Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes
Abstract
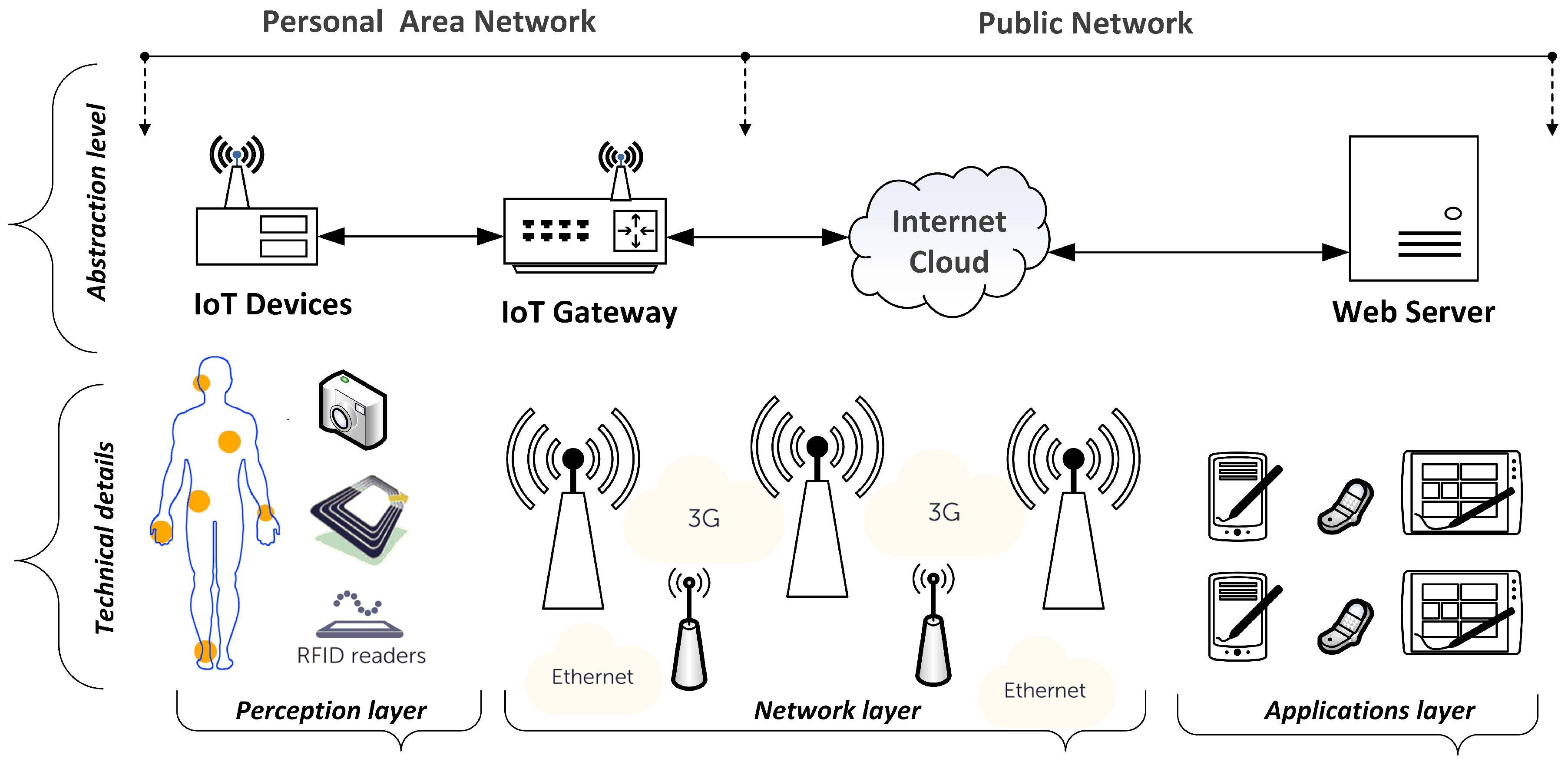
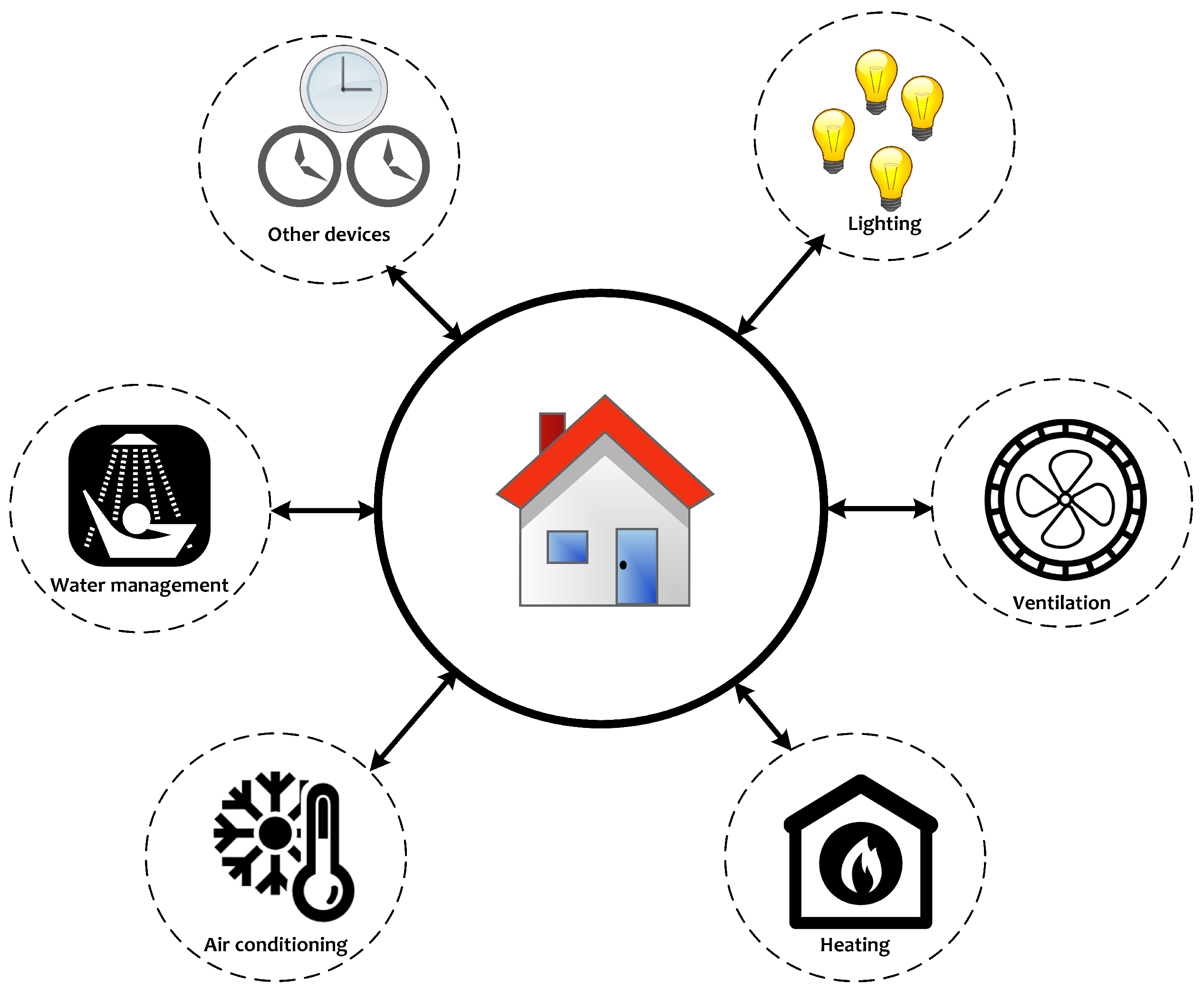
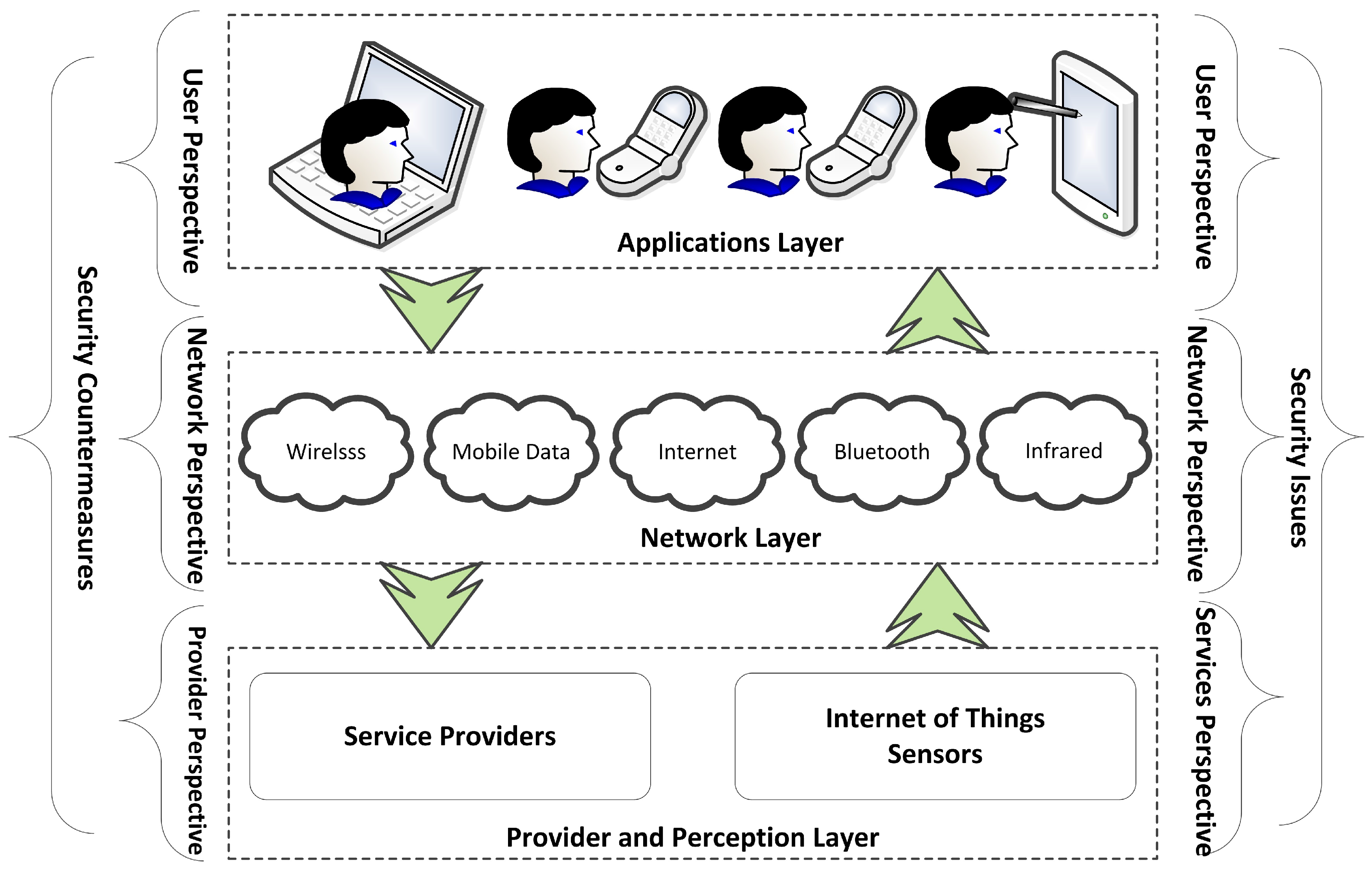
:1. Introduction
2. Related Work
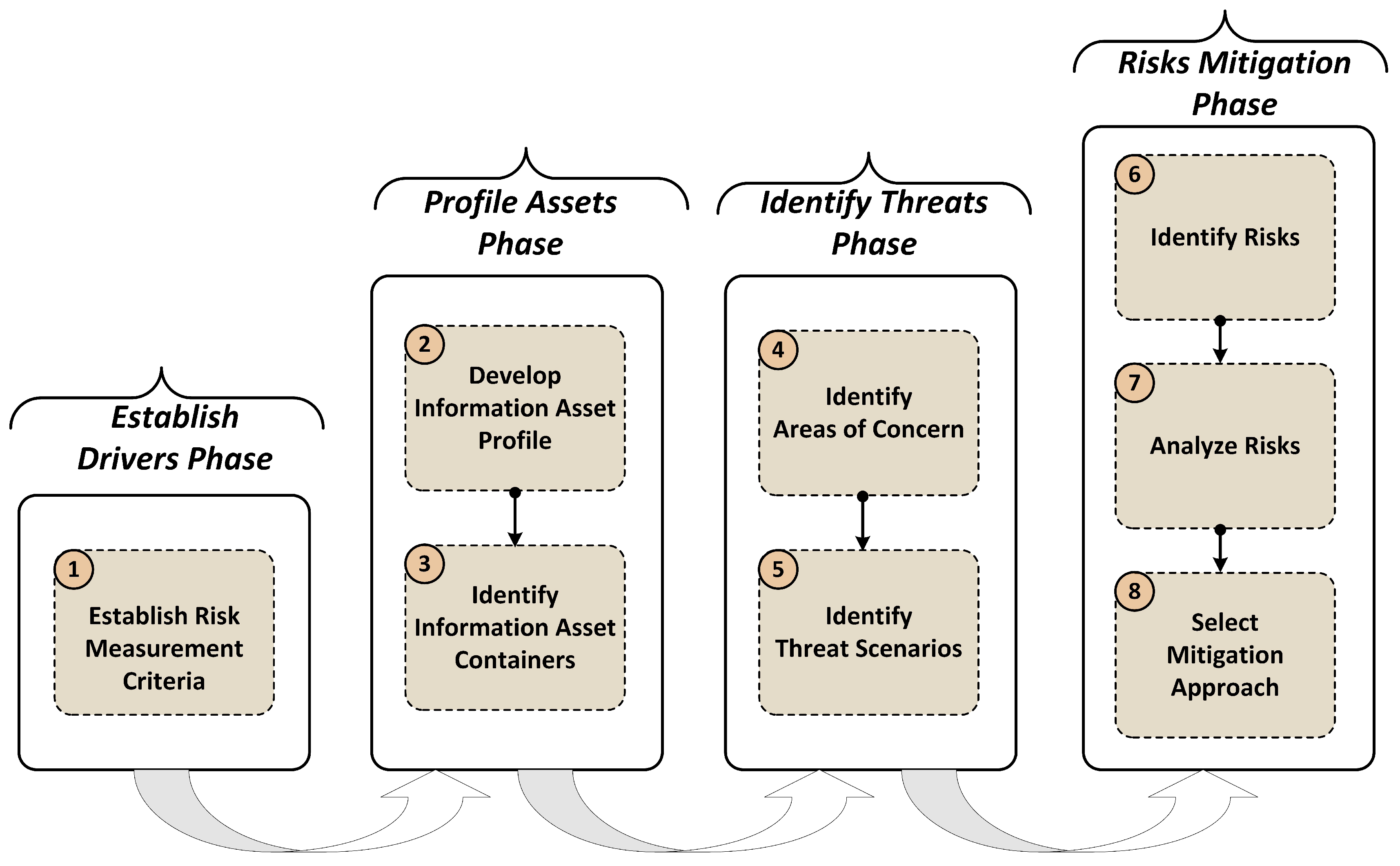
3. Risk Assessment Approach
3.1. Establish Drivers Phase
3.2. Profile Assets Phase
3.3. Identify Threats Phase
3.4. Risk Mitigation Phase
4. Results
Risks and Mitigation Approaches in Action
5. Discussion
6. Conclusions
Author Contributions
Conflicts of Interest
References
- King, J.; Awad, A.I. A Distributed Security Mechanism for Resource-Constrained IoT Devices. Informatica (Slovenia) 2016, 40, 133–143. [Google Scholar]
- Ning, H. Unit and Ubiquitous Internet of Things; CRC Press, Inc.: Boca Raton, FL, USA, 2013. [Google Scholar]
- Miller, M. The Internet of Things: How Smart TVs, Smart Cars, Smart Homes, and Smart Cities are Changing the World; Que Publishing: Indianapolis, Indiana, 2015. [Google Scholar]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Suryadevara, N.K.; Mukhopadhyay, S.C. Smart Homes: Design, Implementation and Issues; Springer: Cham, Switzerland, 2015. [Google Scholar]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 10th International Conference on Frontiers of Information Technology, Islamabad, India, 17–19 December 2012; pp. 257–260. [Google Scholar]
- Fabi, V.; Spigliantini, G.; Corgnati, S.P. Insights on Smart Home Concept and Occupants’ Interaction with Building Controls. Energy Procedia 2017, 111, 759–769. [Google Scholar] [CrossRef]
- Harper, R. (Ed.) Inside the Smart Home: Ideas, Possibilities and Methods. In Inside the Smart Home; Springer: London, UK, 2003; pp. 1–13. [Google Scholar]
- Aarts, E.; Marzano, S. The New Everyday: Views on Ambient Intelligence; 010 Publishers: Rotterdam, The Netherlands, 2003. [Google Scholar]
- Nunes, R.J.C.; Delgado, J.C.M. An Internet Application for Home Automation. In Proceedings of the 10th Mediterranean Electrotechnical Conference, Lemesos, Cyprus, 29–31 May 2000; Volume 1, pp. 298–301. [Google Scholar]
- Erdogan, S.Z. Mobility Monitoring by Using RSSI in Wireless Sensor Networks. In Recent Trends in Networks and Communications, Proceedings of the International Conferences, NeCoM 2010, WiMoN 2010, WeST 2010, Chennai, India, 23–25 July 2010; Meghanathan, N., Boumerdassi, S., Chaki, N., Nagamalai, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 572–580. [Google Scholar]
- Al-sumaiti, A.S.; Ahmed, M.H.; Salama, M.M.A. Smart Home Activities: A Literature Review. Electr. Power Compon. Syst. 2014, 42, 294–305. [Google Scholar] [CrossRef]
- Zupancic, D.; Cvetkovic, B. Smart-home Energy Management in the Context of Occupants’ Activity. Informatica (Slovenia) 2014, 38, 171–180. [Google Scholar]
- Granzer, W.; Kastner, W.; Neugschwandtner, G.; Praus, F. Security in Networked Building Automation Systems. In Proceedings of the 2006 IEEE International Workshop on Factory Communication Systems, Torino, Italy, 28–30 June 2006; pp. 283–292. [Google Scholar]
- Al-Qutayri, H.A.; Jeedella, J.S. IIntegrated Wireless Technologies for Smart Homes Applications. In Smart Home Systems; Al-Qutayri, M.A., Ed.; InTech: Rijeka, Croatia, 2010; pp. 1–27. [Google Scholar]
- Kyas, O. How to Smart Home; Key Concept Press: Wyk auf Föhr, Germany, 2013. [Google Scholar]
- De Silva, L.C.; Morikawa, C.; Petra, I.M. State of the Art of Smart Homes. Eng. Appl. Artif. Intell. 2012, 25, 1313–1321. [Google Scholar] [CrossRef]
- Acharjya, D.P.; Geetha, M.K. Internet of Things: Novel Advances and Envisioned Applications, 1st ed.; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Shen, B.; Lin, Y.; Wang, X. Research on Data Mining Models for the Internet of Things. In Proceedings of the 2010 International Conference on Image Analysis and Signal Processing, Zhejiang, China, 9–11 April 2010; pp. 127–132. [Google Scholar]
- Kang, B.; Liu, F.; Yun, Z.; Liang, Y. Design of an Internet of Things-based Smart Home System. In Proceedings of the 2011 2nd International Conference on Intelligent Control and Information Processing, Harbin, China, 25–28 July 2011; Volume 2, pp. 921–924. [Google Scholar]
- Evans, D. The Internet of Things: How the Next Evolution of the Internet is Changing Everything; Cisco Internet Business Solutions Group (IBSG): San Jose, CA, USA, 2011. [Google Scholar]
- Montano, C.; Lundmark, M.; Mähr, W. Control vs. Convenience: Critical Factors of Smart Homes. In Proceedings of the 2nd Scandinavian Student Interaction Design Research Conference, Gothenburg, Sweden, 25–26 February 2006. [Google Scholar]
- Bandyopadhyay, S.; Sengupta, M.; Maiti, S.; Dutta, S. A Survey of Middleware for Internet of Things. In Recent Trends in Wireless and Mobile Networks, Proceedings of the Third International Conferences, WiMo 2011 and CoNeCo 2011, Ankara, Turkey, 26–28 June 2011; Özcan, A., Zizka, J., Nagamalai, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 288–296. [Google Scholar]
- Papadopoulos, K.; Zahariadis, T.; Leligou, N.; Voliotis, S. Sensor Networks Security Issues in Augmented Home Environment. In Proceedings of the 2008 IEEE International Symposium on Consumer Electronics, Las Vegas, NV, USA, 9–13 January 2008; pp. 1–4. [Google Scholar]
- He, J.; Xiao, Q.; He, P.; Pathan, M.S. An Adaptive Privacy Protection Method for Smart Home Environments Using Supervised Learning. Future Internet 2017, 9, 7. [Google Scholar] [CrossRef]
- Ricquebourg, V.; Menga, D.; Durand, D.; Marhic, B.; Delahoche, L.; Loge, C. The Smart Home Concept: Our Immediate Future. In Proceedings of the 2006 1st IEEE International Conference on E-Learning in Industrial Electronics, Hammamet, Tunisia, 18–20 December 2006; pp. 23–28. [Google Scholar]
- Chaqfeh, M.A.; Mohamed, N. Challenges in Middleware Solutions for the Internet of Things. In Proceedings of the 2012 International Conference on Collaboration Technologies and Systems (CTS), Denver, CO, USA, 21–25 May 2012; pp. 21–26. [Google Scholar]
- Yoo, D.Y.; Shin, J.W.; Choi, J.Y. Home-network Security Model in Ubiquitous Environment. Proc. World Acad. Sci. Eng. Technol. 2007, 26. Available online: http://waset.org/publications/2785 (accessed on 6 March 2018).
- Liu, Y.; Hu, S.; Ho, T.Y. Vulnerability Assessment and Defense Technology for Smart Home Cybersecurity Considering Pricing Cyberattacks. In Proceedings of the 2014 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 2–6 November 2014; pp. 183–190. [Google Scholar]
- Nixon, P.A.; Wagealla, W.; English, C.; Terzis, S. Security, Privacy and Trust Issues in Smart Environments. In Smart Environments; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2005; pp. 249–270. [Google Scholar]
- Schiefer, M. Smart Home Definition and Security Threats. In Proceedings of the 2015 Ninth International Conference on IT Security Incident Management IT Forensics, Magdeburg, Germany, 18–20 May 2015; pp. 114–118. [Google Scholar]
- Can, O.; Sahingoz, O.K. A Survey of Intrusion Detection Systems in Wireless Sensor Networks. In Proceedings of the 2015 6th International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO), Istanbul, Turkey, 27–29 May 2015; pp. 1–6. [Google Scholar]
- Rubio-Loyola, J.; Sala, D.; Ali, A.I. Maximizing Packet Loss Monitoring Accuracy for Reliable Trace Collections. In Proceedings of the 16th IEEE Workshop on Local and Metropolitan Area Networks (LANMAN2008), Chij-Napoca, Transylvania, Romania, 3–6 September 2008; pp. 61–66. [Google Scholar]
- Rubio-Loyola, J.; Sala, D.; Ali, A.I. Accurate Real-time Monitoring of Bottlenecks and Performance of Packet Trace Collection. In Proceedings of the 33rd IEEE Conference on Local Computer Networks (LCN2008), Montreal, QC, Canada, 14–17 October 2008; pp. 884–891. [Google Scholar]
- Jacobsson, A.; Boldt, M.; Carlsson, B. A Risk Analysis of a Smart Home Automation System. Future Gener. Comput. Syst. 2016, 56, 719–733. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and Challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Wu, T.; Zhao, G. A Novel Risk Assessment Model for Privacy Security in Internet of Things. Wuhan Univ. J. Nat. Sci. 2014, 19, 398–404. [Google Scholar] [CrossRef]
- Nurse, J.R.C.; Creese, S.; Roure, D.D. Security Risk Assessment in Internet of Things Systems. IT Prof. 2017, 19, 20–26. [Google Scholar] [CrossRef]
- Yang, L.; Yang, S.H.; Yao, F. Safety and Security of Remote Monitoring and Control of Intelligent Home Environments. In Proceedings of the 2006 IEEE International Conference on Systems, Man and Cybernetics, Taipei, Taiwan, 8–11 October 2006; Volume 2, pp. 1149–1153. [Google Scholar]
- Mantoro, T.; Ayu, M.A.; Mahmod, S.M.B. Securing the Authentication and Message Integrity for Smart Home using Smart Phone. In Proceedings of the 2014 International Conference on Multimedia Computing and Systems (ICMCS), Marrakech, Morocco, 14–16 April 2014; pp. 985–989. [Google Scholar]
- Tong, J.; Sun, W.; Wang, L. An Information Flow Security Model for Home Area Network of Smart Grid. In Proceedings of the 2013 IEEE International Conference on Cyber Technology in Automation, Control and Intelligent Systems, Nanjing, China, 26–29 May 2013; pp. 456–461. [Google Scholar]
- Caralli, R.A.; Stevens, J.F.; Young, L.R.; Wilson, W.R. Introducing Octave Allegro: Improving the Information Security Risk Assessment Process; Technical Report CMU/SEI-2007-TR-012, ESC-TR-2007-012; Software Engineering Institute: Pittsburgh, PA, USA, 2007. [Google Scholar]
- Caralli, R.; Stevens, J.; Young, L.; Wilson, W. The OCTAVE Allegro Guidebook, v 1.0; Cert Program; Software Engineering Institute: Pittsburgh, PA, USA, 2007. [Google Scholar]
- Mouton, F.; Leenen, L.; Venter, H. Social Engineering Attack Examples, Templates and Scenarios. Comput. Secur. 2016, 59, 186–209. [Google Scholar] [CrossRef]
- Awad, A.I.; Hassanien, A.E. Impact of Some Biometric Modalities on Forensic Science. In Computational Intelligence in Digital Forensics: Forensic Investigation and Applications; Muda, A.K., Choo, Y.H., Abraham, A.N., Srihari, S., Eds.; Springer: Cham, Switzerland, 2014; Volume 555, pp. 47–62. [Google Scholar]
- Okoh, E.; Awad, A.I. Biometrics Applications in e-Health Security: A Preliminary Survey. In Health Information Science; Lecture Notes in Computer Science; Yin, X., Ho, K., Zeng, D., Aickelin, U., Zhou, R., Wang, H., Eds.; Springer: Cham, Switzerland, 2015; Volume 9085, pp. 92–103. [Google Scholar]
- Awad, A.I. Fast Fingerprint Orientation Field Estimation Incorporating General Purpose GPU. In Soft Computing Applications; Advances in Intelligent Systems and Computing; Balas, V.E., Jain, L.C., Kovačević, B., Eds.; Springer: Cham, Switzerland, 2016; pp. 891–902. [Google Scholar]
- Stallings, W.; Brown, L. Computer Security: Principles and Practice, 3rd ed.; Prentice Hall Press: Upper Saddle River, NJ, USA, 2014. [Google Scholar]
- Awad, A.I.; Baba, K. Evaluation of a Fingerprint Identification Algorithm with SIFT Features. In Proceedings of the 3rd 2012 IIAI International Conference on Advanced Applied Informatics, Fukuoka, Japan, 20–22 September 2012; pp. 129–132. [Google Scholar]
- Elfatah, A.F.A.; Tarrad, I.F.; Awad, A.I.; Hamed, H.F.A. Optimized Hardware Implementation of the Advanced Encryption Standard Algorithm. In Proceedings of the 8th International Conference on Computer Engineering Systems (ICCES), Cairo, Egypt, 26–28 November 2013; pp. 197–201. [Google Scholar]
- Awad, A.I.; Baba, K. Fingerprint Singularity Detection: A Comparative Study. In Software Engineering and Computer Systems; Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 179, pp. 122–132. [Google Scholar]
- Luo, T.; Hao, H.; Du, W.; Wang, Y.; Yin, H. Attacks on WebView in the Android System. In Proceedings of the 27th Annual Computer Security Applications Conference, Orlando, FL, USA, 5–9 December 2011; ACM: New York, NY, USA, 2011; pp. 343–352. [Google Scholar]
- Krupp, B.; Sridhar, N.; Zhao, W. SPE: Security and Privacy Enhancement Framework for Mobile Devices. IEEE Trans. Dependable Secur. Comput. 2017, 14, 433–446. [Google Scholar] [CrossRef]
- Bako, A. Internet of Things Based Smart Homes: Security Risk Assessment and Recommendations. Master’s Thesis, Department of Computer Science, Electrical and Space Engineering, Luleå University of Technology, Luleå, Sweden, 2016. Available online: http://www.diva-portal.org/smash/get/diva2:1032194/FULLTEXT02.pdf (accessed on 6 March 2018).
- Das, S. Technology for Smart Home. In Proceedings of the International Conference on VLSI, Communication, Advanced Devices, Signals & Systems and Networking (VCASAN-2013), Bangalore, India, 17–19 July 2013; Chakravarthi, V.S., Shirur, Y.J.M., Prasad, R., Eds.; Springer: New Delhi, India, 2013; pp. 7–12. [Google Scholar]
- Khan, S.H.; Akbar, M.A.; Shahzad, F.; Farooq, M.; Khan, Z. Secure Biometric Template Generation for Multi-factor Authentication. Pattern Recognit. 2015, 48, 458–472. [Google Scholar] [CrossRef]
- Zadran, H. Amazing Architecture, 2017. Available online: http://amazingarchitecture.net/2017/05/19/elegant-home-plan-design-ideas/ (accessed on 6 March 2018).
- Pirbhulal, S.; Zhang, H.; E Alahi, M.E.; Ghayvat, H.; Mukhopadhyay, S.C.; Zhang, Y.T.; Wu, W. A Novel Secure IoT-based Smart Home Automation System using a Wireless Sensor Network. Sensors 2016, 17, 69. [Google Scholar] [CrossRef] [PubMed]
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A Practical Evaluation of a High-Security Energy-Efficient Gateway for IoT Fog Computing Applications. Sensors 2017, 17, 1978. [Google Scholar] [CrossRef] [PubMed]
- Moosavi, S.R.; Gia, T.N.; Rahmani, A.M.; Nigussie, E.; Virtanen, S.; Isoaho, J.; Tenhunen, H. SEA: A Secure and Efficient Authentication and Authorization Architecture for IoT-Based Healthcare Using Smart Gateways. Procedia Comput. Sci. 2015, 52, 452–459. [Google Scholar] [CrossRef]
- Gajewski, M.; Batalla, J.M.; Mastorakis, G.; Mavromoustakis, C.X. A Distributed IDS Architecture Model for Smart Home Systems. Clust. Comput. 2017. [Google Scholar] [CrossRef]
- Fathy, A.; Tarrad, I.F.; Hamed, H.F.A.; Awad, A.I. Advanced Encryption Standard Algorithm: Issues and Implementation Aspects. In Advanced Machine Learning Technologies and Applications; Communications in Computer and Information Science; Hassanien, A.E., Salem, A.M., Ramadan, R., Kim, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 322, pp. 516–523. [Google Scholar]
- Awad, A.I. Fingerprint Local Invariant Feature Extraction on GPU with CUDA. Informatica (Slovenia) 2013, 37, 279–284. [Google Scholar]
- Egawa, S.; Awad, A.I.; Baba, K. Evaluation of Acceleration Algorithm for Biometric Identification. In Networked Digital Technologies; Communications in Computer and Information Science; Benlamri, R., Ed.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 294, pp. 231–242. [Google Scholar]
- Bilal, M.; Kang, S.G. An Authentication Protocol for Future Sensor Networks. Sensors 2017, 17, 979. [Google Scholar] [CrossRef] [PubMed]

| Asset ID | Information Asset | Possible Security Threats |
|---|---|---|
| 1 | User credentials | User impersonation |
| Identity and credential theft | ||
| 2 | Mobile personal data and apps | Malicious code injected into apps installed on a phone |
| 3 | Information modification | |
| Information collected by devices | Denial-of-service (DoS) attacks | |
| Device or sensor compromising | ||
| Smart home status information | Information disclosure | |
| Function interruption | ||
| 4 | Smart home structure | Gain access to inventory information to search for a specific device with known vulnerabilities to attack smart homes |
| Inventory information | ||
| 5 | Log information | Gain access to log data and obtain useful information enabling possible attacks on a smart home system |
| 6 | Information transmitted via a gateway | Steal information from packets transmitted via a gateway |
| 7 | Smart home setup information | Information modification |
| 8 | Video feed of surveillance cameras | Control cameras to monitor and spy on users |
| 9 | Location tracking information | Observation of location data traffic |
| 10 | Information resources (e.g., pictures, documents, and music) | Steal private information |
| Make stored media inaccessible due to hardware failure |
| Threat ID | Possible Impacts (Risks) | Risk Scores |
|---|---|---|
| Unauthorized access to the main smart home system | ||
| 1 | Unauthorized execution of operations | 41 |
| Loss of control over smart home system | ||
| Adversary can take photos, record conversations, and track locations | ||
| 2 | Attacker can control the smart phone remotely | 41 |
| Attacker can make calls and access the phone microphone and camera | ||
| Sensor measurements are manipulated to infiltrate the home system | ||
| 3 | Non-presence tracking leads to home break-in | 39 |
| Financial losses | ||
| Attacker identifies the weakest device with known vulnerabilities | ||
| 4 | Attacker takes control of smart home systems | 39 |
| Financial losses | ||
| Attacker finds a way to access the main system | ||
| 5 | Attacker changes the system configuration and adding back doors | 39 |
| Financial losses | ||
| System resources are exhausted via constant self-replication | ||
| 6 | Possibility of bringing the system down, making it ultimately unusable | 39 |
| Possibility of injecting new security vulnerabilities into the system | ||
| Difficulty in setting up the smart home system correctly | ||
| 7 | Misuse of SH systems with the possibility of malfunction | 36 |
| Financial losses | ||
| User privacy violation | ||
| 8 | 34 | |
| Financial losses | ||
| User privacy violation | ||
| 9 | Breaking into the smart home if it is vacant | 34 |
| Financial losses | ||
| User privacy violation | ||
| 10 | Loss of information | 23 |
| Damage to reputation |
| Asset ID | Real-World Examples |
|---|---|
| 1 | An unauthorized individual obtains the necessary credentials and is able to login into the main smart home system. |
| 2 | The legitimate user loses his or her mobile device or it becomes stolen, and then the smart home-related apps are manipulated. The phone application can be manipulated remotely via injecting a malicious code. |
| 3 | An information asset is altered intentionally by malicious individuals to cause the power supply smart meter to show high electricity consumption. |
| Jamming and tampering at the physical layer could prevent sensors from detecting risks such as fire, flood, and unexpected motion. | |
| A compromised motion sensor could be used to determine when there are people at home. | |
| The statuses of door locks and alarm systems could be used to determine when a smart home is occupied. | |
| 4 | Attackers can gain access to this information asset by obtaining unencrypted backup media or via a social engineering attack. |
| 5 | This asset can be obtained if the log data are easily accessible via an insecure channel. |
| 6 | This asset can be obtained if the gateway is not properly secured, e.g., an open Wi-Fi network. The adversary can hijack the Wi-Fi connection, can inject a malicious code, and then takes control over the smart home system. |
| 7 | This asset can be obtained if the information asset is stored as a data file in the smart home system (e.g., a PC) without strong authentication mechanisms. |
| 8 | This asset can be obtained if such devices are outsourced to a non-serious (untrusted) third-party service provider. |
| 9 | This asset can be obtained if such information is sent from the tracking system to a listener device in clear text and is captured by an attacker. |
| 10 | This asset can be found physically or digitally, e.g., on papers, CDs, DVDs, backup media, a PC, communication networks or databases. The information can be accessed by unauthorized people if not stored properly and securely. |
| Threat ID | Possible Mitigation Approaches |
|---|---|
| Control access to the system using efficient biometric identifiers [49] | |
| 1 | Implement a user awareness program to make users aware of social engineering |
| Implement multi-factor authentication | |
| Avoid using insecure Wi-Fi, which gives hackers access to personal data | |
| 2 | Set up a secure network before using a home automation application |
| Be aware of stolen or lost devices | |
| Use a secure communication channel by utilizing a secure virtual private network (VPN) | |
| 3 | Limit network traffic such that it is accessible only to authorized users |
| Develop a security awareness training program for smart home inhabitants | |
| Use an intrusion detection system (IDS) / intrusion prevention system (IPS) | |
| 4 | Use encryption mechanisms for security data transmission [50] |
| Perform frequent data backups to keep copies of sensitive data | |
| Secure the physical locations of installed devices | |
| 5 | Provide secure access to device configuration interfaces |
| Replace the default usability configuration of installed devices | |
| Use commodity hardware and software to collect and examine network traffic [33,34] | |
| 6 | Create backups of the working system’s configurations |
| Always monitor system’s performance, looking for misbehavior incidents | |
| Apply a strong authentication mechanism such as fingerprint authentication [51] | |
| 7 | Offer awareness and training programs regarding system security |
| Ensure that system configurations are secure and performed by authentic people | |
| Restrict physical access to devices to only authentic people | |
| 8 | Avoid infrastructure outsourcing to a third-party service provider |
| Modify default device configurations to achieve a better security level | |
| Disable unnecessary location tracking services on mobile devices | |
| 9 | Develop a good understanding of user privacy concerns |
| Track system behavior to identify any suspicious privacy leakage | |
| Use only trusted and authentic networks (wired or wireless) | |
| 10 | Share information carefully and in a restricted manner |
| Use only trusted providers to receive technical support for hardware failures in smart home |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, B.; Awad, A.I. Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes. Sensors 2018, 18, 817. https://doi.org/10.3390/s18030817
Ali B, Awad AI. Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes. Sensors. 2018; 18(3):817. https://doi.org/10.3390/s18030817
Chicago/Turabian StyleAli, Bako, and Ali Ismail Awad. 2018. "Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes" Sensors 18, no. 3: 817. https://doi.org/10.3390/s18030817
APA StyleAli, B., & Awad, A. I. (2018). Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes. Sensors, 18(3), 817. https://doi.org/10.3390/s18030817






