MultiFuzz: A Coverage-Based Multiparty-Protocol Fuzzer for IoT Publish/Subscribe Protocols
Abstract
1. Introduction
- We propose a multiparty-protocol fuzzer, MultiFuzz, to soundly support the fuzzing of publish/subscribe protocols. The fuzzer could initiate multiple connections to a PUT, and has a new seed format for storing all messages of the connections in a single seed input.
- We propose a message mutation algorithm to mutate message sequences in a seed input, to efficiently stimulate the state transitions of protocols. The mutation algorithm considers the multiple connections stored in a seed as well.
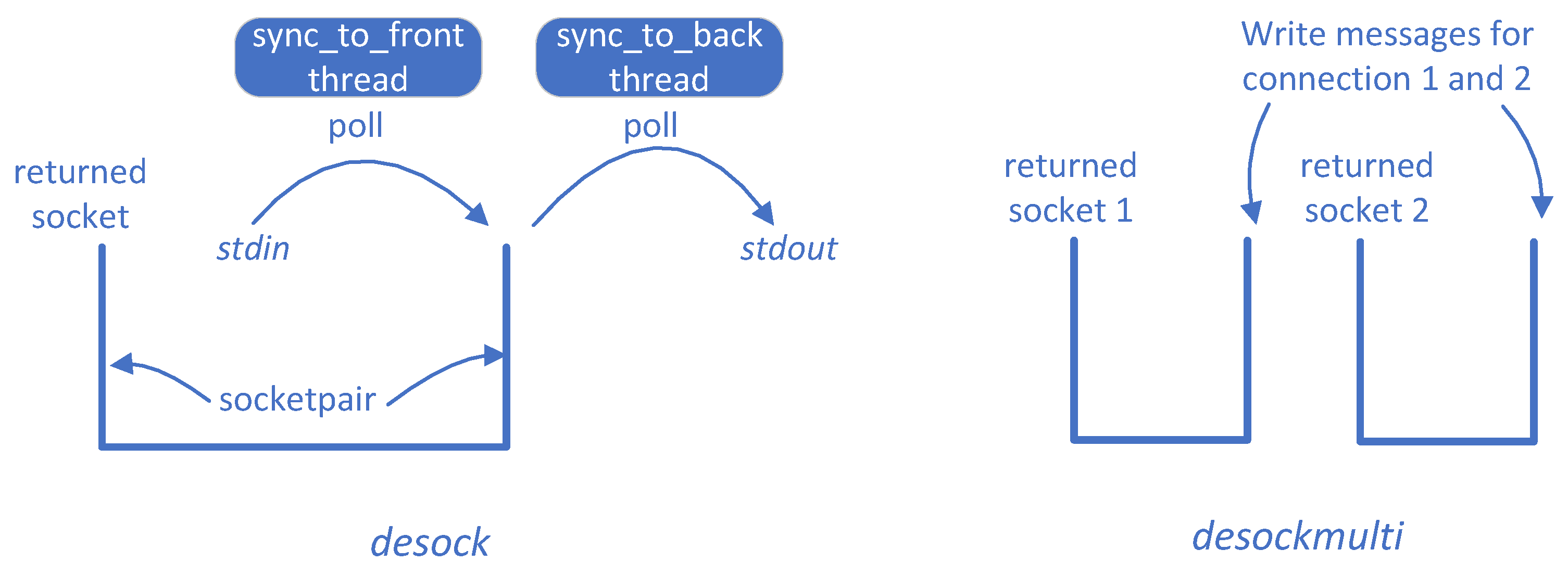
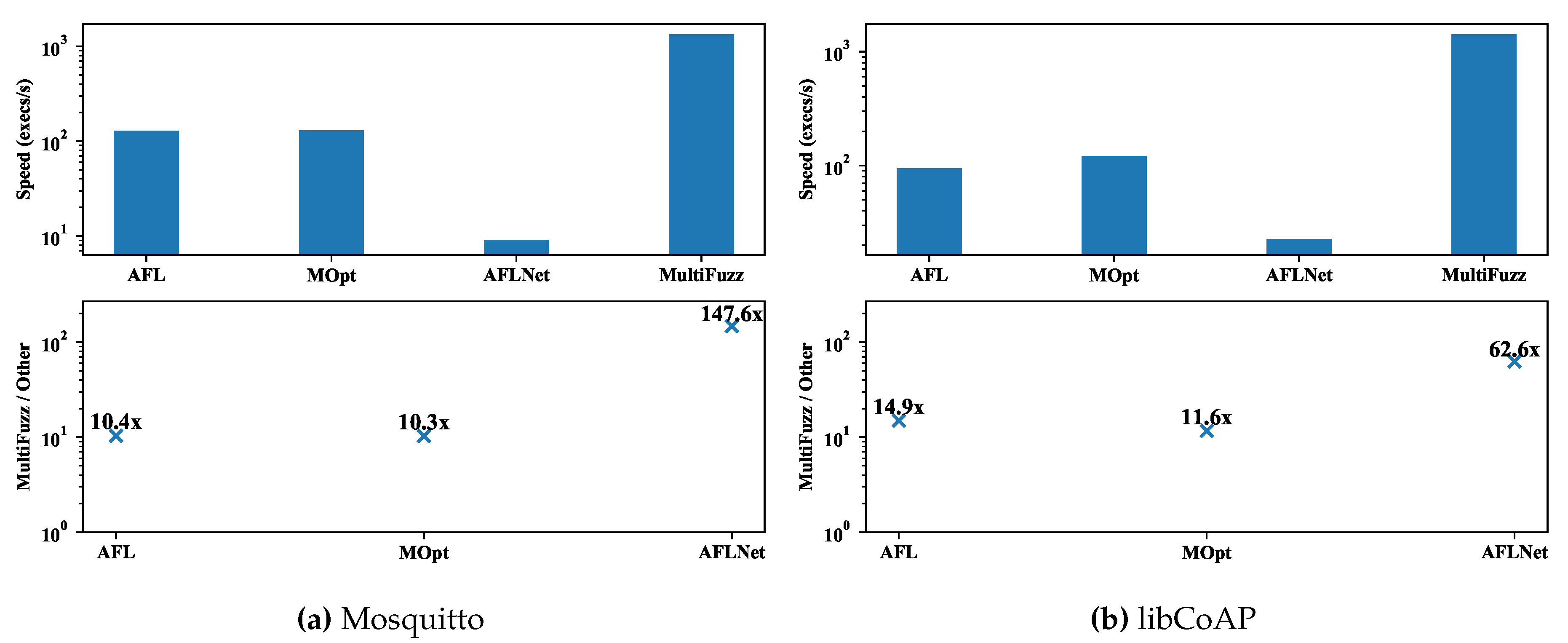
- We design and implement desockmulti for feeding network messages to a PUT. Previously the community usually uses the desock module of Preeny together with AFL to fuzz network services, but desock supports one connection only. We use a new design to support more than one connection, and further optimize desockmulti to be 10x faster than the widely used desock tool (Section 5.4) (We plan to opensource desockmulti after the publication of this paper).
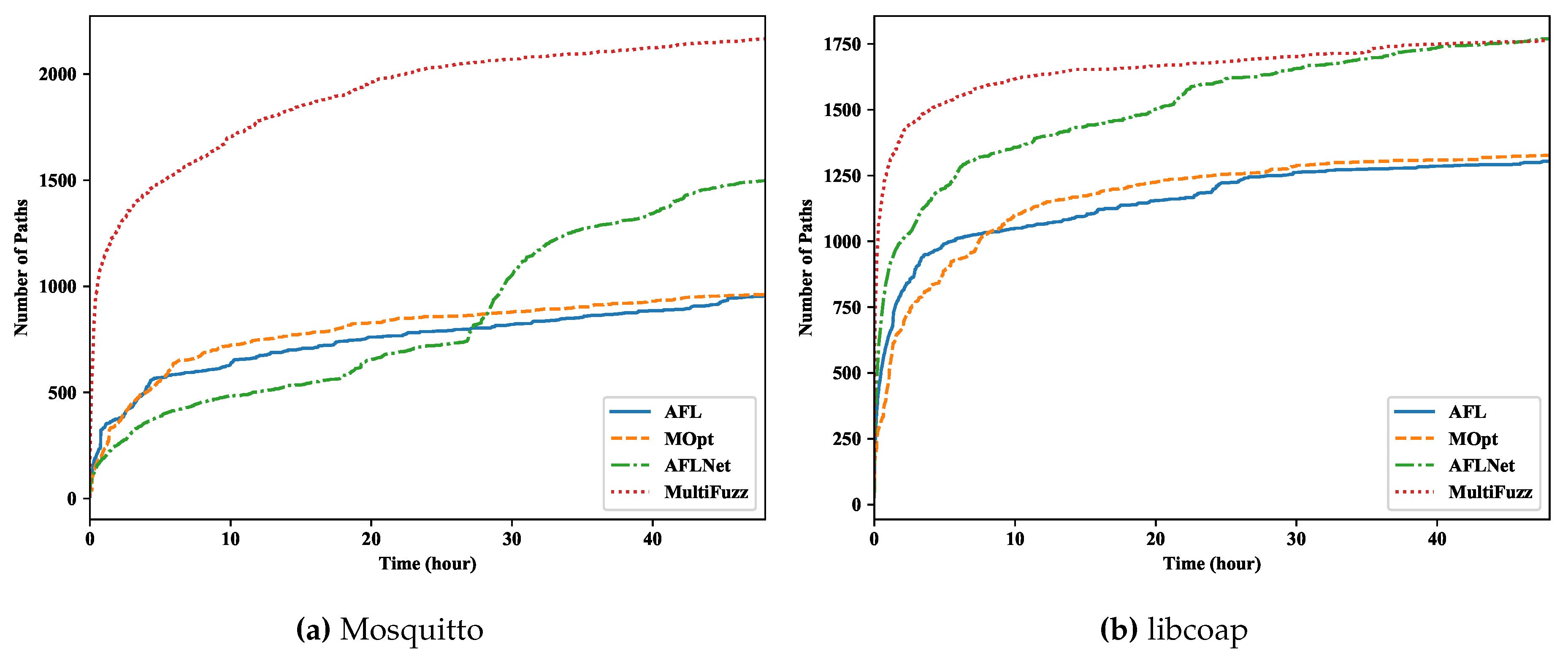
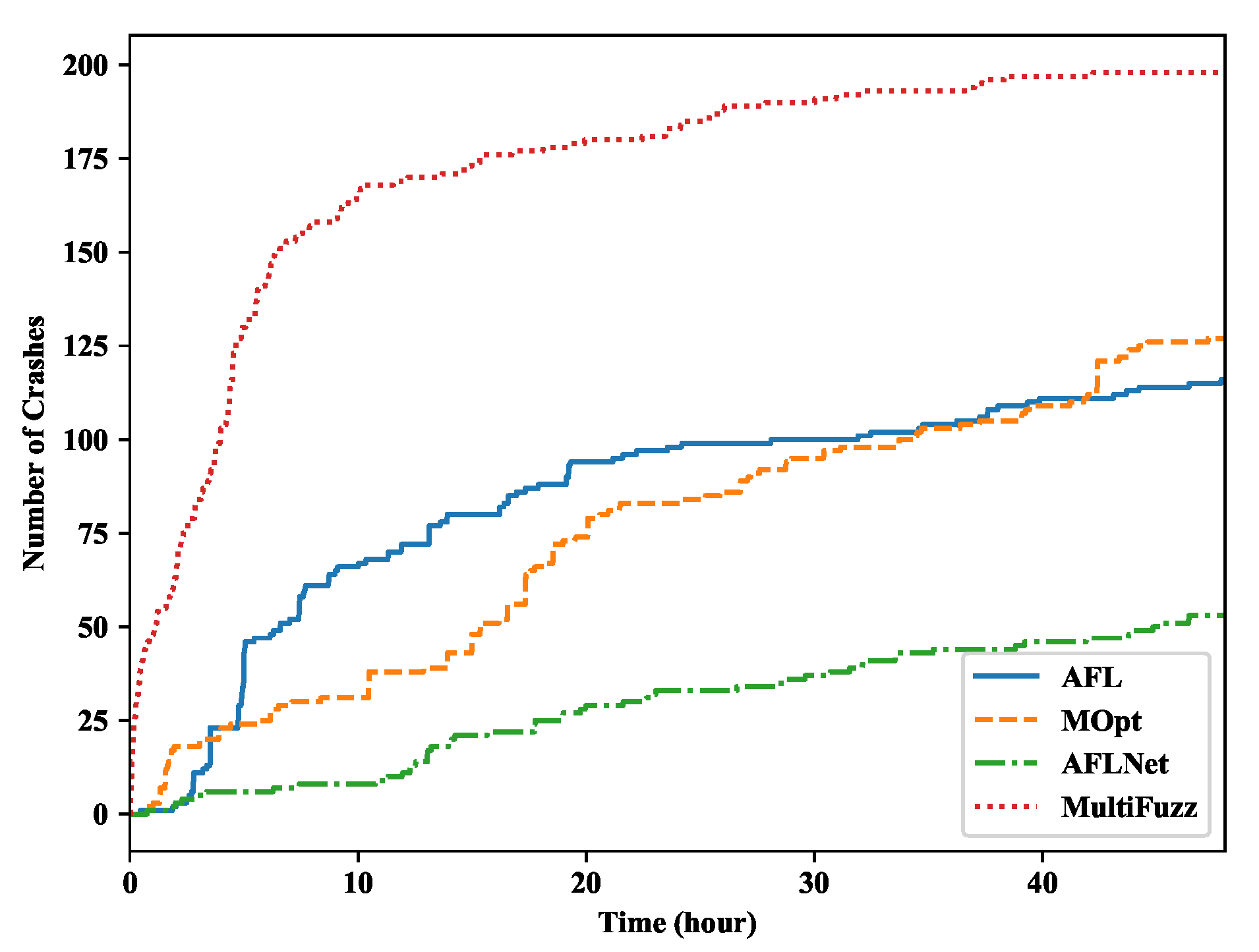
- We implement MultiFuzz based on AFL, and use MultiFuzz to fuzz two popular projects, Eclipse Mosquitto (an MQTT broker) [29], and libCoAP (a CoAP library) [30]. We reported our found vulnerabilities to the projects and were acknowledged (Section 5.5). We also show that MultiFuzz outperforms AFL, and state-of-the-art fuzzers MOPT [14] and AFLNET [15] in finding program paths and crashes (e.g., finding program paths 44.6% more than AFLNET, 126.6% more than AFL, and 125.4% more than MOPT, when fuzzing Eclipse Mosquitto).
2. Related Work
- Blackbox network-protocol fuzzing [19]. It includes general protocol fuzzing tools like SPIKE [33], PROTOS [34], SNOOZE [35], LZFuzz [36], Boofuzz (Sulley) [26], and Peach [8], as well as tools specially designed for some protocols, like TLS-Attacker [27] for the Transport Layer Security (TLS) protocol, and MTF [37] for the Modbus protocol. Most of these tools need users to tell the formats of network messages, and some of them also support users to provide the transition rules of protocol states [8]. For the general protocol fuzzing tools, users need to provide such information by scripts [26,33,34] or xml files [8,35]. For the tools specially designed for some protocols, such information is provided by tool developers. Most of these tools pretend as clients to feed inputs into the network programs, and some tools like LZFuzz [36] act as man-in-the-middle (MITM) proxies to modify messages between the client and the server. Blackbox fuzzing usually requires to write scripts, xml files, or codes following the protocol specifications, and needs to update them accordingly when the protocols have new versions. In addition, blackbox fuzzing may be more suitable for discovering “shallow” bugs, comparing with greybox and whitebox fuzzing [6].
- Greybox network-protocol fuzzing [3,10,15]. The general coverage-based fuzzing tools like AFL [3] and libFuzzer [4] are used to fuzz network protocols as well. Usually users do not need to know protocol specifications or write any scripts/codes, instead, they prepare (e.g., by recording) some messages as seed inputs. However, since tools like AFL [3] were used to fuzz programs using files/stdin/memory buffer as the input source, they need some way to feed fuzzing inputs into the network programs. There are three known ways now. AFL recommends to use Preeny (desock) [28], a hook-based tool, to simply redirect stdin to sockets hijacked by the tool [3], AFLNET [15] sends inputs through ordinary sockets to the network programs, and users could also modify the program source codes to make the programs read packets directly from memory buffers other than real network interfaces, like the Google OSS-Fuzz project does to openssl [10]. The first two ways may limit the execution speed of fuzzing (comparing with the desockmulti tool proposed in this paper). The third way may be difficult if the original developers of the programs do not expect such modification, and is also impossible for closed source programs. A very recent work AFLNET [15] proposed to combine coverage-based fuzzing with automated state model inferencing. While the fuzzing generates new message sequences to cover new states, the inferred state model guides how to do the fuzzing. AFLNET is shown to outperform Boofuzz [26] and AFL [3] in both code coverage and vulnerability discovery [15]. However, it requires users to write codes to extract partial information like the response codes from messages.
3. An Introduction to MQTT and CoAP
4. MultiFuzz
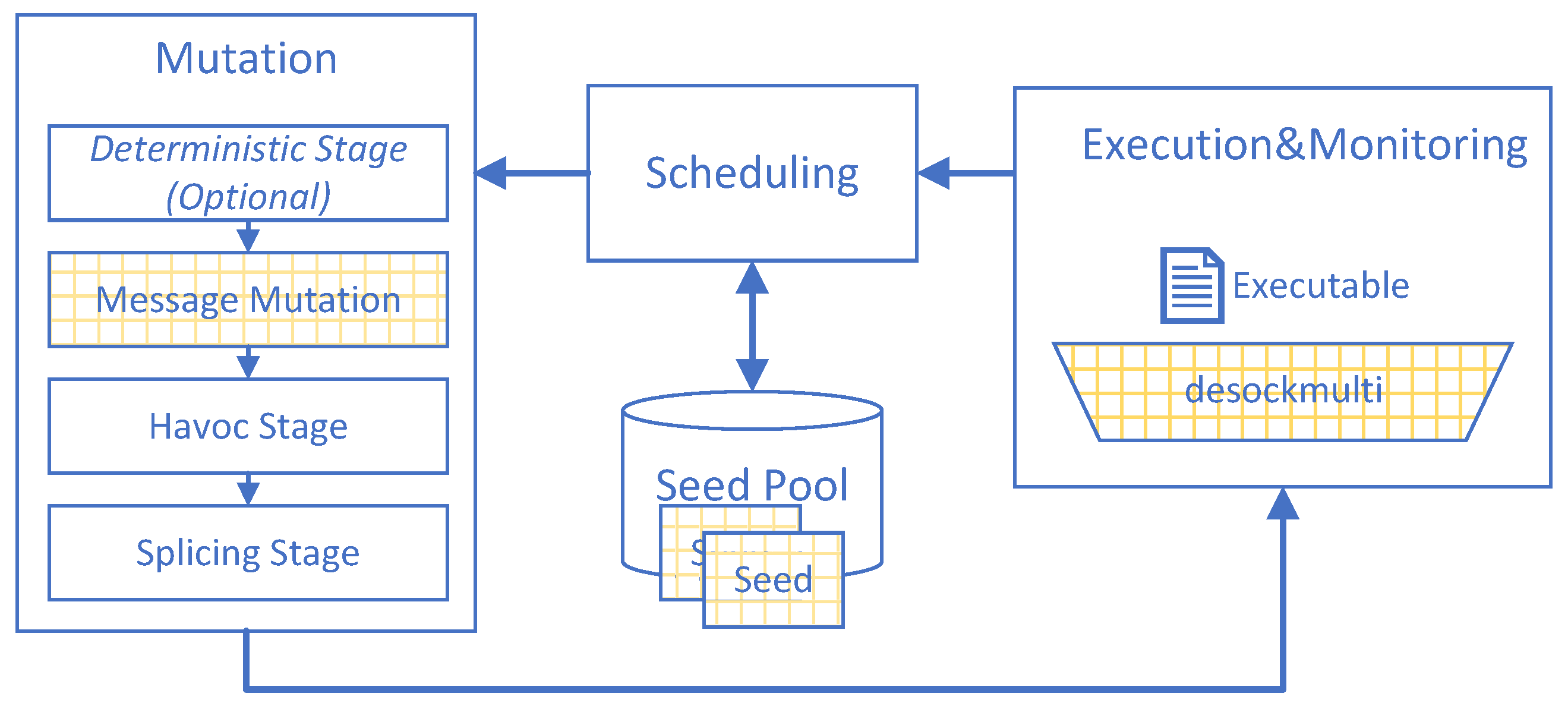
4.1. Overview
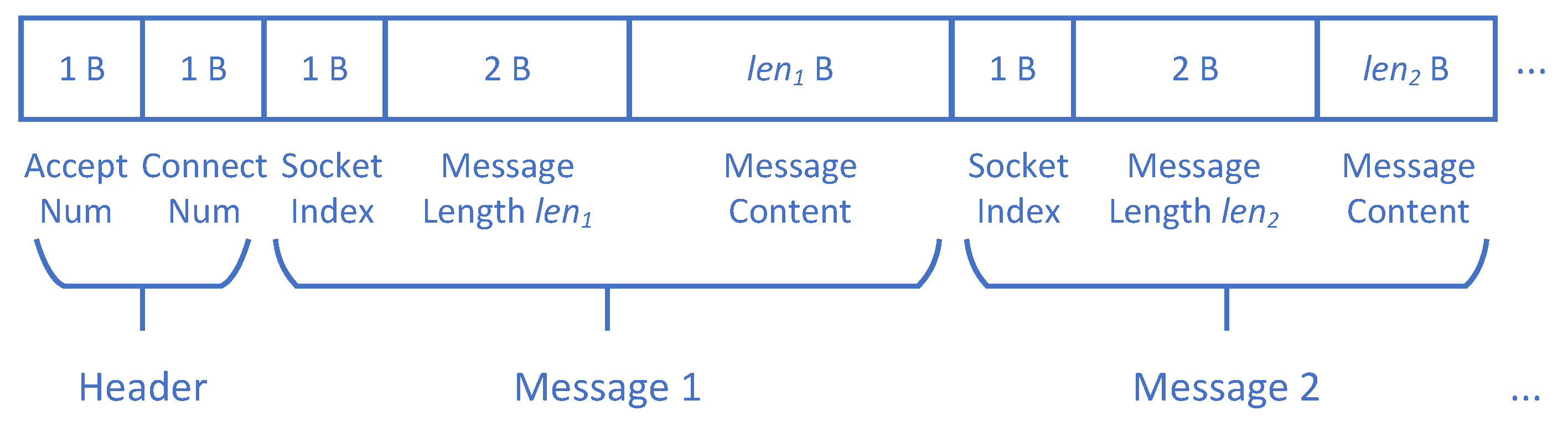
4.2. Augmenting Seeds with Multi-Connection Information
4.3. The New Message Mutation Stage
| Algorithm 1 Message mutation algorithm |
| Input: seed (its connection information already parsed) Output: output buffer
|
4.4. desockmulti, A Fast and Multi-Connection-Oriented De-Socketing Tool
- desockmulti supports the new seed format.
- desockmulti can initiate multiple connections (i.e., one or more) to a PUT, and it could be a replacement of desock, which can only initiate one connection.
- desockmulti is optimized for fuzzing, and is 10x faster than desock.
4.5. Other Implementation Details
5. Evaluation
5.1. Experiment Settings
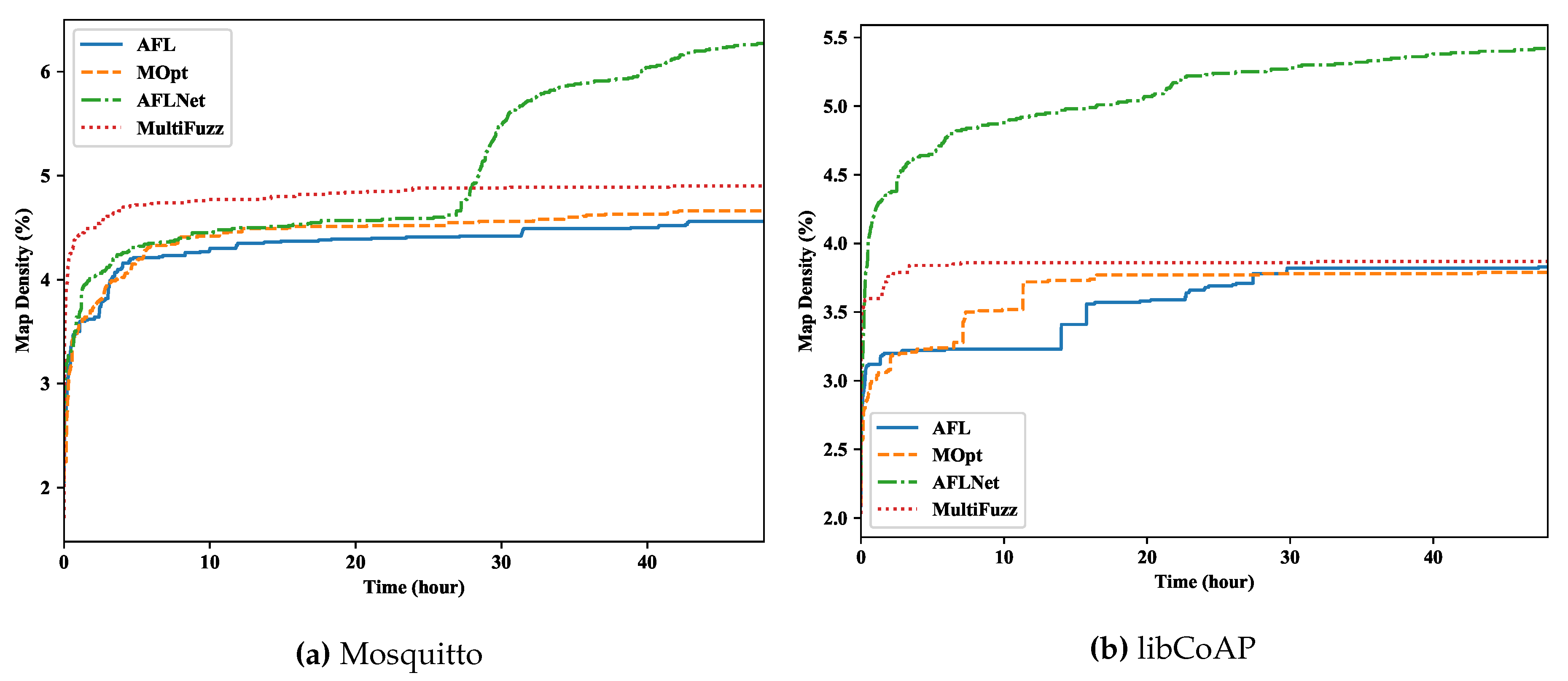
5.2. Path and Crash Discovery
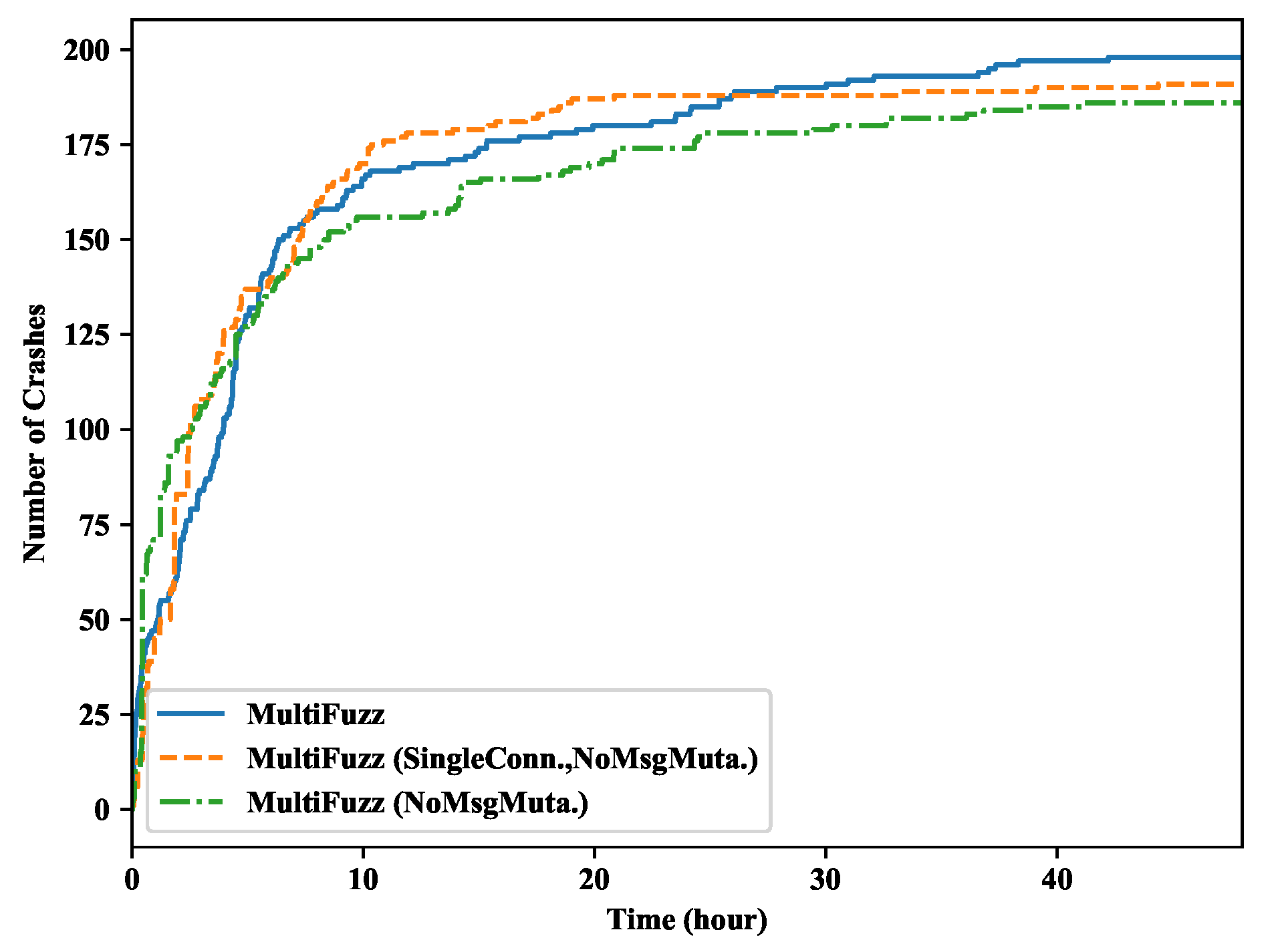
5.3. Effects of the Multi-Connection Design and the Message Mutation Algorithm
5.4. The Comparison of Execution Speeds
5.5. Vulnerability Analysis
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Miller, B.P.; Fredriksen, L.; So, B. An Empirical Study of the Reliability of UNIX Utilities. Commun. ACM. 1990, 33, 32–44. [Google Scholar] [CrossRef]
- Manes, V.J.M.; Han, H.S.; Han, C.; Cha, S.K.; Egele, M.; Schwartz, E.J.; Woo, M. The Art, Science, and Engineering of Fuzzing: A Survey. IEEE T. Software. Eng. 2019, 1–21. [Google Scholar] [CrossRef]
- Zalewski, M. AFL—American Fuzzy Lop. Available online: http://lcamtuf.coredump.cx/afl/ (accessed on 29 July 2020).
- libFuzzer. Available online: http://llvm.org/docs/LibFuzzer.html (accessed on 29 July 2020).
- Böhme, M.; Pham, V.T.; Roychoudhury, A. Coverage-based Greybox Fuzzing as Markov Chain. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (CCS), Vienna, Austria, 24–28 October 2016; pp. 1032–1043. [Google Scholar] [CrossRef]
- Liang, H.; Pei, X.; Jia, X.; Shen, W.; Zhang, J. Fuzzing: State of the Art. IEEE T. Reliab. 2018, 67, 1199–1218. [Google Scholar] [CrossRef]
- zzuf. Available online: http://caca.zoy.org/wiki/zzuf (accessed on 29 July 2020).
- Peach Tech. Peach Fuzzer. Available online: https://www.peach.tech (accessed on 29 July 2020).
- Godefroid, P.; Kiezun, A.; Levin, M.Y. Grammar-based whitebox fuzzing. In Proceedings of the ACM SIGPLAN Conference on Programming Language Design and Implementation (PLDI), Tucson, AZ, USA, 7–13 June 2008; pp. 206–215. [Google Scholar] [CrossRef]
- Google Security Team. A New Chapter for OSS-Fuzz. Available online: https://security.googleblog.com/2018/11/a-new-chapter-for-oss-fuzz.html (accessed on 29 July 2020).
- Gan, S.; Zhang, C.; Qin, X.; Tu, X.; Li, K.; Pei, Z.; Chen, Z. CollAFL: Path Sensitive Fuzzing. In Proceedings of the IEEE Symposium on Security and Privacy (S&P), San Francisco, CA, USA, 21–23 May 2018; pp. 679–696. [Google Scholar] [CrossRef]
- Chen, P.; Chen, H. Angora: Efficient Fuzzing by Principled Search. In Proceedings of the IEEE Symposium on Security and Privacy (S&P), San Francisco, CA, USA, 21–23 May 2018; pp. 711–725. [Google Scholar] [CrossRef]
- Yun, I.; Lee, S.; Xu, M.; Jang, Y.; Kim, T. QSYM: A Practical Concolic Execution Engine Tailored for Hybrid Fuzzing. In Proceedings of the 27th USENIX Security Symposium (Security), Baltimore, MD, USA, 15–17 August 2018; pp. 745–761. [Google Scholar]
- Lyu, C.; Ji, S.; Zhang, C.; Li, Y.; Lee, W.H.; Song, Y.; Beyah, R. MOPT: Optimize Mutation Scheduling for Fuzzers. In Proceedings of the 28th USENIX Security Symposium (Security), Santa Clara, CA, USA, 14–16 August 2019; pp. 1949–1966. [Google Scholar]
- Pham, V.t.; Boehme, M.; Roychoudhury, A. AFLNet: A Greybox Fuzzer for Network Protocols. In Proceedings of the 13rd IEEE International Conference on Software Testing, Verification and Validation: Testing Tools Track, Porto, Portugal, 24–28 October 2020; pp. 460–465. [Google Scholar] [CrossRef]
- Aschermann, C.; Schumilo, S.; Abbasi, A.; Holz, T. IJON: Exploring Deep State Spaces via Fuzzing. In Proceedings of the IEEE Symposium on Security and Privacy (S&P), San Francisco, CA, USA, 17–21 May 2020; pp. 1–16. [Google Scholar]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE. Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Yassein, M.B.; Shatnawi, M.Q.; Al-Zoubi, D. Application layer protocols for the Internet of Things: A survey. In Proceedings of the 2016 International Conference on Engineering and MIS (ICEMIS), Agadir, Morocco, 22–24 September 2016. [Google Scholar] [CrossRef]
- Dizdarević, J.; Carpio, F.; Jukan, A.; Masip-Bruin, X. A survey of communication protocols for internet of things and related challenges of fog and cloud computing integration. ACM. Comput. Surv. 2019, 51, 1–30. [Google Scholar] [CrossRef]
- Pereira, C.; Aguiar, A. Towards efficient mobile M2M communications: Survey and open challenges. Sensors 2014, 14, 19582–19608. [Google Scholar] [CrossRef] [PubMed]
- Banks, A.; Briggs, E.; Borgendale, K.; Gupta, R. (Eds.) MQTT Version 5.0; OASIS Standard: Burlington, MA, USA, 2019. [Google Scholar]
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (CoAP). RFC 7252 2014; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2014. [Google Scholar]
- Hartke, K. Observing Resources in the Constrained Application Protocol (CoAP). RFC 7641 2015; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2015. [Google Scholar]
- Team, T.H. Comparison of MQTT Support by IoT Cloud Platforms. Available online: https://www.hivemq.com/blog/hivemq-cloud-vs-aws-iot/ (accessed on 29 July 2020).
- Ptone. IoT Core CoAP proxy demonstration. Available online: https://cloud.google.com/community/tutorials/cloud-iot-coap-proxy (accessed on 29 July 2020).
- Boofuzz: Network Protocol Fuzzing for Humans. Available online: https://github.com/jtpereyda/boofuzz (accessed on 29 July 2020).
- Somorovsky, J. Systematic Fuzzing and Testing of TLS Libraries. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (CCS), Vienna, Austria, 24–28 October 2016; pp. 1492–1504. [Google Scholar] [CrossRef]
- Preeny. Available online: https://github.com/zardus/preeny (accessed on 29 July 2020).
- Eclipse Mosquitto. Available online: https://mosquitto.org/ (accessed on 29 July 2020).
- libcoap. Available online: https://libcoap.net/ (accessed on 29 July 2020).
- Klees, G.; Ruef, A.; Cooper, B.; Wei, S.; Hicks, M. Evaluating Fuzz Testing. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (CCS), Toronto, ON, Canada, 15–19 October 2018; pp. 2123–2138. [Google Scholar] [CrossRef]
- Godefroid, P.; Levin, M.Y.; Molnar, D. Automated whitebox fuzz testing. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 10–13 February 2008; pp. 416–426. [Google Scholar]
- Aitel, D. The Advantages of Block-Based Protocol Analysis for Security Testing; Technical Report; Immunity Inc.: New York, NY, USA, 2002. [Google Scholar]
- Roning, J.; Laakso, M.; Takanen, A. PROTOS Presentations. Available online: https://www.ee.oulu.fi/research/ouspg/ (accessed on 29 July 2020).
- Banks, G.; Cova, M.; Felmetsger, V.; Almeroth, K.C.; Kemmerer, R.A.; Vigna, G. SNOOZE: Toward a Stateful NetwOrk prOtocol fuzZEr. In Proceedings of the Information Security, 9th International Conference (ISC), Samos Island, Greece, 30 August–2 September 2006; pp. 343–358. [Google Scholar] [CrossRef]
- Bratus, S.; Hansen, A.; Shubina, A. LZfuzz: A fast Compression-Based Fuzzer for Poorly Documented Protocols; Technical Report; Department of Computer Science, Dartmouth College: Hanover, NH, USA, 2008. [Google Scholar]
- Voyiatzis, A.G.; Katsigiannis, K.; Koubias, S. A Modbus/TCP Fuzzer for testing internetworked industrial systems. In Proceedings of the IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Chen, J.; Diao, W.; Zhao, Q.; Zuo, C.; Lin, Z.; Wang, X.; Lau, W.C.; Sun, M.; Yang, R.; Zhang, K. IoTFuzzer: Discovering Memory Corruptions in IoT Through App-based Fuzzing. In Proceedings of the 25th Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 18–21 February 2018; pp. 1–22. [Google Scholar]
- Zheng, Y.; Davanian, A.; Yin, H.; Song, C.; Zhu, H.; Sun, L. FIRM-AFL: High-throughput greybox fuzzing of IoT firmware via augmented process emulation. In Proceedings of the 28th USENIX Security Symposium (Security), Santa Clara, CA, USA, 14–16 August 2019; pp. 1099–1114. [Google Scholar]
- Hernández Ramos, S.; Villalba, M.T.; Lacuesta, R. MQTT Security: A Novel Fuzzing Approach. Wirel. Commun. Mob. Com. 2018, 2018. [Google Scholar] [CrossRef]
- mqtt_fuzz tool. Available online: https://github.com/F-Secure/mqtt_fuzz (accessed on 29 July 2020).
- Rodríguez-Domínguez, C.; Benghazi, K.; Noguera, M.; Garrido, J.L.; Rodríguez, M.L.; Ruiz-López, T. A Communication model to integrate the Request-Response and the publish-subscribe paradigms into ubiquitous systems. Sensors 2012, 12, 7648–7668. [Google Scholar] [CrossRef] [PubMed]
- Davis, E.G.; Calveras, A.; Demirkol, I. Improving packet delivery performance of publish/subscribe protocols in wireless sensor networks. Sensors 2013, 13, 648–680. [Google Scholar] [CrossRef] [PubMed]
- Akasiadis, C.; Pitsilis, V.; Spyropoulos, C.D. A multi-protocol IoT platform based on open-source frameworks. Sensors 2019, 19, 4217. [Google Scholar] [CrossRef] [PubMed]
- Larmo, A.; Ratilainen, A.; Saarinen, J. Impact of CoAP and MQTT on NB-IoT system performance. Sensors 2019, 19, 7. [Google Scholar] [CrossRef] [PubMed]
- Bormann, C.; Lemay, S.; Tschofenig, H.; Hartke, K.; Silverajan, B.; Raymor, B. CoAP (Constrained Application Protocol) over TCP, TLS, and WebSockets. RFC 8323 2018; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2018. [Google Scholar]
- Houimli, M.; Kahloul, L.; Benaoun, S. Formal specification, verification and evaluation of the MQTT protocol in the Internet of Things. In Proceedings of the 2017 International Conference on Mathematics and Information Technology (ICMIT), Adrar, Algeria, 4–5 December 2017; pp. 214–221. [Google Scholar] [CrossRef]
- Vaccari, I.; Aiello, M.; Cambiaso, E. SlowITe, a novel denial of service attack affecting MQTT. Sensors 2020, 20, 2932. [Google Scholar] [CrossRef] [PubMed]
- Granjal, J.; Silva, J.M.; Lourenço, N. Intrusion detection and prevention in CoAP wireless sensor networks using anomaly detection. Sensors 2018, 18, 2445. [Google Scholar] [CrossRef] [PubMed]
- Serebryany, K.; Bruening, D.; Potapenko, A.; Vyukov, D. AddressSanitizer: A fast address sanity checker. In Proceedings of the USENIX Annual Technical Conference (ATC), Boston, MA, USA, 13–15 June 2012; pp. 309–318. [Google Scholar]



| Fuzzer | Need Spec. | Need Coding | Support Multiparty | Message-aware | Taxonomy |
|---|---|---|---|---|---|
| Boofuzz (Sulley) [26] | Yes | Yes | Yes | Yes | blackbox |
| AFL [3] | No | No | No | No | greybox |
| MOPT [14] | No | No | No | No | greybox |
| AFLNET [15] | Partial | Partial | No | Yes | greybox |
| MultiFuzz (this paper) | No | No | Yes | Yes | greybox |
| Name | Direction of Flow | Description |
|---|---|---|
| CONNECT | Client to server | Connection request |
| CONNACK | Server to client | Connect acknowledgment |
| PUBLISH | Client to server or server to client | Publish message |
| PUBACK | Client to server or server to client | Publish acknowledgment (QoS 1) |
| PUBREC | Client to server or server to client | Publish received (QoS 2 delivery part 1) |
| PUBREL | Client to server or server to client | Publish release (QoS 2 delivery part 2) |
| PUBCOMP | Client to server or server to client | Publish complete (QoS 2 delivery part 3) |
| SUBSCRIBE | Client to server | Subscribe request |
| SUBACK | Server to client | Subscribe acknowledgment |
| UNSUBSCRIBE | Client to server | Unsubscribe request |
| UNSUBACK | Server to client | Unsubscribe acknowledgment |
| PINGREQ | Client to server | PING request |
| PINGRESP | Server to client | PING response |
| DISCONNECT | Client to server or server to client | Disconnect notification |
| AUTH | Client to server or server to client | Authentication exchange |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zeng, Y.; Lin, M.; Guo, S.; Shen, Y.; Cui, T.; Wu, T.; Zheng, Q.; Wang, Q. MultiFuzz: A Coverage-Based Multiparty-Protocol Fuzzer for IoT Publish/Subscribe Protocols. Sensors 2020, 20, 5194. https://doi.org/10.3390/s20185194
Zeng Y, Lin M, Guo S, Shen Y, Cui T, Wu T, Zheng Q, Wang Q. MultiFuzz: A Coverage-Based Multiparty-Protocol Fuzzer for IoT Publish/Subscribe Protocols. Sensors. 2020; 20(18):5194. https://doi.org/10.3390/s20185194
Chicago/Turabian StyleZeng, Yingpei, Mingmin Lin, Shanqing Guo, Yanzhao Shen, Tingting Cui, Ting Wu, Qiuhua Zheng, and Qiuhua Wang. 2020. "MultiFuzz: A Coverage-Based Multiparty-Protocol Fuzzer for IoT Publish/Subscribe Protocols" Sensors 20, no. 18: 5194. https://doi.org/10.3390/s20185194
APA StyleZeng, Y., Lin, M., Guo, S., Shen, Y., Cui, T., Wu, T., Zheng, Q., & Wang, Q. (2020). MultiFuzz: A Coverage-Based Multiparty-Protocol Fuzzer for IoT Publish/Subscribe Protocols. Sensors, 20(18), 5194. https://doi.org/10.3390/s20185194






