Minimum Connected Dominating Set Algorithms for Ad Hoc Sensor Networks
Abstract
:1. Introduction
- (1)
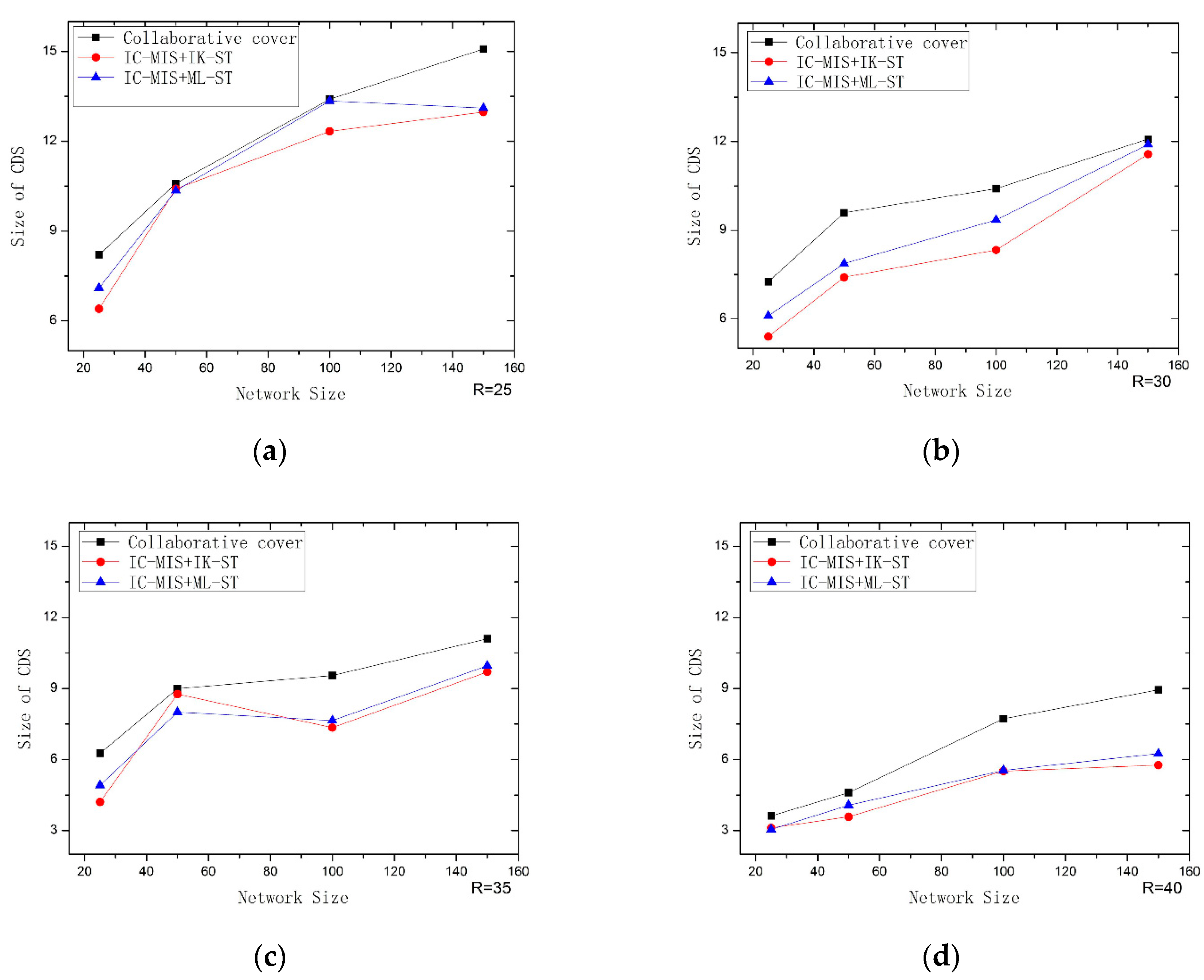
- For the first stage, an improved collaborative coverage algorithm (IC-MIS) for solving the MIS is proposed. The algorithm uses a new dominating node selection scheme to choose the next dominating nodes from the three-hop neighbor of the current dominating nodes, and if it does not exist, the next dominating nodes will be chosen from the two-hop neighbor of the current dominating nodes. The overlap coverage between dominating nodes is reduced and the coverage efficiency is improved under the condition of complete coverage.
- (2)
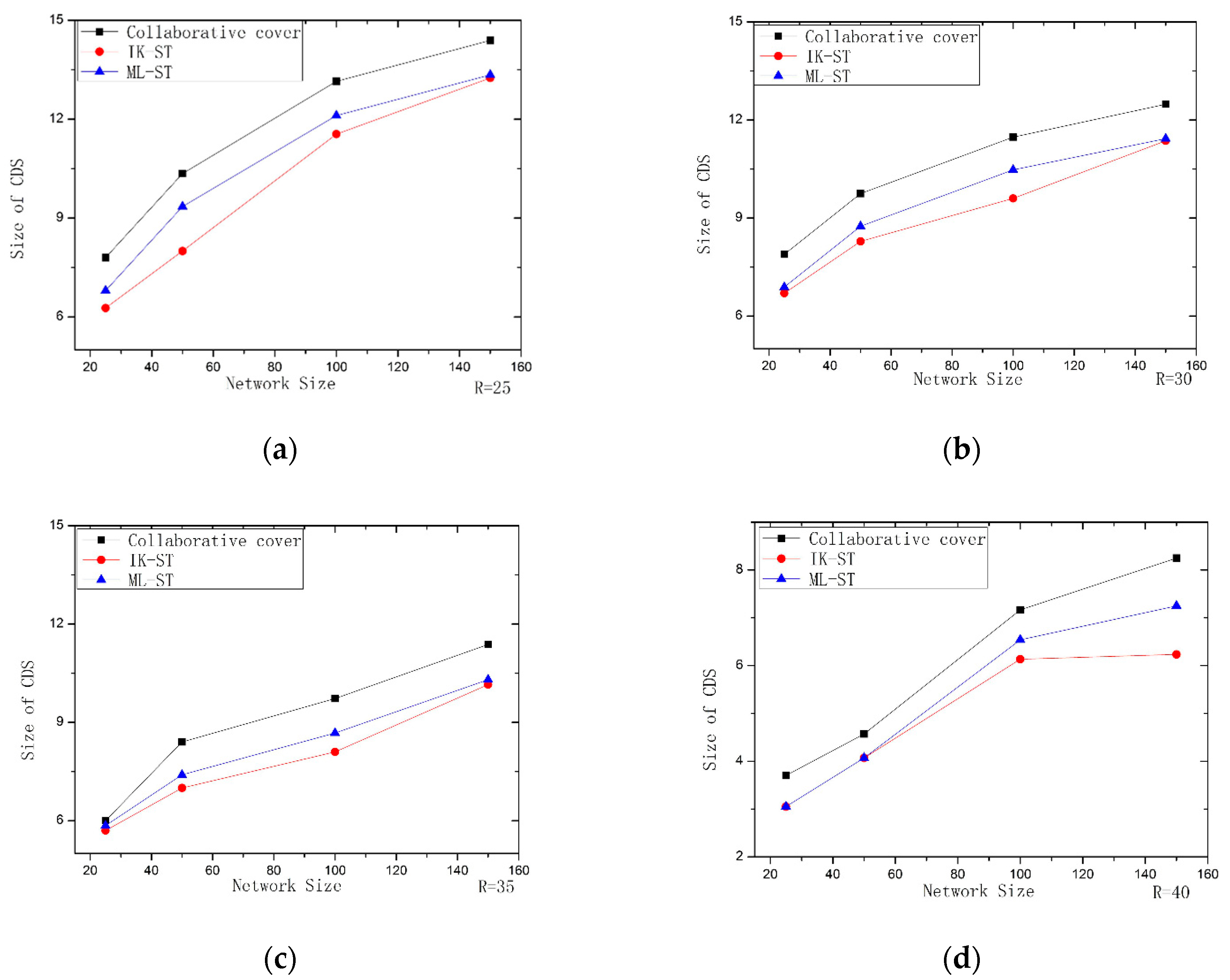
- For the second stage, an improved Kruskal–Steiner tree construction algorithm (IK–ST) is proposed. Most researchers generally use greedy method to construct and solve Steiner nodes, but this kind of algorithm is easy to fall into local optimal solution. In this paper, we improve the idea of IK–ST based on the spanning tree, add the corresponding weight strategy to the nodes selection, and realize the construction of the Steiner tree by adding the nodes replacement edge, In this way, the number of Steiner nodes will be further reduced.
- (3)
- For the second stage, a new Steiner tree construction algorithm, a maximum leaf nodes Steiner tree construction algorithm (ML-ST), is also proposed, which is based on the idea of the maximum leaf nodes tree and sets the weight value for each edge according to a certain strategy. Then, a Steiner tree is generated by merging the edges with large weights to find the Steiner nodes, so that the results are closer to the optimal solution.
- (4)
- Finally, the simulation experiments results show that the proposed algorithm is better than the typical collaborative coverage algorithm in optimizing the size of connected dominating set.
2. Related Work
3. Network Model, Dominating Set and Symbol Definitions
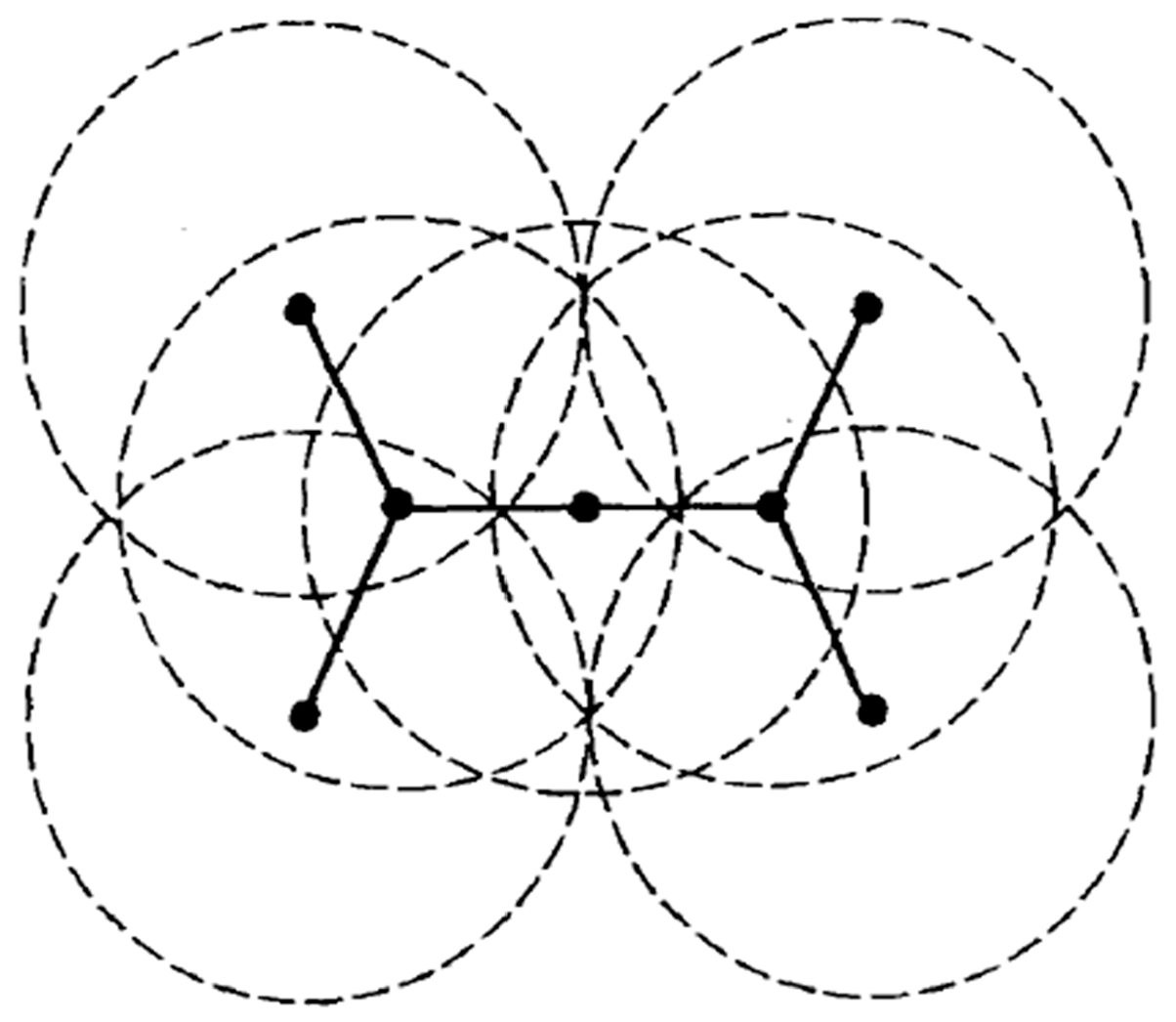
3.1. Related Knowledge
3.2. Formalized Definitions
4. IC-MIS Algorithm
| Algorithm 1: IC-MIS algorithm | |
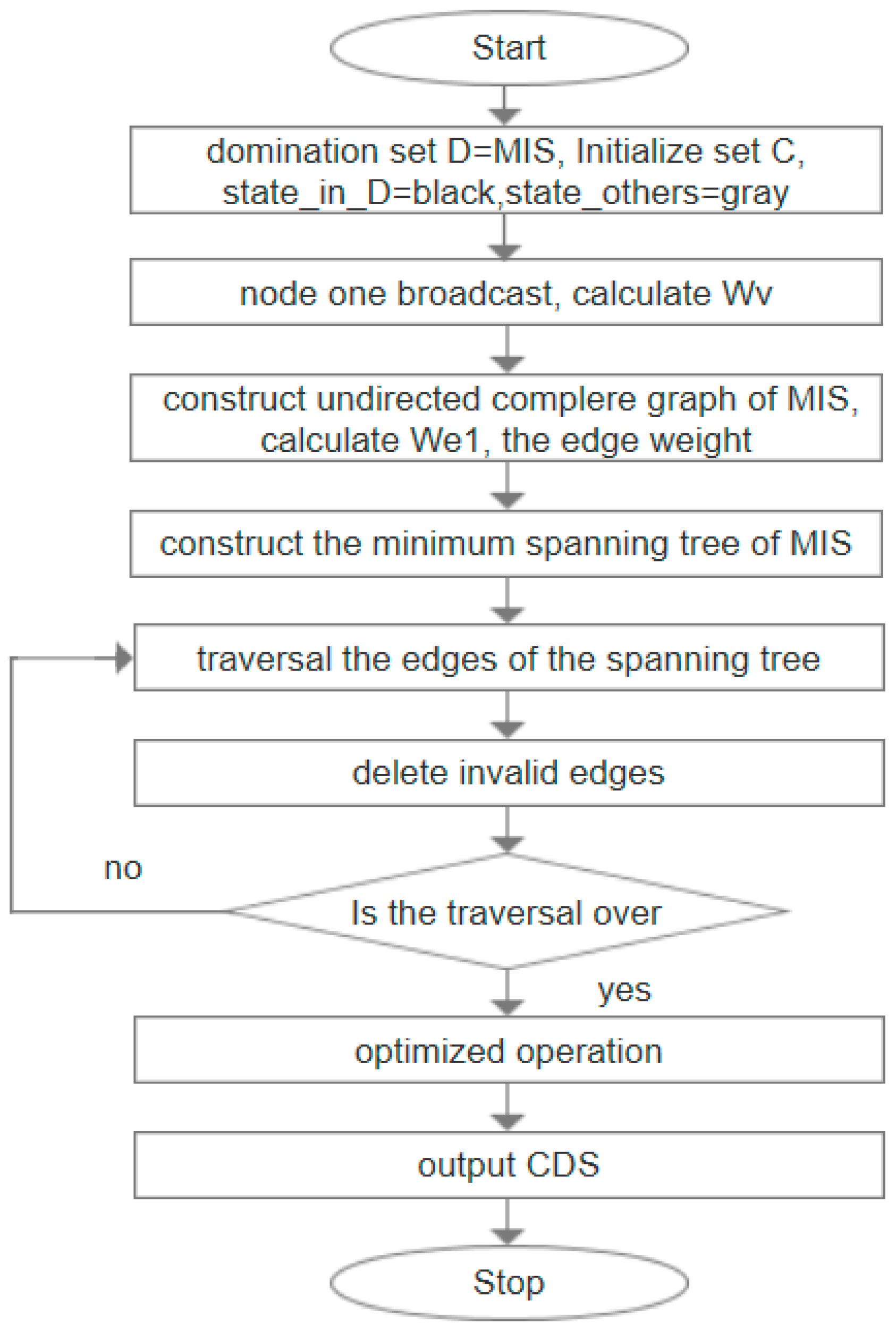
| 1: | Input: graph G = (V, E), initialize set D is empty, state of all nodes is set to white. |
| 2: | Starting from the base station node B, node B is added to the set D as the first dominating node. Node B update its own state to black, and broadcast the message m1 to the neighbor node in the one-hop range; |
| 3: | After receiving m1, each adjacent node sets its state to gray and broadcasts the message m2 to the surrounding hop neighbor nodes, each white node sets its state to blue after receiving m2 message; |
| 4: | Each blue node continues to broadcast message m3 to nearby one-hop. After receiving the m3 message, node t calculates priority Pro(t) according to Definition 8. All blue nodes elect a white node Dt with the highest priority through comparison Pro(t) as an undetermined dominating node, and the status of the node is set to red. If the priority is equal, the node with a larger degree will be chosen; if the node degree is equal, the node with small ID is given priority. If there is no node Dt under white status, the node with the highest Pro(v) from blue nodes is chosen as Dt; |
| 5: | When the Dt node is selected, we calculate the independent set IS of the Dt node in one-hop range through the message broadcast; there will be many IS at this time, and we choose the largest WIS (WIS = the number of nodes covered / the number of dominating nodes) to replace the Dt and restore the state of the Dt node to white, where the nodes in IS are chosen as the dominating nodes. Set the state of the node in IS as black and update the node in one-hop as gray; |
| 6: | Repeat the above steps until no white node exists in all nodes. |
5. Steiner Tree Construction Algorithm Based on Minimum Spanning Tree
5.1. IK–ST Algorithm
| Algorithm 2: IK–ST algorithm | |
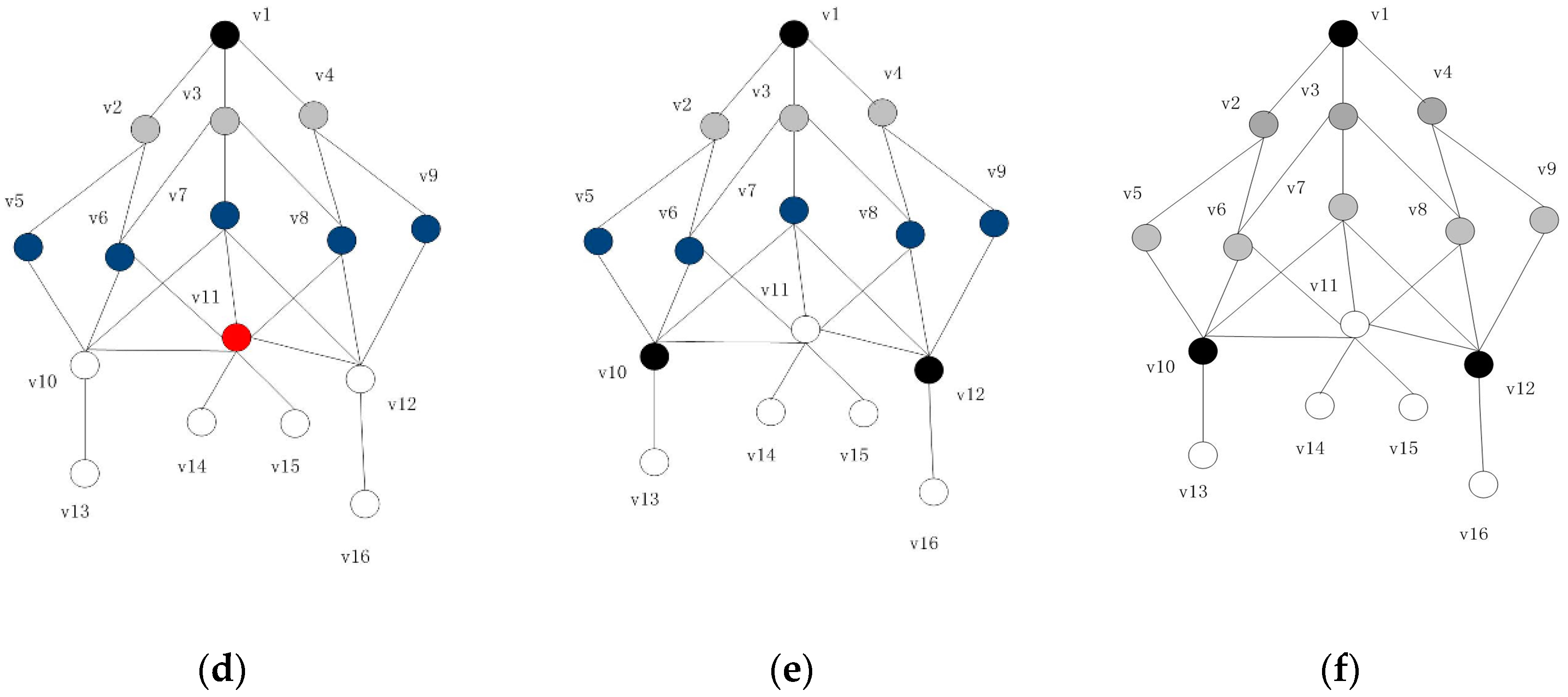
| 1: | Input: graph G = (V, E), dominating set D = MIS; initialize one set C as the node empty; nodes in D are black, and the rest of the nodes are gray. |
| 2: | First of all, set the weight Wv for each node. The Wv can be set by one broadcast of the node, and the rules are calculated according to Definition 5; |
| 3: | The undirected complete graph of MIS is constructed, and the weight value We1(s, d) of each edge is calculated according to Definition 6 (if node s and node d do not have a common join node, set the weight We1 of this edge to a maximum); |
| 4: | The construction method adopts the classical Kruskal algorithm to construct the minimum spanning tree of MIS, TMIS; |
| 5: | Select any edge E from the edge set of the spanning tree, where s and d are the source node and destination node of the edge. Select a node t from one-hop neighbor of s, and make sure that s can be accessed to d through two hops. The selection rule is as follows: select the node that can connect the biggest number of black nodes except d and s nodes, if equal, the node with a small node ID is preferred; |
| 6: | When the t node is found, t is added to C and then delete the invalid edge. The strategy employed is as follows: firstly, delete the current edge; secondly, if t has an adjacent node except s or d, and the node has an edge E’ or the node is adjacent to s or d, then we delete E’; |
| 7: | Repeat 4 and 5 until all the edges of the spanning tree are traversed; |
| 8: | In the optimization stage, the nodes in C are traversed in turn. If all the black nodes adjacent to a node t’ can be adjacent to the nodes in C\{t}and C\{t}can still form a spanning tree, then delete t’. |
| 9: | Output: D + C i.e., (CDS) |
5.2. ML-ST Algorithm
| Algorithm 3 ML-ST algorithm | |
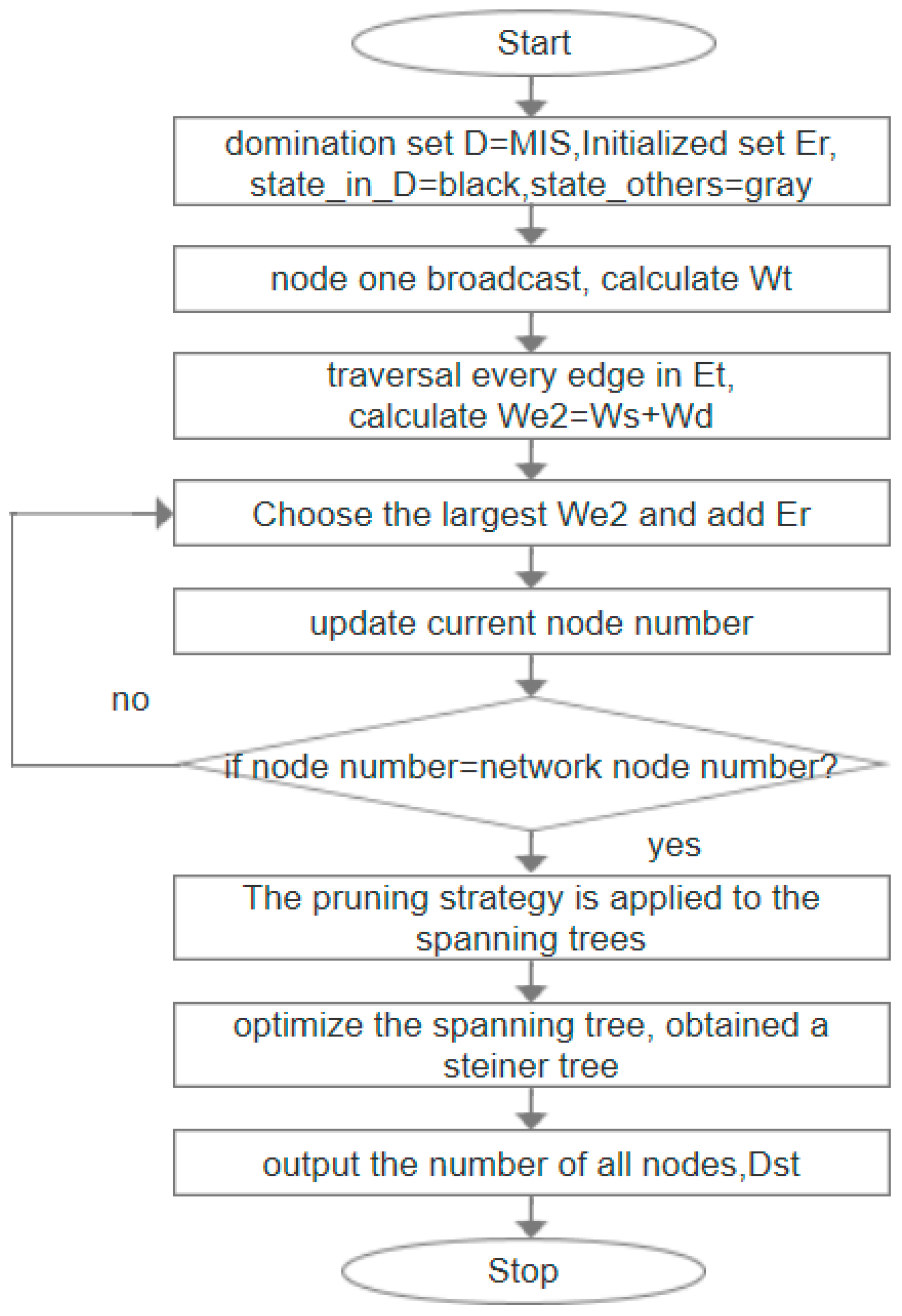
| 1: | Input: graph G = (V, E), dominating set D = MIS; initializing a set Er to be empty, setting the state of nodes in D as black and the rest as gray. |
| 2: | Initialize an edge set Et and add all existing edges in the graph to Et by a broadcast of the node; |
| 3: | The weight value Wt of each node is calculated by a broadcast message of each node, and the standard of calculation is Definition 5, which ensures that the edges adjacent to the midnode of MIS can be selected into the spanning tree first; |
| 4: | Traverse each edge in Et and set weight values for each edge as the standard of merging the spanning tree for the next step, we select a side e, We2 = Ws + Wd by the calculation of the edge weight according to Definition 7, where Ws and Wd are the weights obtained in Step 2, while Ws represents the weight of the source nodes of e, and Wd represents the weight of the destination nodes of e; |
| 5: | Start from any node in MIS and traversing the edge of Et, the edge with maximum We2 is selected to be added to Er for each time, and if equal, any one edge is added. Update the current number of nodes until the number of nodes is equal to the number of network nodes; |
| 6: | A pruning strategy is made for the spanning tree formed by edges in Et. The pruning strategy is as follows: traversing each node, if a node has a degree of 1 and the node is not a black node, he node and its associated edges are deleted; |
| 7: | Optimize the spanning tree after processing of Step 5 and traverse the nodes in the spanning tree in turn. If all the black nodes adjacent to one node t’ can be adjacent to the other nodes, and can still form a spanning tree, then delete t’. It is obtained that the last Er edge set constitutes a Steiner tree, in which the number of all nodes are recorded as DST. |
| 8: | Output: DST |
6. Simulation Experiments
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Eshghi, F.; Elhakeem, A.K. Perofrmance analysis of Ad Hoc wireless LANs for Real-time traffic. IEEE J. Sel. Areas Commun. 2003, 21, 204–215. [Google Scholar] [CrossRef]
- Carlos-Mancilla, M.; Lopez-Mellado, E.; Siller, M.; Fapojuwo, A. An efficient reconfigurable ad-hoc algorithm for multi-sink wireless sensor networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717733390. [Google Scholar] [CrossRef]
- Yang, W.; Zhang, G. A weight-based clustering algorithm for mobile ad hoc network. In Proceedings of the 3rd International Conference on Wireless and Mobile Communications, Harbin, China, 26–30 July 2011. [Google Scholar]
- Joy, P.; Jacob, K. A Virtual Backbone Based Approach for Cooperative Caching in Mobile Ad hoc Networks. In Proceedings of the 16th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Korea, 16–19 February 2014. [Google Scholar]
- Ramtin, A.; Hakami, V.; Dehghan, M. A Perturbation-Proof Self-stabilizing Algorithm for Constructing Virtual Backbones in Wireless Ad-Hoc Networks. In Proceedings of the International Symposium on Computer Networks and Distributed Systems (CNDS)/2nd Conference of Computer-Society-of-Iran (CSI), Tehran, Iran, 25–26 December 2013. [Google Scholar]
- Togou, M.; Hafid, A.; Sahu, P. A Stable Minimum Velocity CDS-based Virtual Backbone for VANET in City Environment. In Proceedings of the 39th Annual IEEE Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 8–11 September 2014. [Google Scholar]
- Asgarnezhad, R.; Torkestani, J.A. A survey on backbone formation algorithms for Wireless Sensor Networks: (A New Classification). In Proceedings of the Telecommunication Networks & Applications Conference, Melbourne, Australia, 9–11 November 2011. [Google Scholar]
- Yu, J.; Wang, N.; Wang, G. Constructing minimum extended weakly-connected dominating sets for clustering in ad hoc networks. J. Parallel Distrib. Comput. 2012, 72, 35–47. [Google Scholar] [CrossRef]
- Al-Nabhan, N.; Al-Rodhaan, M.; Al-Dhelaan, A.; Cheng, X. Connected dominating set algorithms for wireless sensor networks. Int. J. Sens. Netw. 2013, 13, 121–134. [Google Scholar] [CrossRef]
- Ahn, N.; Park, S. An optimization algorithm for the minimum k-connected m-dominating set problem in wireless sensor networks. Wirel. Netw. 2015, 21, 783–792. [Google Scholar] [CrossRef]
- He, H.; Zhu, Z.; Makinen, E. A Neural Network Model to Minimize the Connected Dominating Set for Self-Configuration of Wireless Sensor Networks. IEEE Trans. Neural Netw. 2009, 20, 973–982. [Google Scholar]
- Liu, B.; Wang, B. On Approximating Minimum 3-Connected m-Dominating Set Problem in Unit Disk Graph. IEEE ACM Trans. Netw. 2016, 24, 2722–2733. [Google Scholar] [CrossRef]
- Biniaz, A.; Maheshwari, A.; Smid, M. On full Steiner trees in unit disk graphs. Comput. Geom. Theory Appl. 2015, 48, 453–458. [Google Scholar] [CrossRef]
- Sun, X.; Yan, B. Node Deployment Algorithm Based on Improved Steiner Tree. Int. J. Multimed. Ubiquitous Eng. 2015, 10, 329–338. [Google Scholar] [CrossRef]
- Guha, S.; Khuller, S. Approximation Algorithms for Connected Dominating Sets. Algorithmica 1998, 20, 374. [Google Scholar] [CrossRef]
- Das, B.; Bharghavan, V. Routing in ad hoc networks using a virtual backbone. In Proceedings of the 6th International Conference on Computer Communications and Networks (IC3N.97), Montreal, QC, Canada, 12 June 1997. [Google Scholar]
- Das, B.; Bharghavan, V. Routing in ad hoc networks using minimum connected Dominating sets. In Proceedings of the ICC’97—International Conference on Communications, Montreal, QC, Canada, 12 June 1997. [Google Scholar]
- Wu, J. Extended Dominating-Set-Based Routing in Ad Hoc Wireless Networks with Unidirectional Links. IEEE Trans. Parallel Distrib. Syst. 2002, 9, 189–200. [Google Scholar]
- Ruan, L.; Du, H.; Jia, X.; Wu, W.; Li, Y.; Ko, K. A Greedy Approximation for Minimum Connected Dominating Sets. Theor. Comput. Sci. 2004, 329, 325–330. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Liu, X. Loop-free hybrid single-path flooding routing algorithms with guaranteed delivery for wireless networks. IEEE Trans. Parallel Distrib. Syst. 2001, 12, 1023–1032. [Google Scholar] [CrossRef]
- Cardei, M.; Cheng, X.; Du, D. Connected domination in multi-hop ad hoc wireless networks. International Conference on Computer Science and Informatics. In Proceedings of the 6th Joint Conference on Information Science, Durham, NC, USA, 8–13 March 2002. [Google Scholar]
- Li, Y.; Thai, M.; Wang, F.; Yi, C.; Wan, P.; Du, D. On greedy construction of connected dominating sets in wireless networks. Wirel. Commun. Mob. Comput. 2005, 8, 927–932. [Google Scholar] [CrossRef]
- Misra, R.; Mandal, C. Minimum connected dominating set using a collaborative cover heuristic for ad hoc sensor networks. IEEE Trans. Parallel Distrib. Syst. 2010, 21, 292–302. [Google Scholar] [CrossRef]
- Jovanovic, R.; Tuba, M. Ant Colony Optimization Algorithm with Pheromone Correction Strategy for the Minimum Connected Dominating Set Problem. Comput. Sci. Inf. Syst. 2013, 10, 133–149. [Google Scholar] [CrossRef]
- Tang, Q.; Yang, K.; Li, P.; Zhang, J.; Luo, Y.; Xiong, B. An energy efficient MCDS construction algorithm for wireless sensor networks. Eur. J. Wirel. Commun. Netw. 2012, 2012, 83. [Google Scholar] [CrossRef]
- Mohanty, J.P.; Mandal, C.; Reade, C.; Das, A. Construction of minimum connected dominating set in wireless sensor networks using pseudo dominating set. Ad Hoc Netw. 2016, 42, 61–73. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhou, J.; Mo, Y.; Du, D. Performance-guaranteed approximation algorithm for fault-tolerant connected dominating set in wireless networks. In Proceedings of the IEEE International Conference on Computer Communications IEEE, San Francisco, CA, USA, 10–14 April 2016. [Google Scholar]




| Parameter | Value | Parametric Description |
|---|---|---|
| M | 100 × 100 | Rectangular network deployment area |
| r | 25–50 | Communication radius of each sensor node |
| n | 25–500 | Network size |
| d | 3–50 | Network density, Number of nodes/The unit area |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, X.; Yang, Y.; Ma, M. Minimum Connected Dominating Set Algorithms for Ad Hoc Sensor Networks. Sensors 2019, 19, 1919. https://doi.org/10.3390/s19081919
Sun X, Yang Y, Ma M. Minimum Connected Dominating Set Algorithms for Ad Hoc Sensor Networks. Sensors. 2019; 19(8):1919. https://doi.org/10.3390/s19081919
Chicago/Turabian StyleSun, Xuemei, Yongxin Yang, and Maode Ma. 2019. "Minimum Connected Dominating Set Algorithms for Ad Hoc Sensor Networks" Sensors 19, no. 8: 1919. https://doi.org/10.3390/s19081919
APA StyleSun, X., Yang, Y., & Ma, M. (2019). Minimum Connected Dominating Set Algorithms for Ad Hoc Sensor Networks. Sensors, 19(8), 1919. https://doi.org/10.3390/s19081919




