Low-Rate DoS Attacks Detection Based on MAF-ADM
Abstract
1. Introduction
2. Related Researches
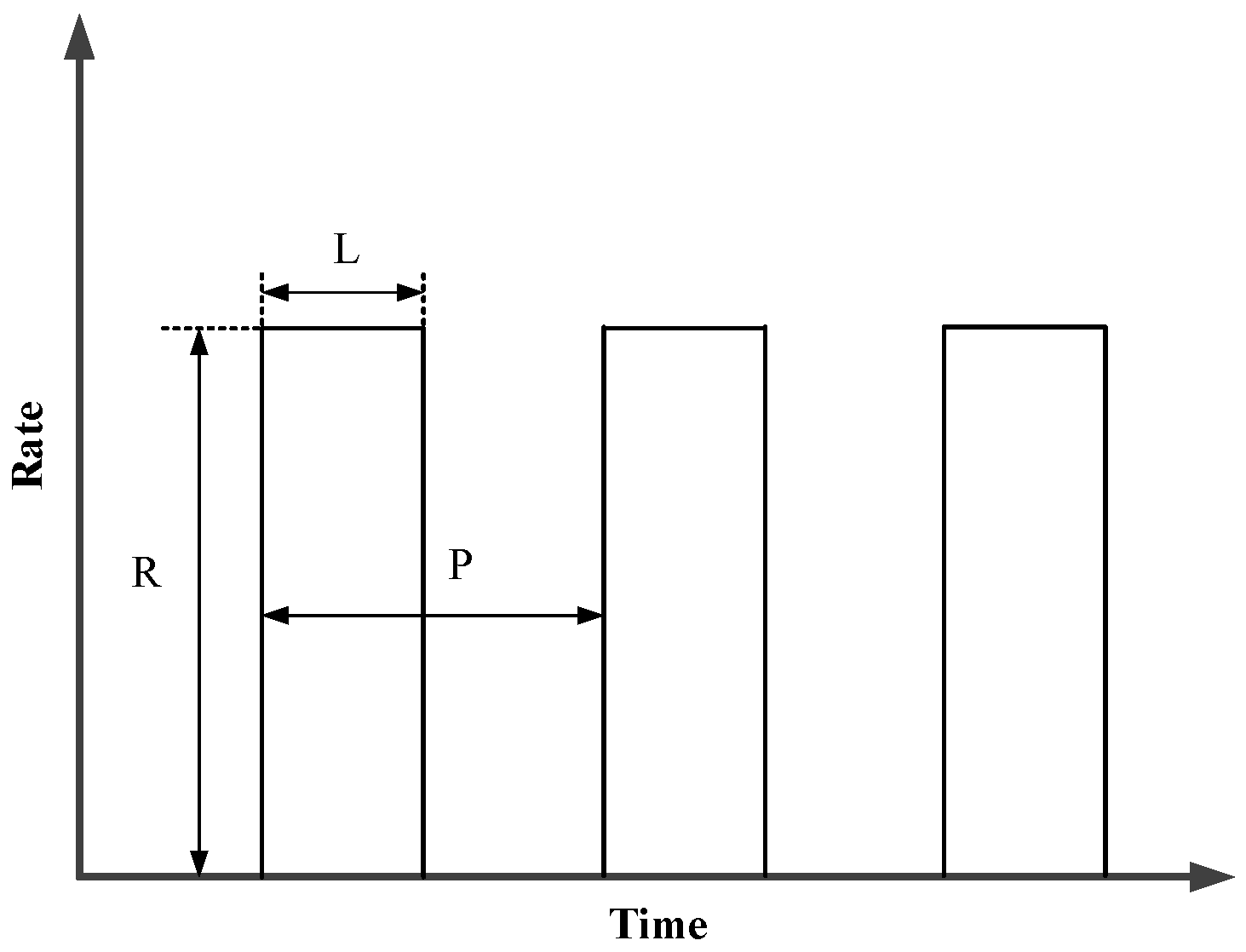
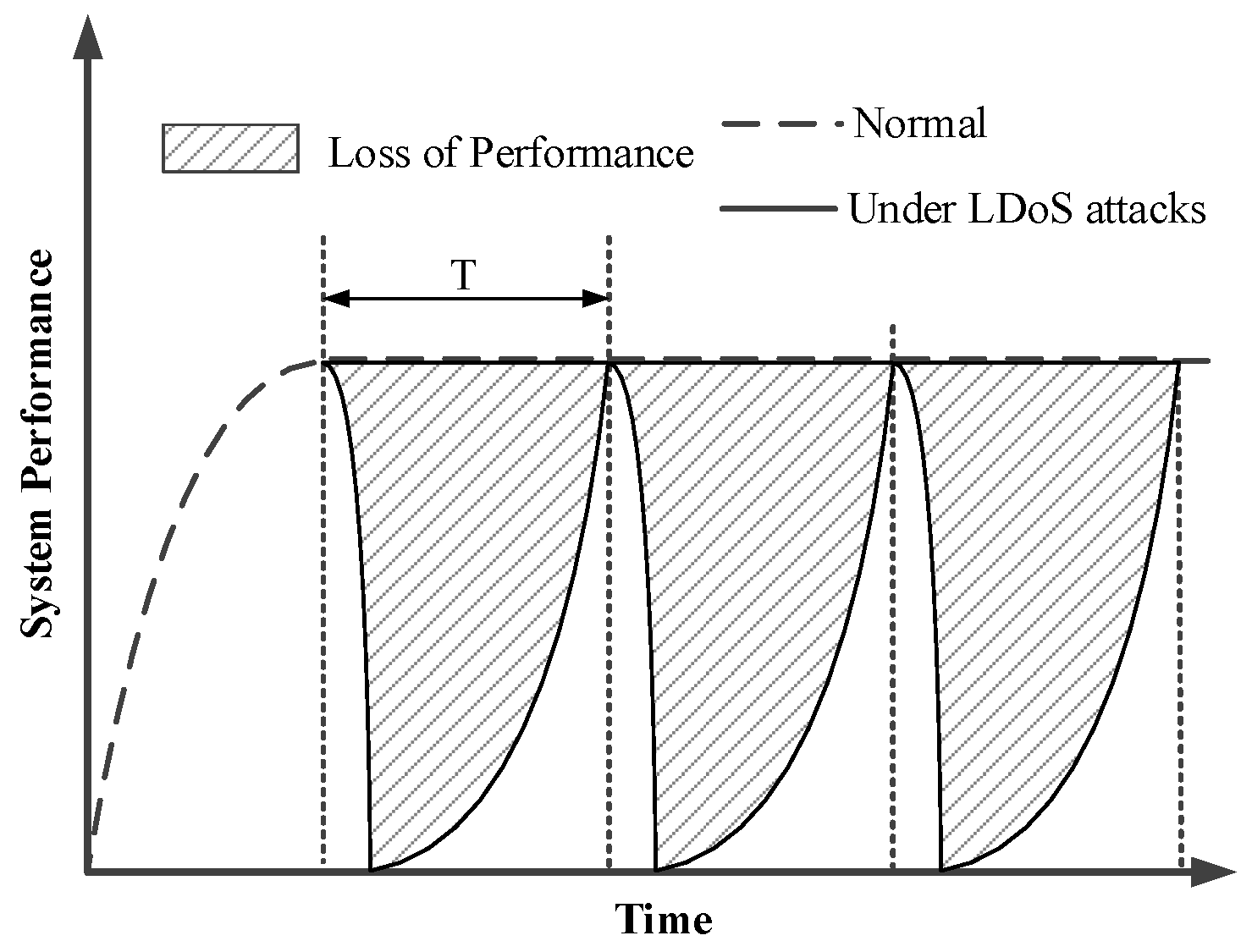
2.1. Characteristics of LDoS Attacks
- RTO-based LDoS attacks: A TCP sender normally sets retransmission timeout () for each packet. As shown in Figure 2a [23], when the network link is in normal state, we can assume that of the sender is the minimum value (usually set to 1 s in order to achieve optimal throughput of the network). But when an attack pulse is arrived, the TCP gets into the timeout retransmission state. During the attack interval, the sender begins to get into the slow start and successfully retransmits. For some data packets, the can also return to the minimum value by Formula (1) [24]. G is the clock granularity. and represent round-trip time and the variation of round-trip time respectively. The above process repeats so that the quality of network services is reduced.
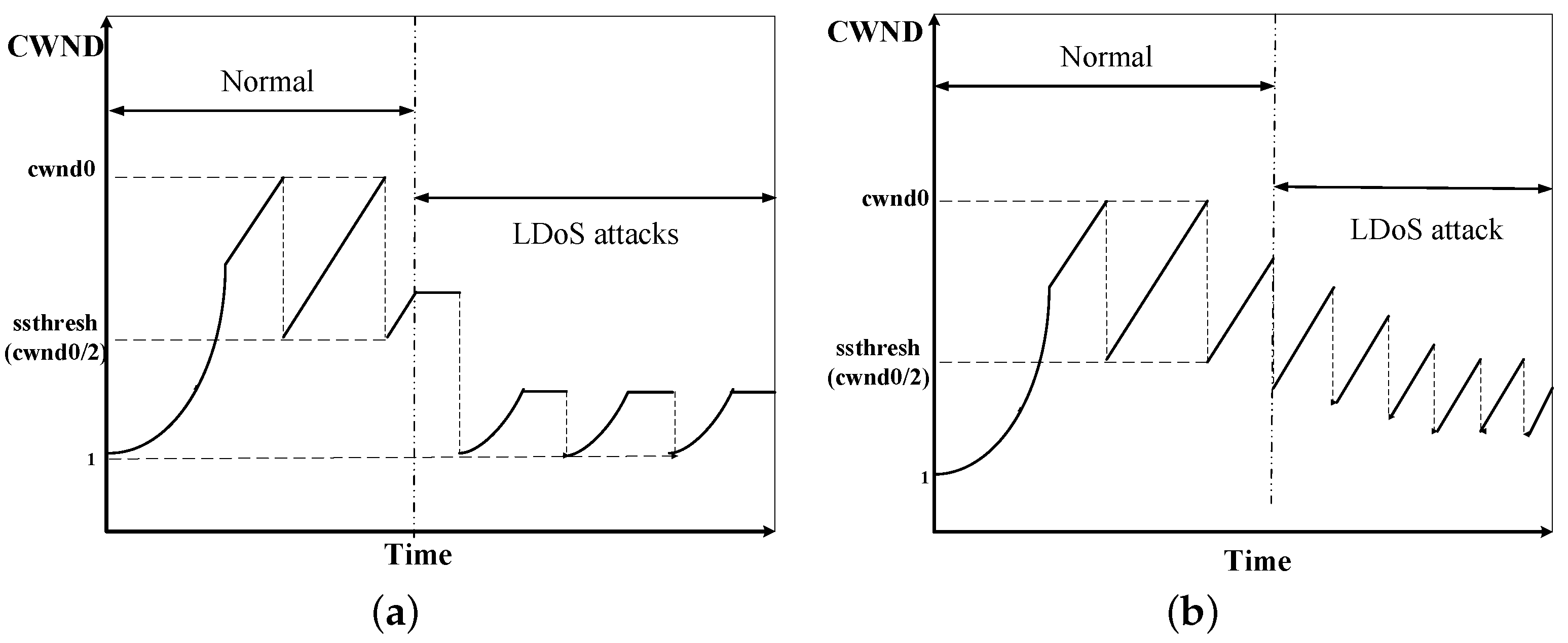
- AIMD-based LDoS attacks: The additive increase and multiplicative decrease (AIMD) mechanism is to resend the packet immediately after the sender receives three duplicate acknowledge characters (ACKs), which reduces its congestion window (CWND) through multiplicative decrease (MD) algorithm and increases the CWND according to additive increase (AI) algorithm. The link is always in the AIMD state and does not enter the timeout retransmission and slow start under the AIMD-based LDoS attacks as Figure 2b [25] presented. But its CWND is decreasing so that the system performance is gradually reduced. Finally the CWND is reduced to a limit and the system performance is the worst, which cannot be recovered by itself.
2.2. Detection of LDoS Attacks
- Time domain based detection algorithmMeng et al. [27] established a feedback control model to describe the process of random early detection(RED) congestion control, by which the congestion window and router queue behaviours were analyzed together. Then a queue distribution model consisted of the instantaneous queue and the average queue was proposed to extract the attack feature. After that, a simple distance-based approach and an adaptive threshold algorithm were combined to detect every LDoS attack burst. The experimental results of NS2 and testbed proved that LDoS attack bursts can almost be detected completely and this method was especially robust to legitimate short bursts.Wu et al. [28] proposed a detection algorithm based on the multifractal characteristics of network traffic. It was proved that the multifractal characteristics of network traffic are different between the states of normal and LDoS attacks by using MF-DFA algorithm. Then the wavelet point-by-point estimation algorithm was used to calculate the exponent to determine when the attack begins and ends. The NS2 results showed that the approach could achieve the detection probability of 92% and false positive rate of 9%.Guo et al. [29] presented a situation aware method based on multi-feature adaptive fusion to detect LDoS attacks in the border gateway protocol (BGP) routing system. The statistical characteristics of BGP routing information such as frequency of announce messages, frequency of withdraw messages and average autonomous systems (AS) path length were selected as representative of security state of the system. Each of the above features was modeled by reverse cloud generation algorithm, and then the dynamic weights were used to fuse the submodel. Experiment results showed that this method can effectively detect not only control plane attacks and but also data plane attacks (BGP-LDoS).Tang et al. [30] applied the two steps cluster to analyze network traffic on a large time scale. According to the characteristics of TCP traffic was abnormal when the LDoS attack occured, the abnormal cluster was further detected by using the concept of data slice from a small time. Experimental results on NS2 and public datasets Lawrence Berkeley National Laboratory (LBNL) and Measurement and Analysis on the WIDE Internet (WIDE2018) showed that LDoS attacks could be effectively detected.
- Frequency domain based detection algorithmNeha et al. [2] proposed an algorithm for detecting and filtering LDoS attack streams in the frequency domain. This method based on power spectral density was used to monitor the aggregated flow in the cloud network in real time. The method could significantly reduce the possibility of attack in a real cloud environment based on OpenStack.Chen et al. [23] combined power spectral density to propose two new information features for detecting LDoS attacks, which named Fourier power spectrum entropy and wavelet power spectrum entropy. Based on these two information features, a Robust-RED queue management algorithm based on power spectral density was proposed to filter the LDoS attack streams. The algorithm was verified on the NS3 simulation experiment platform, which could indeed resist different LDoS attacks.Wu et al. [20] also proposed a method based on frequency spectral analysis for detecting and filtering LDoS attack streams. The TCP streams and LDoS attack streams were transformed from time domain to frequency domain and obtained the round-trip time according to the frequency domain search algorithm. It was found that the magnitude of energy of TCP stream is mainly concentrated in the points of n/RTT. According to this feature, an infinite impulse response filtering algorithm was proposed, which can filter LDoS attack flows with as little impact as possible on legitimate TCP flows.Wu et al. [31] applied Kalman filter to detect LDoS attacks. By analyzing the characteristics of victim network traffic at the beginning of LDoS attacks, the error between one step prediction and the optimal estimation was used as the basis for detection.
3. Time-Frequency Joint Analysis Based Detection Metrics
3.1. STFT Analysis of Network Traffic
3.2. Time-Frequency Joint Distribution Based Detection Metrics
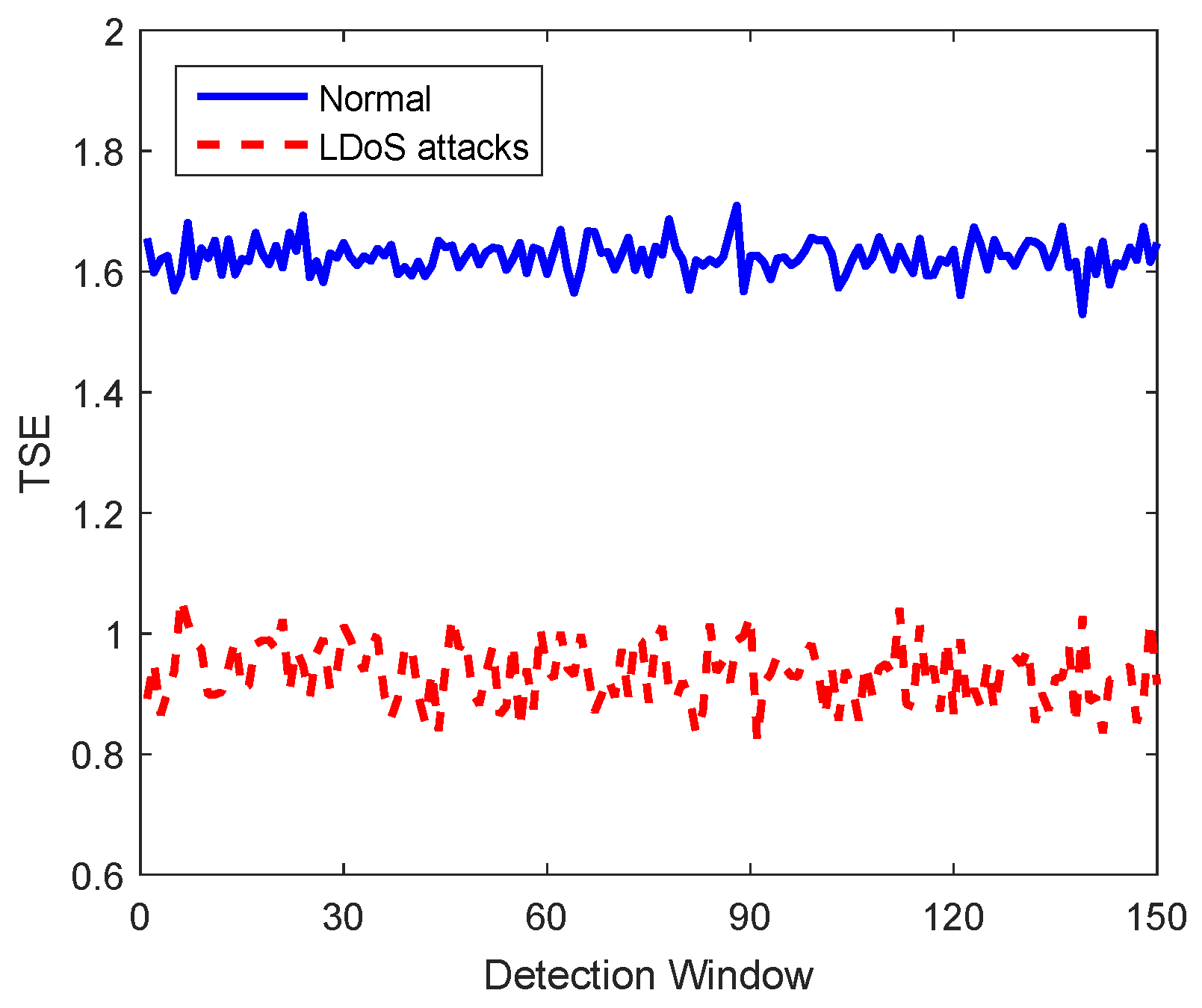
3.2.1. Total Signal Energy
3.2.2. Segmentation Frequency Ratio
3.2.3. Normalized Variance of Segmentation Frequency
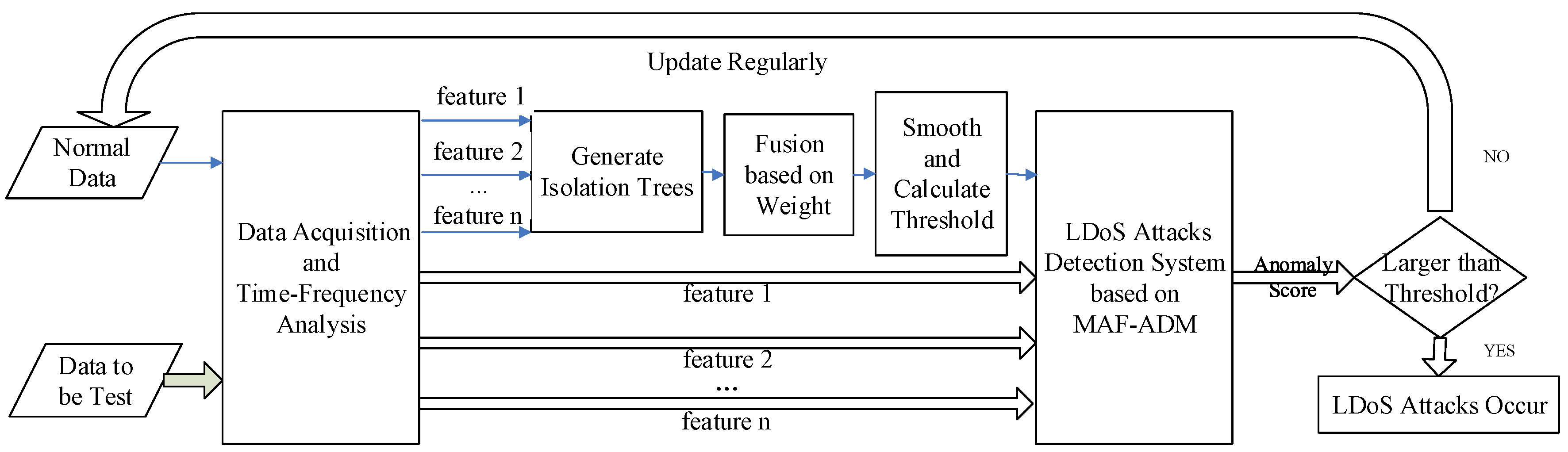
4. LDoS Attacks Detection Method
4.1. Generate Isolation Trees
- The isolation tree reaches a defined height;
- There is only one sample on the node;
- Features of all the nodes are the same.
4.2. Linear Weighted Fusion
4.3. Discrimination of LDoS Attacks
- When , , that means all samples in the data set do not contain obvious LDoS attacks;
- When , , that means the sample includes LDoS attacks;
- When , , that means the sample is normal.
5. Experiments and Results Analysis
5.1. Experiments on NS2
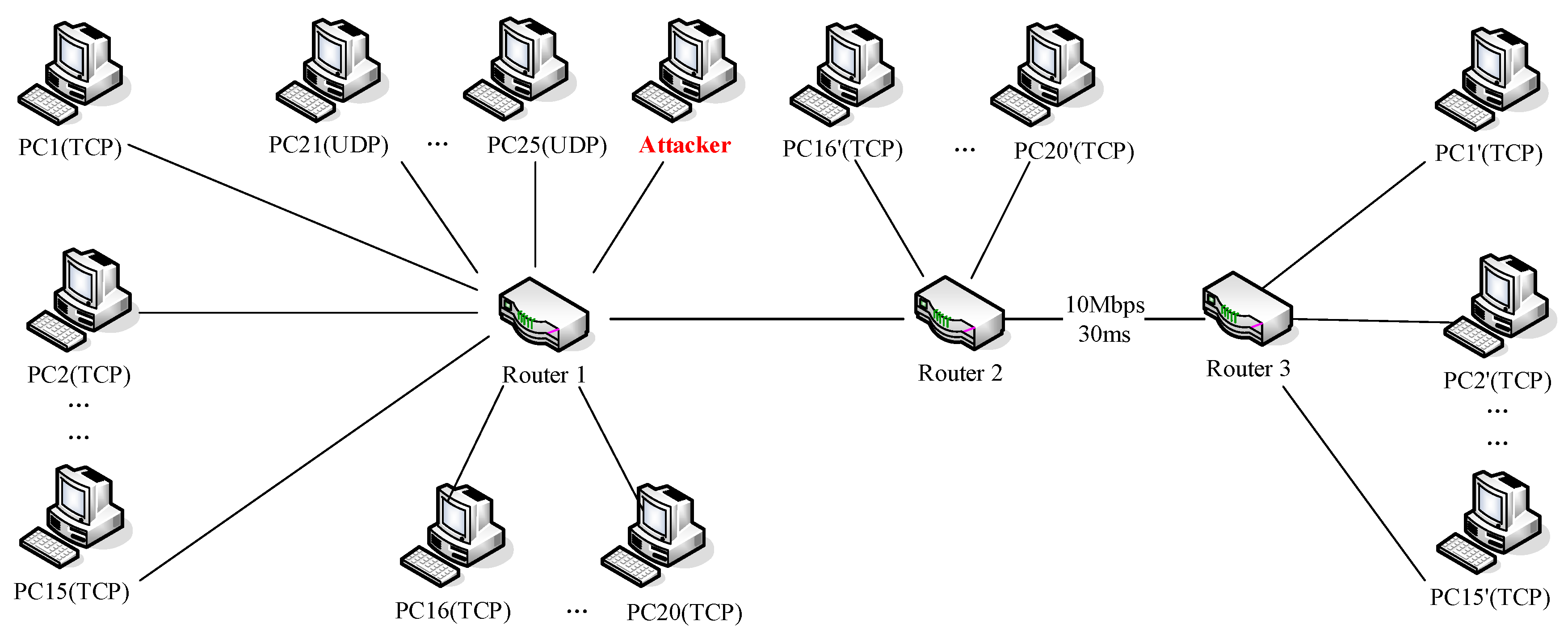
5.1.1. The Experimental Environment
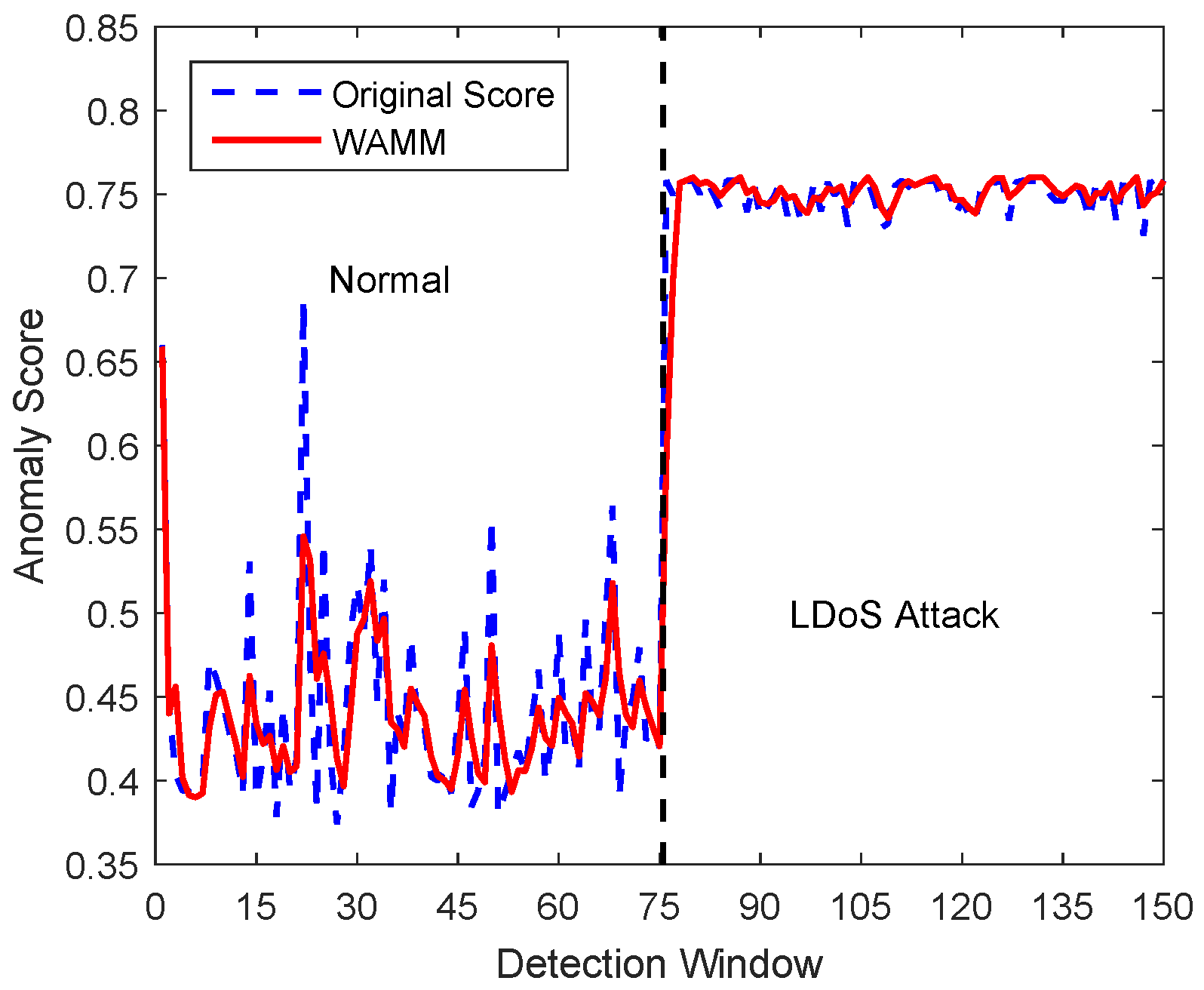
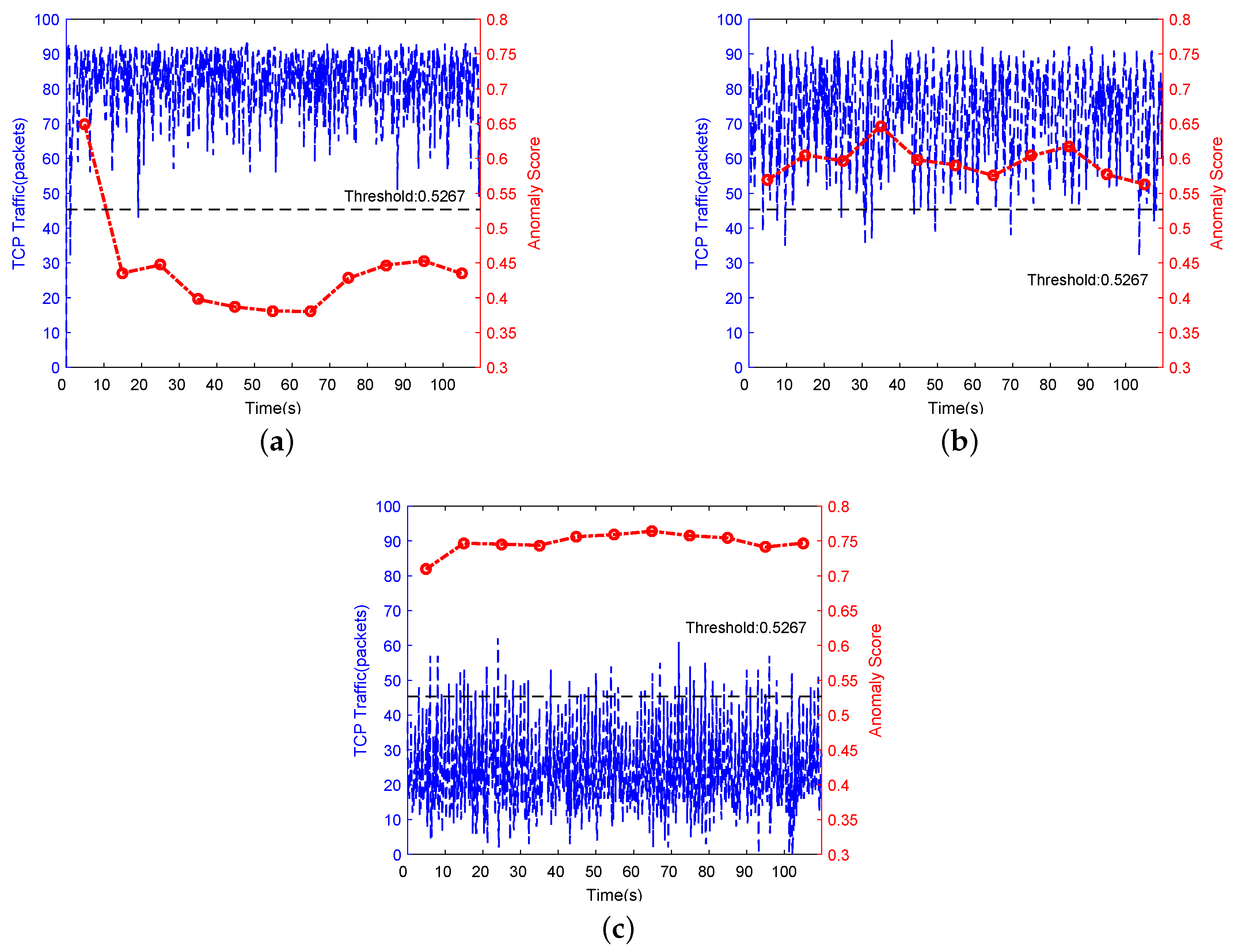
5.1.2. Performance of LDoS Attacks Detection
5.2. Experiments on Testbed
5.2.1. Testbed Experimental Environment
5.2.2. Performance of LDoS Attacks Detection
5.3. Experiments on Public Datasets LBNL and WIDE2018
5.4. Comparison with Other LDoS Methods
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Jhaveri, R.H.; Patel, S.J.; Jinwala, D. DoS Attacks in Mobile Ad Hoc Networks: A Survey. In Proceedings of the Second International Conference on Advanced Computing & Communication Technologies, Rohtak, Haryana, India, 7–8 January 2012. [Google Scholar] [CrossRef]
- Neha, A.; Shashikala, T. Low Rate Cloud DDoS Attack Defense Method Based on Power Spectral Density Analysis. Inf. Process. Lett. 2018, 138, 44–50. [Google Scholar] [CrossRef]
- Sahoo, K.S.; Puthal, D.; Tiwary, M.; Rodrigues, J.J.; Sahoo, B.; Dash, R. An early detection of low rate DDoS attack to SDN based data center networks using information distance metrics. Future Gener. Comput. Syst. 2018, 89, 685–697. [Google Scholar] [CrossRef]
- Cao, J.; Li, Q.; Xie, R.; Sun, K.; Gu, G.; Xu, M.; Yang, Y. The CrossPath Attack: Disrupting the SDN Control Channel via Shared Links. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), USENIX, Santa Clara, CA, USA, 14–16 August 2019; Association: Santa Clara, CA, USA, 2019; pp. 19–36. [Google Scholar]
- De Almeida, M.P.; Júnior, D.S.; Timóteo, R.; Villalba, G.; Javier, L.; Tai-Hoon, K. New DoS Defense Method Based on Strong Designated Verifier Signatures. Sensors 2018, 18, 2813. [Google Scholar] [CrossRef]
- Gao, J.; Chai, S.; Zhang, B.; Xia, Y. Research about DoS Attack against ICPS. Sensors 2019, 19, 1542. [Google Scholar] [CrossRef]
- Chen, H.; Meng, C.; Shan, Z.; Fu, Z.; Bhargava, B.K. A Novel Low-Rate Denial of Service Attack Detection Approach in ZigBee Wireless Sensor Network by Combining Hilbert-Huang Transformation and Trust Evaluation. IEEE Access 2019, 7, 2169–3536. [Google Scholar] [CrossRef]
- Renuka, K.; Kumar, S.; Kumari, S.; Chen, C.M. Cryptanalysis and Improvement of a Privacy-Preserving Three-Factor Authentication Protocol for Wireless Sensor Networks. Sensors 2019, 19, 4625. [Google Scholar] [CrossRef]
- Afianti, F.; Wirawan, I.; Suryani, T. Dynamic Cipher Puzzle for Efficient Broadcast Authentication in Wireless Sensor Networks. Sensors 2018, 18, 4021. [Google Scholar] [CrossRef] [PubMed]
- Cambiaso, E.; Chiola, G.; Aiello, M. Introducing the SlowDrop Attack. Comput. Netw. 2019, 150, 234–249. [Google Scholar] [CrossRef]
- Thomas, J.D.C. Efficient DDoS flood attack detection using dynamic thresholding on flow-based network traffic. Comput. Secur. 2019, 284–295. [Google Scholar] [CrossRef]
- Yue, M.; Wu, Z.; Lei, J. Research on the Aggregation and Synchronization of LDDoS Attack Based on Euclidean Distance. J. Softw. 2014, 9, 1854–1861. [Google Scholar] [CrossRef]
- Paschos, G.S.; Tassiulas, L. Sustainability of Service Provisioning Systems Under Stealth DoS Attacks. IEEE Trans. Control Netw. Syst. 2017, 4, 749–760. [Google Scholar] [CrossRef]
- Marnerides, A.K.; Pezaros, D.P.; Kim, H.C.; Hutchison, D. Internet traffic classification using energy time-frequency distributions. In Proceedings of the 2013 IEEE International Conference on Communications, Budapest, Hungary, 9–13 June 2013; pp. 2513–2518. [Google Scholar] [CrossRef]
- Stimsek, M. A new metric for flow-level filtering of low-rate DDoS attacks. Secur. Commun. Netw. 2016, 8, 3815–3825. [Google Scholar] [CrossRef]
- Wu, Z.; Pan, Q.; Yue, M.; Liu, L. Sequence Alignment Detection of TCP-targeted Synchronous Low-rate DoS Attacks. Comput. Netw. 2019, 152, 64–77. [Google Scholar] [CrossRef]
- Stimsek, M.; Senturk, A. Fast and lightweight detection and filtering method for low-rate TCP targeted distributed denial of service (LDDoS) attacks. Int. J. Commun. Syst. 2018. [Google Scholar] [CrossRef]
- Huang, C.; Yi, P.; Zou, F.; Yao, Y.; Wang, W.; Zhu, T. CCID: Cross-Correlation Identity Distinction Method for Detecting Shrew DDoS. Wirel. Commun. Mob. Comput. 2019, 2019, 6705347. [Google Scholar] [CrossRef]
- Xiang, Y.; Lane, K.L.; Zhou, W. Low-Rate DDoS Attacks Detection and Traceback by Using New Information Metrics. IEEE Trans. Inf. Forensics Secur. 2011, 6, 426–437. [Google Scholar] [CrossRef]
- Wu, Z.; Wang, M.; Yan, C.; Yue, M. Low-Rate DoS Attack Flows Filtering Based on Frequency Spectral Analysis. China Commun. 2017, 14, 98–112. [Google Scholar] [CrossRef]
- Thangavel, S.; Kannan, S. Detection and trace back of low and high volume of distributed denial-of-service attack based on statistical measures. Concurr. Comput. Pract. Exp. 2019, e5428. [Google Scholar] [CrossRef]
- Kuzmanovic, A.; Knightly, E.W. Low-rate TCP-targeted denial of service attacks: The shrew vs. the mice and elephants. In Proceedings of the ACM SIGCOMM 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Karlsruhe, Germany, 25–29 August 2003; pp. 75–86. [Google Scholar] [CrossRef]
- Zhaomin, C.; Chai, K.Y.; Bu, S.L.; Chiew, T.L. Power Spectrum Entropy based Detection and Mitigation of Low-Rate DoS Attacks. Comput. Netw. 2018, 136, 80–94. [Google Scholar] [CrossRef]
- Paxson, V.; Allman, M.; Chu, H.J.; Sargent, M. Computing TCP’s Retransmission Timer. Techn. Rep. 2011. [Google Scholar] [CrossRef]
- Chertov, R.; Fahmy, S.; Fahmy, S. Emulation versus simulation: A case study of TCP-targeted denial of service attacks. In Proceedings of the International Conference on Testbeds & Research Infrastructures for the Development of Networks & Communities, Barcelona, Spain, 1–3 March 2006. [Google Scholar] [CrossRef]
- Tang, D.; Chen, K.; Chen, X.; Liu, H.; Li, X. Adaptive EWMA Method Based on Abnormal Network Traffic for LDoS Attacks. Math. Probl. Eng. 2014, 9, 2981–2986. [Google Scholar] [CrossRef]
- Yue, M.; Wu, Z.; Wang, J. Detecting LDoS Attack Bursts based on Queue Distribution. IET Inf. Secur. 2019, 13, 285–292. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, L.; Yue, M. Low-Rate DoS Attacks Detection Based on Network Multifractal. IEEE Trans. Dependable Secur. Comput. 2016, 13, 559–567. [Google Scholar] [CrossRef]
- Guo, Y.; Duan, H.; Chen, J.; Miao, F. MAF-SAM: An effective method to perceive data plane threats of inter domain routing system. Comput. Netw. 2016, 110, 69–78. [Google Scholar] [CrossRef]
- Tang, D.; Dai, R.; Tang, L.; Zhan, S.; Man, J. Low-Rate DoS Attack Detection Based on Two-Step Cluster Analysis. In Proceedings of the 20th International Conference Information and Communications Security, Lille, France, 29–31 October 2018; pp. 92–104. [Google Scholar] [CrossRef]
- Wu, Z.J.; Yue, M. Detection of LDDoS Attack Based on Kalman Filtering. Acta Electron. Sin. 2008, 36, 1590–1594. [Google Scholar]
- Jiang, D.; Xu, Z.; Chen, Z.; Han, Y.; Xu, H. Joint time-frequency sparse estimation of large-scale network traffic. Comput. Netw. 2011, 55, 3533–3547. [Google Scholar] [CrossRef]
- Ata, L.D.; Arikan, O. Short-time Fourier transform: Two fundamental properties and an optimal implementation. IEEE Trans. Signal Process. 2003, 51, 1231–1242. [Google Scholar] [CrossRef]
- Liu, F.T.; Ting, K.M.; Zhou, Z.H. Isolation Forest. In Proceedings of the Eighth IEEE International Conference on Data Mining, Pisa, Italy, 15–19 December 2009. [Google Scholar] [CrossRef]
- Liu, F.T.; Ming, T.K.; Zhou, Z.H. Isolation-Based Anomaly Detection. ACM Trans. Knowl. Discov. Data 2012, 6, 1–39. [Google Scholar] [CrossRef]
- Fall, K.; Varadhan, K. The NS Manual. Available online: http://www.isi.edu/nsnam/ns/ (accessed on 30 April 2019).
- LBNL; ICSI. LBNL’s Internal Enterprise Traffic. Available online: http://www.icir.org/enterprise-tracing (accessed on 27 May 2019).
- Packet Traces from WIDE Backbone. MAWI Group Working. Available online: http://mawi.wide.ad.jp/ (accessed on 15 August 2019).
- Zhang, X.; Wu, Z.; Chen, J.; Yue, M. An adaptive KPCA approach for detecting LDoS attack. Int. J. Commun. Syst. 2015, 30, e2993. [Google Scholar] [CrossRef]
- Liu, H.; Kim, M.S. Real-Time Detection of Stealthy DDoS Attacks Using Time-Series Decomposition. In Proceedings of the IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010. [Google Scholar] [CrossRef]






| Group | Time (s) | Attack Parameters | |||
|---|---|---|---|---|---|
| R (Mbps) | P (s) | L (s) | |||
| Train | G0 | 2250 | – | – | – |
| Test | G1 | 750 | – | – | – |
| G2 | 1210 | [2,30] | 1 | 0.1 | |
| G3 | 1320 | 8 | [0.4,8] | 0.2 | |
| G4 | 1430 | 8 | 1 | [0.1,0.9] | |
| Group | Sum Time (s) | Time of LDoS Attacks (s) | Attack Parameters | |||
|---|---|---|---|---|---|---|
| R (Thread Count) | P (s) | L (s) | ||||
| Train | G0 | 800 | – | – | – | – |
| Test | G1 | 600 | 200–400 | 500 | 1 | 0.2 |
| G2 | 600 | 200–400 | 750 | 1 | 0.2 | |
| G3 | 900 | 300–600 | 1000 | 1 | 0.1 | |
| G4 | 900 | 300–600 | 1000 | 1 | 0.1 | |
| Detection System | Simulated/Real Environment | Detection Performance (%) | ||
|---|---|---|---|---|
| Detection Accuracy | False Positive Rate | False Negative Rate | ||
| IIR [20] | Network Simulator 2(NS2) | 81.36 | 7.45 | 18.64 |
| Adaptive KPCA [39] | Network Simulator 2(NS2) | 99.2 | 2 | 0.8 |
| Kalman Filtering [31] | Testbed | 89.6 | 12.6 | 10.4 |
| FCE [40] | Testbed | 90.02 | 4.3 | 9.98 |
| Multifractal [28] | Network Simulator 2(NS2) | 92 | 9 | 8 |
| Testbed | 91 | 10 | 9 | |
| FPSE [23] | Network Simulator 3(NS3) | 95.32 | 0.18 | 4.68 |
| Public Datasets (WIDE) | – | 5.876 | – | |
| Two-step Cluster [30] | Network Simulator 2(NS2) | NA | NA | NA |
| Public Datasets (WIDE2018) | – | 5.56 | – | |
| Public Datasets (LBNL) | – | 2.46 | – | |
| Our method | Network Simulator 2(NS2) | 100 | 0.13 | 0 |
| Testbed | 97 | 4.5 | 3 | |
| Public Datasets (WIDE2018) | – | 1.46 | – | |
| Public Datasets (LBNL) | – | 0.71 | – | |
 Testbed
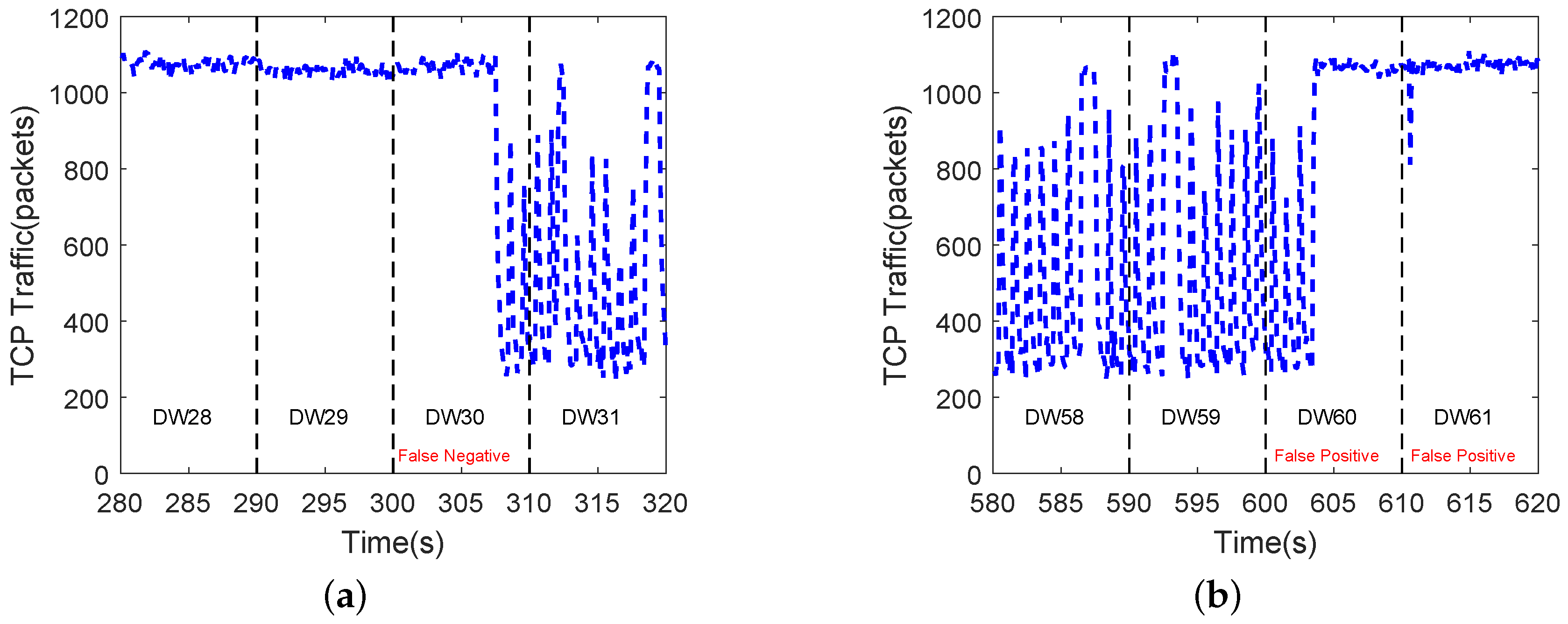
Testbed  Public Datase.
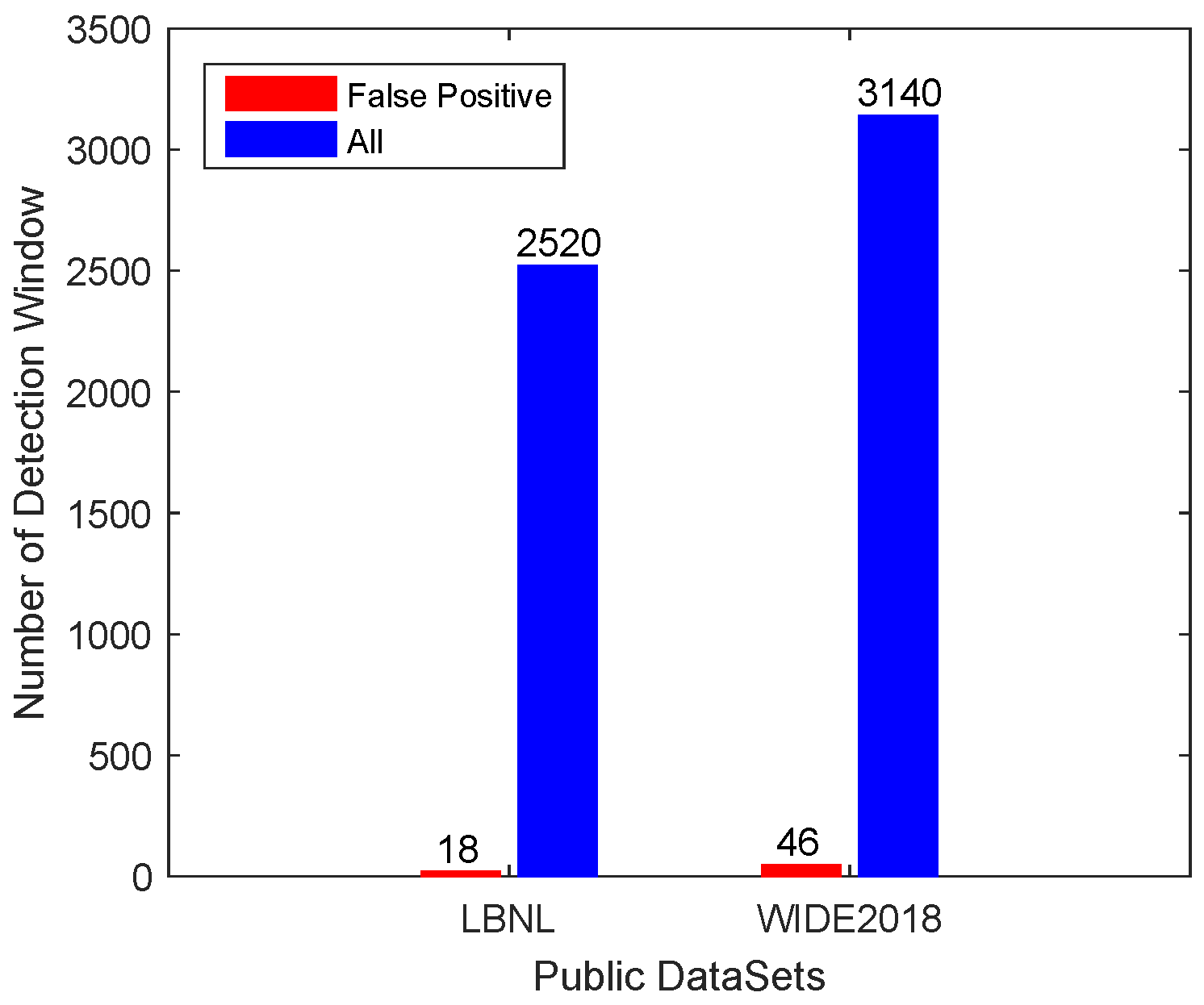
Public Datase.© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhan, S.; Tang, D.; Man, J.; Dai, R.; Wang, X. Low-Rate DoS Attacks Detection Based on MAF-ADM. Sensors 2020, 20, 189. https://doi.org/10.3390/s20010189
Zhan S, Tang D, Man J, Dai R, Wang X. Low-Rate DoS Attacks Detection Based on MAF-ADM. Sensors. 2020; 20(1):189. https://doi.org/10.3390/s20010189
Chicago/Turabian StyleZhan, Sijia, Dan Tang, Jianping Man, Rui Dai, and Xiyin Wang. 2020. "Low-Rate DoS Attacks Detection Based on MAF-ADM" Sensors 20, no. 1: 189. https://doi.org/10.3390/s20010189
APA StyleZhan, S., Tang, D., Man, J., Dai, R., & Wang, X. (2020). Low-Rate DoS Attacks Detection Based on MAF-ADM. Sensors, 20(1), 189. https://doi.org/10.3390/s20010189





