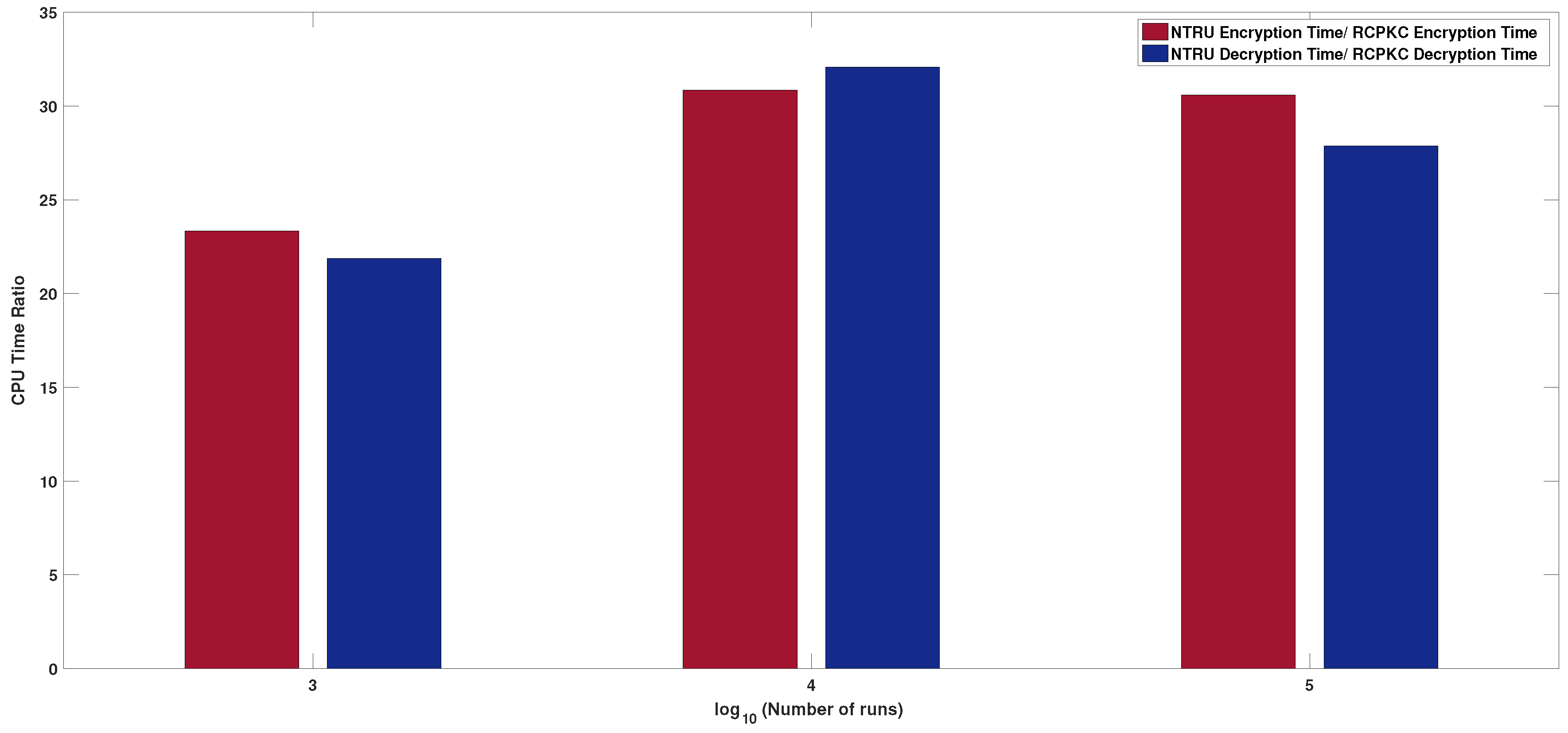1. Introduction
Wireless sensor networks (WSNs) play an important role in the development of the Internet of Things (IoT). WSNs consist of a large number of sensor nodes, battery-supplied devices with a limited memory and computational power microcontroller. WSNs are used widely, e.g., in environmental practices, health, industrial control, military [
1], multimedia networks [
2], and smart grid networks [
3]. WSNs need security and confidentiality since sensitive information is stored, processed, or transferred by sensor nodes [
4]. Therefore, cryptographic schemes efficiently working on limited WSN microcontrollers are demanded [
5]. Furthermore, energy savings is very important for WSNs [
6]. NTRU [
7,
8] is a public key cryptosystem (PKC) standardized as IEEE P1363.1 and is faster than RSA and ECC [
9], and it is applicable to WSNs [
10]. Contrary to RSA and ECC working with big numbers and homomorphic only in one operation, multiplication and addition, respectively, NTRU works with high degree,
N, polynomial rings and is homomorphic with respect to both multiplication and addition [
11]. These features of NTRU allow its use in various applications, such as authentication for smart cards [
12], encryption of user data in smart monitoring systems [
13], securing of SMS [
14], mutual authentication and key agreement for wireless communications [
15], embedded systems including microcontrollers and FPGAs [
16], Internet of Things devices [
17], and NTRU hardware implementation [
18]. The NTRU model expects that the public key is used for encryption only by a public user (sender), whereas the private key is used for decryption by the key’s owner (receiver).
NTRU and its known variants [
7,
8,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31,
32,
33,
34,
35,
36,
37,
38], shown in
Section 2, work with degree
N polynomials. The main problem NTRU faces is that it is susceptible to the lattice basis reduction attack (LBRA) using the Gaussian lattice reduction (GLR) algorithm for two-dimensional lattices and the LLL algorithm for higher dimensions [
39]. The LBRA using LLL algorithm solves the shortest vector problem (SVP) with exponential in
N running time revealing the secret key because the private keys are selected as polynomials with small coefficients for the decryption correctness [
40]. To overcome the problem of susceptibility, NTRU uses large
N resulting in high computational complexity [
11,
41]. Therefore, NTRU variants, shown in
Section 2, try minimizing NTRU computational complexity by extending the coefficients of the polynomials used or using matrices of polynomials that allow preserving the security level while decreasing the polynomial degree. The extreme case is a polynomial of zero degree, that is integers modulo
, as used in the congruential public key cryptosystem (CPKC), but CPKC with the NTRU encryption/encryption mechanism is insecure against LBRA by GLR (crackable in about 10 iterations) ([
26], pp. 373–376, 451). Therefore, the CPKC is considered as a toy model of NTRU because “it provides the lowest dimensional introduction to the NTRU public key cryptosystem” [
26] (p. 374). The insecurity of CPKC stems from the choice of the private keys used as small numbers to provide decryption correctness. If CPKC could be made resistant to GLR attack, it would be the best possible choice for the NTRU modifications. Therefore, we propose a CPKC modification, random CPKC (RCPKC) [
42] (we call it here RCPKC.1).
In this paper, an enhanced RCPKC is proposed by specifying a range from which the random numbers shall be selected based on short vectors returned by GLR attack on it. It provides correct decryption for valid users and incorrect decryption for an attacker using GLR. GLR cannot find its private key because it solves SVP returning the shortest in a lattice vector, whereas our private key is in the safe region (above Minkowski’s boundary (
27)–(
30) for the shortest vector norm of a lattice). On the other hand, the short vectors returned by GLR cannot be used for correct decryption due to our choice of the random numbers. RCPKC is a cryptosystem more secure than NTRU because LBRA is currently considered as one of the most effective attacks against NTRU, and also, a number of other attacks on NTRU are not applicable to RCPKC, whereas RCPKC’s resistance to other known attacks on NTRU is similar to that of NTRU. RCPKC is about 27 times faster in encryption and decryption than NTRU. Simplicity, speed, and security make RCPKC a good candidate cryptosystem for WSNs. The paper’s contribution can be summarized as follows:
RCPKC, an NTRU-like cipher variant resistant to lattice based attacks, is proposed with enhanced security compared to RCPKC.1 [
42].
The hardness of the RCPKC one-way (OW) function is proven.
RCPKC symmetric encryption padding (RAEP) is IND-CCA2 secure is proven under the assumption of the hardness of inverting an associated one-way function.
RCPKC’s performance is justified through implementation and comparison with the state-of-the-art ciphers.
RCPKC’s better applicability than NTRU to WSNs is proven.
The rest of the paper is organized as follows. In
Section 2, known NTRU variants are presented. In
Section 3, an overview of NTRU, NTRU AEP (NAEP), the IND-CCA2 security of NAEP, and CPKC is given, and formulas for CPU power consumption calculation are introduced. LBRA by GLR on CPKC is described, and Minkowski’s second theorem is presented in
Section 4, used to define a region where GLR attack against the CPKC private key/message fails. In
Section 5, RCPKC is presented. In
Section 6, the RCPKC security comparison versus NTRU is conducted. In
Section 7, the RCPKC OW function and RCPKC asymmetric encryption padding (RAEP) IND-CCA2 security are considered. In
Section 8, the RCPKC performance comparison versus NTRU and its variants is presented, and the RCPKC versus NTRU power consumption is studied.
Section 9 concludes the paper.
2. Review of Known NTRU Variants
Many variants of NTRU have been proposed and studied recently, targeting further decreasing its computational complexity. All these variants work with polynomials and mainly differ in the choice of their coefficients, the ring defining polynomial, or the polynomials used as the entries of such structures as matrices. The NTRU variants’ overview follows.
NTRU variants differing in the choice of their coefficients. In [
27], an NTRU variant, ETRU, was proposed working with polynomials over Eisenstein integer coefficients and was faster than NTRU in encryption/decryption by 1.45/1.72 times. Karbasi and Atani [
28] modified ETRU, called ILTRU [
28], so that it works with irreducible cyclotomic polynomial over Eisenstein integer coefficients. An NTRU variant, BITRU, working with polynomials over so-called binary numbers, usually known as complex numbers, was proposed in [
20]. An NTRU variant, QTRU, working with polynomials over hyper-complex four-component numbers, quaternions, was proposed in [
30]. Furthermore, Bagheri and colleagues proposed an NTRU variant, BQTRU, working over quaternions, but with bivariate polynomials, seven times faster than NTRU in encryption [
21]. A variant of NTRU working with polynomials over eight-component hyper-complex numbers, octonions, called OTRU, was proposed in [
29]. In [
34], an NTRU variant, HXDTRU, was proposed working with polynomials over 16-component hyper-complex numbers, hexadecnions, also known as sedenions [
19]. Furthermore, a variant of NTRU working with polynomials over 16-component hyper-complex numbers, sedenions, was proposed in [
31]. A variant of NTRU, called CTRU, working with polynomials, the coefficients of which are also polynomials in one variable over a binary field, was proposed in [
24]. Furthermore, a variant of NTRU working with polynomials, the coefficients of which are polynomials in one variable over a rational field, called BTRU, was proposed in [
32].
NTRU variants working with different rings. An NTRU variant that works with polynomials with prime cyclotomic rings was proposed in [
35]. A variant of NTRU working with non-invertible polynomials was proposed in [
22].
NTRU variants working with polynomials inside more complicated structures. An NTRU variant working with square matrices of polynomials was proposed in [
23] and was shown to be 2.5 times better than NTRU encryption and decryption time. An NTRU variant, called NNRU, working with polynomials also being entries of square matrices forming a non-commutative ring, was proposed in [
33]. Apart from the polynomial variants, an NTRU-like cipher over the ring of integers, called ITRU, was proposed in [
25] without referencing CPKC [
26]. In ITRU [
25],
Table 1, p. 34, the NTRU model specified above was given, but a model for the proposed ITRU was not defined. Its Algorithm 1, [
25], p. 35, describes the key generation, and hence, it shall be made by the key owner (receiver). On the other hand, in
Section 4. A, Parameter selection, [
25], p. 37, the most important parameter,
q, was selected by the sender (which encrypts a message using the public key,
423,642, and random value,
, in [
25], (19), p. 37 with the help of the private keys,
, which contradicts the NTRU model: the secret key is known to only the key owner that uses the private key only for decryption, whereas the public key is used for encryption by the public user only.
Thus, the NTRU variants try minimizing NTRU’s computational complexity by extending coefficients of the polynomials used or using matrices of polynomials that allow preserving the security level while decreasing the polynomial degree because operations with high-degree polynomials are time-consuming. However, these variants are still susceptible to LBRA using LLL, but with less complexity than NTRU has. Furthermore, ITRU can be used by the key owner only for encryption and decryption messages, but cannot be used by a public user knowing the public key only; hence, it is not compatible with the NTRU model of use.
6. RCPKC Security Analysis
In this section, attacks on NTRU are considered (brute force (on the key and message), meet-in-the-middle (MITM) in
Section 6.1, lattice basis reduction in
Section 6.4, hybrid lattice basis reduction and MITM [
52] in
Section 6.2, multiple transmission (MTA) [
11] in
Section 6.3, and also, the most recent, chosen ciphertext [
53,
54,
55,
56], in
Section 6.5), and we try applying them to RCPKC. Herein, the NTRU parameters used, EES401EP1 [
41], of the security level,
bits:
In order to meet the same security level, the RCPKC settings satisfying (
38) are:
The key space cardinality (defined in
Section 6.1 for the parameters (
53) and (
54)) is greater than or equal to
for
k = 112 to avoid the MITM attack explained in
Section 6.1.
6.1. Brute Force and MITM Attacks
An attacker can recover the NTRU private key by trying all possible values of
g and testing whether
has small coefficients (the product corresponds to
g according to (
10)). On the other hand, an attacker can try all possible values of
g and test whether
(corresponding to
f by virtue of (
10)) has small coefficients. Equations (
55) and (
56) show the search space cardinalities for
g and
f for the security level,
k = 112 (taking into account the MITM attack explained later in this section). The search space cardinality for
f is computed as follows (see [
53] (Section 7)):
Similarly, for
g:
it is perceived the search space cardinality for
f is less than that for
g, so the best strategy for an attacker is to search for
f values.
An attacker can reduce the search space cardinality from
to
[
57] using MITM by splitting the private key
f (which is a polynomial of degree
) into two polynomials,
, where
is a polynomial of degree at most
and polynomial
contains terms of degree between
and
, and then trying matches:
Hence, in order to meet the
k = 112 security level, the NTRU parameters must be chosen to meet the
k = 224 security level, as it is already made in (
53). For RCPKC, the secret value,
g, is selected from the interval
(see (
33)); hence, the search space cardinality for
g to meet the
-bit security level against the brute force attack shall satisfy:
The secret value,
f, is selected from the interval
(see (
36)); hence, the search space cardinality for
f to meet the
-bit security level against the brute force attack shall satisfy:
For the parameters (
54),
, while
. In order to provide the security level for
, the parameters (
54) are chosen to meet the twice greater security level of
to counter the MITM attack, considered below, which reduces the brute force attack effort by the square root. Since
the best strategy for an attacker is to search for
g values. Similar to NTRU, the MITM attack can be applied to the RCPKC private key component,
g. Since
is the bit length of
g, then
, and then,
and
, each of a bit length equal to
, can be enumerated with the resulting search space cardinality
trying to find matching:
Thus, the RCPKC parameters (
54) provide the security level
k = 112 against the brute force attack with MITM. Now, let us consider the brute force attack on the message.
An attacker can compromise an NTRU message by trying all possible values of
r and testing whether
has small coefficients. Similarly, the attacker can compromise the RCPKC message by trying all possible values of
r and testing if
by virtue of (
33).
The RCPKC message search space is defined by the interval
(see (
33)); hence, the search space cardinality for
m to meet the
-bit security level against the brute force attack shall satisfy:
while the search space of
r is defined by (
46), (
50) and (
51). Hence, the search space cardinality for
r to meet the
-bit security level against the brute force attack shall satisfy:
Table 1 shows the
and
values to meet different
-bit security levels’ condition (
60) (see Rows 1 and 2) and the width of the range for
r (Row 7) with
f and
g specified in Rows 3 and 4, respectively. It proves that the method can be practically used.
6.2. A Hybrid Lattice Basis Reduction and MITM Attack
The attack [
52] on the NTRU secret key combines the LBRA and MITM strategies. The hybrid attack, first, splits the original lattice of order
,
, into three subparts, only one of which is further reduced, whereas the vectors from the other parts are just enumerated, thus combining the concepts of the LBRA and MITM attacks. The hybrid attack is not applicable to RCPKC since:
- -
The RCPKC lattice is two-dimensional and cannot be split into the three subparts;
- -
RCPKC uses a large norm secret
vector (see (
33) and (
36)) that cannot be found by LBRA looking for an SV, and the SV cannot be used for correct decryption (see (
48)).
6.3. Multiple Transmission Attack
MTA reveals a large part of an NTRU message by sending
n times one and the same message,
m, using the same public key,
h, but different random values,
. For NTRU encryption (
13) (see
Section 3.1):
for
An adversary computes:
thereby recovering
, and from these relations, many coefficients of
may be revealed. Knowledge of
allows disclosing the message,
m. RCPKC is not susceptible to MTA because no special structure is assumed for
contrary to the case of NTRU.
6.4. Lattice Basis Reduction Attacks
The NTRU lattice basis,
, associated with public key
h defined in (
1) is:
where
are the coefficients of the polynomial
h. For convenience, matrix
is abbreviated as:
The NTRU private key recovery problem can be formulated as the SVP in
-dimensional lattice,
. Actually, if a polynomial,
b, of degree
with integer coefficients satisfying:
exists, then:
Therefore, the vector
is in the lattice
. Vector
or its rotation (rotation of a polynomial,
f, by
i steps is
for an integer
i) can be found if it is the shortest vector in
. The lattice reduction algorithm LLL [
51] finds the shortest vector in
in time exponential in
N. According to [
40], LLL takes 1.05
MIPS (million instructions per second)-years to find the shortest vector or its rotation for
N = 400 (as in (
53)) that most likely is the NTRU private key part,
.
Contrary to NTRU, RCPKC is resistant to LBRA since the GLR attack fails for it (see
Section 5). LBRA is one of the most used and effective techniques in attacking an NTRU private key (e.g., it is used in the hybrid lattice attack, the most efficient on practical NTRU parameters [
58]; see
Section 6.2), but it is not applicable to RCPKC.
6.5. Chosen Ciphertext Attack
Three chosen ciphertext attacks (CCA) on NTRU are known. The first key recovering CCA described in [
54] uses a ciphertext of a special shape, which can be countered by message padding [
53]. Standardized parameters [
53] allow decryption failure, i.e., a ciphertext could fail to be decrypted correctly by NTRU. In [
55], a CCA was presented where an attacker collects a large number of decryption failures; see the NTRU correction decryption condition (
5) in
Section 3.1. Another CCA was presented in [
56], which is more efficient than [
55], but still depends on decryption failures. RCPKC works on non-structured integers, and the parameters, set in
Section 5, guarantee correct decryption. Thus, neither of the CCAs described above are applicable to RCPKC.
7. RCPKC Asymmetric Encryption Padding and its IND-CCA2 Security
In this section, we prove the security of the RCPKC one-way function based on the discussions of the security of the NTRU one-way function in [
8], define RCPKC asymmetric encryption padding (RAEP), and prove its IND-CCA2 security as a particular case of NAEP. According to
Section 5.2 and
Section 5.3, RCPKC defines the following four sets:
: private key space, an interval from which a private key, f, is selected;
: private key space, an interval from which a private key, g, is selected;
: RCPKC plaintext space, an interval from which a plaintext, m, is selected;
: RCPKC random value space.
The RCPKC encryption primitive is specified by the parameter set,
. The one-way function underlying RCPKC is:
Definition 3. RCPKC-OW problem: For a parameter set, , we denote by the success probability of a PPT adversary, , for finding a pre-image of , Assumption 2. RCPKC-OW assumption: For every PPT adversary, , solving the RCPKC-OW problem, there exists a negligible function, , such that for sufficiently large k, we have: An adversary
can compromise
by picking
, substituting it in
, and checking, if the result is in
. Thus,
is:
Since
by definition (
38),
decreases exponentially in
, and Assumption 1 holds. Similarly, the attacker can try the following methods with an exponentially decreasing success probability:
The adversary, , chooses randomly a pair and checks if .
The adversary, , picks , substitutes it in , and checks whether the result is in .
The adversary, , chooses randomly a pair , if possible, calculates , decrypts e to , and checks if .
Furthermore, the adversary can apply the GLR attack to get . However, by construction, RCPKC is immune to that attack, and hence, the success probability is zero.
Therefore, Assumption 1 is true for all the above attacks.
RCPKC encryption (
13) differs from NTRU encryption (
2) just by setting
. The conclusion of [
7] on NAEP IND-CCA2 security is also true for asymmetric encryption padding, RAEP. However, NAEP cannot be used as is for
because it utilizes specific true polynomial functions center() and compress(). Since the decryption correctness condition (
15) holds for RCPKC due to the parameter choice, the center() function is not used in RCPKC and RAEP. The function compress() as in NAEP shall map its input,
, to a binary string,
, of the padded message size. In NAEP, it is done in two steps:
. In RAEP, both transforms are done by one hash function,
. Algorithms 3 and 4 show RAEP encryption and decryption, respectively.
| Algorithm 3: RAEP encryption. |
![Sensors 20 04632 i003 Sensors 20 04632 i003]() |
| Algorithm 4: RAEP decryption. |
![Sensors 20 04632 i004 Sensors 20 04632 i004]() |
9. Conclusions
In this paper, RCPKC is proposed, a secure and effective congruential, modulo
q, public-key cryptosystem using big numbers. It uses the same encryption/decryption mechanism as NTRU does, but works with numbers. Contrary to NTRU, RCPKC is resistant to LBRA because its private key components,
f and
g, are chosen big with respect to
to form a two-component vector with the norm exceeding Minkowski’s boundary (
27)–(
30) for the shortest vector in a two-dimensional lattice and meeting (
31). Hence, LBRA by the GLR algorithm returning the shortest vector in a two-dimensional lattice fails at finding the large norm private key vector,
.
In spite of the big numbers,
f and
r, meeting (
36) used in RCPKC, it guarantees that the decryption correctness condition (
15) holds (see (
39)) due to the use of Conditions (
33), (
36), (
38), (
46) and (
50) instead of Conditions (
7), (
11), and (
12), used in the original insecure CPKC (see
Section 3.3,
Section 3.3.1,
Section 3.3.2) considered in [
26]. It was found that the insecurity of the original CPKC stems from the use of Conditions (
7), (
11) and (
12), defining smaller than
numbers
f,
g,
m,
r meeting Minkowski’s boundary (
27) and the decryption correctness condition (
15). RCPKC is resistant to the LBRA by GLR attack due to the special choice of the range for the random value,
r, used in the encryption (
13) that guarantees correctness condition (
15) violation for the short vectors returned by GLR, but holding for the original private key,
.
Section 6 shows also that the security of RCPKC with respect to other known attacks on NTRU is not less than that of NTRU, which allows us to conclude that RCPKC is more secure than NTRU.
Section 7 proves the IND-CCA2 security of RCPKC asymmetric encryption padding (RAEP).
RCPKC uses numbers, i.e., minimal possible, degree zero, polynomials, which makes it about 27 times more effective in encryption and decryption than NTRU and more than three times more effective in encryption with respect to the fastest most recently published NTRU variant, BQTRU [
21], as the experiments show (see
Table 3). Compared to NTRU, RCPKC reduces the energy consumption at least 27 times, which allows increasing the life-time of unattended WSNs by more than 27 times.
As a future work, the proposed RCPKC will be applied to telemedicine to secure the data collected by medical sensors and cameras.