Fortified Anonymous Communication Protocol for Location Privacy in WSN: A Modular Approach
Abstract
:1. Introduction
2. Problem Statement
3. Background and Literature Survey
| No. | Scheme | View of the Adversary | Anonymity Technique | Passive Attacks | Active Attacks |
|---|---|---|---|---|---|
| 1 | SAS & CAS [20] | Global | Pseudonyms | Eavesdropping, SN compromise, limited traffic analysis | - |
| 2 | HIR & RHIR [21] | Global | Pseudonyms | Eavesdropping, SN compromise | - |
| 3 | APR [22] | Local | Pseudonyms | Eavesdropping, hops-tracing | SN compromise |
| 4 | DCARPS & Global DCARPS [6] | Global | Pseudonyms | Eavesdropping, hops-tracing | - |
| 5 | ACS [23] | Local | Pseudonyms | Rate monitoring, time correlation, identity analysis, hops-trace | - |
| 6 | MQA [24] | Global | Aggregation | Eavesdropping, hops-tracing | Packet injection |
| 7 | PhID [4,25] | Local | Pseudonyms | Eavesdropping, traffic analysis | - |
| 8 | EAC [16] | Global | Pseudonyms | Eavesdropping, traffic analysis | DoS, SN compromise, Traffic injection |
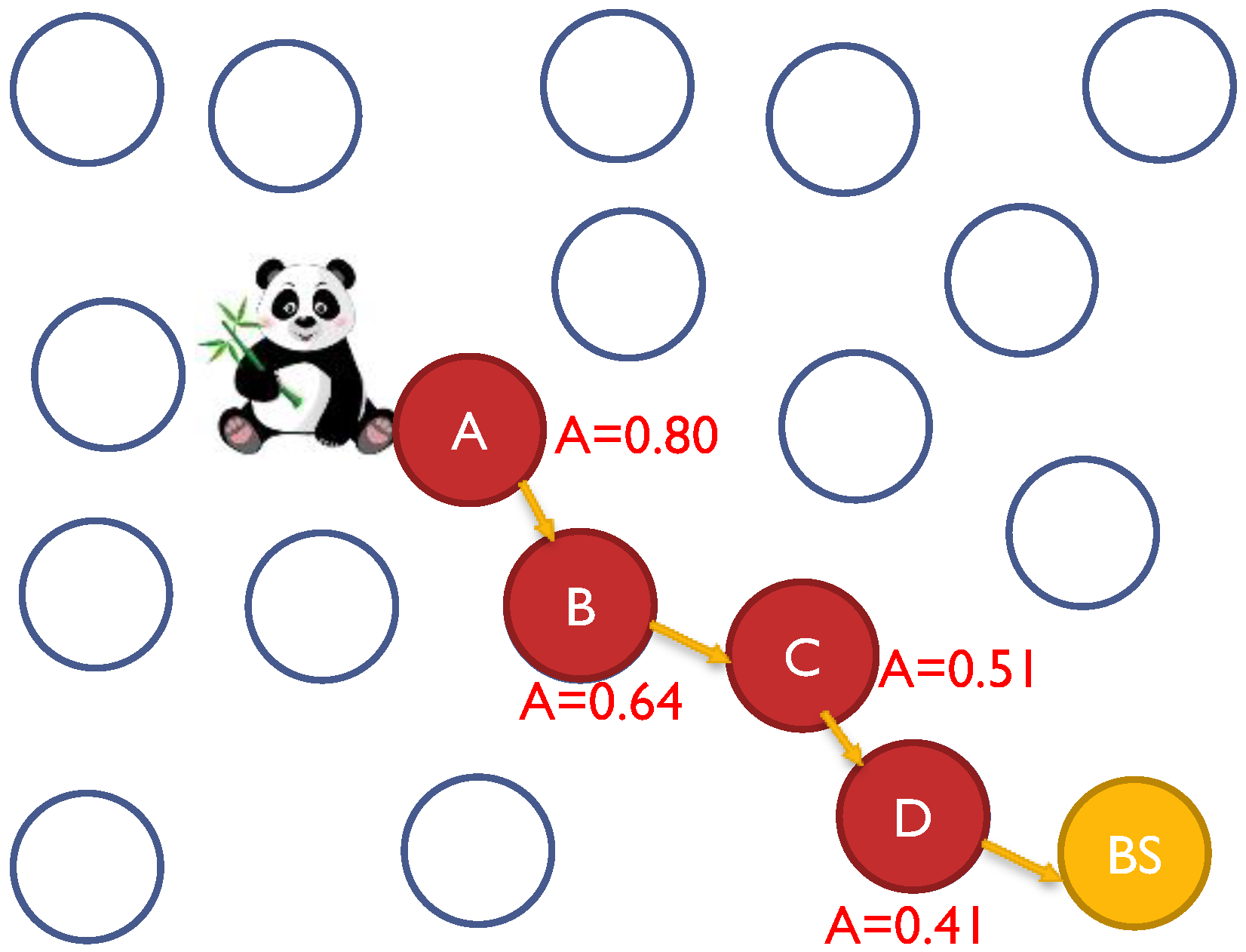
4. System, Network, Threat and Traffic Models
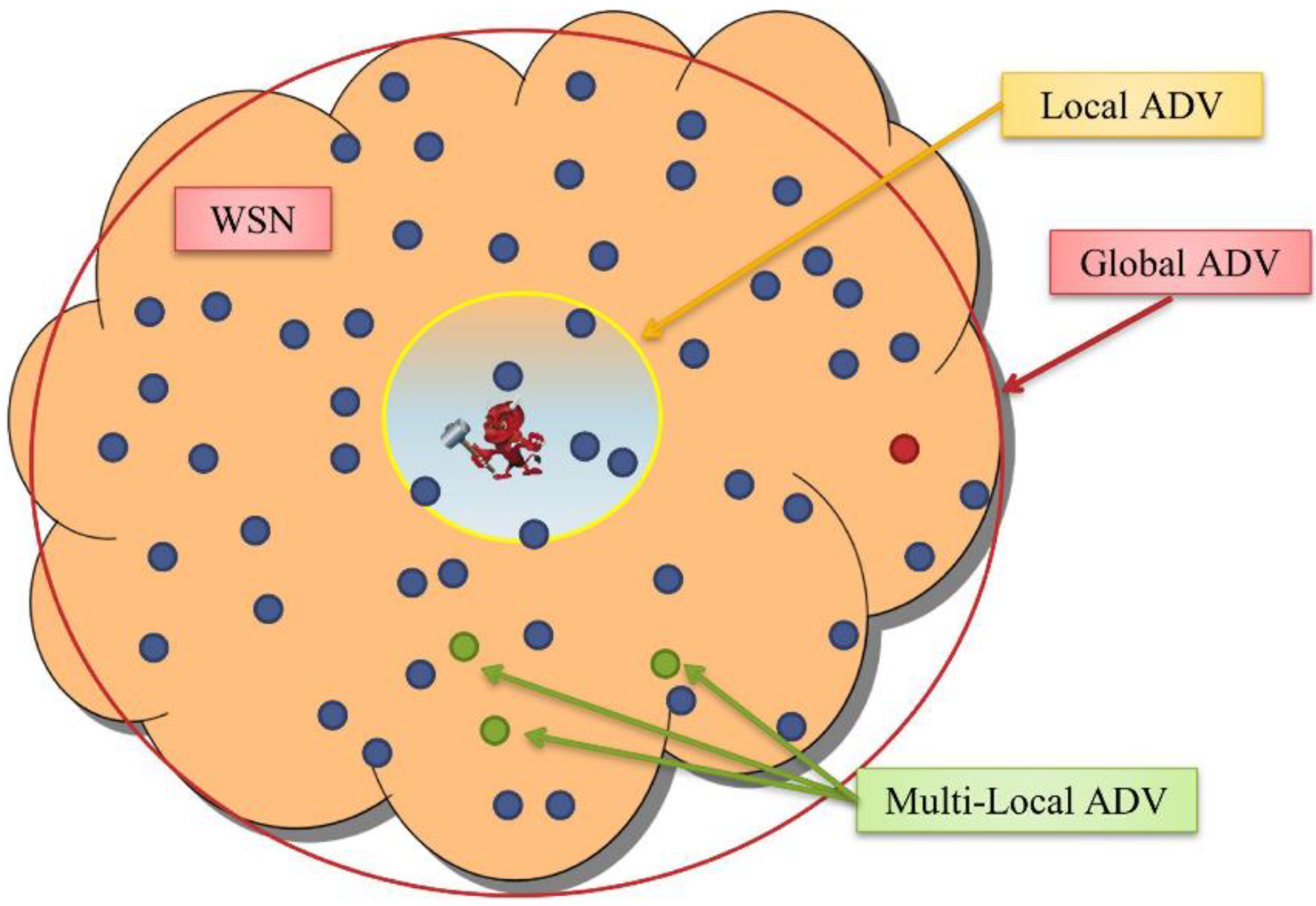
5. Module I: Anonymity
5.1. Pre-Deployment Phase
| Notation | Definition | Source |
|---|---|---|
| IDi | ID of sensor i | Preloaded |
| ai | Random number shared between SNi & BS | Preloaded |
| bi | Random number shared between SNi & neighbors | Preloaded |
| ci | Random number shared between SNi & neighbors | Preloaded |
| H1 | Hash function to create pseudonyms and the keys | Preloaded |
| H | Hash function to create data digest | Preloaded |
| ki↔bs | Pair-wise key shared between SNi & BS | Preloaded |
| kbi | Broadcast key for SNi | Preloaded |
| fkbi | Fake broadcast key for SNi | Preloaded |
| N | Number of SNs in WSN | Learned |
| Ni | Number of neighboring for SNi | Calculated |
| HCi↔bs | Hop-count between SNi & BS | Learned |
| PIDi | Pseudonym ID shared between SNi & BS | Calculated |
| BPIDi | Broadcast pseudonym ID | Calculated |
| ai↔j | Random value shared between SNi & SNj | Calculated |
| ki↔j | Pair-wise key shared between SNi & SNj | Calculated |
| OHPID i↔j | Pseudonym ID shared between SNi & SNj | Calculated |
| APIDi | ACK pseudonym ID for SNi | Calculated |
| FBPIDi | Fake broadcast pseudonym ID | Calculated |
| Ti | Table in SNi for shared parameters | Calculated |
| TIME_STAMP | Time stamp | Calculated |
| SEQ_NO | Sequence number for a message | Calculated |
| TTL | Time to live | Calculated |
| MCG_LGTH | Message size | Calculated |
| Residual energy | Calculated | |
| ⊕ | XOR Operation | Operation |
| || | Concatenation operation | Operation |
5.2. Setup Phase
5.2.1. Creating Pseudonyms
| Information in Ti Per Each Neighbor | Tuple for SNj |
|---|---|
| Shared random number | ai↔j |
| Shared broadcast random number | bj |
| Shared fake broadcast random number | cj |
| Shared broadcast key | BPIDj |
| Shared fake broadcast key | FPIDj |
| Shared one-hop key | ki↔j |
| Current one-hop pseudonym ID | OHPID i↔j |
| Link direction | linki→j |
| Residual energy level | Δj |
5.2.2. Deleting Security Information
5.3. Communication Phase
5.3.1. Transmission as a Sensor
5.3.2. Transmission as a Forwarder
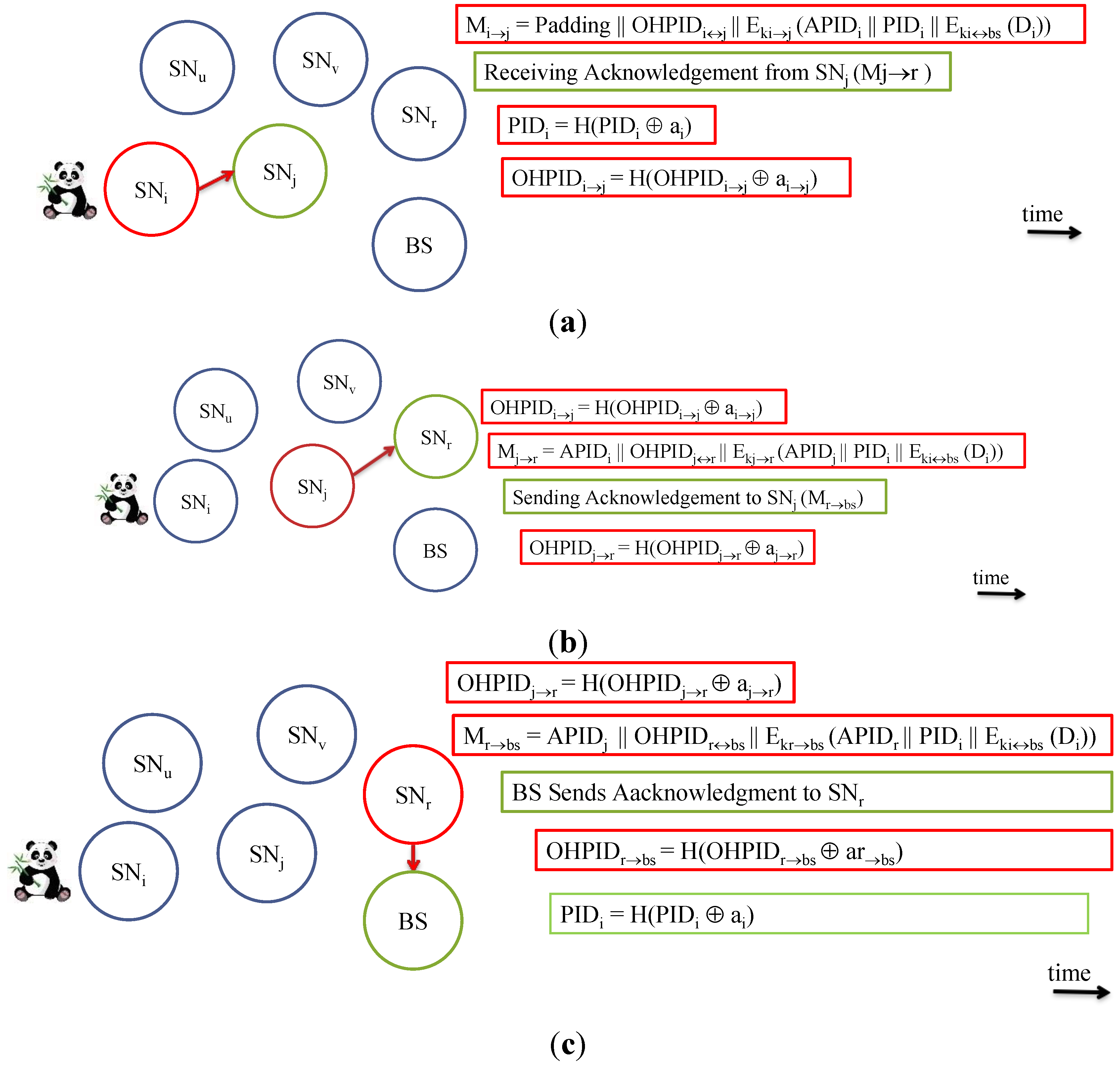
5.3.3. Acknowledgement
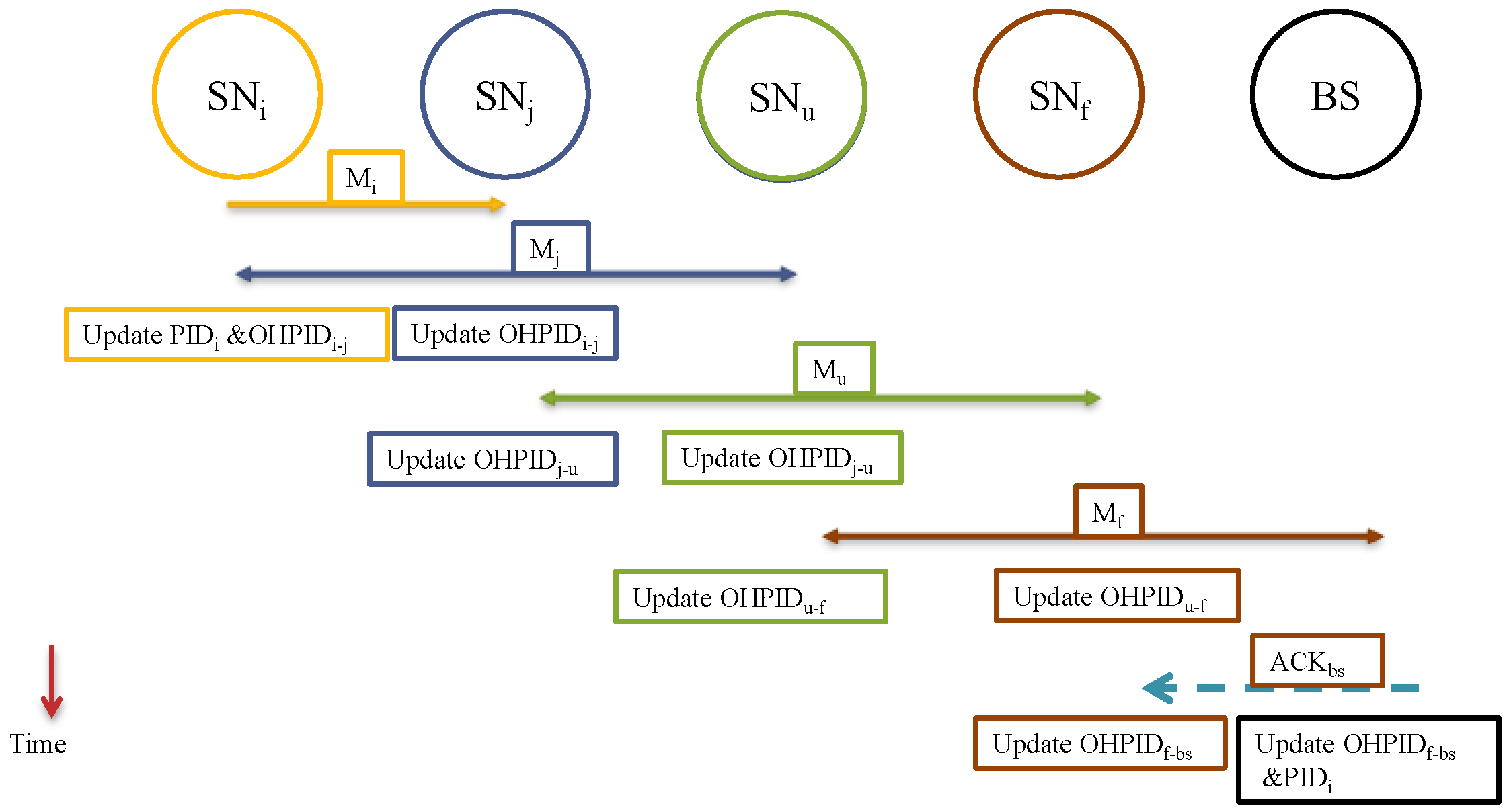
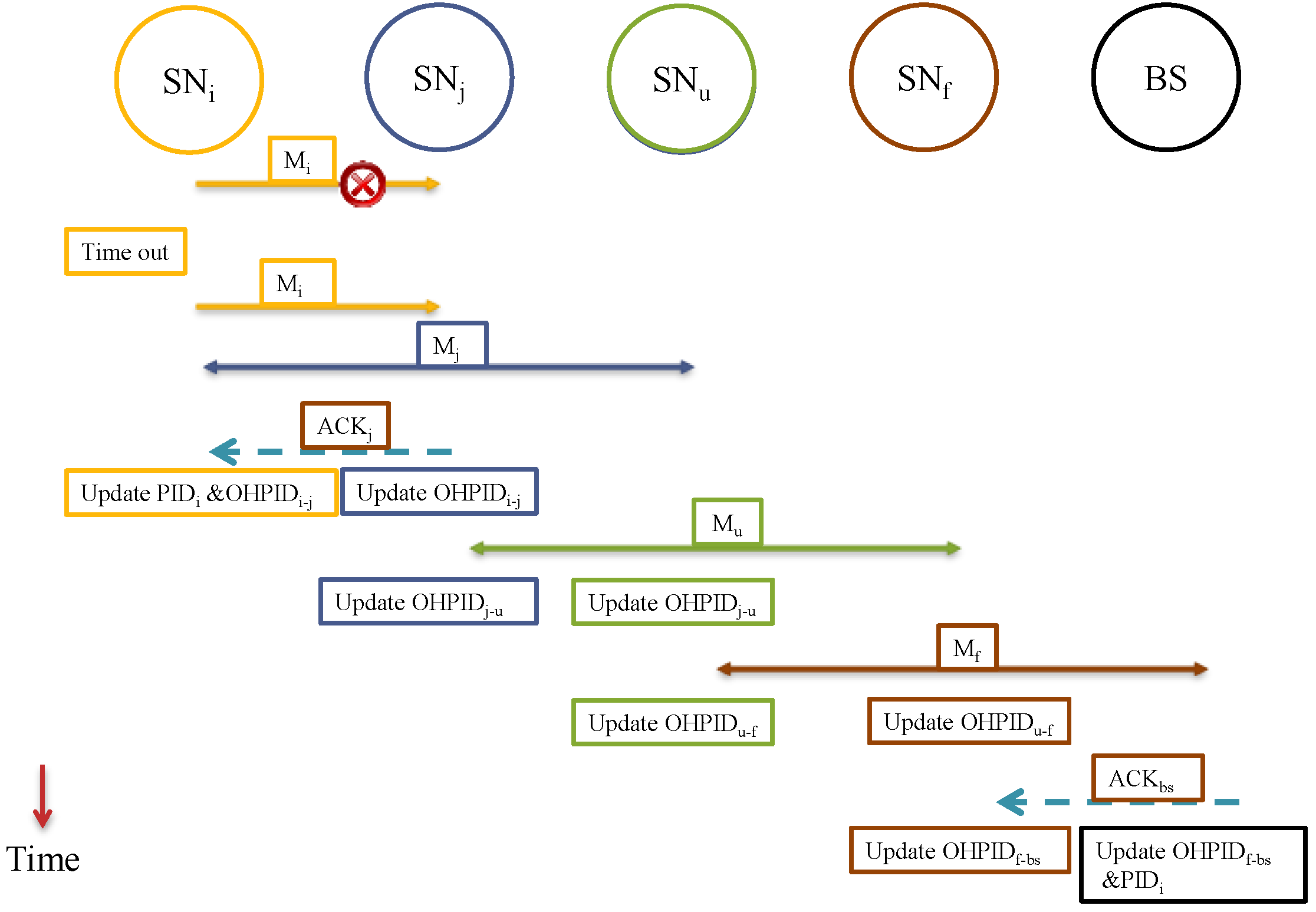

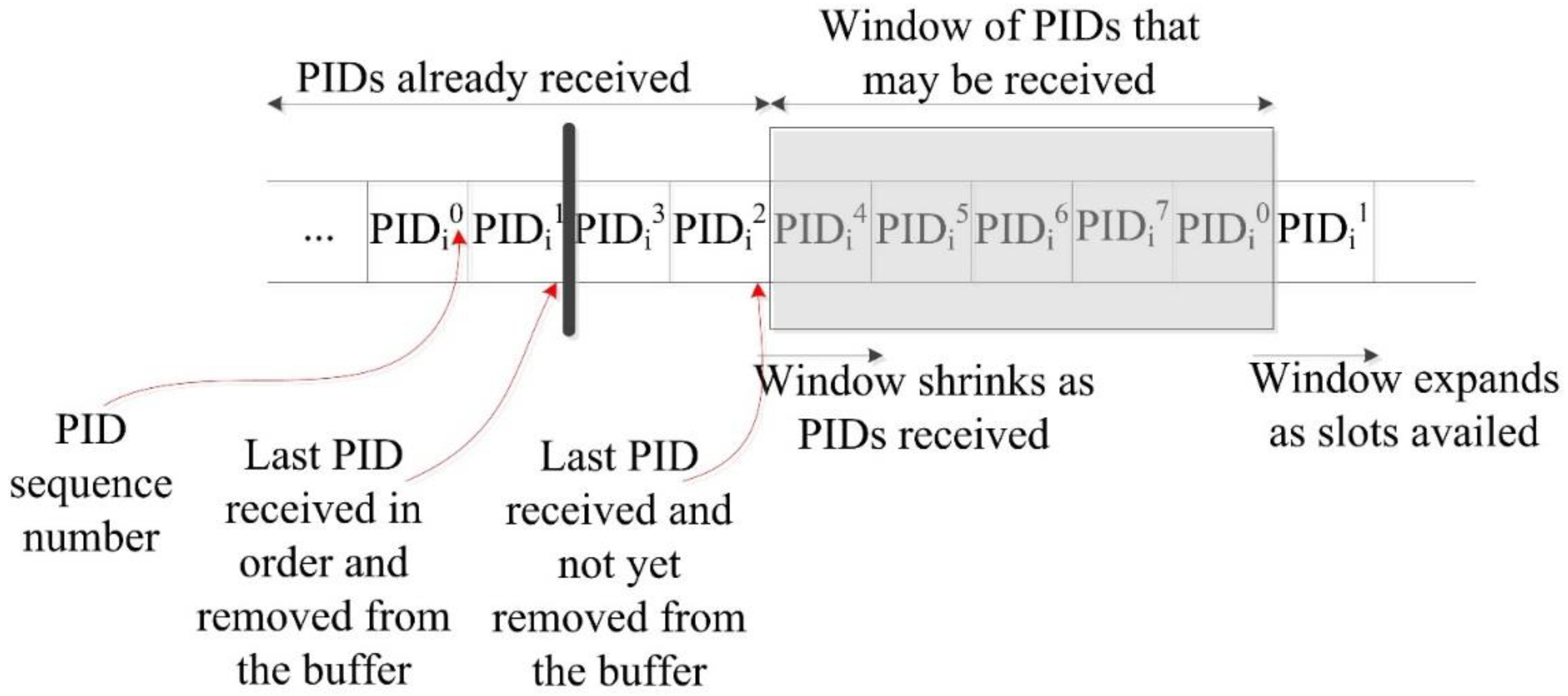
5.3.4. Transmission as a Broadcaster
5.3.5. Limited Broadcast Messages
5.3.6. Fake Broadcast Message
5.4. SN Removal
5.5. SN Addition
5.6. Contribution of Anonymity Module
6. Module II: Data Authentication and Integrity
7. Module III: Temporal Privacy
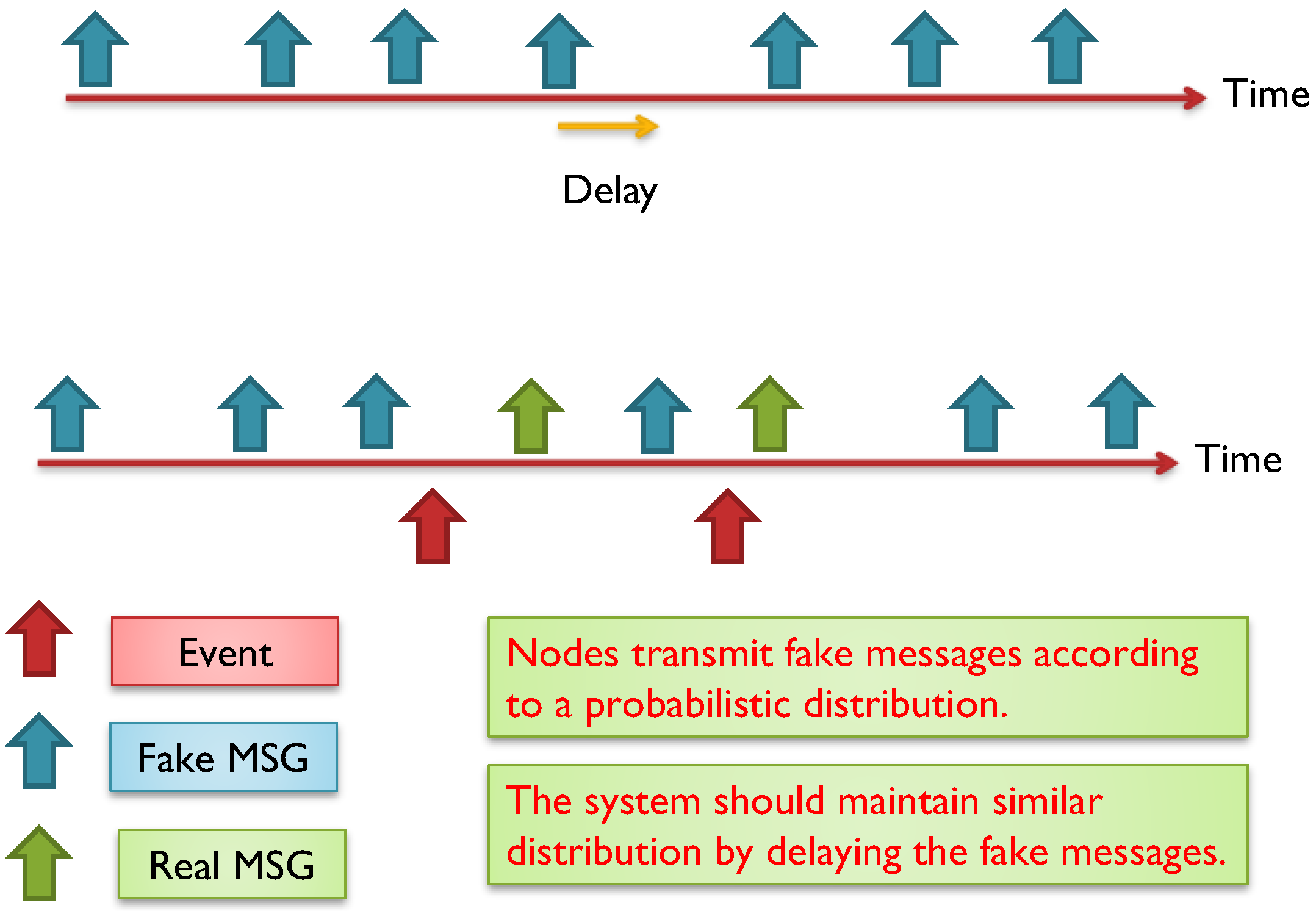
7.1. Simple Global Anti Temporal Scheme (SGAT)
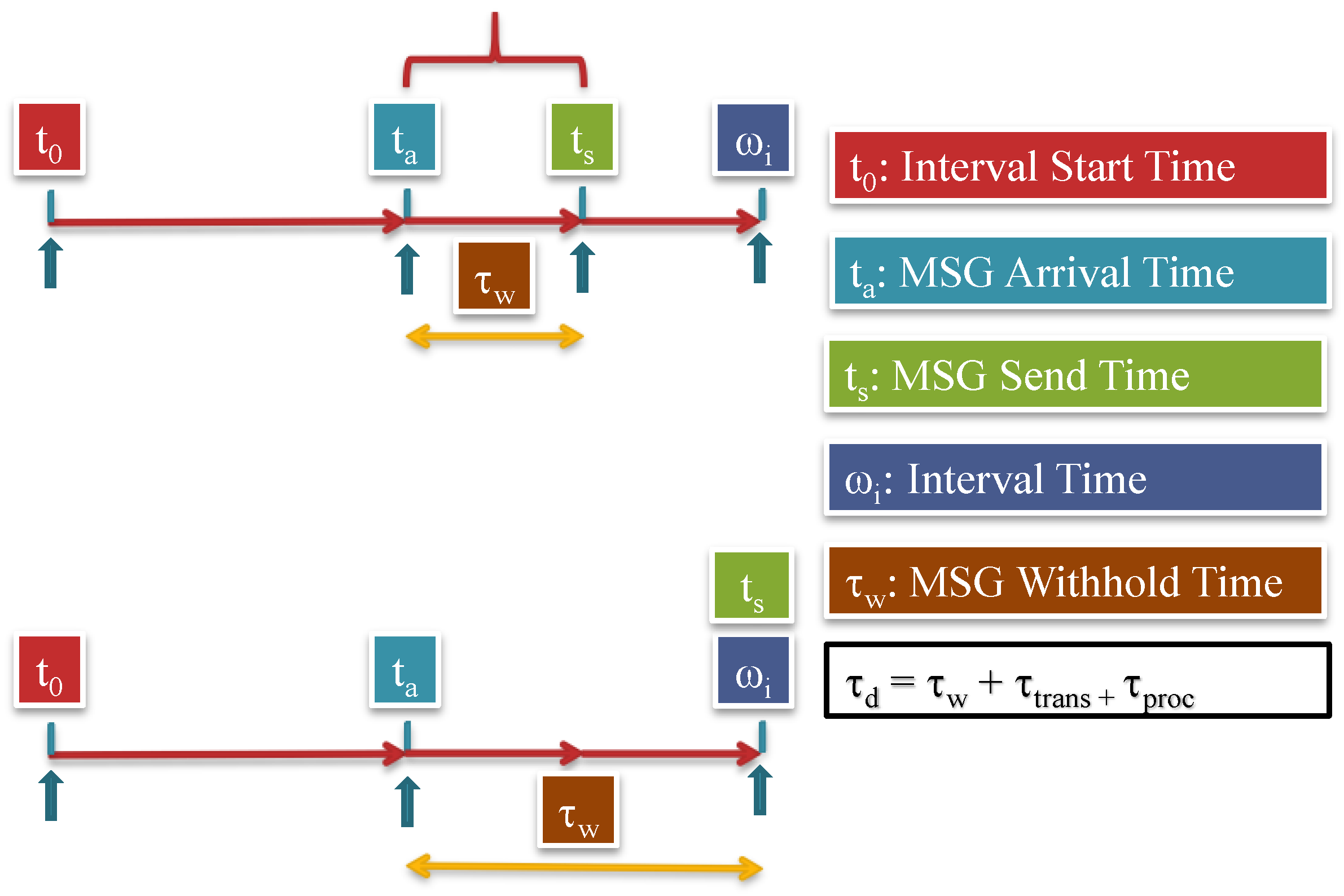
7.1.1. Security Analysis
7.1.2. Delivery Time
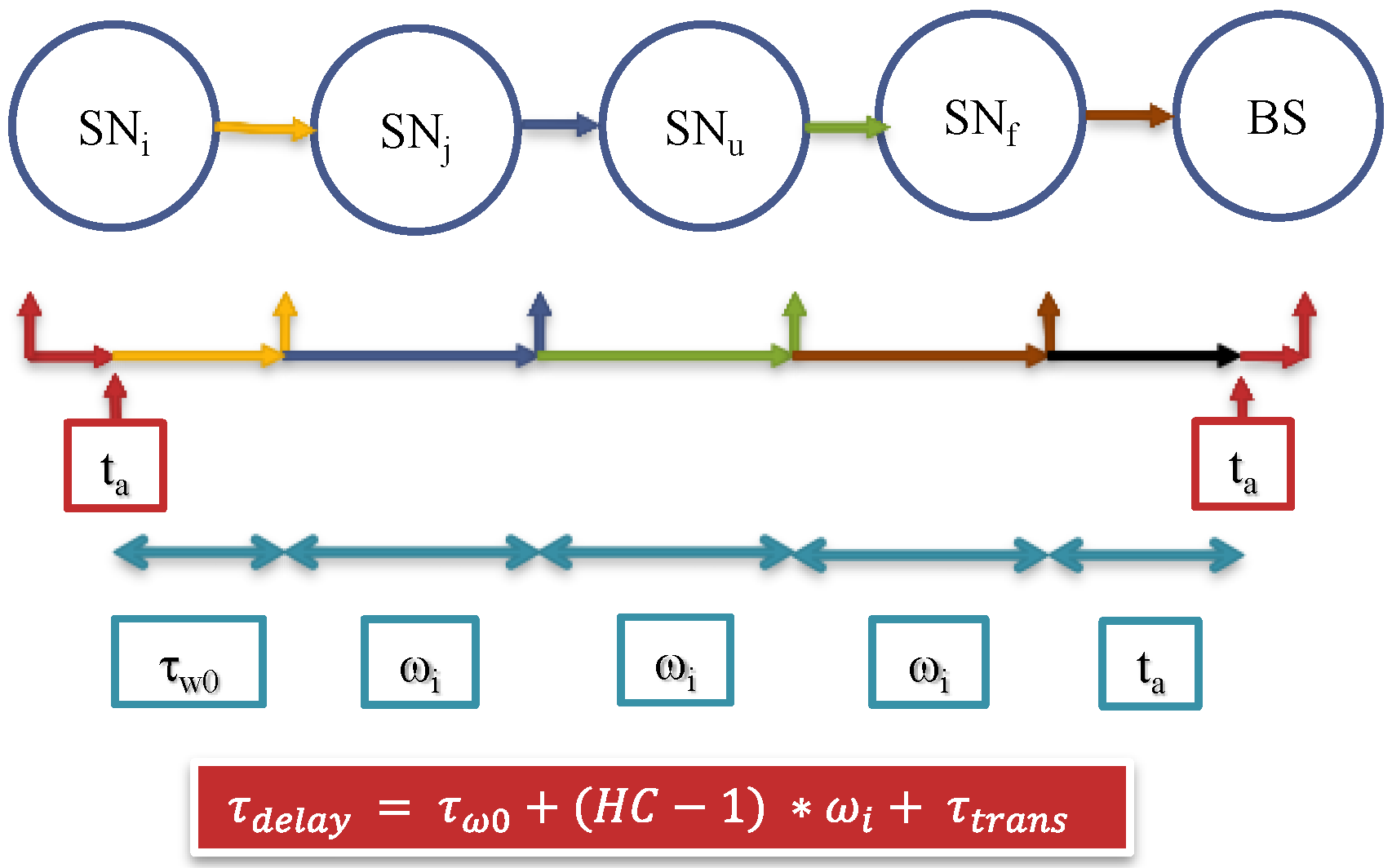
7.1.3. Energy Cost
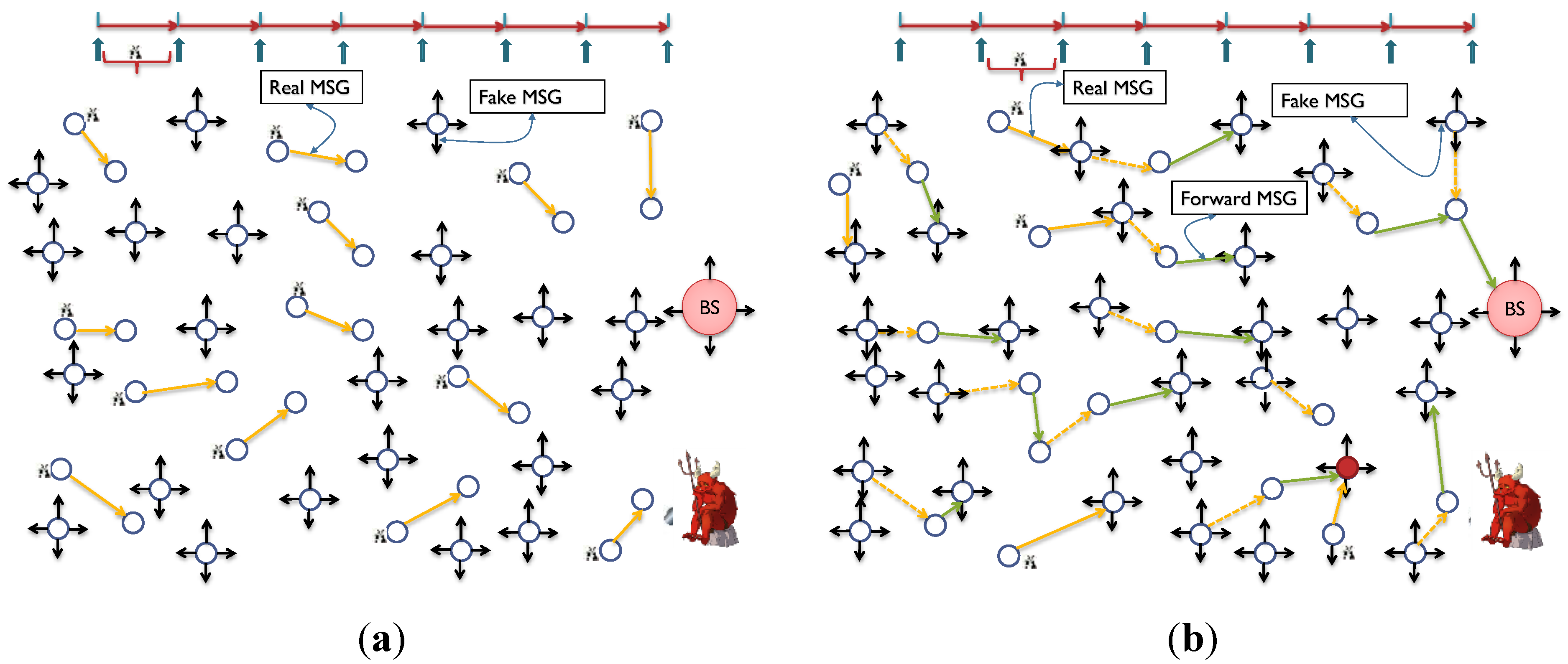
7.2. Energy Controlled Anti Temporal Scheme (ECAT)
7.2.1. Changing ωi from Fixed to Variable
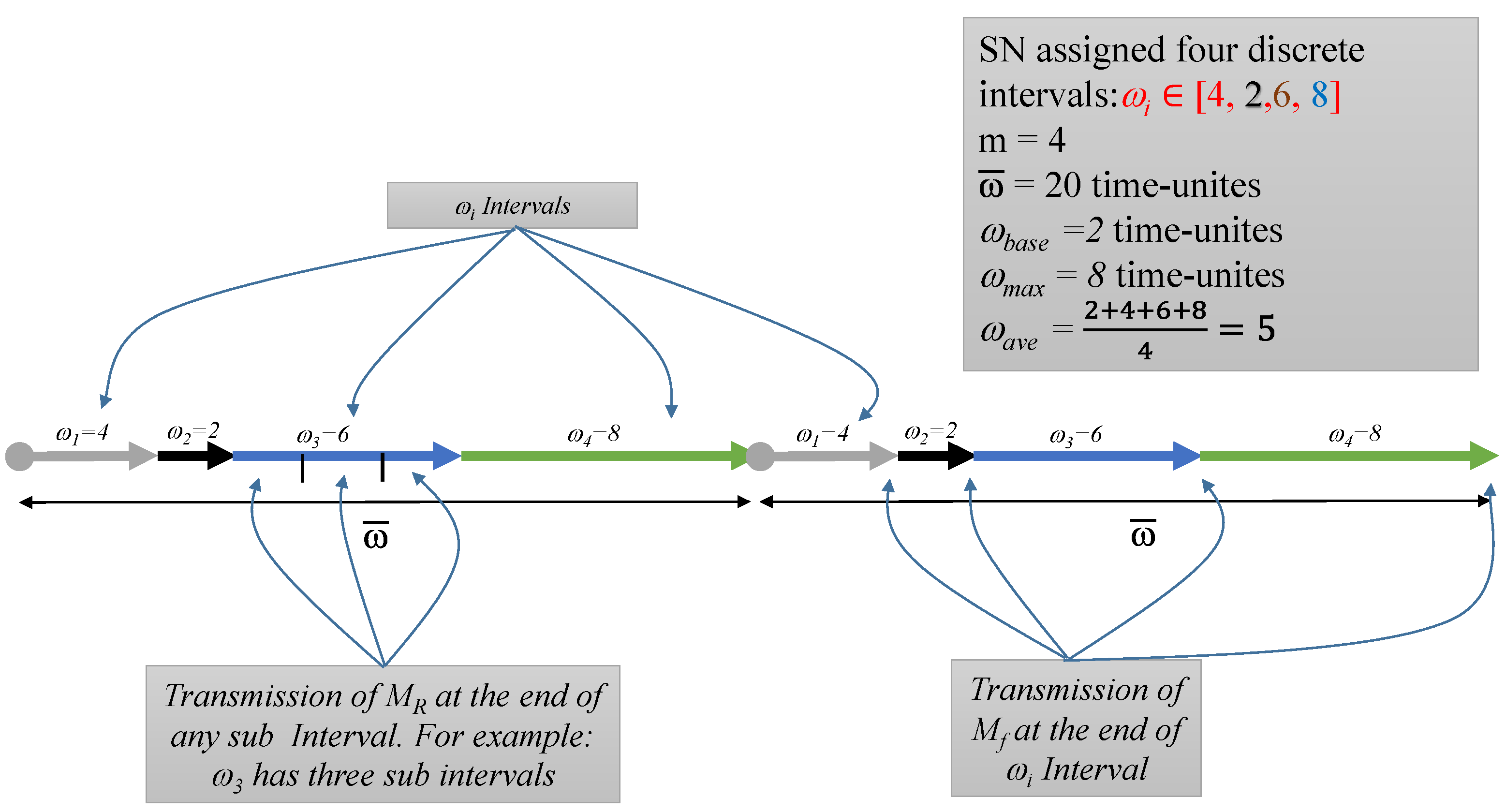
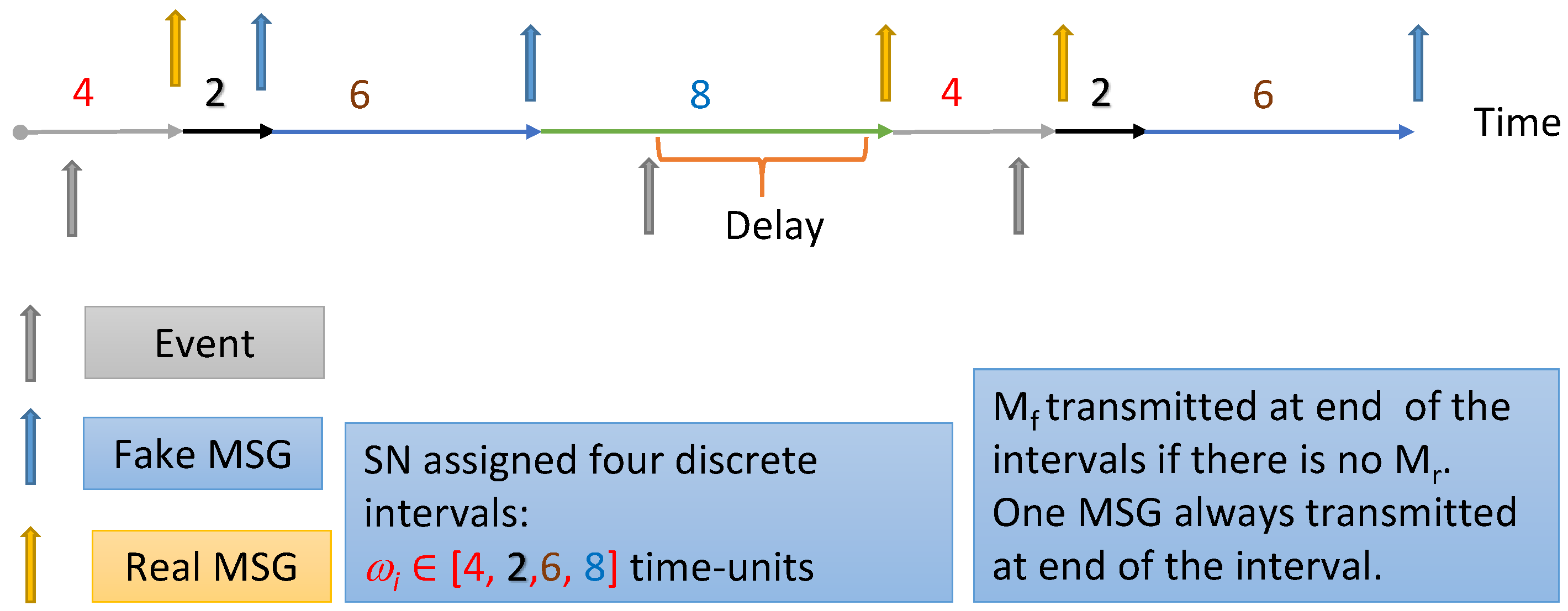
7.2.2. Reducing the Amount of Fake Messages and Delay for Real Messages
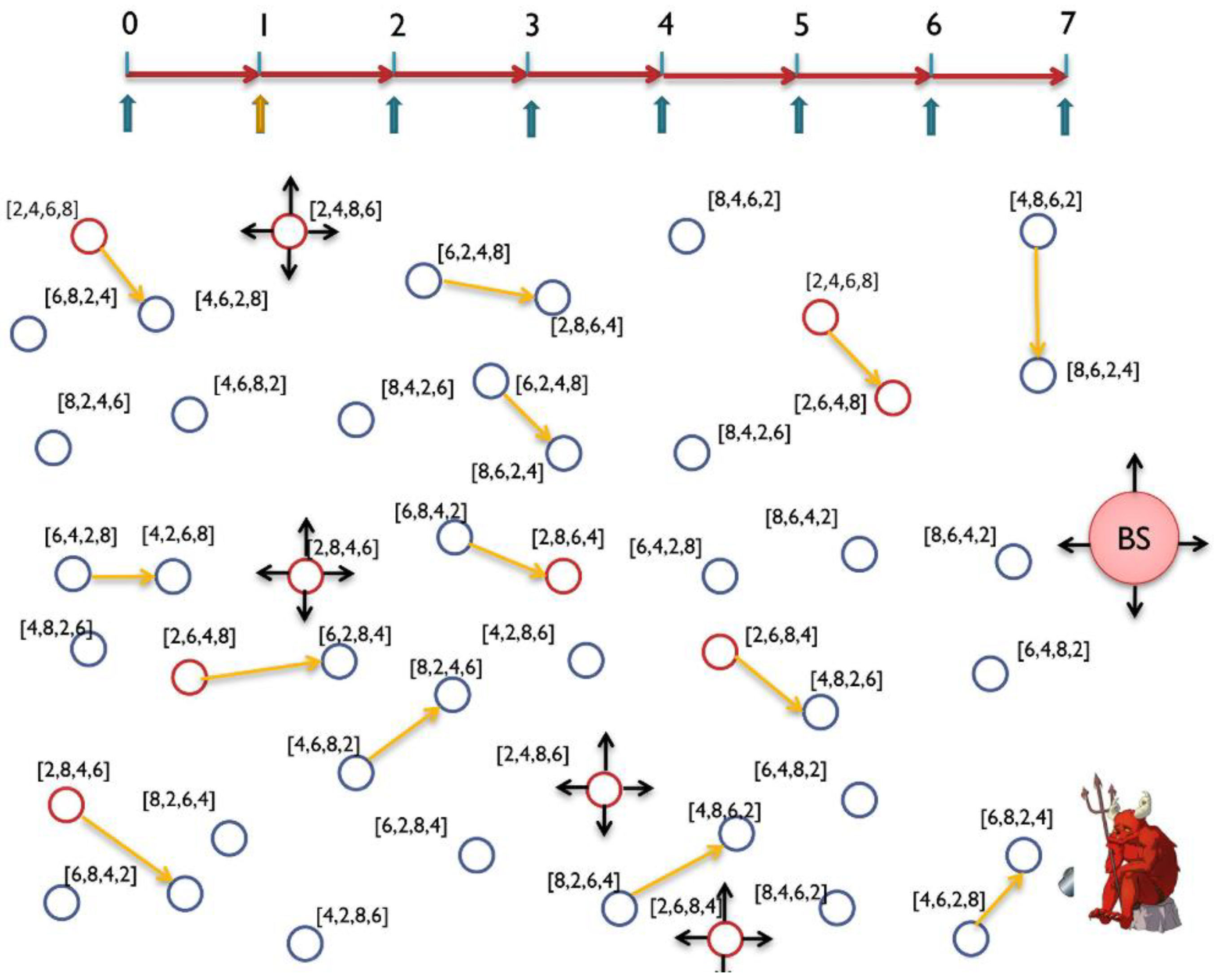
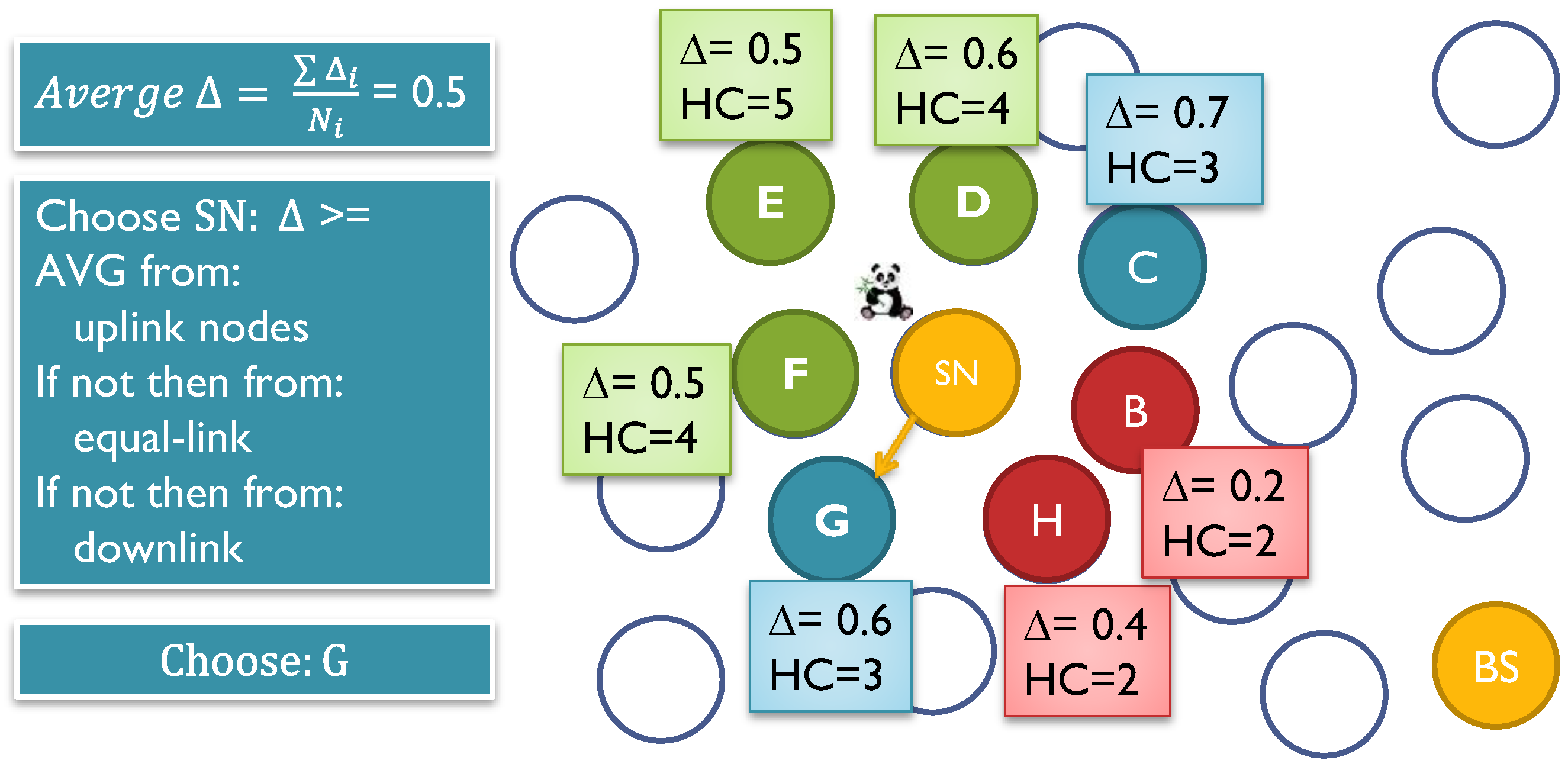
7.2.3. Energy Conservation by Forwarding Messages to Energy-Rich SNs
7.2.4. Handling Rate Attack
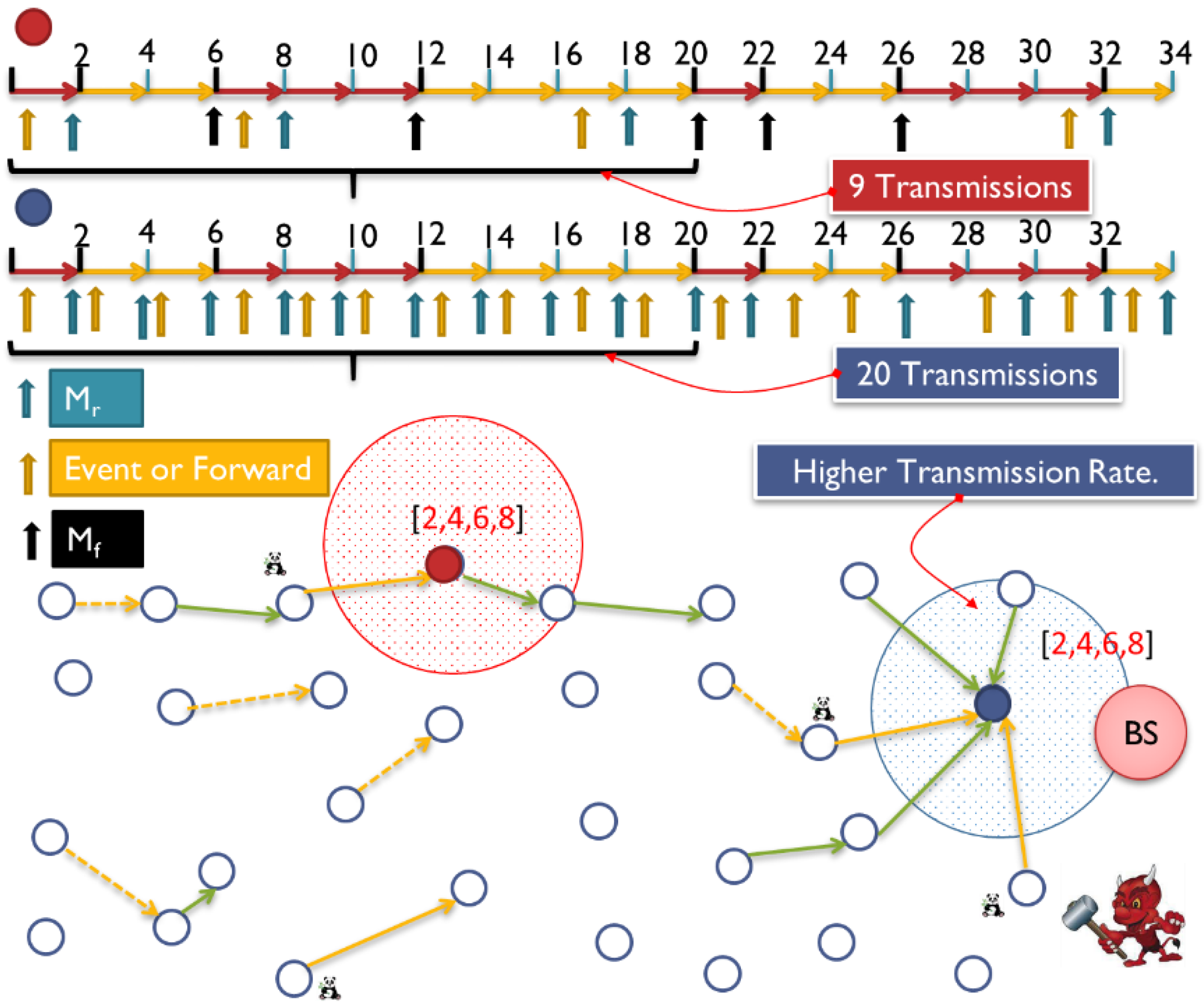
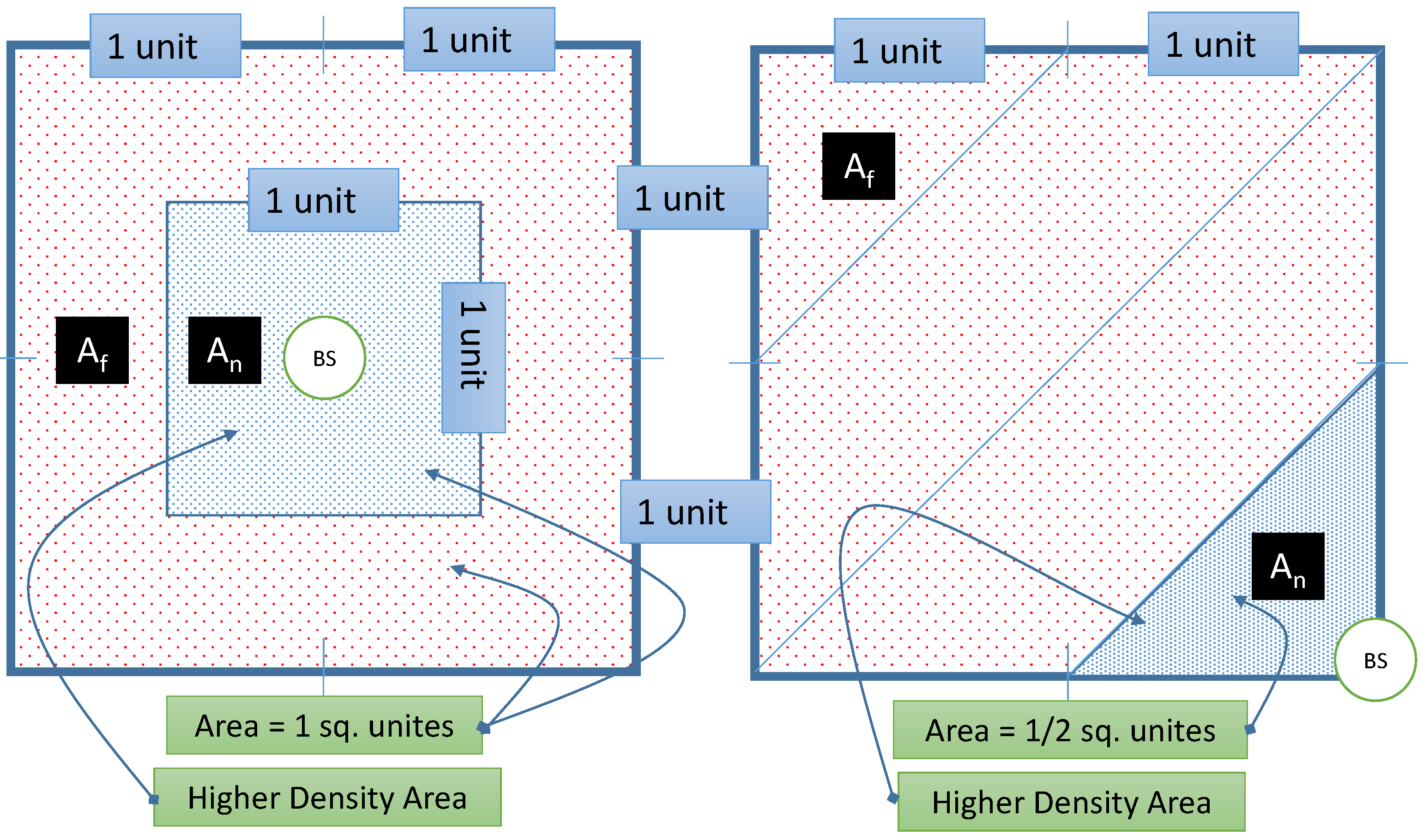
7.3. Contribution of Temporal and Rate Privacy Module
8. Anonymity and Security Analysis
8.1. Security against Passive Attacks
8.2. Security against Active Attacks
8.2.1. Soft-Active Attacks
8.2.2. Hard-Active Attacks
8.3. Sink Security
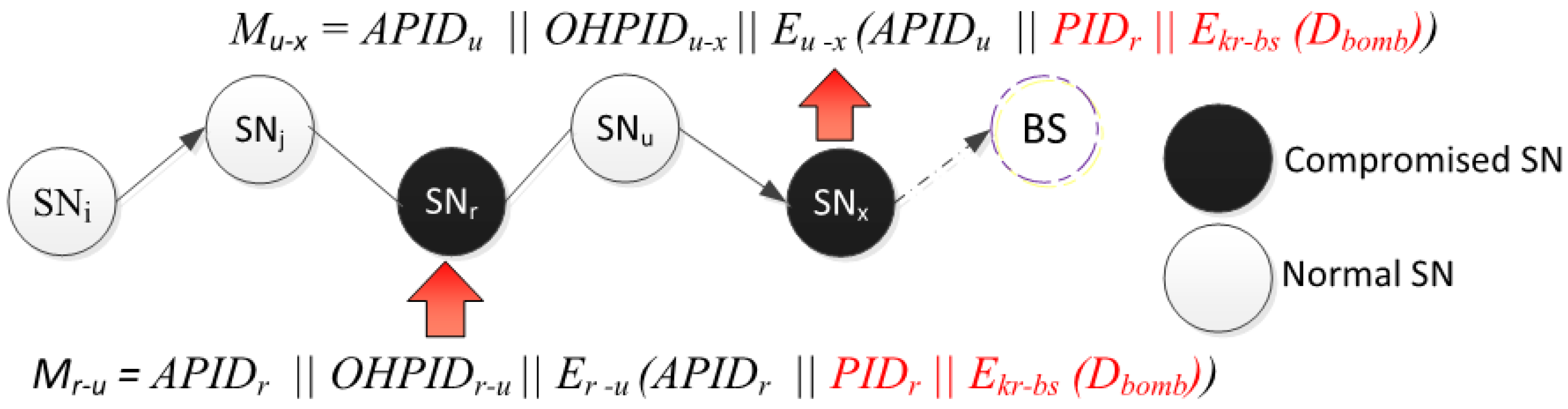
8.4. Link Anonymity
8.5. Timing Privacy
8.6. Routing Privacy
8.7. Data Privacy
8.8. SLP and BLP
9. Performance Evaluation
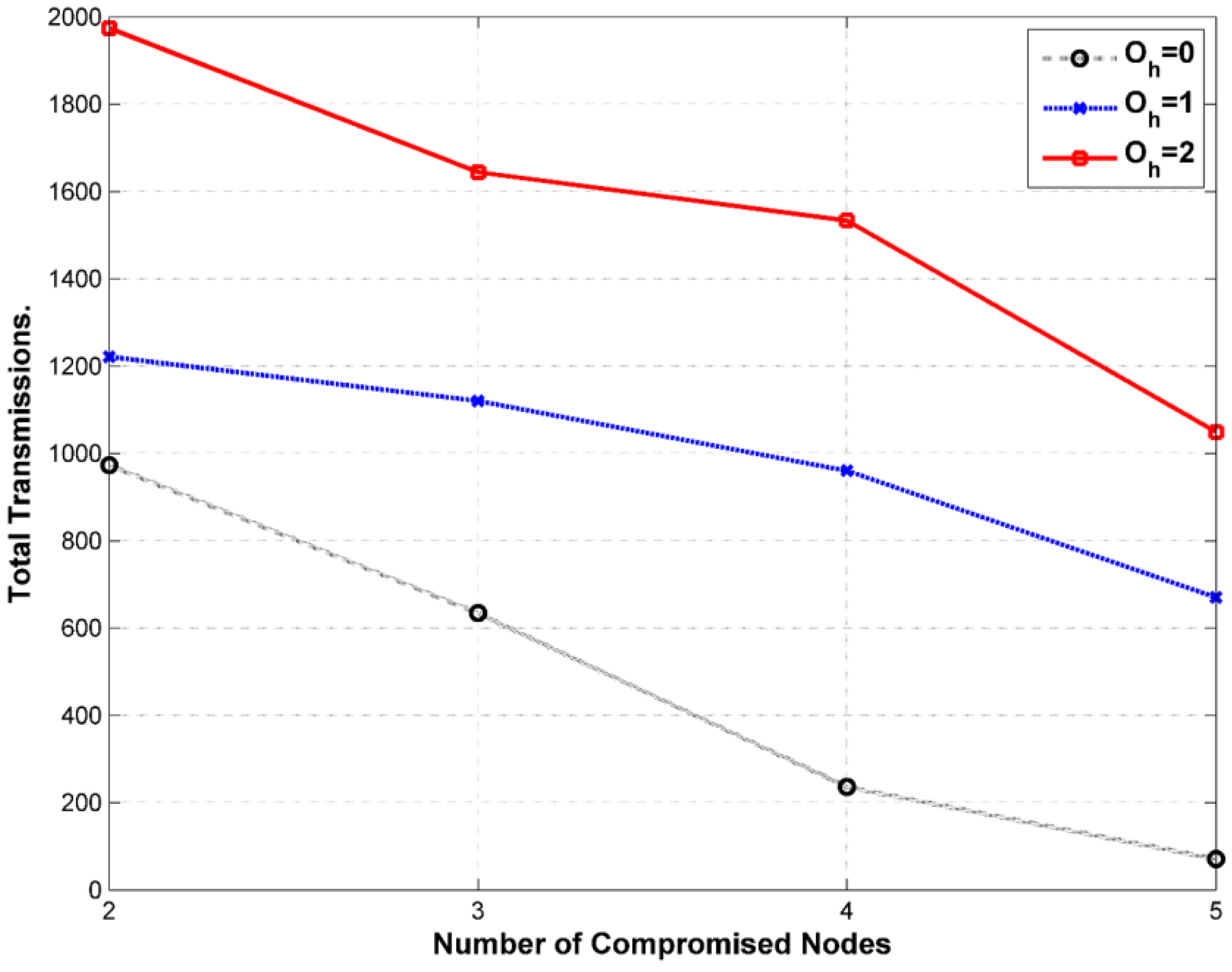
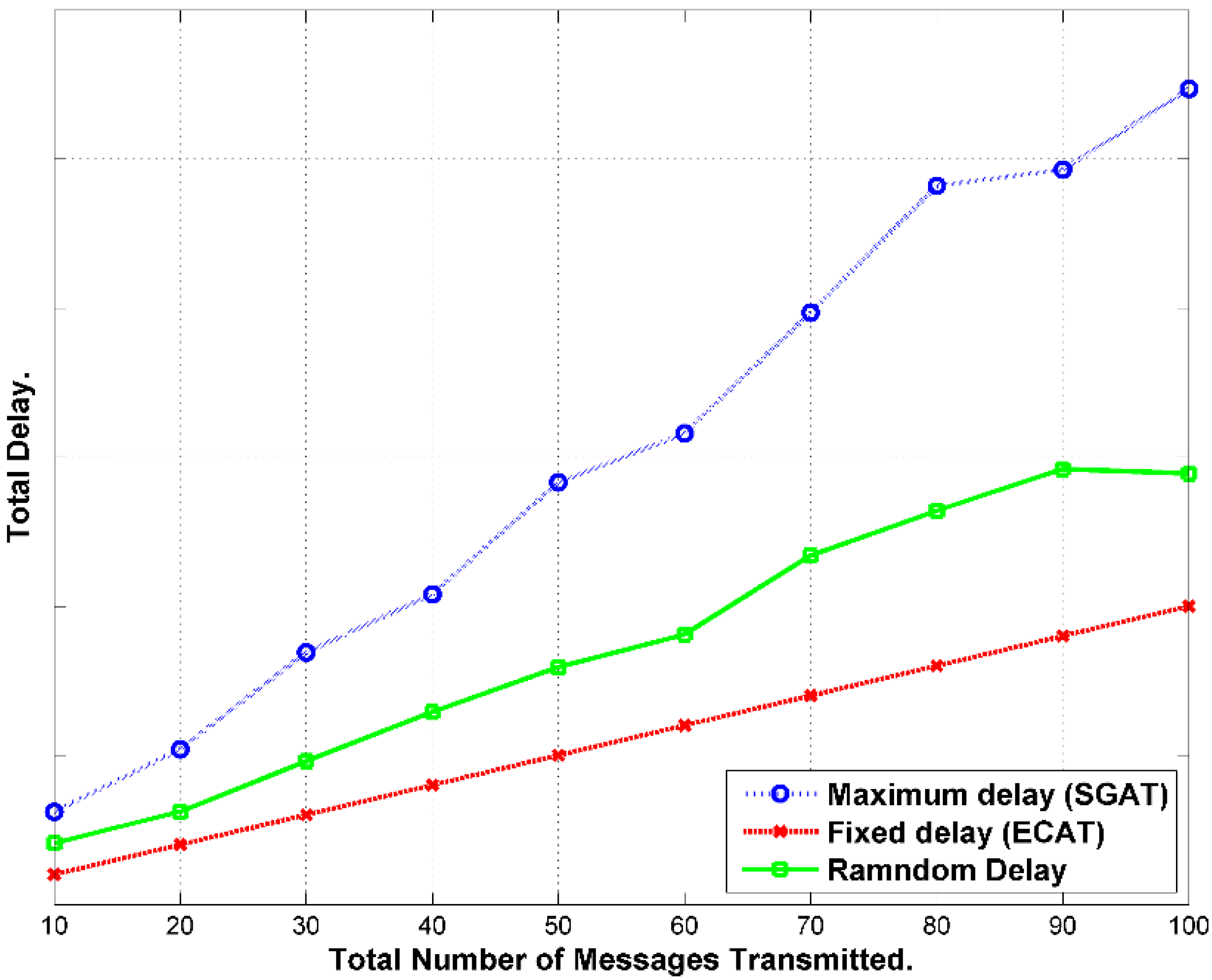
9.1. Delay
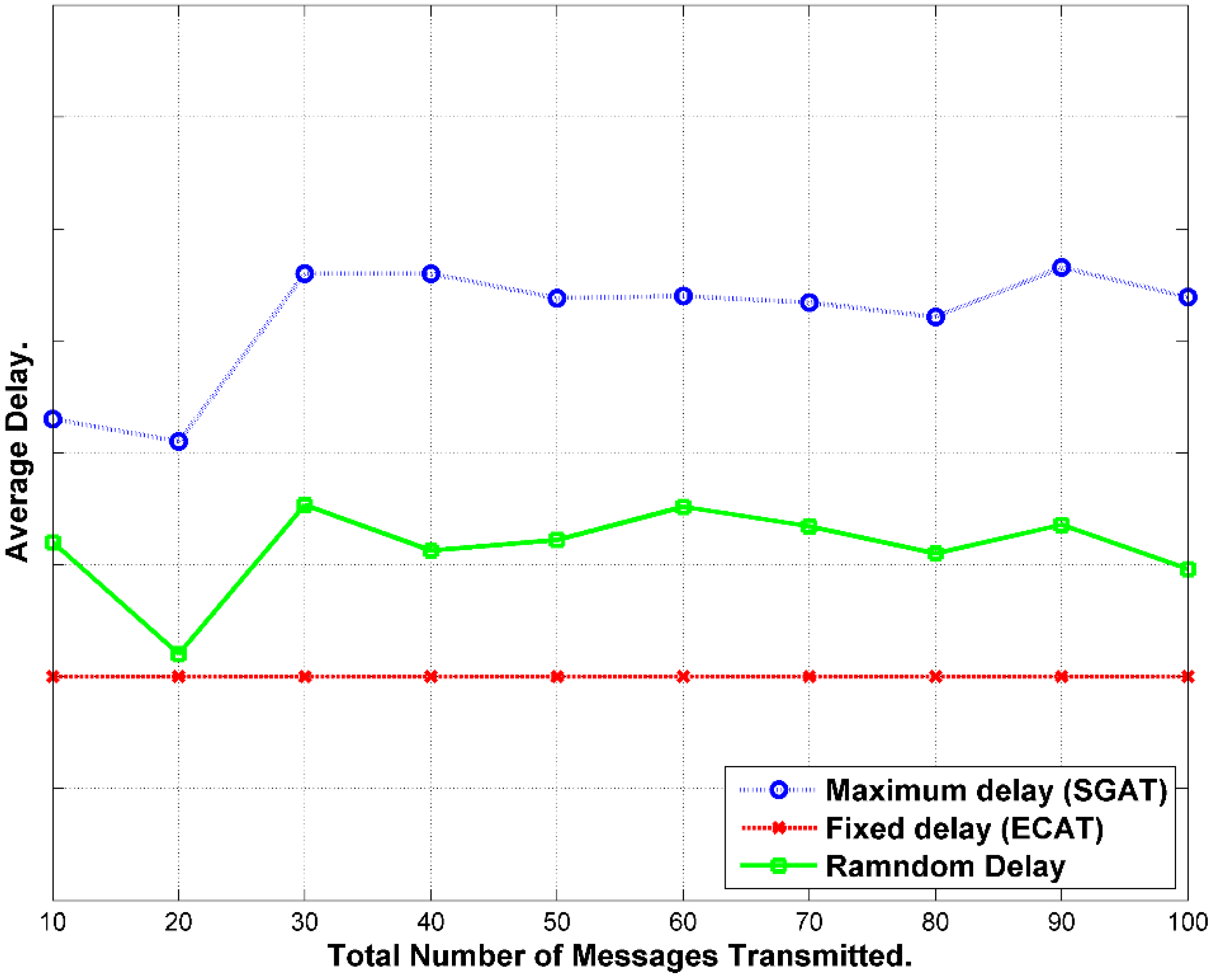
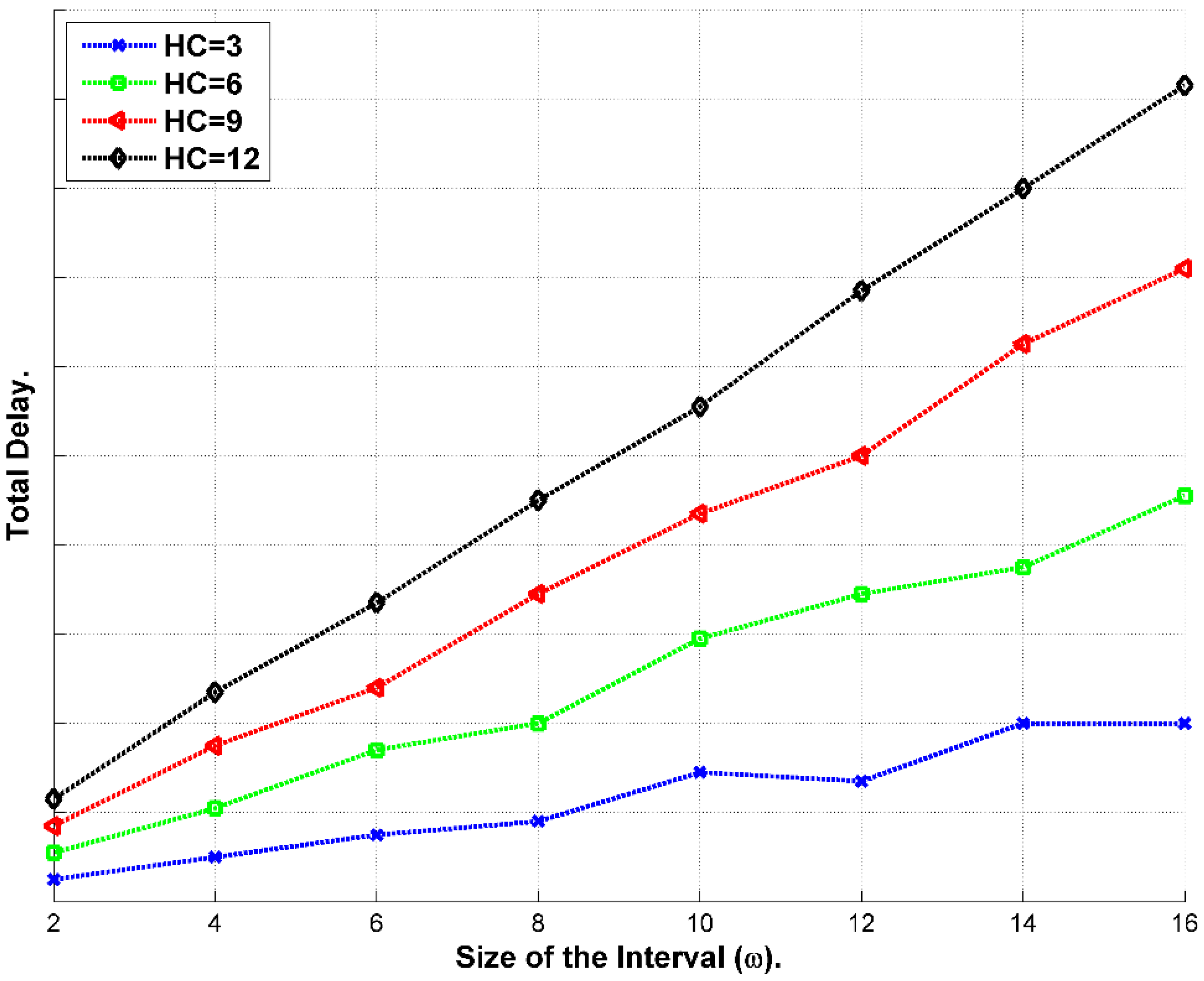
9.2. Energy Cost
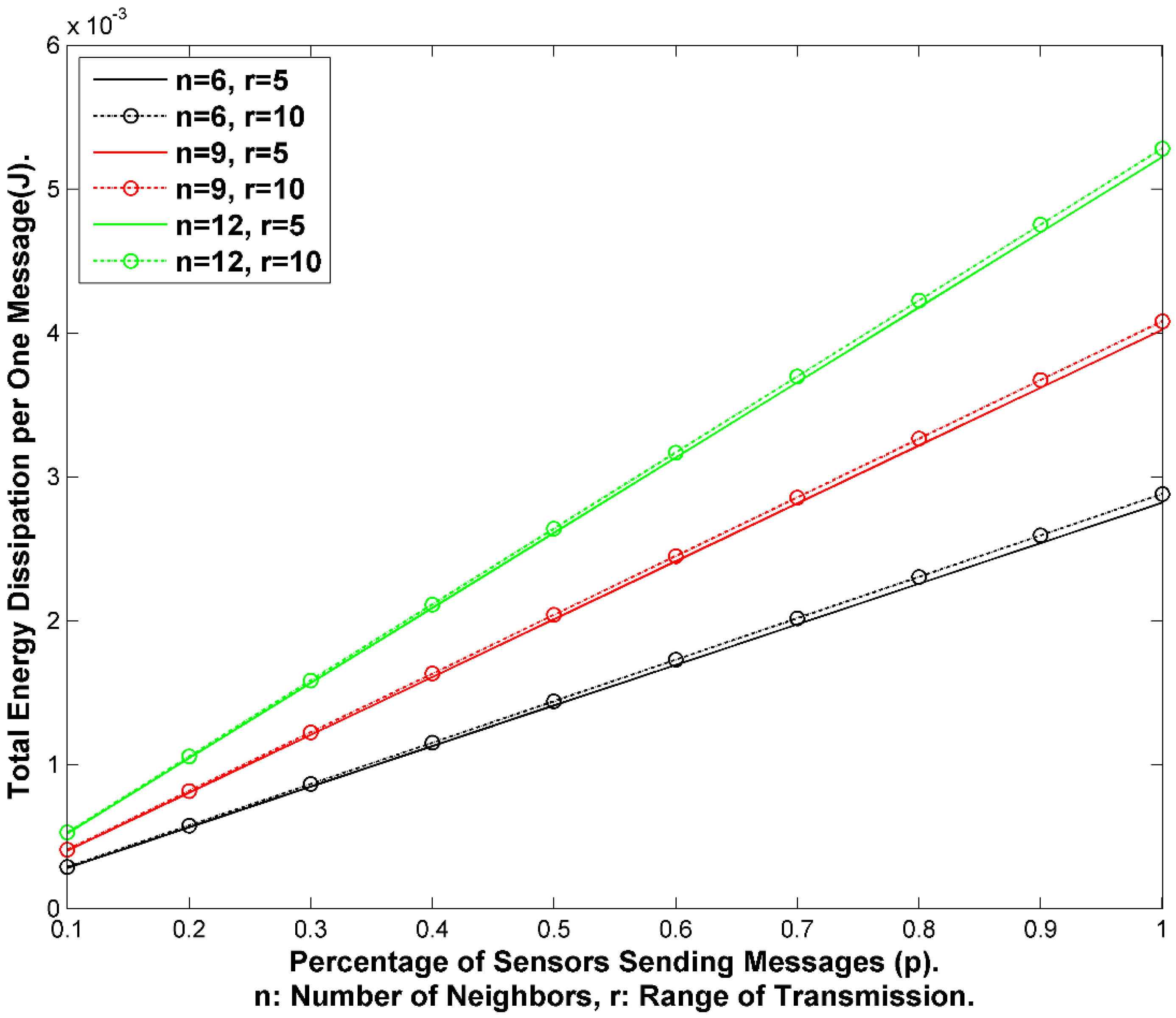
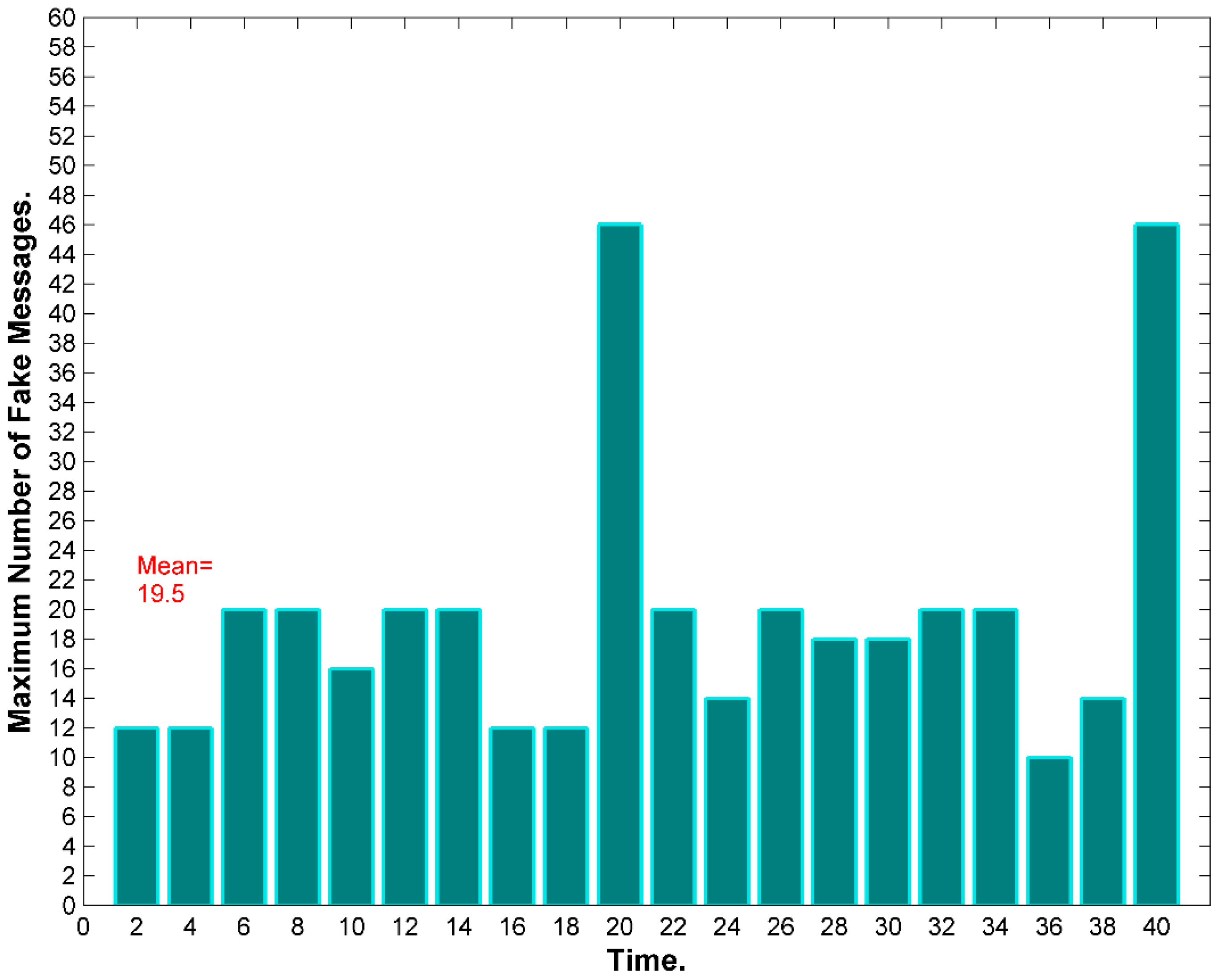
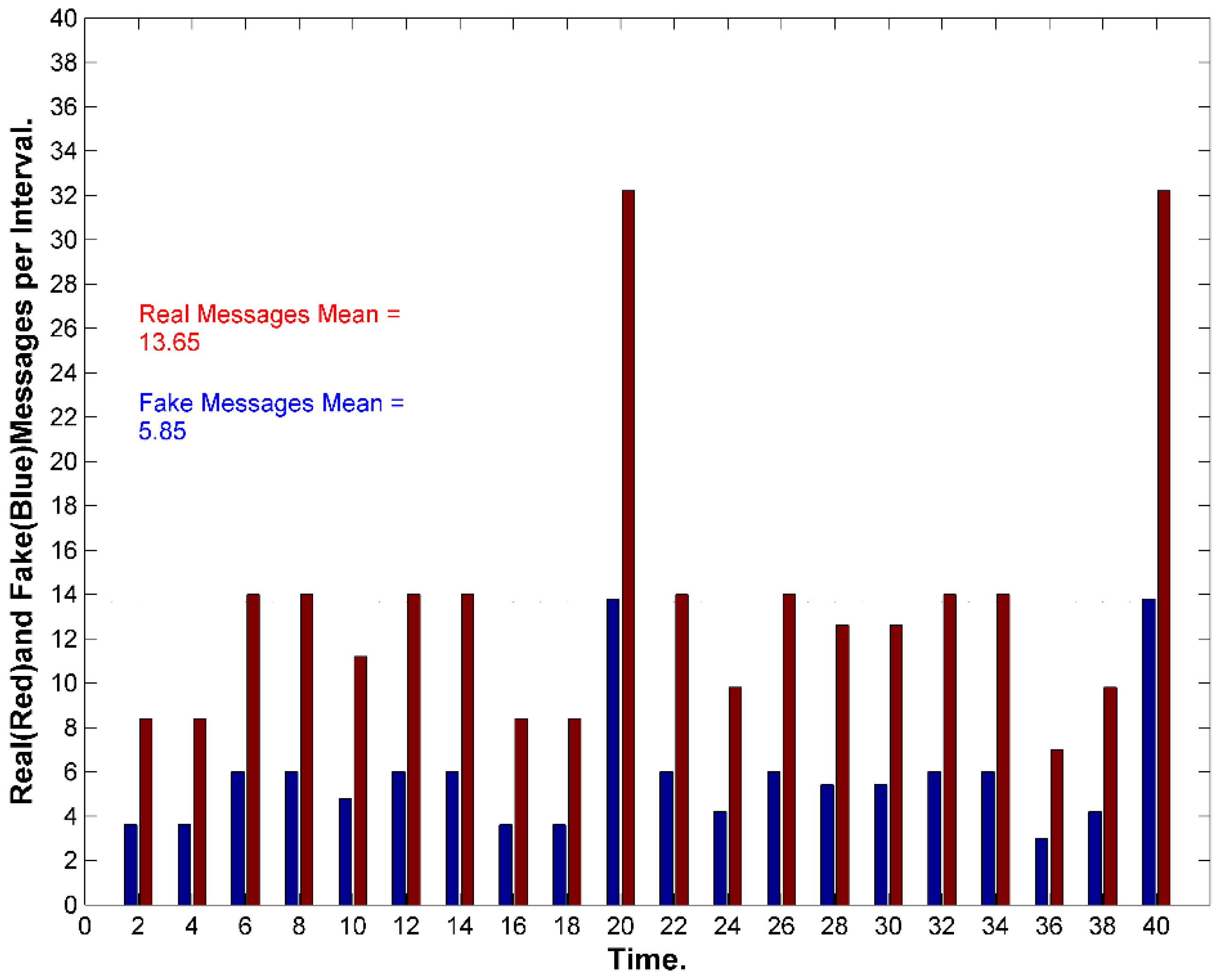
9.3. Transmission Rate Privacy
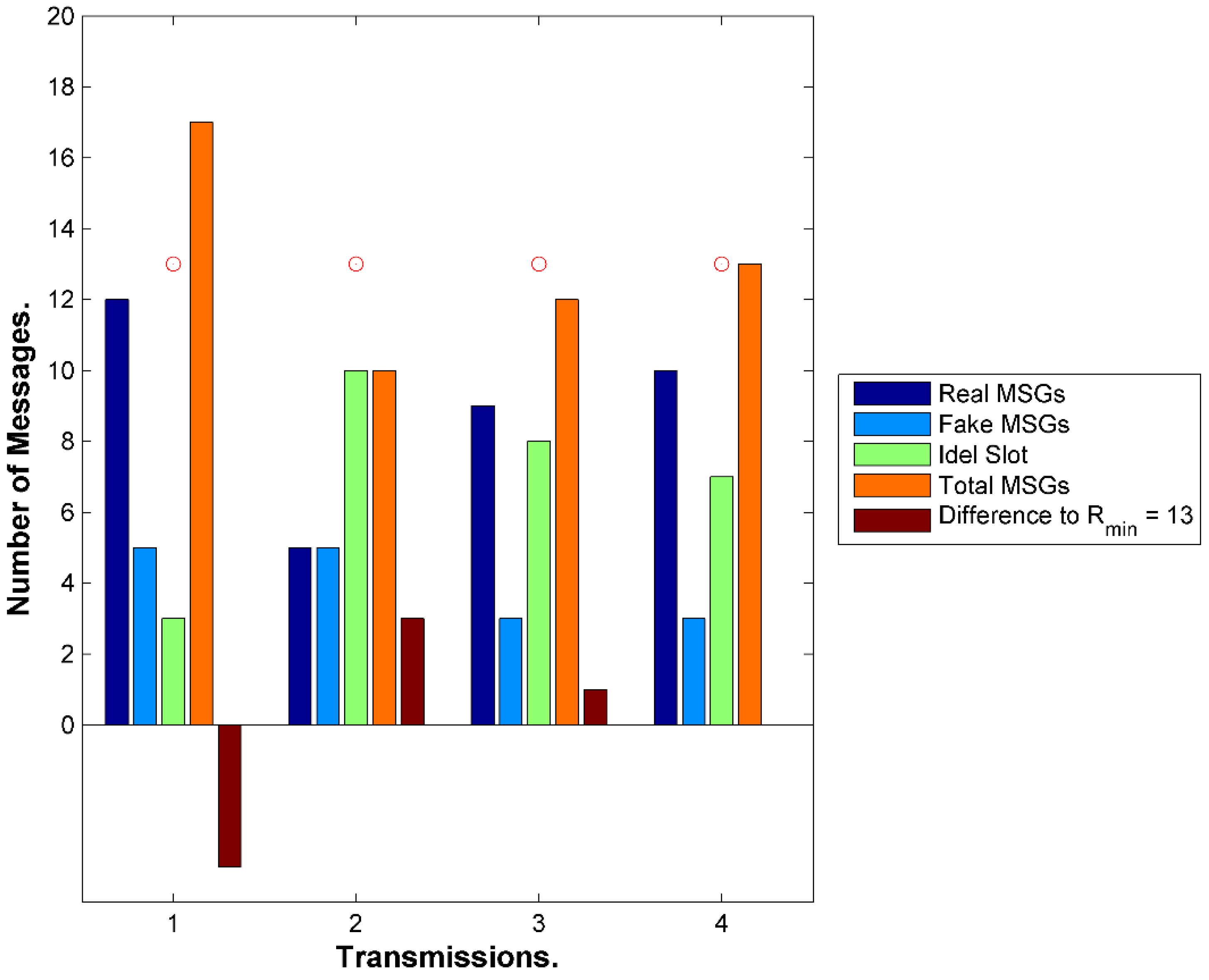
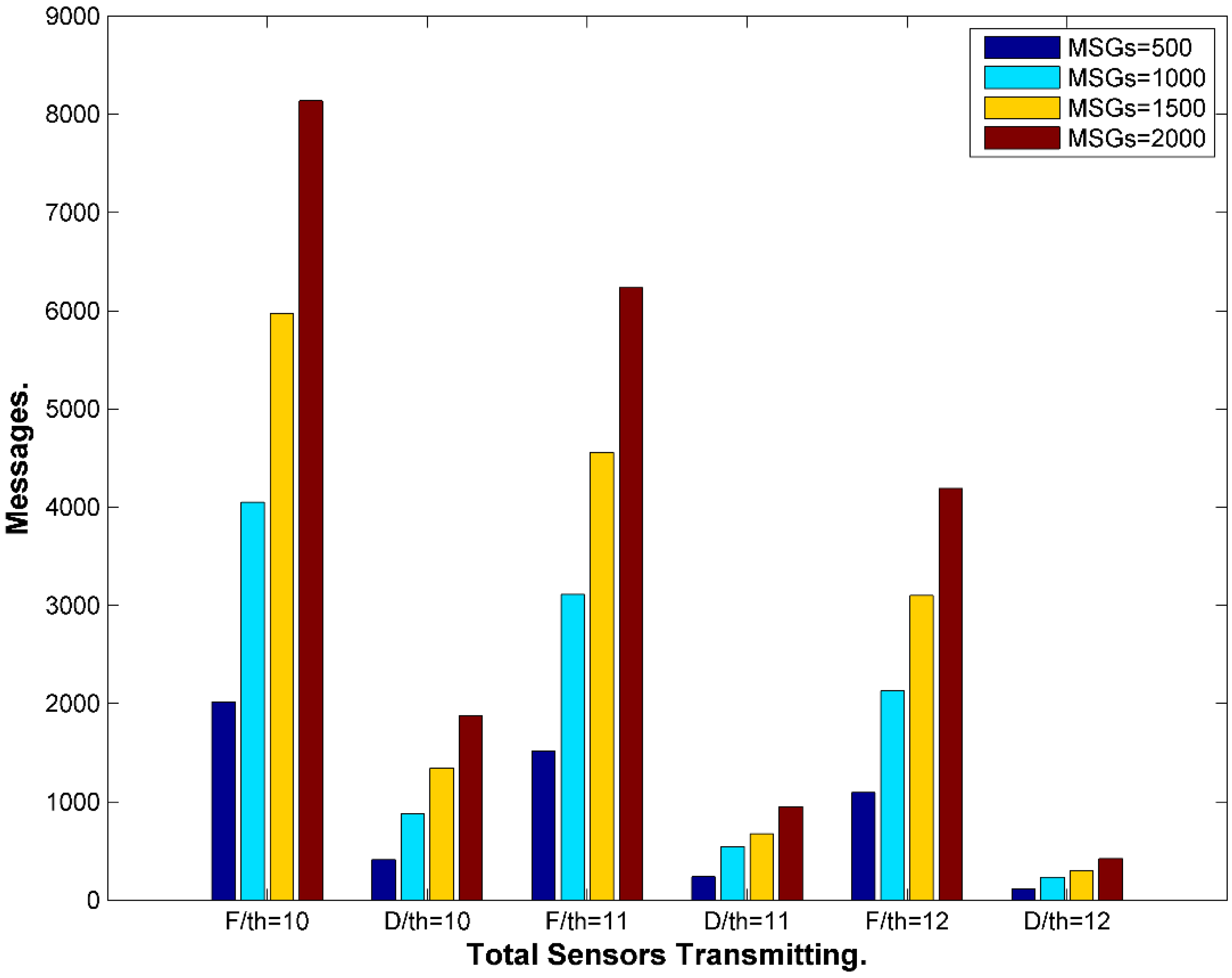
9.4. Storage Evaluation
| No. | Scheme | Storage Cost (bits) | Computation Cost |
|---|---|---|---|
| 1 | SAS | 2nN + 4nNave + 16 | No hashing operations |
| 2 | CAS | 6n + 7nNave + 16 | Two hashing orations and two encryptions |
| 3 | HIR | 2n + 2nNave | One hashing function |
| 4 | RHIR | 2n + 2nNave + nkNave | No hashing functions |
| 5 | APR | 9n + 7nNave + 2N − 2Nave − 2 | Six hashing functions |
| 6 | DCARPS | 3n | No hashing functions |
| 7 | ACS | 5nNave | Two hashing functions |
| 8 | PhID | (3n + 2) × Nave | Four hashing function |
| 9 | EAC | 6n + 6nNave + 2 | Four hashing operations |
| 10 | FAC | 10n + (7n + 16) × Nave | Four hashing operations & Oh encryptions |
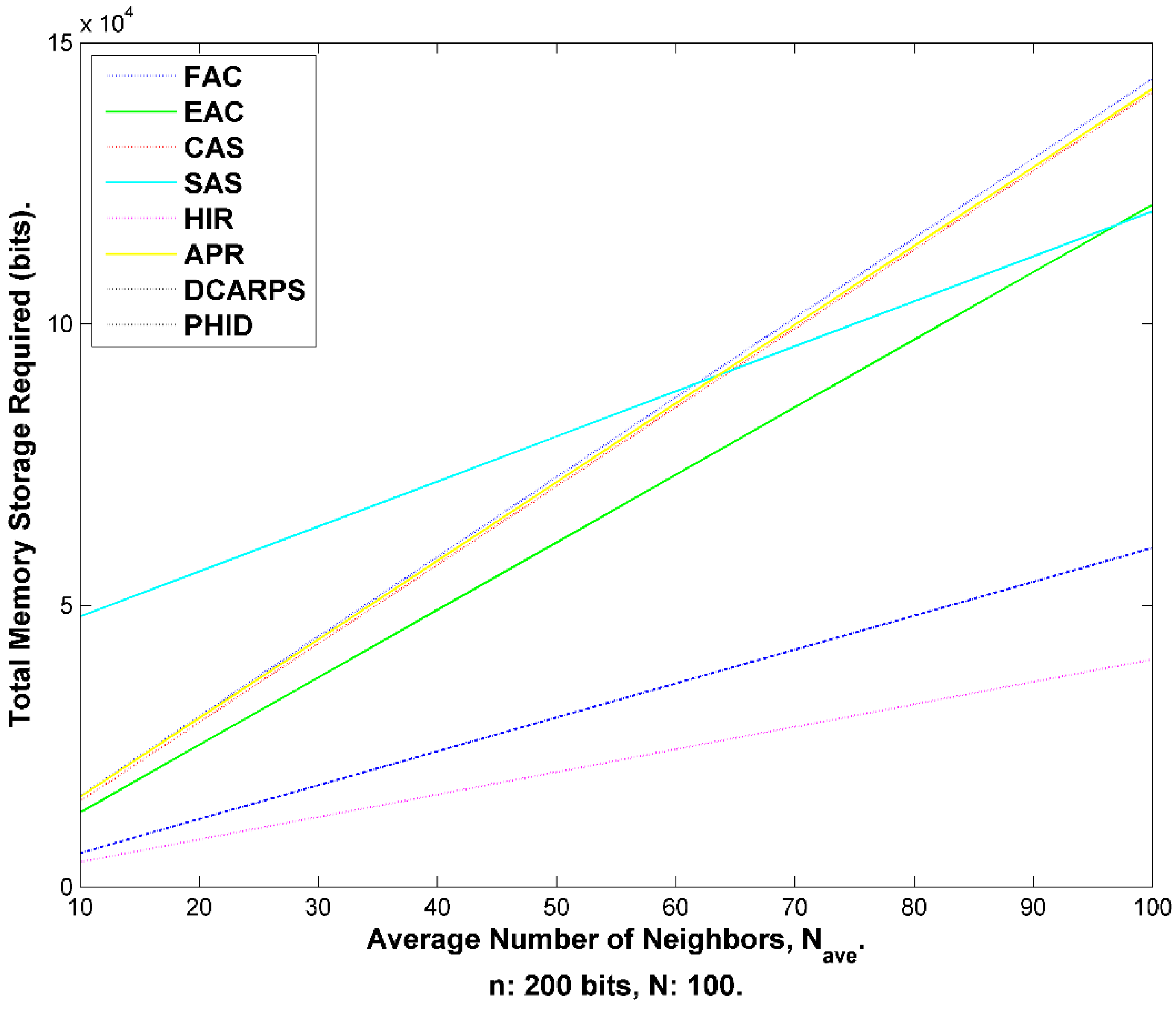
9.5. Processing and Computational Evaluation
10. Conclusions and Future Work
Author Contributions
Conflicts of Interest
References
- Eu, Z.A.; Tan, H.-P.; Seah, W.K.G. Design and Performance analysis of MAC Schemes for Wireless Sensor Networks Powered by Ambient Energy Harvesting. Ad Hoc Netw. 2011, 9, 300–323. [Google Scholar] [CrossRef]
- Noh, D.K.; Hur, J. Using a dynamic backbone for efficient data delivery in solar-powered WSNs. J. Netw. Comput. Appl. 2012, 35, 1277–1284. [Google Scholar] [CrossRef]
- Li, Y.; Ren, J. Providing Source-Location Privacy in Wireless Sensor Networks. In Wireless Algorithms, Systems, and Applications; Liu, B., Bestavros, A., Du, D.-Z., Wang, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5682, pp. 338–347. [Google Scholar]
- Conti, M.; Willemsen, J.; Crispo, B. Providing Source Location Privacy in Wireless Sensor Networks: A Survey. IEEE Commun. Surv. Tutor. 2013, 15, 1238–1280. [Google Scholar] [CrossRef]
- Abbasi, A.; Khonsari, A.; Talebi, M.S. Source Location Anonymity for Sensor Networks. In Proceediongs of the 6th IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 10–13 January 2009.
- Nezhad, A.A.; Miri, A.; Makrakis, D. Location privacy and anonymity preserving routing for wireless sensor networks. Comput. Netw. 2008, 52, 3433–3452. [Google Scholar] [CrossRef]
- Yao, L.; Kang, L.; Shang, P.; Wu, G. Protecting the sink location privacy in wireless sensor networks. Pers. Ubiquitous Comput. 2013, 17, 883–893. [Google Scholar] [CrossRef]
- Li, N.; Zhang, N.; Das, S.K.; Thuraisingham, B. Privacy preservation in wireless sensor networks: A state-of-the-art survey. Ad Hoc Netw. 2009, 7, 1501–1514. [Google Scholar] [CrossRef]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A survey on trust management for Internet of Things. J. Netw. Comput. Appl. 2014, 42, 120–134. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Kamat, P.; Zhang, Y.; Trappe, W.; Ozturk, C. Enhancing Source-Location Privacy in Sensor Network Routing. In Proceedings of the 25th IEEE International Conference on Distributed Computing Systems (ICDCS), Columbus, OH, USA, 10 June 2005.
- Ozturk, C.; Zhang, Y.; Trappe, W.; Ott, M. Source-Location Privacy for Networks of Energy-Constrained Sensors. In Proceediongs of the Second IEEE Workshop on Software Technologies for Future Embedded and Ubiquitous Systems, Vienna, Austria, 11–12 May 2004.
- Jing, D.; Han, R.; Mishra, S. Countermeasures against Traffic Analysis Attacks in Wireless Sensor Networks. In Proceediongs of the First International Conference on Security and Privacy for Emerging Areas in Communications Networks, Washington, DC, USA, 5–9 September 2005.
- Ying, J.; Shigang, C.; Zhan, Z.; Liang, Z. A novel scheme for protecting receiver's location privacy in wireless sensor networks. IEEE Trans. Wirel. Commun. 2008, 7, 3769–3779. [Google Scholar] [CrossRef]
- Xinfeng, L.; Xiaoyuan, W.; Nan, Z.; Zhiguo, W.; Ming, G. Enhanced Location Privacy Protection of Base Station in Wireless Sensor Networks. In Proceedings of the 5th International Conference on Mobile Ad-hoc and Sensor Networks MSN, Fujian, China, 14–16 December 2009.
- Chen, J.; Du, X.; Fang, B. An efficient anonymous communication protocol for wireless sensor networks. Wirel. Commun. Mob. Comput. 2012, 12, 1302–1312. [Google Scholar] [CrossRef]
- Ouyang, Y.; Le, Z.; Liu, D.; Ford, J.; Makedon, F. Source Location Privacy against Laptop-Class Attacks in Sensor Networks. In Proceedings of the 4th International Conference on Security and Privacy in Communication Netowrks, Istanbul, Turkey, 22 September 2008; pp. 1–10.
- Xiaoyan, H.; Pu, W.; Jiejun, K.; Qunwei, Z.; Jun, L. Effective Probabilistic Approach Protecting Sensor Traffic. In Proceedings of the IEEE Military Communications Conference (MILCOM), Atlantic City, NJ, USA, 17–20 October 2005.
- Kamat, P.; Xu, W.; Trappe, W.; Zhang, Y. Temporal privacy in wireless sensor networks: Theory and practice. ACM Trans. Sen. Netw. 2009, 5, 1–24. [Google Scholar] [CrossRef]
- Xue, G.; Misra, S. Efficient anonymity schemes for clustered wireless sensor networks. Int. J. Sens. Netw. 2006, 1, 50–63. [Google Scholar] [CrossRef]
- Yi, O.; Zhengyi, L.; Yurong, X.; Triandopoulos, N.; Sheng, Z.; Ford, J.; Makedon, F. Providing Anonymity in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Pervasive Services, Istanbul, Turkey, 15–20 July 2007.
- Jang-Ping, S.; Jehm-Ruey, J.; Ching, T. Anonymous Path Routing in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Communications (ICC), Beijing, China, 19–23 May 2008.
- Xi, L.; Xu, J.; Myong-Soon, P. Location Privacy against Traffic Analysis Attacks in Wireless Sensor Networks. In Proceedings of the International Conference on Information Science and Applications (ICISA), Seoul, Korea, 21–23 April 2010.
- Di Pietro, R.; Viejo, A. Location privacy and resilience in wireless sensor networks querying. Comput. Commun. 2011, 34, 515–523. [Google Scholar]
- Park, J.-H.; Jung, Y.-H.; Ko, H.; Kim, J.-J.; Jun, M.-S. A Privacy Technique for Providing Anonymity to Sensor Nodes in a Sensor Network. In Ubiquitous Computing and Multimedia Applications; Kim, T.-H., Adeli, H., Robles, R.J., Balitanas, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 327–335. [Google Scholar]
- Juan, C.; Hongli, Z.; Binxing, F.; Xiaojiang, D.; Lihua, Y.; Xiangzhan, Y. Towards Efficient Anonymous Communications in Sensor Networks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM), Houston, TX, USA, 5–9 December 2011.
- Abuzneid, A.; Sobh, T.; Faezipour, M. An Enhanced Communication Protocol for Anonymity and Location Privacy in WSN. In Proceedings of the IEEE Wireless Communications and Networking Conference, New Orleans, LA, USA, 9–12 March 2015.
- Kong, J.; Hong, X. ANODR: Anonymous on Demand Routing with Untraceable Routes for Mobile ad-hoc Networks. In Proceedings of the 4th ACM International Symposium on Mobile ad hoc Networking & Computing, Annapolis, MA, USA, 1–3 June 2003; pp. 291–302.
- Kerckhoffs’ Principle. Available from: http://en.citizendium.org/wiki/Kerckhoffs%27_Principle (accessed on 1 March 2015).
- Yanchao, Z.; Wei, L.; Wenjing, L.; Yuguang, F. Location-based compromise-tolerant security mechanisms for wireless sensor networks. IEEE J. Sel. Areas Commun. 2006, 24, 247–260. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhang, C.; Zhu, H.; Ho, P.; Shen, X. AICN: An Efficient Algorithm to Identify Compromised Nodes in Wireless Sensor Network. In Proceedings of the IEEE International Conference on Communications (ICC), Beijing, China, 19–23 May 2008.
- Song, H.; Xie, L.; Zhu, S.; Cao, G. Sensor Node Compromise Detection: the Location Perspective. In Proceedings of the 2007 International Conference on Wireless Communications and Mobile Computing, Honolulu, HI, USA, 12 August 2007; pp. 242–247.
- Tao, L.; Min, S.; Alam, M. Compromised Sensor Nodes Detection: A Quantitative Approach. In Proceedings of the 28th International Conference on Distributed Computing Systems Workshops (ICDCS), Beijing, China, 17–20 June 2008.
- Alomair, B.; Clark, A.; Cuellar, J.; Poovendran, R. Toward a Statistical Framework for Source Anonymity in Sensor Networks. IEEE Trans. Mob. Comput. 2013, 12, 248–260. [Google Scholar] [CrossRef]
- Zhu, S.; Setia, S.; Jajodia, S. LEAP+: Efficient security mechanisms for large-scale distributed sensor networks. ACM Trans. Sen. Netw. 2006, 2, 500–528. [Google Scholar] [CrossRef]
- Mabrouki, I.; Belghith, A. E-SeRLoc: An Enhanced Serloc Localization Algorithm with Reduced Computational Complexity. In Proceedings of the 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013.
- Lazos, L.; Poovendran, R. SeRLoc: Secure Range-Independent Localization for Wireless Sensor Networks. In Proceedings of the 3rd ACM Workshop on Wireless Security, 1 October 2004; ACM: Philadelphia, PA, USA, 2004; pp. 21–30. [Google Scholar]
- Zheng, W.; Gao, S.; Qiu, L.; Zhang, W. A CDS-based Topology Control Algorithm in Energy Efficient Clustering. In Proceedings of the 31st Chinese Control Conference (CCC), Hefei, China, 25–27 July 2012.
- Hongwei, D.; Weili, W.; Qiang, Y.; Deying, L.; Wonjun, L.; Xuepeng, X. CDS-Based Virtual Backbone Construction with Guaranteed Routing Cost in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 652–661. [Google Scholar] [CrossRef]
- Abduvaliyev, A.; Pathan, A.S.K.; Jianying, Z.; Roman, R.; Wai-Choong, W. On the Vital Areas of Intrusion Detection Systems in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2013, 15, 1223–1237. [Google Scholar] [CrossRef]
- YangXia, L.; Ye, G. A Survey on Intrusion Detection of Wireless Sensor Network. In Proceedings of the 2nd International Conference on Information Science and Engineering (ICISE), Hangzhou, China, 4–6 December 2010.
- Abuzneid, A.; Sobh, T.; Faezipour, M. Temporal Privacy Scheme for End-to-End Location Privacy in Wireless Sensor Networks. In IEEE Electrical, Electronics, Signals, Communiction & Optimization, Visakhapatnam, Andhra Pradesh, India, 24–25 January 2015; pp. 2476–2481.
- Mehta, K.; Donggang, L.; Wright, M. Location Privacy in Sensor Networks Against a Global Eavesdropper. In Proceedings of the IEEE International Conference on Network Protocols (ICNP), Beijing, China, 16–19 October 2007.
- Alomair, B.; Clark, A.; Cuellar, J.; Poovendran, R. Statistical Framework for Source Anonymity in Sensor Networks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM), Miami, FL, USA, 6–10 December 2010.
- Wu, P.-C. Multiplicative, congruential random-number generators with multiplier. ACM Trans. Math. Softw. 1997, 23, 255–265. [Google Scholar] [CrossRef]
- Deng, L.-Y.; Rousseau, C.; Yuan, Y. Generalized Lehmer-Tausworthe Random Number Generators. In Proceedings of the 30th Annual Southeast Regional Conference, Raleigh, NC, USA, 8 April 1992; pp. 108–115.
- Payne, W.H.; Rabung, J.R.; Bogyo, T.P. Coding the Lehmer pseudo-random number generator. ACM Commun. 1969, 12, 85–86. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-Efficient Communication Protocol for Wireless Microsensor Networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Hawaii, HI, USA, 4–7 January 2000.
- Abuhelaleh, M.A.; Mismar, T.M.; Abuzneid, A.A. Armor-LEACH—Energy Efficient, Secure Wireless Networks Communication. In Proceedings of 17th International Conference on Computer Communications and Networks (ICCCN), St. Thomas, USVI, USA, 3–7 August 2008.
- Stallings, W. Network Security Essentials Applications and Standards, 5th ed.; Prentice Hall: Upper Saddle River, NJ, USA, 2014. [Google Scholar]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abuzneid, A.-S.; Sobh, T.; Faezipour, M.; Mahmood, A.; James, J. Fortified Anonymous Communication Protocol for Location Privacy in WSN: A Modular Approach. Sensors 2015, 15, 5820-5864. https://doi.org/10.3390/s150305820
Abuzneid A-S, Sobh T, Faezipour M, Mahmood A, James J. Fortified Anonymous Communication Protocol for Location Privacy in WSN: A Modular Approach. Sensors. 2015; 15(3):5820-5864. https://doi.org/10.3390/s150305820
Chicago/Turabian StyleAbuzneid, Abdel-Shakour, Tarek Sobh, Miad Faezipour, Ausif Mahmood, and John James. 2015. "Fortified Anonymous Communication Protocol for Location Privacy in WSN: A Modular Approach" Sensors 15, no. 3: 5820-5864. https://doi.org/10.3390/s150305820
APA StyleAbuzneid, A.-S., Sobh, T., Faezipour, M., Mahmood, A., & James, J. (2015). Fortified Anonymous Communication Protocol for Location Privacy in WSN: A Modular Approach. Sensors, 15(3), 5820-5864. https://doi.org/10.3390/s150305820