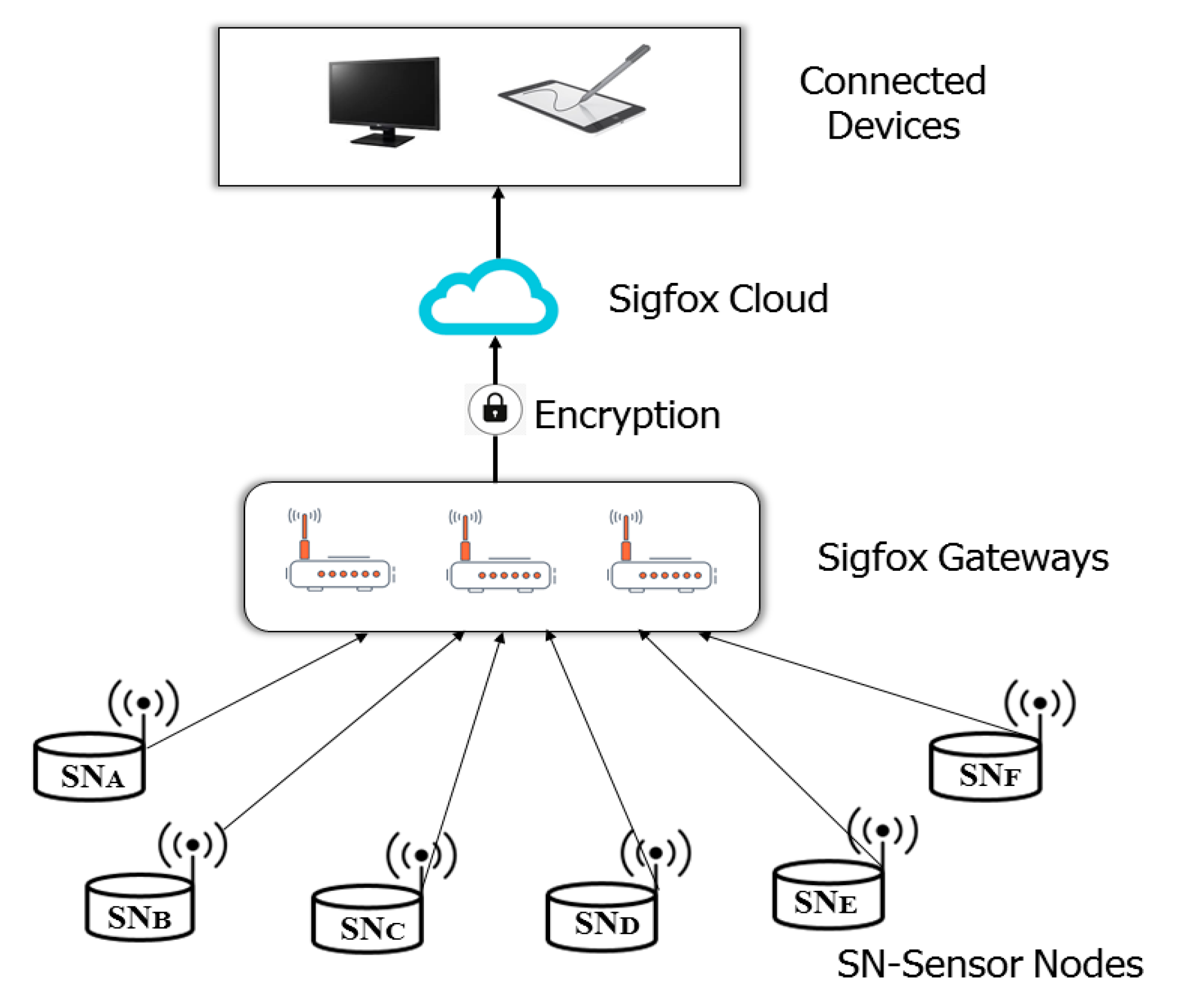
| LPWAN Type | Modulation | Freq. Band | Security/Encryption | Occupied Bandwidth | MAC | Range | Max Data Rate |
|---|---|---|---|---|---|---|---|
| LoRa | CSS/FSK | Sub-GHz ISM: Europe (868 MHz, 433 MHz) USA (915 MHz) | AES 128 bit | 250 kHz, 500 kHz and 125 kHz | ALOHA | Urban-Rural 5–20 km | 50 kbps |
| Sigfox | UNB (DBPSK and GFSK) | Sub-GHz ISM: Europe (868 MHz) USA (902 MHz) | AES + no key OTA emission | UL (100–600 Hz) DL (1.5 kHz) | ALOHA R-FDMA | Urban-Rural 10–50 km | UL (100 bps) DL (600 bps) |
| NB-IoT | QPSK | LTE frequency Bands | 2048-Bit RSA | 200 kHz | OFDMA | 15 km | UL (158.5 kbps) DL (106 kbps) |
| DASH7 | GFSK | 915, 433 and 868 MHz | AES 128 | 25 and 200 kHz | 0–5 km. | 167 kbps | |
| Ingenu-RPMA | DSSS | 2.4 GHz ISM | AES 128, 16B Hash | 1 MHz | CDMA | Urban15 km, 500 km LoS | UL (624 kbps) DL (156 kbps) |
| Weightless | 16QAM, offset-BPSK, QPSK, GMSK and DBPSK | Numerous Bands (sub-GHz) | AES 128/256 Bit | 200 Hz - 12.5 kHz | FHMA with TDD | Up to 5 km | 100 kbps |
| Refs. | Security Threat(s) Addressed | Security Requirements | Brief Summary of Approach, Highlight Strength and Limitation |
|---|---|---|---|
| [62] | Problem of key updates | Confidentiality | Proposed the use of a root key update scheme for reinforcing the session key derivation security. Strength: Requires fewer computing resources. Offers suitable randomness of the generated updated key. |
| [20] | Replay attack | Integrity | For the blockage of repeated transmission of packets, a frame counter which involves two different 128-bit AES keys: AppSKey and NwkSKey for upstream and downstream messages exchange was proposed. |
| [59] | Key management security flaws | Confidentiality | A trusted third-party PKI (scheme) was proposed. Strength: Strong key management and distribution. Limitation: High computation involved due to the involvement of a third party. Complex join produce. |
| [60] | Key management issue | Confidentiality | Several AES-128 encryption keys at the network layer and application layer was used for data authentication and privacy respectively. |
| [61] | Compromised key | Confidentiality | Ephemeral Diffie–Hellman Over COSE (EDHOC) approach that uses a cryptographic material derived at the application layer for updating LoRaWAN session keys is proposed. Strength: Low computational cost and flexibility in session keys updates. |
| [21] | Problem of key updates | Confidentiality | Proposed a dual key-based activation scheme for LoRaWAN security solution. NwkSKey and AppSKey was used in performing initial join procedure and the session key created in the initial join procedure is used for second join procedure. Strength: No third party involved. Secured connectivity between end devices and application server. Limitation: Perfect forward secrecy is not guaranteed. |
| [74] | Bit flipping attack | Integrity | Proposed a shuffling method to prevent bit flipping attack. Strength: Prevent attackers from identifying positions of message field from bit-flipping attacks. Limitation: Not suitable for devices with low power and low resources. |
| [70] | Replay attack | Integrity | Proposed a security protocol that comprises of a dual option (default option and security enhanced option) for preventing intruders from breaking the end-to-end security between a device and the application server. Strength: Supports mutual authentication, secret key exchange, perfect forward secrecy and end-to-end security. |
| [22] | Replay attack | Integrity | Proposed an AES-128 based Secure Low Power Communication (SeLPC) method to boost the security level of LoRaWAN communication. Strength: Efficient power consumption. |
| [71] | Replay attack | Integrity | Used sniffed join request messages to prevent replay attack. Strength: Fully support secure key exchange. Limitation: The approach does not support the perfect forward secrecy nor end-to-end security. |
| [72] | Replay and Decrypt attack | Integrity | Proposed the increment in the size of DevNonce and AppNonce value with no repetition. |
| [73] | Replay attack | Integrity | Network server store all DevNonces used in the previous join procedure in order to prevent the attack. |
| [19] | Jamming attack | Availability | IDS that is based on KLD and HD was used for detecting jamming attacks in a LoRaWAN Network. Strength: Ability to detect and respond quickly to anomalous behavior. Ability to detect new forms of attacks which might deviate from the normal behavior. Limitation: Prone to false positives. |
| [17] | Replay and Wormhole attacks. | Integrity | Used data counter to prevent the attacks. |
| [86] | DoS attack | Availability | The Appskey derivation mechanism need to be changed and a special case for join procedure delegation must be introduced. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Adefemi Alimi, K.O.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S. A Survey on the Security of Low Power Wide Area Networks: Threats, Challenges, and Potential Solutions. Sensors 2020, 20, 5800. https://doi.org/10.3390/s20205800
Adefemi Alimi KO, Ouahada K, Abu-Mahfouz AM, Rimer S. A Survey on the Security of Low Power Wide Area Networks: Threats, Challenges, and Potential Solutions. Sensors. 2020; 20(20):5800. https://doi.org/10.3390/s20205800
Chicago/Turabian StyleAdefemi Alimi, Kuburat Oyeranti, Khmaies Ouahada, Adnan M. Abu-Mahfouz, and Suvendi Rimer. 2020. "A Survey on the Security of Low Power Wide Area Networks: Threats, Challenges, and Potential Solutions" Sensors 20, no. 20: 5800. https://doi.org/10.3390/s20205800
APA StyleAdefemi Alimi, K. O., Ouahada, K., Abu-Mahfouz, A. M., & Rimer, S. (2020). A Survey on the Security of Low Power Wide Area Networks: Threats, Challenges, and Potential Solutions. Sensors, 20(20), 5800. https://doi.org/10.3390/s20205800







