A Distributed Transmission Rate Adjustment Algorithm in Heterogeneous CSMA/CA Networks
Abstract
:1. Introduction
1.1. Motivation
1.2. Related Works and Contributions
- A mathematical characterization of heterogeneous traffics is provided, which enables each node to use CCA information to accurately determine the aggregate transmission rate of all other nodes. Compared with previous methods [8,22,23] that can only be applied for characterization and estimation in homogeneous networks, the proposed algorithm does not assume homogeneity of the network nor prior knowledge on nodes coexisting in the networks. It can thus be used for estimating both homogeneous and heterogeneous traffics;
- Based on the above mathematical framework, a distributed algorithm is proposed to predict the packet success rate and tune the transmission rate to meet the throughput demand. The algorithm is accurate with only an average error of 0.43% for homogeneous networks and 0.524% for heterogeneous networks.
- The algorithm is fully distributed and does not require any central coordination. Moreover, a change detection mechanism is also developed to allow each node to react promptly to on-going traffic changes and re-adjust its transmission rate to meet the throughput demand.
2. Preliminaries and Problem Formulation
2.1. IEEE 802.15.4 CSMA/CA Protocol
2.2. Problem Formulation
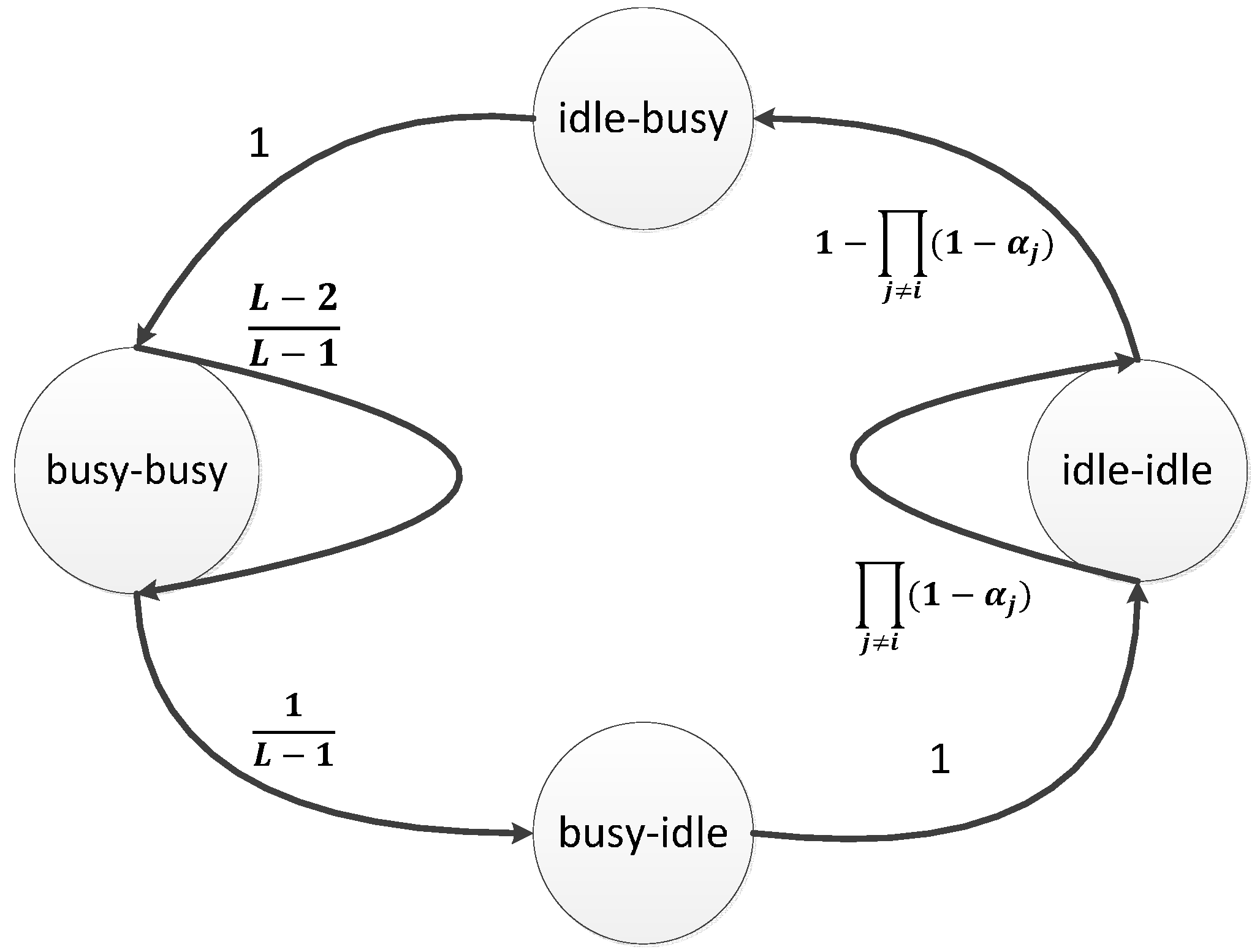
3. Distributed Transmission Rate Adjustment
4. Change Detection Mechanism
4.1. Detectability Analysis
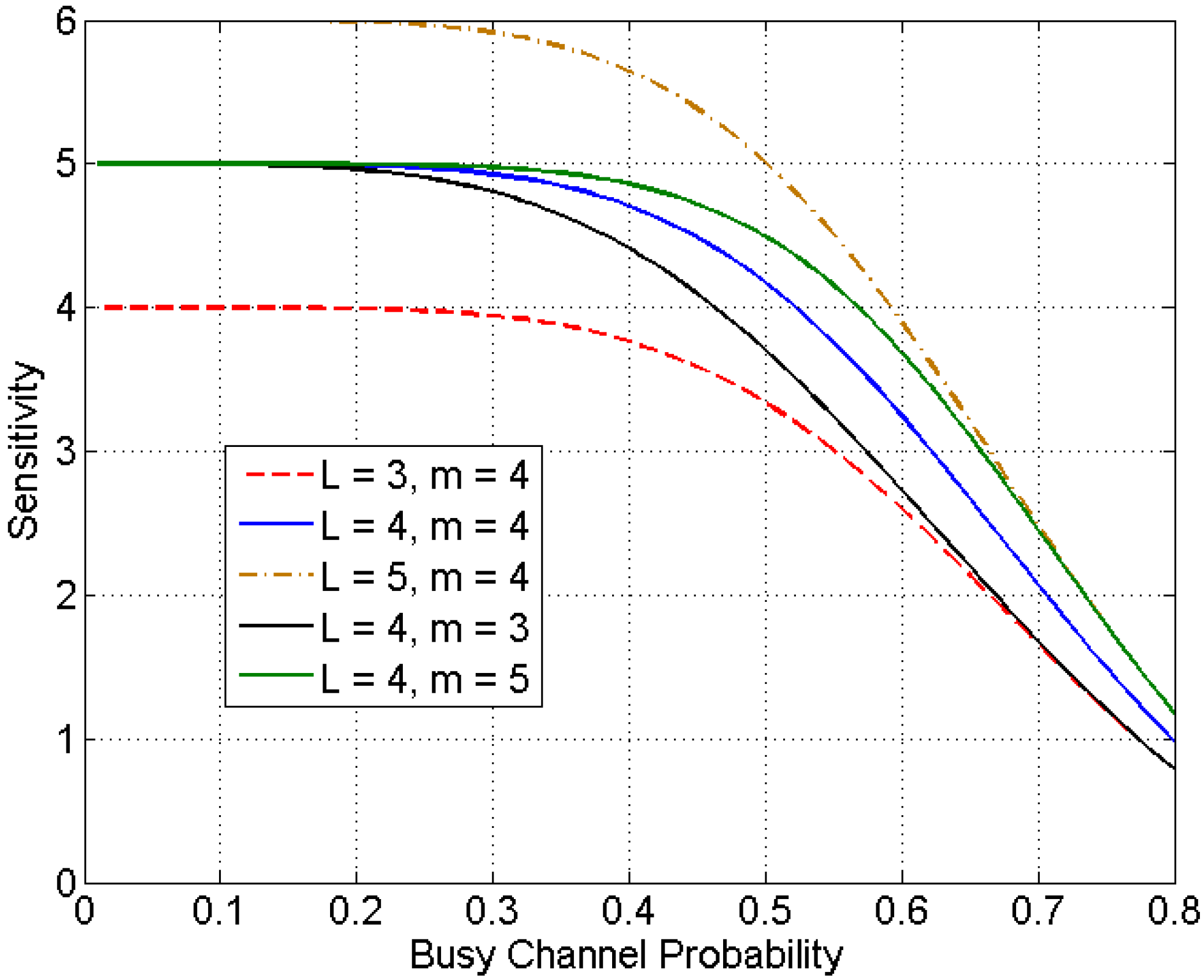
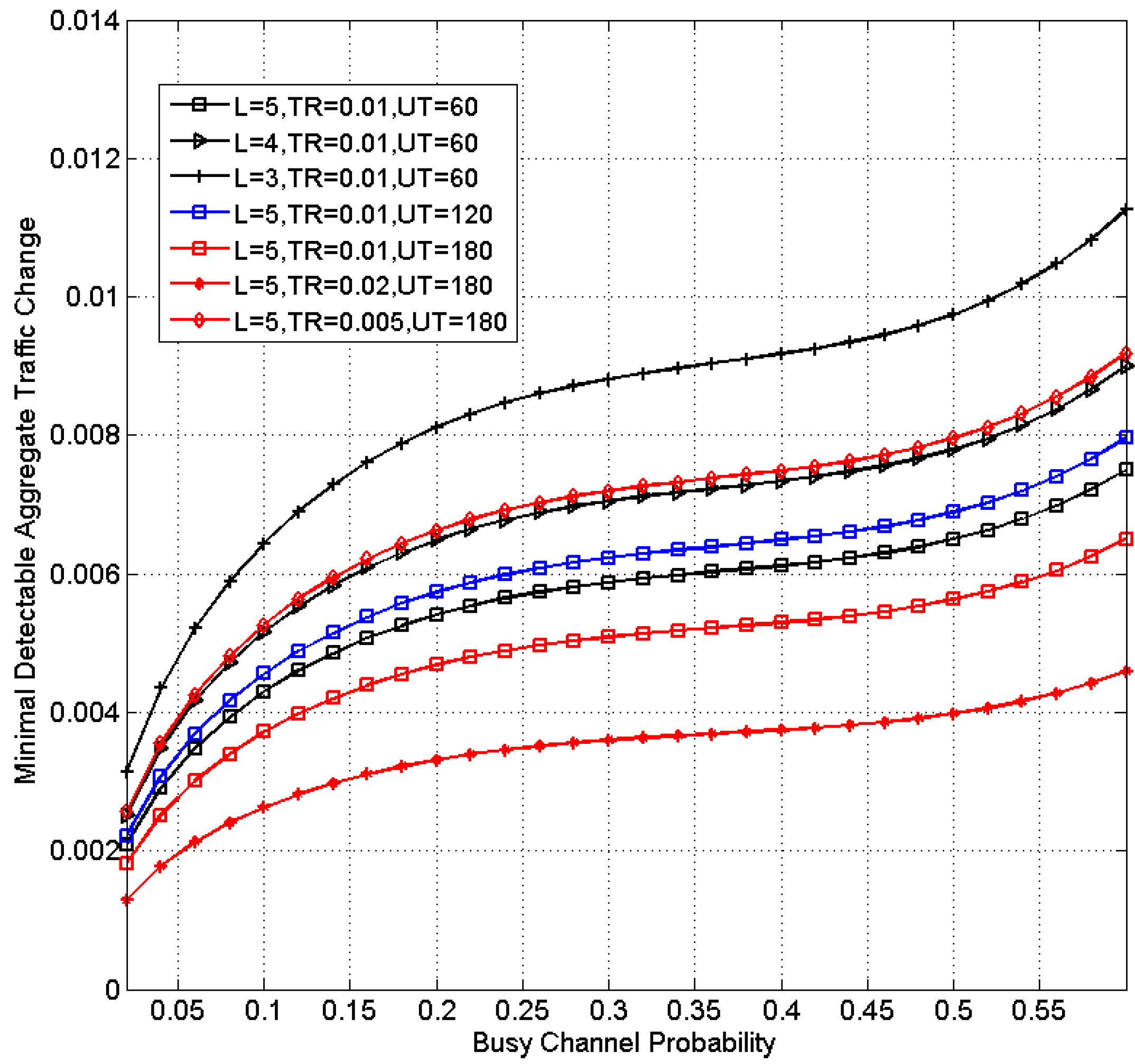
4.2. Change Detection
| Algorithm 1 Pseudo-code of the proposed algorithm |
| c = 0; |
| for k = 1; k < I; k++ |
| while () |
| Perform data transmission and record |
| end |
| if (k == 1) |
| RateUpdate() |
| else if () |
| // Do not change the transmission rate |
| else if |
| Obtain new nodes’ traffic: |
| RateUpdate() |
| else if |
| Obtain the current traffic: |
| RateUpdate() |
| end |
| c = 0 |
| end |
| function RateUpdate(Traffic) |
| (using Equation (11)) |
| end |
5. Experimental Results

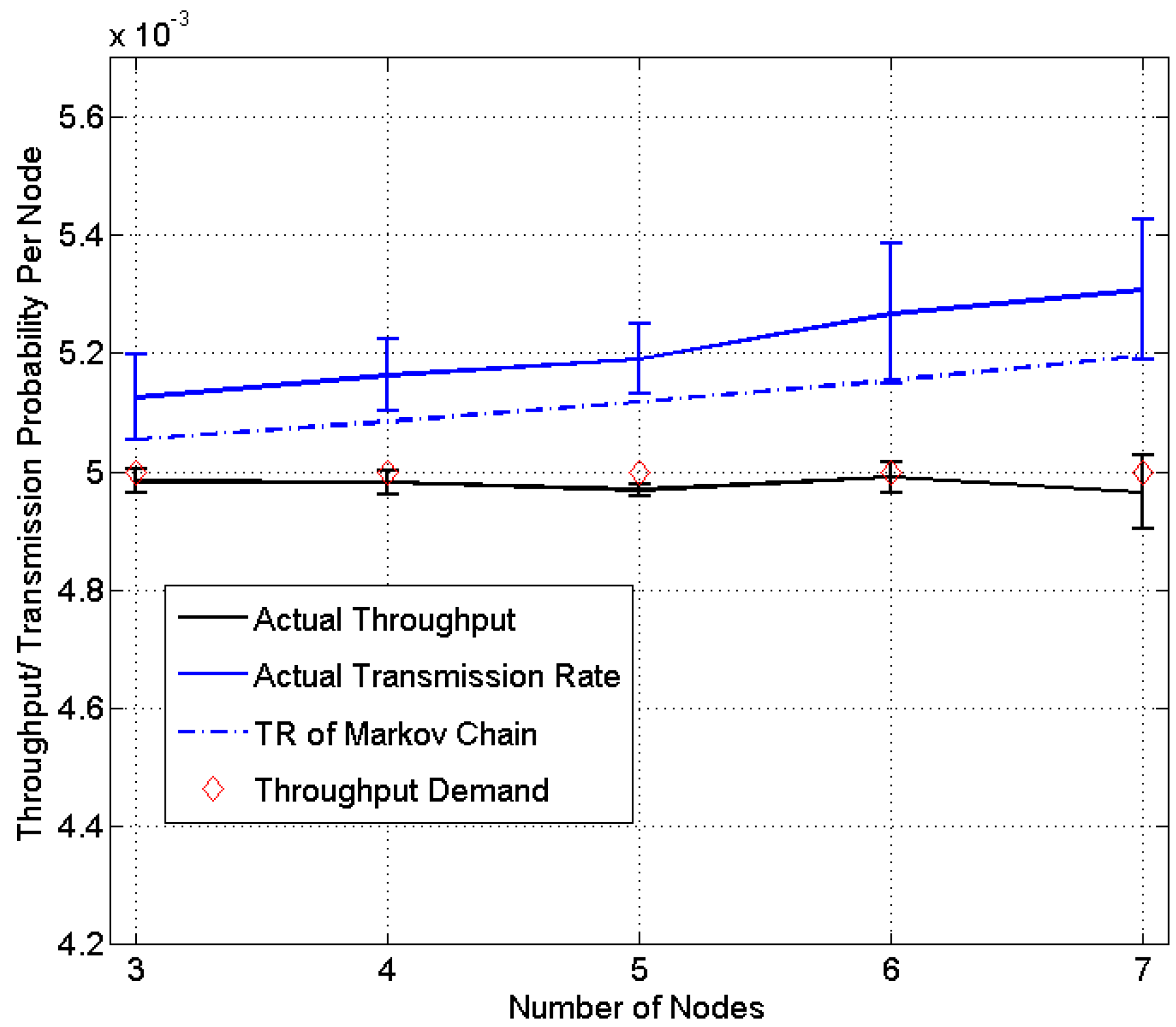
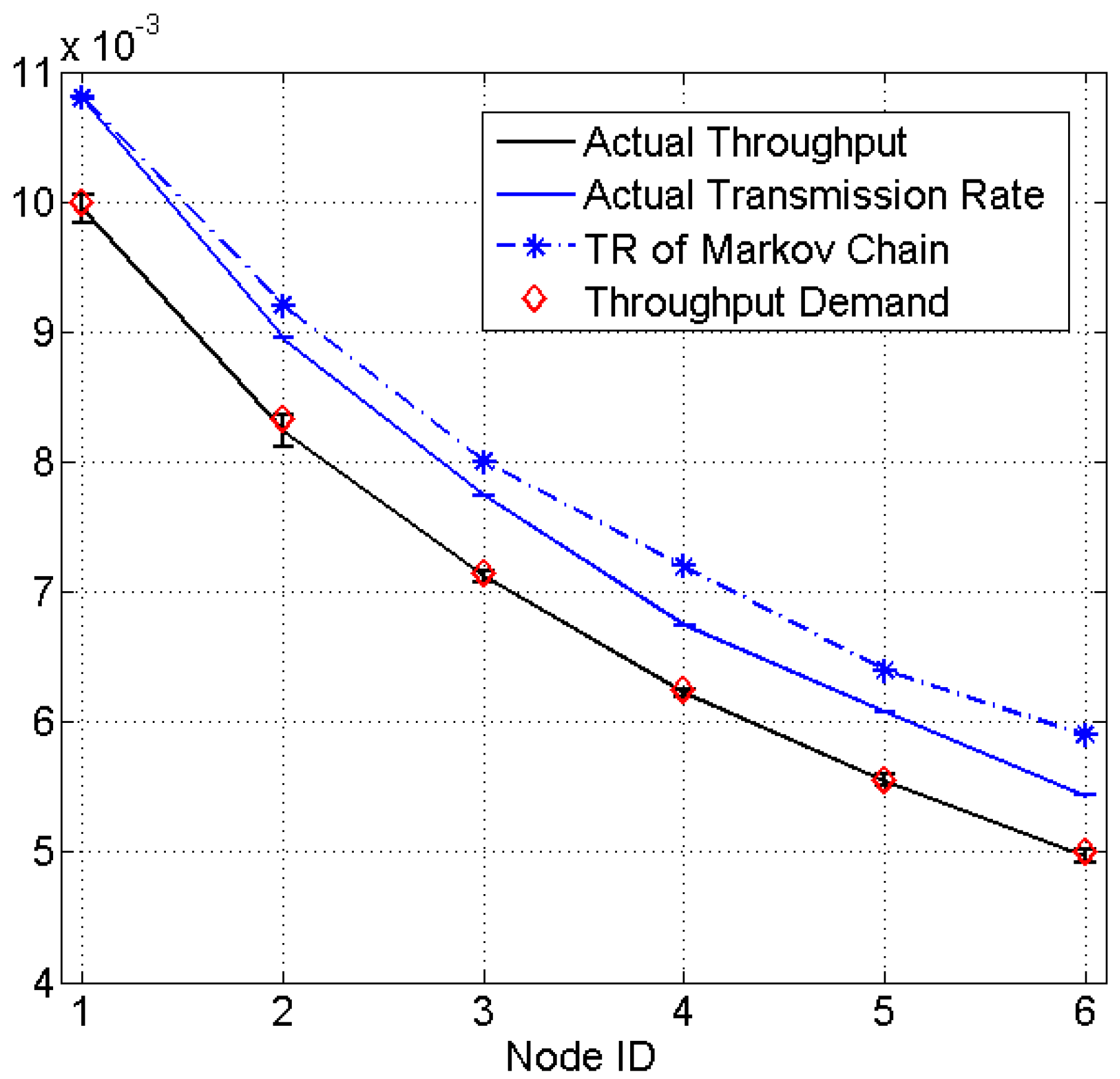
| Method | Proposed Method | Markov Chain-Based Methods | |
|---|---|---|---|
| Errors | Homogeneous | 0.43% | 3.2% |
| Heterogeneous | 0.524% | 4.7% | |
| Complexity | easy to implement; able to be stored in a look-up table | computationally intensive; requires solving of multi-dimension Markov chain | |
| Required Information | local information only, e.g., channel sensing result | needs network-wide information, e.g., the number of active nodes | |
| Flexibility | able to adapt traffic changes | requires the traffics to be constant | |
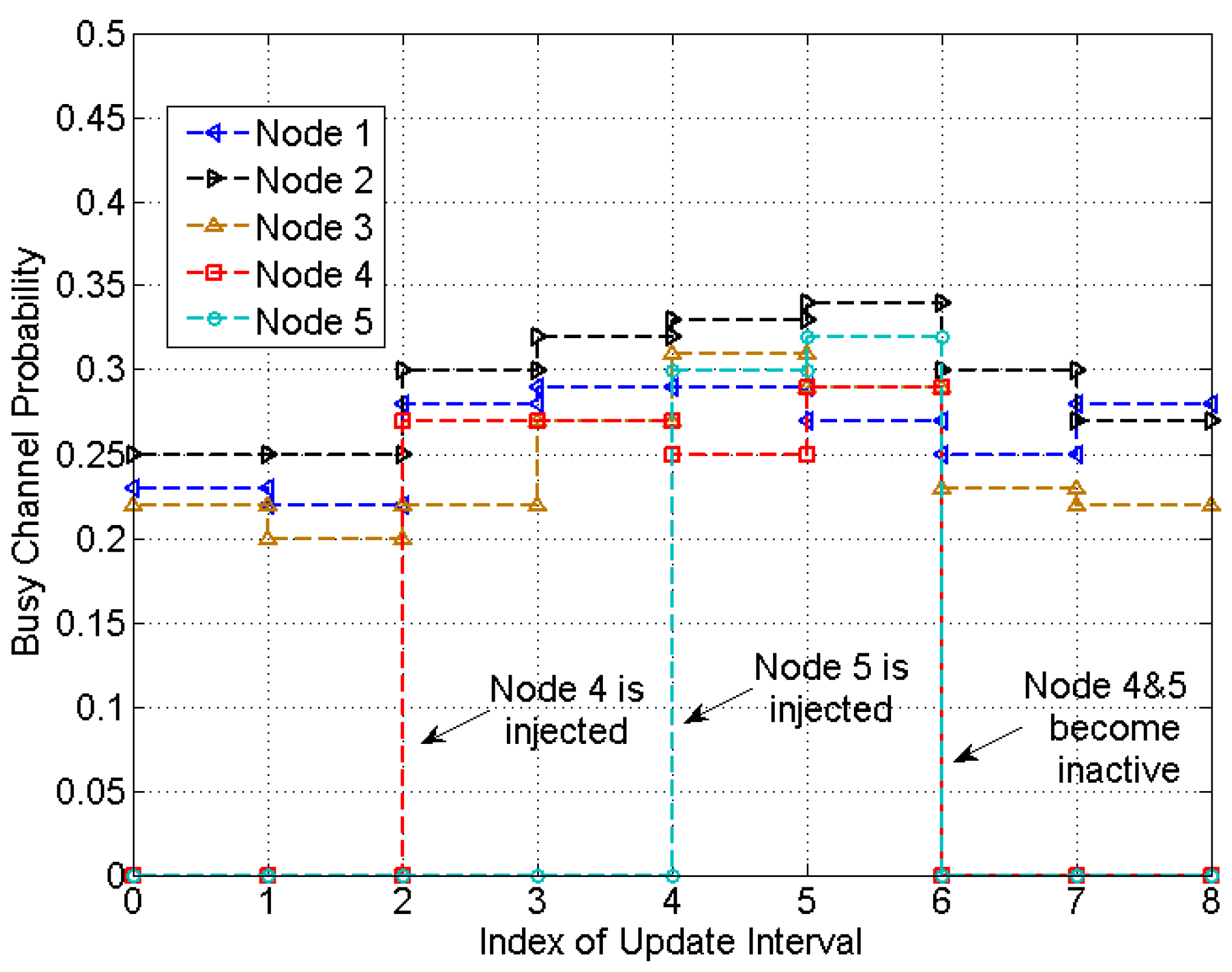
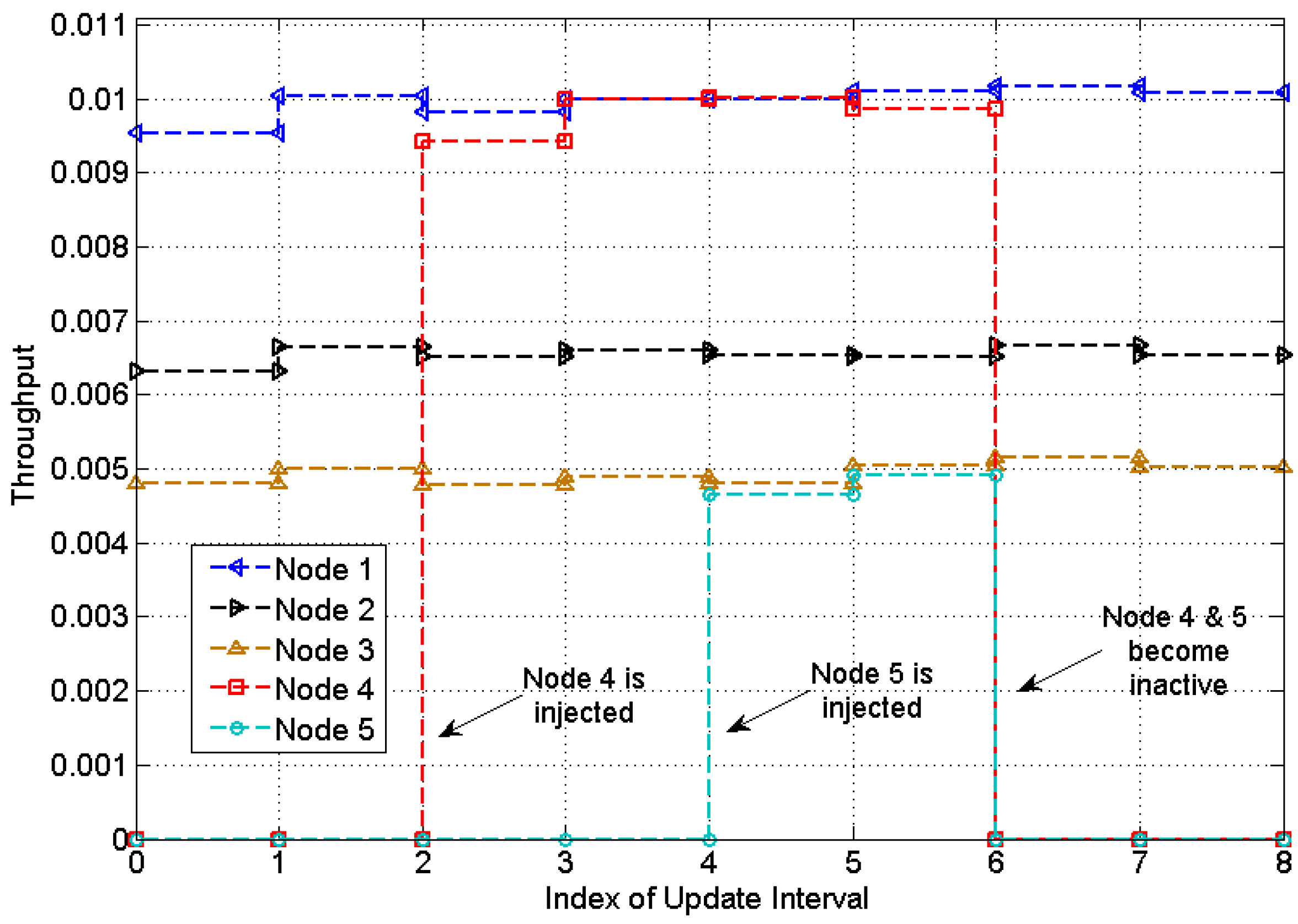
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Khanafer, M.; Guennoun, M.; Mouftah, H. A Survey of Beacon-Enabled IEEE 802.15.4 MAC Protocols in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2014, 16, 856–876. [Google Scholar] [CrossRef]
- IEEE 802.15.4 Standard: Wireless Medium Access Control and Physical Layer Specifications for Low-Rate Wireless Personal Area Networks, IEEE, 2006. Available online: http://www.ieee802.org/15/pub/TG4.html (accessed on 25 March 2015).
- Xie, S.; Lee, G.X.; Low, K.-S.; Gunawan, E. Wireless Sensor Network for Satellite Applications: A Survey and Case Study. Unmanned Syst. 2014, 2, 261–277. [Google Scholar] [CrossRef]
- Shrestha, B.; Hossain, E.; Camorlinga, S. IEEE 802.15.4 MAC with GTS Transmission for Heterogeneous Devices with Application to Wheelchair Body-Area Sensor Networks. IEEE Trans. Inf. Technol. B 2011, 15, 767–777. [Google Scholar] [CrossRef]
- Ashrafuzzaman, K.; Kwak, K.S. On the Performance Analysis of the Contention Access Period of IEEE 802.15.4 MAC. IEEE Commun. Lett. 2011, 15, 986–988. [Google Scholar] [CrossRef]
- Park, P.; di Marco, P.; Soldati, P.; Fischione, C.; Johansson, K.H. A Generalized Markov Chain Model for Effective Analysis of Slotted IEEE 802.15.4. In Proceedings of the 2009 IEEE 6th International Conference on Mobile Adhoc and Sensor Systems (MASS 2009), Macau, China, 12–15 October 2009; pp. 285–294.
- Shu, F.; Sakurai, T.; Zukerman, M.; Vu, H.L. Packet loss analysis of the IEEE 802.15.4 MAC without acknowledgments. IEEE Commun. Lett. 2007, 11, 79–81. [Google Scholar] [CrossRef]
- Park, P.; di Marco, P.; Fischione, C.; Johansson, K.H. Modeling and Optimization of the IEEE 802.15.4 Protocol for Reliable and Timely Communications. IEEE Trans. Parall. Distr. 2013, 24, 550–564. [Google Scholar] [CrossRef]
- Estrada, T.; Antsaklis, P.J. Stability of Discrete-Time Plants using Model-Based Control with Intermittent Feedback. In Proceedings of the 2008 Mediterranean Conference on Control Automation, Ajaccio, France, 25–27 June 2008; pp. 1448–1454.
- Garcia, E.; Antsaklis, P.J. Model-Based Event-Triggered Control with Time-Varying Network Delays. In Proceedings of the 2011 50th IEEE Conference on Decision and Control and European Control Conference (CDC-ECC), Orlando, FL, USA, 12–15 December 2011; pp. 1650–1655.
- Park, P.; Ergen, S.C.; Fischione, C.; Sangiovanni-Vincentelli, A. Duty-Cycle Optimization for IEEE 802.15.4 Wireless Sensor Networks. ACM Trans. Sensor Netw. 2013, 10. [Google Scholar] [CrossRef]
- Bellalta, B.; Zocca, A.; Cano, C.; Checco, A.; Barcelo, J.; Vinel, A. Throughput Analysis in CSMA/CA Networks Using Continuous Time Markov Networks: A Tutorial. In Wireless Networking for Moving Objects; Ganchev, I., Curado, M., Kassler, A., Eds.; Springer International Publishing: New York, NY, USA, 2014; pp. 115–133. [Google Scholar]
- Hester, L.; Huang, Y.; Kyperountas, S.; Callaway, E.H.; Gorday, P.; Bourgeois, M. IEEE 802.15.4: Exploring features of the standard for low-rate WPANs. In Proceedings of the 8th World Multi-Conference on Systemics, Cybernetics and Informatics, Orlando, FL, USA, 18–21 July 2004; Vol XIII, pp. 184–189.
- Onat, A.; Naskali, T.; Parlakay, E.; Mutluer, O. Control over Imperfect Networks: Model-Based Predictive Networked Control Systems. IEEE Trans. Ind. Electron. 2011, 58, 905–913. [Google Scholar] [CrossRef]
- Tiberi, U.; Fischione, C.; Johansson, K.H.; di Benedetto, M.D. Adaptive Self-triggered Control over IEEE 802.15.4 Networks. In Proceedings of the 49th IEEE Conference on Decision and Control (CDC), Atlanta, GA, USA, 15–17 December 2010; pp. 2099–2104.
- Xia, F.; Ma, L.; Peng, C.; Sun, Y.; Dong, J. Cross-layer adaptive feedback scheduling of wireless control systems. Sensors 2008, 8, 4265–4281. [Google Scholar] [CrossRef]
- Ha, J.Y.; Kim, T.H.; Park, H.S.; Choi, S.; Kwon, W.H. An enhanced CSMA-CA algorithm for IEEE 802.15.4 LR-WPANs. IEEE Commun. Lett. 2007, 11, 461–463. [Google Scholar] [CrossRef]
- Zhao, X.D.; Zhang, W.; Niu, W.S.; Zhang, Y.D.; Zhao, L.Q. Power and Bandwidth Efficiency of IEEE 802.15.4 Wireless Sensor Networks. Ubiquitous Intell. Comput. 2010, 6406, 243–251. [Google Scholar]
- Lee, B.H.; Lai, R.L.; Wu, H.K.; Wong, C.M. Study on Additional Carrier Sensing for IEEE 802.15.4 Wireless Sensor Networks. Sensors 2010, 10, 6275–6289. [Google Scholar] [CrossRef] [PubMed]
- Mounib, K.; Mouhcine, G.; Hussein, T.M. Priority-Based CCA Periods for Efficient and Reliable Communications in Wireless Sensor Networks. Wirel. Sensor Netw. 2012, 4, 45. [Google Scholar] [CrossRef]
- Mahmood, D.; Khan, Z.A.; Qasim, U.; Naru, M.U.; Mukhtar, S.; Akram, M.I.; Javaid, N. Analyzing and Evaluating Contention Access Period of Slotted CSMA/CA for IEEE802.15.4. Proc. Comput. Sci. 2014, 34, 204–211. [Google Scholar] [CrossRef]
- Bianchi, G.; Tinnirello, I. Kalman filter estimation of the number of competing terminals in an IEEE 802.11 network. In Proceedings of the IEEE Infocom 2003: The Conference on Computer Communications, San Francisco, CA, USA, 1–3 April 2003; Vols 1–3, pp. 844–852.
- Toledo, A.L.; Vercauteren, T.; Wang, X.D. Adaptive optimization of IEEE 802.11 DCF based on Bayesian estimation of the number of competing terminals. IEEE Trans. Mobile Comput. 2006, 5, 1283–1296. [Google Scholar] [CrossRef]
- Lee, H.; Kim, A.; Lee, K.; Shin, Y. A Improved Channel Access Algorithm for IEEE 802.15. 4 WPAN. Int. J. Secur. Appl. 2012, 6, 281. [Google Scholar]
- Collotta, M.; Gentile, L.; Pau, G.; Scata, G. Flexible IEEE 802.15.4 deadline-aware scheduling for DPCSs using priority-based CSMA-CA. Comput. Ind. 2014, 65, 1181–1192. [Google Scholar] [CrossRef]
- Luo, H.C.; Wu, E.H.K.; Chen, G.H. A Transmission Power/Rate Control Scheme in CSMA/CA-Based Wireless Ad Hoc Networks. IEEE Trans. Veh. Technol. 2013, 62, 427–431. [Google Scholar] [CrossRef]
- Gutierrez, J.A.; Callaway, E.H.; Barrett, R.L. Low-Rate Wireless Personal Area networks: Enabling Wireless Sensors with IEEE 802.15. 4; IEEE Standards Association: Piscataway, NJ, USA, 2004. [Google Scholar]
- Tang, L.; Wang, K.-C.; Huang, Y.; Gu, F. Channel characterization and link quality assessment of ieee 802.15. 4-compliant radio for factory environments. IEEE Trans. Ind. Inf. 2007, 3, 99–110. [Google Scholar] [CrossRef]
- Tiberi, U.; Fischione, C.; Johansson, K.H.; Di Benedetto, M.D. Energy-efficient sampling of networked control systems over IEEE 802.15.4 wireless networks. Automatica 2013, 49, 712–724. [Google Scholar] [CrossRef]
- Baillieul, J. Feedback designs in information-based control. Stochast. Theory Control Proc. 2002, 280, 35–57. [Google Scholar]
- Montestruque, L.A.; Antsaklis, P. Stability of model-based networked control systems with time-varying transmission times. IEEE Trans. Autom. Control 2004, 49, 1562–1572. [Google Scholar] [CrossRef]
- Minero, P.; Franceschetti, M.; Dey, S.; Nair, G.N. Data rate theorem for stabilization over time-varying feedback channels. IEEE Trans. Autom. Control 2009, 54, 243. [Google Scholar] [CrossRef]
- Park, P.; Araújo, J.; Johansson, K.H. Wireless Networked Control System Co-Design. In Proceedings of the 2011 IEEE International Conference on Networking, Sensing and Control (ICNSC), Delft, The Netherlands, 11–13 April 2011; pp. 486–491.
- Park, P.; Fischione, C.; Johansson, K.H. Modeling and Stability Analysis of Hybrid Multiple Access in the IEEE 802.15.4 Protocol. ACM Trans. Sensor Netw. 2013, 9. [Google Scholar] [CrossRef]
- Kreyszig, E. Advanced Engineering Mathematics; John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Datasheet, T. Available online: http://www.willow.co.uk/TelosB_Datasheet.pdf (accessed on 25 March 2015).
- Levis, P.; Madden, S.; Polastre, J.; Szewczyk, R.; Whitehouse, K.; Woo, A.; Gay, D.; Hill, J.; Welsh, M.; Brewer, E. TinyOS: An operating system for sensor networks. In Ambient Intelligence; Springer: Berlin/Heidelberg, Germany, 2005; pp. 115–148. [Google Scholar]
- Gay, D.; Levis, P.; von Behren, R.; Welsh, M.; Brewer, E.; Culler, D. The nesC language: A holistic approach to networked embedded systems. ACM Sigplan. Not. 2003, 38, 1–11. [Google Scholar] [CrossRef]
- TKN15. 4: An IEEE 802.15.4 MAC Implementation for TinyOS. Available online: http://www.tkn.tu-berlin.de/fileadmin/fg112/Papers/TKN154.pdf (accessed on 25 March 2015).
- Martins, N.C.; Dahleh, M.A.; Elia, N. Feedback stabilization of uncertain systems in the presence of a direct link. IEEE Trans. Autom. Control 2006, 51, 438–447. [Google Scholar] [CrossRef]
- Kim, T.H.; Ni, J.; Srikant, R.; Vaidya, N.H. Throughput-optimal CSMA with imperfect carrier sensing. IEEE/ACM Trans. Netw. (TON) 2013, 21, 1636–1650. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, S.; Low, K.S.; Gunawan, E. A Distributed Transmission Rate Adjustment Algorithm in Heterogeneous CSMA/CA Networks. Sensors 2015, 15, 7434-7453. https://doi.org/10.3390/s150407434
Xie S, Low KS, Gunawan E. A Distributed Transmission Rate Adjustment Algorithm in Heterogeneous CSMA/CA Networks. Sensors. 2015; 15(4):7434-7453. https://doi.org/10.3390/s150407434
Chicago/Turabian StyleXie, Shuanglong, Kay Soon Low, and Erry Gunawan. 2015. "A Distributed Transmission Rate Adjustment Algorithm in Heterogeneous CSMA/CA Networks" Sensors 15, no. 4: 7434-7453. https://doi.org/10.3390/s150407434
APA StyleXie, S., Low, K. S., & Gunawan, E. (2015). A Distributed Transmission Rate Adjustment Algorithm in Heterogeneous CSMA/CA Networks. Sensors, 15(4), 7434-7453. https://doi.org/10.3390/s150407434





