Robust Multiple Servers Architecture Based Authentication Scheme Preserving Anonymity
Abstract
1. Introduction
2. Preliminaries
- : Inputs biometric template B, outputs an authenticated value and an auxiliary value .
- : For all , if and , then .
3. Review of Kumari and Om’s Scheme
3.1. Initialization Phase
3.2. Registration Phase
3.2.1. Server Registration
3.2.2. User Registration
3.3. Login Phase
3.4. Authentication Phase
3.5. Password Changing Phase
4. Cryptanalysis of Kumari and Om’s Scheme
4.1. Impersonation Attacks
4.2. Failure of Preserving Anonymity
4.3. Server Spoofing Attack
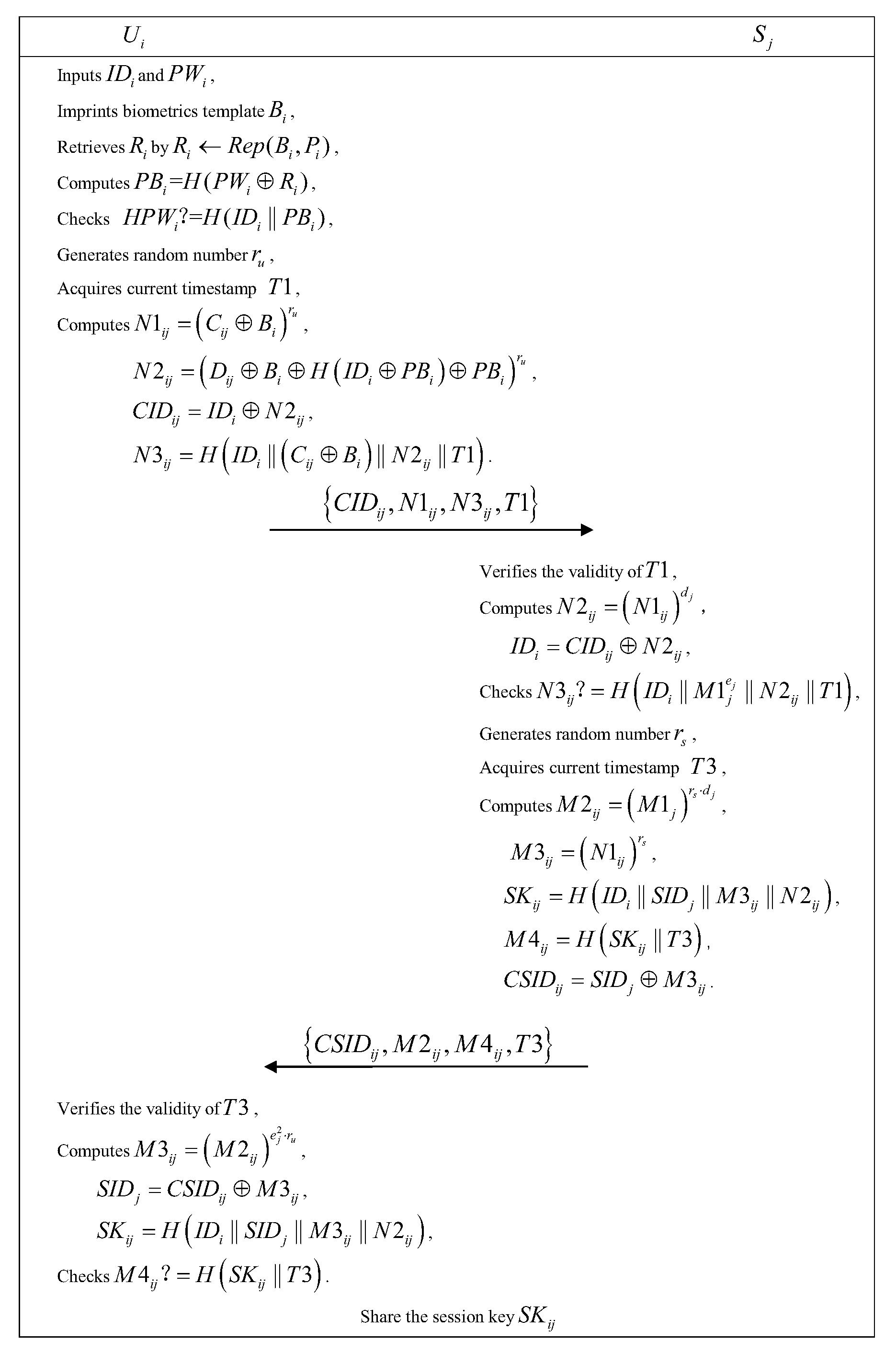
5. Our Scheme
5.1. Initialization Phase
5.2. Registration Phase
5.2.1. Server Registration
5.2.2. User Registration
5.3. Login Phase
5.4. Authentication Phase
5.5. Password Changing Phase
6. Security Analysis and Discussion
6.1. Authentication Proof Based on BAN-Logic
- : The principal believes a statement X or would be entitled to believe X.
- : The formula X is fresh.
- : The principal has jurisdiction over the statement X.
- : The principal sees the statement X.
- : The principal once said the statement X.
- : The formula X or Y is one part of the formula .
- : The formula X is combined with the formula Y.
- : The principals and use the shared key K to communicate. Here, K will never be discovered by any principal except for and .
- : K is shared secret known to , , and possibly to one trusted by them.
- : The session key used in the current session.
- The message-meaning rule: .
- The freshness-conjuncatenation rule: .
- The nonce-verification rule: .
- The jurisdiction rule: , , , .
- Goal 1:
- Goal 2:
- Message 1: :
- Message 2: :
- A.1:
- A.2:
- A.3:
- A.4:
- A.5:
- A.6:
- A.7:
6.2. Discussion on Possible Attacks
6.2.1. Preserve User Privacy
6.2.2. Off-Line Password Guessing Attack
6.2.3. Impersonation Attack
6.2.4. Server Spoofing Attack
6.2.5. Replay Attacks
6.2.6. Forward Secrecy
7. Performance and Functionality Analysis
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Das, M.; Saxena, A.; Gulati, V. A dynamic ID-based remote user authentication scheme. IEEE Trans. Consum. Electron. 2004, 50, 665–667. [Google Scholar] [CrossRef]
- Li, X.; Wen, Q.; Zhang, H.; Jin, Z. An improved authentication with key agreement scheme on elliptic curve cryptosystem for global mobility networks. Int. J. Netw. Manag. 2013, 23, 311–324. [Google Scholar] [CrossRef]
- Guo, D.; Wen, Q.; Li, W.; Zhang, H.; Jin, Z. A Novel Authentication Scheme Using Self-certified Public Keys for Telecare Medical Information Systems. J. Med. Syst. 2015, 39, 62. [Google Scholar] [CrossRef] [PubMed]
- Guo, D.; Wen, Q.; Li, W.; Zhang, H.; Jin, Z. Analysis and Improvement of ‘Chaotic Map Based Mobile Dynamic ID Authenticated Key Agreement Scheme’. Wirel. Pers. Commun. 2015, 83, 35–48. [Google Scholar] [CrossRef]
- Shahzad, M.; Singh, M.P. Continuous Authentication and Authorization for the Internet of Things. IEEE Internet Comput. 2017, 21, 86–90. [Google Scholar] [CrossRef]
- Tan, H.; Gui, Z.; Chung, I. A Secure and Efficient Certificateless Authentication Scheme with Unsupervised Anomaly Detection in VANETs. IEEE Access 2018, 6, 74260–74276. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. A Secure and Efficient Group Key Management Protocol with Cooperative Sensor Association in WBANs. Sensors 2018, 18, 3930. [Google Scholar] [CrossRef] [PubMed]
- Shahzad, M.; Liu, A. Fast and Accurate Estimation of RFID Tags. IEEE/ACM Trans. Netw. 2015, 23, 241–254. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inf. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-Factor Authentication with Security Beyond Conventional Bound. IEEE Trans. Dependable Secure Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Jiang, Q.; Qian, Y.; Ma, J.; Ma, X.; Cheng, Q.; Wei, F. User Centric Three-Factor Authentication Protocol For Cloud-Assisted Wearable Devices. Int. J. Commun. Syst. 2019, 32, e3900. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Yang, C.; Ma, X.; Shen, J.; Chaudhry, S. Efficient end-to-end authentication protocol for wearable health monitoring systems. Comput. Electr. Eng. 2017, 63, 182–195. [Google Scholar] [CrossRef]
- Liao, Y.; Wang, S. A secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interface 2009, 19, 13–22. [Google Scholar] [CrossRef]
- Hsiang, H.; Shih, W. Improvement of the secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interface 2009, 31, 1118–1123. [Google Scholar] [CrossRef]
- Sood, S.; Sarje, A.; Singh, K. A secure dynamic identity based authentication protocol for multi-server architecture. J. Netw. Comput. Appl. 2011, 34, 609–618. [Google Scholar] [CrossRef]
- Chuang, M.C.; Chen, M.C. An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst. Appl. 2014, 41, 1411–1418. [Google Scholar] [CrossRef]
- Li, X.; Xiong, Y.; Ma, J.; Wang, W. An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. J. Netw. Comput. Appl. 2012, 35, 763–769. [Google Scholar] [CrossRef]
- Li, X.; Ma, J.; Wang, W.; Xiong, Y.; Zhang, J. A novel smart card and dynamic ID based remote user authentication scheme for multi-server environments. Math. Comput. Model. 2013, 58, 85–95. [Google Scholar] [CrossRef]
- Guo, D.; Wen, F. Analysis and improvement of a robust smart card based-authentication scheme for multi-server architecture. Wirel. Pers. Commun. 2014, 78, 475–490. [Google Scholar] [CrossRef]
- Wang, B.; Ma, M. A smart card based efficient and secured multi-server authentication scheme. Wirel. Pers. Commun. 2013, 68, 361–378. [Google Scholar] [CrossRef]
- Pippal, R.; Jaidhar, C.; Tapaswi, S. Robust smart card authentication scheme for multi-server architecture. Wirel. Pers. Commun. 2013, 72, 729–745. [Google Scholar] [CrossRef]
- Xue, K.; Hong, P.; Ma, C. A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. J. Comput. Syst. Sci. 2014, 80, 195–206. [Google Scholar] [CrossRef]
- Kumari, S.; Om, H. Cryptanalysis and Improvement of an Anonymous Multi-server Authenticated Key Agreement Scheme. Wirel. Pers. Commun. 2017, 96, 2513–2537. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. Cryptanalysis and improvement of a chaotic maps-based anonymous authenticated key agreement protocol for multiserver architecture. Secur. Commun. Netw. 2016, 9, 1321–1330. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. A chaotic map-based anonymous multi-server authenticated key agreement protocol using smart card. Int. J. Commun. Syst. 2015, 28, 1955–1963. [Google Scholar] [CrossRef]
- Jangirala, S.; Mukhopadhyay, S.; Das, A.K. A Multi-server Environment with Secure and Efficient Remote User Authentication Scheme Based on Dynamic ID Using Smart Cards. Wirel. Pers. Commun. 2017, 95, 2735–2767. [Google Scholar] [CrossRef]
- Juels, A.; Wattenberg, M. A fuzzy commitment scheme. In Proceedings of the 6th ACM Conference on Computer and Communications Security, Kent Ridge Digital Labs, Singapore, 1–4 November 1999; ACM: New York, NY, USA, 1999; pp. 28–36. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the 19th Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Messerges, T.; Dabbish, E.; Sloan, R. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 5, 541–552. [Google Scholar] [CrossRef]

| User | |
| Service providing server | |
| Registration center | |
| Identification of user | |
| Password of user | |
| Public identification of server | |
| Biometrics information of user | |
| Secret key of registration center | |
| Two distinct large primes | |
| , | |
| Session key shared between user and server | |
| Hash function | |
| ⊕ | Exclusive-OR operation |
| ∥ | String concatenation operation |
| [16] | [23] | [26] | Ours | |
|---|---|---|---|---|
| Prevention of impersonation attack | No | No | No | Yes |
| Prevention of off-line password guessing attack | Yes | No | Yes | Yes |
| Prevention of server spoofing attack | No | No | No | Yes |
| Preserving user privacy | Yes | No | No | Yes |
| Prevention of replay attack | No | Yes | Yes | Yes |
| Formal security proof | No | Yes | Yes | Yes |
| Mutual authentication | No | No | No | Yes |
| Smart card breach attack | Yes | No | No | Yes |
| Perfect forward secrecy | No | Yes | Yes | Yes |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, H.; Guo, D.; Zhang, H.; Wen, Q. Robust Multiple Servers Architecture Based Authentication Scheme Preserving Anonymity. Sensors 2019, 19, 3144. https://doi.org/10.3390/s19143144
Wang H, Guo D, Zhang H, Wen Q. Robust Multiple Servers Architecture Based Authentication Scheme Preserving Anonymity. Sensors. 2019; 19(14):3144. https://doi.org/10.3390/s19143144
Chicago/Turabian StyleWang, Huawei, Dianli Guo, Hua Zhang, and Qiaoyan Wen. 2019. "Robust Multiple Servers Architecture Based Authentication Scheme Preserving Anonymity" Sensors 19, no. 14: 3144. https://doi.org/10.3390/s19143144
APA StyleWang, H., Guo, D., Zhang, H., & Wen, Q. (2019). Robust Multiple Servers Architecture Based Authentication Scheme Preserving Anonymity. Sensors, 19(14), 3144. https://doi.org/10.3390/s19143144





