Auto-Configuration in Wireless Sensor Networks: A Review
Abstract
1. Introduction
2. Research Challenges in WSN Configuration
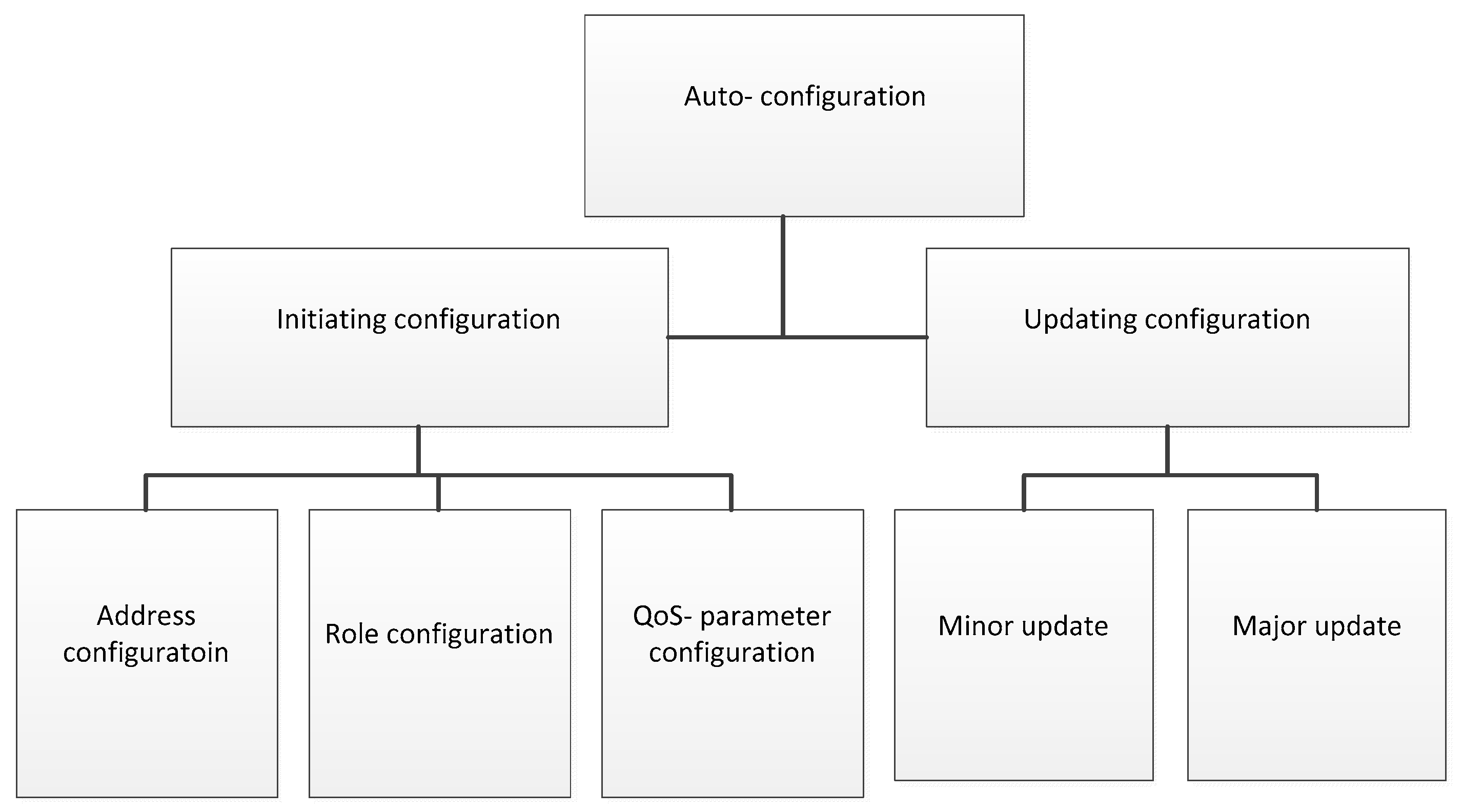
Taxonomy of the Existing Auto-Configuration
3. Initiating Configuration
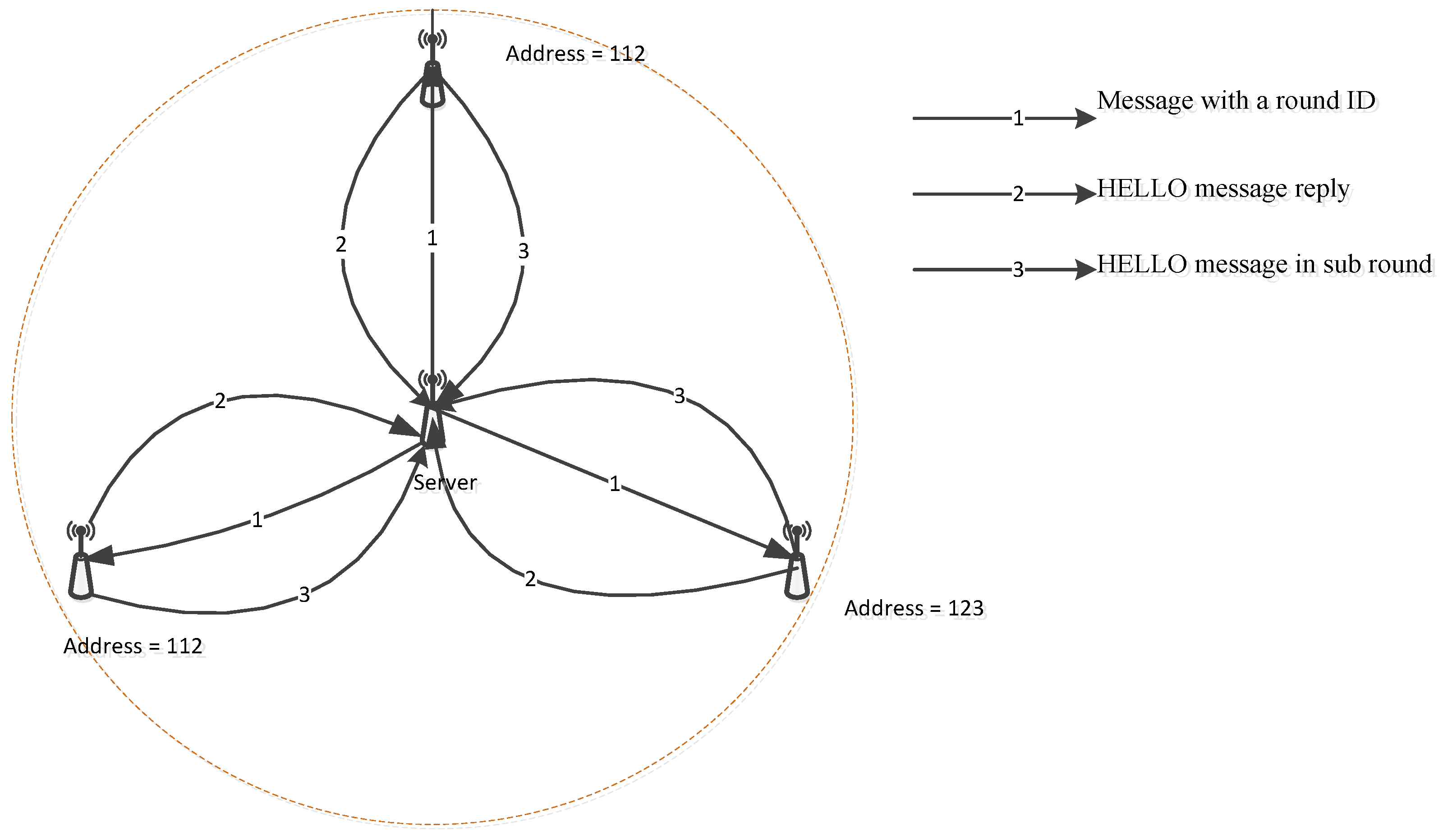
3.1. Address Configuration
3.2. Pure Address Auto-Configuration
3.2.1. Proxy-Based Address Assignment
3.2.2. Multi-Tiers Configuration
3.2.3. Cluster-Based Addressing
3.2.4. Localized Address Assignments
3.3. Configuration with Additional Information
3.3.1. Group-Addressing
3.3.2. Geometric Information Based Addressing
3.3.3. Location-Based IP Addressing
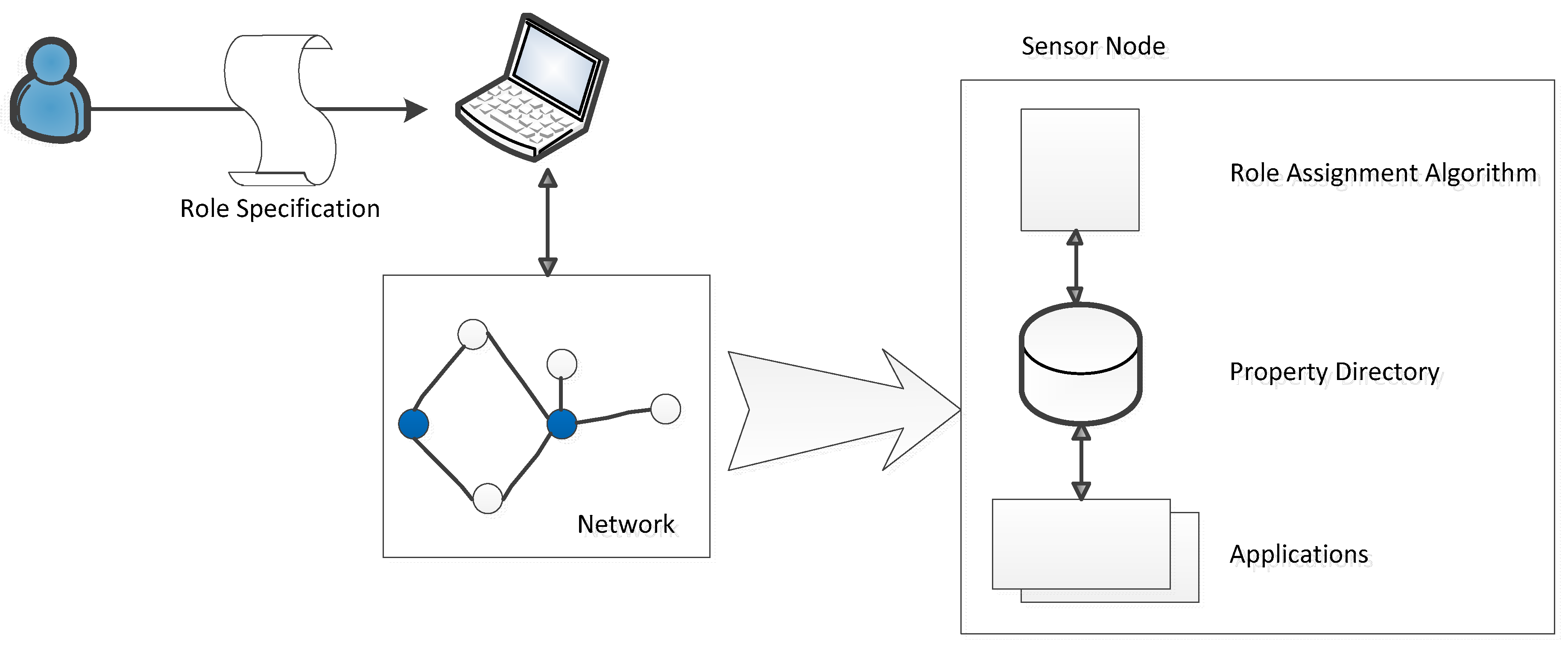
3.4. Role Configuration
3.4.1. Cache Algorithm
3.4.2. Probabilistic Initialization
3.4.3. Wave Initialization
3.4.4. Heuristic Approach
3.5. QoS-Parameter Configuration
3.5.1. Flat Configuration
3.5.2. Mapping
3.5.3. Sub-Domain Based Configuration
4. Update Configuration
4.1. Minor Update
4.1.1. TinyCubus
4.1.2. Middleware
4.1.3. Ginconf
4.1.4. Context-Aware Middleware
4.1.5. Edit Script
4.1.6. Update-Conscious Compilation
4.2. Major Update
4.2.1. A Complete Model
4.2.2. RECOUP
4.2.3. A Simple Upgrade Method
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Couto, D.S.J.D.; Aguayo, D.; Bicket, J.; Morris, R. A high-throughout path metric for multi-hop wireless routing. Wirel. Netw. 2005, 11, 419–434. [Google Scholar] [CrossRef]
- Chen, D.; Varshney, P.K. QoS support in wireless sensor networks: A survey. In Proceedings of the International Conference on Wireless Networks, ICWN, Las Vegas, NV, USA, 21–24 June 2004. [Google Scholar]
- Radi, M.; Dezfouli, B.; Bakar, K.A.; Lee, M. Multipath routing in wireless sensor networks: Survey and research challenges. Sensors 2012, 12, 650–685. [Google Scholar] [CrossRef] [PubMed]
- Dietrich, I.; Dressler, F. On the lifetime of wireless sensor networks. ACM Trans. Sens. Netw. 2009, 5, 5. [Google Scholar] [CrossRef]
- Gao, X.; Vanq, Y.; Zhou, D. Coverage of communication-based sensor nodes deployed location and energy efficient clustering algorithm in WSN. J. Syst. Eng. Electron. 2010, 21, 698–704. [Google Scholar] [CrossRef]
- Rajagopalan, R.; Varshney, P.K. Data aggregation techniques in sensor networks: A survey. IEEE Commun. Surv. Tutor. 2006, 8, 48–63. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A survey on Sensor Networks. IEEE Commun. Mag. 2002, 40, 102–114. [Google Scholar] [CrossRef]
- Talipov, E.; Shin, H.; Seungjae, H. A lightweight stateful address auto-configuration for 6LoWPAN. Wirel. Netw. 2011, 17, 183–197. [Google Scholar] [CrossRef]
- Wang, X.; Qian, H. IPv6 address configuration scheme for wireless sensor networks. J. Comput. Stand. Interfaces 2012, 34, 334–341. [Google Scholar] [CrossRef]
- Jobin, J.; Srikanth, V.K.; Satish, K.T. A scheme for the assignment of unique addresses to support self-organization in wireless sensor networks. In Proceedings of the IEEE 60th Vehicular Technology Conference, Los Angeles, CA, USA, 26–29 September 2004. [Google Scholar]
- Lin, J.; Liu, Y.; Ni, L.M. SIDA-self organizing ID assignment. In Proceedings of the IEEE International Conference on Mobile Adhoc and Sensor Systems, Pisa, Italy, 8–11 October 2017. [Google Scholar]
- Wang, X.; Qian, H. Hierarchical and low-power IPv6 address configuration for wireless sensor networks. Int. J. Commun. Syst. 2012, 25, 1513–1529. [Google Scholar] [CrossRef]
- Zheng, Y.; Falko, D. Dynamic address allocation for management and control in wireless sensor networks. In Proceedings of the 2007 40th Annual Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 3–6 January 2007. [Google Scholar]
- Teng, R.; Morikawa, H.; Aoyama, T.; Zhang, B. Network-layer and MAC-layer address auto configuration in self-organized sensor networks. In Proceedings of the International Conference on ITS Telecommunications, Chengdu, China, 21–23 June 2006. [Google Scholar]
- Du, Z.; Qian, D.; Stanczak, S.; Heras, R.; Liu, Y. Auto-configuration of shared network-layer address in cluster-based wireless sensor network. In Proceedings of the IEEE Conference on Networking Sensing and Control, Sanya, China, 6–8 April 2008. [Google Scholar]
- Shin, H.; Talipov, E.; Cha, H. IPv6 lightweight stateless address auto-configuration for 6LoWPAN using color coordinators. In Proceedings of the 2009 IEEE International Conference on Pervasive Computing and Communications, Galveston, TX, USA, 9–13 March 2009. [Google Scholar]
- Ding, R.; Du, H. Location-based IP addressing in IP-enable wireless sensor networks. In Proceedings of the International Conference on Control, Automation and Systems Engineering, CASE, Singapore, 30–31 July 2011. [Google Scholar]
- Frank, C. Role-Based Configuration of Wireless Sensor Networks. Ph.D. Thesis, ETH Zurich, Zurich, Switzerland, 2007. [Google Scholar]
- Frank, C.; Romer, K. Algorithms for generic role assignment in wireless sensor network. In Proceedings of the 3rd International Conference on Embedded Networked Sensor Systems, San Diego, CA, USA, 2–4 November 2005. [Google Scholar]
- Frank, C.; Romer, K. Solving generic role assignment exactly. In Proceedings of the 20th IEEE International Parallel & Distributed Processing Symposium, Rhodes Island, Greece, 25–29 April 2006. [Google Scholar]
- Romer, K.; Frank, C.; Marron, P.J.; Becker, C. Generic role assignment for wireless sensor networks. In Proceeding of the 11th Workshop on ACM. SIGOPS, Leuven, Belgium, 19–22 September 2004. [Google Scholar]
- De Souz, F.S.H.; Mateus, G.R. Exact and heuristic approaches for role assignment problem in wireless sensor networks. In Proceedings of the International Network Optimization Conference, Spa, Belgium, 22–25 April 2007. [Google Scholar]
- Perillo, M. Role Assignment in Wireless Sensor Networks: Energy-Efficient Strategies and Algorithms. Ph.D. Thesis, University of Rochester, Rochester, NY, USA, 2007. [Google Scholar]
- Nabi, M.; Blagojevic, M.; Basten, T.; Geilen, M.; Hendriks, T. Configuring multi-objective evolutionary algorithms for design-space exploration of wireless sensor networks. In Proceedings of the 4th ACM Workshop on Performance Monitoring and Measurement of Heterogeneous Wireless and Wired Networks, Tenerife, Canary Islands, Spain, 26 October 2009. [Google Scholar]
- Hoes, R. Configuring Heterogeneous Wireless Sensor Networks under Quality of Service Constraints. Ph.D. Thesis, Technische Universiteit Eindhoven, Eindhoven, The Netherlands, 2009. [Google Scholar]
- Aral, M.M.; Guan, J.; Maslia, M.L. A multi-objective optimization algorithm for sensor placement in water distribution systems. In Proceedings of the World Environmental and Water Resources Congress 2008, Honolulu, HI, USA, 12–16 May 2008. [Google Scholar]
- Marrón, P.J.; Lachenmann, A.; Minder, D.; Gauger, M.; Saukh, O.; Rothermel, K. Management and configuration issues for sensor networks. Int. J. Netw. Manag. 2005, 15, 235–253. [Google Scholar] [CrossRef]
- Cecílio, J.; Furtado, P. Distributed configuration and processing for industrial sensor networks. In Proceedings of the International Workshop on Middleware Tools, Services and Run-time Support, Lisbon, Portugal, 12 December 2011. [Google Scholar]
- Gámez, N.; Cubo, J.; Fuentes, L.; Pimentel, E. Configuring a context-aware middleware for wireless sensor networks. J. Sens. 2012, 12, 8544–8570. [Google Scholar] [CrossRef] [PubMed]
- Reijers, N.; Langendoen, K. Efficient code distribution in wireless sensor networks. In Proceedings of the 2nd ACM International Conference on Wireless Sensor Networks and Applications, San Diego, CA, USA, 19 September 2003. [Google Scholar]
- Li, W.; Zhang, Y.; Yang, J.; Zheng, J. Towards update-conscious compilation for energy-efficient code dissemination in WSNs. In Proceedings of the IEEE International Symposium on Parallel and Distributed, Miami, FL, USA, 14–18 April 2008. [Google Scholar]
- Brown, S.; Sreenan, C.J. A new model for updating software in wireless sensor networks. IEEE Netw. 2006, 20, 42–47. [Google Scholar] [CrossRef]
- Hui, J.W.; Culler, D. The dynamic behavior of a data dissemination protocol for network programming at scale. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004. [Google Scholar]
- Liu, T.; Sadler, C.M.; Zhang, P.; Martonosi, M. Implementing software on resource-constrained mobile sensor–experiences with Impala and ZebraNet. In Proceedings of the International Conference on Mobile Systems, Applications, and Services, Boston, MA, USA, 6–9 June 2004. [Google Scholar]
- Stathopoulos, T.; Heidemann, J.; Estrin, D. A Remote Code Update Mechanism for Wireless Sensor Networks; CENS Techical Report; Center for Embedded Networked Computing, University of California: Los Angeles, CA, USA, 2003. [Google Scholar]
- Levis, P.; Culler, D. A tiny virtual machine for sensor networks. In Proceedings of the Architectural Support for Programming Languages and Opt, San Jose, CA, USA, 5–9 October 2002. [Google Scholar]
- Pennington, S.; Waller, A.; Baugé, T. RECOUP efficient decentralized configuration update for wireless sensor networks. In Proceedings of the MobiQuitous, Dublin, Ireland, 21–25 July 2008. [Google Scholar]
- Yeungmoon, K.; Byoungchul, W.S.N. Firmware update methods by relay node selection. In Proceedings of the Computer Communication, Shanghai, China, 8 April 2011. [Google Scholar]
- Baba, D.; Suematsu, N.; Nabeshima, S.; Miyazaki, T. ReSNE: Reconfigurable sensor network emulator virtualizing integrated large-scale sensor network. In Proceedings of the International Conference on Computing, Networking and Communications (ICNC), Kauai, HI, USA, 15–18 February 2016. [Google Scholar]
- Varga, L.-O.; Romaniello, G.; Vučinić, M.; Favre, M.; Banciu, A.; Guizzetri, R.; Planat, C.; Urard, P.; Heusse, M.; Rousseau, F.; et al. GreenNet: An Energy-Harvesting IP-Enabled Wireless Sensor Network. IEEE Internet Things J. 2015, 2, 412–426. [Google Scholar] [CrossRef]
- Kim, S.-M.; Choi, H.-S.; Rhee, W.-S. IoT home gateway for auto-configuration and management of MQTT devices. In Proceedings of the IEEE Conference on Wireless Sensors (ICWiSe), Melaka, Malaysia, 24–26 August 2015. [Google Scholar]
- Javadi, S.H.; Peiravi, A. Distributed detection in serial and parallel configurations of wireless sensor networks. In Proceedings of the 2018 Electric Electronics, Computer Science, Biomedical Engineerings, Istanbul, Turkey, 18–19 April 2018. [Google Scholar]
- Nishikawa, Y.; Sasamura, T.; Ishizuka, Y.; Sugimoto, S.; Iwasaki, S.; Wang, H.; Fujishima, T.; Fujimoto, T.; Yamashita, K.; Suzuki, T.; et al. Design of stable wireless sensor network for slope monitoring. In Proceedings of the IEEE Topical Conference on Wireless Sensors and Sensor Networks (WiSNet), Anaheim, CA, USA, 14–17 January 2018. [Google Scholar]
- Tian, Y.; Ou, Y.; You, G.; Wang, Z. A coverage configuration scheme of wireless sensor networks base on collaborative sensing in shadow fading. In Proceedings of the 29th Chinese Control and Decision Conference (CCDC), Chongqing, China, 28–30 May 2017. [Google Scholar]
- Titaev, A. Construction of a maximum lifetime route tree in wireless sensor networks for nodes with a two-level transmission power. In Proceedings of the Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology, Yekaterinburg, Russia, 7–8 May 2018. [Google Scholar]
- Nene, M.J.; Deodhar, R.S.; Patnaik, L.M. Algorithm for Autonomous Reorganization of Mobile Wireless Camera Sensor Networks to Improve Coverage. IEEE Sens. J. 2015, 15, 4428–4441. [Google Scholar] [CrossRef]
- Ou, Y.; Tian, Y.; Liu, M. A distributed self-organizing clustering routing protocal for wireless sensor networks. In Proceedings of the Automation Congress (CAC), Jinan, China, 20–22 October 2017. [Google Scholar]
- Gou, L.; Zhang, G.; Bian, D.; Zhang, W.; Xie, Z. Data dissemination in wireless sensor networks with instantly decodable network coding. J. Commun. Netw. 2017, 18, 846–856. [Google Scholar]
- Lim, S.-H.; Kim, Y.-I. The efficient algorithm for autonomous configuration in WSNs-based trains. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016. [Google Scholar]
- Kim, J.; Jeon, H.; Lee, J. Network management framework and lifetime evaluation method for wireless sensor networks. Integr. Comput. Aided Eng. 2012, 19, 165–178. [Google Scholar] [CrossRef]
- Lee, W.L.; Datta, A.; Cardell-Oliver, R. Network Management in Wireless Sensor Networks. Available online: http://www.csse.uwa.edu.au/˜winnie/Network Management in WSNs.pdf (accessed on 15 August 2019).
- Ruiz, L.B.; Nogueira, J.M.; Loureiro, A.A.F. MANNA: A Management Architecture for Wireless Sensor Networks. IEEE Commun. Mag. 2003, 41, 116–125. [Google Scholar] [CrossRef]
- Deb, B.; Bhatnagar, S.; Nath, B. Wireless Sensor Networks Management. 2005. Available online: http://www.research.rutgers.edu/∼bdeb/sensor networks.html (accessed on 15 August 2019).
- Tolle, G.; Culler, D. Design of an Application Cooperative Management System for Wireless Sensor Networks. In Proceedings of the Second European Workshop on Wireless Sensor Networks 2005, Istanbul, Turkey, 2 February 2005. [Google Scholar]
- Ahmed, F.; Kervadec, C.; Le Moullec, Y.; Tamberg, G.; Annus, P. Autonomous Wireless Sensor Networks: Implementation of Transient Computing and Energy Prediction for Improved Node Performance and Link Quality. Comput. J. 2019, 62, 820–837. [Google Scholar] [CrossRef]
- Wang, W.; Wang, N.; Jafer, E.; Hayes, M.; O’Flynn, B.; O’Mathuna, C. Autonomous wireless sensor network based Building Energy and Environment Monitoring system design. In Proceedings of the 2010 2nd Conference on Environmental Science and Information Application Technology, Wuhan, China, 17–18 July 2010; pp. 367–372. [Google Scholar]
- Dondi, D.; Scorcioni, S.; Bertacchini, A.; Larcher, L.; Pavan, P. An autonomous wireless sensor network device powered by a RF energy harvesting system. In Proceedings of the IECON 2012 38th Annual Conference on IEEE Industrial Electronics Society, Montreal, QC, Canada, 25–28 October 2012; pp. 2557–2562. [Google Scholar]
- Tuna, G.; Gungor, V.C.; Gulez, K. An autonomous wireless sensor network deployment system using mobile robots for human existence detection in case of disasters. Ad Hoc Netw. 2014, 13, 54–68. [Google Scholar] [CrossRef]













| Method | Hierarchy | Unique Address | DAD | Distributed | Address Space | Overhead | Latency | Scalability |
|---|---|---|---|---|---|---|---|---|
| Proxy-based addressing | Yes | Yes | Yes | Yes | 16 bit | Low | Low | Yes |
| Multi-tier | Yes | Yes | No | Yes | Vary | Large | Low | Yes |
| Cluster-based | Yes | Yes | Passive | No | 128 bit | Large | Low | Yes |
| Localized | No | No | Yes | No | Vary | Low | No |
| Method | Scalability | Energy Efficient | Address Unique | Address Space | Structure | DAD |
|---|---|---|---|---|---|---|
| Group-addressing | Yes | Yes | No | Vary | Hierarchical | Yes |
| Geometric-based addressing | Yes | No | Yes | 16 bits | Hierarchical | Yes |
| Location-based addressing | Yes | No | Yes | 128 bits | Hierarchical | No |
| Method | Scalable | Scope | Optimal | Hierarchical | Method | Complexity |
|---|---|---|---|---|---|---|
| Mapping | Yes | Any | Yes | Yes | Pareto optimal front | High |
| Flat configuration | No | Not large | Near | No | Dominated sorting algorithm, Pareto optimal front | High |
| Sub-domain based configuration | Weak | Any | Near | Yes | Pareto optimal front, NSGA-II | Low |
| Method | Reliable | Update Time | Overhead | Repair | Speed of Adaptation |
|---|---|---|---|---|---|
| TinyCubus | Low | Long | High | No | Low |
| Middle layer | Low | Short | Low | No | High |
| Efficient Code Distribution | Low | Short | Low | No | Low |
| Update-conscious | Low | Long | Low | No | Low |
| Model | Reliable | Update Time | Repair | Energy Efficient | Completion of Process | Security | Complexity |
|---|---|---|---|---|---|---|---|
| Complete model | High | Long | Yes | Low | Complete | Yes | High |
| RECOUP | High | Short | Yes | Medium | Focus on distributing update packet | No | Medium |
| A simple upgrade method | Low | Short | No | Medium | Lack of most process. | no | Low |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dinh, N.-T.; Kim, Y. Auto-Configuration in Wireless Sensor Networks: A Review. Sensors 2019, 19, 4281. https://doi.org/10.3390/s19194281
Dinh N-T, Kim Y. Auto-Configuration in Wireless Sensor Networks: A Review. Sensors. 2019; 19(19):4281. https://doi.org/10.3390/s19194281
Chicago/Turabian StyleDinh, Ngoc-Thanh, and Younghan Kim. 2019. "Auto-Configuration in Wireless Sensor Networks: A Review" Sensors 19, no. 19: 4281. https://doi.org/10.3390/s19194281
APA StyleDinh, N.-T., & Kim, Y. (2019). Auto-Configuration in Wireless Sensor Networks: A Review. Sensors, 19(19), 4281. https://doi.org/10.3390/s19194281






