An Efficient Two-Factor Authentication Scheme Based on the Merkle Tree
Abstract
:1. Introduction
- We propose a novel OTP algorithm, referred to as the Merkle tree-based One-Time Password (MOTP). MOTP combines a Merkle tree with T/Key to construct many OTPs. Again, since it is affected by the limited number of generated OTPs, MOTP can be periodically reinitialized, reducing the probability for OTP to be cracked.
- We improve the execution efficiency of the OTP algorithm. More precisely, MOTP improves the OTP verification performance of T/Key, at the cost of little server storage. In particular, since the time consumption of MOTP is milliseconds, it is difficult for users to notice such delays. On the other hand, compared with TOTP, the time consumption can increase the cost of brute force attacks for the adversary, and MOTP can resist leakage attacks against servers.
- Security analysis and experiments prove the effectiveness of MOTP. More precisely, security analysis demonstrates that MOTP can resist leakage attacks against the server, and experimental results show that MOTP brings little delay to two-factor authentication.
2. Related Work
3. Merkle Tree-Based One-Time Password Algorithm
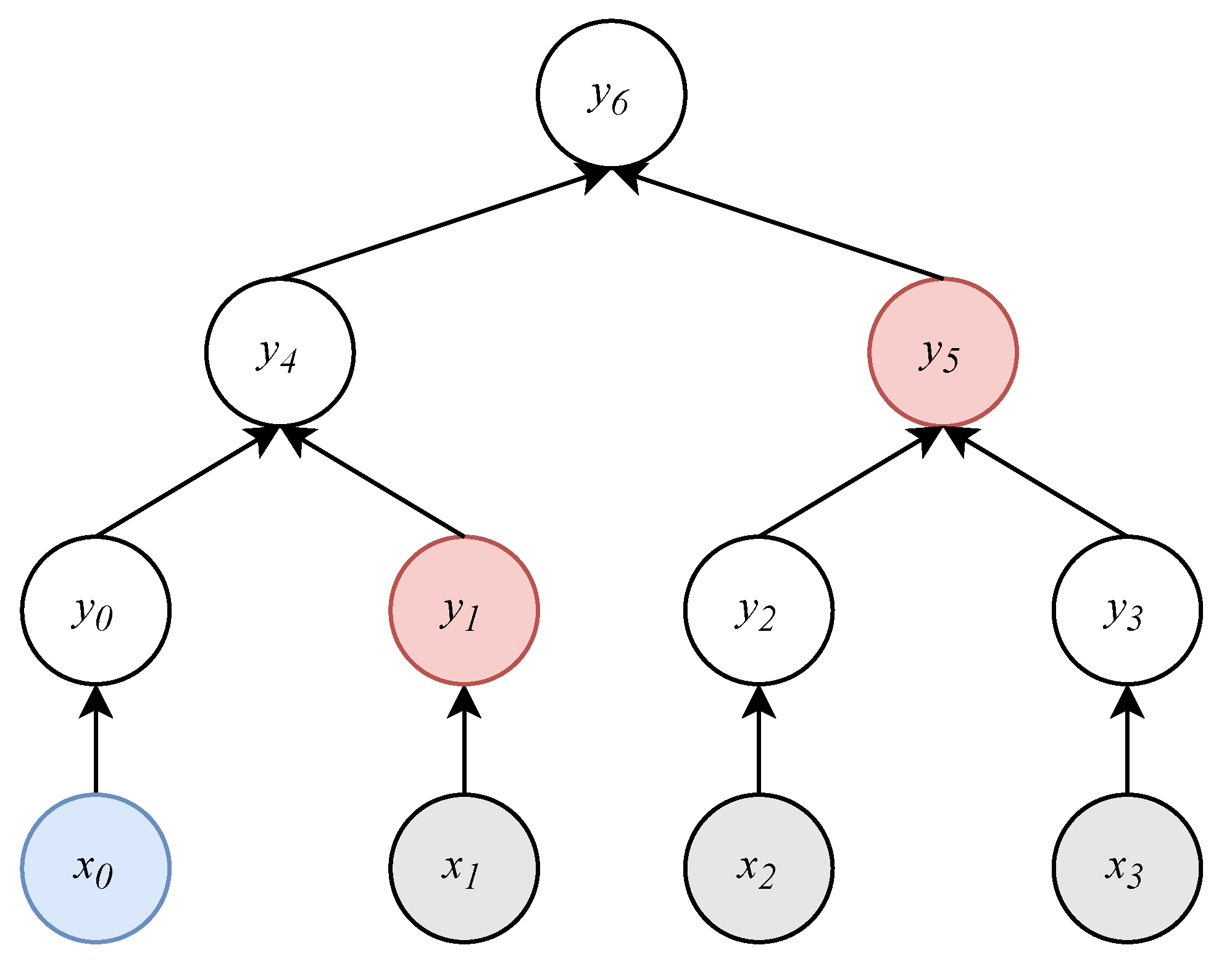
3.1. Merkle Tree
3.2. A Naive Merkle Tree-Based One-Time Password Scheme
3.3. An Improved Merkle Tree-Based One-Time Password Scheme
3.3.1. Efficiency
3.3.2. Network Transmission
3.3.3. Client Storage
3.3.4. Validity
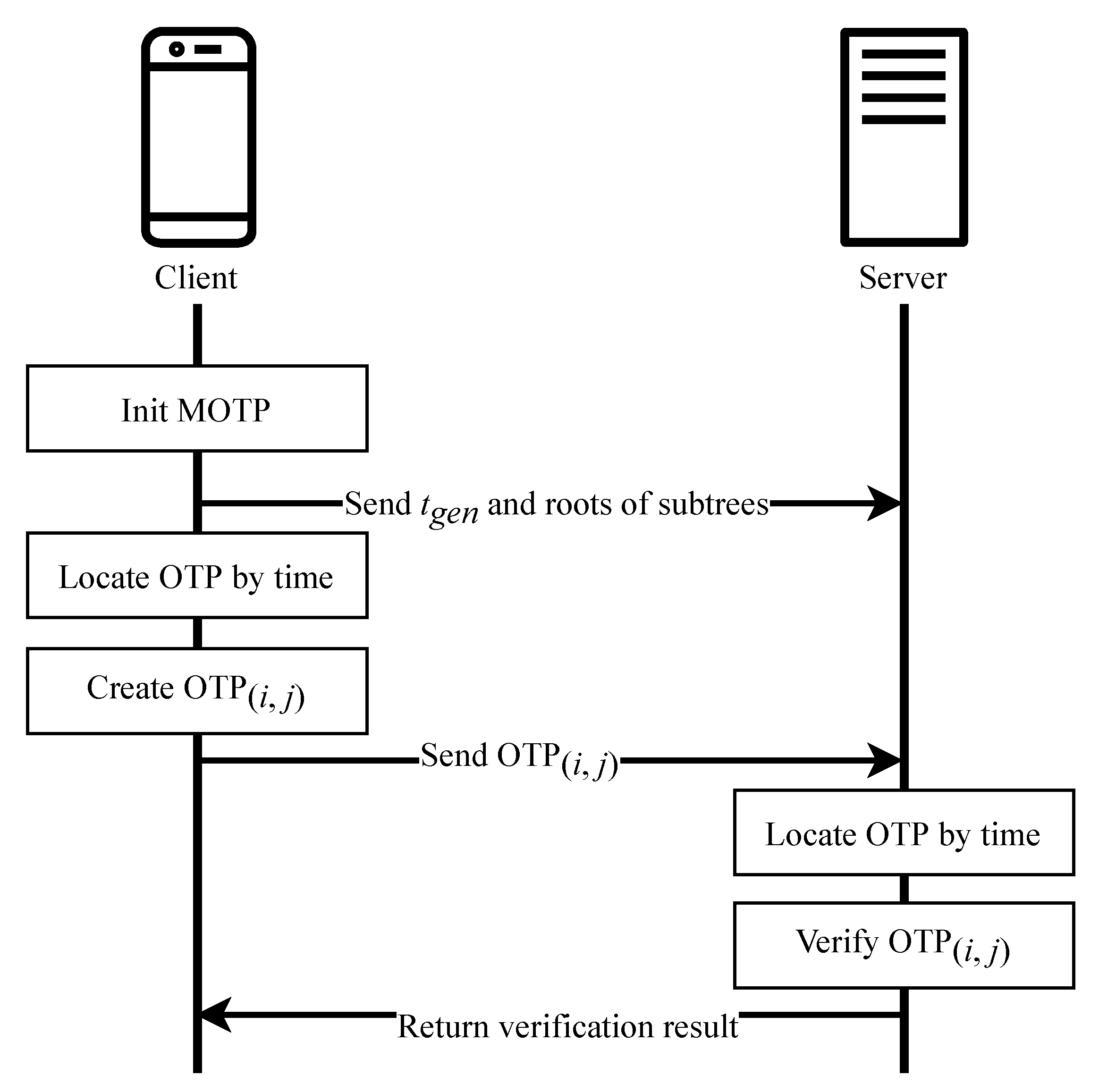
3.3.5. Overall Schema
- The client generates nonces and then performs p hash operations on each nonce to generate each hash chain.
- The tail nodes of all hash chains serve as the leaf nodes and then generate a Merkle tree of height .
- Split the Merkle tree into subtrees of height .
- The client stores subtrees, the nonces, and , then it sends the root nodes of subtrees and to the server through a secure channel.
| Algorithm 1: MOTP initialization. |
 |
- Calculates and obtains , according to Equation (1).
- Reads the nonce, , and hashes it times to get .
- Reads the proof path of .
- Sends as to the server through a secure channel.
| Algorithm 2: MOTP generation. |
| Input: Output: OTP ; ; ; ; ; return; |
- Receives and parses it to get and .
- Calculates and gets according to Equation (1).
- Hashes i times to get .
- Calculates , which is the sequence number of the subtree corresponding to .
- Uses and the root node value of the subtree to verify the correctness of .
| Algorithm 3: MOTP verification. |
| Input: Output: verification result (true / false) ; ; ; ; ; return; |
3.4. Security Analysis
- The adversary can access all information stored on the server by using leakage attacks, but he/she cannot modify any value. Such information could be the root nodes.
- The adversary can perform at most T hash function computations until the server detects the attack and resets the Merkle tree.
- There is no malware on the client, and the adversary cannot get the OTP from the client. If the adversary can directly access the user’s device, he/she can carry out session hijacking, and authentication cannot prevent it. Then, the communication between the client and the server is protected by TLS, so the adversary cannot intercept the OTP through a man-in-the-middle attack.
- We divide adversaries into two types. Adversary performs guessing attacks to guess the correct OTP. Adversary intends to restore the Merkle tree by the root stored on the server and obtains all OTPs.
4. Two-Factor Authentication
5. Experimental Results and Discussion
5.1. Implementation
5.2. Experiment
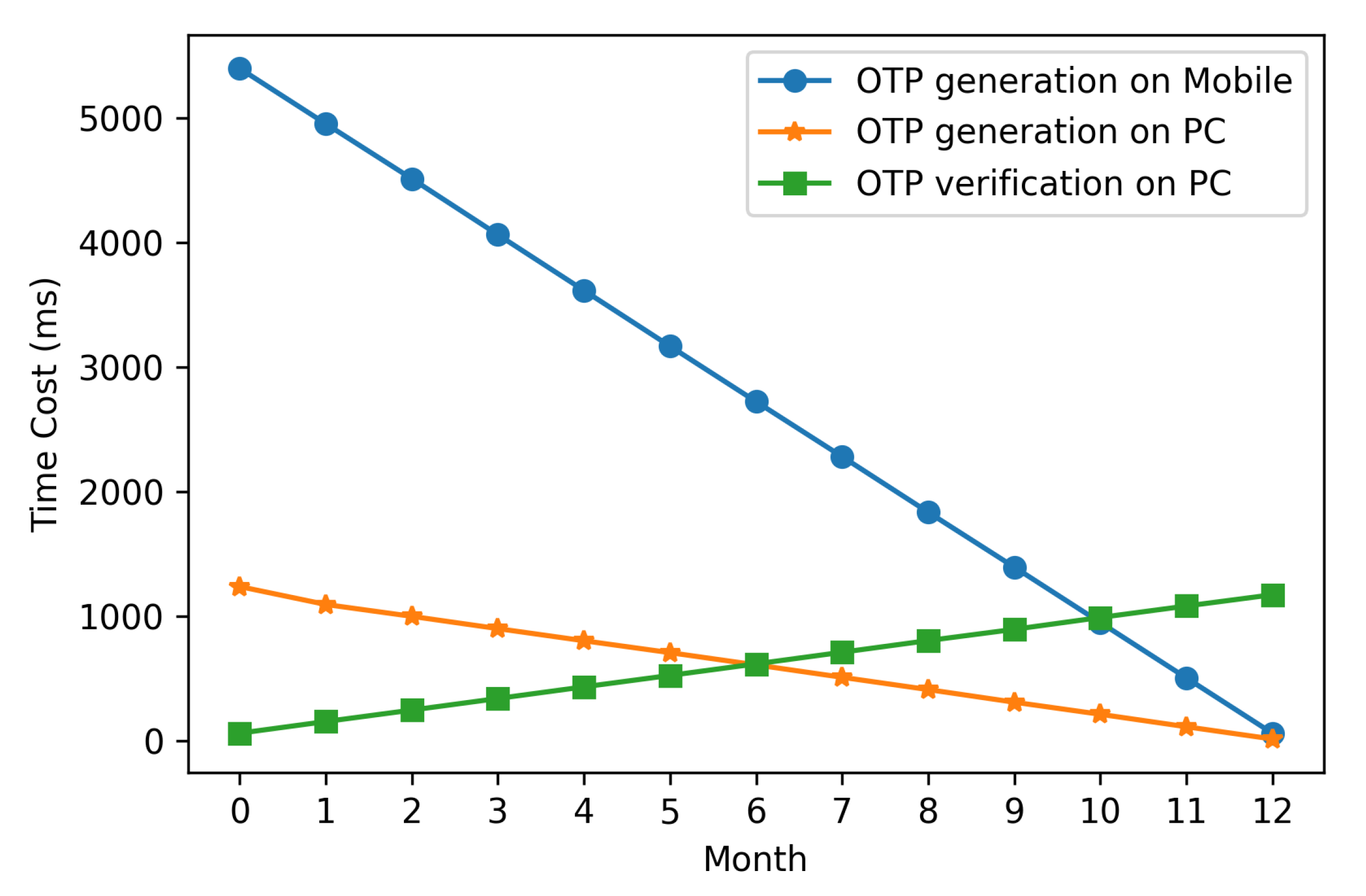
5.2.1. Execution Cost
5.2.2. Transmission Cost
- Request without OTP
- Request with OTP
5.3. Comparison
5.3.1. Comparison with T/Key
5.3.2. Comparison with SmartOTPs
- In terms of the entities involved, SmartOTPs involves four entities: an authenticator (mobile), a client, a private key wallet, and a smart contract. MOTP only involves two entities: a client and a server.
- In terms of OTP usability, SmartOTPs separates the construction of on two devices. The authenticator is used to generate so that the user only needs to enter the short digit to the client. Then, the client generates and sends to the smart contract. On the other hand, MOTP uses QR codes to transmit the OTP generated by the client.
- In the use of the hash chain, SmartOTPs only uses Lamport’s hash chain, while MOTP adopts the idea of T/Key and introduces a time gap to make OTP time sensitive.
- In terms of OTP location, SmartOTPs relies on the sequence number sent by the client to the authenticator to generate the corresponding OTP. On the other hand, MOTP uses the current time of the device to generate the corresponding OTP without relying on other devices.
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Adams, A.; Sasse, M. Users are not the enemy. Commun. ACM 1999, 42, 40–46. [Google Scholar] [CrossRef]
- Bošnjak, L.; Sreš, J.; Brumen, B. Brute-force and dictionary attack on hashed real-world passwords. In Proceedings of the 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018; pp. 1161–1166. [Google Scholar] [CrossRef]
- Han, W.; Li, Z.; Yuan, L.; Xu, W. Regional Patterns and Vulnerability Analysis of Chinese Web Passwords. IEEE Trans. Inf. Forensics and Secur. 2016, 11, 258–272. [Google Scholar] [CrossRef]
- Velásquez, I.; Caro, A.; Rodríguez, A. Authentication schemes and methods: A systematic literature review. Inform. Software Tech. 2018, 94, 30–37. [Google Scholar] [CrossRef]
- Google. Google-Authenticator. Available online: https://github.com/google/google-authenticator/wiki (accessed on 20 January 2020).
- M’Raihi, D.; Bellare, M.; Hoornaert, F.; Naccache, D.; Ranen, O. RFC 4226 HOTP: An HMAC-Based One-Time Password Algorithm. Available online: https://www.rfc-editor.org/info/rfc4226 (accessed on 20 January 2020).
- M’Raihi, D.; Machani, S.; Pei, M.; Rydell, J. RFC 6238 TOTP: Time-Based One-Time Password Algorithm. Available online: https://www.rfc-editor.org/info/rfc6238 (accessed on 20 January 2020).
- Kogan, D.; Manohar, N.; Boneh, D. T/Key: Second-Factor Authentication From Secure Hash Chains. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Association for Computing Machinery. New York, NY, USA, 30 October–3 November 2017; CCS ’17. pp. 983–999. [Google Scholar] [CrossRef] [Green Version]
- Homoliak, I.; Breitenbacher, D.; Binder, A.; Szalachowski, P. SmartOTPs: An Air-Gapped 2-Factor Authentication for Smart-Contract Wallets. arXiv 2018, arXiv:1812.03598. [Google Scholar]
- Herley, C.; Oorschot, P.V. A Research Agenda Acknowledging the Persistence of Passwords. IEEE Secur. Priv. 2012, 10, 28–36. [Google Scholar] [CrossRef] [Green Version]
- Li, H.; Lu, R.; Zhou, L.; Yang, B.; Shen, X. An Efficient Merkle-Tree-Based Authentication Scheme for Smart Grid. IEEE Syst. J. 2014, 8, 655–663. [Google Scholar] [CrossRef]
- Huszti, A.; Oláh, N. A simple authentication scheme for clouds. In Proceedings of the 2016 IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA, 17–19 October 2016; pp. 565–569. [Google Scholar]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Bittl, S. Efficient construction of infinite length hash chains with perfect forward secrecy using two independent hash functions. In Proceedings of the 2014 11th International Conference on Security and Cryptography (SECRYPT), Vienna, Austria, 28–30 August 2014; pp. 1–8. [Google Scholar]
- Park, C.S. One-time password based on hash chain without shared secret and re-registration. Comput. Secur. 2018, 75, 138–146. [Google Scholar] [CrossRef]
- Erdem, E.; Sandıkkaya, M.T. OTPaaS—One Time Password as a Service. IEEE Trans. Inf. Forensics Secur. 2019, 14, 743–756. [Google Scholar] [CrossRef]
- Shirvanian, M.; Jarecki, S.; Saxena, N.; Nathan, N. Two-Factor Authentication Resilient to Server Compromise Using Mix-Bandwidth Devices. Presented at NDSS Symposium 2014, San Diego, CA, USA, 23–26 February 2014. [Google Scholar] [CrossRef] [Green Version]
- Merkle, R.C. A Certified Digital Signature. In Proceedings of the Advances in Cryptology—CRYPTO’ 89 Proceedings, Santa Barbara, CA, USA, 20–24 August 1989; Brassard, G., Ed.; Springer: New York, NY, USA, 1990; pp. 218–238. [Google Scholar]
- Dai, H.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A Survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef] [Green Version]
- Liang, W.; Huang, W.; Long, J.; Zhang, K.; Li, K.; Zhang, D. Deep Reinforcement Learning for Resource Protection and Real-time Detection in IoT Environment. IEEE Internet Things J. 2020, 7, 6392–6401. [Google Scholar] [CrossRef]
- Liang, W.; Li, K.; Long, J.; Kui, X.; Zomaya, A. An Industrial Network Intrusion Detection Algorithm based on Multi-Feature Data Clustering Optimization Model. IEEE Trans. Industr. Inform. 2020, 16, 2063–2071. [Google Scholar] [CrossRef]
- Narayanan, A.; Shmatikov, V. Fast Dictionary Attacks on Passwords Using Time-Space Tradeoff. In CCS ’05, Proceedings of the 12th ACM Conference on Computer and Communications Security, New York, NY, USA, 7–11 November 2005; Association for Computing Machinery: New York, NY, USA, 2005; pp. 364–372. [Google Scholar] [CrossRef]
- Gupta, S.; Singhal, A.; Kapoor, A. A literature survey on social engineering attacks: Phishing attack. In Proceedings of the 2016 International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India 29–30 April 2016; pp. 537–540. [Google Scholar] [CrossRef]
- AbdAllah, E.G.; Hassanein, H.S.; Zulkernine, M. A Survey of Security Attacks in Information-Centric Networking. IEEE Commun. Surv. 2015, 17, 1441–1454. [Google Scholar] [CrossRef]
- Starnberger, G.; Froihofer, L.; Goeschka, K.M. QR-TAN: Secure Mobile Transaction Authentication. In Proceedings of the 2009 International Conference on Availability, Reliability and Security, Fukuoka, Japan, 16–19 March 2009; pp. 578–583. [Google Scholar] [CrossRef]
- Babkin, S.; Epishkina, A. Authentication Protocols Based on One-Time Passwords. In Proceedings of the 2019 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow and St. Petersburg, Russia, 28–31 January 2019; pp. 1794–1798. [Google Scholar] [CrossRef]
- Jiao, J.; Wang, L.; Li, Y.; Han, D.; Yao, M.; Li, K.; Jiang, H. CASH: Correlation-aware scheduling to mitigate soft error impact on heterogeneous multicores. Conn. Sci. 2020. [Google Scholar] [CrossRef]
- Xiao, T.; Han, D.; He, J.; Li, K.; de Mello, R. Multi-Keyword ranked search based on mapping set matching in cloud ciphertext storage system. Conn. Sci. 2020. [Google Scholar] [CrossRef]
- Liang, W.; Fan, Y.; Li, K.; Zhang, D.; Gaudiot, J. Secure Data Storage and Recovery in Industrial Blockchain Network Environments. IEEE Trans. Industr. Inform. 2020, 16, 6543–6552. [Google Scholar] [CrossRef]
- Han, D.; Pan, N.; Li, K. A traceable and revocable ciphertext-policy attribute-based encryption scheme based on privacy protection. IEEE Trans. Dependable Secur. Comput. 2002. [Google Scholar] [CrossRef]









| Notation | Description |
|---|---|
| Height of the Merkle tree (the height of the root node is 0) | |
| Height of the subtree | |
| p | Execution times of the hash function when constructing a hash chain |
| Hash x | |
| Hash x p times | |
| Generation time of the Merkle tree | |
| Difference between the device’s current time and | |
| Time gap of the OTP | |
| Node value on the hash chain | |
| Proof path |
| Height | Number of OTPs | Client Storage |
|---|---|---|
| 10 | 1024 | 96 KB |
| 15 | 32,768 | 3 MB |
| 20 | 1,048,576 | 96 MB |
| Parameter | Value | Parameter | Value |
|---|---|---|---|
| 10 | p | 1024 | |
| 7 | Hash algorithm | SHA256 | |
| (s) | 30 | Size of nonce (bit) | 256 |
| Validity Period (Year) | Mobile | PC | ||
|---|---|---|---|---|
| T/Key | MOTP | T/Key | MOTP | |
| 1 | 5403 | 5445 | 1193 | 1280 |
| 2 | 10791 | 10,809 | 2356 | 2409 |
| 4 | 21,610 | 21,540 | 4713 | 4812 |
| Request without OTP | Request with OTP | |
|---|---|---|
| Time (ms) | 0.7811 | 1.0923 |
| Scheme | Resistance to Leakage Attacks | Infinite OTPs | OTPs’ Validity Is Limited in Time | Ease of Implementation |
|---|---|---|---|---|
| Lamport’s OTP | + | − | − | + |
| TOTP | − | + | + | + |
| T/Key | + | − | + | + |
| SmartOTPs | + | − | − | − |
| MOTP | + | − | + | + |
| Comparison | MOTP | T/Key without Checkpoints | T/Key with Checkpoints |
|---|---|---|---|
| Client storage | b | ||
| Server storage | b | ||
| OTP generation time complexity | , | , | , |
| OTP verification time complexity | , | , | , |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yin, X.; He, J.; Guo, Y.; Han, D.; Li, K.-C.; Castiglione, A. An Efficient Two-Factor Authentication Scheme Based on the Merkle Tree. Sensors 2020, 20, 5735. https://doi.org/10.3390/s20205735
Yin X, He J, Guo Y, Han D, Li K-C, Castiglione A. An Efficient Two-Factor Authentication Scheme Based on the Merkle Tree. Sensors. 2020; 20(20):5735. https://doi.org/10.3390/s20205735
Chicago/Turabian StyleYin, Xinming, Junhui He, Yi Guo, Dezhi Han, Kuan-Ching Li, and Arcangelo Castiglione. 2020. "An Efficient Two-Factor Authentication Scheme Based on the Merkle Tree" Sensors 20, no. 20: 5735. https://doi.org/10.3390/s20205735
APA StyleYin, X., He, J., Guo, Y., Han, D., Li, K.-C., & Castiglione, A. (2020). An Efficient Two-Factor Authentication Scheme Based on the Merkle Tree. Sensors, 20(20), 5735. https://doi.org/10.3390/s20205735







