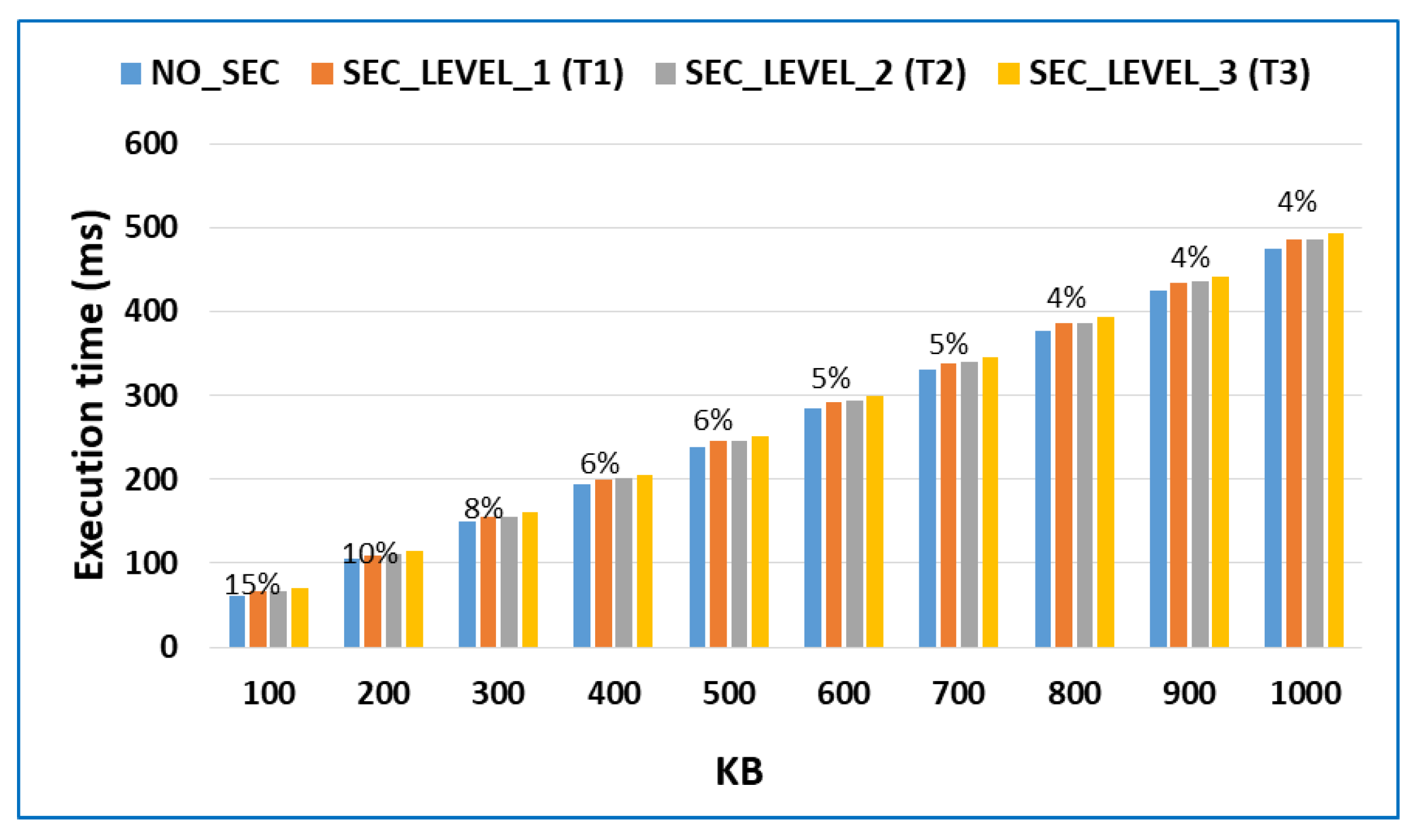
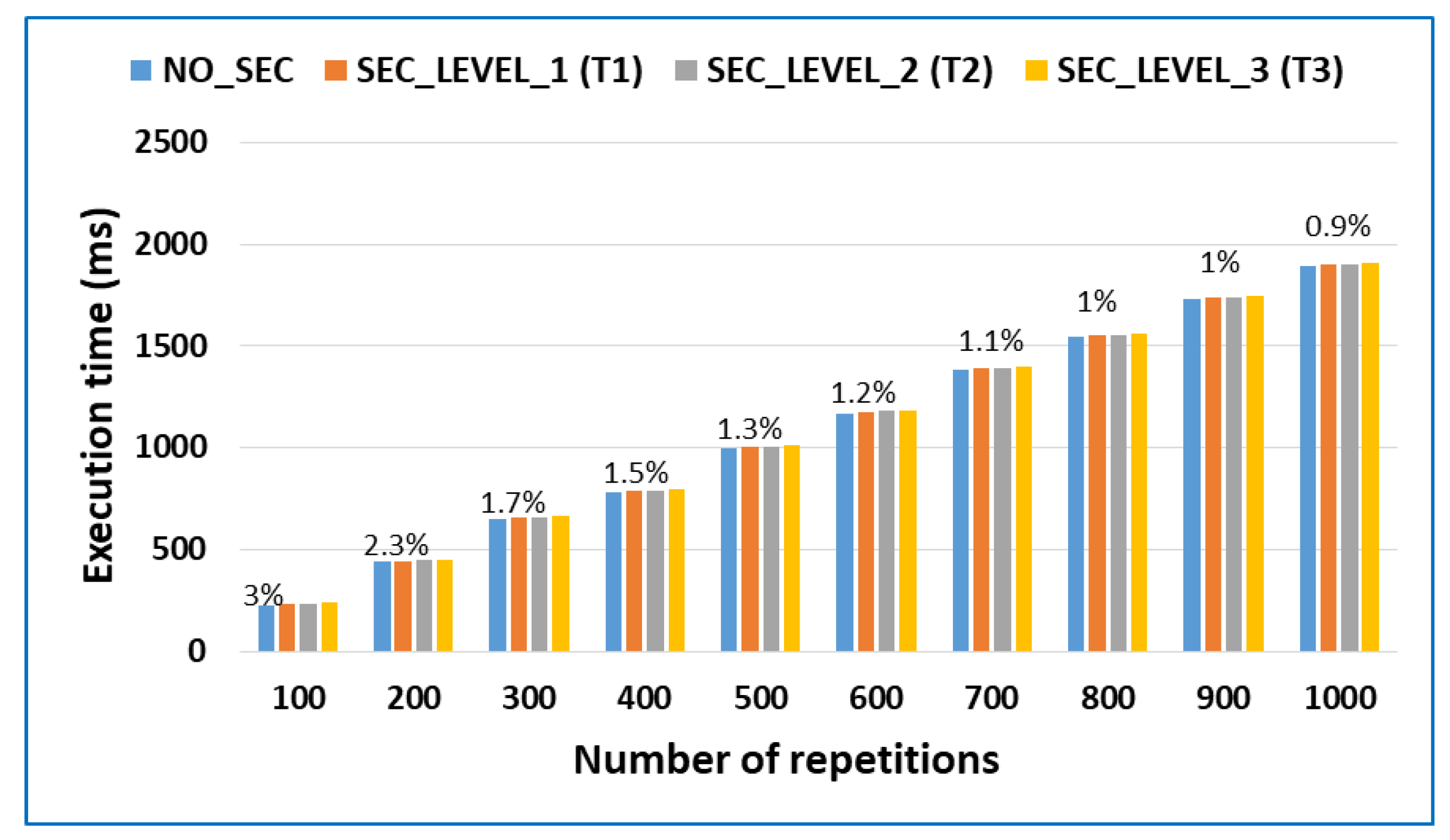
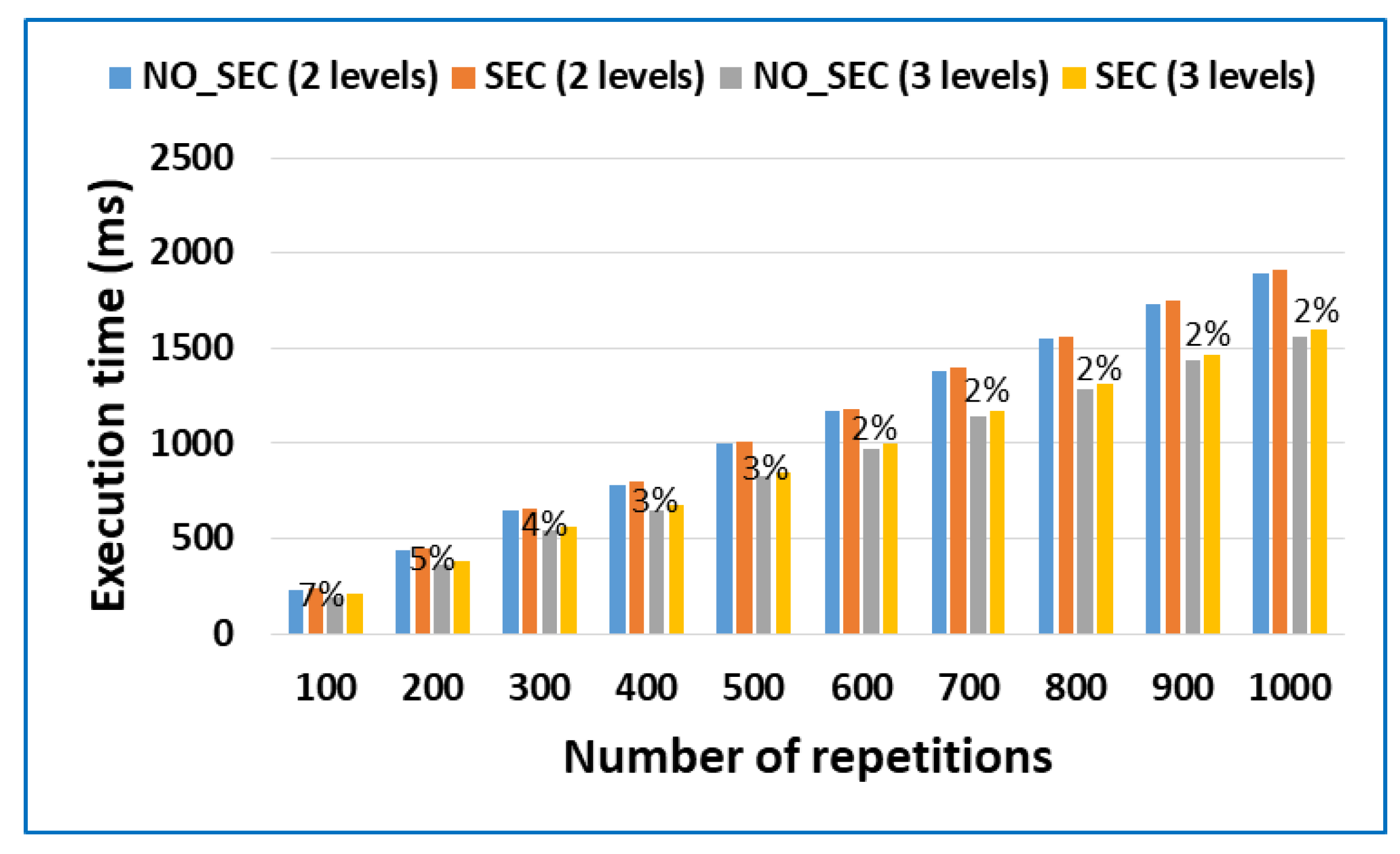
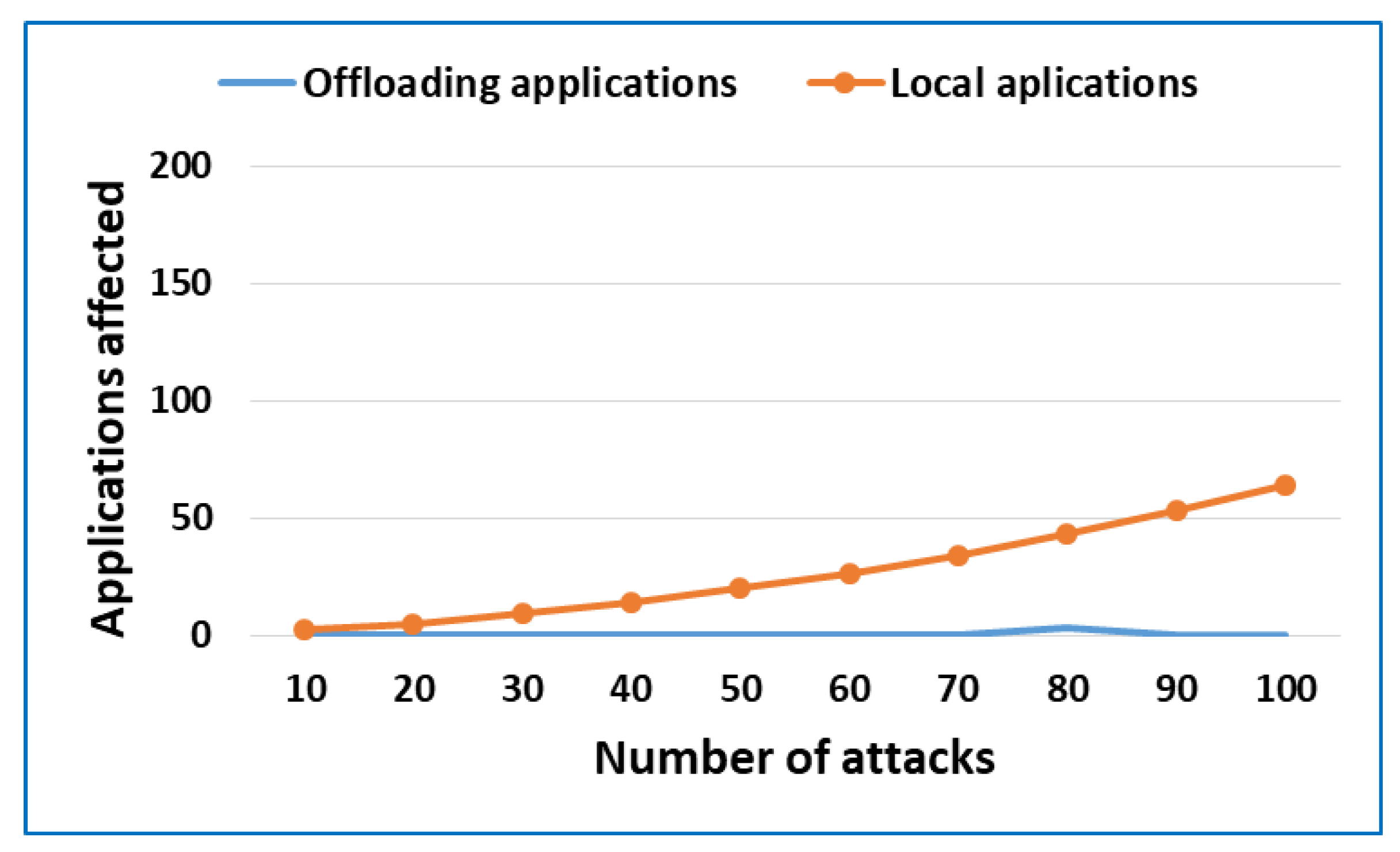
3.1. Formal Framework
This section introduces a general formulation of the multi-tier MEC paradigm and, more specifically, the aspects related to data processing offloading architectures. In addition, because security is the main purpose of this study, we go in-depth and focus on the formulation related to the security of MEC models in computational offloading scenarios.
First, it is necessary to consider that an application will be composed of a list of tasks to perform. There may be dependent tasks that need sequential execution and independent tasks that can be executed in parallel in different tiers. However, splitting an application into a list of tasks is a problem called application partitioning that is outside the scope of this paper. We will generally make use of the concept of task with independence from its granularity unit, which may be of variable size. The granularity unit can be a fragment of code, a method, class, process, etc.
Let Γ
App be the list of tasks of an application:
Because we are formally modeling multi-tier MEC architectures in data processing offloading scenarios, the tasks of an application can be executed in any of the MEC tiers or layers. In the rest of the paper, we will use tier or layer indistinctly. Let
be the set of available computing layers of the MEC architecture:
The MEC architecture may have any number of layers between 2 and c + 1. L0 is the layer made up by the mobile device in which the application initiates and, if c + 1 layers are used, Lc is the layer in which the remote Cloud Computing servers are located. The number of layers of the MEC architecture will depend on the execution environment, and different environments can have a different number of layers. For example, a user in his home environment may have only two layers: the mobile device (L0) and the fog servers of his home (L1). But, the same user in his work environment may have three layers: the mobile device (L0), the company’s fog servers (L1) and the company’s ISP cloud servers (L2).
In general, each of the layers of a multi-tier MEC architecture can have a set of heterogeneous computation platforms with different processing and performance capacities. Thus, the layer L
j, has m computing platforms where j ∈ {0,c} and m > 0.
where p
jk is the platform k of the layer j. In general, the number of platforms (m) will be different in each layer, for example, a private cloudlet usually has several servers while a large public cloud has thousands of servers.
At any given time, for a mobile device, there is a list of platforms that belong to each of the upper layers to offload the code. In other words, a device can offload the tasks to a specific fog node, cloudlet server, base station or cloud server, but normally, it cannot decide which of the platforms of a layer to use. This depends on several aspects such as geographical location, etc.
For a specific mobile device i, the list of higher MEC layer platforms available can be expressed as A
i:
The set of platforms described establishes the specific multi-tier MEC architecture of a mobile device and expresses the data processing offloading possibilities of the device applications at a given time. The list of platforms of a mobile device depends on the environment and may vary with time as a function of different situations. For example, it may vary based on changes in the availability of infrastructure or changes in the location of the mobile device (home, office, etc.).
There are currently multiple mechanisms or methods to provide security to computational systems. Some of the most widely used methods are user authentication using different types of credentials [
30], server authentication mainly using digital certificates [
12], confidentiality through the use of encryption mechanisms [
31], firewall systems for filtering information [
32], intrusion detection systems [
33,
34], integrity using digital signatures [
35], application and data isolation [
16], etc. Let M be the set of available security methods:
The previous methods allow for adding security to the computer systems independent of their architecture and heterogeneity. In addition, each of the security techniques can be used individually or in combination with others. As the number of security methods used increases and as long as they are combined adequately, the system security is improved. Therefore, different security levels can be established, with S being the set of possible different security levels:
The order of the different levels is important, S1 is the least safe level and Sq is the safest level. The cardinality of S is not determined, in general, few security levels are usually defined. For example, Microsoft Forefront has five security levels.
M and S are related by the fact that a higher level of security is associated with the use of more and better security methods. This relationship is expressed in the definition (9). We can extend the formalism of the framework to include different degrees of trust that each of the layers of a distributed multi-tier MEC architecture may have. Therefore, let T be the set of different degrees of trust that each of the different layers of a distributed multi-tier MEC architecture may have:
Of course, logic dictates that there is an inverse relationship between the degree of trust of a layer and its security needs. The basic idea is that the higher the degree of trust in a layer of the model, the lower the security level that will be required to establish communication with this layer. In contrast, if the degree of trust is lower, a higher level of security will be required.
Taking into account this key concept, we can establish a relationship between the degree of trust of any layer of the distributed multi-tier architecture and the level of security that this layer requires. In other words, we can determine the level of security of a model layer based on the degree of trust placed in this layer. Therefore, the following expression defines § as the function that returns a specific level of security for a given degree of trust:
where T
j ∈ T and S
i ∈ S. Since the cardinality of T and S is the same (q), there is a direct relationship between a specific degree of trust and its corresponding level of security. After determining the different degrees of trust and different security levels, we must establish the set of security methods that will be applied in each of the levels. In this case, a higher security level requires a higher number of mechanisms to guarantee the level’s security. We can establish the function Φ as a function that yields the list of security methods that we must use for a given security level:
where S
i ∈ S, M
1 ∈ M and M
k ∈ M.
In this case, the order of security methods is not important, therefore ‹M1, …, Mk› = ‹Mk, …, M1›. What is really important is to use all the methods determined by the function Φ, because the level of security is guaranteed only if all the methods are used.
After establishing the different sets of elements present, it is necessary to be able to determine the behavior of any computing paradigm and, in this specific case, the behavior of the secure MEC models with multi-tier architecture.
To determine the behavior, we will analyze the system performance and we will measure this performance as cost of execution (E) in terms of time. The cost of execution of an application in the distributed multi-tier MEC infrastructure is determined by three main components, as described in expression (10): (a) the cost of computation (Cmp); (b) the cost of communication throughout the network and its tiers (Net); and (c) the cost of security (Sec):
In expression (10), we focus on the component related to security, because this paper addresses the security of the multi-tier MEC paradigm. Therefore, the objective is to independently determine the cost associated exclusively with the security of these distributed architectures.
The cost of execution depends on the environment’s dynamics, i.e., the execution conditions change based on aspects related to the work load of each platform and the amount of network traffic. The optimal placement of edge servers in MEC environments is able to optimize the mobile edge computing network performance [
36].
In expression (10), the computation cost component is related to the processing capacity of the different computing platforms in each of the layers of the distributed MEC architecture. Of course, the higher the processing capacity of the platform is, the lower the associated computing cost associated with it. We can determine the computation cost of a task t
i of an application in any platform of the MEC architecture. The following expression shows the computation cost of a task t
i in platform j of layer k of a multi-layer architecture. The cost will be a positive real value:
where ℝ+ ⋃ {0} means the set of positive real numbers, including zero.
Similarly, the cost of execution in expression (10) also depends on the cost of communication throughout the different layers of the architecture. This second component in turn depends on the bandwidth and dynamic aspects such as the network traffic present in these links, which may generate bottlenecks or even disconnections at specific points or failure of certain links.
Based on this, the cost of communication of moving tasks and their associated data between platforms in different layers can vary according to the state conditions and workload of the communication network. Expression (12) describes the cost of communication of moving a task t
i from the mobile device to platform j in layer k:
Finally, the cost of security is related to both the processing capacity of the platforms as well as the quality of the links in the networks that connect the MEC architecture tiers. For example, encrypting communications to guarantee the confidentiality of the information will be related to the processing velocity of the corresponding encryption algorithms and therefore to the computation capacity of the platforms. On the other hand, implementing authentication mechanisms will be related to the communication velocity of the credentials of the layers involved. The following expression shows the cost of security associated with the execution of a task t
i in platform j of layer k of a multi-tier architecture:
By analyzing these three cost components and setting aside the dynamic environmental conditions (workload, network traffic, etc.), we observe that the computation cost and the cost of communication are fundamentally related to only one principal variable. The cost of computation is related to the processing capacity of the platform, and the cost of communication is related to the quality of the communications link, which is directly related to connection bandwidth.
However, the cost of security depends on multiple variables determined in the design phases and during configuration of the computational systems; in other words, the cost of the security will be directly related to the number of security mechanisms or methods used. Of course, the more security mechanisms that are used the more the total cost of security is increased.
Each of the security methods has an associated cost that is independent of the cost of the other methods. There are methods related to the processing and communication capacity, for example, authentication methods that depend on transmitting user or server credentials and subsequent verification in the database. On the other hand, there are methods that fundamentally depend on the processing capacity, for example, encryption done to guarantee the confidentiality or verification of digital signatures to guarantee integrity.
Based on this information, we will define the set of CM as the set of security costs of each of the existing methods defined in Equation (5):
The different MEC architecture layers can incorporate different numbers of security methods based on their own requirements. In other words, the distributed architecture layers can have different security levels with a combination of methods for inherent security and therefore different costs. In addition, the costs will depend on the capacities of the platforms in the layers. The top layers of multi-tier MEC architectures are those that provide services to the lower layers because they have higher computation and storage capacities. In general, the higher the number of services offered, the higher the level of security required. Given that each security level has its own cost, let CS be the set of security costs of each of the security levels defined in Equation (6).
Taking into account the previous sets and equations, we can determine the cost of security of an application based on the list of layers and platforms in which each task is executed.
We can define ∧
i[k,j] = (t
i, p
k,j) to represent that the task t
i is processed on platform j of layer k. Then, the security cost of executing task t
i on platform j of layer k is defined as:
Sec(∧i[k,j]) will be equal to the security cost of the layer k where the task ti is executed, which will depend on the level of security of the layer. Finally, Sec(∧i[k,j]) will be the sum of the security costs of each security method used in that layer of the MEC architecture.
Based on the above definitions, the sequence of layers and platforms on which the application runs is defined by the vector ∧(Γ
App) as follows:
In the above definition, ∧1[k1,j1] represents the execution of task t1 on platform j1 of layer k1 and ∧n[kn,jn] indicates execution of task tn on platform jn of layer kn.
Finally, the execution cost of an application can be obtained by expanding expression (10) with the layers and platforms of the vector ∧:
3.2. Use Case
As defined in the general framework of the model, it is possible to establish as many degrees of trust and security levels as one desires as well as to use any number of available security methods. However, for the sake of simplicity and clarity, this section proposes a use case with three degrees of trust, three security levels and five security methods. The following expressions describe the sets of degrees of trust, levels and methods that are used in the use case:
As commented before, according to the general framework, we can have as many degrees of trust in the layers of the distributed architecture as we want to have. However, this use case will only establish three degrees of trust, as follows:
High trust—corresponds to those layers of the MEC architecture in which there is total trust. In general, the layers of high trust will belong to the administrative domain itself, i.e., private fog, cloudlets or clouds which there is administrative authority. In addition, this degree of trust may also be assigned to public providers with SLA contracts for which there is certainty that they have significant security measures and third-party auditing systems [
16].
Medium trust—corresponds to those MEC layers in which there is some trust but over which there is no type of administrative authority. This degree of trust corresponds to fog or cloudlets offered by a provider of services with a measure of reliability and with which there is an SLA contract. A characteristic that defines the medium degree of trust is the limited security and auditing resources. This degree of trust will also be assigned to public providers with SLA contracts for which there is no certainty regarding the implementation of strong security measures and, especially, to those that do not have independent auditing systems.
Low trust—corresponds to those MEC layers for which there is no trust. There will be no administrative authority, and there will also be no service contract associated with them. The low degree of trust will be assigned to public providers without a service contract and which can independently decide on security and auditing measures they implement.
After defining the different degrees of trust, we will establish the level of security of each of the three degrees of trust. Like the degrees of trust, the set of security levels established in the general framework can have as many levels as required. This use case will only define three security levels that will be related to the three degrees of trust. However, a different number of degrees of trust or security levels could have been established.
As previously indicated, a higher degree of trust requires a lower level of security, i.e., there is an inverse relationship between the degree of trust of a layer in the model and its security level. This relationship will be determined by the function introduced in expression (8), which is based on degree of trust and yields of associated level of security. In this use case, we have manually set the three security levels, but they could be calculated automatically by defining a specific function according to the expression (8). In our case, the three security levels will be as follows:
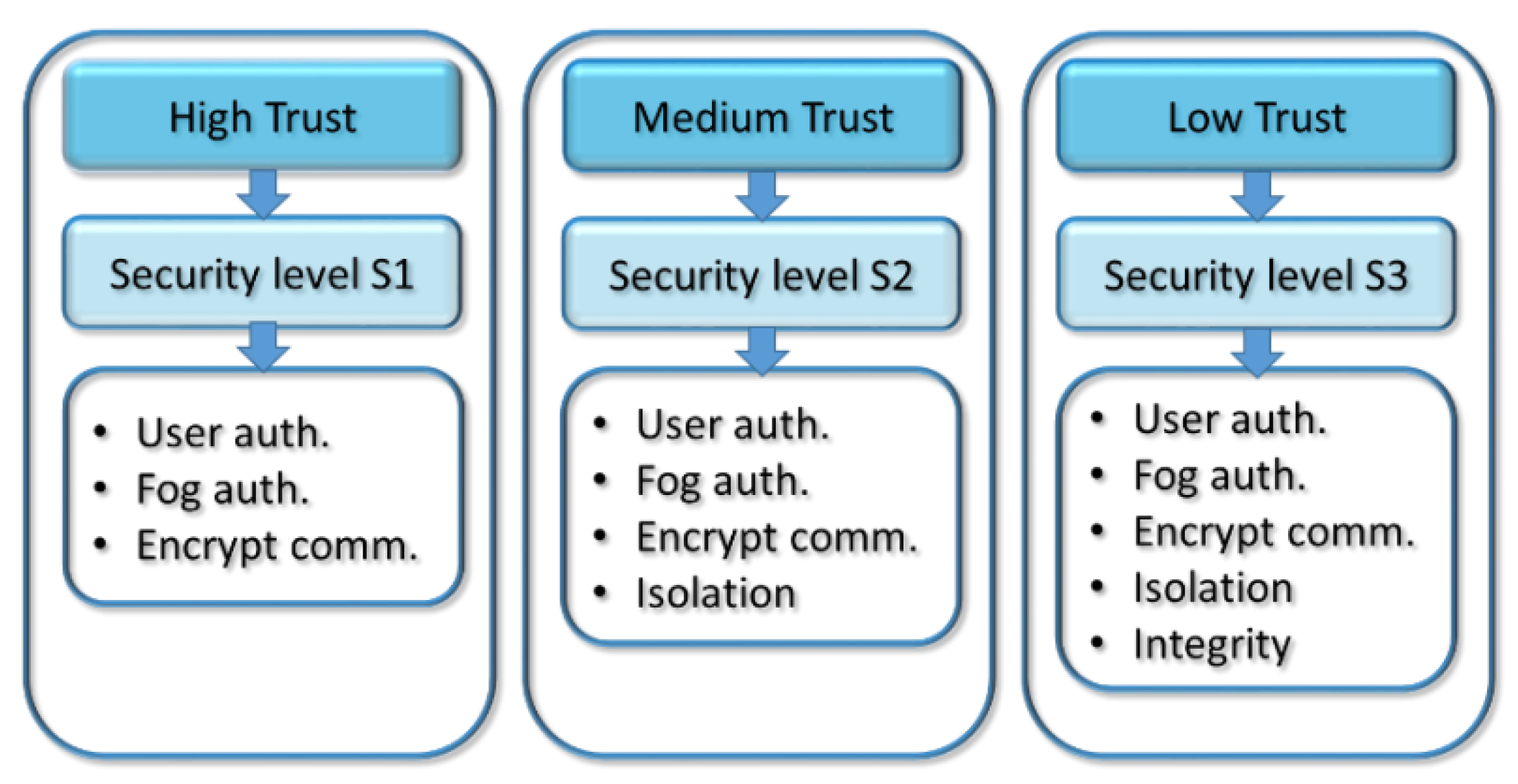
Security level S1. When a layer i of the MEC architecture is related to another layer i+1 with which there is a high degree of trust, an S1 security level will be established. The security level S1 will require the implementation of the fewest security measures.
Security level S2. This will be the security level established for those layers of the distributed architecture over which the degree of trust is medium. This level of security will require more security measures than the previous level.
Security level S3. The security level S3 will be defined for those layers of the architecture that have a low degree of trust. Of course, this level will incorporate the highest number of security measures.
In the rest of the paper the word element will refer to any computing platform, for example, a mobile device, a fog node, a cloudlet server, a cloud server, etc. When an element of the multi-tier MEC architecture establishes a relationship with another element of a higher layer in which there is a high degree of trust and, therefore, the security level is determined to be low, it will be necessary to use the following security methods:
User authentication. The element corresponding to the higher layer of the multi-tier architecture will carry out the authentication of the user that is establishing the communication. For example, if a mobile device establishes a connection with a private fog node, it will be necessary for the private fog node to carry out the user authentication of the mobile device.
Fog/cloudlet authentication. The element of the lower layer of the distributed architecture will carry out the server authentication of the higher layer with which communication is being established. For example, in the previous case, the mobile device must use the private fog node certificate to guarantee the authenticity of the fog node.
Encrypted communications. Although the degree of trust may be high, for security reasons, the exchange of information must always be encrypted using technologies such as SSL/TLS.
In summary, for a high degree of trust, the elements must use communication encryption and double authentication in both directions of the communication. On the one hand, user authentication is needed for the MEC element to validate the user that is connecting from his/her mobile device. On the other hand, fog/cloudlet authentication is needed for the device to authenticate the fog or cloudlet with which it will establish a communication.
If the degree of trust between the elements that intervene in the communication is medium, then the level of security will also be medium (S2), and therefore, the security needs will be greater than in the previous case. Specifically, when the security level is S2, the three security methods of the previous level will be used: user authentication, fog/cloudlet authentication and connection encryption. However, in addition to the three previous methods, isolation techniques or sandboxing will also be used on both sides of the connection so that the information on both MEC elements is completely isolated from other applications and the communication can only occur between the two sandboxes involved.
Finally, a low degree of trust will demand the highest level of security, which is why more security techniques will be needed than for the medium degree. Specifically, we have added integrity management through digital signatures to the methods used in the security level S2. By using this security method, we periodically verify the digital signature of the tasks that have been taken to the higher layers of the distributed MEC architecture for execution to guarantee their integrity.
Figure 1 shows the use case of the security model with different degrees of trust and security levels defined, as well as the security measures required in each of the levels. Although this use case has defined three degrees of trust, three security levels and five security methods, it is important to emphasize that we can establish as many degrees of trust and security levels as we want, and for each of them, we can use many different combinations of security methods. The key idea of the proposal is that we can adapt the level and methods of security used in relation to the degree of trust of the elements in the MEC architecture, independently of the degree of trust, levels and methods used.
The algorithms or security methods used are the following: user authentication by username and password; fog/cloudlet servers authentication using self-signed X509 certificates with openssl; communications have been made using https connections using openssl for encryption; isolation via Android Application Sandbox and servlets; and, digital signatures based on the SHA-256 algorithm were used to verify the integrity of downloaded applications.
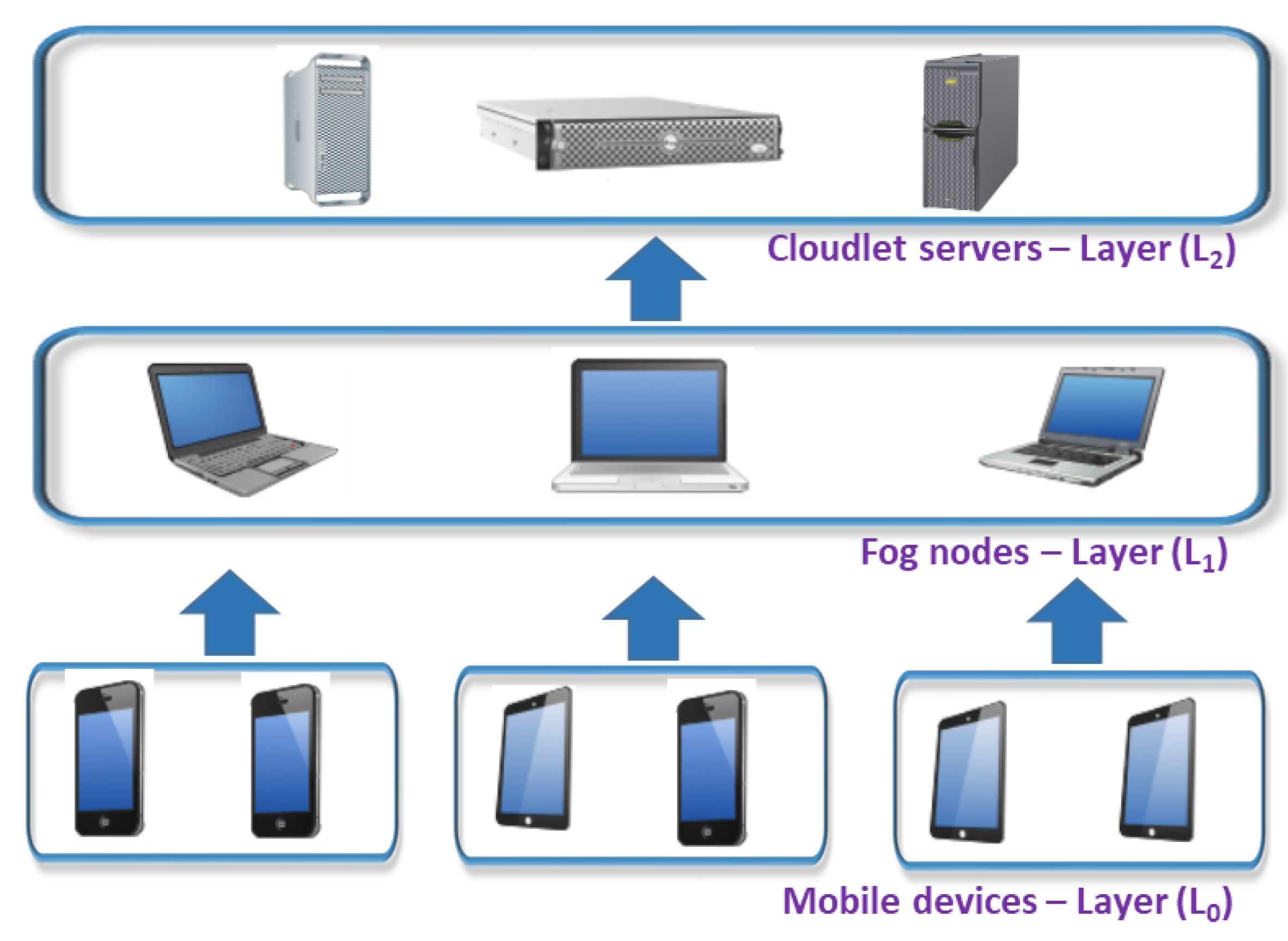
After defining the use case of the security model based on the degree of trust of the different layers of the MEC architecture and establishing the different security needs as a function of the degree of trust, we will show that the model can be applied to multi-tier MEC architectures. Specifically, we will apply the use case to a classical three-tier MEC architecture: mobile devices, fog nodes and cloudlet servers. This classical architecture is shown in
Figure 2.
Let us suppose that the fog nodes of the intermediate layer (L1) belongs to a service provider with which we have an SLA contract and that the cloudlet has no contract (L2). According to our previous description, the degree of trust placed in the fog will be medium and the degree of trust placed in the cloudlet will be low. Therefore, to establish communication between the mobile devices (layer L0) and the fog nodes (layer L1), it will be necessary to have a double authentication process; the fog will authenticate the user of the mobile device, and the mobile device will authenticate the fog node. In addition to the double authentication, the communications will be encrypted as well as isolated for both the mobile device and the fog node. In addition, for the intermediate level fog node (L1) to communicate with the cloudlet server (L2), it will be necessary to have not only the double authentication of the previous level, encrypted communications and application isolation but also the integrity of the applications guaranteed using digital signatures when offloading to the cloudlet server. As shown, the model can be extended to multi-tier MEC architectures in which each layer establishes the security measures only for the layer with which it needs to communicate, which in turn will depend on the degree of trust placed in the subsequent layer.
3.3. System Architecture
In this section, we will describe the system’s architecture by determining the different components derived from the proposed use case as well as their distribution within a multi-tier MEC architecture.
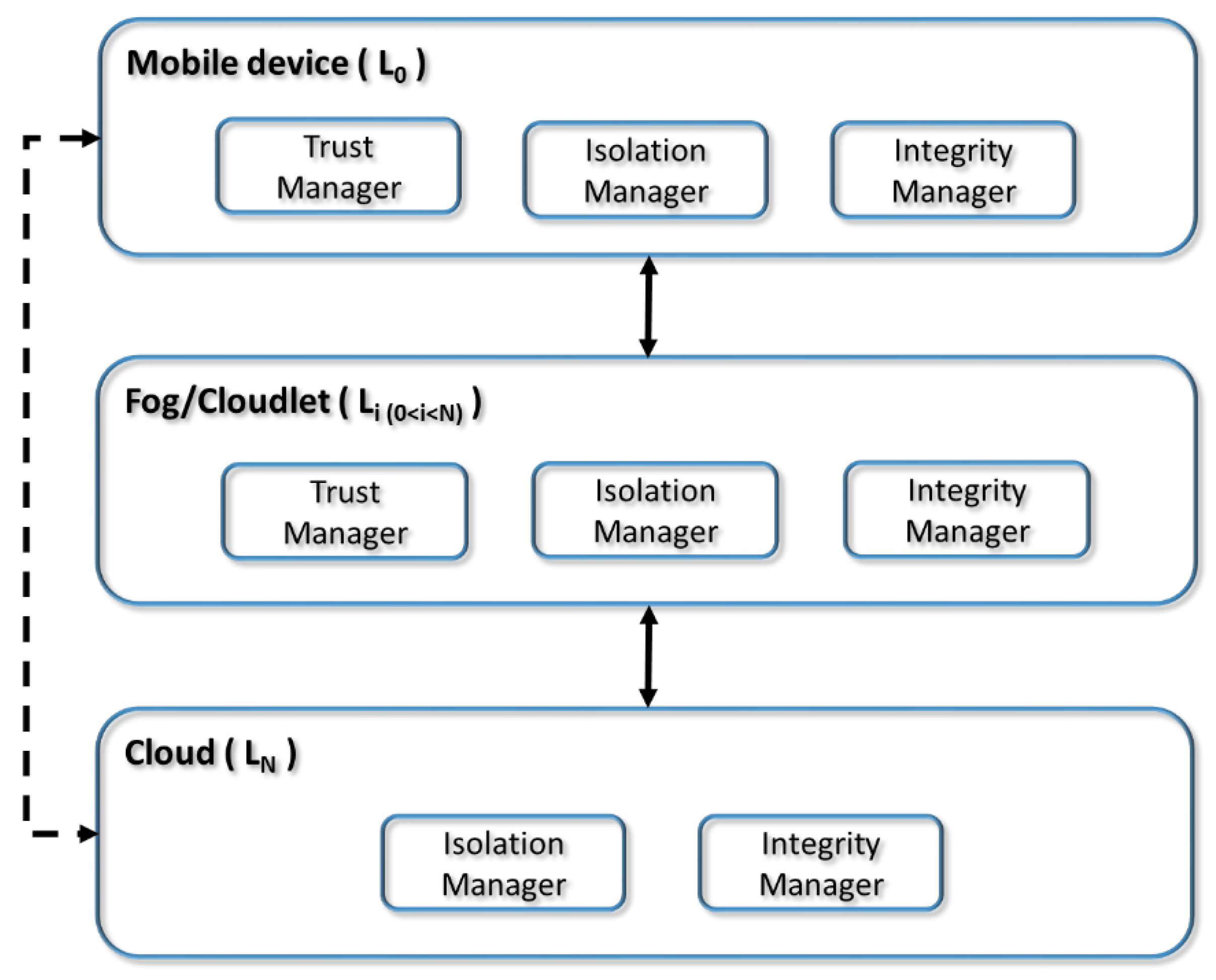
Figure 3 shows the components of the architecture and their distribution in the different MEC layers.
We have designed an architecture with three modules or principal components: trust manager, isolation manager and integrity manager. The security methods user authentication, fog/cloudlet authentication and communications encryption are not included as specific modules of the architecture because they are already well established elements that are present in all systems. These methods use user credentials and digital certificates, which will be transmitted through SSL/TLS tunnels.
When a user wishes to establish a connection through his/her mobile device with a fog or cloudlet, the first thing the user must do is to determine the degree of trust of the fog or cloudlet. The trust manager module is in charge of determining the degree of trust of the layer with which connections are to be established. There are different approximations to carry out this function, ranging from protocols—that establish trust through verifications before use—to trust schemes—based on reputation systems [
16]. In our use case, we have manually defined the degree of trust in based on compliance with a set of conditions, which include belonging to the same administrative domain, having an established SLA contract, etc.
In addition, when one of the layers that intervene in the connection has a medium degree of trust, it is necessary to use isolation techniques on both ends of the communication. The isolation manager module will be responsible for implementing the different techniques that allow for the highest possible level of isolation on both ends of the connection. To achieve this, techniques such as virtual machines and containers that are conveniently fortified for processing and storage will be used. In addition, perimeter security techniques will be used for communication isolation.
Finally, in the case of the layers that have a low degree of trust and demand a high security level, in addition to all the methods used in the medium level, it is necessary to guarantee the integrity of the tasks and applications. The integrity manager module will be in charge of validating the integrity of the applications that are offloaded from the mobile device to the low trust layer through the use of digital signature methods. To that end, the integrity manager will periodically verify the digital signature of the applications or tasks that are executed in the fog or cloudlet through data processing offloading.
The distribution of the three principal modules of the architecture in the different MEC layers is not uniform, as can be seen in
Figure 3, which shows the architecture of the system for a three-tier MEC paradigm deployment (mobile device, fog and cloudlet). The reason is that each of the layers of a multi-tier MEC architecture has different security needs or functionalities.
The mobile device (layer 0) and the intermediate layers of the MEC architecture, typically fog and cloudlets, do require the three modules: the trust manager—to obtain the degree of trust of the next layer with which it communicates—; the isolation manager—to isolate tasks and communications—; and, the integrity manager—to periodically check the integrity of the tasks—. The last layer of the MEC architecture, generally corresponding to public clouds, which can only be servers, do not have any subsequent level and do not need the trust manager module.
Note that the security model’s architecture allows the mobile device to connect only with one fog or cloudlet (continuous line) or only one cloud (dashed line), which is a two-tier MEC architecture. However, it also allows the connection to the cloud through k fog or cloudlet layers (continuous lines), establishing a multi-tier architecture. In addition, given that the intermediate MEC layers have all the modules of the security use case, it is possible to have multiple intermediate layers. Therefore, the security model and its architecture can be applied in multi-tier MEC architectures.
In summary, the multi-tier security platform, for this use case, consists of three main functional blocks: trust manager; isolation manager; and, integrity manager. These three components are necessary because they perform specific functions that are not usually present by default in existing systems. All tiers need all three components except for the last tier (LN), which does not need the trust manager. It is important to consider that there is no direct relationship between the different functional blocks. Furthermore, other use cases may need or define different functional blocks, for example, two-factor authentication. In addition, the model uses user/fog/cloudlet authentication and encryption are not shown in the architecture because they are well-known functional blocks and are present in all systems.