Clustering Based Physical-Layer Authentication in Edge Computing Systems with Asymmetric Resources
Abstract
1. Introduction
- We propose the first CPAS scheme, which combines clustering and lightweight symmetric cipher with physical-layer channel state information firstly and can be employed to authenticate mutually between terminals and edge devices. We also show the detailed implementing procedures of the proposed scheme.
- We analyze the security of the proposed scheme and prove that it can resist small integer attacks, replay attacks, and spoofing attacks.
- The CPAS scheme is implemented in a real world environment based on MIMO-OFDM systems. We also show the impacts of adjusting parameters of clusters on the success rate of physical-layer channel authentication, the data frame loss rate, the total success rate of access authentication, and the time cost through experimental results demonstration.
2. Basic Principles of Physical Layer Channel Authentication
3. System Model and Proposed Scheme
3.1. Secret Key Sharing
3.2. Initial Authentication
- (1)
- Alice generates a pseudorandom number , and encrypts with a lightweight cryptographic algorithm to obtain ciphertext , where means that encrypting message, such as the random number in the parentheses by using a lightweight cryptographic algorithm and a secret key. Then, the terminal generates a login request message and sends it to the edge computing device, where the request message includes the ciphertext .
- (2)
- Bob extracts the channel state information from the received signal sent by Alice, and then gets the ciphertext from decoding data and the plaintext via decrypting with the same lightweight cryptographic algorithm and secret key, where , means that decrypting message, such as in the parentheses via using a lightweight cryptographic algorithm and a secret key, and the channel information is a complex matrix of m rows and n columns.
- (3)
- Bob generates two pseudorandom numbers and , and calculates the ciphertext . Then, Bob sends a response message to Alice, where contains the ciphertext .
- (4)
- Alice verifies the legitimacy of Bob. When Alice receives the response message , it decodes to obtain the ciphertext , and then decrypts to obtain the plaintext () = . If the is not equal to , Bob is an illegal edge device and Alice cancels the login; otherwise, Alice considers Bob to be a legitimate edge computing device, calculates two response messages and , and continuously sends them to the edge computing device, where includes ciphertext , and contains ciphertext .
- (5)
- Bob verifies the legitimacy of Alice. Bob extracts the channel information and from the received response messages and sent from Alice, and then gets the ciphertext and from decoding and the plaintext and by decrypting and with the same lightweight cryptographic algorithm and secret key, where , , the channel information extracted by Bob from and from , and are complex matrices of m rows and n columns. If is equal to and is matching to , Bob considers Alice as a legitimate terminal, and the initial authentication ends; otherwise, Alice is an illegal terminal and Bob cancels the login.
3.3. Physical-Layer Channel Modeling
- (1)
- Preprocessing channel state informationThe channel information , , and , which are extracted during the initial full authentication phase, are complex matrices of m rows and n columns, where m denotes the number of carriers, and n indicates the number of antennas. To obtain the statistical characteristics of channel information, we accumulate the absolute value of the real part and the imaginary part about the complex matrices, respectively. The statistical coordinates of channel information are named as , , and , which are coordinate pairs on the complex plane.
- (2)
- Locating central position of clusterAfter completing the previous sub-step, preprocessing channel information, the central position of cluster (channel model), named as , is estimated bywhere represents minimum value, while implies maximum value.
- (3)
- Estimating coverage radius of clusterThe Euclidean distances between the central position and the statistical position of channel information , , and are given bywhere denotes the Euclidean distances between and , , and , respectively. Then, the maximum Euclidean distance is taken as the radius of cluster.where R denotes the radius of cluster. Further, the coverage radius of channel model is obtained bywhere is the adjusting parameter of the coverage radius of channel model.
- (4)
- Clustering physical-layer channel modelWhen the central position and the coverage radius of channel model are determined, the categories of physical-layer channel model are defined aswhere i indicates the index of terminal, and different is specified for a different cluster, i.e., a different terminal.
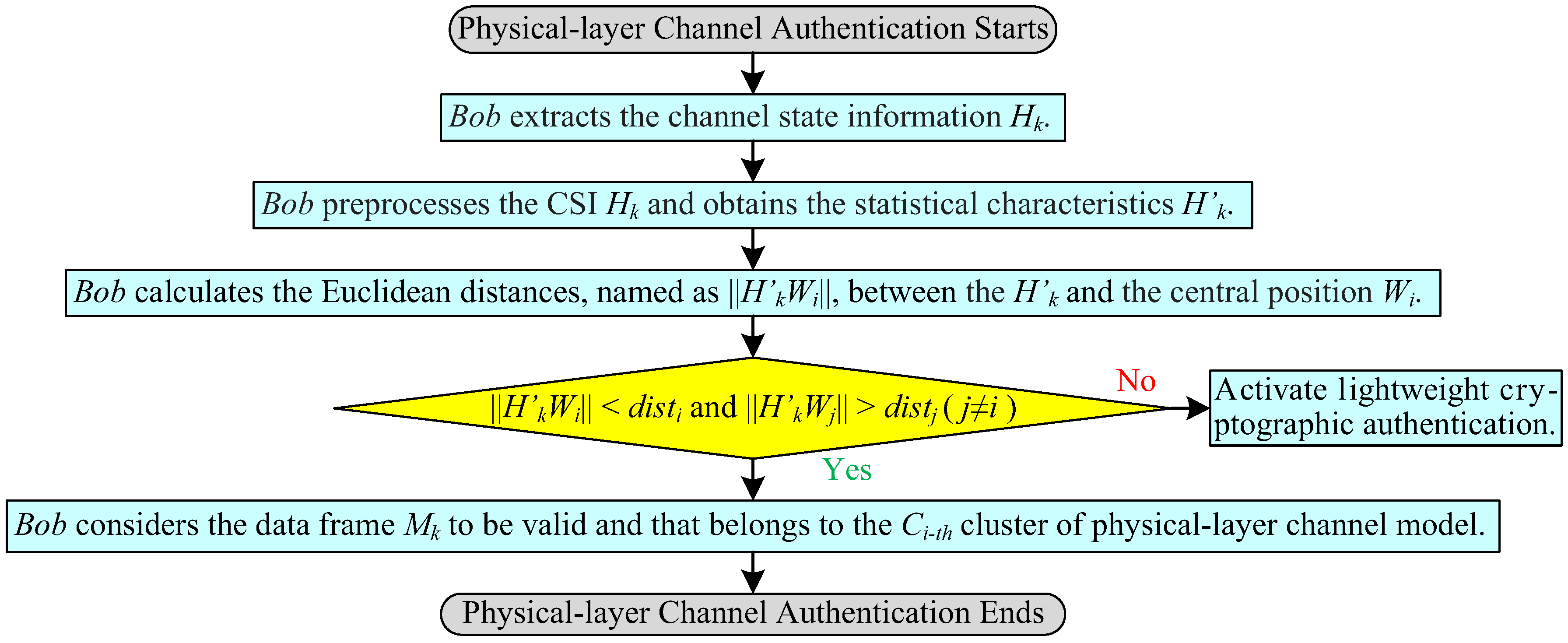
3.4. Physical-Layer Channel Authentication
- (1)
- Bob extracts the channel information from the received data frame sent from Alice, where, the channel information is a complex matrix of m rows and n columns, the data frame contains the cipher text , “⨁” means XOR function, and the k indicates the index of data frame.
- (2)
- Bob preprocesses the channel information . To obtain the statistical characteristics of channel information, Bob accumulates the absolute value of the real part and the imaginary part of , respectively. The statistical characteristics denote the coordinate pairs on the complex plane.
- (3)
- Bob checks the validity of the data frame . Firstly, Bob calculates the Euclidean distances, named as , between the and the central position of the cluster, respectively. Then, Bob compares the sizes of and : when and , Bob considers the data frame to be valid and that belongs to the cluster (physical-layer channel model); otherwise, Bob activates lightweight cryptographic authentication.
3.5. Lightweight Cryptographic Authentication
- (1)
- Bob gains the ciphertext, , and the number of data frame, , which is also a pseudorandom number, via decoding the data frame sent from Alice, where , and the length of the random number is determined according to the actual application scenario. If matches the previous number of data frame, considers as a replayed packet and throws it away; otherwise, Bob goes to next step.
- (2)
- Bob decrypts the ciphertext to get the plaintext .
- (3)
- Bob checks the validity of the data frame . If does not match , the data frame is illegal and Bob discards it. If is equal to , Bob considers as a valid data frame, and then extracts and records its channel information . When Bob receives j data frames , namely lightweight cryptographic authentication being activated j times continuously, the model update of physical-layer channel authentication will be activated.
3.6. Model Update of Physical-Layer Channel Authentication
- (1)
- Preprocessing the new channel informationThe sequences of channel information , , ⋯, , which are extracted during the lightweight cryptographic authentication phase, are complex matrices of m rows and n columns. To obtain the statistical characteristics of channel information, we accumulate the absolute values of the real part and the imaginary part about the complex matrices, respectively. The statistical sequences of channel information are named as , , ⋯, , which are coordinate pairs on the complex plane.
- (2)
- Locating new central position of clusterAfter completing the previous sub-step, preprocessing the new channel information, the new central positions of physical-layer channel model, named as , are estimated by Equation (10).
- (3)
- Estimating new coverage radius of clusterThe Euclidean distances between the new central position and the statistical sequences of channel information , , ⋯, , are given bywhere (, , ⋯, ) denote the Euclidean distances. Then, the maximum Euclidean distance is taken as the new radius () of cluster.where denotes the new radius of channel model. Further, the new coverage radius of cluster is obtained bywhere indicates the adjusting parameter of the coverage radius of channel model.
- (4)
- Re-clustering physical-layer channel modelWhen obtaining the new central position and the new coverage radius of channel model, the new cluster of physical-layer channel model is redefined as
4. Security Analysis
5. Performance
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| CPAS | Clustering based physical-layer authentication scheme |
| CPU | Central processing unit |
| CSI | Channel state information |
| ED | Edge computing device |
| GHz | Giga Hertz |
| IoT | Internet of things |
| LRT | Likelihood ratio test |
| MHz | Mega Hertz |
| SPRT | Sequential probability ratio test |
| TCAS | Traditional cipher authentication scheme |
| USRP | Universal software radio peripheral |
References
- Kawamoto, Y.; Yamada, N.; Nishiyama, H.; Kato, N.; Shimizu, Y.; Zheng, Y. A feedback control-based crowd dynamics management in IoT system. IEEE Internet Things J. 2017, 4, 1466–1476. [Google Scholar] [CrossRef]
- Verma, S.; Kawamoto, Y.; Fadlullah, Z.M.; Nishiyama, H.; Kato, N. A survey on network methodologies for real-time analytics of massive IoT data and open research issues. IEEE Commun. Surv. Tutor. 2017, 19, 1457–1477. [Google Scholar] [CrossRef]
- Rodrigues, T.G.; Suto, K.; Nishiyama, H.; Kato, N. Hybrid method for minimizing service delay in edge cloud computing through VM migration and transmission power control. IEEE Trans. Comput. 2017, 66, 810–819. [Google Scholar] [CrossRef]
- Bhardwaj, I.; Kumar, A.; Bansal, M. A review on lightweight cryptography algorithm for data security and authentication in IoTs. In Proceedings of the 4th International Conference on Signal Processing, Computing and Control (ISPCC 2017), Solan, India, 21–23 September 2017; pp. 504–509. [Google Scholar]
- Cazorla, M.; Marquet, K.; Minier, M. Survey and benchmark of lightweight block ciphers for wireless sensor networks. In Proceedings of the 10th International Conference on Security and Cryptography (SECRYPT 2013), Reykjavik, Iceland, 29–31 July 2013; pp. 543–548. [Google Scholar]
- Wen, H.; Li, S.Q.; Zhu, X.P.; Zhou, L. A framework of the PHY-layer approach to defense against security threats in cognitive radio networks. IEEE Netw. 2013, 27, 34–39. [Google Scholar]
- Wen, H.; Wang, Y.F.; Zhu, X.P.; Li, J.Q.; Zhou, L. Physical layer assist authentication technique for smart meter system. IET Commun. 2013, 7, 189–197. [Google Scholar] [CrossRef]
- Hu, L.; Wen, H.; Wu, B.; Pan, F.; Liao, R.F.; Song, H.H.; Tang, J.; Wang, X.M. Cooperative jamming for physical layer security enhancement in Internet of things. IEEE Internet Things J. 2018, 5, 219–228. [Google Scholar] [CrossRef]
- Xie, F.Y.; Wen, H.; Li, Y.S.; Chen, S.L.; Hu, L.; Chen, Y.; Song, H.H. Optimized coherent integration-based radio frequency fingerprinting in Internet of things. IEEE Internet Things J. 2018, 5, 3967–3977. [Google Scholar] [CrossRef]
- Chen, Y.; Wen, H.; Song, H.; Chen, S.; Xie, F.; Yang, Q.; Hu, L. Lightweight one-time password authentication scheme based on radio-frequency fingerprinting. IET Commun. 2018, 12, 1477–1484. [Google Scholar] [CrossRef]
- Zeng, K.; Govindan, K.; Mohapatra, P. Non-cryptographic authentication and identification in wireless networks. IEEE Wirel. Commun. 2010, 17, 56–62. [Google Scholar] [CrossRef]
- Xiao, L.; Greenstein, L.; Mandayam, N.; Trappe, W. Fingerprints in the Ether: Using the Physical Layer for Wireless Authentication. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, UK, 24–28 June 2007; pp. 4646–4651. [Google Scholar]
- Xiao, L.; Greenstein, L.J.; Mandayam, N.B.; Trappe, W. Using the physical layer for wireless authentication in time-variant channels. IEEE Trans. Wirel. Commun. 2008, 7, 2571–2579. [Google Scholar] [CrossRef]
- Xiao, L.; Greenstein, L.; Mandayam, N.; Trappe, W. A Physical-Layer Technique to Enhance Authentication for Mobile Terminals. In Proceedings of the 2008 IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 1520–1524. [Google Scholar]
- Wang, N.; Jiang, T.; Lv, S.C.; Xiao, L. Physical-layer authentication based on extreme learning machine. IEEE Commun. Lett. 2017, 21, 1557–1560. [Google Scholar] [CrossRef]
- Pan, F.; Pang, Z.; Luvisotto, M.; Xiao, M.; Wen, H. Physical-Layer Security for Industrial Wireless Control Systems: Basics and Future Directions. IEEE Ind. Electron. Mag. 2018, 12, 18–27. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT security techniques based on machine learning: How do IoT devices use AI to enhance security? IEEE Signal Process. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]
- Xiao, L.; Li, Y.; Han, G.; Liu, G.; Zhuang, W. PHY-Layer spoofing detection with reinforcement learning in wireless networks. IEEE Trans. Veh. Technol. 2016, 65, 10037–10047. [Google Scholar] [CrossRef]
- Xiao, L.; Chen, T.; Han, G.; Zhuang, W.; Sun, L. Game theoretic study on channel-based authentication in MIMO systems. IEEE Trans. Veh. Technol. 2017, 66, 7474–7484. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Han, Z. PHY-Layer authentication with multiple landmarks with reduced overhead. IEEE Trans. Wirel. Commun. 2018, 17, 1676–1687. [Google Scholar] [CrossRef]
- Pan, F.; Pang, Z.; Xiao, M.; Wen, H.; Liao, R. Clone detection based on physical layer reputation for proximity service. IEEE Access 2019, 7, 3948–3957. [Google Scholar] [CrossRef]
- He, F.; Man, H.; Kivanc, D.; McNair, B. EPSON: Enhanced physical security in OFDM networks. In Proceedings of the IEEE International Conference on Communications (ICC 2009), Dresden, Germany, 14–18 June 2009; pp. 824–828. [Google Scholar]
- Li, Y.; Cimini, L.J.; Sollenberger, N.R. Robust channel estimation for OFDM systems with rapid dispersive fading channels. IEEE Trans. Commun. 1998, 46, 902–915. [Google Scholar] [CrossRef]
- Larsson, E.G.; Liu, G.Q.; Li, J.; Giannakis, G.B. Joint symbol timing and channel estimation for OFDM based WLANs. IEEE Commun. Lett. 2001, 5, 325–327. [Google Scholar] [CrossRef]
- Su, W.; Pan, Z. Iterative LS channel estimation for OFDM systems based on transform-domain processing. In Proceedings of the 2007 International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, 21–25 September 2007; pp. 416–419. [Google Scholar]
- Jain, A.K.; Murty, M.N.; Flynn, P.J. Data clustering: A review. ACM Comput. Surv. 1999, 31, 264–323. [Google Scholar] [CrossRef]
- Xu, R.; Wunsch, D. Survey of clustering algorithms. IEEE Trans. Neural Netw. 2005, 16, 645–678. [Google Scholar] [CrossRef]
- Singh, D.; Gosain, A. A comparative analysis of distributed clustering algorithms: A survey. In Proceedings of the 2013 International Symposium on Computational and Business Intelligence (ISCBI), New Delhi, India, 24–26 August 2013; pp. 165–169. [Google Scholar]
- Fahad, A.; Alshatri, N.; Tari, Z.; Alamri, A.; Khalil, I.; Zomaya, A.Y.; Foufou, S.; Bouras, A. A survey of clustering algorithms for big data: Taxonomy and empirical analysis. IEEE Trans. Emerg. Top. Comput. 2014, 2, 267–279. [Google Scholar] [CrossRef]
- Osman, M.M.A.; Syed-Yusof, S.K.; Abd Malik, N.N.N.; Zubair, S. A survey of clustering algorithms for cognitive radio ad hoc networks. Wirel. Netw. 2018, 24, 1451–1475. [Google Scholar] [CrossRef]
- Alaghi, A.; Hayes, J.P. Survey of stochastic computing. ACM Trans. Embed. Comput. Syst. 2013, 12, 92:1–92:19. [Google Scholar] [CrossRef]
- Han, J.; Chen, H.; Liang, J.H.; Zhu, P.C.; Yang, Z.X.; Lombardi, F. A stochastic computational approach for accurate and efficient reliability evaluation. IEEE Trans. Comput. 2014, 63, 1336–1350. [Google Scholar] [CrossRef]
- Bakiri, M.; Guyeux, C.; Couchot, J.F.; Marangio, L.; Galatolo, S. A hardware and secure pseudorandom generator for constrained devices. IEEE Trans. Ind. Inform. 2018, 14, 3754–3765. [Google Scholar] [CrossRef]
- Harase, S. On the F-2-linear relations of Mersenne Twister pseudorandom number generators. Math. Comput. Simul. 2014, 100, 103–113. [Google Scholar] [CrossRef]
- Borle, K.M.; Chen, B.A.; Du, W.L. Physical layer spectrum usage authentication in cognitive radio: Analysis and implementation. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2225–2235. [Google Scholar] [CrossRef]
- Tong, Z.; Russ, C.; Vanka, S.; Haenggi, M. Prototype of virtual full duplex via rapid on-off-division duplex. IEEE Trans. Commun. 2015, 63, 3829–3841. [Google Scholar] [CrossRef]
- Omar, M.S.; Naqvi, S.A.R.; Kabir, S.H.; Hassan, S.A. An experimental evaluation of a cooperative communication-based smart metering data acquisition system. IEEE Trans. Ind. Inform. 2017, 13, 399–408. [Google Scholar] [CrossRef]















© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Y.; Wen, H.; Wu, J.; Song, H.; Xu, A.; Jiang, Y.; Zhang, T.; Wang, Z. Clustering Based Physical-Layer Authentication in Edge Computing Systems with Asymmetric Resources. Sensors 2019, 19, 1926. https://doi.org/10.3390/s19081926
Chen Y, Wen H, Wu J, Song H, Xu A, Jiang Y, Zhang T, Wang Z. Clustering Based Physical-Layer Authentication in Edge Computing Systems with Asymmetric Resources. Sensors. 2019; 19(8):1926. https://doi.org/10.3390/s19081926
Chicago/Turabian StyleChen, Yi, Hong Wen, Jinsong Wu, Huanhuan Song, Aidong Xu, Yixin Jiang, Tengyue Zhang, and Zhen Wang. 2019. "Clustering Based Physical-Layer Authentication in Edge Computing Systems with Asymmetric Resources" Sensors 19, no. 8: 1926. https://doi.org/10.3390/s19081926
APA StyleChen, Y., Wen, H., Wu, J., Song, H., Xu, A., Jiang, Y., Zhang, T., & Wang, Z. (2019). Clustering Based Physical-Layer Authentication in Edge Computing Systems with Asymmetric Resources. Sensors, 19(8), 1926. https://doi.org/10.3390/s19081926




