Abstract
With wireless sensor networks (WSNs), a driver can access various useful information for convenient driving, such as traffic congestion, emergence, vehicle accidents, and speed. However, a driver and traffic manager can be vulnerable to various attacks because such information is transmitted through a public channel. Therefore, secure mutual authentication has become an important security issue, and many authentication schemes have been proposed. In 2017, Mohit et al. proposed an authentication protocol for WSNs in vehicular communications to ensure secure mutual authentication. However, their scheme cannot resist various attacks such as impersonation and trace attacks, and their scheme cannot provide secure mutual authentication, session key security, and anonymity. In this paper, we propose a secure authentication protocol for WSNs in vehicular communications to resolve the security weaknesses of Mohit et al.’s scheme. Our authentication protocol prevents various attacks and achieves secure mutual authentication and anonymity by using dynamic parameters that are changed every session. We prove that our protocol provides secure mutual authentication by using the Burrows–Abadi–Needham logic, which is a widely accepted formal security analysis. We perform a formal security verification by using the well-known Automated Validation of Internet Security Protocols and Applications tool, which shows that the proposed protocol is safe against replay and man-in-the-middle attacks. We compare the performance and security properties of our protocol with other related schemes. Overall, the proposed protocol provides better security features and a comparable computation cost. Therefore, the proposed protocol can be applied to practical WSNs-based vehicular communications.
1. Introduction
Wireless sensor networks (WSNs), in conjunction with intelligent transport systems (ITS) and embedded technology, have advanced to such an extent that drivers can make full use of various information such as traffic congestion, vehicle accidents, and speed. To provide these useful services, a sensor in the vehicle collects data on the vehicle and surrounding area and sends it to the traffic manager through a sink node. The traffic manager in the traffic management office receives data from vehicle sensors and can monitor a vehicle and the surrounding area to provide useful data to the driver in real time. However, a malicious adversary can easily obtain and modify the data because it is transmitted via a public network. Therefore, the authentication protocol between the vehicle and user in vehicular communications has become a very important security issue. In the last few decades, numerous authentication schemes for WSNs have been proposed to ensure secure communications and user privacy [1,2,3,4,5,6,7,8]. In 2006, Wong et al. [9] proposed a dynamic ID-based user authentication scheme for WSNs. However, Das et al. [10] showed that Wong et al.’s [9] scheme is vulnerable to the stolen verifier attack and proposed an improved two-factor authentication scheme to overcome these security problems. In 2010, Chen et al. [11] demonstrated that Das et al.’s scheme [10] cannot provide secure mutual authentication and cannot resist parallel session attacks. To resolve this problem, they proposed a robust mutual authentication scheme for WSNs. Khan et al. [12] also showed that Das et al.’s scheme [10] cannot prevent the privileged insider and bypassing attacks, nor can it provide mutual authentication and the password changing phase. To overcome these security weaknesses, they proposed a two-factor user authentication protocol that uses secret parameters. In 2011, Yeh et al. [13] found that Das et al.’s scheme cannot resist the insider attack and provide mutual authentication, which are essential security requirements for the WSNs. They proposed a secured authentication protocol for WSNs that uses elliptic curve cryptography (ECC). Unfortunately, Han [14] pointed out that Yeh et al.’s scheme cannot provide mutual authentication, perfect forward secrecy, and key agreement. To resolve the security weaknesses of Yeh et al.’s scheme, Shi et al. [15] proposed a new user authentication protocol for WSNs using ECC. However, Choi et al. [16] showed that Shi et al.’s [15] scheme is vulnerable to a smartcard being stolen, sensor energy exhaustion, and session key attacks. They proposed a new user authentication protocol based on ECC.
In the last few decades, numerous protocols for secure vehicle communications have been proposed [17,18,19,20,21,22,23,24,25]. In 2008, Zhang et al. [17] proposed an efficient roadside unit (RSU)-aided message authentication scheme that uses a hash message authentication code (HMAC) for vehicular communications networks. Zhang et al. also proposed [18] an efficient message authentication scheme for vehicular communications. Lu et al. [19] proposed an efficient conditional privacy preservation protocol for secure vehicular communications that uses bilinear pairing. However, their protocol is not efficient in resource-constrained vehicular ad hoc networks (VANETs) because it has used multiple anonymous key and has high latency for generating of pseudo-random keys [20]. In 2014, Chuang and Lee [21] proposed an authentication mechanism for vehicle to vehicle communications in VANETs. However, in 2016, Kumari et al. [22] showed that Chuang and Lee’s authentication protocol is vulnerable to insider and impersonation attacks, and they proposed an enhanced authentication protocol for VANETs. In 2017, Mohit et al. [23] also proposed an authentication protocol for WSNs in vehicle communications. Mohit et al. claimed that their proposed scheme can resist various attacks such as smartcard stolen, impersonation, and untraceable attacks. In this paper, however, we demonstrate that their scheme cannot resist impersonation and trace attacks. In addition, we show that Mohit et al.’s scheme cannot provide anonymity, session key security, and mutual authentication. We propose a secure authentication protocol for WSNs in vehicle communications that overcomes these security weaknesses.
1.1. Threat Model
To analyze the security of our proposed scheme, we introduce the Dolev–Yao (DY) threat model, which is widely used to evaluate the security of a protocol. The detailed assumptions of the DY threat model are as follows:
- An adversary can modify, eavesdrop, insert or delete the transmitted messages over a public channel.
- An adversary can obtain a lost or smartcard stolen, and he/she can also extract the information stored in the smartcard [26,27].
- An adversary can perform various attacks such as impersonation, trace, smartcard stolen, and replay attacks.
1.2. Our Contributions
The main contributions of this paper are as follows:
- We demonstrate that Mohit et al.’s scheme is vulnerable to various attacks such as impersonation and trace attacks. In addition, we point out that their scheme cannot provide mutual authentication, session key security and anonymity.
- We propose a secure authentication protocol for WSNs in vehicular communications to resolve these security weaknesses. Our proposed protocol prevents impersonation and trace attacks, and also achieves anonymity, session key security and secure mutual authentication. In addition, the proposed scheme is efficient because it utilizes only hash function and XOR operation in authentication phase.
- We prove that our protocol provides secure mutual authentication by using the broadly accepted Burrows–Abadi–Needham (BAN) logic [28]. We also perform an informal analysis to demonstrate the security of the proposed protocol against various attacks such as impersonation and trace attacks.
- We compare the performance of our scheme against those of related existing schemes and perform a formal security verification by using the widespread Automated Validation of Internet Security Protocols and Applications (AVISPA) simulation software tool.
1.3. Paper Outline
The remainder of this paper is organized as follows. In Section 2, we introduce the vehicular communications system model. In Section 3 and Section 4, we review Mohit et al.’s authentication scheme and analyze its security weaknesses. In Section 5, we propose a secure authentication protocol for WSNs in vehicular communications to resolve the security problems of their scheme. In Section 6, we present an informal analysis on the security of our protocol and prove that it achieves secure mutual authentication by using BAN logic. In Section 7 and Section 8, we present the formal security verification with the AVISPA simulation tool and compare the performance of our protocol with that of related protocols. Finally, we present our conclusions in Section 9.
2. System Model
In this section, we introduce a vehicular communication system using WSNs and essential security requirements. There are three entities involved in the vehicular communications system: the vehicle sensor, sink node, and user. The vehicular communications system model is shown in Figure 1.
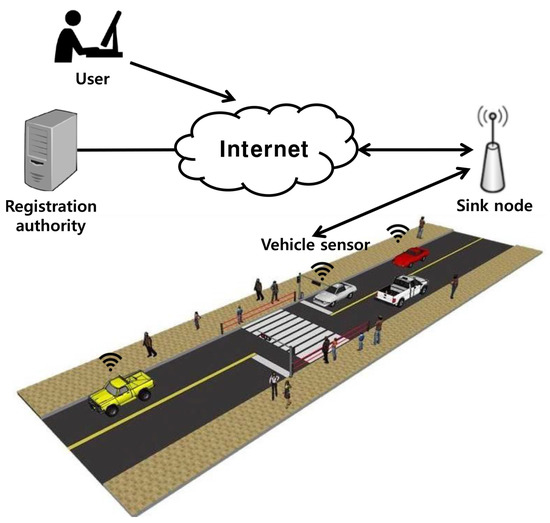
Figure 1.
Vehicular communications system model.
The vehicular communications system consists of two parts: the WSNs and vehicle and the user and sink node. The vehicle sensor is deployed in the vehicle and collects data on the traffic and surrounding area in real time, which it then sends to the sink node. After receiving the data from the vehicle sensor, the sink node stores it for the user. The user can control the response to traffic jams, speed, and emergency situations based on the data collected by the sink node.
The numerous authentication protocols [29,30,31] have defined security requirements in order to explain their security goals. Therefore, we also define the essential security requirements to explain and ensure our security goals.
- Untraceability and anonymity. In a modern vehicular communication system, user’s real identity and location data are very sensitive information. For these reason, an adversary cannot trace a user’s location and know the user’s real identity to guarantee a privacy of user.
- Secure mutual authentication. A secure mutual authentication is known for a essential security requirement in VANETs in order to guarantee that only the legitimate users should access the services and communicate securely with each other [32].
- Confidentiality. In our system, the user, sink node, and vehicle sense can freely communicate among themselves through a internet. However, an adversary can try to obtain various pieces of information from users such as traffic congestion, speed, and vehicle accident because it is transmitted in a public channel. Therefore, a confidentiality must be guaranteed and the transmitted data is only known to legitimate user in order to ensure a security.
3. Review of Mohit et al.’s Scheme
In this section, we review Mohit et al.’s authentication protocol for WSNs, which consists of three phases: system setup, user registration, and user login and authentication. Table 1 presents the notations used in this paper.

Table 1.
Notations.
3.1. System Setup Phase
When a driver wants to deploy a sensor in a vehicle, the registration authority (RA) registers the vehicle sensor in the network. In addition, RA stores various data on the vehicle such as the vehicle number, engine, battery, and insurance in a database.
3.2. User Registration Phase
If a new traffic manager wants to register him or herself, must send the registration request message to the sink node first. The user registration phase of Mohit et al.’s scheme is shown in Figure 2, and the detailed steps are described as follows.
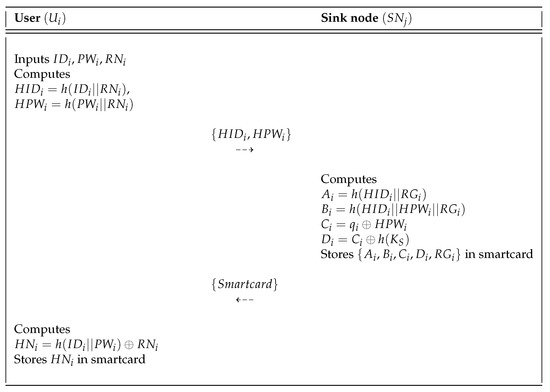
Figure 2.
User registration phase of the Mohit et al.’s scheme.
- Step 1:
- chooses an identity , password , and random nonce . then computes , and sends them to the sink node via a secure channel.
- Step 2:
- selects a random nonce and random number , and then computes , , , and . After that, stores in the smartcard and issues the smartcard to through a secure channel.
- Step 3:
- Upon receiving the smartcard, computes and stores it in the smartcard. Ultimately, the smartcard contains .
3.3. User Login and Authentication Phase
If a user wants to access the system, must send the login request message to the sink node . After receiving the login request message from , checks whether it is legitimate. If it is valid, performs the authentication phase. The user login and authentication phase of Mohit et al.’s scheme is shown in Figure 3. The detailed steps of this phase are described as follows.
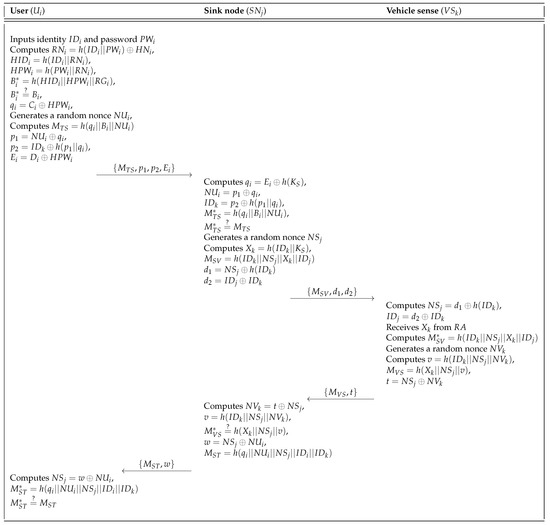
Figure 3.
User login and authentication phase of the Mohit et al.’s scheme.
- Step 1:
- inserts the smartcard into a card reader and inputs and . The smartcard then computes , , , and . Then, the smartcard checks whether . If it is equal, the smartcard computes and generates a random nonce . The smartcard also computes , , and . Finally, the smartcard sends the login request message to via a public channel.
- Step 2:
- After receiving the login request message from , retrieves and . Then, computes and checks whether is equal to . Then, generates a random nonce and computes , , . Finally, sends to the vehicle sensor.
- Step 3:
- Upon receiving the message , the vehicle sensor retrieves and . Then, checks the freshness of . If it is fresh, sends and requests the sink node’s master key from . After receiving from through a secure channel, computes and checks whether . If it is verified, chooses a random nonce and computes , , and . Finally, sends to .
- Step 4:
- After receiving the message , retrieves and computes . Then, checks whether is correct. If it is correct, computes , and sends to .
- Step 5:
- Upon receiving the message from , retrieves and computes , and then checks whether is correct. If they are equal, mutual authentication has been successfully achieved.
3.4. Password Change Phase
can freely update his or her password when desired. The password change phase is described in Figure 4 and the detailed steps of this phase are as follows.
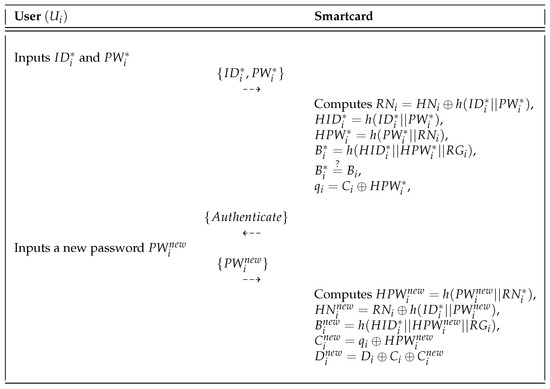
Figure 4.
Password change phase of the Mohit et al.’s scheme.
- Step 1:
- inserts smartcard in the card reader and inputs the identity and password , and then submits to the card reader via a secure channel.
- Step 2:
- After receiving , the smartcard computes , , , and . It checks whether . If this is verified, the smartcard sends the authentication message and requests a new password from . After receiving the authentication message from smartcard, inputs the new password .
- Step 3:
- The smartcard calculates , , , , and by using the new password of . Finally, smartcard replaces with .
4. Cryptanalysis of Mohit et al.’s Scheme
In this section, we discuss the security weaknesses of Mohit et al.’s scheme. They asserted that their scheme is secure against trace and impersonation attack, and they showed that their scheme can provide anonymity, session key security and secure mutual authentication. However, here we demonstrate that Mohit et al.’s scheme does not resist the following attacks.
4.1. Impersonation Attack
If an adversary tries to impersonate a legitimate user, can successfully generate a login request message of legitimate user . According to Section 1.1, we can assume that obtains the smartcard of the legitimate user and extracts the values stored in smartcard and that has the messages transmitted in the previous session. Here, we show that Mohit et al.’s scheme does not prevent an impersonation attack.
- Step 1:
- computes , , , , and , where , , and are messages of the previous session.
- Step 2:
- can obtain the secret parameters , , and and a random nonce . then chooses a random nonce and computes , , and . Finally, generates the login request message and sends it to the sink node .
- Step 3:
- After receiving the login request message from , retrieves , and . then computes and checks whether is equal to . Then, generates a random nonce and computes , , , and . Finally, sends to the vehicle sensor.
- Step 4:
- Upon receiving the message , the vehicle sensor retrieves and , and then checks the freshness of . If it is fresh, sends and requests the sink node’s master key from . After receiving from through a secure channel, computes and checks whether . If it is verified, chooses a random nonce and computes , , and . Finally, sends to .
- Step 5:
- After receiving the message , retrieves and computes and . Then, checks whether is correct. If it is correct, computes and and sends to .
- Step 6:
- Upon receiving the message from , successfully achieves mutual authentication.
Therefore, Mohit et al.’s scheme is vulnerable to impersonation attacks.
4.2. Trace Attack and Anonymity Preservation
According to Section 4.1, an adversary can obtain the real identities of the vehicle sensor and sink node. First, retrieves the vehicle sensor’s real identity and then computes . Finally, retrieves the sink node’s real identity . For this reason, Mohit et al.’s scheme does not prevent trace attack or provide anonymity.
4.3. Mutual Authentication
In Section 4.1, we demonstrate that Mohit et al.’s scheme does not resist impersonation attacks. An adversary can compute the login request message and successfully achieve mutual authentication with . In addition, the sink node cannot compute the authentication message in the login and authentication phase because does not know the real identity of . Therefore, Mohit et al.’s scheme does not provide secure mutual authentication.
4.4. Session Key Security
Mohit et al. claimed that their scheme can provide session key security because an adversary cannot compute . However, we demonstrate that an adversary can compute the value in Section 4.1. Therefore, Mohit et al.’s scheme cannot achieve session key security.
5. Proposed Protocol
In this section, we propose a secure authentication protocol for WSNs in vehicle communications to resolve the security problems of Mohit et al.’s scheme [23]. Our proposed scheme consists of four phases: system setup, user registration, login and authentication and password change. In our protocol, the system setup phase is equivalent to that of Mohit et al.’s scheme. The details of the other three phases are presented below.
5.1. User Registration Phase
When a new user wants to first access the sink node as a traffic manager, he or she must first register with the sink node. The user registration phase of the proposed protocol is shown in Figure 5 and the detailed steps are as follows:
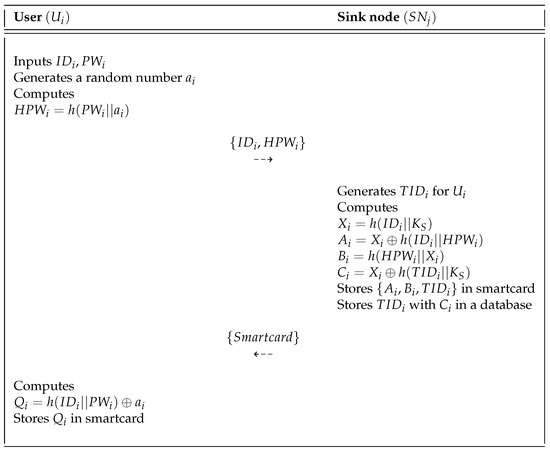
Figure 5.
User registration phase of the proposed scheme.
- Step 1:
- The user selects the identity and password and then generates a random number to computes . Then, sends to the sink node via a secure channel.
- Step 2:
- After receiving the registration request message from , generates a random unique identity for and computes , and . After that, stores in a smartcard, which it issues to through a secure channel. Finally, stores in a database.
- Step 3:
- Upon receiving the smartcard from , calculates and stores in the smartcard. Consequently, stores in the smartcard.
5.2. Login and Authentication Phase
If a user wants to access the sink node , must send a login request message. The login and authentication phase of our scheme is shown in Figure 6 and the details of this phase are as follows.
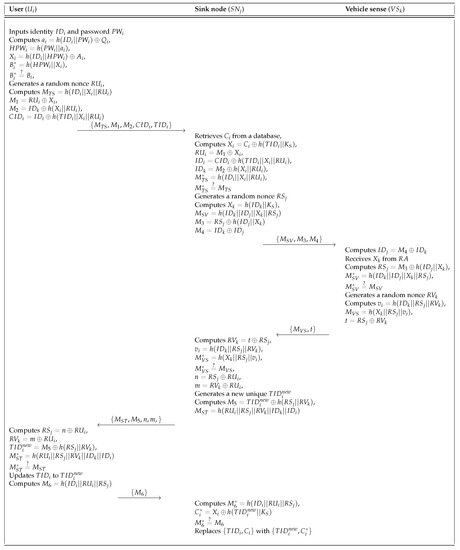
Figure 6.
User login and authentication phase of the proposed scheme.
- Step 1:
- inserts the smartcard and inputs the identity and password into a smartcard reader. Then, computes , and and checks whether . If it is equal, generates a random nonce and computes , and . sends the login request message to through a public channel.
- Step 2:
- After receiving the login request message from , retrieves matched with in a database. Then, computes , and and checks whether . If it is correct, generates a random nonce and computes , and . also sends the authentication request message to via a public channel.
- Step 3:
- Upon receiving the message , computes and receives from . Then, computes and and checks whether . If they are equal, generates a random nonce and computes , and . Finally, sends to through a public channel.
- Step 4:
- After receiving the message from , computes and . Then, checks whether . If it is equal, computes and . After that, generates a new random unique identity and computes and . also sends the message to via an open channel.
- Step 5:
- Upon receiving the message , computes , and . Then, checks whether . If it is equal, updates to . Finally, computes and sends the confirmation message to .
- Step 6:
- After receiving the message from , computes and . Then, checks whether . If it is valid, replaces with .
5.3. Password Change Phase
In our proposed protocol, can change the password when desired without the help of the sink node . The password change phase is shown in Figure 7 and the detailed steps of this phase are presented below:
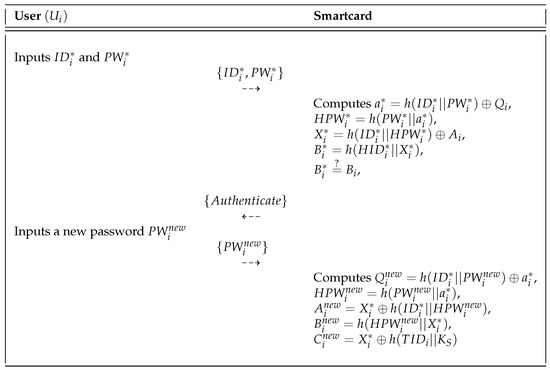
Figure 7.
Password change phase of the proposed scheme.
- Step 1:
- inserts his or her smartcard into a card reader and inputs the identity and old password .
- Step 2:
- computes , and . Then, compares the computed with the stored in its memory. If it is valid, sends an authentication message to .
- Step 3:
- On receiving the message from the smartcard, inserts the new password in the smartcard.
- Step 4:
- Using the new password , computes , and . Finally, the smartcard replaces the old information with .
6. Security Analysis
In this section, we use the Burrow–Abadi–Needham (BAN) logic [28], which is a broadly accepted formal security model, to carry out an analysis and prove that our protocol can provide secure mutual authentication. We also demonstrate that our proposed protocol can resist various attacks through an informal security analysis, which is based on Section 1.1.
6.1. Informal Security Analysis
We present an informal security analysis of our proposed scheme to show that it prevents trace, impersonation, and replay attacks. In addition, we demonstrate that our protocol can achieve mutual authentication and anonymity.
6.1.1. Impersonation Attack
If an adversary tries to impersonate a legitimate user , must generate a login request message and response message successfully. However, cannot generate these because cannot know the real identity of and secret parameters , and . In addition, does not retrieve a random nonce from . Therefore, our protocol resists impersonation attacks because cannot generate valid messages.
6.1.2. Trace Attack and Anonymity
In the login and authentication phase of our protocol, an adversary cannot trace a legitimate user or vehicle because all transmitted messages are changed every session. In addition, sends the dynamic identity and to the sink node, and the identity of is also included in . In other words, to obtain the record of a user’s movement and real identity, an adversary must know the user’s real identity , secret parameter , and random nonces , , and . For these reasons, our protocol provides the anonymity and is secure against trace attacks.
6.1.3. Smartcard Stolen Attack
According to Section 1.1, we assume that an adversary can obtain a smartcard and extract the parameters . However, cannot obtain any sensitive user information without and because the parameters stored in smartcards are masked in , , , , and by the hash function and XOR operation. Consequently, our proposed protocol prevents smartcard stolen attack.
6.1.4. Replay Attack
According to Section 1.1, we suppose that adversary tries to impersonate a legitimate user by resending messages transmitted in the previous session, cannot impersonate successfully. In our scheme, the sink node checks whether a random nonce is fresh or not. If a random nonce value is not fresh, rejects the login request message. In addition, cannot generate the confirmation message successfully because cannot obtain the random nonce generated by . Therefore, the proposed protocol is secure against replay attacks.
6.1.5. Secure Mutual Authentication
When receiving the login message and confirmation message from , the sink node checks whether and are correct. In addition, retrieves from a database to validate . If this is correct, authenticates . After receiving from , the sink node checks whether is valid. If it is valid, authenticates . Finally, the user checks whether the received value is correct. If it is correct, authenticates . Therefore, all entities authenticate each other successfully because an adversary cannot know the important parameters discussed in Section 6.1.1 and Section 6.1.2.
According to Section 6.1.2 and Section 6.1.5, all transmitted messages are changed every session and an adversary cannot obtain user’s sensitive information. Therefore, we achieve essential security requirement into untraceability, anonymity, secure mutual authentication and confidentiality. Furthermore, secure mutual authentication is proved in Section 6.2 using BAN logic.
6.2. Security Analysis Using BAN Logic
To prove the secure mutual authentication of our protocol, we perform an analysis with the BAN logic [28], which is a widely accepted formal security model. First, we define the notation of the BAN logic in Table 2. Then, we describe the logical postulates of the BAN logic in Section 6.2.1. Next, we present the goals, idealized form, and initial assumptions of our protocol. Finally, we demonstrate that our protocol achieves secure mutual authentication between and by using the BAN logic.

Table 2.
Notations of the BAN logic.
6.2.1. Postulates of BAN Logic
The postulates of the BAN logic are given below:
- 1.
- Message meaning rule :
- 2.
- Nonce verification rule :
- 3.
- Jurisdiction rule :
- 4.
- Freshness rule :
- 5.
- Belief rule :
6.2.2. Goals
We have the following goals to prove the secure mutual authentication of our proposed protocol:
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- Goal 5:
- Goal 6:
6.2.3. Idealized Forms
The idealized forms of the transmitted messages are given below:
- Msg1:
- :
- Msg2:
- :
- Msg3:
- :
- Msg4:
- :
- Msg5:
- :
6.2.4. Assumptions
We make the following initial assumptions to perform the BAN logic proof:
- A1:
- A2:
- A3:
- A4:
- A5:
- A6:
- A7:
- A8:
- A9:
- A10:
- A11:
- A12:
6.2.5. Proof Using BAN Logic
The detailed steps of the main proof are as follows:
- Step 1:
- According to , we can obtain
- Step 2:
- In conformity with the message meaning rule with and , we can get
- Step 3:
- According to the freshness rule with , we can get
- Step 4:
- According to the nonce verification rule with and , we can obtain
- Step 5:
- According to , we can get
- Step 6:
- In conformity with the message meaning rule with and , we can get
- Step 7:
- According to the freshness rule with , we can obtain
- Step 8:
- According to the nonce verification rule with and , we can get
- Step 9:
- According to , we can obtain
- Step 10:
- In conformity with the message meaning rule with and , we can obtain
- Step 11:
- According to the freshness rule with , we can get
- Step 12:
- According to the nonce verification rule with and , we can get
- Step 13:
- According to , we can obtain
- Step 14:
- In conformity with the message meaning rule with and , we can get
- Step 15:
- According to the freshness rule with , we can get
- Step 16:
- According to the nonce verification rule with and , we can get
- Step 17:
- According to the belief rule with , we can get
- Step 18:
- In conformity with the jurisdiction rule with and , we can obtain
- Step 19:
- In conformity with the belief rule with , we can get
- Step 20:
- According the jurisdiction rule with and , we can obtain
- Step 21:
- In conformity with the belief rule with , we can get
- Step 22:
- According the jurisdiction rule with and , we can obtain
Based on goals 1–6, we prove that our proposed protocol achieves secure mutual authentication between and .
7. Security Analysis Using the AVISPA Tool
In this section, we perform a formal security verification of our protocol with the widely accepted Automated Validation of Internet Security Protocols and Applications (AVISPA) simulation tool [33,34]. Formal security verification with this tool has received much attention and has been used in numerous studies to demonstrate that various authentication protocols are secure against replay and man-in-the-middle attacks [35,36,37,38,39].
With AVISPA, the security protocol must be implemented by using the High Level Protocols Specification Language (HLPSL) [40]. The HLPSL specifications of the security protocol are translated to an intermediate format (IF) by the HLPSLIF translator. Finally, it is converted to the output format (OF) with the On-the-fly Model-Checker (OFMC) [41], the CL-based Attack Searcher (AtSe) [42], SAT-based Model-Checker (SATMC), or Tree Automata-based Protocol Analyzer (TA4SP).
7.1. HLPSL Specifications
According to HLPSL, the proposed protocol has three entities, which are called : denotes a user , denotes a sink node , and denotes a vehicle sense . The and also contain the security goals, as shown in Figure 8. The role specifications of are shown in Figure 9 and the details are as follows.

Figure 8.
Role specification for session and environment.

Figure 9.
Role specification for user .
When receives the start message, changes the state value 0 to 1. Then, sends the registration request to via a secure channel and receives the smartcard from . After that, updates the state from 1 to 2. During the login and authentication phase, sends the login message to via a public channel. Then, declares , which means that it generates a random nonce . After generating , receives the message from and updates the state from 2 to 3. Finally, sends to through a public channel and authenticates by using a random nonce . Similarly, the simulated results of and are defined as shown in Figure 10 and Figure 11.

Figure 10.
Role specification for .

Figure 11.
Role specification for .
7.2. Analysis of Simulation Results
In this section, we present the results of the AVISPA analysis using OFMC and CL-AtSe back-ends to ensure the security of our protocol, as shown in Figure 12. To estimate the security against replay attack, the OFMC and CL-AtSe back-ends check whether a legitimate entity can execute the protocol by searching for a passive adversary. Moreover, the OFMC and CL-AtSe back-ends also check whether the proposed protocol is secure against the man-in-the-middle attack for the DY model checking.
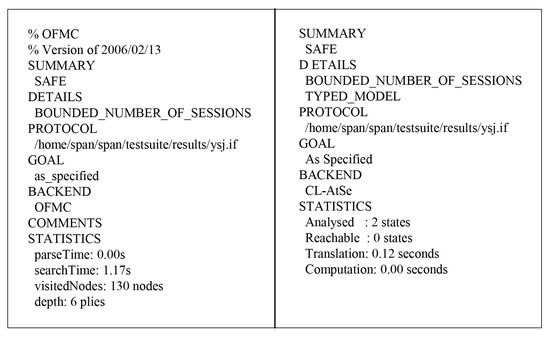
Figure 12.
The result of analysis using OFMC and CL-AtSe
The OFMC back-end has a search time of 1.17 seconds to visit 130 nodes, and the CL-AtSe back-end analyzes two states with a translation time of 0.12 seconds. Because the replay attack and Dolev–Yao model checking are performed successfully, the proposed protocol is safe against replay and man-in-the-middle attacks.
8. Performance Analysis
In this section, we compare the computation and communication costs of our proposed protocol with those of related protocols [3,15,16,23,43,44] and discuss the security properties.
8.1. Computation Cost
We compare the computation overheads of our protocol with those of related protocols [3,15,16,23,43,44]. For the comparison of computation cost, we define the notations as follows. , , and denote the times for hash operation (≈0.0005 s), symmetric key cryptographic operation (≈0.0087 s) and elliptic curve scalar point multiplication operation (≈0.0630 s), respectively. The analysis results are presented in Table 3.

Table 3.
Computation cost of our proposed scheme with other related schemes.
We use the existing computation analysis results of Mohit et al. [23] for a rough evaluation. We do not include the XOR operation because it is negligible compared with the other operations. The results show that our protocol needs for the user, for the sink node, and for the sensor. Thus, total cost of our protocol is 0.0125 seconds. Even though this is slightly higher than the cost for Mohit et al.’s protocol, the difference is negligible, and the proposed protocol provides better security than other protocols. Therefore, our protocol is secure and suitable for practical WSNs environments.
8.2. Security Properties
Table 4 compares the security properties of our proposed protocol compared with other related protocols. The existing related schemes clearly cannot resist various attacks, and their protocols cannot achieve anonymity and mutual authentication. For these reasons, our protocol provides better security features than the other protocols [3,15,16,23,43,44].

Table 4.
Security properties of our proposed scheme with other related schemes.
8.3. Communication Cost
Finally, we analyze the communication cost of our scheme with related protocols. For the communication analysis, we assume that a random nonce (number) and timestamp are 64 bits, a pseudo-identity is 160 bits, the SHA-1 hash digest [45] is 160 bits, elliptic curve scalar multiplication is 512 bits, and symmetric key cryptographic operation is 256 bits. In the login and authentication phase of our protocol, the transmitted messages require bits), bits), bits), bits) and 160 bits, respectively. Consequently, the total communication cost is bits). Table 5 presents the results of this analysis. Even though our protocol has a higher communication cost than Mohit et al.’s scheme, the vehicle sense sends only 224 bits, which is similar to that of their scheme. Therefore, from the perspective of limited resources, the proposed scheme is sufficiently applicable to WSN environments.

Table 5.
Communication cost of our proposed scheme with other related schemes.
9. Conclusions
In this paper, we demonstrate that Mohit et al.’s scheme does not resist the impersonation and trace attacks. We also show that it does not achieve secure mutual authentication, session key security, and anonymity. We propose a secure authentication protocol for WSNs in vehicular communications to resolve the security problems of their scheme. The proposed protocol is secure against impersonation, replay, smartcard stolen and trace attacks and can achieve secure mutual authentication and anonymity by using dynamic values for the transmitted messages that change every session. We also prove that our protocol can provide secure mutual authentication between , and by using BAN logic and we present a formal security verification using the AVISPA tool. Furthermore, we compare the performance and security functionalities with those of other related protocols. Therefore, the proposed protocol can be efficiently applied to practical vehicle communications systems.
Author Contributions
Conceptualization, S.Y.; Formal Analysis, K.P.; Project Administration, Y.P.; Software, J.L.; Supervision, Y.P.; Writing—Original Draft, S.Y.; Writing—Review and Editing, K.L., K.P. and Y.P.
Funding
This work was supported by the Basic Science Research Program through the National Research Foundation of Korea funded by the Ministry of Science, ICT and Future Planning under Grant 2017R1A2B1002147 and in part by the BK21 Plus project funded by the Ministry of Education, Korea under Grant 21A20131600011.
Acknowledgments
The authors would like to thank the anonymous reviewers and the Associate Editor for their valuable feedback on the paper, which helped us to improve its quality and presentation.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chatterjee, K.; De, A.; Gupta, D. A secure and efficient authentication protocol in wireless sensor network. Wirel. Pers. Commun. 2015, 81, 17–37. [Google Scholar] [CrossRef]
- Kim, J.; Lee, D.; Jeon, D.; Lee, Y.; Won, D. Security anaylsis and improvements two-factor mutual authentication with key agreement in wireless sensor networks. Sensors 2014, 14, 6443–6462. [Google Scholar] [CrossRef] [PubMed]
- Kumari, S.; Om, H. Authentication protocol for wireless sensor networks applications like safety monitoring in coal mines. Comput. Netw. 2016, 104, 137–154. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. On the anonymity of two-factor authentication schemes for wireless sensor networks. Comput. Netw. 2014, 73, 41–57. [Google Scholar] [CrossRef]
- Park, Y.; Park, Y. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Q.; MA, P.F.; Lu, X.; Tian, Y.L. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl. 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G.P. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Amin, R.; Hafizul Islam, S.K.; Biswas, G.P.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the 2006 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC’06), Taichung, Taiwan, 5–7 June 2006; Volume 1, pp. 1–8. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Chen, T.H.; Shih, W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and security improvements of two-factor user authentication in wireless sensor networks. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef] [PubMed]
- Han, W. Weakness of a Secured Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. IACR Cryptol. ePrint Arch. 2011, 2011, 293. [Google Scholar]
- Shi, W.; Gong, P. A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Sens. Netw. 2013, 2013, 730831. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, D.; Kim, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef] [PubMed]
- Zhang, C.; Lin, X.; Lu, R.; Ho, P.H. RAISE: An efficient RSU-aided message authentication scheme in vehicular communication networks. In Proceedings of the 2008 IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 1–7. [Google Scholar]
- Zhang, C.; Lin, X.; Lu, R.; Ho, P.H.; Shen, S. An Efficient Message Authentication Scheme for Vehicular Communications. IEEE Trans. Veh. Technol. 2008, 57, 3357–3368. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.H.; Shen, X. ECPP: Efficient conditional privacy preservation protocol for secure vehicular communications. In Proceedings of the 2008 IEEE INFOCOM Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1–9. [Google Scholar]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An efficient pseudonymous authentication-based conditional privacy protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]
- Chuang, M.C.; Lee, J.F. Team: Trust-extended authentication mechanism for vehicular ad hoc networks. IEEE Syst. J. 2014, 8, 749–758. [Google Scholar] [CrossRef]
- Kumari, S.; Karuppiah, M.; Li, X.; Wu, F.; Das, A.K.; Odelu, V. An enhanced and secure trust-extended authentication mechanism for vehicular ad-hoc networks. Secur. Commun. Netw. 2016, 9, 4255–4271. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Biswas, G. Design of authentication protocol for wireless sensor network-based smart vehicular system. Veh. Commun. 2017, 9, 64–71. [Google Scholar] [CrossRef]
- Alshaer, H.; Elmirghani, J.M. Road safety based on efficient vehicular broadcast communications. In Proceedings of the 2009 IEEE Intelligent Vehicles Symposium, Xian, China, 3–5 June 2009; pp. 1155–1160. [Google Scholar]
- Alshaer, H. Securing vehicular ad-hoc networks connectivity with roadside units support. In Proceedings of the 2015 IEEE 8th GCC Conference & Exhibition, Muscat, Oman, 1–4 February 2015; pp. 1–6. [Google Scholar]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology; Springer Science+Business Media: Berlin, Germany; New York, NY, USA, 1999; pp. 388–397. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Domingo-Ferrer, J.; Qin, B.; Hu, C. Distributed Aggregate Privacy-Preserving Authentication in VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 18, 516–526. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Solanas, A.; Domingo-Ferrer, J. A Scalable Robust Authentication Protocol for Secure Vehicular Communications. IEEE Trans. Veh. Technol. 2009, 59, 1606–1617. [Google Scholar] [CrossRef]
- Liu, J.; Li, J.; Zhang, L.; Dai, F.; Zhang, Y.; Meng, X.; Shen, J. Secure intelligent traffic light control using fog computing. Future Gener. Comput. Syst. 2018, 78, 817–824. [Google Scholar] [CrossRef]
- Riley, M.; Akkaya, K.; Fong, K. A survey of authentication schemes for vehicular ad hoc networks. Secur. Commun. Netw. 2011, 4, 1137–1152. [Google Scholar] [CrossRef]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 4 July 2018).
- SPAN: A Security Protocol Animator for AVISPA. Available online: http://www.avispa-project.org/ (accessed on 4 July 2018).
- Park, K.S.; Park, Y.H.; Park, Y.H.; Reddy, A.G.; Das, A.K. Provably secure and efficient authentication protocol for roaming service in global mobility networks. IEEE Access 2017, 5, 25110–25125. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Choo, K.R.; Kumar, N.; Park, Y.H. Efficient and secure time-key based single sign-on authentication for mobile devices. IEEE Access 2017, 5, 27707–27721. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Kumari, S.; Huang, X.; Wazid, M. Provably secure authenticated key agreement scheme for distributed mobile cloud computing services. Futuer Generat. Comput. Syst. 2017, 68, 74–88. [Google Scholar] [CrossRef]
- Park, K.S.; Park, Y.H.; Park, Y.H.; Das, A.K. 2PAKEP: Provably Secure and Efficient Two-Party Authenticated Key Exchange Protocol for Mobile Environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Park, Y.H.; Tanwar, S. Design of an Anonymity-Preserving Group Formation Based Authentication Protocol in Global Mobility Networks. IEEE Access 2018, 6, 20673–20693. [Google Scholar] [CrossRef]
- Von Oheimb, D. The high-level protocol specification language HLPSL developed in the EU project avispa. In Proceedings of the APPSEM 2005 Workshop, Tallinn, Finland, 13–15 September 2005; pp. 1–2. [Google Scholar]
- Basin, D.; Modersheim, S.; Vigano, L. OFMC: A symbolic model checker for security protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- Turuani, M. The CL-Atse porotocol analyser. In Proceedings of the International Coneference on Rewriting Techniques and Applications (RTA), Seattle, WA, USA, 12–14 August 2006; pp. 227–286. [Google Scholar]
- He, D.; Kumar, N.; Chen, J.; Lee, C.C.; Chilamkurti, N.; Yeo, S.S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 2015, 21, 49–60. [Google Scholar] [CrossRef]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal credential based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- FIPS PUB 180-4: Secure Hash Standard (SHS). Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.180-4.pdf (accessd on 23 July 2018).
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).