Abstract
User authentication and key management are two important security issues in WSNs (Wireless Sensor Networks). In WSNs, for some applications, the user needs to obtain real-time data directly from sensors and several user authentication schemes have been recently proposed for this case. We found that a two-factor mutual authentication scheme with key agreement in WSNs is vulnerable to gateway node bypassing attacks and user impersonation attacks using secret data stored in sensor nodes or an attacker's own smart card. In this paper, we propose an improved scheme to overcome these security weaknesses by storing secret data in unique ciphertext form in each node. In addition, our proposed scheme should provide not only security, but also efficiency since sensors in a WSN operate with resource constraints such as limited power, computation, and storage space. Therefore, we also analyze the performance of the proposed scheme by comparing its computation and communication costs with those of other schemes.1. Introduction
A wireless sensor network (WSN) is composed of a number of sensors (tens to thousands) that are deployed to collect data in a target area [1,2]. The number of potential applications for WSNs is increasing in various fields, including environmental monitoring, healthcare, agriculture, manufacturing, military sensing and tracking, and disaster alert [1–5]. The design of a specific WSN is dependent on the given application and the environment under which it operates [1]. In addition, sensors in a WSN operate with resource constraints such as limited power, computation, and storage space [1,3,6–8]. In WSNs, user queries are generally transmitted to the gateway [1,3,8,9]. However, for some applications, the user needs to obtain real-time data directly from sensors [1,3,8,9]. In this case, only legitimate users should be able to access the WSN.
Several schemes for user authentication in WSNs have been proposed recently. Wong et al. [10] proposed a user authentication scheme that uses only one-way hash functions for computation efficiency on sensor nodes [10]. However, Das [3] pointed out that Wong et al.'s scheme does not prevent many logged-in users with the same login-ID threats and stolen-verifier attacks [3]. Das [3] proposed a two-factor user authentication in WSNs using a smart card and a password instead of maintaining a password/verifier table [3]. Other researchers, however, pointed out that Das' scheme still has security flaws. Chen and Shih [11] insisted that Das' scheme does not provide mutual authentication, and proposed a mutual authentication scheme between the user, the gateway, and the sensor node [11]; He et al. [9] said that Das' scheme has security weaknesses against insider attacks and impersonation attacks [9]; and Khan and Alghathbar [4] pointed out that Das' scheme is vulnerable to gateway node bypassing attacks and privileged-insider attacks [4]. In 2012, Vaidya et al. [12] pointed out that the schemes proposed by Das [3], Kan and Alghathbar [4] and Chen and Shih [11] are all insecure against stolen smart card attacks and sensor node impersonation attacks with node capture attacks and do not provide key agreement [12]. Therefore, they proposed a novel two-factor mutual authentication and key agreement scheme to prevent these attacks. In addition, they insisted that computational costs for gateway and sensor nodes in their proposed scheme are not so high. However, we found that their proposed scheme still has security flaws.
In this paper, we present that gateway node bypassing attacks and user impersonation attacks are possible using secret data stored in a sensor or an attacker's own smart card in Vaidya et al.'s scheme. Additionally, we propose an improved scheme that eliminates such security weaknesses from Vaidya et al.'s scheme. We verify that the proposed scheme is secure against possible attacks. We also analyze the performance of the proposed scheme by comparing its computation cost and communication cost with those of other schemes.
The remainder of the paper is organized as follows. Section 2 presents a review of Vaidya et al.'s scheme. Section 3 is devoted to analyzing the security of Vaidya et al.'s scheme. Section 4 proposes the improved scheme. Section 5 analyzes the security of the proposed scheme against possible attacks. Section 6 is devoted to analyzing the performance of the proposed scheme and Section 7 concludes this paper.
2. Review of Vaidya et al.'s Scheme
There are three communication parties in Vaidya et al.'s scheme [12]: a user, a gateway node, and a sensor node. This scheme is composed of four phases: registration phase, login phase, authentication-key agreement phase, and password change phase. We describe each phase in detail in Sections 2.1–2.4, and Table 1 shows the notations used in the remainder of the paper.

Registration phase begins when the user sends a registration request with his/her identity and a hashed password to the gateway node. Then, the gateway node personalizes a smart card for the user and sends it to him/her as a response to the registration request. In the registration phase, all these communication messages are transmitted in secure channels.
Login phase begins when the user inserts his/her smart card into the terminal and inputs his/her identity and password. After the verification of the user's input value, the smart card computes and sends the authentication request to the gateway node. When the gateway node receives the authentication request from the user side, the authentication-key agreement phase begins. The gateway node verifies whether the authentication request comes from a legitimate user. If the verification is successful, the gateway node sends the authentication request to a sensor node which can respond to a request or a query from the user. In this phase, three authentication requests are transmitted. The first request is from the gateway node to the sensor node, the second is from the sensor node to the gateway node, and the final is from the gateway node to the user. As stated, when one party receives an authentication request, the party verifies its validity and sends a new authentication request to the other party. In login phase and authentication-key agreement phase, these request messages are transmitted in insecure channels. If all verifications are passed successfully, the user and the sensor node then share the session key for communication. The password change phase begins whenever the user wants to change his/her password. In the password change phase, the user side does not have to communicate with other parties.
2.1. Registration Phase
We describe the registration phase in this subsection. Ui selects IDi and pwi, computes H_PWi=h(pwi) and sends the registration request {IDi,h(pwi)} to GW. Then, GW personalizes a smart card for Ui and sends it to Ui. Figure 1 shows the registration phase of Vaidya et al.'s scheme.
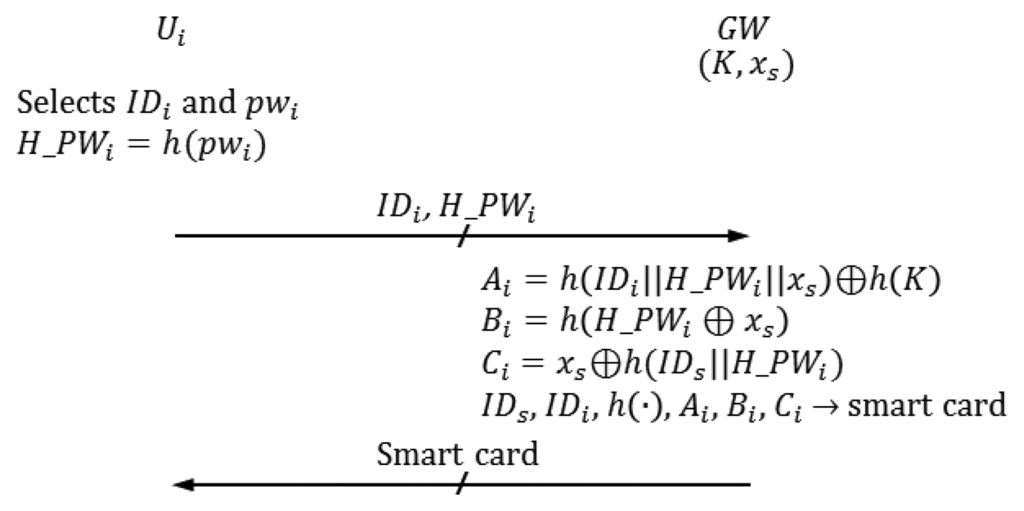
| R-1 | Ui selects IDi and.PWi |
| R-2 | Ui computes H_PWi=h(pwi) |
| Ui sends a registration request {IDi, H_PWi} to GW in secure channels (it was not mentioned whether the registration request from Ui to GW is sent by secure channels [12], but we guess that it is sent this way). | |
| R-3 | GW computes the following when it receives the registration request from Ui. |
| Ai=h(IDi∥H_PWi∥xs)⊕h(K) | |
| Bi=h(H_PWi⊕xs) | |
| Ci=xs⊕h(IDs∥H_PWi) | |
| GW personalizes the smart card with IDs, IDi, h(·), Ai, Bi and Ci. | |
| GW sends the smart card to Ui in secure channels. | |
Meanwhile, SIDj and a secret value xs generated by GW are stored in Sj before it is deployed into a target field.
2.2. Login Phase
The login phase begins when Ui inserts Ui's smart card into a terminal and inputs and . In this phase, Ui sends the authentication request to GW. Figure 2 illustrates the login phase of Vaidya et al.'s scheme.
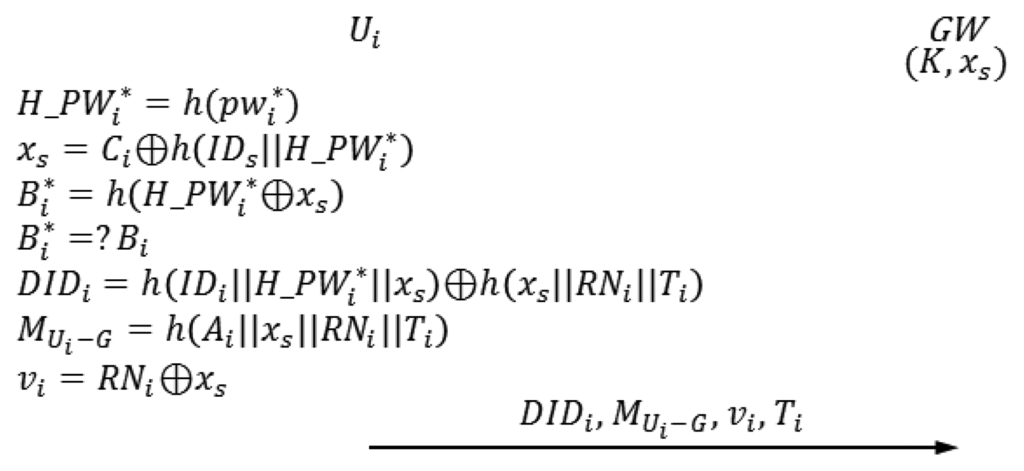
| L-1 | Ui inserts Ui's smart card into a terminal and inputs and |
| L-2 | The smart card computes the following. |
| The smart card compares with Bi. If, , then the next step proceeds; otherwise, this phase is aborted. | |
| L-3 | The smart card generates a random nonce RNi and computes the following. Ti is the current timestamp of Ui system. |
| MUi−G=h(Ai∥xs∥RNi∥Ti) | |
| vi=RNi⊕xs | |
| The smart card sends the authentication request {DIDi, MUi−G, vi, Ti} to GW. | |
2.3. Authentication-Key Agreement Phase
When GW receives the authentication request from Ui, the authentication-key agreement phase begins. In this phase, Ui, GW, Sj and send and receive authentication requests from one another. Figure 3 depicts the authentication-key agreement phase of Vaidya et al.'s scheme. The following describes this process in detail.
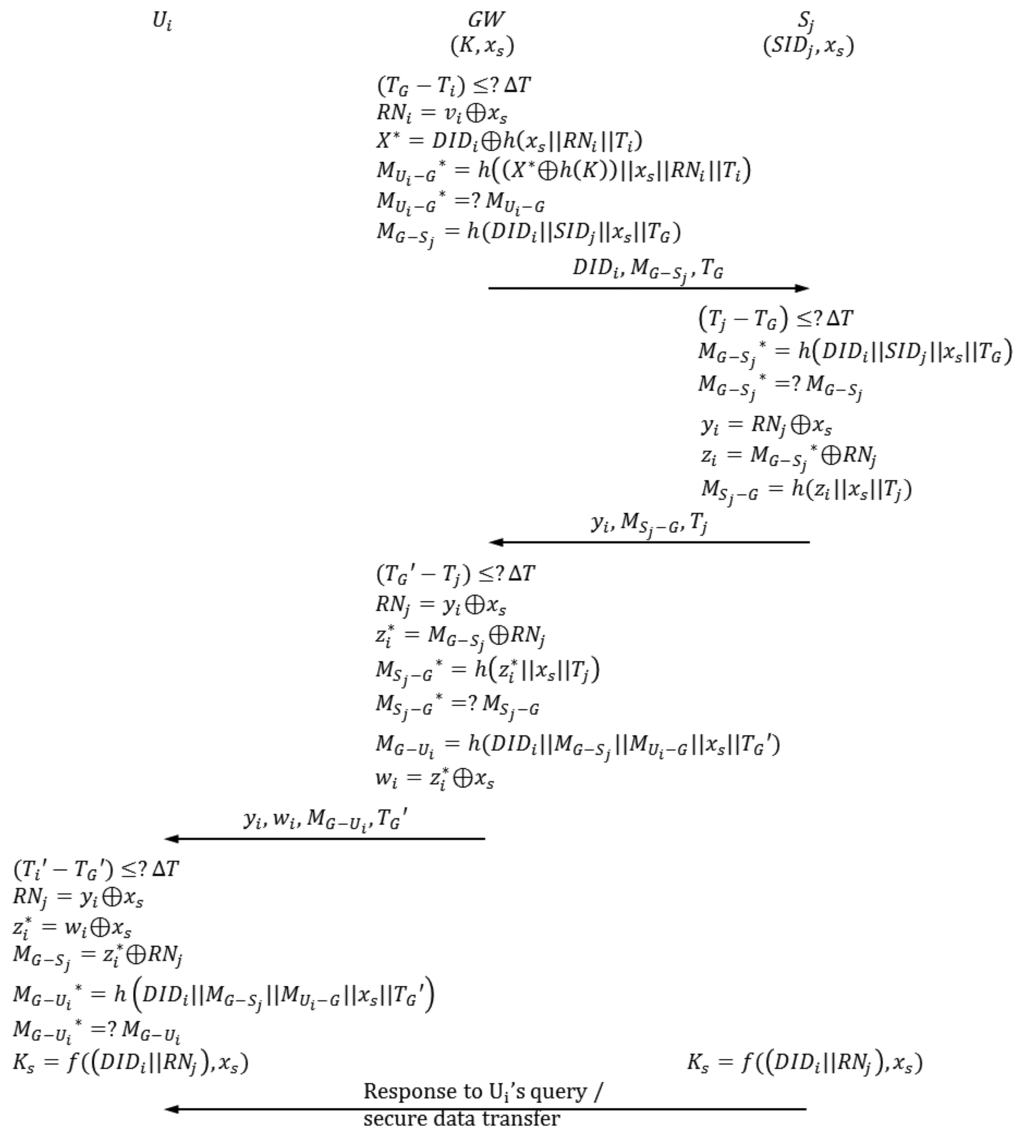
| A-1 | GW checks if (TG−Ti) ≤ ΔT, where TG is the current timestamp of GW system, and ΔT is the maximum permitted transmission delay time. If (TG−Ti) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. |
| A-2 | GW computes the following. |
| RNi=vi⊕xs | |
| X*=DIDi⊕h(xs∥RNi∥Ti) | |
| MUi−G*=h((X*⊕h(K))∥xs∥RNi∥Ti) | |
| GW compares MUi−G* with MUi−G*. If MUi−G* =MUi−G, then the next step proceeds; otherwise, this phase is aborted. | |
| A-3 | GW computes MG−Sj=h(DIDi∥SIDj∥xs∥TG). TG is the current timestamp of GW system. Sj is the nearest sensor node that can respond to Ui's request. |
| GW sends the authentication request {DIDi, MG−Sj, TG} to Sj. | |
| A-4 | GW checks if (Tj − TG) ≤ ΔT, where Tj is the current timestamp of Sj system. |
| If (Tj −TG) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. | |
| A-5 | Sj computes MG−Sj*=h(DIDi∥SIDj∥xs∥TG). |
| Sj compares MG−Sj* with MG−Sj. If MG−Sj* = MG−Sj, then the next step proceeds; otherwise, this phase is aborted. | |
| A-6 | Sj generates a random nonce RNj and computes the following. |
| yi = RNj⊕xs | |
| zi = MG−Sj*⊕RNj | |
| MSj−G = h(zi∥xs∥Tj) | |
| Sj sends the authentication request {yi, MSj−G, Tj} to GW. | |
| A-7 | GW checks if (TG′ − Tj) ≤ ΔT, where TG′ is the current timestamp of GW system. |
| If (TG′−Tj) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. | |
| A-8 | GW computes the following. |
| RNj=yi ⊕ xs | |
| GW compares MSj−G* with MSj−G. If MSj−G* = MSj−G, then the next step proceeds; otherwise, this phase is aborted. | |
| A-9 | GW computes the following. |
| MG−Ui = h(DIDi∥MG−Sj∥MUi−G∥xs∥TG′) | |
| GW sends the authentication request {yi, wi, MG−Ui, TG′} to Ui. | |
| A-10 | Ui checks if (Ti′ − TG′) ≤ ΔT, where Ti′ is the current timestamp of Ui system. If (Ti′ − TG′) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. |
| A-11 | The smart card computes the following. |
| RNj = yi ⊕ xs | |
| MG−Ui* = h(DIDi∥MG−Sj∥MUi−G∥xs∥TG′) | |
| The smart card compares MG−Ui* with MG−Ui. If MG−Ui* = MG−Ui, then mutual authentication between Ui and Sj is completed successfully; otherwise, this phase is aborted. | |
| A-12 | The smart card computes Ks = f((DIDi∥RNi),xs) to obtain a session key for communication with Sj. Meanwhile, Sj also computes KS = f((DIDi∥RNi),xs) to share a session key with Ui. |
2.4. Password Change Phase
The password change phase proceeds when Ui changes Ui's existing password to a new one. In the password change phase, Ui does not communicate with GW.
| P-1 | Ui inserts Ui's smart card into a terminal and inputs, , , and pwni. pwni is Ui's new password. |
| P-2 | The smart card computes the following. |
| The smart card compares with Bi. If , then the next step proceeds; otherwise, this phase is aborted. | |
| P-3 | The smart card computes the following. |
| Bni=h(H_PWni⊕xs) | |
| Cni=xs⊕h(IDs∥H_PWni) | |
| The smart card replaces the existing values Ai, Bi, and Ci with the new values Ani, Bni, and Cni. | |
3. Security Analysis of Vaidya et al.'s Scheme
In this section, we analyze the security of Vaidya et al.'s scheme. We found that gateway node bypassing attacks are possible in Vaidya et al.'s scheme if an attacker captures a sensor node and extracts secret values stored in it. Additionally, an attacker can know secret values xs and h(K) from the attacker's own smart card and use them for user impersonation attacks or gateway node bypassing attacks.
In Sections 3.1–3.3, we describe possible attacks in Vaidya et al.'s scheme in detail. We assume that an attacker can eavesdrop on or intercept all messages sent or received between communication parties. We also assume that an attacker can read data stored in a smart card in any manner like in the related works [2,6,13–16]. In addition, we have to note that data stored in sensor nodes are not secure since an attacker can capture sensor nodes that are deployed in unattended environments and can then extract data from them.
3.1. Gateway Node Bypassing Attacks Using Secret Data Stored in a Sensor Node
In Vaidya et al.'s scheme, if an attacker extracts the secret data xs from a sensor node, he/she can impersonate GW and communicate with Ui. These attacks proceed as explained below. Uα denotes an attacker here.
| Step 1 | Uα extracts xs and SIDj from a sensor node captured in the WSN. |
| Step 2 | Login phase begins when Ui wants to access to the WSN as in Section 2.2. When Ui sends the authentication request {DIDi, MUi−G, vi, Ti} to GW, Uα eavesdrops on it. |
| Step 3 | Uα computes the following using xs, SIDj and {DIDi, MUi−G, vi, Ti}. Tα and Tα′ denote the current timestamp of Uα system, and Tα < Tα′. Uα generates a random nonce RNα. |
| yi=RNα⊕xs | |
| MG-Sj = h(DIDi∥SIDj ∥xs ∥Tα) | |
| MG−Ui*=h(DIDi∥MG−Sj∥MUi−G∥xs∥Tα′) | |
| Uα forges the authentication request sent from GW to Ui in authentication-key agreement phase using {yi, wi, MG−Ui),Tα′}. | |
| Step 4 | When Ui receives {yi, wi, MG−Ui, Tα′} from Uα, Ui checks if (TU′−Tα′) ≤ ΔT, where (TU′ is the current timestamp of Ui system. If (TU′−Tα′) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. |
| Step 5 | The smart card computes the following. |
| RNα = yi ⊕ xs | |
| MG−Ui*=h(DIDi∥MG−Sj∥MUi−G∥xs∥Tα′) | |
| The smart card compares MG−Uiwith MG−Ui*. Since MG−Ui = MG−Ui*, Ui regards {yi, wi, MG−Ui,Tα′} as being transmitted from GW. Therefore, Uα can communicate with Ui using the session key Ks = f((DIDi∥RNα), xs). | |
3.2. User Impersonation Attacks Using an Attacker's Own Smart Card
If an attacker Uα registers with GW, Uα receives the smart card personalized with Uα's own identity and password, IDα and pwα. Uα can compute xs and h(K) using IDα, pwα, and secret values stored in the smart card.
| Step 1 | As shown in the Section 2.1, Uα selects IDα and pwα. |
| Step 2 | Uα computes H_PWα=h(pwα). |
| Uα sends the registration request {IDα, h(pwα)} to GW. | |
| Step 3 | GW computes the following when it receives the registration request from Uα. |
| Aα = h(IDα∥H_PWα∥xs)⊕h(K) | |
| Bα=h(H_PWα⊕xs) | |
| Cα=xs ⊕ h(IDs∥H_PWα) | |
| GW personalizes the smart card with IDs, IDα, h(·), Aα, Bα and Cα. | |
| GW sends the smart card to Uα. | |
| Step 4 | Uα reads IDs, IDα, Aα, Bα, and Cα from the smart card. |
| Uα can know xs and h(K) by computing the following. | |
| xs= Cα ⊕ h(IDs∥H_PWα) | |
| h(K) = Aα ⊕ h(IDα∥H_PWα∥ xs) | |
Uα can impersonate a legitimate user who has registered with GW using xs and h(K). In addition, Uα can also log in with any temporary identity that does not actually exist.
3.2.1. Logging in with Any Temporary Identity
We describe the process where Uα logs in with any temporary identity that does not actually exist using xs and h(K).
| Step 1 | Uα selects any temporary identity and password IDβ and pwβ. Uα computes the authentication request as follows. Tα denotes the current timestamp of Uα system, and RNα is a random nonce generated by Uα. |
| MUβ−G=h(Aβ∥xs∥RNα∥Tα) | |
| vβ=RNα ⊕ xs | |
| Uα sends the authentication request {DIDβ, MUβ−G, vβ, Tα} to GW. | |
| Step 2 | When GW receives the authentication request, GW checks if (TG−Tα) ≤ ΔT, where TG is the current timestamp of GW system. If (TG−Tα) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. |
| Step 3 | GW computes the following. |
| RNα=vβ⊕ xs | |
| X*=DIDβ ⊕ h(xs∥RNα∥Tα) | |
| MUβ−G* = h((X* ⊕ h(K))∥xs∥RNα∥Tα) | |
| GW compares MUβ−G with MUβ−G*. GW regards {DIDβ, MUβ−G, vβ, Tα} as being sent from a legitimate user because MUβ−G = MUβ−G*. | |
3.2.2. Logging in with the Identity of a Legitimate User
We describe when Uα impersonates a legitimate user Ui who has registered with GW using xs and h(K).
| Step 1 | In the previous session, when Ui sends the authentication request {DIDi, MUi−G, vi, Ti} to GW as shown in Section 2.2, Uα eavesdrops on it. |
| Step 2 | Uα computes the following. RNα is a random nonce generated by Uα. Tα is the current timestamp of Uα system. xs and h(K) are already known to Uα, as mentioned above. |
| RNi=vi ⊕ xs | |
| MUi−G = h(Ai∥xs∥RNα∥Tα) | |
| vi = RNα ⊕ xs | |
| Uα sends the authentication request {DIDi, MUi−G, vi, Tα} to GW. | |
| Step 3 | When GW receives {DIDi, MUi−G, vi, Tα}, GW checks if (TG−Tα) ≤ ΔT, where TG is the current timestamp of GW system. If (TG−Tα) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. |
| Step 4 | GW computes the following. |
| RNα = vi ⊕ xs | |
| X*=DIDi ⊕ h(xs∥RNα∥Tα) | |
| MUi−G* = h((X* ⊕ h(K))∥xs∥RNα∥Tα) | |
| GW compares MUi−G with MUi−G*. GW regards {DIDi, MUi−G, vi, Tα} as being sent from a legitimate user because MUi−G=MUi−G*. | |
3.3. Gateway Node Bypassing Attacks Using an Attacker's Own Smart Card
As discussed in Section 3.2, if an attacker Uα obtains xs and h(K) using data stored in his/her own smart card, he/she can impersonate GW. The following shows the attack process in detail. Uα denotes an attacker here.
| Step 1 | Login phase begins when Ui wants to access the WSN as described in Section 2.2.When Ui sends the authentication request {DIDi, MUi−G, vi, Ti} to GW, Uα eavesdrops on the transmission. |
| Step 2 | Uα computes the following using xs and {DIDi, MUi−G, vi, Ti}. Tα and Tα′ denote the current timestamp of Tα system, and Tα < Tα′. Uα generates a random nonce RNα. SIDα is created by Uα. |
| yi = RNα ⊕ xs | |
| MG−Sj = h(DIDi∥SIDα∥xs∥Tα) | |
| MG−Ui = h(DIDi∥MG−Sj∥MUi−G∥xs∥Tα′) | |
| Uα forges the authentication request sent from GW to Ui in authentication-key agreement phase using {yi, wi, MG−Ui, Tα′}. | |
| Step 3 | When Ui receives {yi, wi, MG−Ui, Tα′} from Uα, Ui checks if (TU′ − Tα′) ≤ ΔT, where TU′ is the current timestamp of Ui system. If (TU′ − Tα′) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. |
| Step 4 | The smart card computes the following. |
| RNα = yi ⊕ xs | |
| MG−Ui*=h(DIDi∥MG−Sj∥MUi−G∥xs∥Tα′) | |
| The smart card compares MG−Uiwith MG−Ui*. Since MG−Ui=MG−Ui*, Ui regards {yi, wi, MG−Ui,Tα′} as being transmitted from GW. Therefore, Uα can communicate with Ui using the session key Ks = f((DIDi∥RNα), xs). | |
4. The Proposed Scheme
In this section, we propose an improved scheme that can overcome the security weaknesses presented in Section 3. The reason why Vaidya et al.'s scheme is vulnerable to sensor node capture attacks is that xs is stored in plaintext form in Sj though it is a secret value. To make matters worse, xs is shared between all sensor nodes in the WSN. Also, in Vaidya et al.'s scheme, an attacker can compute and use xs and h(K) for attacks because they are stored in all users' smart cards. Therefore, the main ideas of our proposed scheme are as follows:
- ▪
When GW personalizes a smart card for Ui in the registration phase, GW uses Xsi = h(H_IDi ∥xs) and h(H_IDi∥K; instead of xs and h(K) to prevent an attacker from computing xs or h(K). Since Xsi and h h(H_IDi∥K; are unique for each user, an attacker cannot reuse them to impersonate a legitimate user.
- ▪
In the proposed scheme, instead of xs is stored in Sjto prevent an attacker from extracting xs from Sj. Since is unique for each sensor node, we can attenuate the effects of sensor node capture attacks as much as possible.
We describe each phase in detail in Sections 4.1 through 4.4. Before describing the proposed scheme in detail, we present the security requirements for the proposed scheme.
- ▪
The proposed scheme has to be secure against possible attacks such as replay, password guessing, user impersonation, gateway node bypassing and parallel session attacks.
- ▪
The proposed scheme has to minimize the damage caused by sensor node capture attacks. The authentication scheme cannot be a perfect solution that blocks sensor node capture attacks completely. Nevertheless, the proposed scheme should attenuate the effects of sensor node capture attacks as much as possible.
- ▪
We assume an attacker can obtain all data from a smart card. Therefore, our proposed scheme has to be devised considering stolen smart card attacks, lost smart card problems, and attacks that use an attacker's own smart card, as shown in Section 3.
- ▪
The proposed scheme must be secure against privileged-insider attacks or stolen-verifier attacks.
- ▪
The proposed scheme has to provide methods for mutual authentication, key agreement between Ui and Sj, and password change.
4.1. Registration Phase
In the registration phase, Ui selects IDi and pwi. Ui computes and sends the registration request {IDi, h(pwi)∥RNr)} to the gateway node, where RNr is a random nonce. Then, GW personalizes a smart card for Ui. Figure 4 illustrates the registration phase of the proposed scheme. Meanwhile, SIDj and are stored in Sj, where
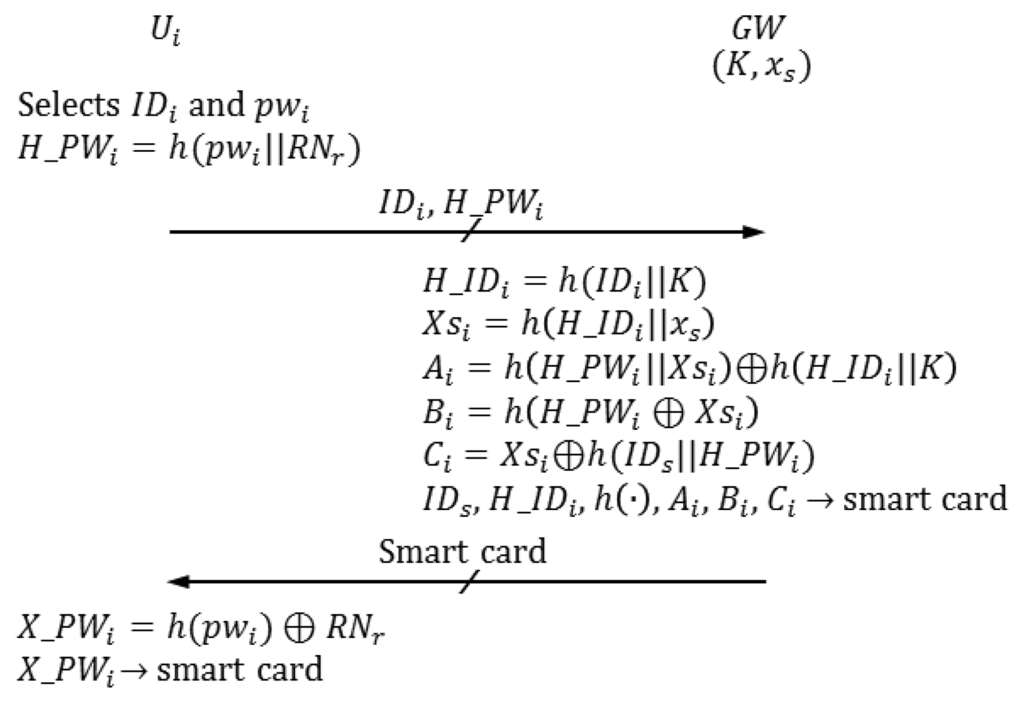
before Sj is deployed into a target field.
| R-1 | Ui selects IDi and pwi. |
| R-2 | Ui generates a random nonce RNr and computes H_PWi = h(pwi∥RNr). |
| Ui sends the registration request {IDi, H_PWi} to GW in secure channels. | |
| R-3 | GW computes the following when it receives a registration request from Ui. |
| H_IDi = h(IDi∥K) | |
| Xsi = h(H_IDi∥xs) | |
| Ai=h(H_PWi∥Xsi) ⊕ h(H_IDi ∥K) | |
| Bi = h(H_PWi ⊕ Xsi) | |
| Ci = XSi ⊕ h(IDs∥H_PWi) | |
| GW personalizes the smart card with IDs, H_IDi, h(·),Ai,Biand Ci. | |
| GW sends the smart card to Ui in secure channels. | |
| R-4 | Ui computes X_PWi = h(pwi) ⊕ RNr and adds X_PWi to the smart card. |
4.2. Login Phase
The login phase begins when Ui inserts Ui's smart card into a terminal and inputs and . In this phase, Ui sends the authentication request to GW. Figure 5 depicts the login phase of the proposed scheme.
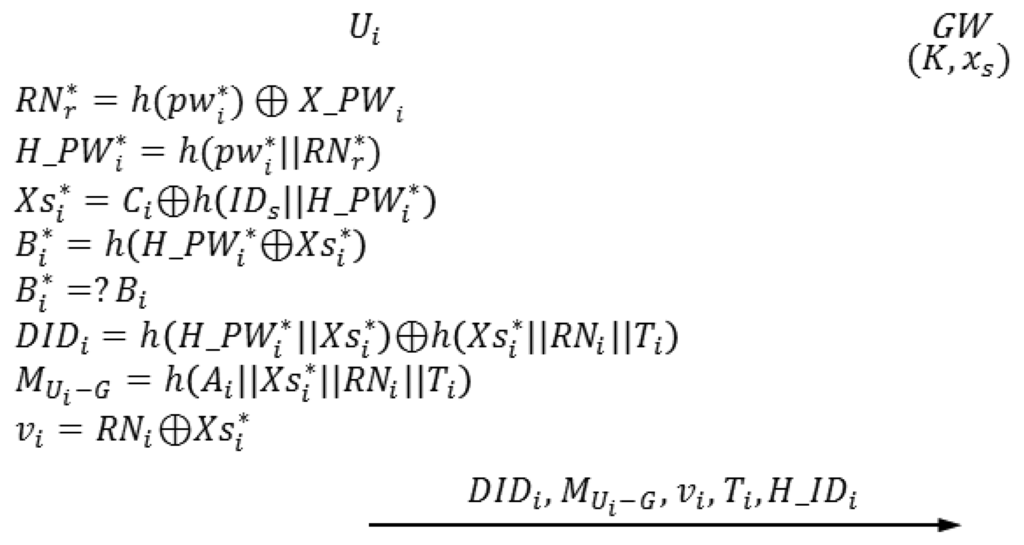
| L-1 | Ui inserts Ui's smart card into a terminal and inputs and. |
| L-2 | The smart card computes the following. |
| The smart card compares with Bi. If , then the next step proceeds; otherwise, this phase is aborted. | |
| L-3 | The smart card generates a random nonce RNi and computes the following. Ti is the current timestamp of Ui system. |
| The smart card sends the authentication request {DIDi, MUi−G, vi, Ti, H_IDi } to GW. | |
4.3. Authentication-Key Agreement Phase
When GW receives an authentication request from Ui, the authentication-key agreement phase begins. In this phase, Ui, GW, Sj and send and receive authentication requests from one another. Figure 6 shows the authentication-key agreement phase of the proposed scheme. The following describes this process in detail.
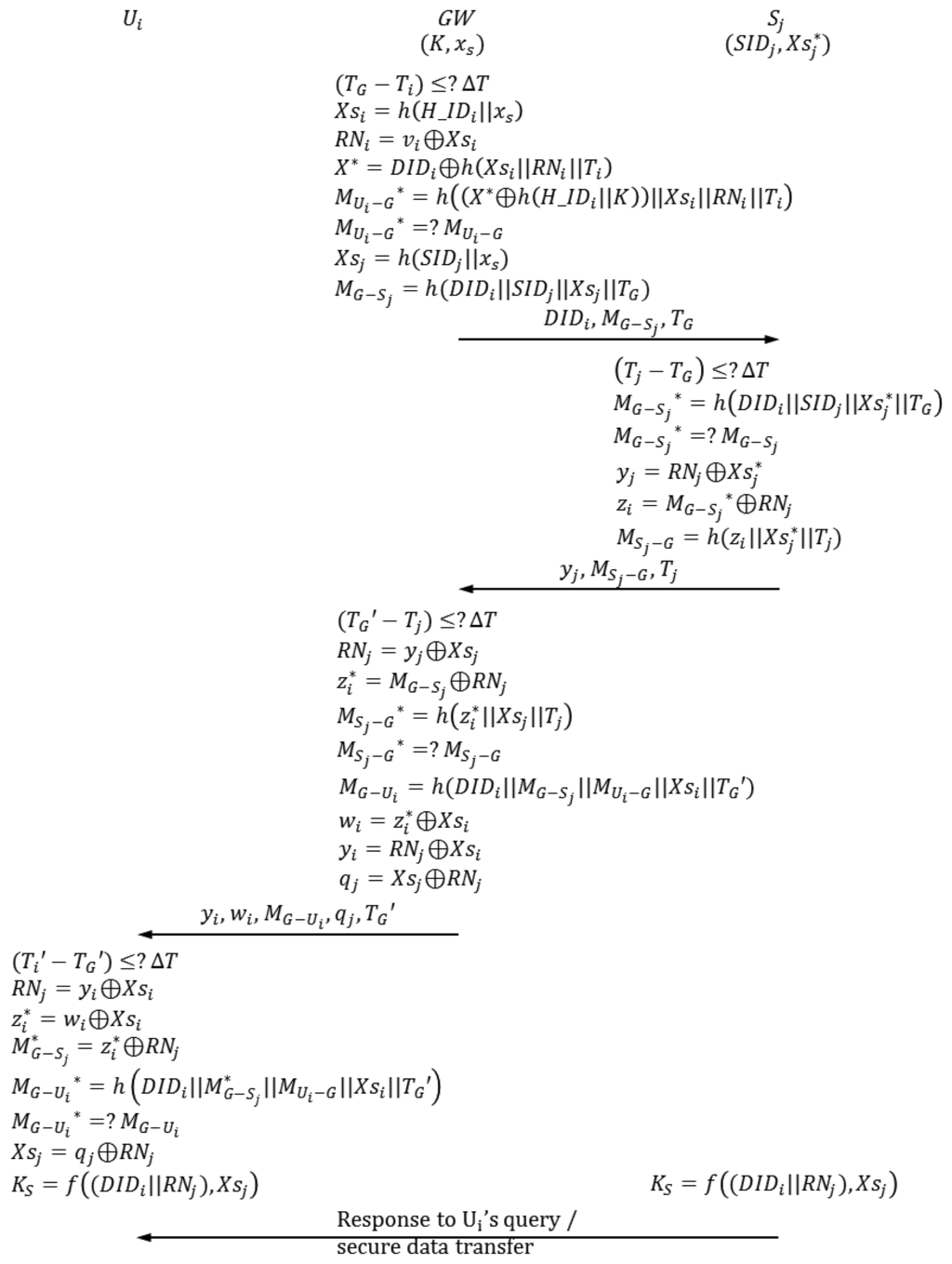
| A-1 | GW checks if (TG − Ti) ≤ ΔT, where TG is the current timestamp of GW system. | |
| If (TG − Ti) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. | ||
| A-2 | GW computes the following. | |
| XSi = h(H_IDi∥xs) | ||
| RNi = vi ⊕ Xsi | ||
| X* = DIDi ⊕ h(Xsi∥RNi∥Ti) | ||
| MUi−G* = h((X* ⊕ h(H_IDi∥K))∥Xsi∥RNi∥Ti) | ||
| GW compares MUi−G* with MUi−G. If MUi−G*=MUi−G, then the next step proceeds; otherwise, this phase is aborted. | ||
| A-3 | GW computes the following. TG is the current timestamp of GW system. Sj is the nearest sensor node that can respond to Ui 's request. | |
| Xsj=h(SIDj∥xs) | ||
| MG−Sj = h(DIDi∥SIDj∥Xsj∥TG) | ||
| GW sends the authentication request {DIDi, MG−Sj, TG} to Sj. | ||
| A-4 | GW checks if (T j − TG) ≤ ΔT, where Tj is the current timestamp of Sj. | |
| If (T j − TG) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. | ||
| A-5 | Sj computes | |
| Sj compares MG−Sj* with MG−Sj. If MG−Sj* = MG−Sj, then the next step proceeds; otherwise, this phase is aborted. | ||
| A-6 | Sj generates a random nonce RNj and computes the following. | |
| zi = MG−Sj*⊕RNj | ||
| Sj sends the authentication request {yi, MSj−G, Tj} to GW. | ||
| A-7 | GW checks if (TG′ − Tj) ≤ ΔT, where TG′ is the current timestamp of GW. | |
| If (TG′ − Tj) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted | ||
| A-8 | GW computes the following. | |
| RNj = yj ⊕ Xsi | ||
| GW compares MSj−G* with MSj−G. If MSj−G = MSj−G, then the next step proceeds; otherwise, this phase is aborted. | ||
| A-9 | GW computes the following: | |
| MG−Ui = h(DIDi ∥MG−Sj∥MUi−G∥Xsi∥TG′) | ||
| yi=RNj ⊕ Xsi | ||
| qj=Xsj ⊕ RNj | ||
| GW sends the authentication request {yi, wi, MG−Ui, qj, TG′)} to Ui. | ||
| A-10 | Ui checks if (Ti′−TG′) ≤ ΔT, where Ti′ is the current timestamp of Ui. If (Ti′−TG′) ≤ ΔT, then the next step proceeds; otherwise, this phase is aborted. | |
| A-11 | The smart card computes the following: | |
| RNj =yi ⊕Xsi | ||
| The smart card compares MG−Ui* with MG−Ui. If MG−Ui* =MG−Ui, then mutual authentication between Ui and SNj is completed successfully; otherwise, this phase is aborted. | ||
| A-12 | The smart card computes the following to get a session key for communication with Sj. Meanwhile, Sj also computes KS = f((DIDi ∥RNi), Xsj to share a session key with Ui. | |
| Xsj = qj ⊕ RNj | ||
| Ks = f((DIDi∥RNj), Xsj) | ||
4.4. Password Change Phase
The password change phase proceeds when Ui changes Ui 's existing password to a new one. In the password change phase, Ui does not have to communicate with GW.
| P-1 | Ui inserts its smart card into a terminal and inputs, , and pwni. is Ui's new password. |
| P-2 | The smart card computes the following. |
| The smart card compares with Bi. If , then the next step proceeds; otherwise, this phase is aborted. | |
| P-3 | The smart card computes the following. |
| The smart card replaces the existing values Ai, Bi and Ci with the new values Ani, Bni and Cni. | |
5. Security Analysis of the Proposed Scheme
This section is devoted to the security analysis of our proposed scheme. We discuss the security of our proposed scheme in terms of the security requirements presented in Section 4. Table 2 shows a security comparison of the proposed scheme.

- ▪
Replay attacks: The proposed scheme resists replay attacks because all authentication requests include current timestamps, such as Ti of {DIDi, MUi−G, vi, Ti, H_IDi}.
- ▪
User impersonation attacks and gateway node bypassing attacks: In the proposed scheme, an attacker cannot create valid authentication requests {DIDi, MUi−G, vi, Ti, H_IDi} and {yi, wi, MG−Ui,qj,TG′} because he/she cannot compute the secret data xs and h(K). Therefore, user impersonation attacks and gateway node bypassing attacks are impossible.
- ▪
Parallel session attacks: The proposed scheme is secure against parallel session attacks because all authentication requests include random nonces such as DIDi, and vi of {DIDi, MUi−G, vi, Ti, H_IDi}.
- ▪
Password guessing attacks: pwi cannot be guessed by an attacker because it is transmitted as the results which are concatenated with some secret values and one-way hashed. Even a privileged-insider cannot guess Ui's password from the registration request {IDi,H_PWi} because RNr in H_PWi = h(pwi∥RNr) is a unknown value to him/her.
- ▪
Sensor node capture attacks: Though an attacker captures a sensor node and obtains secret data SIDj and from it, the attacker cannot impersonate Ui, GW, or other sensor nodes. Since is the unique secret data only for Sj, an attacker cannot compute Xsj for Ui or xs for GW. In addition, he/she cannot compute the secret data of other sensor nodes except Sj.
- ▪
Stolen smart card attacks and lost smart card problems: Though an attacker extracts IDs, H_IDi, h(·), Ai, Bi, Ci, and X_PWi from Ui's smart card, he/she cannot compute any secret data h(K)or xs for attacks. Therefore, the proposed scheme is secure against stolen smart card attacks or lost smart card problems. In addition, though an attacker extracts, IDs, HiDα, h(·), Aα, Bα, Cα, and X_PWα from his/her own smart card, he/she cannot compute any secret data h(K) or xs for attacks. Therefore, the proposed scheme prevents attacks using an attacker's own smart card.
- ▪
Privileged-insider attacks: The proposed scheme resists privileged-insider attacks because pwi is transmitted as a digest of some other secret components.
- ▪
Stolen-verifier attacks: The proposed scheme is secure against stolen-verifier attacks, since does not maintain a verifier table.
- ▪
Mutual authentication, key agreement, and password change phase: The proposed scheme provides mutual authentication, key agreement between Ui and Sj, and password change phase.
6. Performance Analysis of the Proposed Scheme
Table 3 shows the computation cost comparison of the proposed scheme. Das' scheme [3], Khan and Alghathbar's scheme [4], Vaidya et al.'s scheme [12], and the proposed scheme use only hash and XOR operations. We compare these schemes in terms of the number of hash and XOR operations. The proposed scheme needs seven hash operations more than Vaidya's et al.'s [12]. Nevertheless, one of our main concerns is the computation cost of a sensor node rather than that of the entire scheme, because sensor nodes are resource-constrained. The computation cost of in the proposed scheme is the same as that of Vaidya et al.'s [12]. This means that the computation cost increase of the entire scheme is negligible considering the enhanced security. Meanwhile, with respect to communication cost, the number of messages transmitted in the proposed scheme is four, which is the same as that of Vaidya et al.'s scheme.

7. Conclusions
We have proposed an improved mutual authentication and key agreement scheme to overcome the security weaknesses of Vaidya et al.'s scheme. The proposed scheme resists user impersonation attacks and gateway node bypassing attacks using secret data stored in an attacker's own smart card or a sensor. In addition, the proposed scheme prevents possible attacks such as replay attacks, parallel session attacks, password guessing attacks, sensor node capture attacks, stolen smart card attacks, lost smart card problems, privileged-insider attacks, and stolen-verifier attacks. The proposed scheme is also efficient in terms of computation and communication cost considering the limited resources of sensors.
Acknowledgments
This research was supported by the MSIP(Ministry of Science, ICT and Future Planning), Korea, under the ITRC(Information Technology Research Center) support program (NIPA-2014-H0301-14-1004) supervised by the NIPA(National IT Industry Promotion Agency).
Author Contributions
Jiye Kim, Donghoon Lee, Woongryul Jeon, Youngsook Lee, and Dongho Won have contributed to security analysis, design of the proposed scheme, and manuscript preparation.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar]
- Yoon, E.J.; Yoo, K.Y. Cryptanalysis of robust mutual authentication protocol for wireless sensor networks. Proceedings of the 10th IEEE International Conference on Cognitive Informatics & Cognitive Computing (ICCI*CC), Banff AB, Canada, 18-20 August 2011.
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and security improvements of “two-factor user authentication in wireless sensor networks”. Sensors 2010, 10, 2450–2459. [Google Scholar]
- Nyang, D.H.; Lee, M.K. Improvement of Das's Two-Factor Authentication Protocol in Wireless Sensor Networks. IACR Cryptology ePrint Archive. Available online: http://eprint.iacr.org/2009/631.pdf (accessed on 20 January 2014).
- Li, C.T.; Weng, C.Y.; Lee, C.C. An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors 2013, 13, 9589–9603. [Google Scholar]
- Yoo, S.G.; Lee, H.; Kim, J. A. Performance and Usability Aware Secure Two-Factor User Authentication Scheme for Wireless Sensor Networks. Available online: http://www.hindawi.com/journals/ijdsn/2013/543950/ (accessed on 20 January 2014).
- Tseng, H.R.; Jan, R.H.; Yang, W. An Improved dynamic user authentication scheme for wireless sensor networks. Proceedings of the Global Telecommunications Conference (GLOBECOM'07), Washington, DC, USA, 26-30 November 2007.
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Wong, K.H.M.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5-7 June 2006.
- Chen, T.H.; Shih, W.K. A robust mutual authentication protocol for wireless sensor networks. Electron. Telecommun. Res. Inst. 2010, 32, 704–712. [Google Scholar]
- Vaidya, B.; Makrakis, D.; Mouftah, H. Two-Factor Mutual Authentication with Key Agreement in Wireless Sensor Networks. Available online: http://onlinelibrary.wiley.com/doi/10.1002/sec.517/full (accessed on 20 January 2014).
- Das, A.K.; Sharma, P.; Chatterjee, S.; Sing, J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1646–1656. [Google Scholar]
- Xu, J.; Zhu, W.T.; Feng, D.G. An improved smart card based password authentication scheme with provable security. Comput. Stand. Interfaces 2009, 31, 723–728. [Google Scholar]
- Turkanovic, M.; Holbl, M. An improved dynamic password-based user authentication scheme for hierarchical wireless sensor networks. Electron. Electr. Eng. 2013, 19, 109–116. [Google Scholar]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar]
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license ( http://creativecommons.org/licenses/by/3.0/).