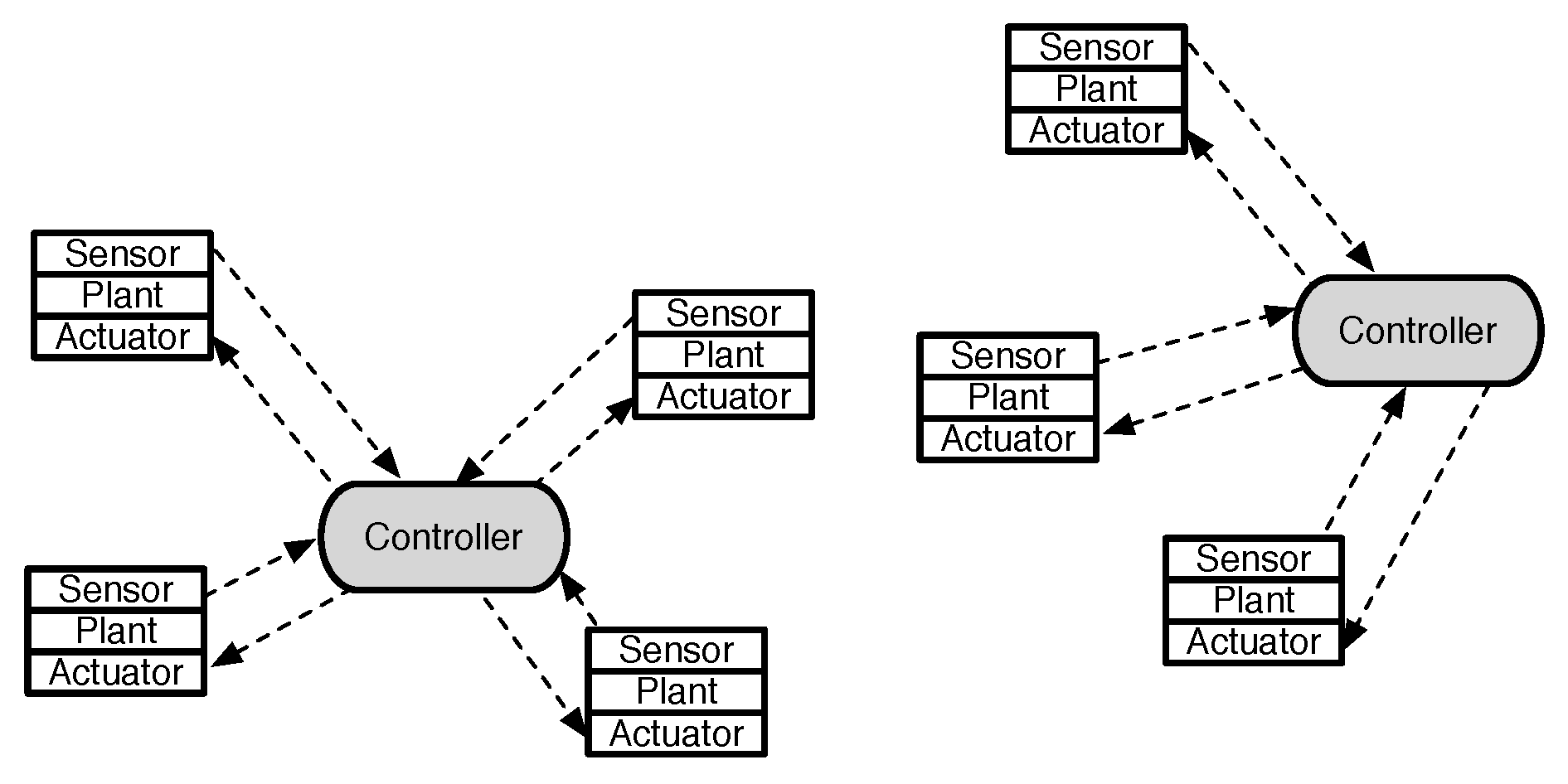
1. Introduction
Industrial internet of things (IIoT) through wireless sensors and actuators have tremendous potential to improve the efficiency of various industrial control systems in both process automation and factory automation [
1,
2,
3,
4,
5]. IIoTs are integrated systems of computation, wireless networking, and physical systems, in which embedded devices are connected to sense, actuate, and control the physical plants. In wireless networked control systems (WNCSs), the wireless sensors basically measure the physical plants and transmit its information to the controllers. The controllers then compute the control signal based on the received sensing information in order to manipulate the physical plants through the actuators. The wireless networks of IIoTs provide many benefits such as simple deployment, flexible installation and maintenance, and increased modularity in many practical control systems with the low cost [
1].
Unfortunately, the network constraints such as delays and losses can significantly degrade the control performance and can even lead to unstable control systems [
1,
6]. In the control community, extensive research has been conducted to analyze the communication effects on control systems and design the control algorithm to handle its effects on the control performance [
7]. Comparatively, much less work of wireless network design for control systems has been proposed. In fact, current wireless networks do not offer guaranteed stability of heterogeneous multiple control systems over lossy channels [
1]. The main reason is that the numerous parameters of the control system and the communication system influence each other due to the complex interactions among different layers. It is important to understand how these communication constraints affect the control stability and performance properties in a quantitative manner. The quantitative result is an important factor to bridge the gap between control and communication layers for the efficient and stable control operations using IIoTs. Furthermore, the communication protocol must guarantee the stability of all control-loops since each industrial process affects the performance of overall connected control systems [
7].
The transmission scheduling policies of sensors and controllers must efficiently optimize the traffic generation instance and transmit slot allocation since it directly affects the network delay and loss, and eventually leading to the stability issue of control systems. Decreasing the traffic generation interval of sensors and controllers generally improves the performance of the control system at the cost of lossy and delayed control feedback due to the increasing network congestion. Moreover, increasing the traffic generation rate may not satisfy the schedulability constraint of the communication system. Thus, the transmission scheduling must adjust its operations dependent on the control system requirements and the link conditions.
The main contribution of the paper is to propose three transmission scheduling policies, namely centralized stationary random access, distributed random access, and Lyapunov-based scheduling scheme, of wireless networks to guarantee the stability of heterogeneous multiple control systems over different lossy links. The three transmission scheduling policies are based on the max-min optimization problem where the objective is to maximize the minimum slack of the stability constraint of the control systems. We show the performance of the proposed scheduling schemes in terms of the stability region of heterogeneous multiple control systems over different link conditions.
The paper is organized as follows.
Section 2 discusses the related works on both control and communication aspects. In
Section 3, we present a general WNCS modeling framework to include both communication constraints such as varying delays, packet losses, and sampling intervals. In
Section 4, an illustrative WNCS example is used to present the fundamental performance issues of general communication protocols in terms of the control stability. Based on the fundamental observation, we formulate a novel optimization problem for the transmission scheduling of wireless networks in
Section 5. We present three different scheduling schemes, namely centralized stationary random access, distributed random access, and centralized Lyapunov-based schedule schemes, to solve the proposed optimization problem in
Section 6,
Section 7 and
Section 8, respectively. In
Section 9, we analyze the robust performance of the proposed three transmission scheduling schemes to guarantee the stability of heterogeneous control systems. Finally, we summarize the contributions of the paper in
Section 10.
Notations: denotes all nonnegative integers. Normal font x, bold font , and calligraphic font denote scalar, vector, and set, respectively.
2. Related Works
In the control community, extensive research has been conducted to analyze control stability and to design control algorithms by considering the communication constraints [
1,
7,
8]. The control community generally considers network imperfections and constraints such as the varying packet dropouts, network delays, and traffic generation intervals [
1]. Note that all these network factors are highly correlated dependent on the assumptions of the NCS literature. However, most NCS studies only consider some of the network effects, while ignoring the other factors, due to the high complexity of the stability analysis. For instance, the network effects of packet dropouts are investigated in [
9,
10], of time-varying sampling intervals in [
11,
12], and of delays in [
6,
13,
14]. By considering the structure of NCSs, previous works analyze the stability of control systems by using either only wireless sensor–controller channel (e.g., [
15,
16]) or both sensor–controller and controller–actuator (e.g., [
8,
17,
18,
19]).
In [
19], the explicit bounds on the maximum allowable transfer interval and the maximally allowable delay are derived to guarantee the control stability of NCSs, by considering time-varying sampling period and time-varying packet delays. If there are packet losses for the time-triggered sampling, its effect is modeled as a time-varying sampling period from receiver point-of-view. The maximum allowable transfer interval is the upper bound on the transmission interval for which stability can be guaranteed. If the network performance exceeds the given requirements, then the stability of the overall system could not be guaranteed. The developed results lead to tradeoff curves between maximum allowable transfer interval and maximally allowable delay. These tradeoff curves provide effective quantitative information to the network designer when selecting the requirements to guarantee stability and a desirable level of control performance.
In the communication community, most existing approaches design the scheduling algorithms to meet the delay constraint of each packet for a given traffic demand [
20,
21,
22,
23]. An interesting design framework is proposed to minimize the energy consumption of the network, while meeting reliability and delay requirements from the control application [
24,
25]. In [
24], modeling of the slotted random access scheme of the IEEE 802.15.4 medium access control (MAC) is developed by using a Markov chain model. The proposed Markov chain model is used to derive the analytical expressions of reliability, delay, and energy consumption. By using this model, an adaptive IEEE 802.15.4 MAC protocol is proposed. The protocol design is based on a constrained optimization problem where the objective function is the energy consumption of the network, subject to constraints on reliability and packet delay. The protocol is implemented and experimentally evaluated on a testbed. Experimental results show that the proposed algorithm satisfies reliability and delay requirements while ensuring a longer network lifetime under both stationary and transient network conditions.
The cross-layer protocol solution, called Breath, is designed for industrial control applications where source nodes attached to the plant must transmit information via multihop routing to a sink [
25]. The protocol is based on randomized routing, MAC, and duty-cycling to minimize the energy consumption, while meeting reliability and packet delay constraints. Analytical and experimental results show that Breath meets reliability and delay requirements while exhibiting a nearly uniform distribution of the work load.
Since the joint design of controller and wireless networks necessitates the derivation of the required packet loss probability and packet delay to achieve the desired control cost, we provided the formulation of the control cost function as a function of the sampling period, packet loss probability, and packet delay [
26]. We first presented how the wireless network affects the performance of NCSs by showing the feasible region of the control performance. By considering these results, the joint design between communication and control application layers is proposed for multiple control systems over the IEEE 802.15.4 wireless network. In particular, a constrained optimization problem is studied, where the objective function is the energy consumption of the network and the constraints are the packet loss probability and delay, which are derived from the desired control cost. We clearly observe the tradeoff between the control cost and power consumption of the network.
Recently, a novel framework of communication system design is proposed by efficiently abstracting the control system in the form of maximum allowable transmission interval and maximum allowable delay constraints [
27,
28]. The transmission interval is the traffic generation interval of successfully received information. The objective of the optimization is to minimize the total energy consumption of the network while guaranteeing interval and delay requirements of the control system and schedulability constraints of the wireless communication system. A schedulability constraint is introduced as the sum of the utilization of the nodes, namely the ratio of the delay to the sampling periods. The decision variables are the set of transmission rate and sampling period. The proposed mixed-integer programming problem is converted to an integer programming problem based on the analysis of optimality and relaxation [
27]. Then, the centralized resource allocation algorithm gives the suboptimal solution for the specific case of M-ary quadrature amplitude modulation and earliest deadline first scheduling. For a fixed sampling period, the formulation is also extended for any non-decreasing function of the power consumption as the objective function, any modulation scheme, and any scheduling algorithm in [
28]. All related works [
27,
28] propose the centralized algorithm to adapt the communication parameters for the homogeneous control systems over the equal link condition.
In [
29], the cross-layer optimized control protocol is proposed to minimize the worst-case performance loss of multiple control systems over a multihop mesh network. The design approach relies on a constrained max–min optimization problem, where the objective is to maximize the minimum resource redundancy of the network and the constraints are the stability of the closed-loop control systems and the schedulability of the communication resources. The stability condition of the control system has been formulated in the form of stochastic transmission interval constraint [
19]. The centralized algorithm gives the optimal solutions of the protocol operation in terms of the sampling period, slot scheduling, and routing.
In comparison to these works [
27,
28,
29], the transmission control policies of IIoTs must optimize both traffic generation instance and transmit slot allocations to guarantee the stability of heterogeneous control systems over different link conditions. The earliest deadline first scheduling only guarantees the optimal performance for the homogeneous requirements [
30]. Furthermore, the centralized approach generally provides the optimal performance but at the cost of the monitoring and network control overhead and single point failure problem. In this paper, we focus on the robust performance guarantee of the control stability rather than the energy efficiency issue of wireless networks. In fact, researchers have recently applied the IEEE 802.11 standards for the real-time control applications instead of low-power wireless standards such as IEEE 802.15.4 and 802.15.3 [
1,
31,
32].
4. Fundamental Observation
To analyze the stability of control systems, linear matrix inequality (LMI) conditions were verified on the polytopic overapproximation in [
6,
19,
33]. The LMI conditions were verified using the YALMIP [
34] and the SeDuMi solver [
35]. We used the analytical technique of the control stability in [
33]. This technique effectively analyzes the stability to a given linear time-invariant (LTI) plant model, a LTI controller model, and MATI and MAD bounds on the network uncertainties. In this illustrative example, we first analyzed the batch reactor system [
33,
36] to demonstrate how stability regions can be visualized. Then, we investigated the fundamental tradeoff between MATI and MAD for the control stability. The network is assumed to incur
uncertain time-varying TIs ; and
uncertain time-varying network delays .
We fixed
ms and
ms due to the slot duration of the typical industrial wireless standards [
37].
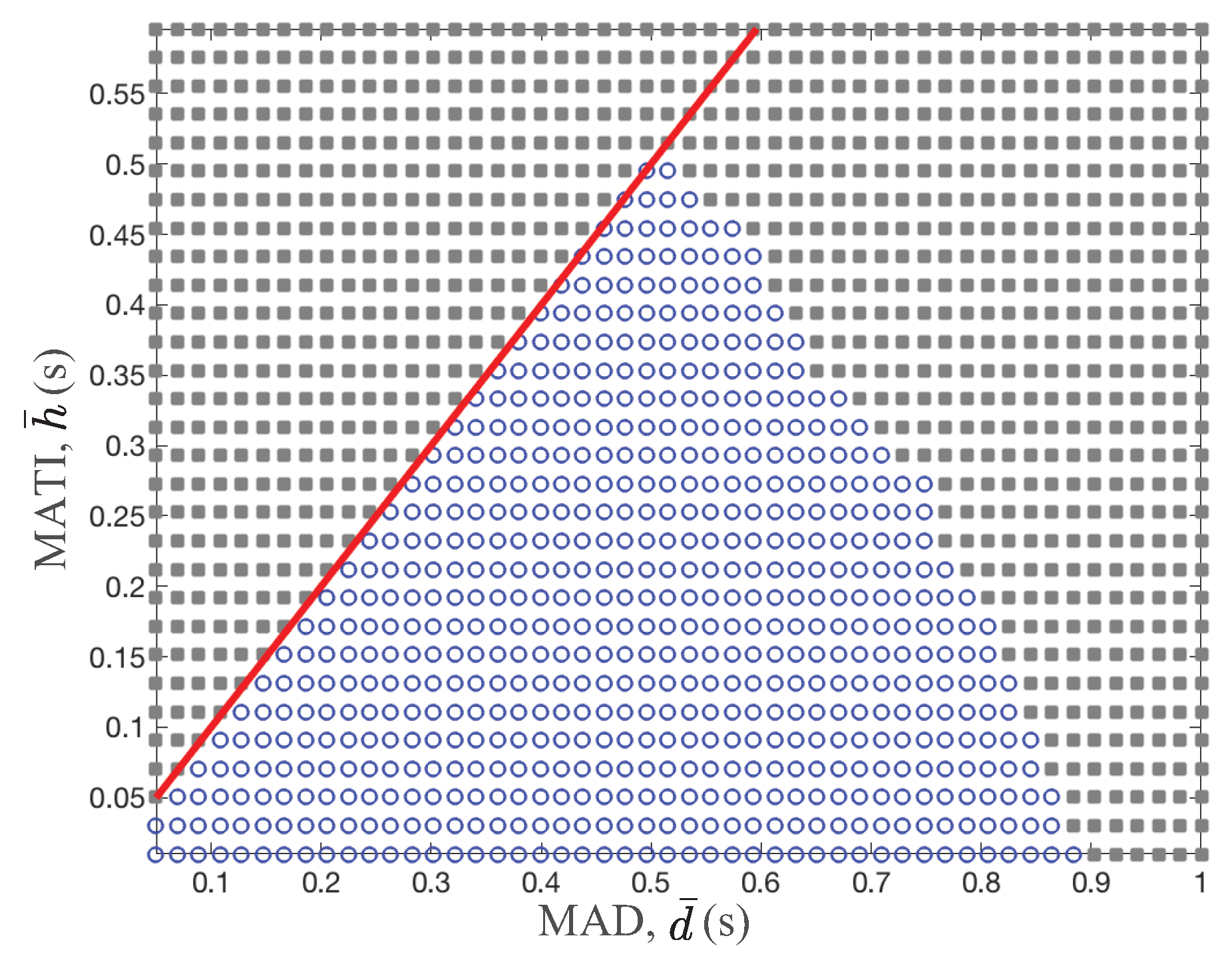
Figure 3 shows the stability region over different MATI,
s and MAD,
s. The circle and rectangular marker present the stability and instability operating region for a given MATI and MAD value. The solid line represents the assumption of the MATI and MAD constraints, namely
. Clearly, as the MATI and MAD values increase, the control system becomes unstable. In other words, the lower are the MATI and MAD values, the better is the control system stability. It is not simple to approximate the boundary between stability and instability region due to the complex stability analysis techniques in
Figure 3. However, in general, the MAD requirement of the stability becomes more strict as the MATI requirement is relaxed. Hence, there is a fundamental tradeoff between MATI and MAD requirements for the stability guarantee of control systems.
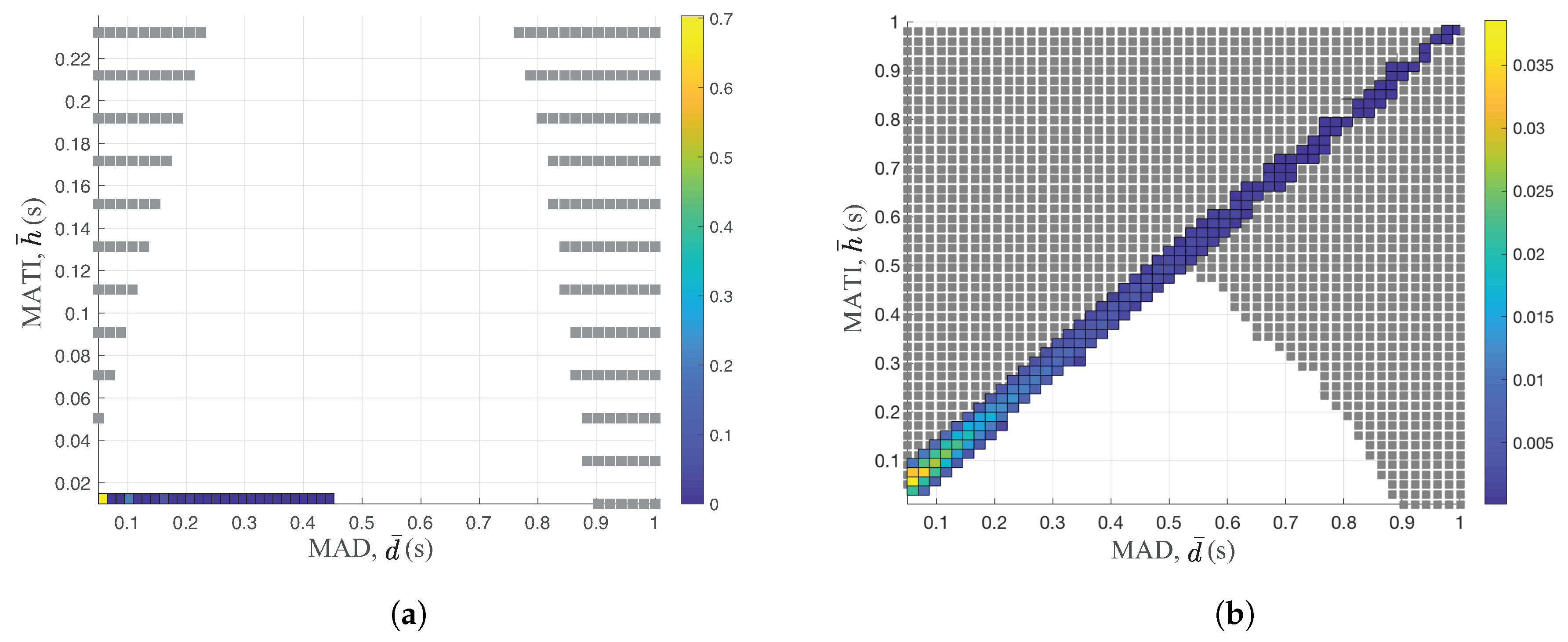
Since the wireless medium is shared between nodes, we analyzed the performance of typical access control schemes in the context of the control stability. In
Figure 4, we provide the TI and the delay performance of two well-known schemes, namely time division multiple access (TDMA) and slotted Aloha over the stability region. The color bar shows the probability density function of the TI and the delay measurements of different access schemes. Note that the stability region in
Figure 4 is equal to that in
Figure 3 with different X and Y scales. The medium access scheme guarantees the control stability if it satisfies the network performance of both TI and the delay inside of the stability region. Hence, the outage probability of the control stability is a good performance metric of wireless networks in the context of the control stability.
Both access schemes rely on the time slotted mode with
and
. TDMA uses a simple round robin algorithm to assign the slot to each node of the network in
Figure 4a. On the other hand, each node randomly decides its transmission based on the traditional slotted Aloha mechanism in
Figure 4b. We set the optimal channel access probability of slotted Aloha to maximize the network throughput [
38].
By comparing
Figure 4a,b, we clearly observed the completely different network performances over the stability region. Since each node of TDMA transmits its corresponding values on the assigned slots, it generates the packet before the transmitting slot. Hence, the delay of the TDMA scheme is constant to 1 time slot, 10 ms, as shown in
Figure 4a. On the other hand, the slotted Aloha only generates new packets after it successfully transmits the packets. Hence, the delay of the slotted Aloha is equal to TI. This is the main reason for significantly different behaviors between TDMA and slotted Aloha. In fact, the outage probability of the stability region of slotted Aloha is
while its corresponding probability is 0 for the TDMA scheme.
The MATI requirement is around
s when the delay is 10 ms for the TDMA scheme. However, as the MAD constraint is increased to
s, the MATI requirement becomes around
s, beyond which the control systems are unstable, as shown in
Figure 4b. Increasing the packer delay significantly degrades the stability region. Note that the retransmission of old data to maximize the reliability increases the delay and is generally not useful for control applications [
7]. As we increase the MATI requirement, the WNCS becomes more robust since it allows more number of packet losses. Hence, it is great to minimize the time delay between packet generation instance and packet transmission to maximize the MATI requirement and to simplify the protocol operation. This is the main reason of the actual packet transmission right after the packet generation in
Section 3.2. Hence, the transmission scheduling policy controls both the packet generation instance and the actual packet transmission in this paper.
5. Optimization Problem Formulation
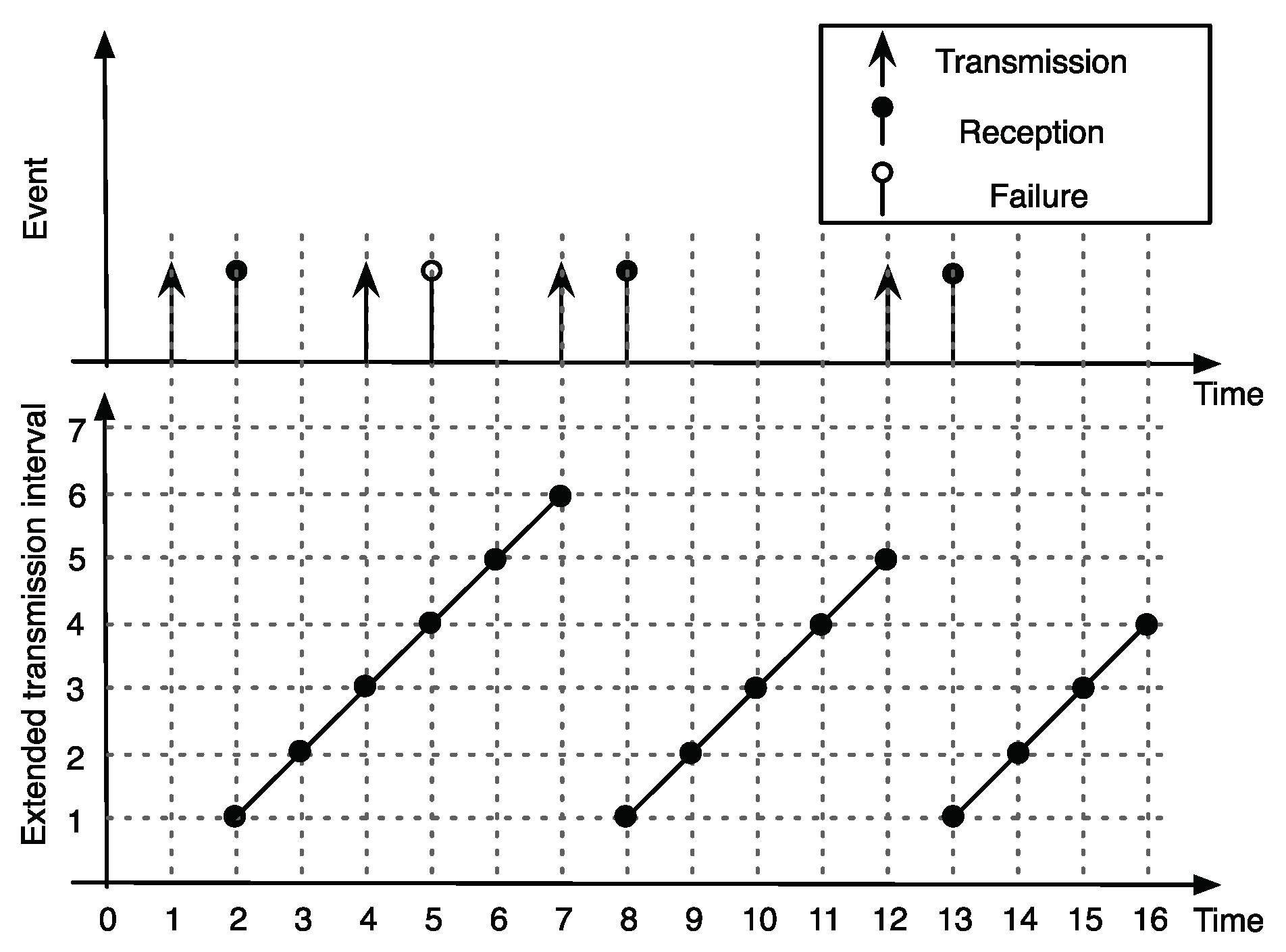
A transmission scheduling policy is an essential component to meet the MATI requirement of node i for a given network setup . Our objective was to design low complexity scheduling schemes to optimize the TI performance with respect to the heterogeneous MATI requirements of each node. In this section, we first introduce the performance metric called extended transmission interval (ETI) of the network. Then, we formulate a constrained optimization problem to optimize the ETI performance.
5.1. Extended Transmission Interval
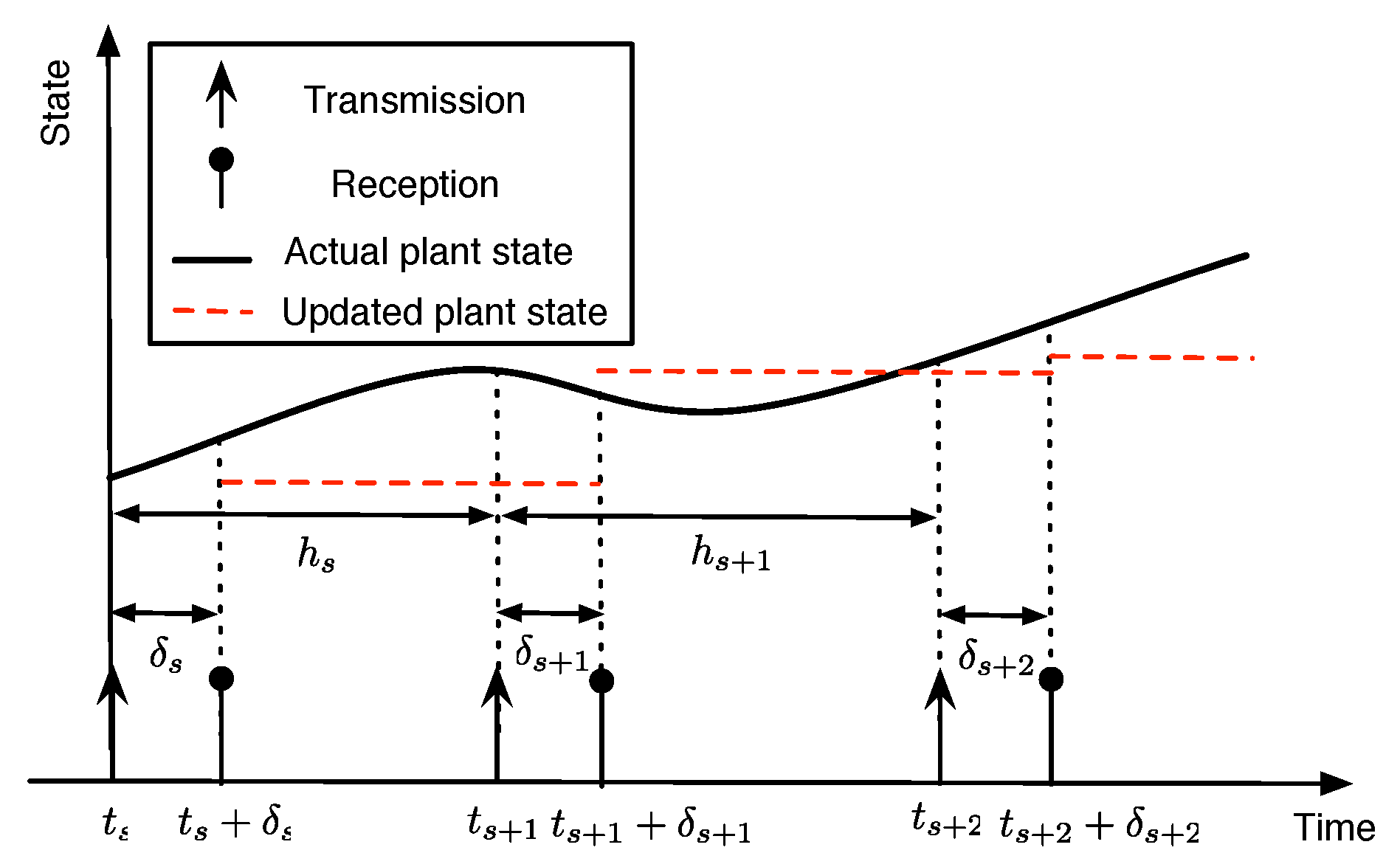
Since the exact definition of TI is based on the discrete random event of packet receptions, it is not an efficient performance metric to use for the transmission scheduling policy. Hence, we introduced a continuous version of the TI metric, called the ETI metric. The extended transmission interval describes how old the information is from the controller perspective.
Figure 5 illustrates the evolution of ETI for a given sequence of packet deliveries of node
i. Let
denote the positive integer to represent the ETI value of node
i at slot
k. We reset
if the controller receives a packet from node
i at slot
k. As a reminder, the received packet was generated at the beginning of slot
k. However, if the controller does not receive a packet, then we increase
. Hence, the iterative update of
is
Note that the ETI linearly increases when there is no packet reception, as shown in
Figure 5.
The ETI constraint of each link is
Since we are interested on the robust ETI performance with respect to the MATI requirement of each node, we define the ETI slack of node
i as
at slot
k. Hence, the expected value of the ETI slack of node
i is
5.2. Optimization Problem
By considering the ETI metric with the robustness criterion, our objective is to maximize the minimum ETI slack of the network. We formulate the constrained optimization problem
Equations (6b) and (6c) present the minimum ETI slack value constraint and the schedulability constraint, respectively. The optimal solution of the optimization problem assigns more network resources as decreases, i.e., more network resources for faster control systems.
In the following section, we propose three low-complex scheduling schemes based on the optimization problem in Equation (6). Three transmission scheduling policies are centralized random access scheme, distributed random access scheme, and centralized Lyapunov-based scheduling scheme. The first two approaches are randomized methods and the third one is a deterministic approach in order to assign the slot resources to all requirement sets .
6. Centralized Random Access Scheme
In this section, we propose the ETI optimization problem for the stationary randomized scheduling scheme in a centralized manner. The controller selects node i with probability in each time slot. Hence, the randomized scheduling scheme is the vector of scheduling probabilities . They select nodes randomly based on the fixed scheduling probabilities .
Since we consider the stationary random scheduling, we first derive the expected behavior of ETI in the following proposition.
Proposition 1. The long-term expected ETI of node i is Proof. The proof of Proposition 1 is provided in
Appendix A. □
By using Proposition 1 and the schedulability constraint of
, the optimization problem in Equation (6) is reformulated as
Note that Equation (8c) represents the schedulability constraint.
Optimal Solution
Since the proposed optimization problem in Equation (8) is a convex problem, we obtain the optimal stationary scheduling probabilities
by analyzing the KKT conditions of the problem. The Lagrange function of the problem is
where
and
are the Lagrange multipliers due to Equations (8b) and (8c), respectively.
The KKT conditions are
Complementary slackness of Equation (8b)
Complementary slackness of Equation (8c)
The first stationarity condition,
, gives
from the partial derivation. With a similar method, the second stationarity condition,
, gives
We obtain that either
or
from the complementary slackness of Equation (
13). However, Equation (
17) implies
since the value of
is zero if
or
, which conflicts the conditions of Equation (
18) or
, respectively. Hence, we obtain
since
. We separate node
i into two groups, namely
and
, based on the dual feasibility
.
If node
i has
, then
from Equation (
17) since
. On the other hand, if node
i has
, then
due to the complementary slackness of Equation (
12). For any fixed value of
, the randomized scheduling probability of node
i is given by Equation (
20).
Our objective is to find the optimal values to meet the constraints of Equations (
19) and (
20). In Equation (
20),
is only unknown variable to compute the scheduling probability. Hence, we first find the optimal value of
satisfying Equations (
19) and (
20). Now, let us derive the boundaries of
. The minimum value of
is
if
from Equation (
20). Hence, the feasible range of
is
From Equation (
20), a decreasing value of
, the probability
increases. As
converges to the lower bound,
, Equation (
19) becomes
. On the other hand, as
, then
due to Equation (
20). Hence, there is a unique value of
to meet Equation (
19) due to the monotonicity of
with respect to
. By gradually increasing
from
and adjusting
using Equation (
20), we find the unique set of
and
that satisfies Equations (
19) and (
20).
Next, we compute the optimal set of
and
. With a similar method, the boundaries of
are
The upper bound of
is derived from Equations (
17) and (
19). By gradually decreasing
from
, we adjust
from Equation (
17). We then obtain the optimal set of
and
for Equation (
18). Note that the unique vector
fulfills the KKT conditions.
7. Distributed Random Access Scheme
In this section, we present a distributed random access where each node decides its transmission probability so that the minimum ETI slack of the network is maximized. Let us assume that each node
i transmits a packet with probability
in each slot. As a reminder, the set of
i’s interfering links is
. Let
be the vector of transmission probabilities of all nodes. Hence, a transmission of node
is successful if and only if no node in
transmits during the transmission of node
i. Hence, the successful transmission probability of node
i is
By applying Equation (
23) to Proposition 1, the long-term expected ETI of node
i is
After substituting Equation (
24) into Equation (
4) of the ETI constraint, we obtain
Motivating by the network utility problem [
39,
40], we formulate a constrained optimization problem to optimize the transmission probability of nodes. Our objective is to maximize the minimum ETI slack with respect to
of the network. After some manipulations of Equation (6), we propose the max-min robust optimization problem
where
. Notice that
is necessary for the feasibility of ETI constraint of Equation (
4). Different fairness notions corresponding to different utility functions are discussed in [
39,
40].
Unfortunately, the proposed max-min robust problem in Equation (26) is a non-convex problem. Next, we convert the problem in Equation (26) to a convex optimization problem in order to design the distributed random access scheme.
Proposition 2. The max-min robust problem in Equation (26)
is equivalent to the following convex programming problem Proof. The proof of Proposition 2 is provided in
Appendix B. □
Optimal Solution
A distributed algorithm can effectively obtain the optimal access probability of the previous convex optimization problem in Equation (27). In this section, we show how globally optimal access probability is obtained in a distributed manner. When we replace the equality constraints
of Equation (27) by two inequality constraints,
and
, the Lagrange function of the problem is
where
and
are the Lagrange multipliers and
.
Our basic idea is to apply the gradient project method for the dual problem
where the dual function is
[
41]. By considering the stationarity condition of the Lagrange function, they give
and
where
. Note that
satisfies the constraints
. The Lagrange multipliers of the gradient project method are adjusted in the direction of the gradient
:
Here, is the step size at the nth iteration, and . The gradient are and .
8. Centralized Lyapunov-Based Scheduling Scheme
The Lyapunov optimization theory is extensively applied to the general communication and queueing systems [
42]. Using Lyapunov optimization techniques, we derive the centralized scheduling scheme for the ETI optimization problem in Equation (6). The Lyapunov-based scheduling scheme uses the feedback ETI state of nodes in order to reduce the value of the Lyapunov function. We define the Lyapunov function to give a large positive scalar when nodes have high ETI with respect to the MATI
. Hence, the Lyapunov-based scheduling approach basically tries to minimize the growth of its function.
Next, we define the fundamental components of the Lyapunov-based scheduling scheme, namely Lyapunov function with notions of the ETI debt. Let us denote
as the ETI debt of node
i at slot
k. The ETI debt of node
i is
where
is the MATI value and
is the ETI at slot
k.
When the scheduling scheme does not meet the ETI requirement , then the value of the ETI debt is positive. We define the positive part of the ETI debt, . As increasing debt indicates to the scheduling scheme that node i needs more transmission slots to meet the MATI requirement.
Let
be a vector of network ETI dept states at slot
k. Then, we define the Lyapunov Function by
where
G is a large positive value to emphasize the ETI constraints. Remark that
is large when nodes have high ETI with respect to the requirement or positive ETI debt.
Optimal Solution
To minimize the Lyapunov function, we introduce the Lyapunov drift
Note that the Lyapunov drift measures the change of the Lyapunov function over time slots. The Lyapunov-based scheduling scheme minimizes by reducing in every slot k.
The high computation complexity of prevents us from deriving the exact form of . Hence, we derive the upper bound of and apply it for the actual transmission scheduling scheme.
Proposition 3. The upper bound ofiswhereandare given by Proof. The proof of Proposition 3 is provided in
Appendix C. □
We observe that both
and
are functions of the network state
and setup parameters
. However,
of Equation (
38) is not dependent on the scheduling decision
. Hence, in each slot
k, the centralized Lyapunov-based scheduling scheme selects the node with maximum value of
to minimize the upper bound of
.
9. Performance Evaluation
In this section, we evaluate the performance of four transmission scheduling policies, namely ideal scheduling scheme, centralized random access scheme, distributed random access scheme, and centralized Lyapunov-based scheduling scheme. The ideal scheduling scheme optimizes the transmission schedule based on the entire packet loss sequences of each link. Hence, it gives the fundamental performance bounds even though it is not feasible to implement in practice. We considered a star network topology where
N sensor nodes contend to send data packets to the controller. Each node has different sets of
and
. Note that each link
i of the centralized scheduling approach has equal
for both uplink and downlink. Let us denote the maximum MATI and minimum MATI of the network as
and
, respectively. With a similar method, we define the maximum link reliability and minimum link reliability of the network
and
, respectively. Then, the MATI and link reliability of node
i are
The lower are the values of and , the more challenging are the constraints. Hence, the lower node ID has more strict MATI requirement with worse link reliability. Each simulation ran time slots.
Both centralized schemes of static random access and Lyapunov-based schedule need the resource allocation message to assign the time slot to nodes. We assumed that both centralized schemes use one additional slot to transmit the resource allocation message. The centralized solutions consume two slots for the single data transmission while the distributed random access only requires one slot for the data transmission. Since the packet delay is fixed to 1 time slot, we mainly analyzed the performance of TI of different schemes.
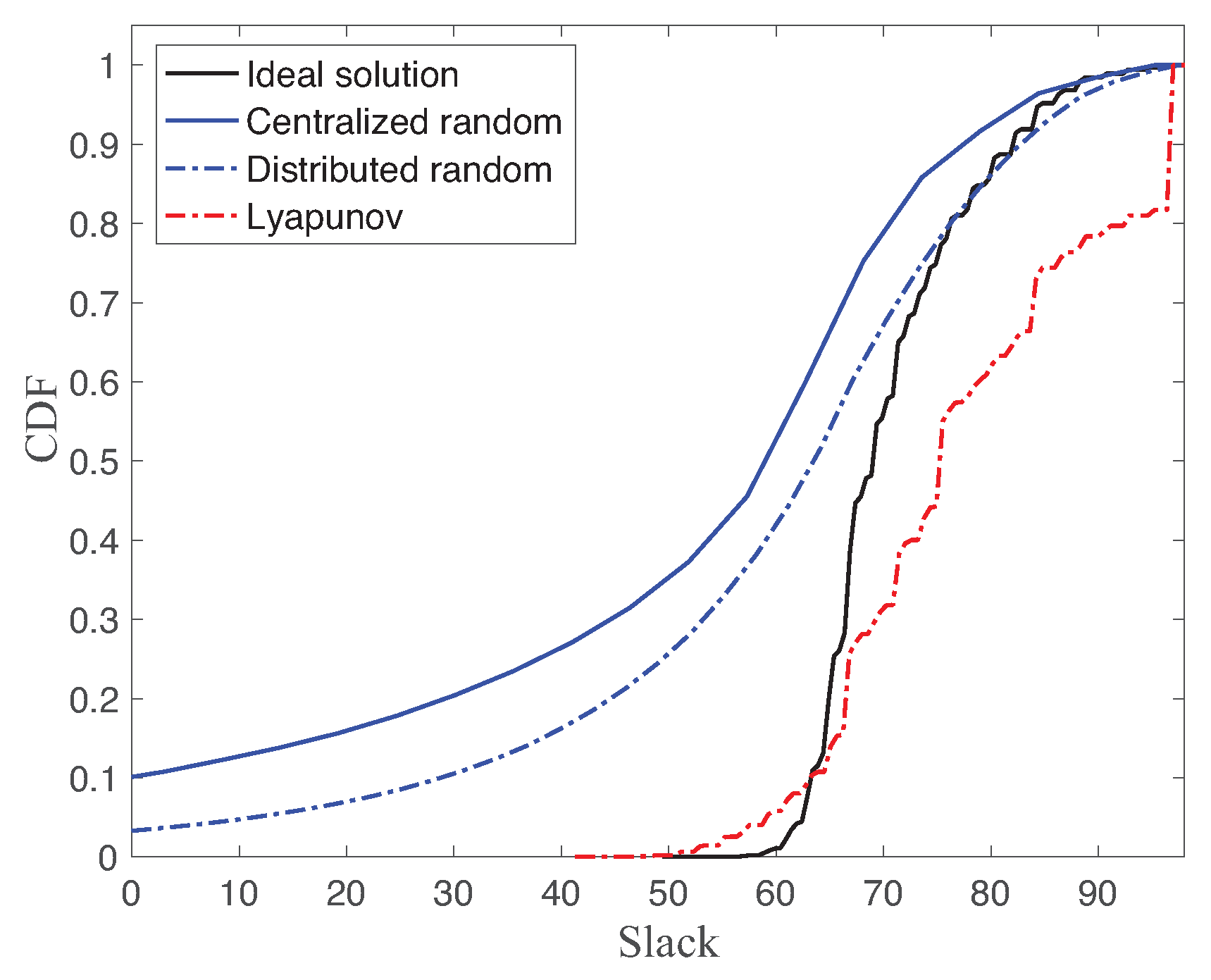
Figure 6 shows the cumulative density function (CDF) of slack of ideal solution, centralized random access, distributed random access, and Lyapunov-based approach with link reliability
, MATI requirement
, and number of nodes
. The slack is the difference between MATI and TI measurements. As a reminder, the minimum slack of TI with respect to MATI is the objective value of the proposed optimization problem. The higher is the slack, the better is the robustness. Hence, a lower CDF is better than a higher CDF for the stability guarantee. The Lyapunov-based scheduling scheme generally gives a lower CDF than other CDFs. However, our objective was to maximize the worst slack of the network. In fact, the worst slack value of the ideal solution is greater than the one of the Lyapunov-based approach in
Figure 6. Hence, the ideal solution still provides the optimal solution of our proposed optimization problem in Equation (6) using the perfect knowledge of the packet loss sequences. The Lyapunov-based approach efficiently improves the robust performance based on the feedback slack information between TI and MATI of heterogeneous multiple control systems.
On the other hand, there is a significant gap between ideal solution with two randomized scheduling approaches, namely centralized random access and distributed random access. Note that the centralized random access does not rely on any feedback information of TI. The interesting observation is that the distributed random access generally performs better than the centralized one for
. Even though the distributed random access may incur the collisions with other transmissions, each data transmission requires only one time slot. While the centralized random access has no contention with other nodes, each data transmission consumes two time slots due to the resource allocation message. Since the collision probability is low for the small number of nodes, the distributed random access gives better robustness, as shown in
Figure 6.
Another interesting point is the different percentile values between four schemes. While the four schemes have similar 50th percentile values, the percentile difference between different approaches increases as the percentage decreases. It means the worst case performance of the proposed approaches is significantly different.
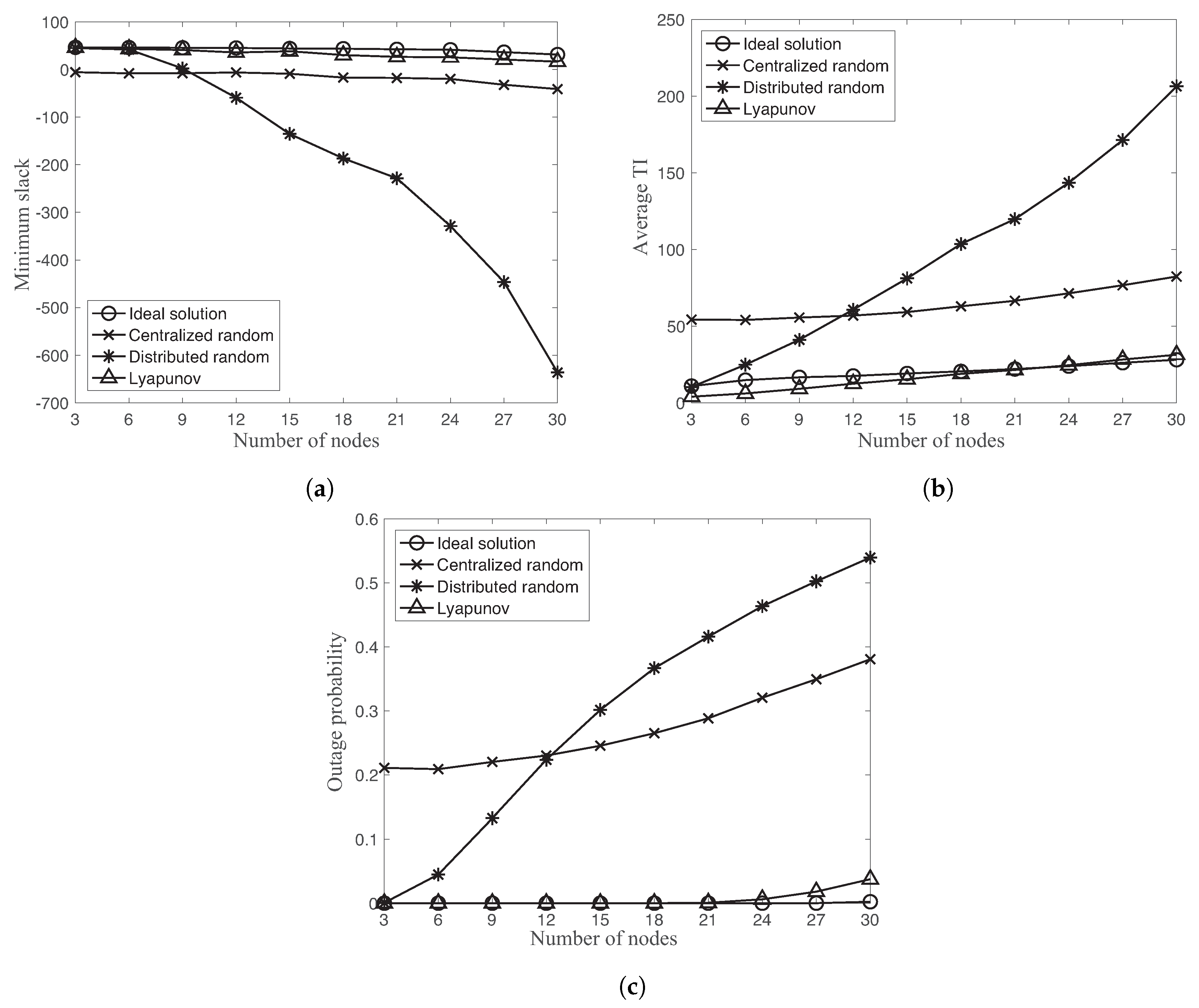
Figure 7 shows the minimum slack, average TI, and outage probability of four different schemes as a function of different number of nodes
with link reliability
, and MATI requirement
. The outage probability is defined as the probability that the TI value is greater than MATI,
.
Let us first compare the performance between ideal solution and Lyapunov-based approach. In
Figure 7a,c, the ideal solution provides the lower outage probability and higher minimum slack than the one of the Lyapunov-based approach. However, the average TI of the ideal solution is slightly higher than the one of Lyapunov-based approach in
Figure 7b. As a reminder, the objective of the proposed optimization problem is to maximize the minimum TI slack with respect to MATI requirements instead of minimizing average TI value of the network. The average TI is not explicitly considered in the optimization problem.
While the Lyapunov-based approach is comparable with the ideal solution, both random accesses show significantly different behaviors. In
Figure 7, the centralized random access has an almost constant gap of the minimum slack, average TI, and outage probability with the Lyapunov-based approach over different number of nodes. On the other hand, the distributed random access significantly degrades these performance metrics as increasing the number of nodes. By comparing two random accesses, the distributed random approach provides better performance than the centralized random access for the small number of nodes
. There is the fundamental stability limits of the distributed random access approach due to the increasing collision probability dependent on the number of nodes [
38].
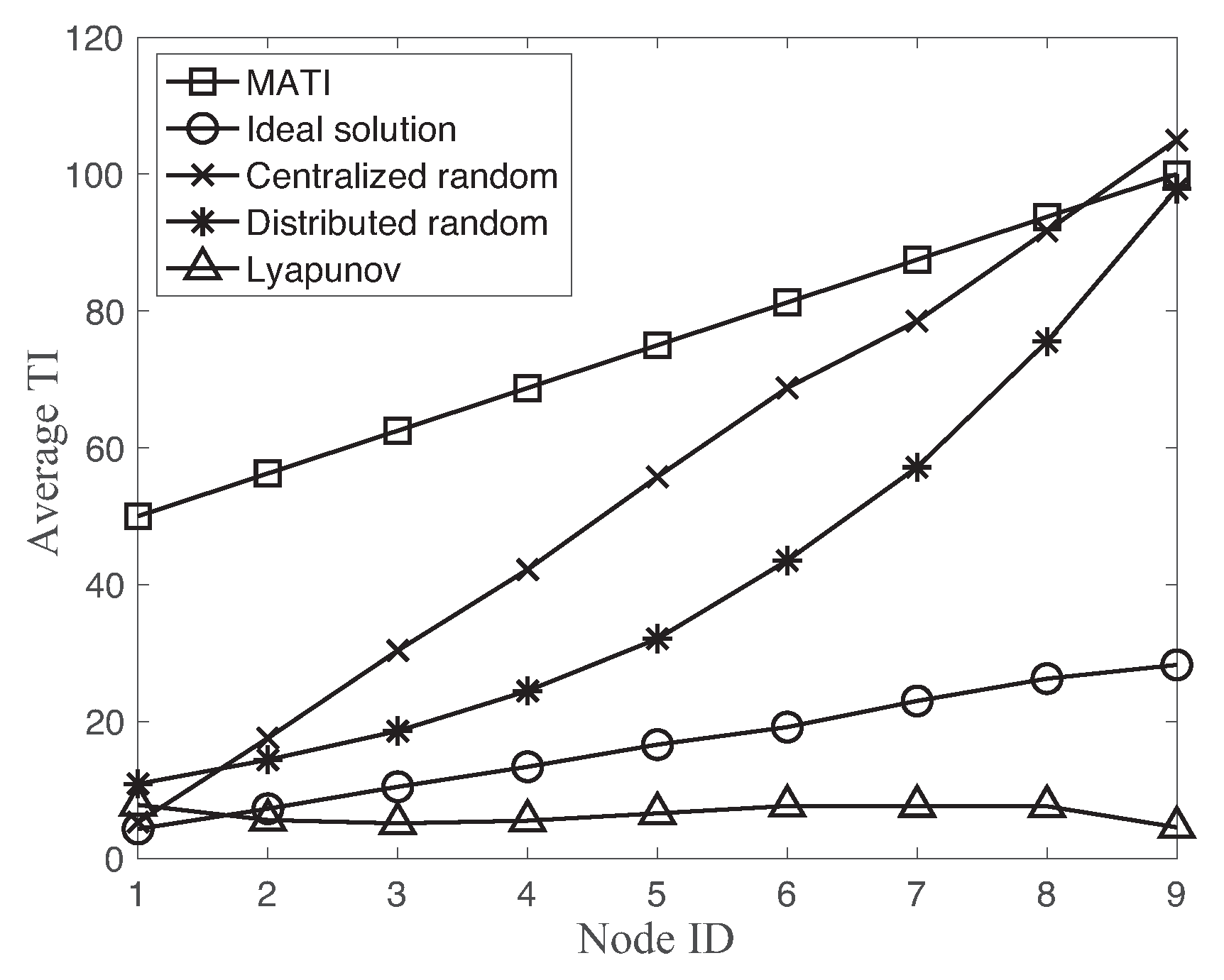
Figure 8 shows the MATI requirement and the average TI of each node using different transmission scheduling schemes with
. As a reminder, the MATI requirement and link reliability become more strict as decreasing node ID of the network. We observe that the average TI of the ideal solution is decreasing as the MATI requirement becomes more strict for the lower node ID. However, the Lyapunov-based approach is quite flat over different MATI requirements with respect to the ideal solution. The node ID 1 provides the minimum slack of both ideal solution and Lyapunov-based approach of the network. This is the main reason of the greater minimum slack of the ideal solution at the cost of the higher average TI compared to the Lyapunov-based approach in
Figure 7.
On the other hand, both random accesses significantly increase the average TI as the MATI requirement becomes relaxed for the higher node ID. In both random accesses, the slack between MATI and average TI is decreasing as the node ID increases. In fact, the minimum slack value of both random accesses occurs at node ID 9.
While the centralized random access supports the stationary optimal resource allocation, its operation requires the additional slots for the resource allocation message. In fact, each successful data transmission of the centralized approaches needs both successful transmissions of the resource allocation message and data packet. Hence, the performance of the random access is a complex function of number of nodes, link reliability, and operational overhead.
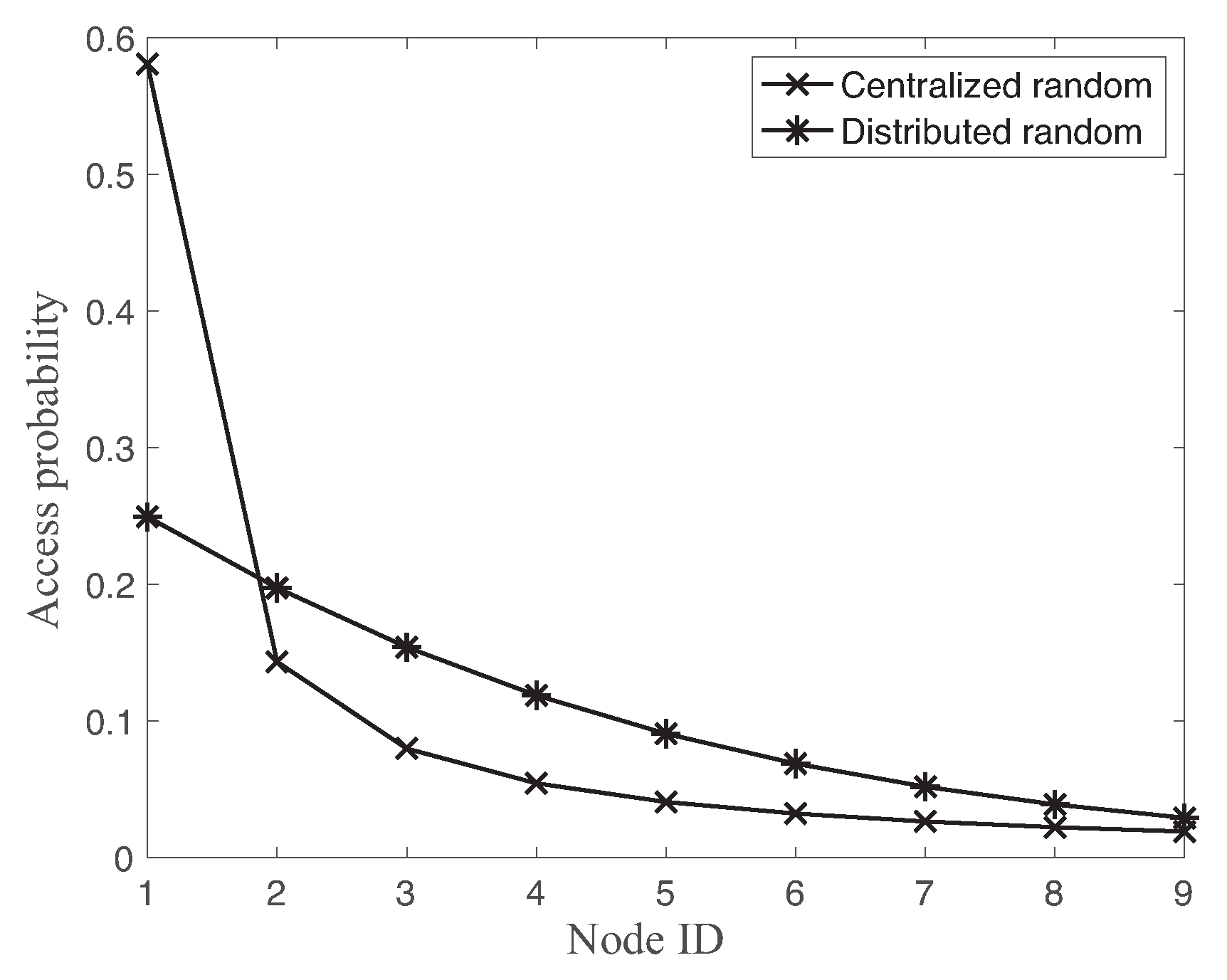
Figure 9 compares the channel access probabilities of each node using both centralized random access and distributed random access with
. Both solutions of random accesses assign the higher access probability to the higher priority node ID, i.e., lower node ID. While the channel access probability of distributed random access is mush smoother for different nodes, the centralized random access approach sets the very high channel access probability
for the most demanded node ID 1. In fact, both random accesses show the over-allocation of slot resources to the most demanded node as shown in
Figure 8.