An Effective Spectrum Handoff Based on Reinforcement Learning for Target Channel Selection in the Industrial Internet of Things
Abstract
1. Introduction
- (1)
- We propose an SH scheme that separates spectrum sensing, profiling, sorting, and ranking of target channels from channel-switching time of CR user, this approach minimizes the channel-switching delay.
- (2)
- We propose a network model that achieves low latency by introducing a gateway that only performs the spectrum sensing function (SSF) to eliminate the time spent in spectrum sensing from channel-switching time.
- (3)
- We introduce RL into the design of the proposed CSS to improve the quality of channels selected for an SH to reduce avoidable SHs and to improve throughput performance of the network.
- (4)
- We use a masking method to mitigate the curse of dimensionality to reduce the convergence of the Q-learning algorithms. Then we develop a BCL to prevent collision between multiple CR users attempting to use the same channel, this improves the throughput performance of our approach.
2. Related Works
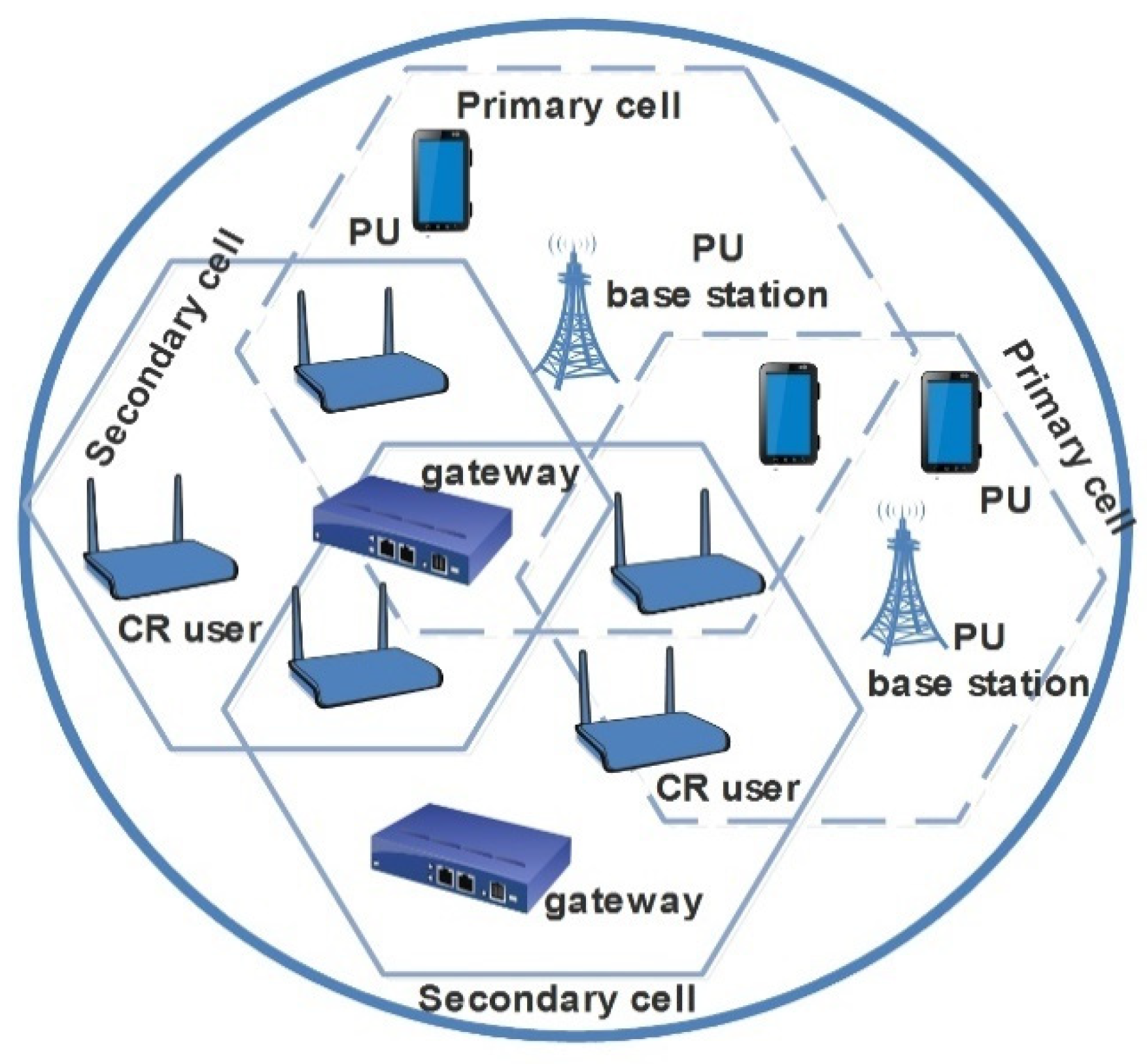
3. System Model
3.1. Assumptions
3.2. Network Model
3.3. Channel Modelling
4. Design of the Proposed Scheme
4.1. Selecting Channels for the CCL
4.2. Integrating Two Reinforcement Learning Algorithms to Perform Channel Selection
4.3. Historical Occupancy Learning
4.4. Channel Conditions Learning
4.5. Sorting and Ranking of Channels
| Algorithm 1 Selecting and ranking the CCL | |
| 1 | |
| 2 | |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 | |
| 8 | |
| 9 | |
| 10 | |
| 11 | |
| 12 | |
| 13 | |
| 14 | |
| 15 | |
| 16 | Compute Score using Equation (10) |
| 17 | |
| 18 | |
4.6. Dimensionality Reduction for Learning Convergence
| Algorithm 2 Reducing state dimension | |
| 1 | Let denotes the Q-table used to store the computed Q-values obtained from Q learning. |
| 2 | Let S-table store the state values for the state from Q learning. |
| 3 | Let which is a matrix represents a snapshot of the S-table at the th learning episode, where is the number of data samples in , and is the dimension of . |
| 4 | Let matrix represents only linearly independent state dimension which are relevant to the task learning. |
| 5 | Initialize matrix to an empty set. |
| 6 | Select and remove which is a linearly dependent and irrelevant state element of the task learning from |
| 7 | If zero eigenvalues of the matrix exist, then is linearly independent with matrix . |
| 8 | Insert into matrix . |
| 9 | Repeat steps (6) to (8) until X is empty |
4.7. Creating BCL for Each CR Users in the Network
4.8. Conditions for Spectrum Handoff
4.9. Decision Making
| Algorithm 3 Conditions and decision for SH | |
| 1: | Compute the Received Power of the Channel, |
| 2: | Obtain the Channel Quality Index, using Equation (13) |
| 3: | |
| 4: | |
| 5: | |
| 6: | to target channel, obtained from Algorithm 1 |
| 7: | |
5. Simulation Setup
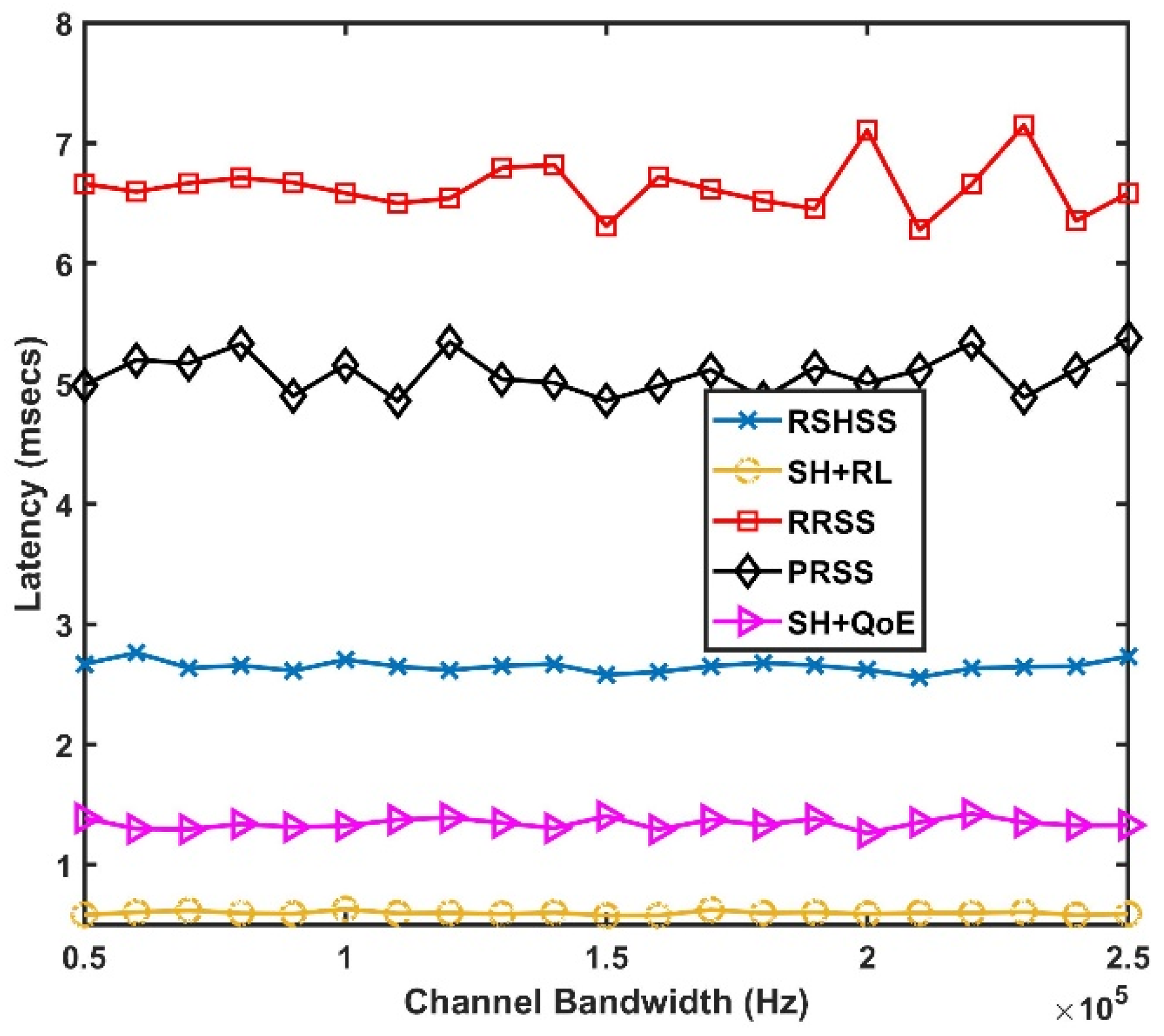
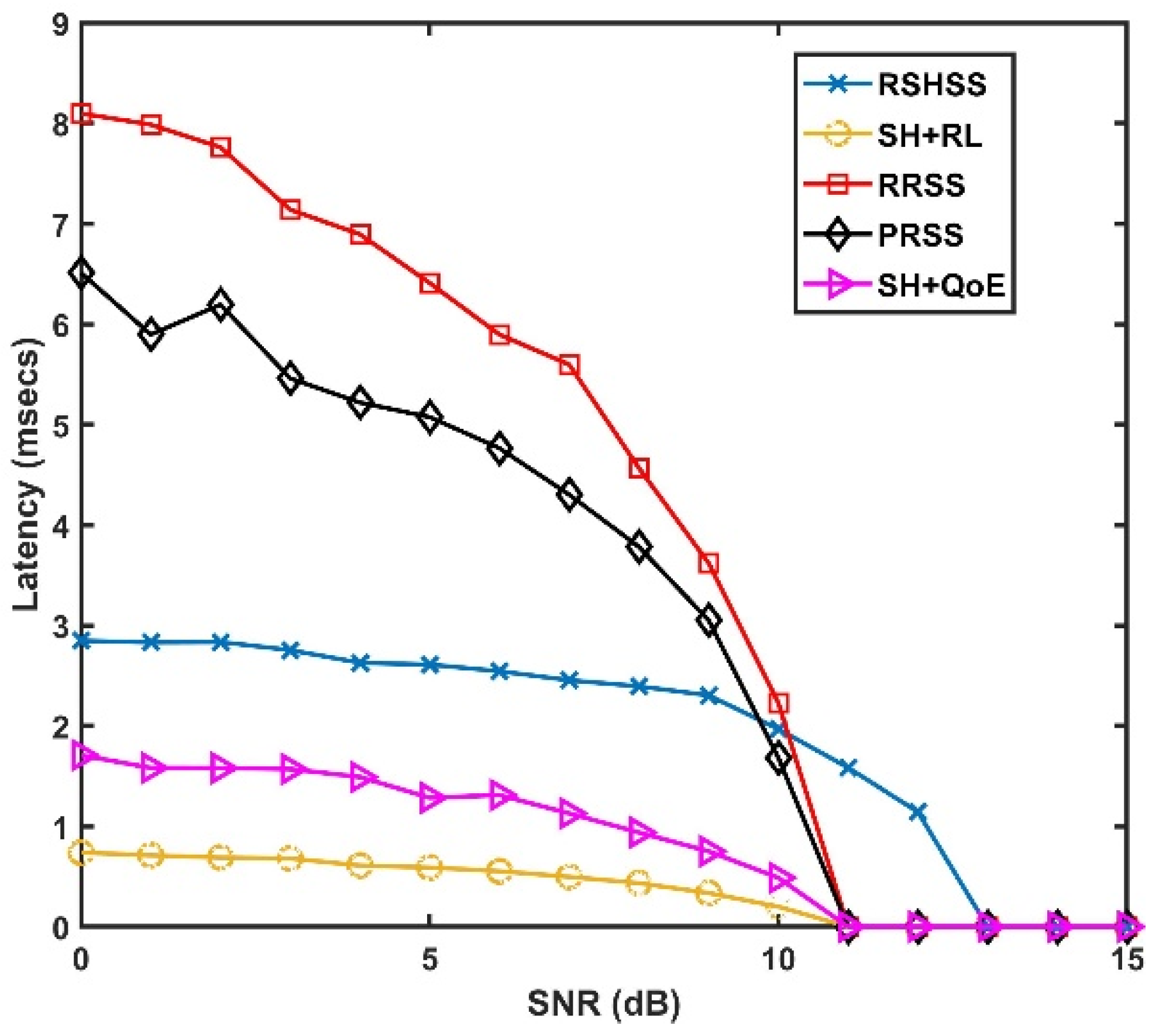
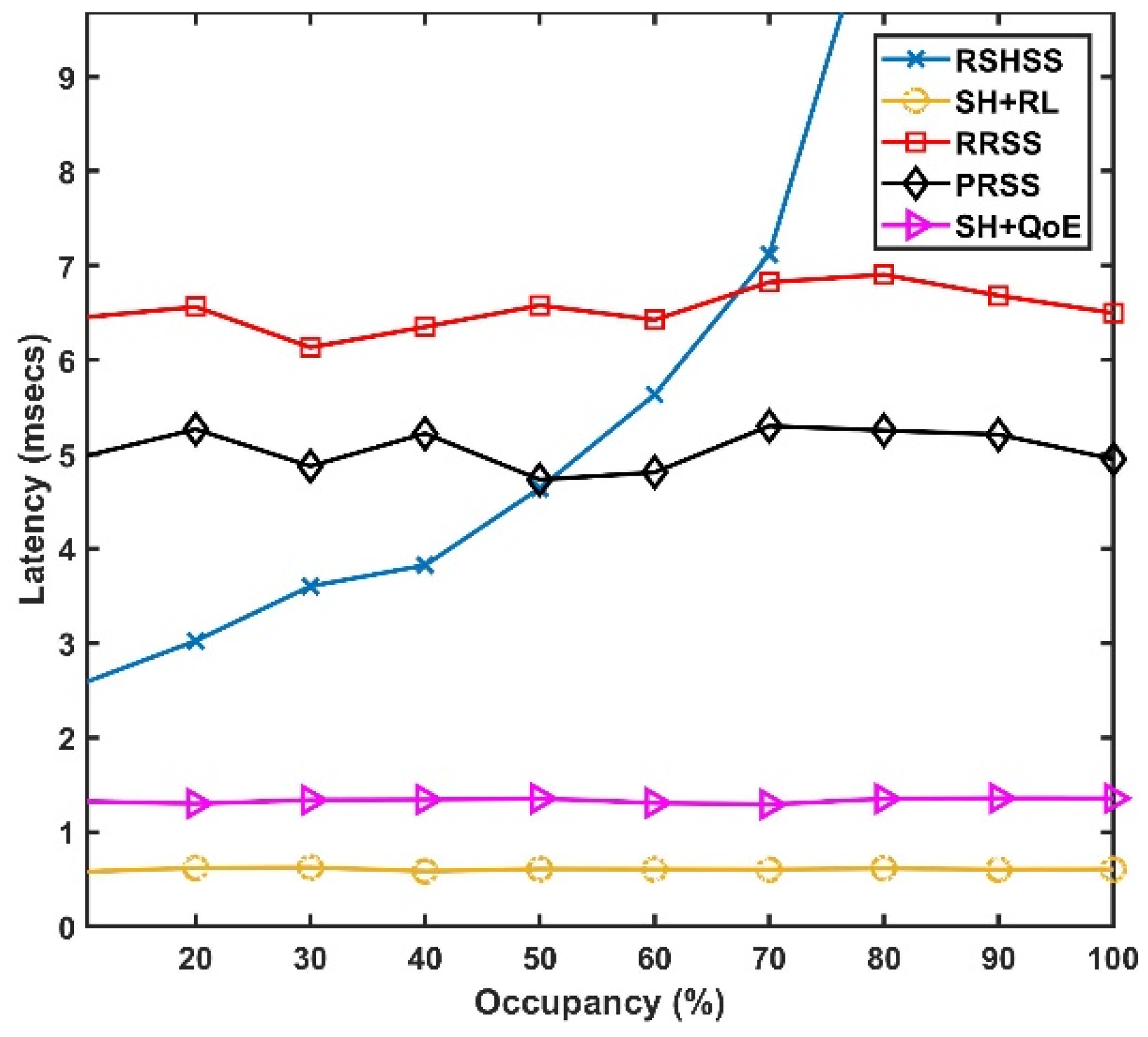
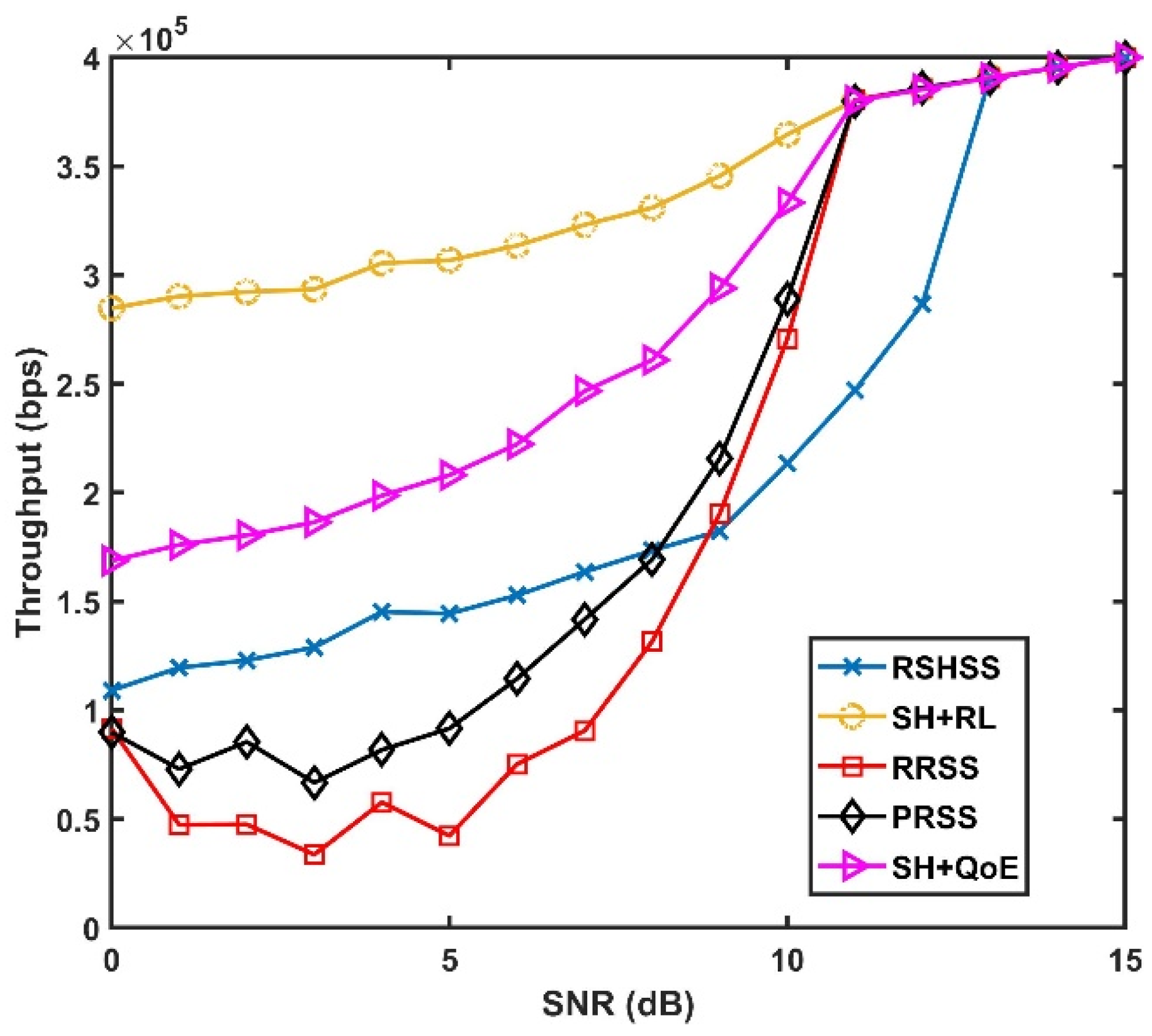
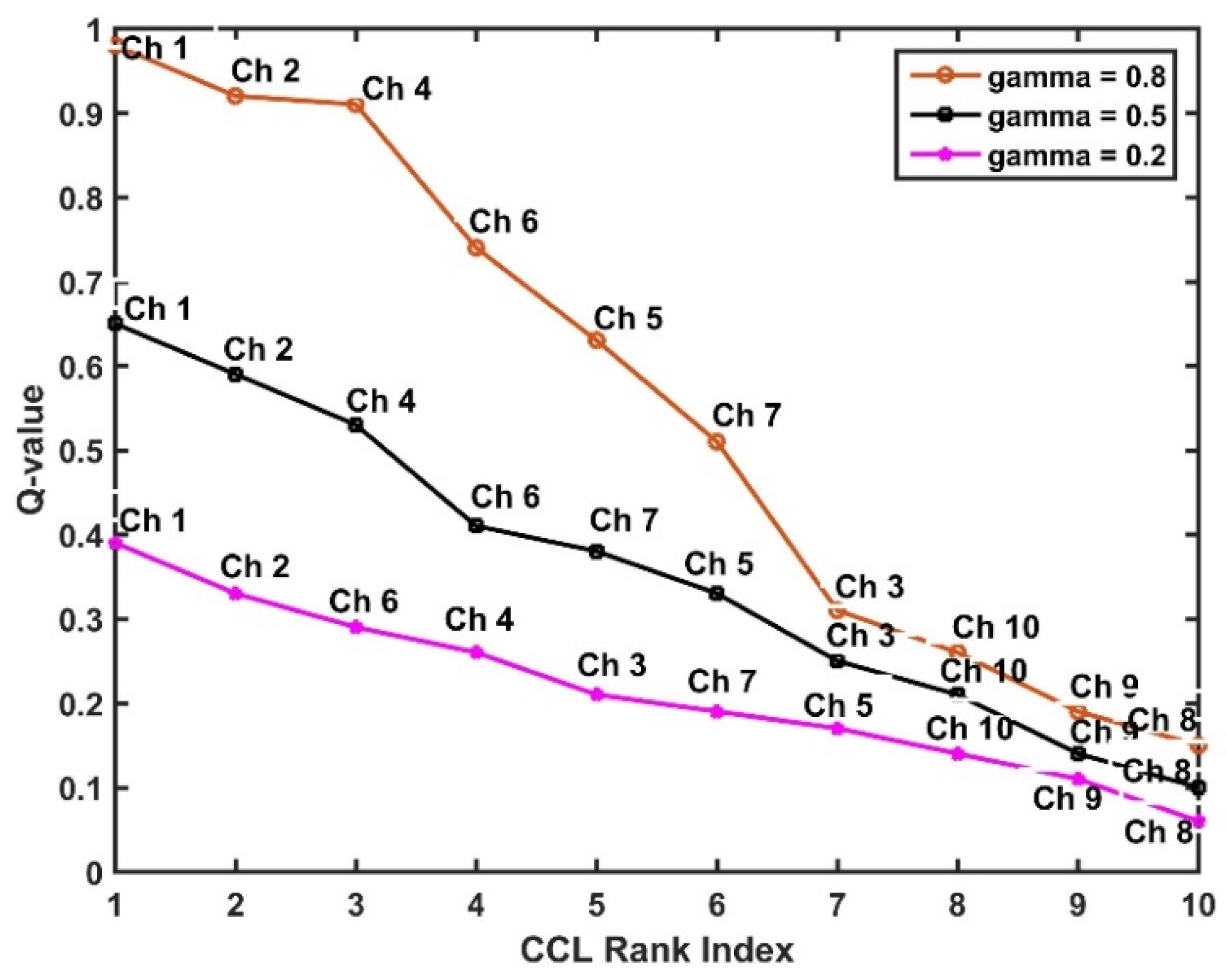
6. Simulation Results
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kurunathan, H.; Severino, R.; Koubaa, A.; Tovar, E. IEEE 802.15. 4e in a Nutshell: Survey and Performance Evaluation. IEEE Commun. Surv. Tutor. 2018, 20, 1989–2010. [Google Scholar] [CrossRef]
- Nkomo, M.; Hancke, G.; Abu-Mahfouz, A.; Sinha, S.; Onumanyi, A. Overlay Virtualized Wireless Sensor Networks for Application in Industrial Internet of Things: A Review. Sensors 2018, 18, 3215. [Google Scholar] [CrossRef] [PubMed]
- Wollschlaeger, M.; Sauter, T.; Jasperneite, J. The future of industrial communication: Automation networks in the era of the internet of things and industry 4.0. IEEE Ind. Electron. Mag. 2017, 11, 17–27. [Google Scholar] [CrossRef]
- Perera, C.; Liu, C.H.; Jayawardena, S. The emerging internet of things marketplace from an industrial perspective: A survey. IEEE Trans. Emerg. Top. Comput. 2015, 3, 585–598. [Google Scholar] [CrossRef]
- Oyewobi, S.S.; Hancke, G.P. A survey of cognitive radio handoff schemes, challenges and issues for industrial wireless sensor networks (CR-IWSN). J. Netw. Comput. Appl. 2017, 97, 140–156. [Google Scholar] [CrossRef]
- Sun, Y.; Song, H.; Jara, A.J.; Bie, R. Internet of Things and Big Data Analytics for Smart and Connected Communities. IEEE Access 2016, 4, 766–773. [Google Scholar] [CrossRef]
- Rodriguez, P.M.; Val, I.; Lizeaga, A.; Mendicute, M. Evaluation of cognitive radio for mission-critical and time-critical WSAN in industrial environments under interference. In Proceedings of the 2015 IEEE World Conference on Factory Communication Systems (WFCS), Palma de Mallorca, Spain, 27–29 May 2015; pp. 1–4. [Google Scholar]
- Rodriguez, P.M.; Lizeaga, A.; Mendicute, M.; Val, I. Spectrum Handoff Strategy for Cognitive Radio-Based MAC for Real-Time Industrial Wireless Sensor and Actuator Networks. Comput. Netw. 2019, 152, 186–198. [Google Scholar] [CrossRef]
- Akpakwu, G.A.; Silva, B.J.; Hancke, G.P.; Abu-Mahfouz, A.M. A Survey on 5G Networks for the Internet of Things: Communication Technologies and Challenges. IEEE Access 2017, 5, 3619–3647. [Google Scholar] [CrossRef]
- Kobo, H.I.; Abu-Mahfouz, A.M.; Hancke, G.P. Fragmentation-Based Distributed Control System for Software Defined Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2019, 15, 901–910. [Google Scholar] [CrossRef]
- Ogbodo, E.U.; Dorrell, D.; Abu-Mahfouz, A.M. Cognitive Radio based Sensor Network in Smart Grid: Architectures, Applications and Communication Technologies. IEEE Access 2017, 5, 19084–19098. [Google Scholar] [CrossRef]
- Pritchard, S.W.; Hancke, G.P.; Abu-Mahfouz, A.M. Security in software-defined wireless sensor networks: Threats, challenges and potential solutions. In Proceedings of the 2017 IEEE 15th International Conference on Industrial Informatics (INDIN), Emden, Germany, 24–26 July 2017; pp. 168–173. [Google Scholar]
- Chiwewe, T.M.; Mbuya, C.F.; Hancke, G.P. Using Cognitive Radio for Interference-Resistant Industrial Wireless Sensor Networks: An Overview. IEEE Trans. Ind. Inform. 2015, 11, 1466–1481. [Google Scholar] [CrossRef]
- Ramotsoela, D.; Abu-Mahfouz, A.; Hancke, G. A Survey of Anomaly Detection in Industrial Wireless Sensor Networks with Critical Water System Infrastructure as a Case Study. Sensors 2018, 18, 2491. [Google Scholar] [CrossRef]
- Jeschke, S.; Brecher, C.; Meisen, T.; Özdemir, D.; Eschert, T. Industrial internet of things and cyber manufacturing systems. In Industrial Internet of Things; Springer: Berling, Germany, 2017; pp. 3–19. [Google Scholar]
- Zhang, W.; Yeo, C.K. Sequential sensing based spectrum handoff in cognitive radio networks with multiple users. Comput. Netw. 2014, 58, 87–98. [Google Scholar] [CrossRef]
- Bondan, L.; Marotta, M.A.; Faganello, L.R.; Rochol, J.; Granville, L.Z. ChiMaS: A spectrum sensing-based channels classification system for cognitive radio networks. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference (WCNC), Doha, Qatar, 3–6 April 2016; pp. 1–7. [Google Scholar]
- Joshi, G.P.; Acharya, S.; Kim, S.W. Fuzzy-logic-based channel selection in IEEE 802.22 WRAN. Inf. Syst. 2015, 48, 327–332. [Google Scholar] [CrossRef]
- Mohammadi, M.; Al-Fuqaha, A.; Guizani, M.; Oh, J.-S. Semisupervised deep reinforcement learning in support of IoT and smart city services. IEEE Internet Things J. 2018, 5, 624–635. [Google Scholar] [CrossRef]
- Bkassiny, M.; Li, Y.; Jayaweera, S.K. A survey on machine-learning techniques in cognitive radios. IEEE Commun. Surv. Tutor. 2013, 15, 1136–1159. [Google Scholar] [CrossRef]
- Tabaa, M.; Chouri, B.; Saadaoui, S.; Alami, K. Industrial Communication based on Modbus and Node-RED. Procedia Comput. Sci. 2018, 130, 583–588. [Google Scholar] [CrossRef]
- Rodríguez, P.M.; Torrego, R.; Casado, F.; Fernández, Z.; Mendicute, M.; Arriola, A.; Val, I. Dynamic spectrum access integrated in a wideband cognitive RF-ethernet bridge for industrial control applications. J. Signal Process. Syst. 2016, 83, 19–28. [Google Scholar] [CrossRef]
- Darshini, B.D.; Paventhan, A.; Krishna, H.; Pahuja, N. Enabling real time requirements in industrial IoT through IETF 6TiSCH. In Proceedings of the International Conference on Internet of Things and Applications (IOTA), Pune, India, 22–24 January 2016; pp. 121–124. [Google Scholar]
- Duan, Y.; Li, W.; Zhong, Y.; Fu, X. A multi-network control framework based on industrial internet of things. In Proceedings of the 2016 IEEE 13th International Conference on Networking, Sensing, and Control (ICNSC), Mexico City, Mexico, 28–30 April 2016; pp. 1–5. [Google Scholar]
- Aazam, M.; Zeadally, S.; Harras, K.A. Deploying fog computing in industrial internet of things and industry 4.0. IEEE Trans. Ind. Inform. 2018, 14, 4674–4682. [Google Scholar] [CrossRef]
- Esposito, C.; Ficco, M.; Castiglione, A.; Palmieri, F.; Lu, H. Loss-tolerant event communications within industrial internet of things by leveraging on game theoretic intelligence. IEEE Internet Things J. 2018, 5, 1679–1689. [Google Scholar] [CrossRef]
- Rothe, L.; Loske, M.; Gertler, D.G. Proposing Context-Aware Authentication for the Industrial Internet of Things. In Proceedings of the 2018 IEEE Global Conference on Internet of Things (GCIoT), Alexandria, Egypt, 5–7 Decmeber 2018; pp. 1–5. [Google Scholar]
- Jin, M.; Zhou, X.; Luo, E.; Qing, X. Industrial-QoS-oriented remote wireless communication protocol for the Internet of construction vehicles. IEEE Trans. Ind. Electron. 2015, 62, 7103–7113. [Google Scholar] [CrossRef]
- Li, W.; Zhu, C.; Leung, V.C.; Yang, L.T.; Ma, Y. Performance comparison of cognitive radio sensor networks for industrial IoT with different deployment patterns. IEEE Syst. J. 2017, 11, 1456–1466. [Google Scholar] [CrossRef]
- Piran, M.J.; Tran, N.H.; Suh, D.Y.; Song, J.B.; Hong, C.S.; Han, Z. QoE-Driven Channel Allocation and Handoff Management for Seamless Multimedia in Cognitive 5G Cellular Networks. IEEE Trans. Veh. Technol. 2017, 66, 6569–6585. [Google Scholar] [CrossRef]
- Kim, D.; Nam, H.; Kim, D. Adaptive Code Dissemination Based on Link Quality in Wireless Sensor Networks. IEEE Internet Things J. 2017, 4, 685–695. [Google Scholar] [CrossRef]
- Rahman, M.A.; Asyhari, A.T.; Bhuiyan, M.Z.A.; Salih, Q.M.; Zamli, K.Z.B. L-CAQ: Joint link-oriented channel-availability and channel-quality based channel selection for mobile cognitive radio networks. J. Netw. Comput. Appl. 2018, 113, 26–35. [Google Scholar] [CrossRef]
- Skokowski, P.; Malon, K.; Kelner, J.M.; Dolowski, J.; Lopatka, J.; Gajewski, P. Adaptive channels’ selection for hierarchical cluster based cognitive radio networks. In Proceedings of the 2014 8th International Conference on Signal Processing and Communication Systems (ICSPCS), Gold Coast, Australia, 15–17 December 2014; pp. 1–6. [Google Scholar]
- Gao, W.; Zhao, Z.; Min, G.; Cao, Y.; Duan, H.; Liu, L.; Long, Y.; Yin, G. Link quality aware channel allocation for multichannel body sensor networks. Pervasive Mob. Comput. 2017, 41, 354–364. [Google Scholar] [CrossRef]
- Faganello, L.R.; Kunst, R.; Both, C.B.; Granville, L.Z.; Rochol, J. Improving reinforcement learning algorithms for dynamic spectrum allocation in cognitive sensor networks. In Proceedings of the 2013 IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 35–40. [Google Scholar]
- Wyglinski, A.M.; Nekovee, M.; Hou, Y.T. Cognitive radio communications and networks. IEEE Commun. Mag. 2008, 46, 30–31. [Google Scholar] [CrossRef]
- Gomes, R.D.; Queiroz, D.V.; Lima Filho, A.C.; Fonseca, I.E.; Alencar, M.S. Real-time link quality estimation for industrial wireless sensor networks using dedicated nodes. Ad Hoc Netw. 2017, 59, 116–133. [Google Scholar] [CrossRef]
- Wilhelmi, F.; Bellalta, B.; Cano, C.; Jonsson, A. Implications of Decentralized Q-learning Resource Allocation in Wireless Networks. arXiv, 2017; arXiv:1705.10508. [Google Scholar]
- Shahin, N.; Ali, R.; Kim, Y.-T. Hybrid Slotted-CSMA/CA-TDMA for Efficient Massive Registration of IoT Devices. IEEE Access 2018, 6, 18366–18382. [Google Scholar] [CrossRef]
- Kosunalp, S.; Chu, Y.; Mitchell, P.D.; Grace, D.; Clarke, T. Use of Q-learning approaches for practical medium access control in wireless sensor networks. Eng. Appl. Artif. Intell. 2016, 55, 146–154. [Google Scholar] [CrossRef]
- Kumar, N.; Swain, S.N.; Murthy, C.S.R. A Novel Distributed Q-Learning Based Resource Reservation Framework for Facilitating D2D Content Access Requests in LTE-A Networks. IEEE Trans. Netw. Serv. Manag. 2018. [Google Scholar] [CrossRef]
- Cheng, Z.; Ray, L.E. State Abstraction in Reinforcement Learning by Eliminating Useless Dimensions. In Proceedings of the 2014 13th International Conference on Machine Learning and Applications, Lanzhou, China, 13–16 December 2014; pp. 105–110. [Google Scholar]
- Joshi, G.; Nam, S.; Kim, S. Cognitive Radio Wireless Sensor Networks: Applications, Challenges and Research Trends. Sensors 2013, 13, 11196–11228. [Google Scholar] [CrossRef]
- Onumanyi, A.; Abu-Mahfouz, A.; Hancke, G. A comparative analysis of local and global adaptive threshold estimation techniques for energy detection in cognitive radio. Phys. Commun. 2018, 29, 1–11. [Google Scholar] [CrossRef]
- Chiwewe, T.M.; Hancke, G.P. Cognitiva—A cognitive industrial wireless network protocol: Protocol design and testbed implementation. In Proceedings of the 2016 IEEE International Conference on Industrial Technology (ICIT), Taipei, Taiwan, 14–17 March 2016; pp. 2042–2047. [Google Scholar]
- Son Duc, N.; Tung-Linh, P.; Kim, D.S. Dynamic spectrum handoff for industrial cognitive wireless sensor networks. In Proceedings of the 2013 11th IEEE International Conference on Industrial Informatics (INDIN), Bochum, Germany, 29–31 July 2013; pp. 92–97. [Google Scholar]
- Zhang, Y.; Zheng, J.; Chen, H.-H. Cognitive Radio Networks: Architectures, Protocols, and Standards; CRC Press: New York, NY, USA, 2016. [Google Scholar]


| Industrial System | Categories | No. of Nodes | Real-Time Requirements | QoS Requirements | Latency (ms) | Reliability (PLR) | Jitters (ms) |
|---|---|---|---|---|---|---|---|
| Monitoring systems | Information and Alerting systems | 100–1000 | No real-time | Reliability, energy efficiency, load balancing, and availability | ≥100 | 10−3–10−4 | − |
| Safety systems | Alarm systems | 100–300 | Soft real-time | Availability, also timeliness | 10–100 | 10−3–10−4 | ≤1 |
| Control systems | Control and Factory automation | 2–50 | Hard real-time | Timeliness, reliability, and energy efficiency | 0.25–10 | 10−9 | ≤0.02 |
| Parameter | Value |
|---|---|
| Unlicensed band | |
| Frequency | 2.4 GHz ISM band |
| Transceiver | CC2420 |
| Number of active nodes | 10 IIoT devices |
| Bandwidth | 50 KHz |
| Number of channel | 3 |
| Packet rate | Poisson distribution |
| SINR | 5 dB |
| Licensed band | |
| Frequency | 470–890 MHz |
| Number of active nodes | 5 PUs, |
| Number of channel | 10 |
| Packet rate | Poisson distribution |
| SINR | 1–15 dB |
| Network and channel model | |
| Network radius | 100 m |
| PU coverage radius | 50 m |
| IIoT devices coverage radius | 35 m |
| Propagation-loss exponent | Random (obstructed industrial environment) |
| Transmitted power | −63 dBm |
| Path loss | 20 dBm |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oyewobi, S.S.; Hancke, G.P.; Abu-Mahfouz, A.M.; Onumanyi, A.J. An Effective Spectrum Handoff Based on Reinforcement Learning for Target Channel Selection in the Industrial Internet of Things. Sensors 2019, 19, 1395. https://doi.org/10.3390/s19061395
Oyewobi SS, Hancke GP, Abu-Mahfouz AM, Onumanyi AJ. An Effective Spectrum Handoff Based on Reinforcement Learning for Target Channel Selection in the Industrial Internet of Things. Sensors. 2019; 19(6):1395. https://doi.org/10.3390/s19061395
Chicago/Turabian StyleOyewobi, Stephen S., Gerhard P. Hancke, Adnan M. Abu-Mahfouz, and Adeiza J. Onumanyi. 2019. "An Effective Spectrum Handoff Based on Reinforcement Learning for Target Channel Selection in the Industrial Internet of Things" Sensors 19, no. 6: 1395. https://doi.org/10.3390/s19061395
APA StyleOyewobi, S. S., Hancke, G. P., Abu-Mahfouz, A. M., & Onumanyi, A. J. (2019). An Effective Spectrum Handoff Based on Reinforcement Learning for Target Channel Selection in the Industrial Internet of Things. Sensors, 19(6), 1395. https://doi.org/10.3390/s19061395







