1. Introduction
Biometric verification technology has aroused a lot of interest due to its reliability, effectiveness, and convenience in verifying personal identity [
1]. Verification techniques based on face [
2], fingerprint, and some such physiological biometric attributes have brought extra convenience and changed our lifestyle [
3]. Although behavioral biometric attributes are slightly inferior to physiological ones in stability and uniqueness, they are more accessible and less intrusive to users. Voice, signature, gait, etc. are all typical behavioral attributes. Among them, signature remains the most widespread and recognized socially and legally verification approach in our day-to-day life [
4]. Signing is a customary and fast movement driven by long-term nervous system and writing habit. Therefore, signature verification techniques can have more potential applications in the real world.
Depending on the different methods of signature acquisition, signature verification technique can be split into two categories: offline and online. In the system of offline signature verification [
5], images containing signatures are collected after finishing the signing process. For online signature verification, signatures are captured by sensor-based devices while the user is signing and represented by a set of temporal functions, from which both static and dynamic features are extracted and then used to make a decision on whether the signature belongs to its claimed user. Compared with offline signature verification, the dynamic information collection of online signature ensures its uniqueness and higher difficulty to forge, so online signature verification technique usually owns better performance in accuracy and security.
There are two parts of an online signature verification system: enrolment and verification. Several signatures are provided as reference signatures by the users during enrolment and their extracted features along with calculated thresholds would be stored in the knowledge base. In verification, the authenticity of a test signature is evaluated by matching its features with those from reference signatures of its claimed user [
6].
Online signatures are collected by electronic devices such as tablets, smart phones, and so on. Most of them use sensors to capture various real-time data such as coordinates, pressure, timestamp, etc. during signing. After collection, the signatures are represented as time series and then undergo preprocessing and feature extraction modules successively.
Online signature verification methods can be categorized based on the feature extraction process and matching strategy [
7]. According to the employed features, there are broadly two groups: parametric and function features-based approaches. In the framework of parametric features-based methods, a signature is characterized as a vector of elements and each one is a representative of the value of one feature [
8]. Examples of such attributes are width, height, average speed, etc. The dimensions of parametric features of signatures are all equal. In the function features-based method, a signature is represented by a multi-dimension feature set constituted by several time functions. Coordinate, timestamp, pressure, etc. are commonly used function features. Generally, the function features-based approaches perform better due to more dynamic information application, but these kinds of method consume more computational time and memory.
With regards to the matching methods, distance-based and model-based approaches are two main techniques [
9]. Dynamic time warping (DTW) has been often adopted in distance-based methods [
10]. DTW is a well-known approach for aligning vectors of different lengths. For application in signature verification, a set of features at each sample point is extracted and the similarity between the test signatures and enrolled reference signatures is then computed using dynamic programming. Point-based warping technique is a variant of DTW, wherein only selective points are warped. Extreme point [
11] and stroke point [
12] are often used. In addition, some works make a fusion of DTW with other methods. Sharma and Sundaram [
9] propose a method that uses the information from DTW cost matrix and warping paths alignments. The decision is made by the conjunction of warping path score and DTW score. Yanikoglu and Kholmatov [
13] fuse the Fast Fourier Transform with DTW and the fusion system lowers the error rate by up to about 25%. Chen and Xia [
14] extract a set of function features for comparing the dissimilarity-based DTW between the test signature and the template database. In addition, the nearest template and majority vote are proposed to classify. Model-based approaches employ either generative-based classifiers such as hidden Markov model (HMM) [
15,
16,
17] or discriminative ones such as neural network (NN) [
18,
19,
20] and support vector machine (SVM) [
21,
22]. Also, there are some hybrid methods that combine different methods mentioned above. Multi-stage cascade framework [
23], multi-stage decision-level score fusion [
24,
25] or a multi-expert system for signature verification [
26,
27] have been reported in the literature. Recently, inspired by the great success of recurrent neural networks (RNNs) in sequential modeling, several verification methods based on RNNs are proposed. Lai et al. [
28] propose a novel descriptor called the length-normalized path signature (LNPS) for feature representation and then features are fed into the GRU (Gated recurrent unit) network. Triplet loss and center loss were used to train the network with the BP algorithm. The method proposed in [
29] extracts 23 hand-crafted time function features and uses the bidirectional LSTM (Long short-term memory) and GRU networks with Siamese architecture to learn a dissimilarity metric from the pairs of signatures.
Although it is not that easy for a forger to fake a signature that is exactly the same as the genuine one, due to the large intra-class variations from one person and small inter-class variations between forgeries and genuine ones, accurate online signature verification still remains a challenging problem.
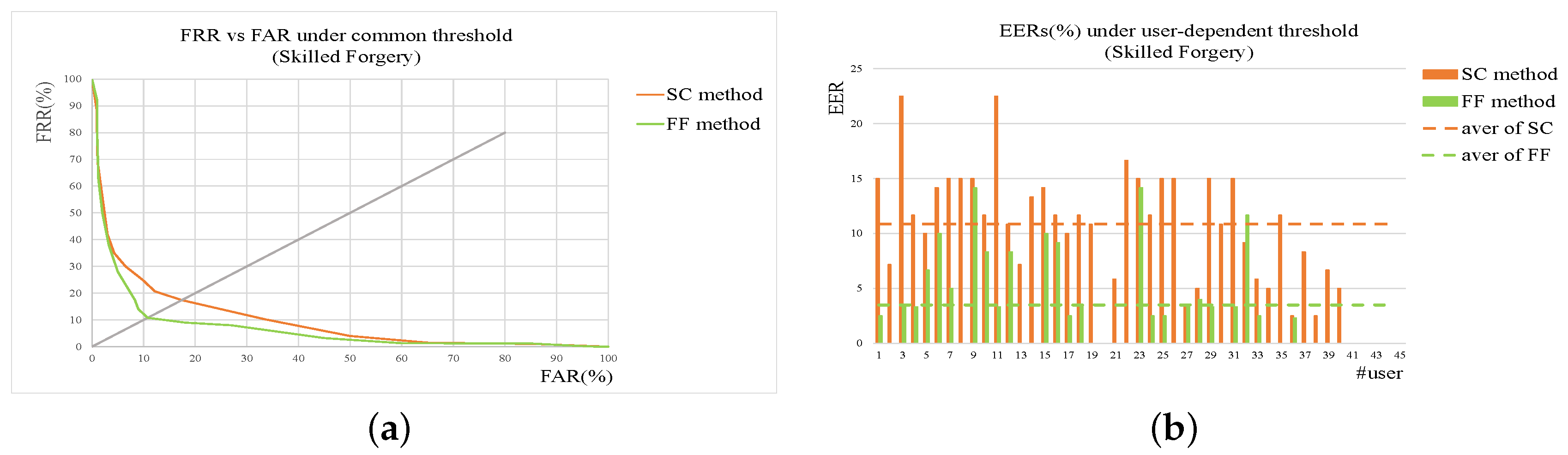
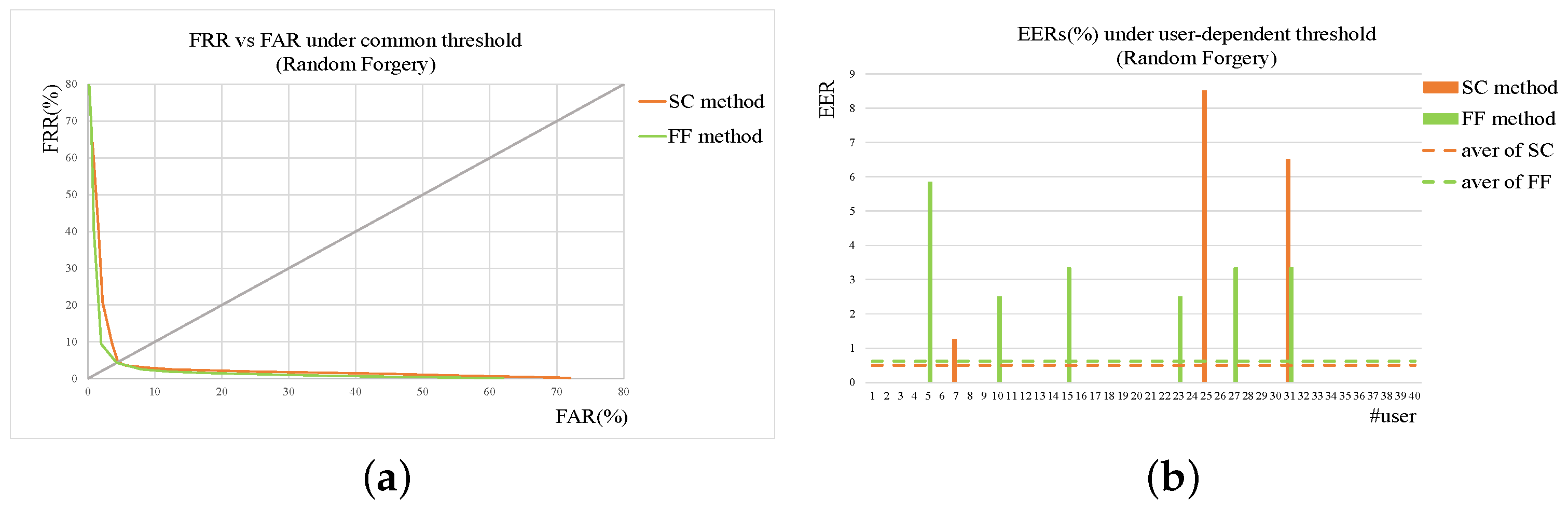
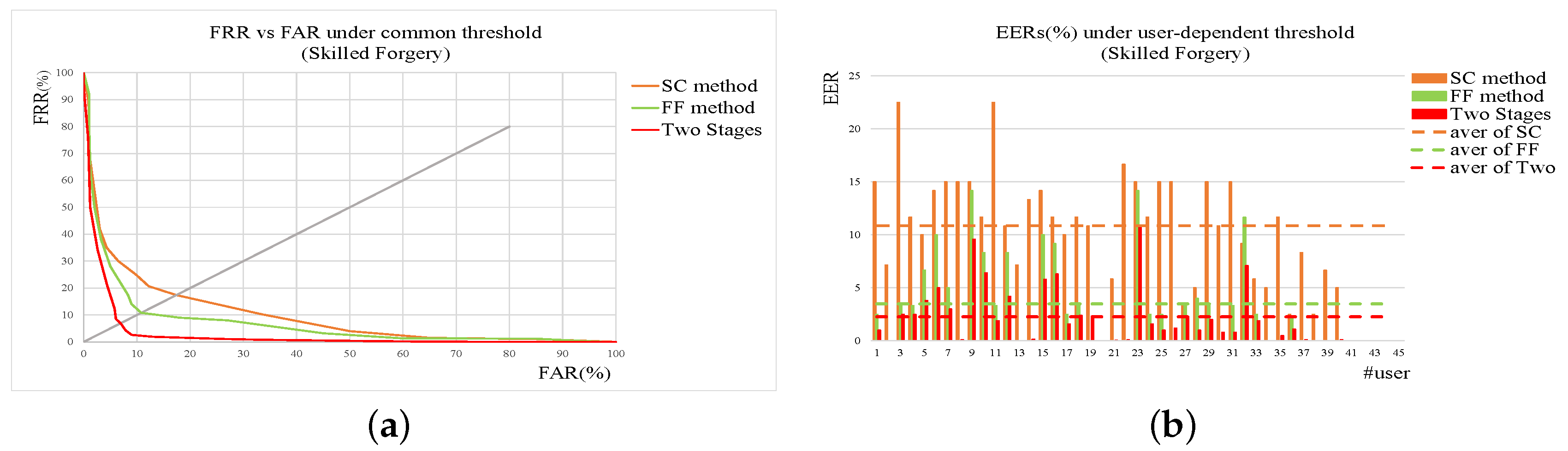
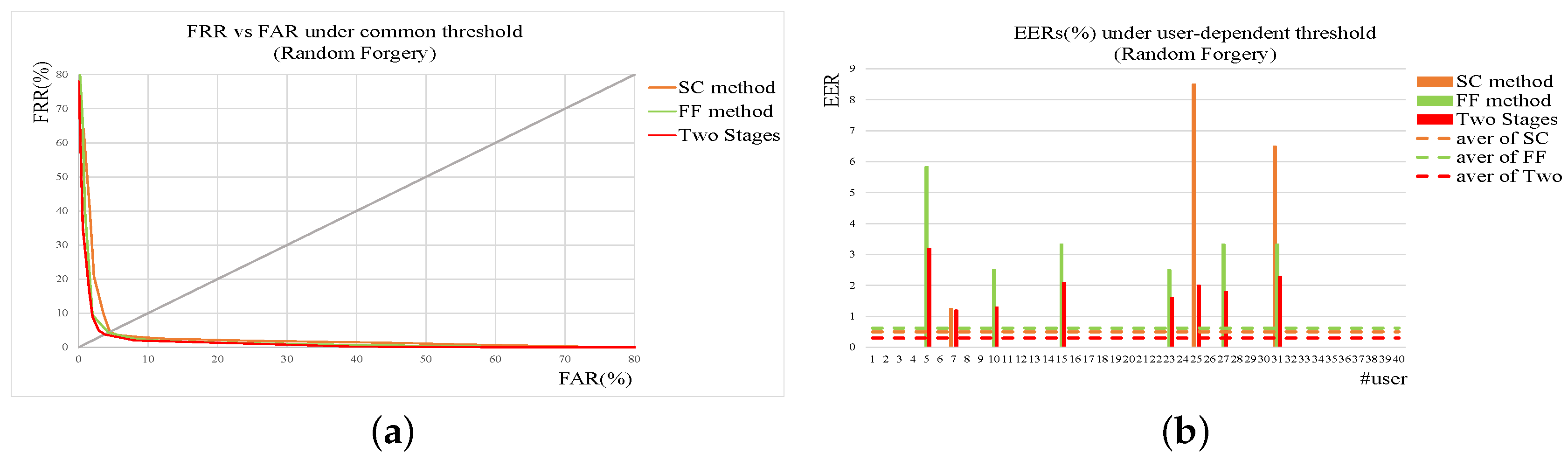
In real applications, the forgeries are usually classified to be two types, named skilled forgery and random one. A skilled forgery is signed by a person who had access to the genuine signatures and practiced for a while. A random forgery is signed without with any information about the signature, or even the name of the person whose signature is forged [
30]. Compared with skilled forgeries, the random forgeries are more common in our daily life. Obviously, the skilled forgeries are more difficult to verify. In addition, the loss brought by accepting forgeries is higher than that by rejecting genuine signatures, which means accepting a signature as genuine should be stricter. Considering these factors, we propose a two-stage method using shape contexts and function features for accurate online signature verification. Features of shape contexts are extracted from the input firstly and classification of this stage is based on shape distance metric. Only the inputs passing by the first stage are represented by a set of function features and verified. To improve the matching accuracy and efficiency, we employ a shape context-dynamic time warping (SC-DTW) to compare the test signature with the enrolled reference ones based on the extracted function features. An interval-valued symbolic representation-based classifier is proposed to decide if the test signature is a genuine one.
The contributions of this paper are as follows:
Based on the fact of unbalanced occurrence probability of skilled signature forgeries and random ones, a fast and accurate two-stage verification method is proposed.
Shape context feature extractor is designed to describe global shape characteristics of signature for fast classification of random forgeries.
SC-DTW is applied to fulfill comparison task and interval-valued-based representation classifier is proposed for final decision-making to achieve state-of-the-art verification performance.
This paper is an extended version of the one published in proceedings of PRCV2018 [
31]. In this paper, more details on feature extraction and matching methods are given. Moreover, to further improve the performance method in the paper of PRCV2018, more effective features are extracted. Instead of distance metric classification, an interval-valued symbolic representation-based classifier is employed to enhance classification ability. Besides, more detailed experimental results are reported.
The rest of this paper is organized as follows.
Section 2 details the methodology we proposed. Signature preprocessing is presented in
Section 2.1.
Section 2.2 presents the shape context descriptor and online signature verification method based on it. The function features extraction, feature alignment, and symbolic classifier are showed in
Section 2.3.
Section 2.4 discusses the two-stage verification protocol. The database used in our experiment, experimental results, and performance analysis are provided in
Section 3. The conclusion is offered finally in
Section 4.
2. Methodology
The diagram of the proposed method is shown in
Figure 1. The input signature is first preprocessed for smoothing and normalization, and then it is fed into the shape context-based verification module, which does well in quickly distinguishing the random forgeries owing to their manifest differences in shape. Most obvious forgeries can be rule out in this stage. The signature passed through the first module is verified by function features-based verification module. This module achieves more accurate verification results due to the application of details in signature and decision fusion by interval-valued symbolic representation-based classifier.
2.1. Preprocessing
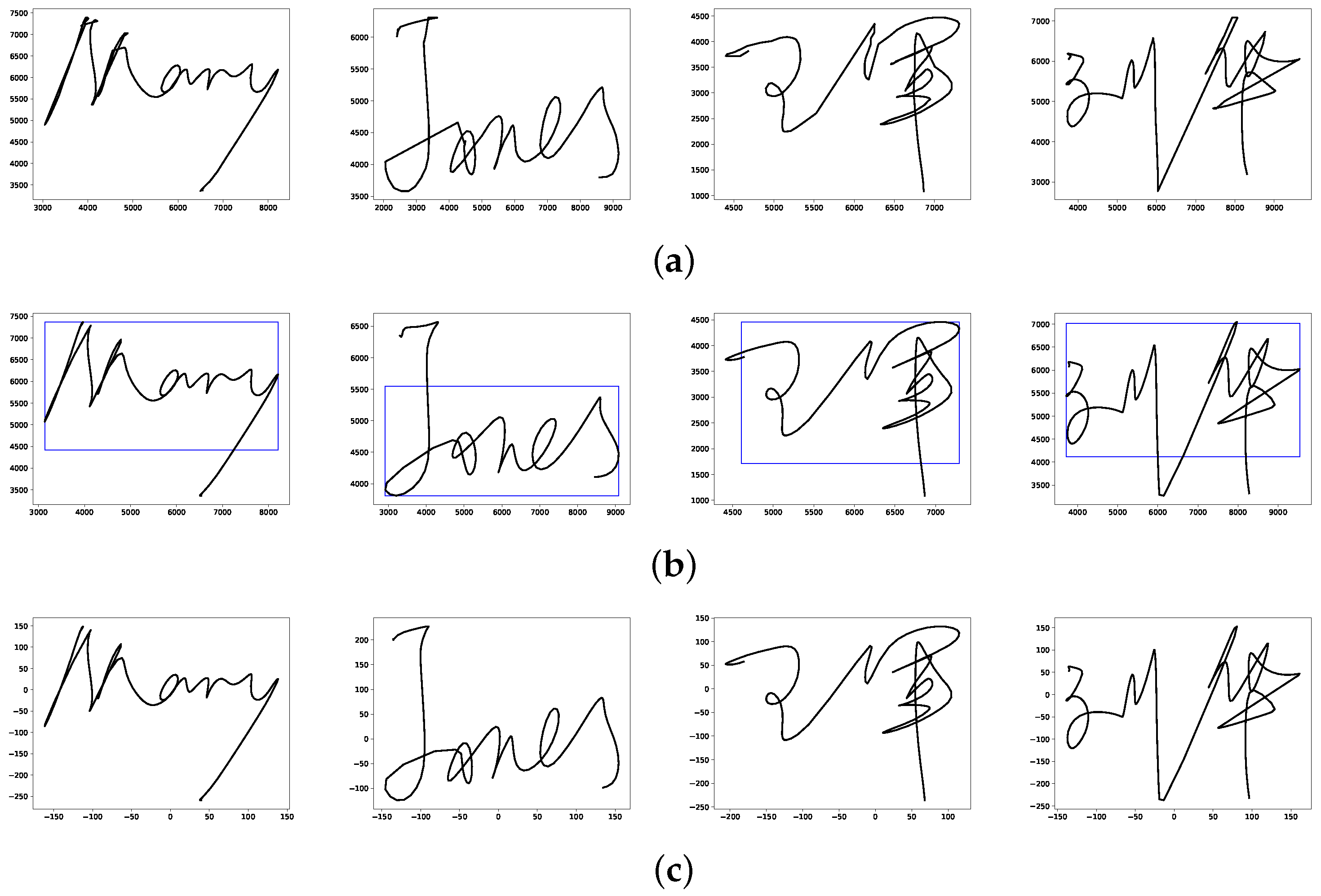
Captured by electronic devices, the time series of a signature are mixed with noises and fluctuations unavoidably. In addition, the acquired signatures of one individual vary with time or places, with the result that there are differences in size and location between signatures. Therefore, we firstly let the acquired signatures pass the preprocessing module to address those issues. The preprocessing module includes smoothing and normalization. Gaussian smoothing is employed to filter the artifacts and smooth the data. Then we adopt moment normalization technique [
32] to standardize the size and location of acquired signatures.
Set the signature as , . N is the number of sample points, is x and y coordinates information.
In the moment normalization technique, the size of a signature is not the difference between maximum and minimum in horizontal and vertical directions, but the width and height of the window derived from its moment, as is show in
Figure 2. Denote the width and height of window as W and H, given by
denotes the center moment, and
denotes the signature’s centroid.
After window calculation, the size normalization technique is implemented as follows. The heights of the signatures are normalized to a predetermined value that in this paper is 300. Moreover, the aspect ratio of before and after preprocessing remains consistent to keep the signature shape unchanged.
where
x and
y are smoothed originate coordinates.
and
are normalized coordinates.
and
are the centroid of normalized signature.
and
are the ratio of the normalized signature size to its original size, given by
where
and
denote the normalized width and height.
Signatures are centered at (0, 0) to normalize their locations. After preprocessing, the signatures have the same size and location. In this paper, we did not employ translation normalization since we believe signature’s angle is an out-of-habit feature.
Figure 2 shows some examples of original signatures and corresponding preprocessed signatures.
2.2. Shape Context-Based Online Signature Verification
In the methods proposed for online signature verification, the dynamics properties of the signatures, for example, velocity, pressure, acceleration, etc. are widely applied. However, the shape of signature contains very useful details, which is critical for distinguish a signature between forgery and genuine one. The method proposed by Gupta and Joyce [
33] extracts the dynamics properties of position extreme points of signatures and achieved better performance. Features based on shape also have been successively applied in offline signature verification [
34].
In this paper, we propose a verification method based on shape context features. Specifically, shape context descriptor [
34,
35] is used to extract features of a signature and a cost matrix is computed. After finding the best one-to-one matching between two signatures’ shape and modeling transformation, the measurable shape distance is used for classification. To further improve the efficiency, only trend-transition-points (TTPs) that can represent the shape of a signature roughly are used for calculating distance.
2.2.1. Shape Context Feature Extraction
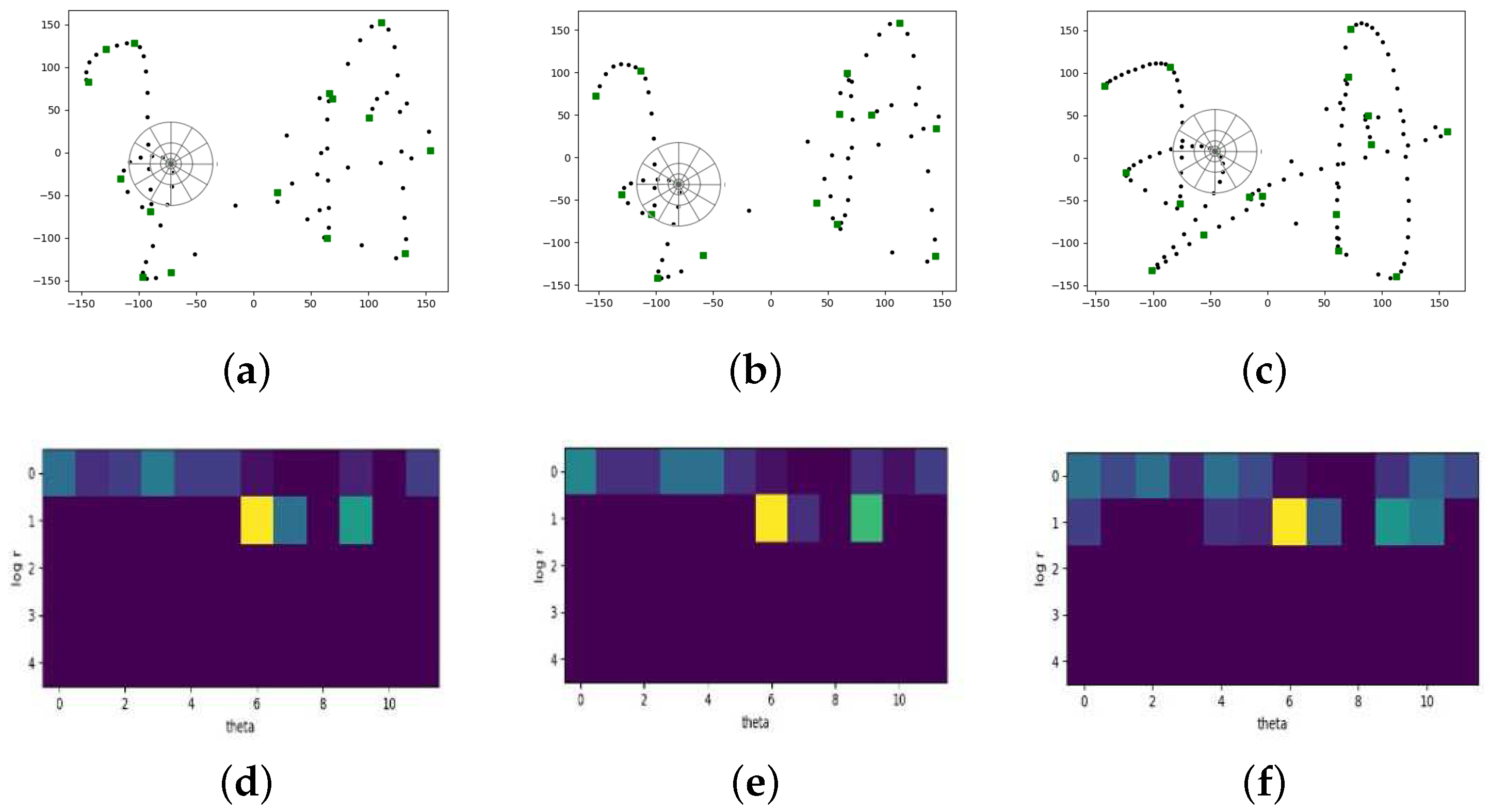
Shape context descriptor captures the distribution over relative positions of shape points and the connectivity properties between features points along curves. Therefore, shape context features not only provide global characterization of shape but also contain more contextual information within a certain range of a signature. Besides, shape context descriptor is designed in a way of describing shapes that allows for measuring shape similarity and the recovering of point correspondences. Traditionally, the first step is to randomly select a set of points that lie on the edges of two shapes separately. Here the shape of an online signature is represented by a set of sampled points which in this work is , . N is the number of sampled points.
Figure 3 shows the shapes and shape context histograms of a reference signature, a genuine signature and a skilled forgery of one user. Because the writing speed is a kind of relatively fixed and unique information, the number and distribution of sample points between genuine signature and reference signature are more similar. Taking one point as the origin of polar coordinate, the shape contexts of this point can be represented using log-polar histogram. We set five bins for
and 12 bins for
. The number of neighboring points that fall into the very bin is just the histogram value.
Figure 3d–f present the corresponding histograms for certain points. We can see that the difference in shape context histograms between genuine signature and reference signature is relatively small, while the histogram of skilled forgeries is quite dissimilar to the reference ones.
Considering a point
on the first shape and a point
on the second shape, denote
as the matching cost of these two points, given by
where
and
denote the
bin histogram at
and
respectively.
For all pairs of points
on the first shape and
on the second shape, calculate the cost as Equation (
5) and then we got a cost matrix. The next step is to find the optimal alignment between two shapes that minimizes total cost. This can be done by the Hungarian method with time complexity of
. The cost between shape contexts is based on the chi-square test statistic that is not a suitable distance metric. Thin plate spline (TPS) model is adopted for modeling transformation [
35]. After that, we get the measurable distance of two shapes. The smaller the distance, the more similar these two shapes, or vice versa. So, if the average distance between test signature and reference signatures is lower than a threshold, it would be accepted as a genuine signature of its claimed user.
2.2.2. Trend-Transition-Point Selection
The shape context representation of signature should not only capture specific shape features but also allow considerable variations. Besides, the computational load of distance calculation is closely related to the number of points. Therefore, with the hope of efficiency improvement and variances tolerance, a few representative points are selected. Only selected points can participate in shape distance calculation. In this paper, we propose the TTP selection method.
Trend-transition-points are the points where the curve trends before and after them are completely different while the trends between two successive TTPs do not have obvious change so that the curve shape of the segment approximates to a straight line. So, the signature could be re-constructed with these points. In our method, local extreme points and corner points are all defined as TTPs. The local extreme points are selected depending on its value greater or smaller than its neighborhood. The corner points selection we adopted is proposed in [
36,
37], which makes use of the smaller eigenvalues of covariance matrices of regions of support.
Let
denotes the region of support (ROS) of point
, a small curve segment containing itself and
k points in its left and right neighborhoods. That is
where
are the Cartesian coordinates of
.
Therefore, the covariance matrix for points in the segment is calculated. and are two eigenvalues corresponding to the covariance matrix. The smaller eigenvalues can be used to measure prominence of corners over its ROS. In other words, sharper corner points have the large and weaker corners have small one. When the points are on a straight line or on a flat curve, the will be very small, even approximate to zero. So, corners can be determined if its exceeds a predetermined threshold.
Shape contexts are calculated on every point, but only TTPs are used to distance calculation. For every sample point of signatures, the algorithm is implemented as follows.
- Step 1:
If the point is a start point, add it to TTP dataset. Else, go to Step 2;
- Step 2:
If the point is an end point, add it to TTP dataset and go to Step 5. Else, go to Step 3;
- Step 3:
If the point is an extreme point, add it to TTP dataset. Else, go to Step 4;
- Step 4:
If the point is a corner point, add it to TTP dataset. Else, head to next sample point and return to Step 2;
- Step 5:
For all points in TTP dataset, the point with smaller would be deleted when the distance of two successive points is lower than a threshold. The process repeats several times until the distances between points are long enough.
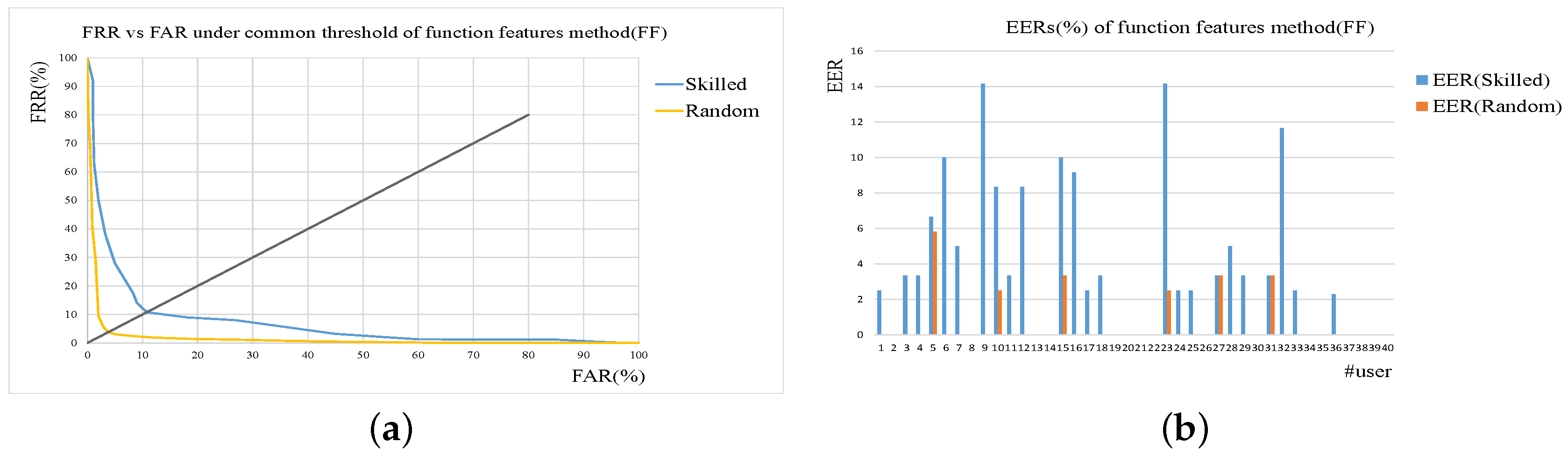
2.3. Function Features-Based Online Signature Verification
One of the advantages of online signature verification is that signature is captured by specialized sensors-based devices. So dynamic information can be recorded and used for verification, which makes verification more accurate and reliable. In function features-based methods, a set of function features, such as position, pressure, velocity, acceleration, etc., is firstly captured. Then matching between features of the test and the reference and decision-making are implemented.
2.3.1. Function Features Extraction
Usually, lots of features can be obtained directly from the specialized electronic devices. Horizontal and vertical position, pressure and timestamp of each sample point are the basic measurements. Let
be the mentioned basic measurements,
be the discrete time index of the temporal functions and
N be the time duration of a signature in sampling units [
14]. Based on them, various features can be derived. Among them, 20 frequently used function features are selected. The features are grouped according to their properties, such as position-related, pressure-related, velocity-related, acceleration-related, and angle-related. The features are listed in
Table 1.
2.3.2. Matching Based on Shape Context-Dynamic Time Warping (SC-DTW)
Feature matching is very critical for function features-based verification. In recent years, DTW has been widely applied as the matching technique in online signature verification. The DTW method compress or expand the time axis of two temporal functions locally to make them aligned.
Here are two time series
and
and their lengths are N and M respectively. The similarity between the
point of
T and the
point of
R are calculated according to defined similarity rule. All the similarity values constitute a DTW cost matrix denoted by
defined as:
The overall distance is calculated as following equation:
where
is the cumulative distance up to the current element and C is gap cost. To alleviate the situation of signature at different length, the distance is normalized by Equation (
8).
DTW has been an effective method of finding the alignment between two signatures with different length. However, a time series has both numerical nature and shape nature. DTW warps time series depending on the similarity of their numerical characteristics as Equation (
6) but ignores the shape properties. It may lead to abnormal alignment sometimes. Zhang and Tang [
38] propose a novel variant of DTW, named SC-DTW. The SC-DTW employs shape context to replace the raw observed values used in conventional DTW, getting ahead in time series data mining. In this paper, we adopted the SC-DTW for function features-based verification to further improve the accuracy.
Specifically, the alignment of two point is decided by their shape matching cost of shape contexts, which means
where
is defined in Equation (
5).
Under this circumstance, a function feature is considered to be a 1-D array and a 2-D shape. The problem of measuring the similarity of two function features can be translate into how similar these two shapes.
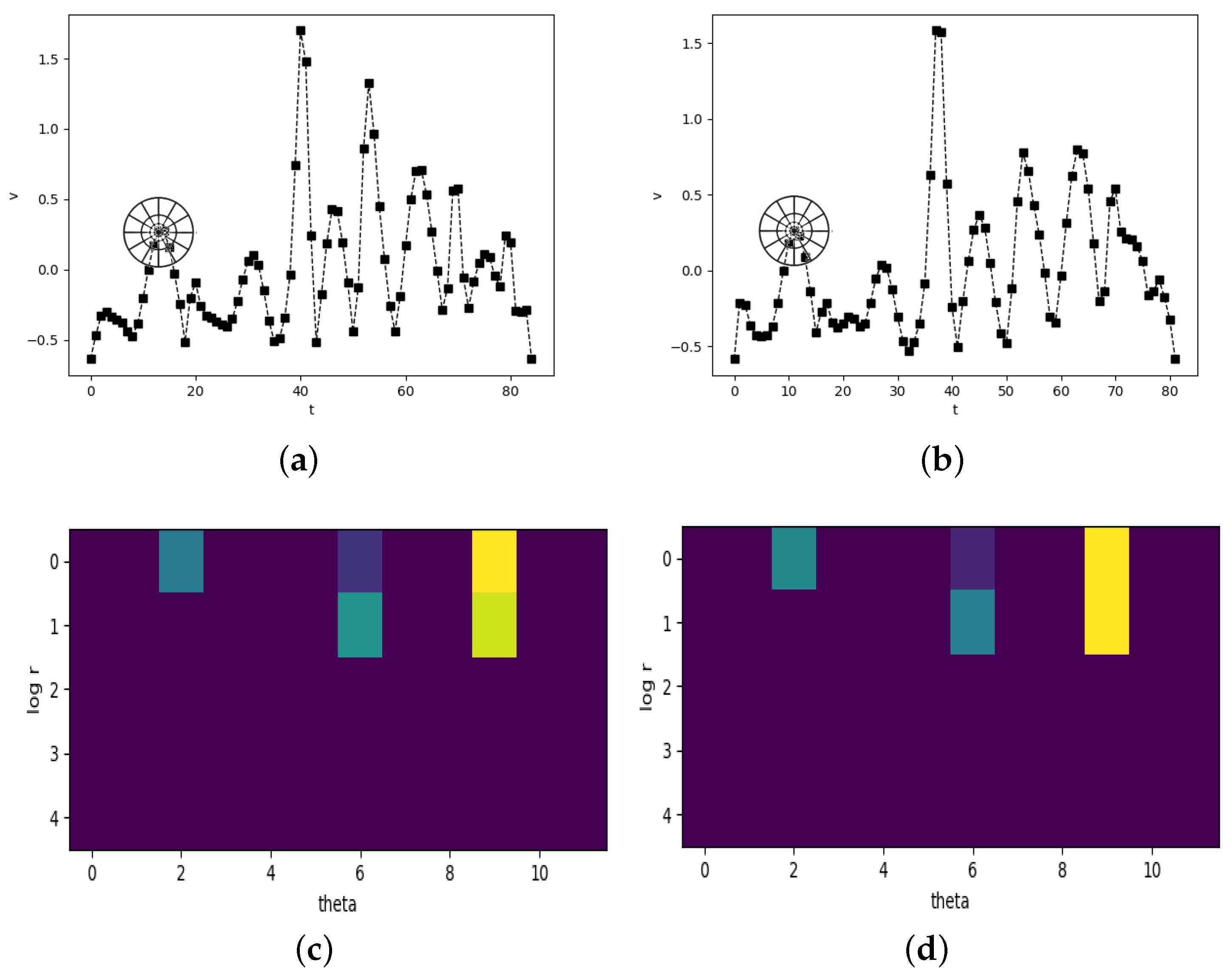
Figure 4 shows the process of SC-DTW.
Figure 4a,b are the time series of
function feature
v listed in
Table 1 of two signatures from the same user.
Figure 4c,d are the corresponding shape context histograms. That the shape context is similar means the sample points in time series are well matched. Please note that the application of shape contexts is only used to find the alignment between two time series. The measurable cumulative distance of them is still obtained by the original cost matrix for the convenience of following classification.
Given a feature set , extracted from a reference signature and a feature set , extracted from a signature which is claimed to belong to the same user, a D-dimensional vector called ’similarity feature vector’ can be derived by calculating the similarity between each pair of corresponding function features using SC-DTW mentioned above.
2.3.3. Classification Based on Interval-Valued Symbolic Representation
The concept of symbolic data analysis has been applied in the field of document image analysis and cluster analysis. Interval-valued and histogram-valued symbolic representation can represent the variability and distribution of feature values. Guru and Prakash [
39] extract global features of signature to form an interval-valued feature vectors and proposed a method for verification and recognition based on the symbolic representation. Pal and Alaei [
5] also propose an interval-valued symbolic representation-based method for offline verification. In this paper, we first use the interval-valued symbolic representation to model the similarity features derived from SC-DTW and then build a classifier for verification.
Let
be a set of
n enrolled reference signatures of user. In addition, denote
D as the similarity feature vector of an user, where
is the SC-DTW distance of feature
r between signature
and
, as is showed in
Table 2. Each user has a feature vector like that. For the
feature, we compute the statistical mean
and standard deviation
and the lower and upper bound of interval value can be computed as Equation (
10).
where
is the symbolic representation of
feature of a user and includes an interval value and two continuous values.
is a scalar to control the upper and lower limit of each feature. In addition, the symbolic feature vectors are computed for all users and stored in the template base for future verification.
For signature verification problem, the signature is compared with all the reference signatures belonging to the claimed ID. Let
denote a D-dimensional feature vector representing the average SC-DTW distance with reference signatures. In addition, denote
as the reference signatures of the claimed identity described by an interval-valued symbolic feature vector. Each feature value of the test signature is compared with corresponding interval in
to examine whether it lies within the interval. The feature value represents the dissimilarity of two signatures. That is, the more similar the two signatures, the smaller the value and the closer to 0. The total value of features of a test signature which fall inside the interval value decides how this test signatures is similar to genuine ones, as is showed in Equations (
11) and (
12). Define
A as the measure of measure of degree of authenticity:
where
If the acceptance count A is greater that a threshold , the test signature will be classified as a genuine signature of its claimed user. In the user-dependent scenario, every person has its own A which is computed using those training samples. For each training signature, there is an A we got. For each person, we compute several A and then average them thus getting . The threshold equals to .
2.4. Two-Stage Online Signature Verification
The forgery can be classified to be two types, named skilled forgery and random one. In real applications, random forgeries appear more frequently while skilled forgeries occur less. On the other hand, skilled forgeries are much more difficult to be verified correctly. In this paper, we propose a method using shape contexts and function features as well as a two-stage strategy for accurate online signature verification. The shape context-based verification module is firstly used to reject obvious random forgeries quickly while the function features-based verification module is applied to re-check the signatures survived from the previous module. In this way, the whole system can achieve higher accuracy and consume less computation cost at the mean time.
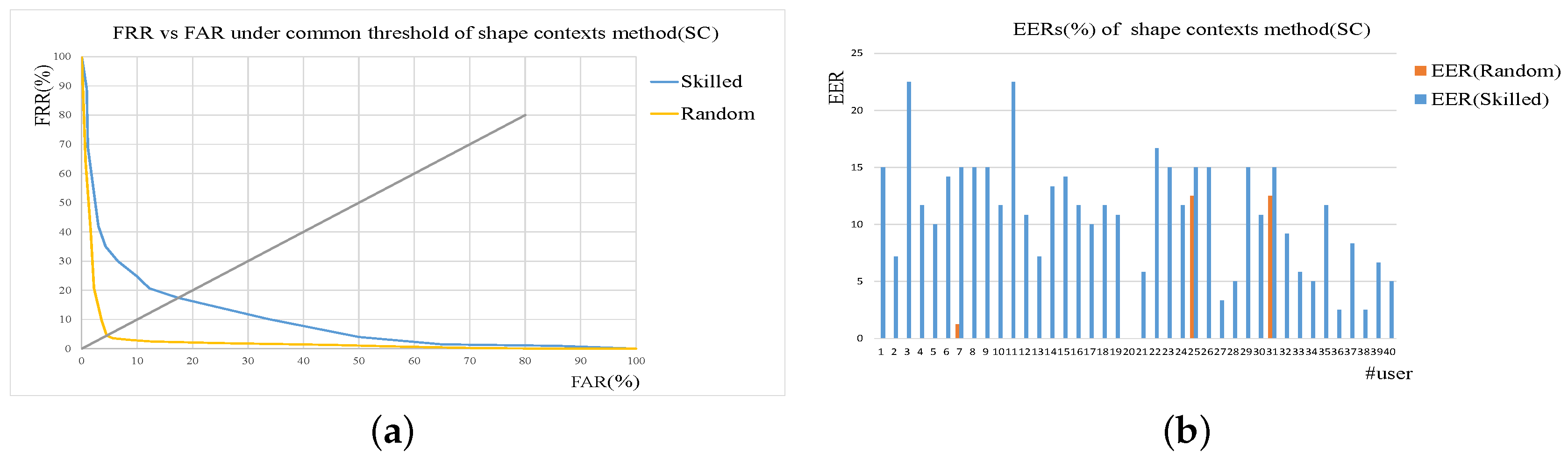
Two metrics named FRR (False Reject Rate) and FAR (False Accept Rate) have been widely used to evaluate signature verification system. For cascade structure applied in our method, the relationship of FRR and FAR between the sub-verification modules and the whole system are showed in
Table 3, where
p denotes the reject percentage of first sub-verification module. Obviously,
p takes the value smaller than 1.
It can be seen that the performance of the cascade system depends on the thresholds of two sub-verification modules. If
and
is set to be smaller than
, the cascade system can achieve better performance than the sub-verification modules in terms of false acceptance rate, which is illustrated in Equation (
13).