IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”
Abstract
:1. Introduction
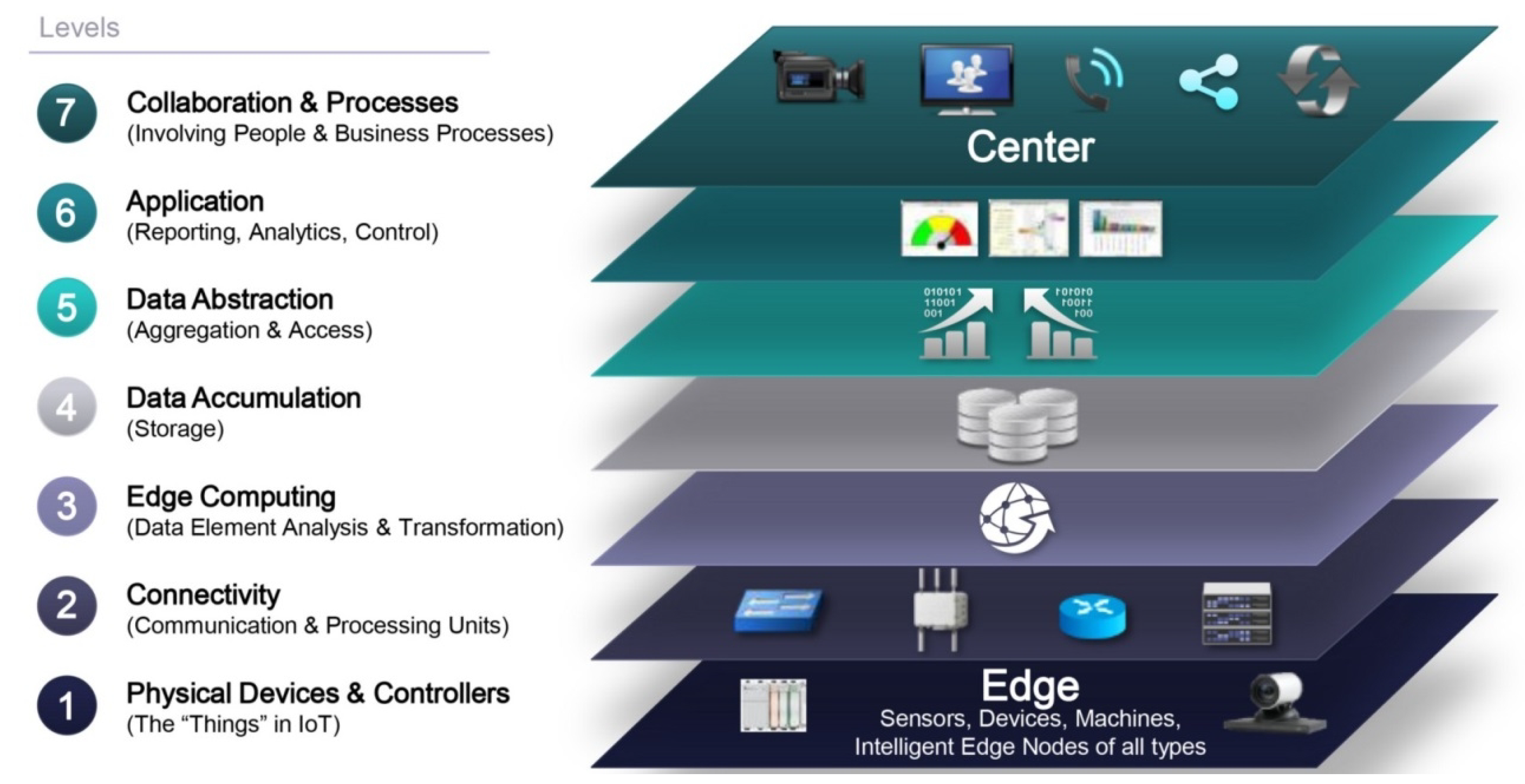
2. The Internet of Things: Infrastructure and Security Issues
3. RFID Authentication Protocols Using PUF
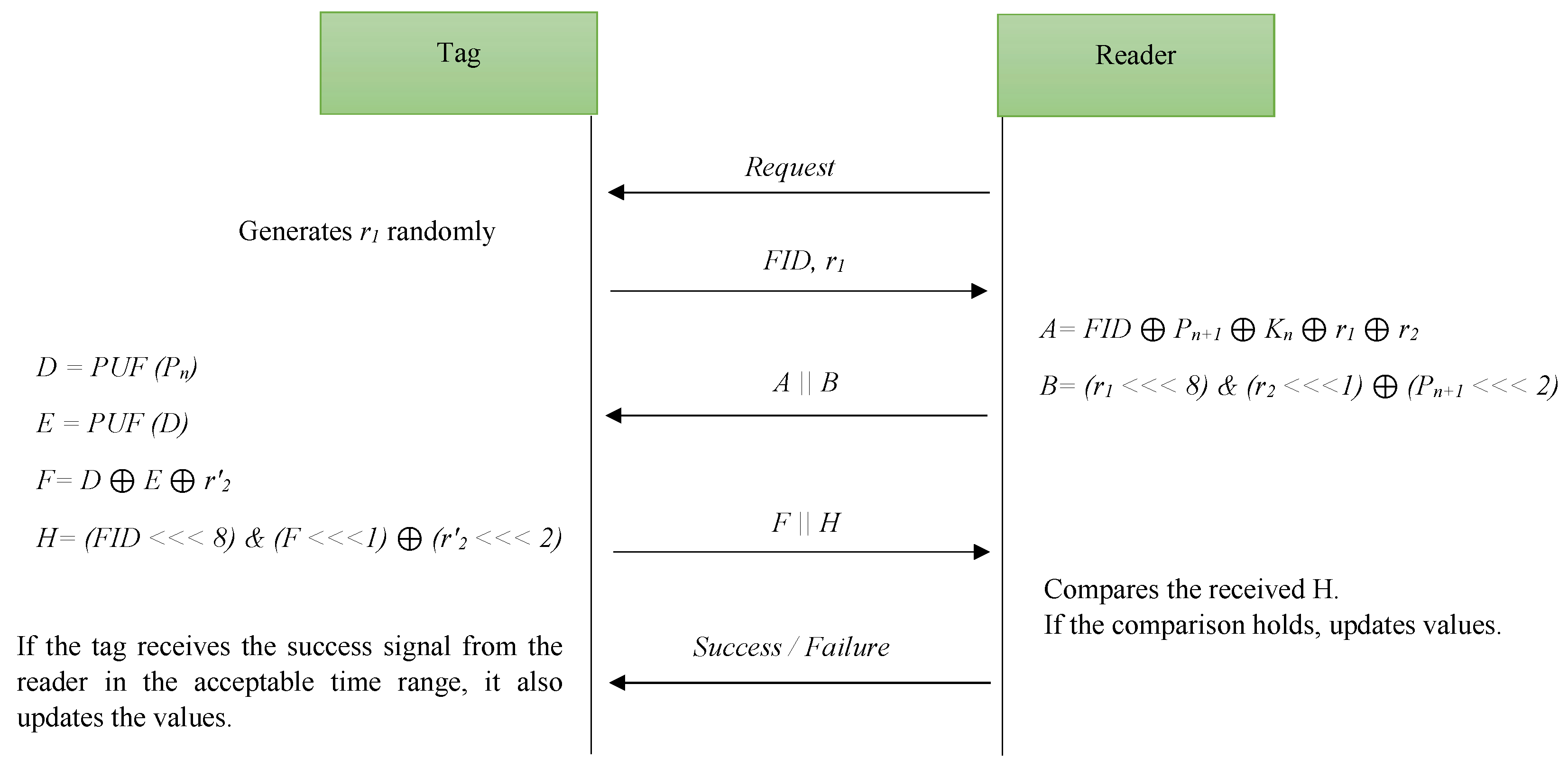
4. Xu et al.’s Protocol
4.1. Tag Verification Phase
4.2. Mutual Verification Phase
4.3. Update Process Phase
5. Security Analysis of Xu et al.’s Protocol
5.1. Desynchronization Attack
- On a legitimate session between the target tag T and the reader R, the reader starts the process and sends a search request to the tag.
- Upon receiving the request, the tag generates randomly and transfers and to the reader.
- The adversary intercepts the sent message from the tag to the reader and replaces with .
- When the reader receives , it utilizes it as a search key in the database and seeks to find an equal in the field. We assume that the comparison holds, meaning that the tag belongs to the system and the reader uses for the next phase.
- The reader generates randomly and computes A and B as:
- It concatenates A and B and transfers the combination message to the tag.
- The adversary intercepts the sent message from the reader to the tag and replaces A with .
- Upon receiving the message from the reader, the tags computes D and E as follows:
- In addition, it calculates by the receiving messages to recalculate as:
- The tag checks . If the equation does not hold, it means the reader is not valid and the session is terminated. Otherwise, the tag verifies the reader and continues the process.
- Based on D, E and calculated , the tag computes F and then H as:
- It concatenates F and H as and sends this message to the reader.
- When the reader receives the tag’s response, by local parameters, it recalculates , and as:
- Then, it checks . If it does not hold, the tag is not valid, and the reader aborts the session. Otherwise, it verifies the tag and continues the process.
- Based on the assumption in Step 4, in the update process phase of the protocol verification phase, the database updates its parameters and then sends a signal to the tag to inform it that the update process is completed. The reader updates the database as follows:
- When the tag receives the success signal from the reader in the acceptable time range, it also updates the parameters as:
5.2. Secret Disclosure Attack
- On a legitimate session between the target tag T and the reader R, the reader starts the process and sends a search request to the tag.
- Upon receiving the request, the tag generates randomly and transfers and to the reader.
- The adversary intercepts the sent message from the tag to the reader and just replaces by 0 and stores .
- When the reader receives , it utilizes it as a search key in the database and seeks to find an equal in the field. We assume that the comparison holds, meaning that the tag belongs to the system and the reader uses for the next phase.
- The reader generates randomly and computes A and B as:
- The adversary stores and blocks it, where and is the tag’s secret value and .
- The adversary waits until the reader starts the process and sends a search request to a tag.
- Upon receiving the request, the adversary sets and transfers the stored and to the reader.
- When the reader receives , it utilizes it as a search key in the database and seeks to find an equal in the field. Based on the assumption of Step 4, the comparison holds, meaning that the tag belongs to the system and the reader uses for the next phase.
- The reader generates randomly and computes and as:
- The adversary stores and blocks it, where . Given from Step 6, the adversary extracts as and as .
- The adversary impersonates the legitimate reader and sends a search request to the target tag.
- Upon receiving the request, the tag generates randomly and transfers and to the reader (adversary).
- The adversary generates randomly and computes and as follows and sends them to the tag:
- Upon receiving the message, the tag computes and , verifies the received to validate the reader and continues the process.
- Based on D, E and calculated , the tag computes F and then H as:
- It concatenates and as and sends this message to the reader (adversary).
- When the adversary receives the tag’s response, it extracts , sends a signal to the tag to inform that the update process was done, and does the following updates in the stored information related to the target tag:
- When the tag receives the success signal from the reader (adversary) in the acceptable time range, it also updates the parameters as:
- In a legitimate session between the target tag T and the reader R, the reader starts the process and sends a search request to the tag.
- Upon receiving the request, the tag generates randomly and transfers and to the reader.
- The adversary intercepts the sent message from the tag to the reader and just replaces by 0 and stores .
- When the reader receives , it utilizes it as a search key in the database and seeks to find an equal in the field. We assume that the comparison holds, meaning that the tag belongs to the system and the reader uses for the next phase.
- The reader generates randomly and computes A and B as:
- The adversary stores and blocks it, where, for any , we have and is the tag’s secret value and .
- The adversary waits until the reader starts another session of the protocol and sends a search request to a tag.
- Upon receiving the request, the adversary sets and transfers the stored and to the reader.
- When the reader receives , it utilizes it as a search key in the database and seeks to find an equal in the field. We again assume that the comparison holds, meaning that the tag belongs to the system and the reader uses for the next phase.
- The reader generates randomly and computes and as:
- The adversary stores and blocks it, where, for any . Combining these bits of with the bits retrieved in Step 6, the adversary has a whole .
- The adversary waits until the reader starts the next process and sends a search request to a tag.
- Upon receiving the request, the adversary generates a random value as , transfers and the stored to the reader.
- When the reader receives , it utilizes it as a search key in the database and seeks to find an equal in the field. Based on the assumption of Step 4, the comparison holds, meaning that the tag belongs to the system and the reader uses for the next phase.
- The reader generates randomly and computes A and B as:
- The adversary stores and blocks it, where, for any we have and . Given that the adversary has , , and , it can extract for any j that .
- The adversary waits until the reader starts another session of the protocol and sends a search request to a tag.
- Upon receiving the request, the adversary sets and transfers the stored and to the reader.
- When the reader receives , it utilizes it as a search key in the database and seeks to find an equal in the field. We again assume that the comparison holds, meaning that the tag belongs to the system and the reader uses for the next phase.
- The reader generates randomly and computes and as:
- , we have and . Given that the adversary has , , and , it can extract for any j that . Combining these bits of with the bits retrieved in Step 16, the adversary has a whole .
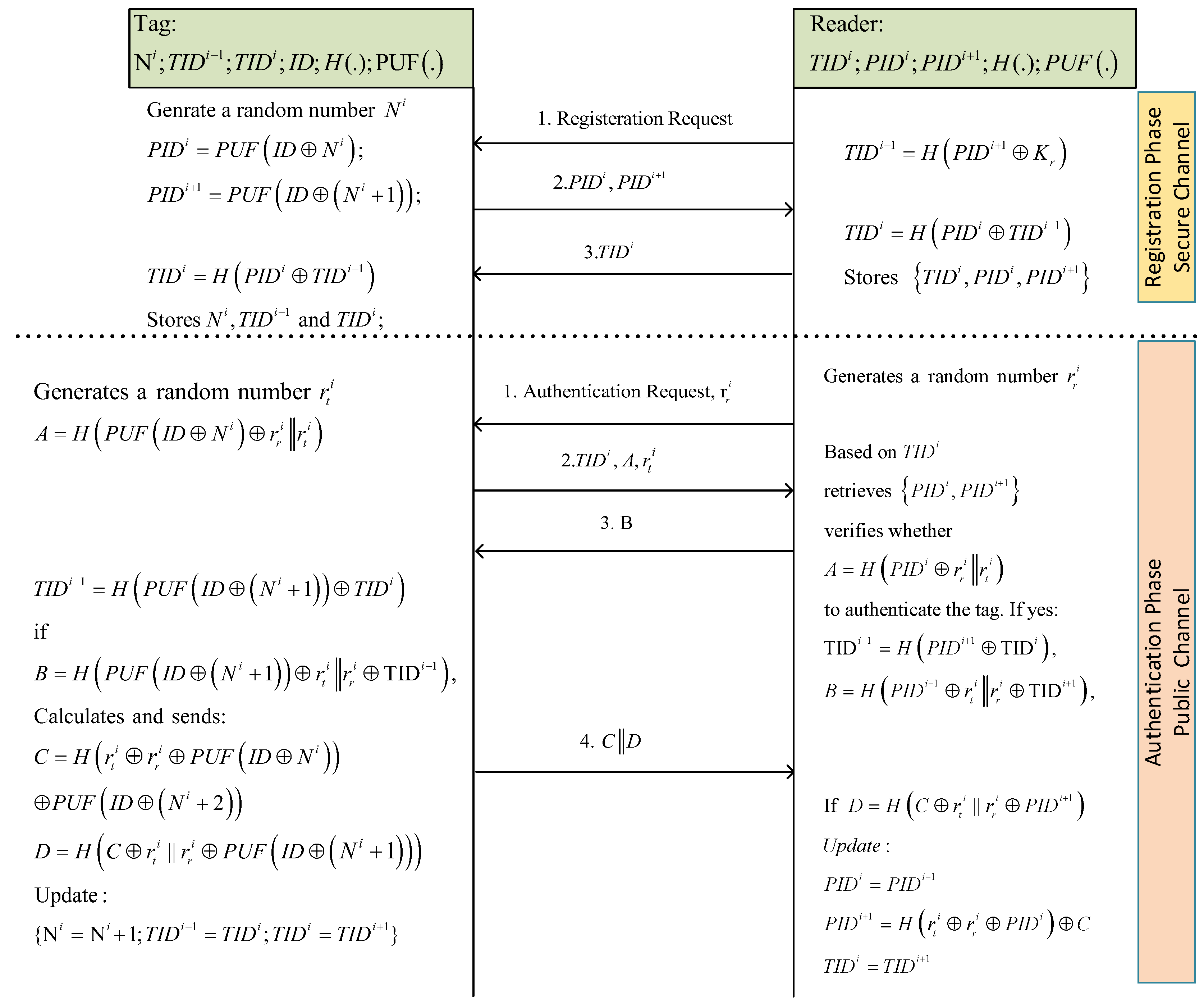
6. Improved Protocol
6.1. The Proposed Protocol
- The reader sends a registration request command to the tag.
- The tag generates a random number , calculates and as follows and sends them to the reader:
- The reader calculates a temporary identifier for the tag and sends to it, where is the secret parameter of the reader.
- It also updates as and creates a record in its database for this tag, including .
- Given , the tag calculates . It stores .
- The reader sends an authentication request command along a random number to the tag.
- The tag generates a random number , calculates and sends tuple to the reader.
- Given , the reader finds the related record in its database, i.e., . Then, the reader verifies whether to authenticate the tag. If the tag is authenticated, then the reader calculates and . Next, it sends B to the tag.
- The tag also calculates and verifies whether , to authenticate the reader. If the reader is certified as valid, the tag does the following calculations:
- Next, the tag sends to the reader and updates its records as .
- Once the reader received , it verifies whether , to authenticate the tag and the received data. If it is authenticated, then the reader updates its records as follows:
- If the tag has not been authenticated based on and , it assumes that the last session was not finished successfully and the tag tries to be authenticated based on and .
6.2. Security Evaluation of the Proposed Protocol
6.2.1. Informal Analysis
6.2.2. Formal Verification Using a Scyther Tool
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A. Implementation of the Proposed Protocol in the Scyther Tool
References
- Weiser, M. Hot topics-ubiquitous computing. Computer 1993, 26, 71–72. [Google Scholar] [CrossRef]
- Pelino, M.; Hammond, J.; Dai, C.; Miller, P.; Belissent, J.; Ask, J.; Fenwick, N.; Gillett, F.; Husson, T.; Maxim, M.; et al. Predictions 2018: IoT Moves From Experimentation To Business Scale. Available online: https://www.forrester.com/report/Predictions+2018+IoT+Moves+From+Experimentation+To+Business+Scale/-/E-RES139752 (accessed on 12 October 2018).
- Markit, I. Number of Connected IoT Devices Will Surge to 125 Billion by 2030. Available online: https://technology.ihs.com/596542/number-of-connected-iot-devices-will-surge-to-125-billion-by-2030-ihs-markit-says (accessed on 12 October 2018).
- Hung, M. Leading to IoT: Gartner Insights on How to Lead in a Connected World. Available online: https://www.gartner.com/imagesrv/books/iot/iotEbook_digital.pdf (accessed on 12 October 2018).
- Wang, K.H.; Chen, C.M.; Fang, W.; Wu, T.Y. A secure authentication scheme for Internet of Things. Pervas. Mob. Comput. 2017, 42, 15–26. [Google Scholar] [CrossRef]
- EPCglobal, G. EPC Radio-Frequency Identity Protocols Generation-2 UHF RFID; Specification for RFID Air Interface Protocol for Communications at 860 MHz–960 MHz; EPCglobal Inc.: Menlo Park, CA, USA, 2013. [Google Scholar]
- Karygiannis, T.; Eydt, B.; Barber, G.; Bunn, L.; Phillips, T. Guidelines for securing radio frequency identification (RFID) systems. NIST Spec. Pub. 2007, 80, 1–154. [Google Scholar]
- Gassend, B.; Clarke, D.; Van Dijk, M.; Devadas, S. Silicon physical random functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; Volume 1, pp. 148–160. [Google Scholar]
- RFID Startup Offers Enhanced Security for Tag Chips. Available online: https://www.rfidjournal.com/articles/view?7042 (accessed on 12 October 2018).
- Xu, H.; Ding, J.; Li, P.; Zhu, F.; Wang, R. A Lightweight RFID mutual authentication protocol based on physical unclonable function. Sensors 2018, 18, 760. [Google Scholar] [CrossRef] [PubMed]
- Kulseng, L.; Yu, Z.; Wei, Y.; Guan, Y. Lightweight mutual authentication and ownership transfer for RFID systems. In Proceedings of the 2010 Proceedings IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; Volume 1, pp. 1–5. [Google Scholar]
- Sector, S.; Itu, O. SERIES Y: GLOBAL INFORMATION INFRASTRUCTURE, INTERNET PROTOCOL ASPECTS AND NEXT-GENERATION NETWORKS Next Generation Networks–Frameworks and Functional Architecture Models; International Telecommunication Union: Geneva, Switzerland, 2012. [Google Scholar]
- Lu, Y.; Papagiannidis, S.; Alamanos, E. Internet of Things: A systematic review of the business literature from the user and organisational perspectives. Technol. Forecast. Soc. Chang. 2018, 23, 31–41. [Google Scholar] [CrossRef]
- Krotov, V. The Internet of Things and new business opportunities. Bus. Horiz. 2017, 60, 831–841. [Google Scholar] [CrossRef]
- IoT Business Models Framework UNIFY-IoT. Available online: http://www.unify-iot.eu/wp-content/uploads/2016/10/D02_01_WP02_H2020_UNIFY-IoT_Final.pdf (accessed on 12 October 2018).
- The Internet of Things Reference Model, Whipe paper. Available online: https://www.cisco.com/c/dam/global/en_ph/assets/ciscoconnect/pdf/bigdata/jim_green_cisco_connect.pdf (accessed on 12 October 2018).
- Qi, J.; Yang, P.; Min, G.; Amft, O.; Dong, F.; Xu, L. Advanced internet of things for personalised healthcare systems: A survey. Pervas. Mob. Comput. 2017, 41, 132–149. [Google Scholar] [CrossRef]
- Bendavid, Y. Positioning RFID technologies in the enterprise information systems portfolio: A case in supply chain management. Int. J. Autom. Technol. 2012, 4, 11–24. [Google Scholar]
- Tan, H.; Choi, D.; Kim, P.; Pan, S.; Chung, I. Secure Certificateless Authentication and Road Message Dissemination Protocol in VANETs. Wirel. Commun. Mob. Comput. 2018, 2018, 7978027. [Google Scholar] [CrossRef]
- Afifi, M.; Zhou, L.; Chakrabartty, S.; Ren, J. Dynamic authentication protocol using self-powered timers for passive Internet of Things. IEEE Internet Things J. 2018, 5, 2927–2935. [Google Scholar] [CrossRef]
- Tan, H.; Choi, D.; Kim, P.; Pan, S.; Chung, I. Comments on “Dual Authentication and Key Management Techniques for Secure Data Transmission in Vehicular Ad Hoc Networks”. IEEE Trans. Intell. Transp. Syst. 2018, 19, 2149–2151. [Google Scholar] [CrossRef]
- Shen, J.; Tan, H.; Zhang, Y.; Sun, X.; Xiang, Y. A new lightweight RFID grouping authentication protocol for multiple tags in mobile environment. Multimed. Tools Appl. 2017, 76, 22761–22783. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forens. Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, X.; Ye, W.; Han, Q.; Pan, X. A Compact and Low Power RO PUF with High Resilience to the EM Side-Channel Attack and the SVM Modelling Attack of Wireless Sensor Networks. Sensors 2018, 18, 322. [Google Scholar] [CrossRef] [PubMed]
- Sadeghi, A.R.; Visconti, I.; Wachsmann, C. PUF-enhanced RFID security and privacy. SECSI 2010, 110, 146–149. [Google Scholar]
- Kardaş, S.; Kiraz, M.S.; Bingöl, M.A.; Demirci, H. A novel RFID distance bounding protocol based on physically unclonable functions. In International Workshop on Radio Frequency Identification: Security and Privacy Issues; Springer: Berlin/Heidelberg, Germany, 2011; Volume 1, pp. 78–93. [Google Scholar]
- Akgun, M.; Caglayan, M.U. PUF based scalable private RFID authentication. In Proceedings of the 2011 Sixth International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, 22–26 August 2011; Volume 1, pp. 473–478. [Google Scholar]
- Akgün, M.; Çaglayan, M.U. Providing destructive privacy and scalability in RFID systems using PUFs. Ad Hoc Netw. 2015, 32, 32–42. [Google Scholar] [CrossRef]
- Kardaş, S.; ÇElik, S.; YıLdıZ, M.; Levi, A. PUF-enhanced offline RFID security and privacy. J. Netw. Comput. Appl. 2012, 35, 2059–2067. [Google Scholar] [CrossRef]
- Van Herrewege, A.; Katzenbeisser, S.; Maes, R.; Peeters, R.; Sadeghi, A.R.; Verbauwhede, I.; Wachsmann, C. Reverse fuzzy extractors: Enabling lightweight mutual authentication for PUF-enabled RFIDs. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2012; Volume 1, pp. 374–389. [Google Scholar]
- Moriyama, D.; Matsuo, S.; Yung, M. PUF-based RFID authentication secure and private under memory leakage. IACR Cryptol. ePrint Arch. 2013, 3, 61–83. [Google Scholar]
- Aysu, A.; Gulcan, E.; Moriyama, D.; Schaumont, P.; Yung, M. End-to-end design of a PUF-based privacy preserving authentication protocol. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2015; pp. 556–576. [Google Scholar]
- Huth, C.; Aysu, A.; Guajardo, J.; Duplys, P.; Güneysu, T. Secure and Private, yet Lightweight, Authentication for the IoT via PUF and CBKA. In International Conference on Information Security and Cryptology; Springer: Berlin/Heidelberg, Germany, 2016; pp. 28–48. [Google Scholar]
- Ray, B.; Howdhury, M.; Abawajy, J.; Jesmin, M. Secure object tracking protocol for Networked RFID Systems. In Proceedings of the 2015 16th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Takamatsu, Japan, 1–3 June 2015; Volume 1, pp. 1–7. [Google Scholar]
- Li, Y.; Deng, R.H.; Bertino, E. RFID security and privacy. Synth. Lect. Inf. Secur. Privacy Trust 2013, 4, 1–157. [Google Scholar] [CrossRef]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The SIMON and SPECK lightweight block ciphers. In Proceedings of the 52nd Annual Design Automation Conference, San Francisco, CA, USA, 7–11 June 2015; pp. 175:1–175:6. [Google Scholar]
- Beierle, C.; Jean, J.; Kölbl, S.; Leander, G.; Moradi, A.; Peyrin, T.; Sasaki, Y.; Sasdrich, P.; Sim, S.M. The SKINNY Family of Block Ciphers and Its Low-Latency Variant MANTIS. In Proceedings of the 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016. [Google Scholar]
- Aumasson, J.; Jovanovic, P.; Neves, S. NORX: Parallel and Scalable AEAD. In Proceedings of the 19th European Symposium on Research in Computer Security, Wroclaw, Poland, 7–11 September 2014. [Google Scholar]
- Bogdanov, A.; Knezevic, M.; Leander, G.; Toz, D.; Varici, K.; Verbauwhede, I. SPONGENT: A Lightweight Hash Function. In CHES; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6917, pp. 312–325. [Google Scholar]
- Lightweight Hash Functions. Available online: https://www.cryptolux.org/index.php/Lightweight_Hash_Functions#cite_note-BKLT11-22 (accessed on 10 November 2018).
- Guo, J.; Peyrin, T.; Poschmann, A. The PHOTON Family of Lightweight Hash Functions. In CRYPTO; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6841, pp. 222–239. [Google Scholar]
- Aumasson, J.; Henzen, L.; Meier, W.; Naya-Plasencia, M. Quark: A Lightweight Hash. J. Cryptol. 2013, 26, 313–339. [Google Scholar] [CrossRef]
- Cremers, C.J.F. The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols. In Computer Aided Verification; Gupta, A., Malik, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 414–418. [Google Scholar]
- Sundaresan, S.; Doss, R.; Piramuthu, S.; Zhou, W. A robust grouping proof protocol for RFID EPC C1G2 tags. IEEE Trans. Inf. Forens. Secur. 2014, 9, 961–975. [Google Scholar] [CrossRef]
| Notations | |
|---|---|
| Fake tag ID | |
| Physical Unclonable Function | |
| The tag’s ID number | |
| Pseudo ID of the tag | |
| The tag’s secret value | |
| The shared secret value of the tag and the reader | |
| ⋘ | The left rotation operator |
| & | The AND operator |
| The concatenation operator | |
| A random number | |
| ⊕ | XOR function |
| Denotes the bit of the string , where is the most right bit | |
| Claim | Status | Comments | |||
|---|---|---|---|---|---|
| improved | R | improved,R1 | Secret ID | OK | No attacks within bounds. |
| improved,R2 | Niagree | OK | No attacks within bounds. | ||
| improved,R3 | Nisynch | OK | No attacks within bounds. | ||
| improved,R4 | Alive | OK | No attacks within bounds. | ||
| improved,R5 | Weakagree | OK | No attacks within bounds. | ||
| T | improved,T1 | Secret PIDi | OK | No attacks within bounds. | |
| improved,T2 | Secret PIDip1 | OK | No attacks within bounds. | ||
| improved,T3 | Niagree | OK | No attacks within bounds. | ||
| improved,T4 | Nisynch | OK | No attacks within bounds. | ||
| improved,T5 | Alive | OK | No attacks within bounds. | ||
| improved,T6 | Weakagree | OK | No attacks within bounds. |
| Protocols | Impersonation | Traceability | Disclosure | Desynchronization |
|---|---|---|---|---|
| Sadeghi et al. [25] | × | × | ✓ | ✓ |
| Aysu et al. [32] | ✓ | × | × | ✓ |
| Van Herrewege et al. [30] | ✓ | ✓ | × | ✓ |
| Kulseng et al. [11] | ✓ | ✓ | × | × |
| Xu et al. [10] | ✓ | ✓ | × | × |
| Improved Protocol | ✓ | ✓ | ✓ | ✓ |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bendavid, Y.; Bagheri, N.; Safkhani, M.; Rostampour, S. IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”. Sensors 2018, 18, 4444. https://doi.org/10.3390/s18124444
Bendavid Y, Bagheri N, Safkhani M, Rostampour S. IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”. Sensors. 2018; 18(12):4444. https://doi.org/10.3390/s18124444
Chicago/Turabian StyleBendavid, Ygal, Nasour Bagheri, Masoumeh Safkhani, and Samad Rostampour. 2018. "IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”" Sensors 18, no. 12: 4444. https://doi.org/10.3390/s18124444
APA StyleBendavid, Y., Bagheri, N., Safkhani, M., & Rostampour, S. (2018). IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”. Sensors, 18(12), 4444. https://doi.org/10.3390/s18124444






