A Source Anonymity-Based Lightweight Secure AODV Protocol for Fog-Based MANET
Abstract
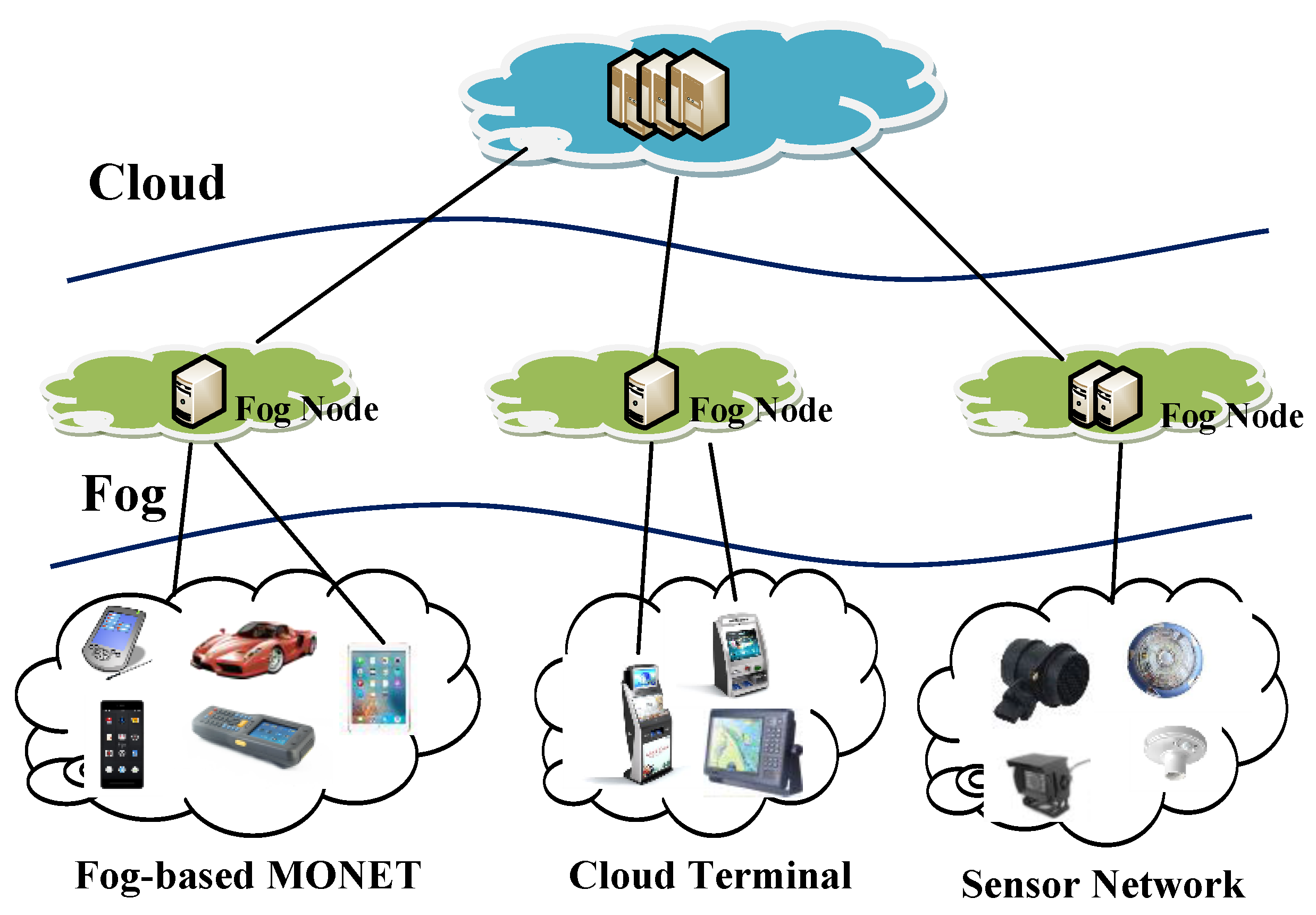
:1. Introduction
2. Related Works
2.1. Enhancing Security
2.2. Improving Transmission Performance
3. Preliminary Knowledge and Analysis
3.1. AODV
3.1.1. Route Discovery
3.1.2. Route Maintenance
3.1.3. Setting the Immediate Nodes
3.1.4. Management of the Routing Table
3.1.5. Local Connectivity Management
3.2. Secure AODV
3.2.1. SAODV Hash Chain
3.2.2. SAODV Digital Signature
3.3. Security Analysis
4. Source Anonymity-Based Lightweight Secure AODV Protocol
4.1. Source Anonymity-Based Lightweight Secure AODV Protocol
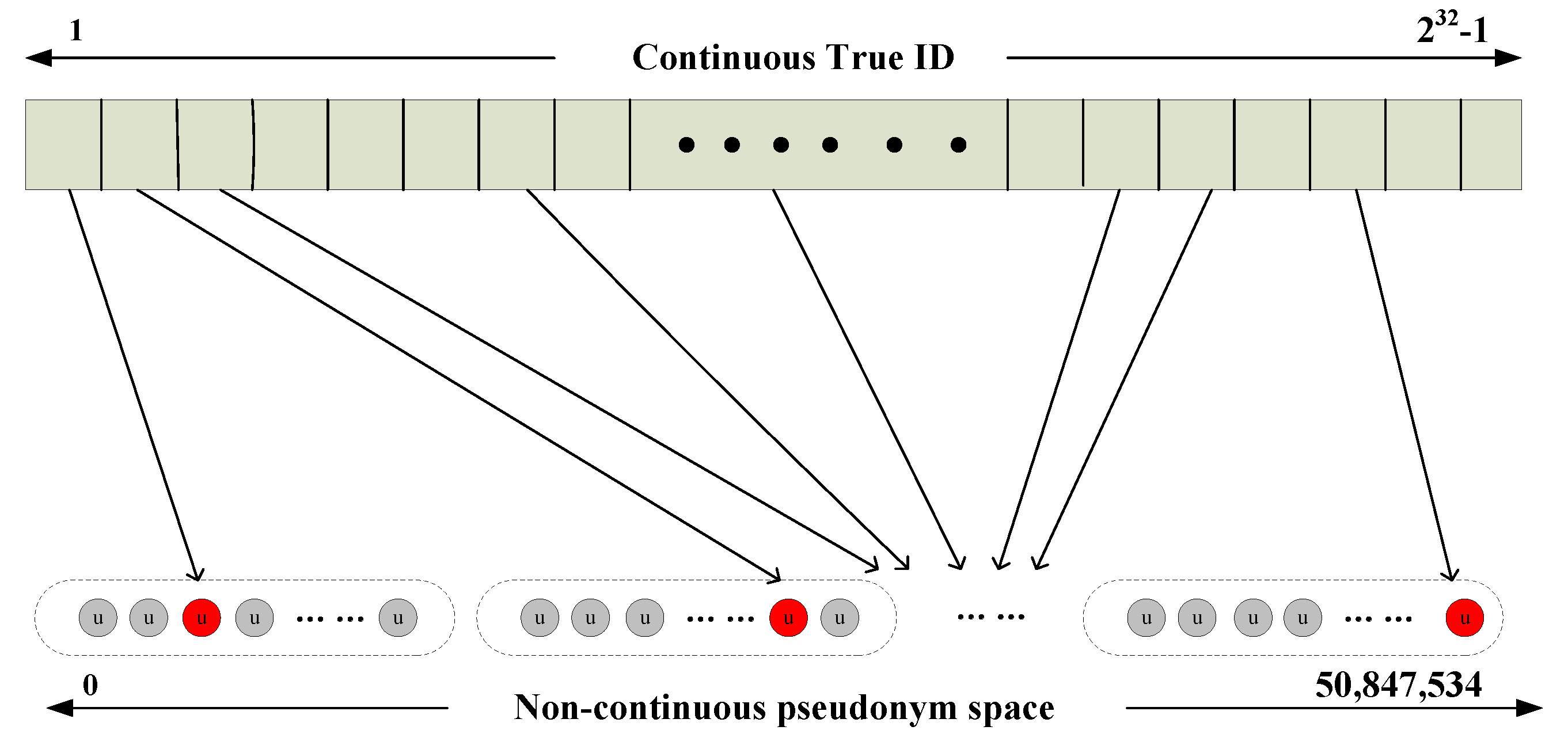
4.1.1. Source Anonymity Algorithm
| Algorithm 1. Prime queue generation algorithm. |
| 1: Set nodes’ maximum number (NMAX) in MANET, Initialize the prime queue Pi = 0, Set P1 = 2 |
| 2: for (Set counter A = 1; A <= NMAX; A = A + 1) |
| 3: for (Set counter B = 2; B <= [A square root] + 1; A = A + 1) |
| 4: if A/B = 0 then |
| 5: Exit this loop |
| 6: else |
| 7: PA = B |
| 8: end if |
| 9: end for |
| 10: end for |
4.1.2. Lightweight Tamper-Proof Scheme
4.1.3. Random Delayed Transmitting Scheme
| Algorithm 2. To shuffle an array a of n elements (indices 0…n−1). |
| 1: for i from n−1 down to 1 do |
| 2: j <- random integer with 0 <= j <= i |
| 3: exchange a[j] and a[i] |
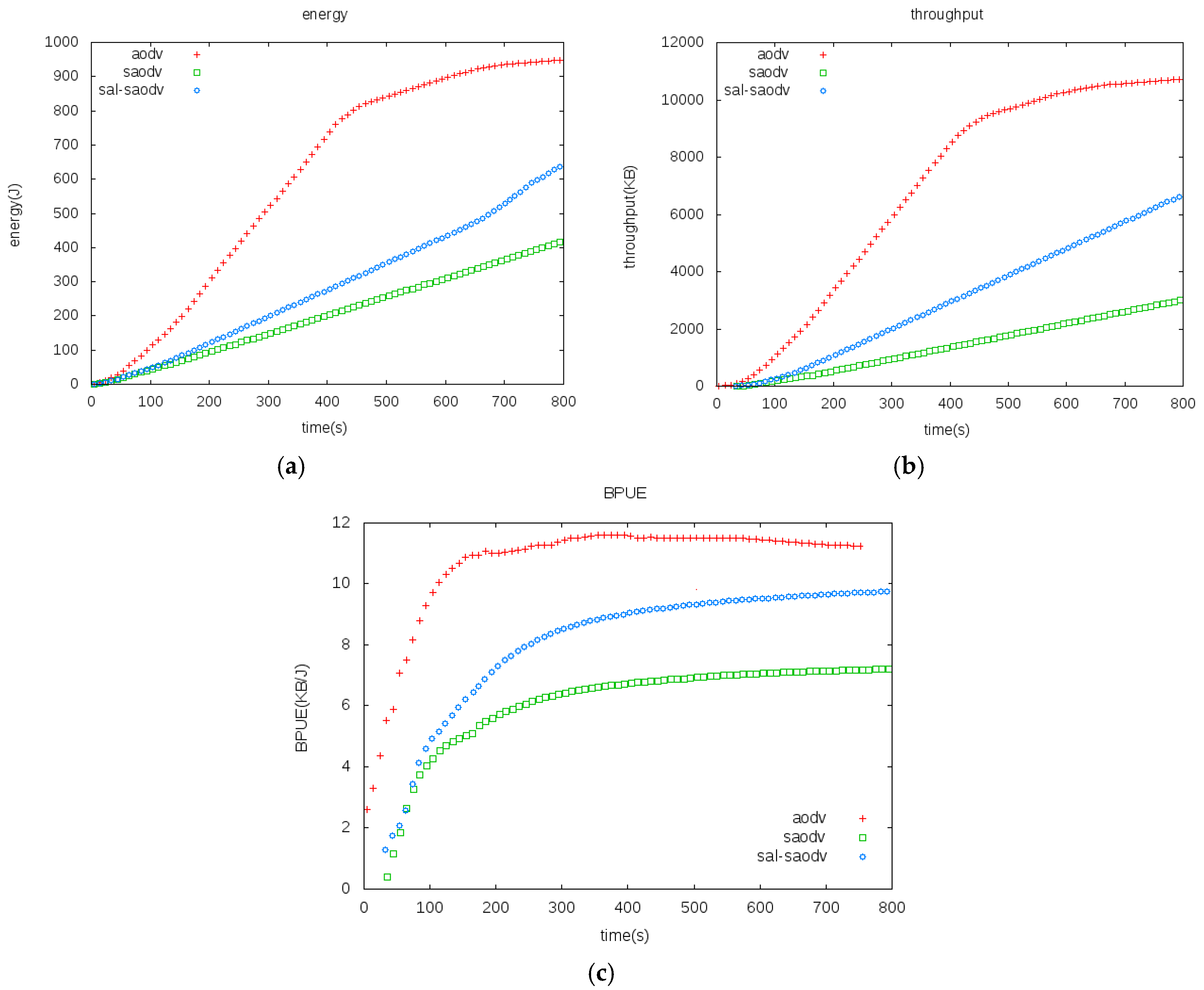
4.2. Simulation and Analysis
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Ahmed, A.; Bakar, K.A.; Channa, M.I.; Khan, A.W. Complex IoT Control System Modeling from Perspectives of Environment Perception and Information Security. Mob. Netw. Appl. 2016, 21, 272–285. [Google Scholar] [CrossRef]
- Zhang, P.; Lin, C.; Jiang, Y.; Fan, Y. A Lightweight Encryption Scheme for Network-Coded Mobile Ad Hoc Networks. IEEE Trans. Parallel Distrib. 2014, 25, 2211–2221. [Google Scholar] [CrossRef]
- Fang, W.D.; Zhang, W.X.; Yang, Y.; Yang, L.; Chen, W. A resilient trust management scheme for defending against reputation time-varying attacks based on BETA distribution. Sci. China Inf. Sci. 2017, 60, 040305. [Google Scholar] [CrossRef]
- Raja, G.; Baskaran, S.B.M.; Ghosal, D.; Padmanabhan, J. Reduced Overhead Frequent User Authentication in EAP-Dependent Broadband Wireless Networks. Mob. Netw. Appl. 2016, 21, 523–538. [Google Scholar] [CrossRef]
- Fang, W.; Shan, L.; Jia, G.; Ji, X.; Chen, S. A Low Complexity Secure Network Coding in Wireless Sensor Network. J. Internet Technol. 2016, 17, 905–913. [Google Scholar]
- Perkins, C.E.; Royer, E.M. Ad-Hoc On-Demand Distance Vector Routing. In Proceedings of the 2nd Workshop on Mobile Computing Systems and Applications (WMCSA), Washington, DC, USA, 25–26 February 1999. [Google Scholar]
- Ranjan, R.; Singh, N.K.; Singh, A. Security Issues of Black Hole Attacks in MANET. In Proceedings of the 2015 International Conference on Computing, Communication & Automation (ICCCA), Greater Noida, India, 15–16 May 2015. [Google Scholar]
- Choudhurya, D.R.; Raghab, L.; Marathe, N. Implementing and improving the performance of AODV by receive reply method and securing it from Black hole attack. Procedia Comput. Sci. 2015, 45, 564–570. [Google Scholar] [CrossRef]
- Choudhary, N.; Tharani, L. Preventing Black Hole Attack in AODV Using Timer-Based Detection Scheme. In Proceedings of the 2015 International Conference on Signal Processing and Communication Engineering Systems (SPACES), Guntur, India, 2–3 January 2015. [Google Scholar]
- Bhandare, A.S.; Patil, S.B. Securing MANET Against Co-Operative Black Hole Attack and Its Performance Analysis—A Case Study. In Proceedings of the 2015 International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 26–27 February 2015. [Google Scholar]
- Siddiqua, A.; Sridevi, K.; Mohammed, A.A.K. Preventing Black Hole Attacks in MANET Using Secure Knowledge Algorithm. In Proceedings of the 2015 International Conference on Signal Processing and Communication Engineering Systems (SPACES), Guntur, India, 2–3 January 2015. [Google Scholar]
- Jain, A.K.; Tokekar, V. Mitigating the Effects of BLACK Hole Attacks on AODV Routing Protocol in Mobile Ad-Hoc Networks. In Proceedings of the 2015 International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015. [Google Scholar]
- Hazra, S.; Setua, S.K. Sybil Attack Defending Trusted AODV in Ad-Hoc Network. In Proceedings of the 2012 2nd International Conference on Computer Science and Network Technology (ICCSNT), Changchun, China, 29–31 December 2012. [Google Scholar]
- Kasiran, Z.; Mohamad, J. Throughput Performance Analysis of the Wormhole and Sybil Attack in AODV. In Proceedings of the 2014 Fourth International Conference on Digital Information and Communication Technology and It’s Applications (DICTAP), Bangkok, Thailand, 6–8 May 2014. [Google Scholar]
- Patel, A.; Patel, N.; Patel, R. Defending Against Wormhole Attack in MANET. In Proceedings of the IEEE 2015 Fifth International Conference on Communication Systems and Network Technologies (CSNT), Gwalior, India, 4–6 April 2015. [Google Scholar]
- Ehsan, H.; Khan, F.A. Malicious AODV: Implementation and Analysis of Routing Attacks in MANET. In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Liverpool, UK, 25–27 June 2012. [Google Scholar]
- Harwahyu, R.; Simaremare, H.; Sari, R.F.; Lorenz, P. Performance Estimation of AODV Variant with Trust Scheme. In Proceedings of the 2014 International Conference on Communications (ICC), Melmaruvathur, India, 3–5 April 2014. [Google Scholar]
- Chaubey, N.; Aggarwal, A.; Gandhi, S.; Jani, K.A. Effect of Pause Time on AODV and TSDRP Routing Protocols under Black Hole Attack and DoS Attacks in MANET. In Proceedings of the 2015 2nd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 11–13 March 2015. [Google Scholar]
- Su, M.Y.; Yang, C.W. A Resilient Routing Approach for Mobile Ad Hoc Networks. In Proceedings of the 2015 International Conference on High Performance Computing & Simulation (HPCS), Amsterdam, The Netherlands, 20–24 July 2015. [Google Scholar]
- Liu, S.; Yang, Y.; Wang, W. Research of AODV Routing Protocol for Ad Hoc Networks1. AASRI Procedia 2013, 5, 21–31. [Google Scholar] [CrossRef]
- Hanji, B.R.; Shettar, R. Improved AODV with Restricted Route Discovery Area. In Proceedings of the 2015 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 8–10 January 2015. [Google Scholar]
- Apidet, B.; Wiklom, T.; Chusak, L. Energy Consumption and Control Response Evaluations of AODV Routing in WSANs for Building-Temperature Control. Sensors 2013, 13, 8303–8330. [Google Scholar] [CrossRef]
- Carolina, D.-V.-S.; Carlos, M.-P.; Aldo, O.-L.; Mauricio, L.; Giselle, M.G.-T.; Oscar, O. On the MAC/Network/Energy Performance Evaluation of Wireless Sensor Networks: Contrasting MPH, AODV, DSR and ZTR Routing Protocols. Sensors 2014, 14, 22811–22847. [Google Scholar] [CrossRef]
- Bala, R.; Krishna, C.R. Scenario Based Performance Analysis of AODV and GPSR Routing Protocols in a VANET. In Proceedings of the 2015 IEEE International Conference on Computational Intelligence & Communication Technology (CICT), Ghaziabad, India, 13–14 February 2015. [Google Scholar]
- Hamidian, A. A Study of Internet Connectivity for Mobile Ad Hoc Networks in NS2. Master’s Thesis, Lund Institute of Technology, Lund, Sweden, January 2003. [Google Scholar]
- Wantoro, J.; Mustika, I.W. M-AODV+: An Extension of AODV+ Routing Protocol for Supporting Vehicle-to-Vehicle Communication in Vehicular Ad Hoc Networks. In Proceedings of the 2014 IEEE International Conference on Communication, Networks and Satellite (COMNETSAT), DKI Jakarta, Indonesia, 4–5 November 2014. [Google Scholar]
- Arya, V.; Gandhi, C. NDj—AODV: Node Disjoint Multipath Routing in Mobile Ad Hoc Networks based on AODV Protocol. In Proceedings of the 2014 Seventh International Conference on Contemporary Computing (IC3), Noida, India, 7–9 August 2014. [Google Scholar]
- Sharma, L.; Dimri, P. An improved AODV with QoS support in mobile ad-hoc network. In Proceedings of the 2015 2nd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 11–13 March 2015. [Google Scholar]
- Zapata, M.G. Secure Ad Hoc On-Demand Distance Vector (SAODV) Routing. Available online: http://ietfreport.isoc.org/idref/draft-guerrero-manet-saodv/ (accessed 7 September 2006).
- Fang, W.; Shi, Z.; Shan, L.; Li, F.; Xiong, Y. A Multi-Parameter Joint Evaluation Scheme in Energy Consumption for Wireless Sensor Networks. Chin. High Technol. Lett. 2015, 34, 753–759. [Google Scholar]
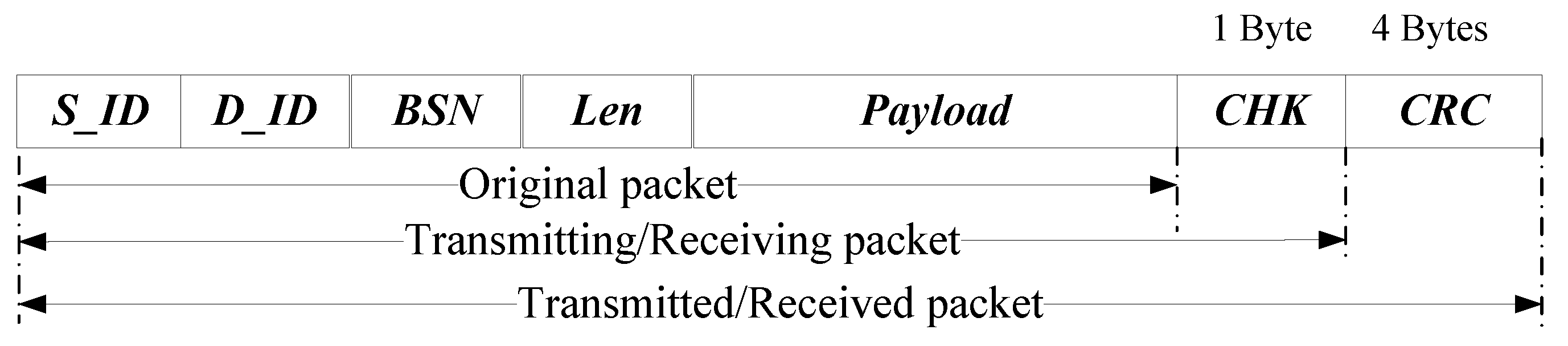

| Notation | Definition |
|---|---|
| S_ID | Source node ID |
| D_ID | Destination node ID |
| BSN | Block sequence number |
| Len | Length of original packet |
| Payload | Payload of packet |
| CHK[BSN] | Checknum for CRC |
| CRC[BSN] | Cyclic Redundancy Check for original packet |
| P_buffer | Transmitting/Receiving packets buffer |
| C_buffer | Transmitting/Receiving CRCs buffer |
| Tx_packet | Transmitted packet (involved: packet, CHK and CRC) |
| Rx_packet | Received packet (involved: packet, CHK and CRC) |
| Parameter | Value |
|---|---|
| Number of nodes | 50 |
| Initial energy of nodes (J) | 2 |
| Simulation area (m2) | 1000 × 1000 |
| Node movement speed (m/s) | 0 |
| Simulation time (s) | 800 |
| Transmission range(m) | 200 |
| Antenna Type | Omni antenna |
| Mobility Model | Random Way Point |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fang, W.; Zhang, W.; Xiao, J.; Yang, Y.; Chen, W. A Source Anonymity-Based Lightweight Secure AODV Protocol for Fog-Based MANET. Sensors 2017, 17, 1421. https://doi.org/10.3390/s17061421
Fang W, Zhang W, Xiao J, Yang Y, Chen W. A Source Anonymity-Based Lightweight Secure AODV Protocol for Fog-Based MANET. Sensors. 2017; 17(6):1421. https://doi.org/10.3390/s17061421
Chicago/Turabian StyleFang, Weidong, Wuxiong Zhang, Jinchao Xiao, Yang Yang, and Wei Chen. 2017. "A Source Anonymity-Based Lightweight Secure AODV Protocol for Fog-Based MANET" Sensors 17, no. 6: 1421. https://doi.org/10.3390/s17061421
APA StyleFang, W., Zhang, W., Xiao, J., Yang, Y., & Chen, W. (2017). A Source Anonymity-Based Lightweight Secure AODV Protocol for Fog-Based MANET. Sensors, 17(6), 1421. https://doi.org/10.3390/s17061421






