An Effective Multifactor Authentication Mechanism Based on Combiners of Hash Function over Internet of Things
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Summary of Contributions
2. Related Work on IoT Cybersecurity
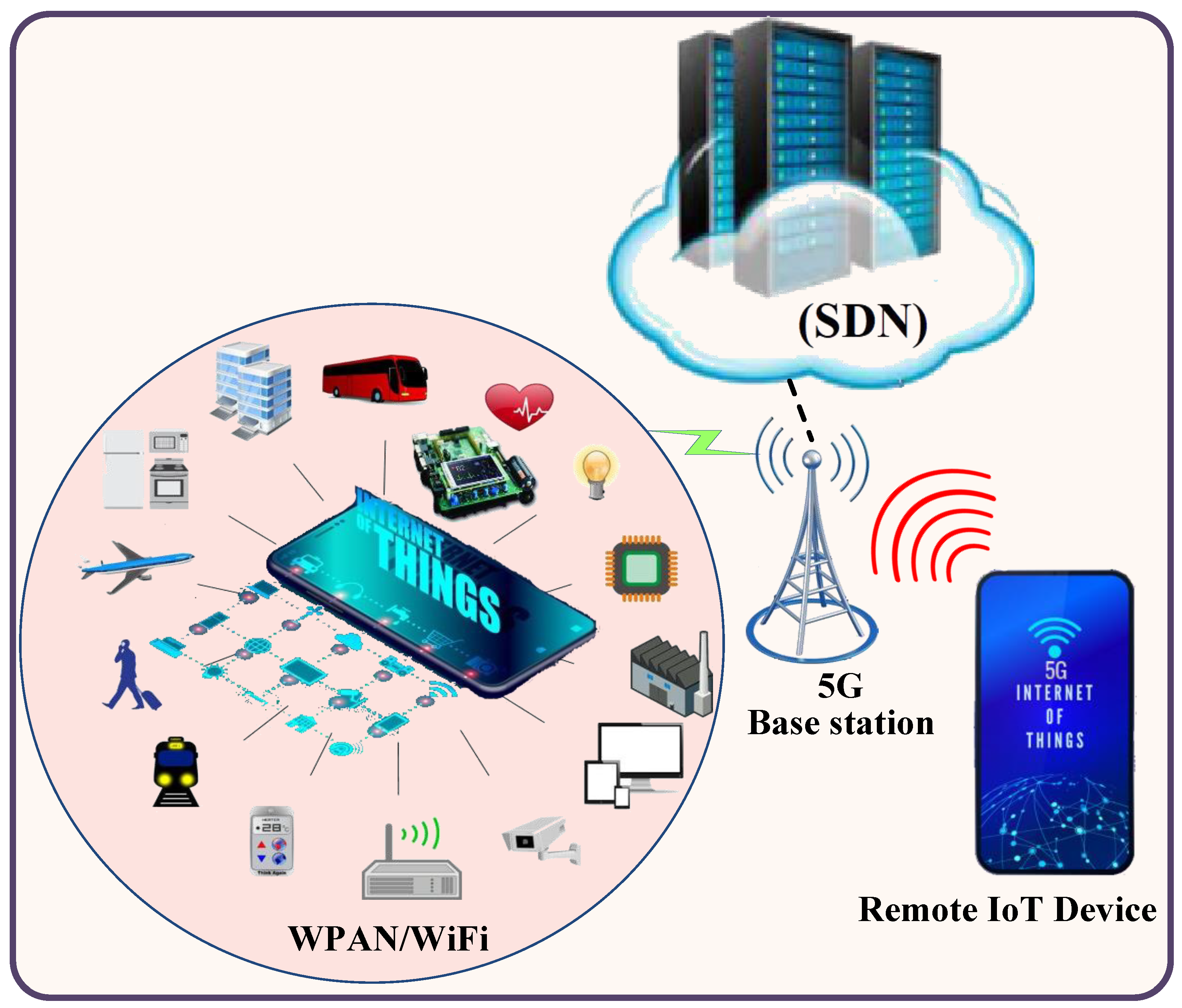
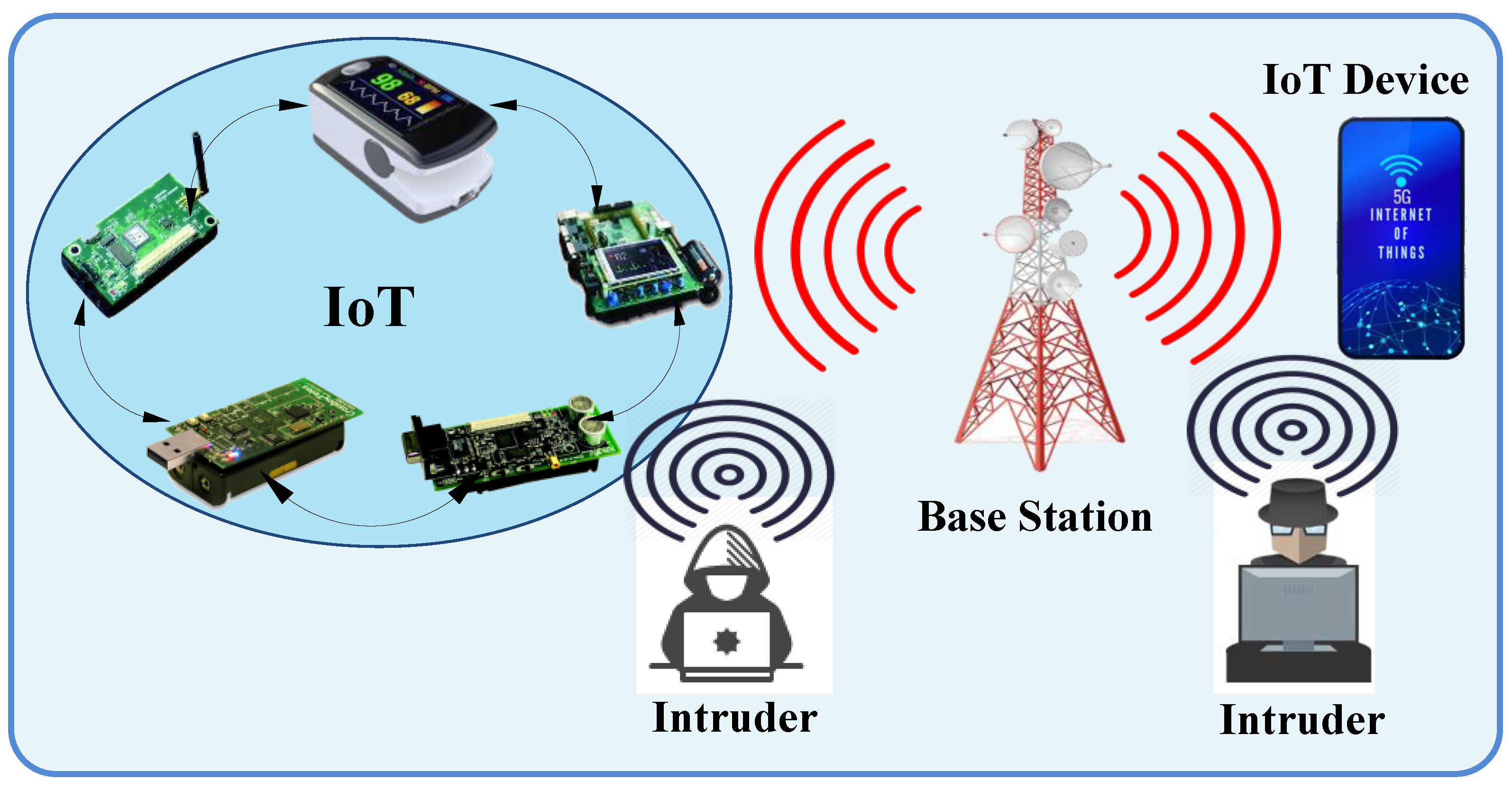
3. System Design of Proposed Cybersecurity Mechanism
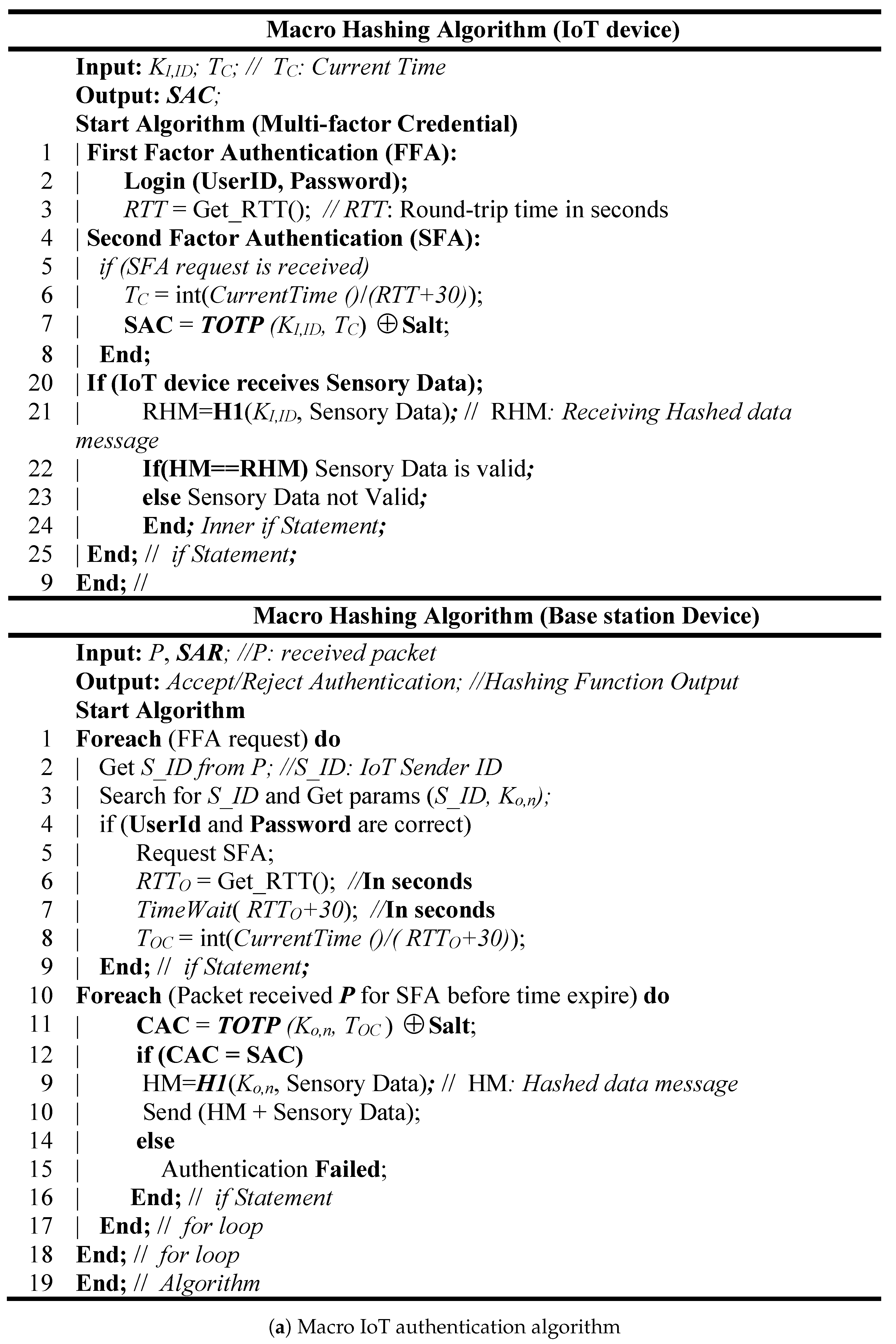
3.1. Multifactor Authentication Algorithm
- Each sensor device has three secure keys—two privates (K1 and K2) and one public (K_DSA: key for direct access control)—which are stored during device programming.
- Each sensor device static or mobile is aware of its location.
- Sink is a trusted base station.
- A sensor device cannot use TOTP because it has limited resources which affect the precision calculation of the absolute time that is required in a synchronous TOTP.
- Each IoT device has two secure keys—one private (KI, ID) and one public K_DSA.
- An IoT device and the sink have an ability to implement TOTP and the TEOTP.
- A sink or a base station has a database that stores the complete details of all sensors and IoT devices.
3.1.1. Micro IoT Authentication Paradigm
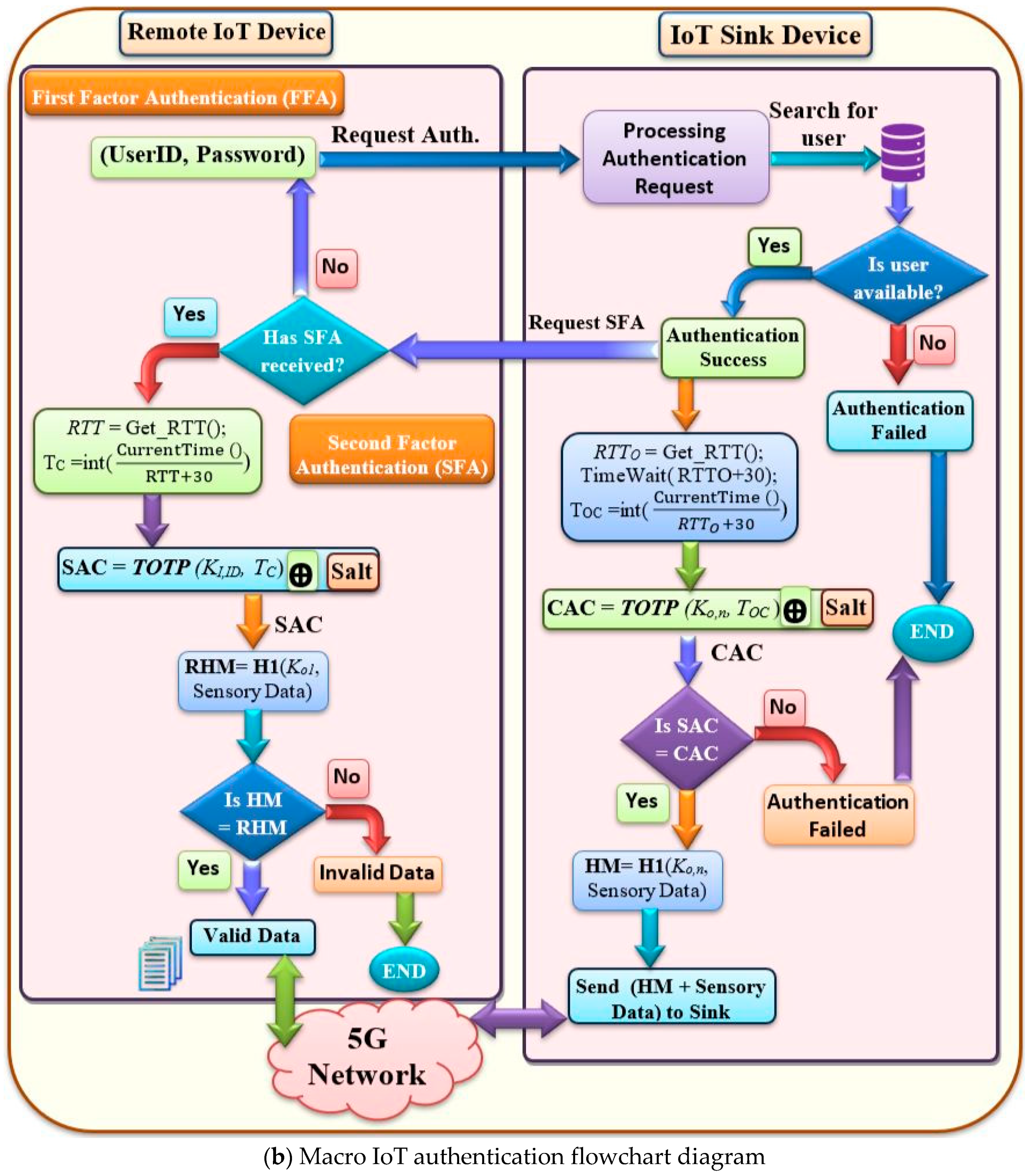
3.1.2. Macro IoT Authentication Paradigm
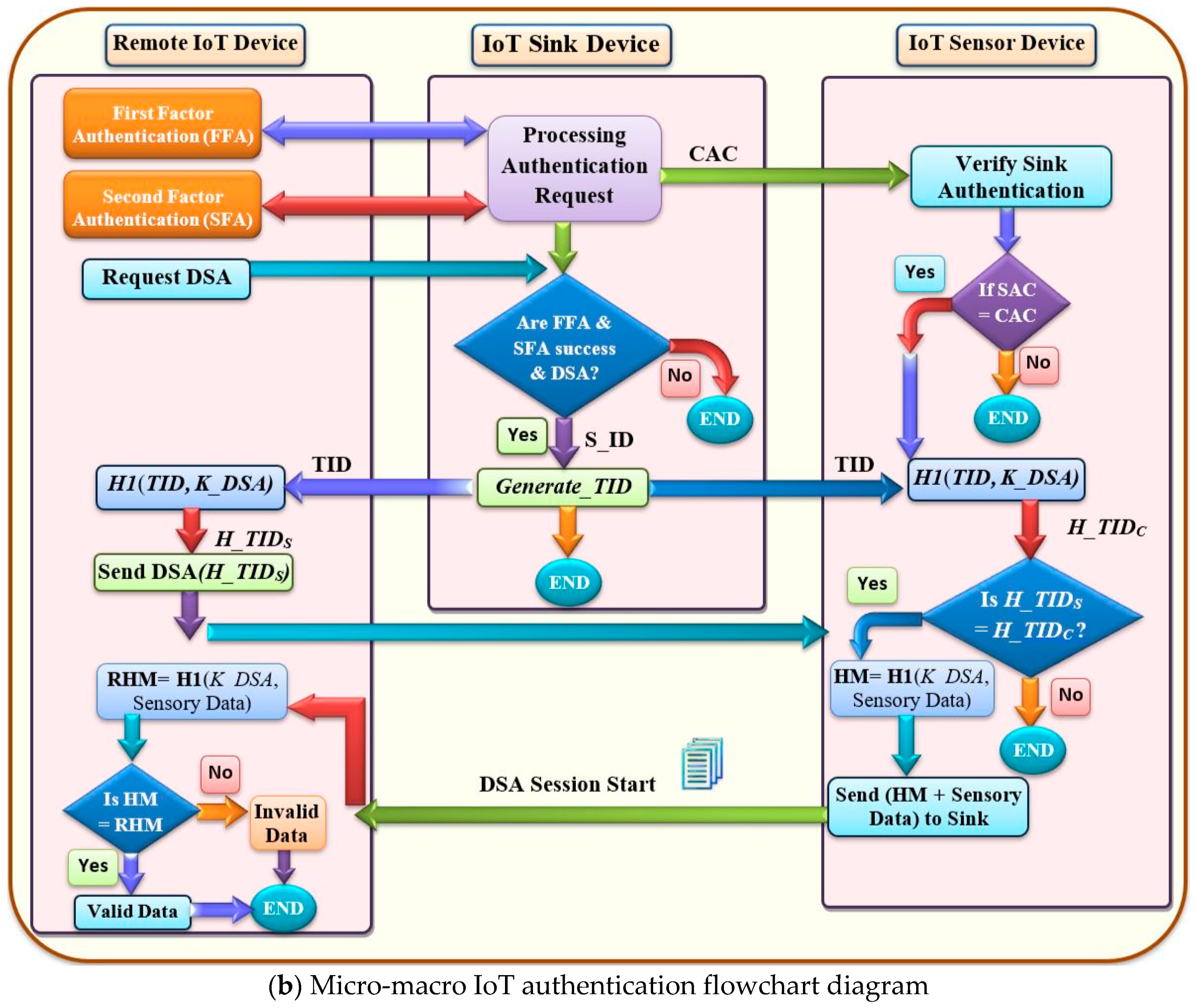
3.1.3. Micro–Macro IoT Authentication Paradigm
4. Cybersecurity Analysis
4.1. Multi-Property Robustness of the Proposed Mechanism
4.2. Countermeasures of the Proposed Mechanism
4.2.1. Countermeasures against Man-in-the-Middle and Replay Attacks
- The multifactor credentials should be inspected between a man-in-the-middle and the sender before accepting any data message.
- The reply message should be hashed using the secret key which is not included in the original message and only known by the sender and the base station.
- The replay attacks cannot forward the copy of sending messages, because the proposed CMA uses TEOTP which changes after a set time period (30 s + RTT).
4.2.2. Countermeasures against Dictionary and Brute Force Attacks
4.2.3. Countermeasures against Spoofing and Session Hijacking Attacks
4.2.4. Countermeasures against Sensor Capture and Stolen-Verifier Attacks
5. Implementation of CMA and Evaluation
5.1. Performance Evaluation and Results Discussion
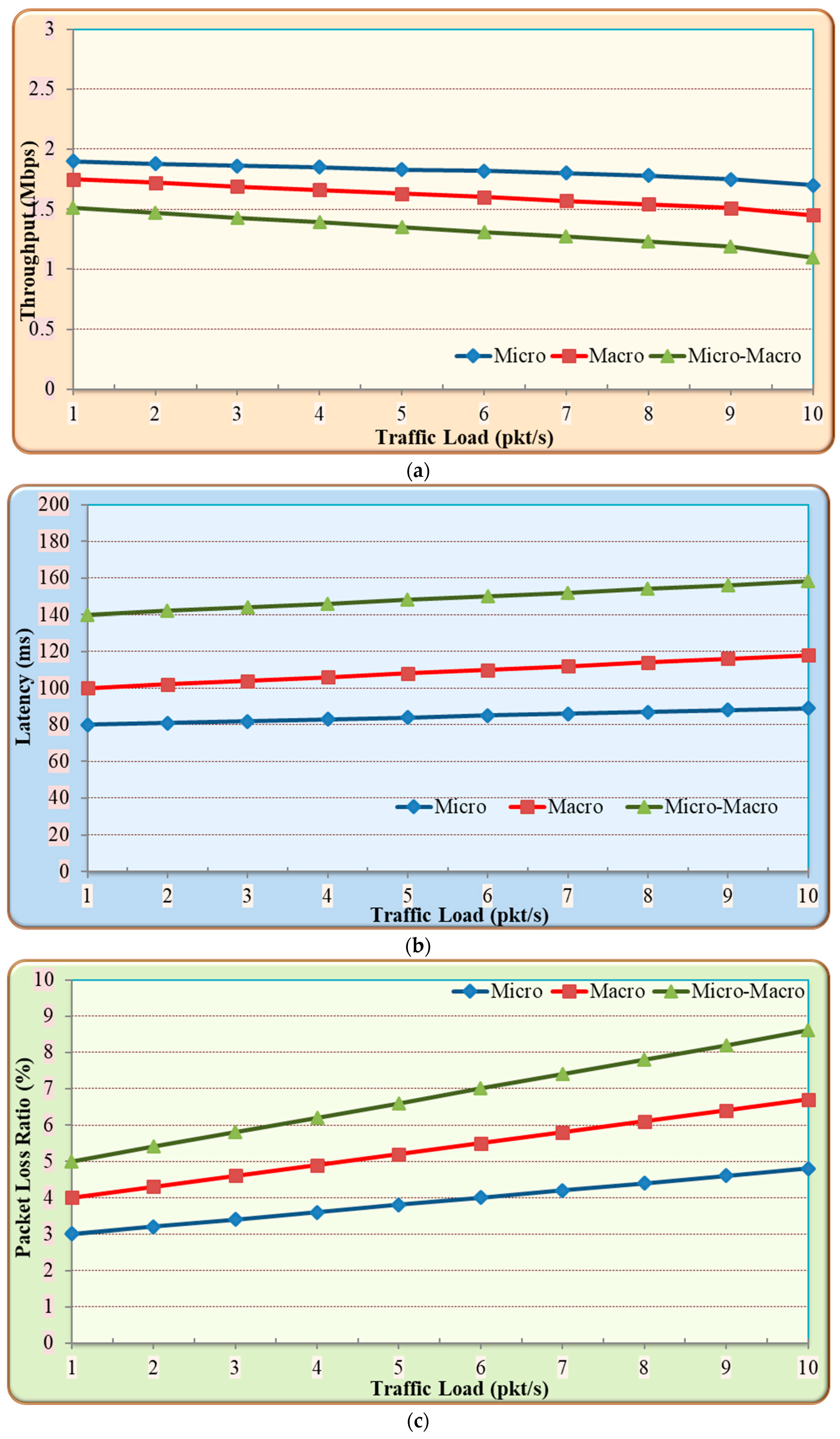
5.1.1. Impact of Proposed Authentication Algorithms on IoT Performance
- Discussion
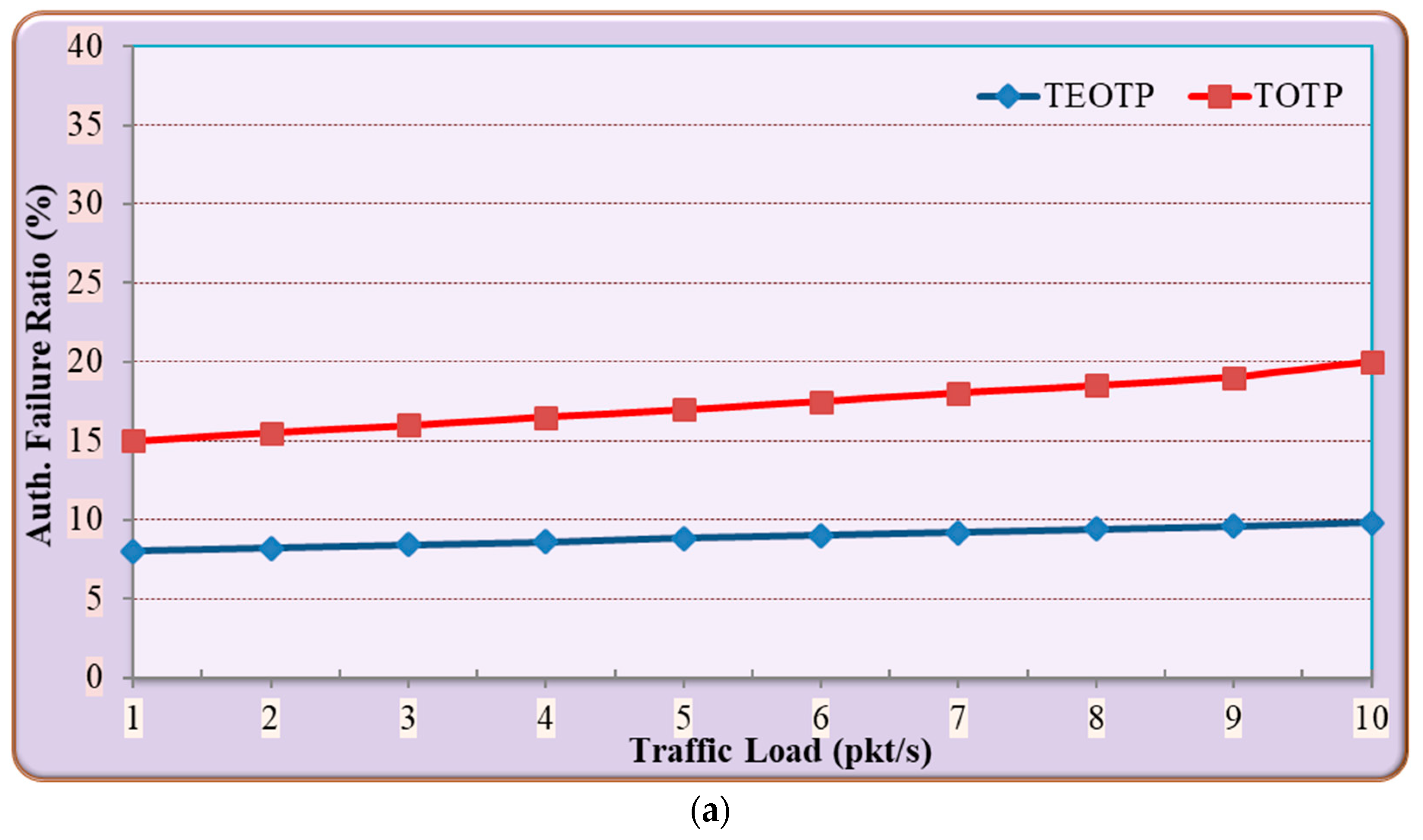
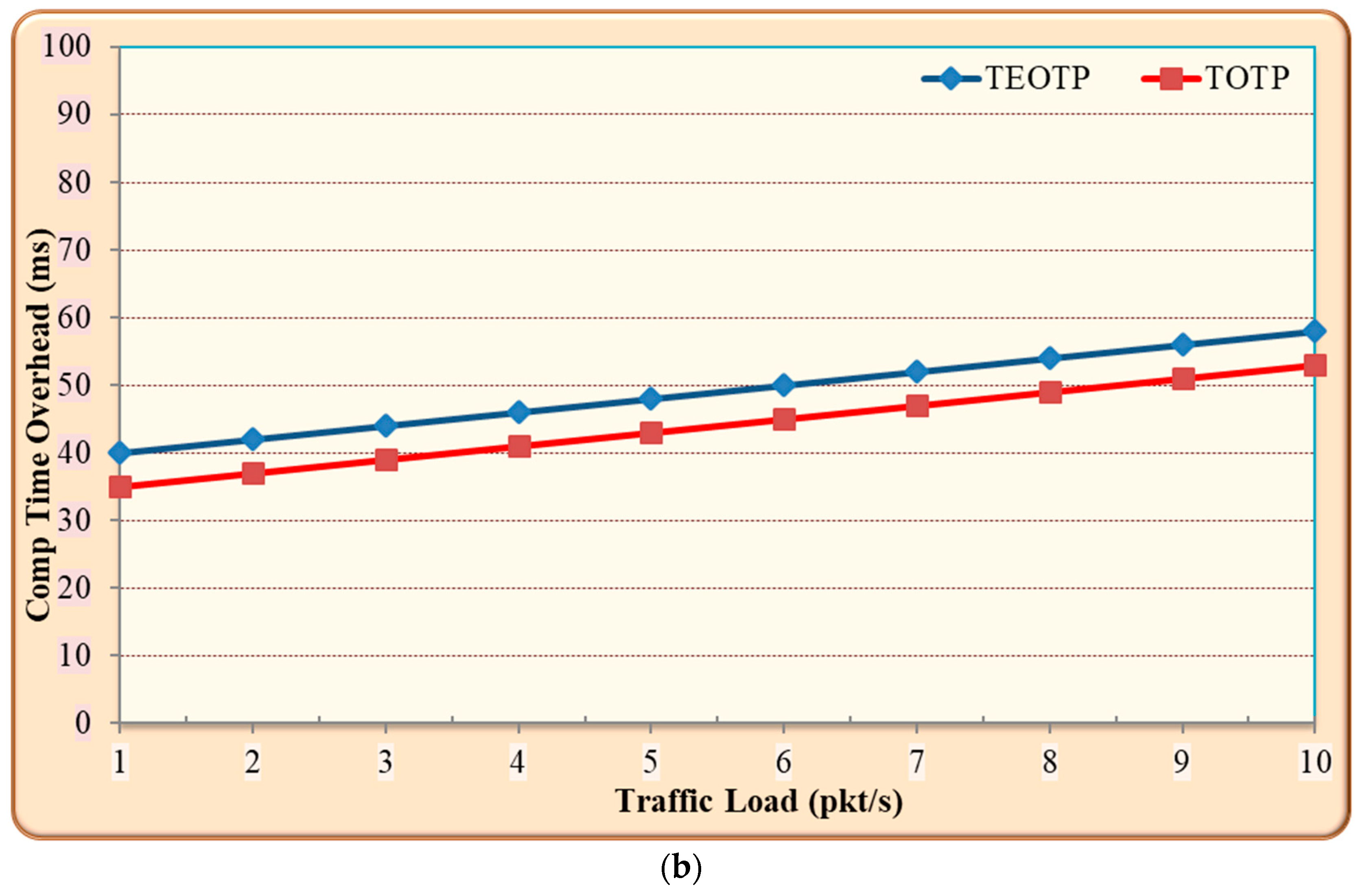
5.1.2. Comparison between the Performance of TEOTP and TOTP
- Discussion
6. Potential Limitations for Implementing CMA in IoT
7. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Davoli, L.; Belli, L.; Cilfone, A.; Ferrari, G. From Micro to Macro IoT: Challenges and Solutions in the Integration of IEEE 802.15.4/802.11 and Sub-GHz Technologies. IEEE Internet Things J. 2018, 5, 784–793. [Google Scholar] [CrossRef]
- Weyrich, M.; Ebert, C. Reference Architectures for the Internet of Things. IEEE Softw. 2016, 33, 112–116. [Google Scholar] [CrossRef]
- Kreutz, D.; Yu, J.; Ramos, F.; Esteves-Verissimo, P. ANCHOR: Logically Centralized Security for Software-Defined Networks. ACM Trans. Priv. Secur. 2019, 22, 1–36. [Google Scholar] [CrossRef]
- Pakzad, F.; Portmann, M.; Tan, W.L.; Indulska, J. Efficient topology discovery in OpenFlow-based software defined networks. Comput. Commun. 2016, 77, 52–61. [Google Scholar] [CrossRef]
- Alharbi, T.; Portmann, M.; Pakzad, F. The (in)security of Topology Discovery in Software Defined Networks. In Proceedings of the IEEE 40th Conference on Local Computer Networks (LCN), Clearwater Beach, FL, USA, 26–29 October 2015; pp. 502–505. [Google Scholar]
- Duan, X.; Wang, X. Authentication handover and privacy protection in 5G hetnets using software-defined networking. IEEE Commun. Mag. 2015, 53, 28–35. [Google Scholar] [CrossRef]
- Tweneboah-Koduah, S.; Skouby, K.E.; Tadayoni, R. Cyber security threats to IoT applications and service domains. Wirel. Pers. Commun. 2017, 95, 169–185. [Google Scholar] [CrossRef]
- Ciampa, M. Security + Guide to Networking Security Fundamentals, 5th ed.; Course Technology Press: Boston, MA, USA, 2015. [Google Scholar]
- Chuang, Y.-H.; Lo, N.-W.; Yang, C.-Y.; Tang, S.-W. A Lightweight Continuous Authentication Protocol for the Internet of Things. Sensors 2018, 18, 1104. [Google Scholar] [CrossRef]
- Khemissa, H.; Tandjaoui, D.; Novel, A. Lightweight Authentication Scheme for Heterogeneous Wireless Sensor Networks in the Context of Internet of Things. In Proceedings of the Wireless Telecommunications Symposium (WTS), London, UK, 18–20 April 2016; pp. 1–6. [Google Scholar]
- Lehmann, A. On the Security of Hash Function Combiners. Ph.D. Thesis, Darmstadt University of Technology, Darmstadt, Germany, 2010. [Google Scholar]
- Fischlin, M.; Lehmann, A.; Pietrzak, K. Robust multi-property combiners for hash functions. J. Cryptol. 2014, 7, 397–428. [Google Scholar] [CrossRef]
- Gerber, A. Top 10 IoT Security Challenges. Available online: https://developer.ibm.com/articles/iot-top-10-iot-security-challenges/ (accessed on 2 July 2019).
- Lu, Y.; Xu, L.D. Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics. IEEE Internet Things J. 2019, 6, 2103–2115. [Google Scholar] [CrossRef]
- Cirani, S.; Picone, M.; Gonizzi, P.; Veltri, L.; Ferrari, G. IoT-OAS: An oauth-based authorization service architecture for secure services in IoT scenarios. IEEE Sens. J. 2015, 15, 1224–1234. [Google Scholar] [CrossRef]
- Hummen, R.; Shafagh, H.; Raza, S.; Voig, T.; Wehrle, K. Delegation-based authentication and authorization for the IP-based Internet of Things. In Proceedings of the 11th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Singapore, 30 June–3 July 2014; pp. 284–292. [Google Scholar]
- Moosavi, S.R.; Gia, T.N.; Rahmani, A.M.; Nigussie, E.; Virtanen, S.; Isoaho, J.; Tenhunen, H. SEA: A secure and efficient authentication and authorization architecture for IoT-based healthcare using smart gateways. Procedia Comput. Sci. 2015, 52, 452–459. [Google Scholar] [CrossRef]
- Aman, M.N.; Chua, K.C.; Sikdar, B. Mutual Authentication in IoT Systems Using Physical Unclonable Functions. IEEE Internet Things J. 2017, 4, 1327–1340. [Google Scholar] [CrossRef]
- Aman, M.N.; Basheer, M.H.; Sikdar, B. Two-Factor Authentication for IoT With Location Information. IEEE Internet Things J. 2019, 6, 3335–3351. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Lightweight and Privacy-Preserving Two-Factor Authentication Scheme for IoT Devices. IEEE Internet Things J. 2019, 6, 580–589. [Google Scholar] [CrossRef]
- Li, N.; Liu, D.; Nepal, S. Lightweight Mutual Authentication for IoT and Its Applications. IEEE Trans. Sustain. Comput. 2017, 2, 359–370. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Piro, G.; Boggia, G.; Bianchi, G. Public Key Authentication and Key Agreement in IoT Devices with Minimal Airtime Consumption. IEEE Embed. Syst. Lett. 2017, 9, 1–4. [Google Scholar] [CrossRef]
- Xiong, L.; Jianwei, N.; Saru, K.; Fan, W.; Arun, K.S.; Raymond, K.-K.C. A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl. 2017, 103, 194–204. [Google Scholar]
- Kumari, S.; Karuppiah, M.; Das, A.K.; Li, X.; Wu, F.; Kumar, N. A secure authentication scheme based on elliptic curve cryptography for IoT and cloud servers. J. Supercomput. 2017, 74, 6428–6453. [Google Scholar] [CrossRef]
- Dhillon, P.K.; Kalra, S. Multi-factor user authentication scheme for IoT-based healthcare services. J. Reliab. Intell. Environ. 2018, 4, 141–160. [Google Scholar] [CrossRef]
- Xie, Q.; Wong, D.S.; Wang, G.; Tan, X.; Chen, K.; Fang, L. Provably Secure Dynamic ID-Based Anonymous Two-Factor Authenticated Key Exchange Protocol with Extended Security Model. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1382–1392. [Google Scholar] [CrossRef]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT security through authentication of wireless nodes using in-situ machine learning. IEEE Internet Things J. 2019, 6, 388–398. [Google Scholar] [CrossRef]
- Alizai, Z.A.; Tareen, N.F.; Jadoon, I. Improved IoT device authentication scheme using device capability and digital signatures. In Proceedings of the International Conference on Applied and Engineering Mathematics, London, UK, 4–6 July 2018; pp. 115–119. [Google Scholar]
- Shah, R.H.; Salapurkar, D.P. A multifactor authentication system using secret splitting in the perspective of Cloud of Things. In Proceedings of the International Conference on Emerging Trends & Innovation in ICT (ICEI), Pune, India, 3–5 February 2017; pp. 1–4. [Google Scholar]
- Mininet-IoT Emulator of Internet of Things. Available online: https://github.com/ramonfontes/mininet-iot (accessed on 4 April 2019).
- IPv6 over Low-Power Wireless Personal Area Networks (6LoWPANs): Overview, Assumptions, Problem Statement, and Goals. Available online: http://www.ietf.org/rfc/rfc4919.txt. (accessed on 16 Aug 2016).
- Saleem, K.; Khalil, M.S.; Fisal, N.; Ahmed, A.A.; Orgun, M.A. Efficient Random Key Based Encryption System for Data Packet Confidentiality in WSNs. In Proceedings of the 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 13–16 July 2013; pp. 1662–1668. [Google Scholar]
- Ahmed, A.A.; Fisal, N. Secure real-time routing protocol with load distribution in wireless sensor networks. Secur. Commun. Netw. 2011, 4, 839–869. [Google Scholar] [CrossRef]
- TOTP Library source code. Available online: https://github.com/pyauth/pyotp. (accessed on 27 May 2019).



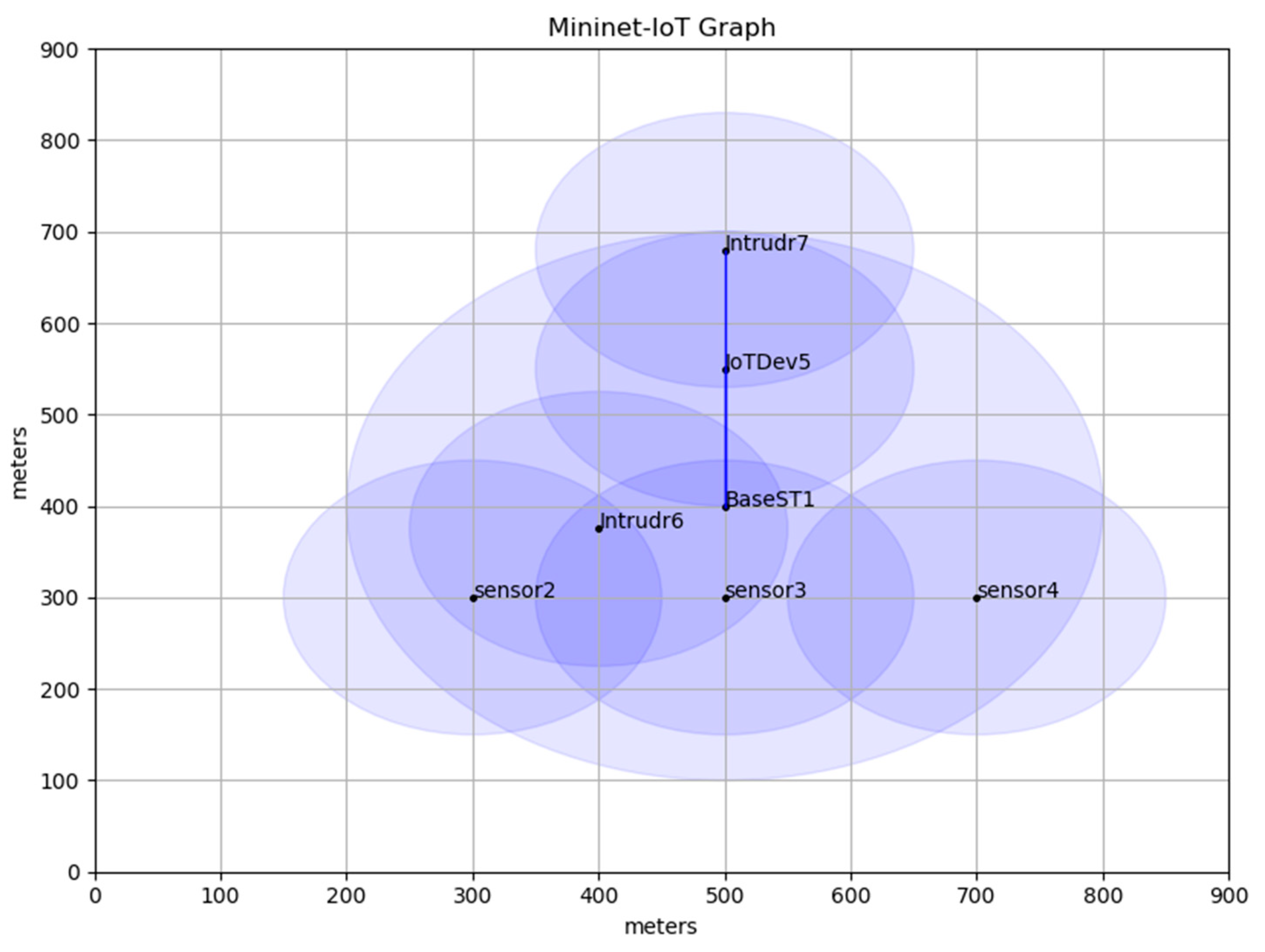
| Parameter | Values |
|---|---|
| MAC and PHY | 802.15.14_hmsim and 802.11_hmsim |
| Propagation Model | Shadowing |
| Path loss exponent | 3.0 |
| Shadowing deviation (dB) | 3.0 |
| Emulation area | (1000 m × 1000 m) 1.0 Km2 |
| Range of IoT device | 150 m |
| Radio range of BaseST1 | 250 m |
| Protocols used | TCP, UDP, ICMP |
| Number of Intruders | 2 |
| Traffic Emulator | Iperf with TCP, Iperf with UDP |
| Traffic Type | Constant Bit Rate (CBR) |
| Traffic Load | 1 packet/second (pkt/s)–10 packet/second (pkt/s) |
| Performance metrics | Throughput, latency, packet loss ratio, authentication failure ratio, and computation time overhead |
| K1, K1 and SALT length size | 4 bytes |
| TOTP | PyOTP |
| Emulation duration | 1000 s |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmed, A.A.; Ahmed, W.A. An Effective Multifactor Authentication Mechanism Based on Combiners of Hash Function over Internet of Things. Sensors 2019, 19, 3663. https://doi.org/10.3390/s19173663
Ahmed AA, Ahmed WA. An Effective Multifactor Authentication Mechanism Based on Combiners of Hash Function over Internet of Things. Sensors. 2019; 19(17):3663. https://doi.org/10.3390/s19173663
Chicago/Turabian StyleAhmed, Adel Ali, and Waleed Ali Ahmed. 2019. "An Effective Multifactor Authentication Mechanism Based on Combiners of Hash Function over Internet of Things" Sensors 19, no. 17: 3663. https://doi.org/10.3390/s19173663
APA StyleAhmed, A. A., & Ahmed, W. A. (2019). An Effective Multifactor Authentication Mechanism Based on Combiners of Hash Function over Internet of Things. Sensors, 19(17), 3663. https://doi.org/10.3390/s19173663





