DMP: Detouring Using Multiple Paths against Jamming Attack for Ubiquitous Networking System
Abstract
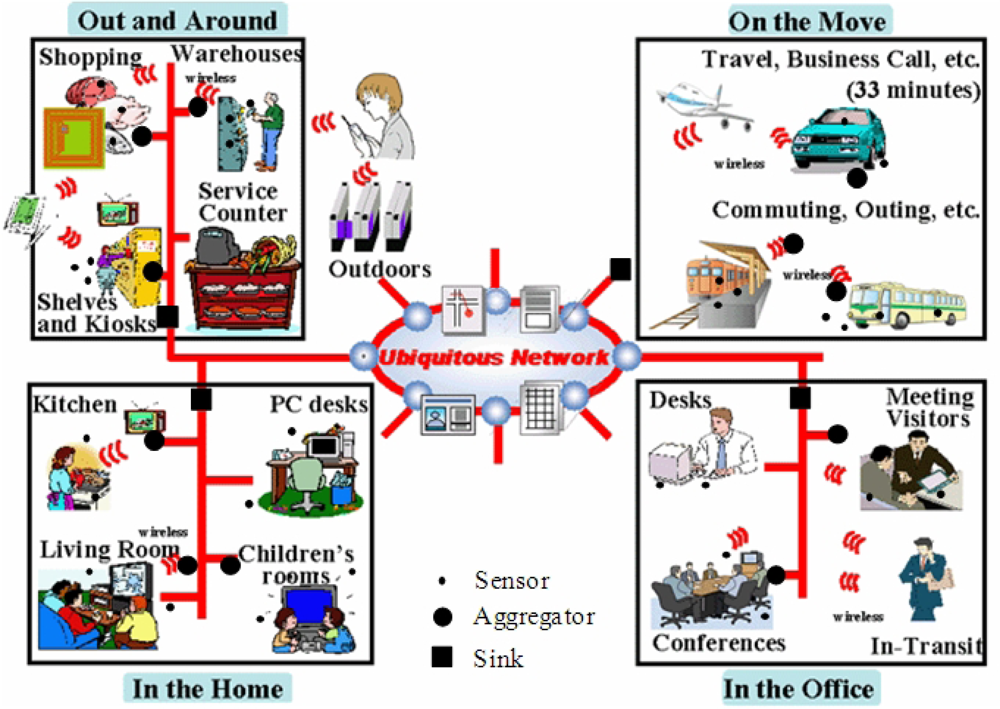
:1. Introduction
2. Related Work
2.1. Detour Architectures on Wired Network
2.2. Ad-Hoc/Sensor Routing
2.3. Existing Defense Mechanisms against Jamming
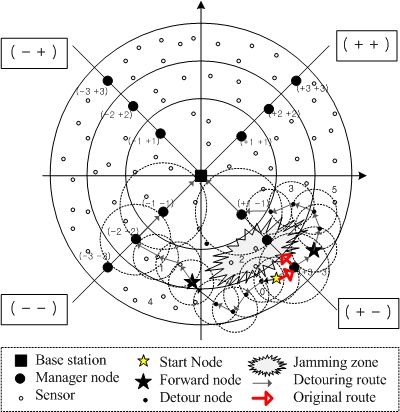
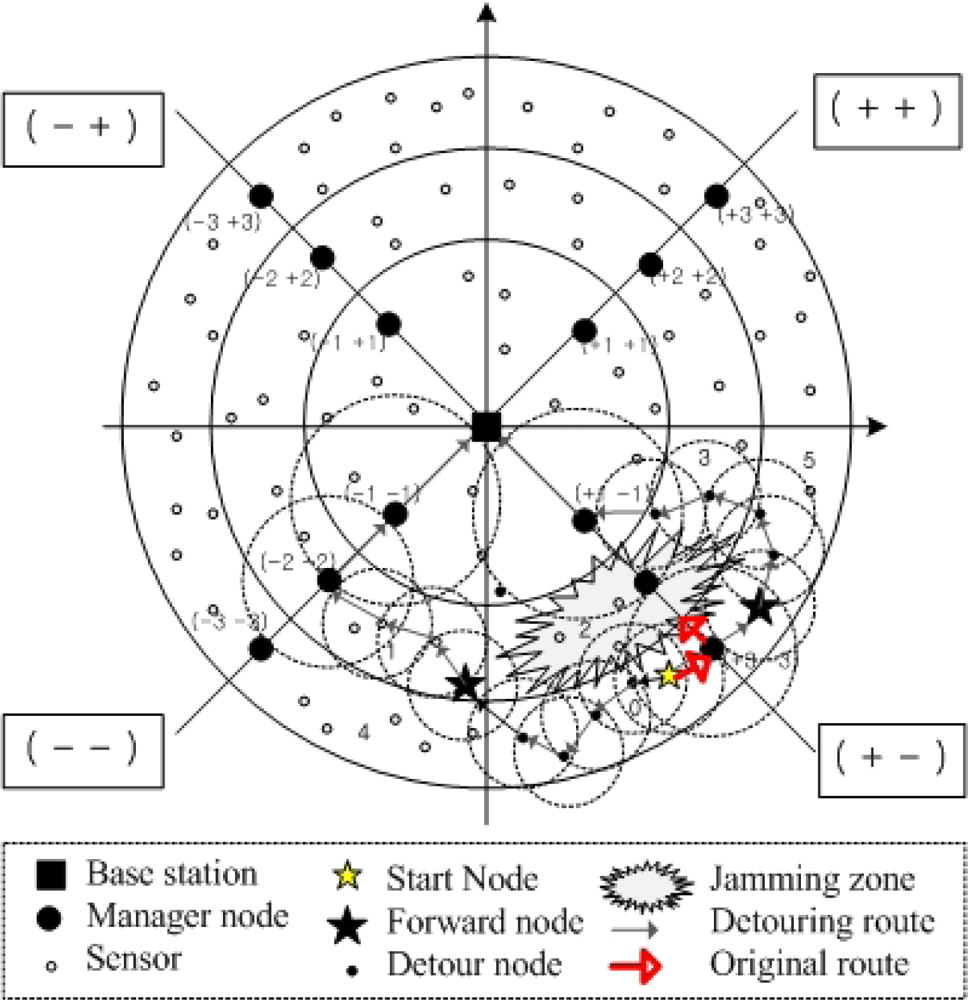
3. Detouring Service via Multiple Paths
3.1. Basic Detouring Service
- Victim/Jamming zone: Zone including victim nodes against jamming attacks
- Neighbor zone: Adjacent zones of each zone
- Destination zone: Zone including a destination node
- Detour node: As the boundary node of the victim zone, it performs the algorithm shown in Table 2, thus it detours normal traffic with the determined multiple paths.
- Forward node: The first foothold nodes are used to detour normal traffic. After the detour nodes determine these nodes, they forward normal traffic to them.
- Forward zone: Zone determined by a detour node for detouring normal traffic
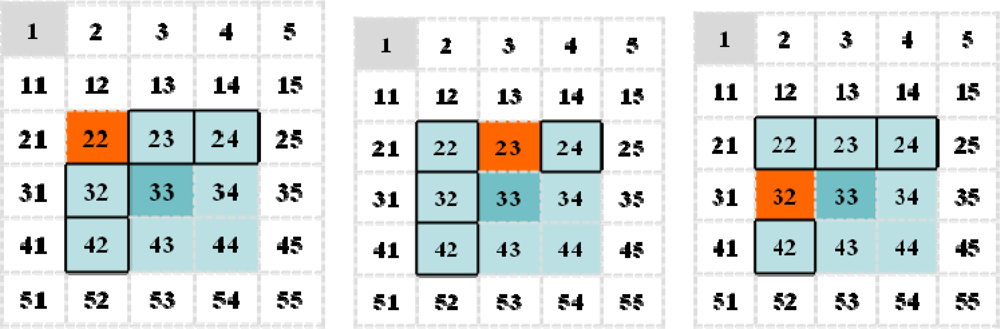
3.2. An Extension of a Routing Protocol RDSR [27]
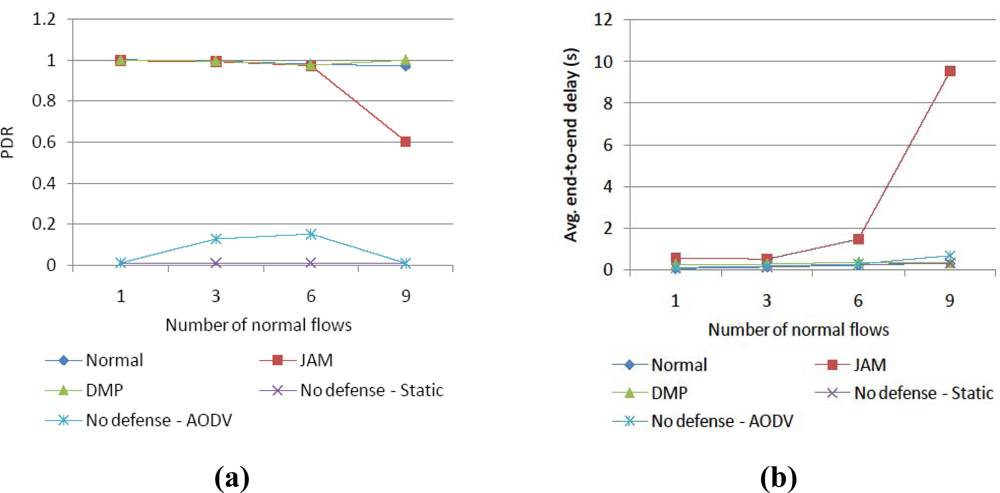
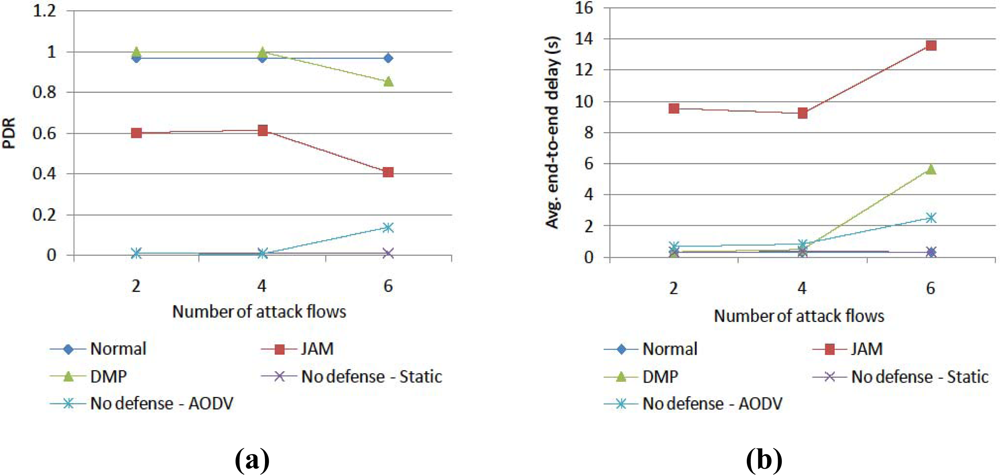
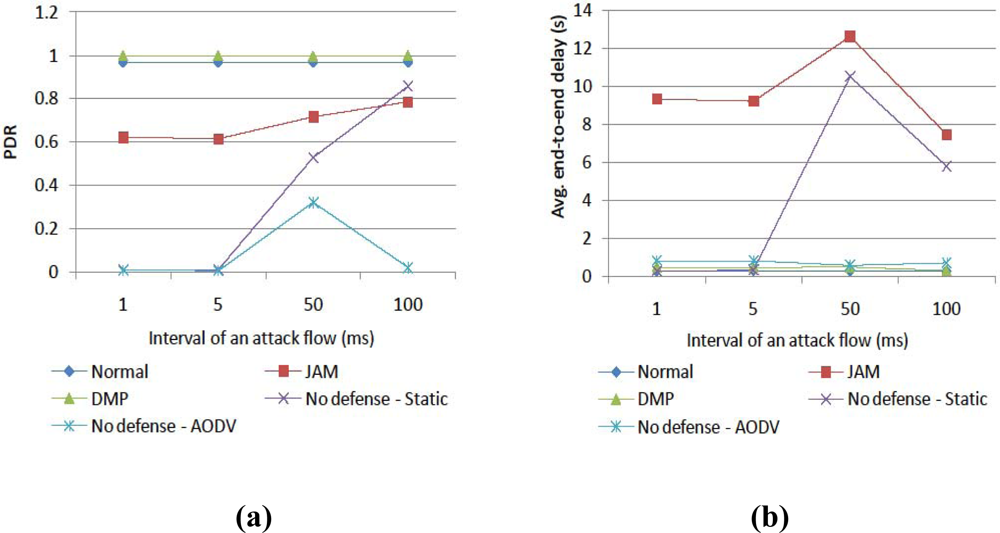
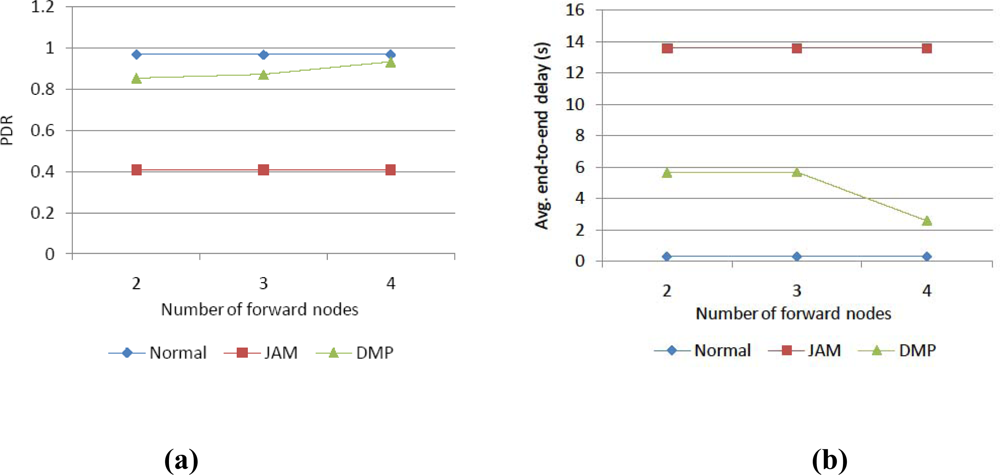
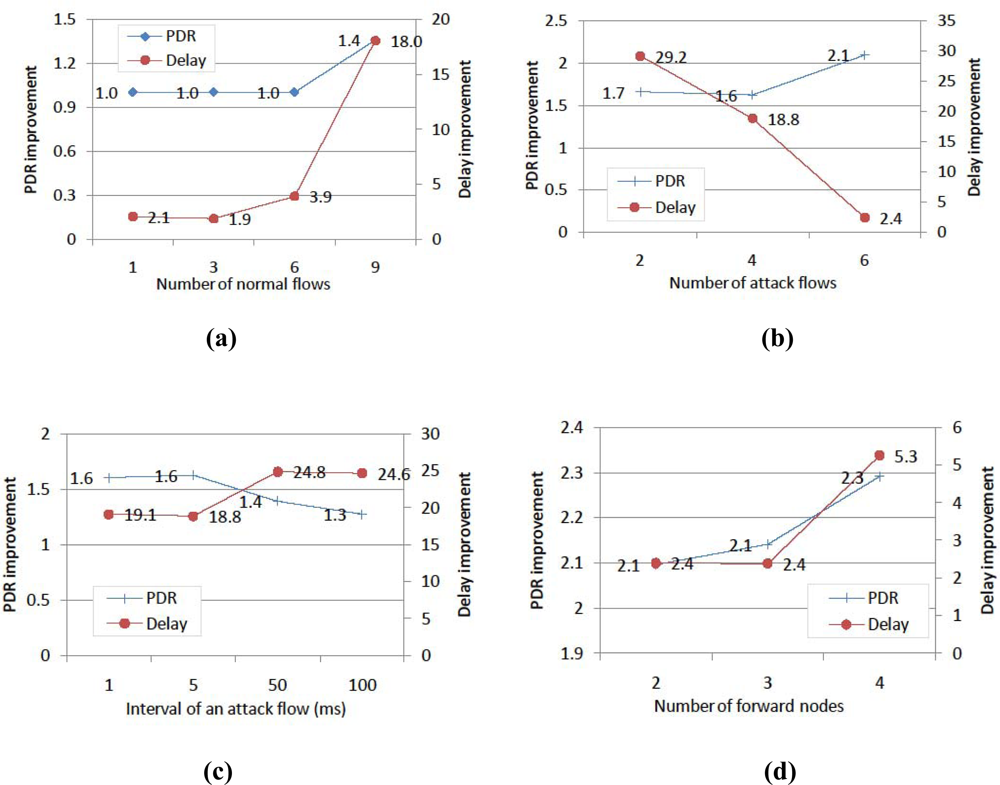
4. Simulation Results
5. Conclusions
Acknowledgments
References and Notes
- What Is Ubiquitous? Available online: http://www.nhk.or.jp/strl/publica/dayori-new/en/qa-0108e.html (accessed on January 1, 2010).
- Wood, A.D.; Stankovic, J.A. Denial of Service in Sensor Networks. Computer 2002, 35, 54–62. [Google Scholar]
- Li, M.; Koutsopoulos, I.; Poovendran, R. Optimal jamming attacks and network defense policies in wireless sensor networks. Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), Anchorage, AK, USA, May 2007; pp. 1307–1315.
- Raymond, D.; Marchany, R.; Brownfield, M.; Midkiff, S. Effects of Denial of Sleep Attacks on Wireless Sensor Network MAC Protocols. Proceedings of the IEEE Information Assurance Workshop, Cagliari, Italy, June 2006; pp. 297–304.
- Raymond, D.R.; Midkiff, S.F. Denial-of-Service in Wireless Sensor Networks: Attacks and Defenses. IEEE Pervasive Comput 2008, 7, 74–81. [Google Scholar]
- Intanagonwiwat, C.; Govindan, R.; Estrin, D. Directed diffusion: A scalable and robust communication paradigm for sensor networks. Proceedings of the 6th annual international conference on Mobile computing and networking (ACM Mobicom), Boston, MA, USA, August 2000; pp. 56–67.
- Kulik, J.; Heinzelman, W.R.; Balakrishnan, H. Negotiation-based protocols for disseminating information in wireless sensor networks. Wirel. Netw 2002, 8, 169–185. [Google Scholar]
- Wood, A.; Stankovic, J.; Son, S. JAM: A Jammed-Area Mapping Service for Sensor Networks. Proceedings of 24th IEEE Real-Time System Symposium, Cancun, Mexico, December 2003; pp. 286–297.
- Keromytis, A.; Misra, V.; Rubenstein, D. SOS: An Architecture for Mitigating DDoS Attacks. IEEE J. Sel. Area. Commun. (JSAC) 2004, 22, 176–188. [Google Scholar]
- Yang, H.; Luo, H.; Yang, Y.; Lu, S.; Zhang, L. HOURS: Achieving DoS Resilience in an Open Service Hierarchy. Proceedings of International Conference on Dependable Systems and Netowrks (DSN), Florence, Italy, July 2004; pp. 83–92.
- Perkins, C.; Belding-Royer, E.; Das, S. Ad hoc On-Demand Distance Vector (AODV) Routing. IETF RFC 2003, 3561. [Google Scholar]
- Kang, B; Ko, I. Effective Route Maintenance and Restoration Schemes in Mobile Ad Hoc Networks. Sensors 2010, 1, 808–821. [Google Scholar]
- Liu, M; Cao, J.; Chen, G.; Wang, X. An Energy-Aware Routing Protocol in Wireless Sensor Networks. Sensors 2009, 1, 445–462. [Google Scholar]
- Tufail, A; Khayam, S.A.; Raza, M.T.; Ali, A.; Kim, K. An Enhanced Backbone-Assisted Reliable Framework for Wireless Sensor Networks. Sensors 2010, 3, 1619–1651. [Google Scholar]
- Al-Karaki, J.N.; Ul-Mustafa, R.; Kamal, A.E. Data Aggregation in Wireless Sensor Networks - Exact and Approximate Algorithms. Proceedings of the IEEE Workshop on High Performance Switching and Routing (HPSR), Phoenix, AZ, USA, February 2004; pp. 241–245.
- Xu, W.; Trappe, W.; Zhang, Y.; Wood, T. The Feasibility of Launching and Detecting Jamming Attacks in Wireless Networks. Proceedings of the ACM International Symposium on Mobile Ad Hoc Networking and Computing (Mobihoc), Urbana-Champaign, IL, USA, May 2005; pp. 46–57.
- Xu, W.; Ma, K.; Trappe, W.; Zhang, Y. Jamming Sensor Networks: Attack and Defense Strategies. IEEE Network 2006, 20, 41–47. [Google Scholar]
- Chiang, J.; Hu, Y. Cross-layer jamming detection and mitigation in wireless broadcast networks. Proceedings of the 13th annual ACM international conference on Mobile computing and networking (ACM MobiCom), Montreal, QC, Canada, September 2007; pp. 346–349.
- Chiang, J.; Hu, Y. Dynamic jamming mitigation for wireless broadcast networks. Proceedings of the IEEE Conference on Computer Communications (InfoCom), Phoenix, AZ, USA, April 2008; pp. 1211–1219.
- Strasser, M.; Pöpper, C.; Capkun, S.; Cagalj, M. Jamming-resistant Key Establishment using Uncoordinated Frequency Hopping. Proceedings of the 2008 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, May 2008; pp. 64–78.
- Wood, A.D.; Stankovic, J.A.; Zhou, G. DEEJAM: Defeating energy-efficient jamming in IEEE 802.15.4-based wireless networks. Proceedings of IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON), Glasgow, Scotland, June 2007; pp. 60–69.
- Xu, W.; Trappe, W.; Zhang, Y. Channel surfing: defending wireless sensor networks from interference. Proceedings of ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), New York, NY, USA, 2007; pp. 499–508.
- Khattab, S.; Mosse, D.; Melhem, R. Jamming Mitigation in Multi-Radio Wireless Networks: Reactive or Proactive? Proceedings of the 4th international Conference on Security and Privacy in Communication Networks (SecureComm), Istanbul, Turkey, September 2008; pp. 1–10.
- Ma, K.; Zhang, Y.; Trappe, W. Mobile Network Management and Robust Spatial Retreats Via Network Dynamics. Proceedings of the First International Workshop on Resource Provisioning and Management in Sensor Networks (RPMSN), Washington, DC, USA, November 2005.
- Tague, P.; Li, M.; Poovendran, R. Probabilistic Mitigation of Control Channel Jamming via Random Key Distribution. Proceedings of IEEE Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Athens, Greece, September 2007.
- Lazos, L.; Liu, S.; Krunz, M. Mitigating control-channel jamming attacks in multi-channel ad hoc networks. Proceedings of the Second ACM Conference on Wireless Network Security (WiSec), Zurich, Switzerland, March 2009; pp. 169–180.
- Oh, H.; Bahn, H.; Chae, K. An Energy-Efficient Sensor Routing Scheme for Home Automation Networks. IEEE Trans. Consum. Electron 2005, 51, 836–839. [Google Scholar]
- GloMoSim. Available online: http://pcl.cs.ucla.edu/projects/glomosim/ (accessed on January 1, 2010).
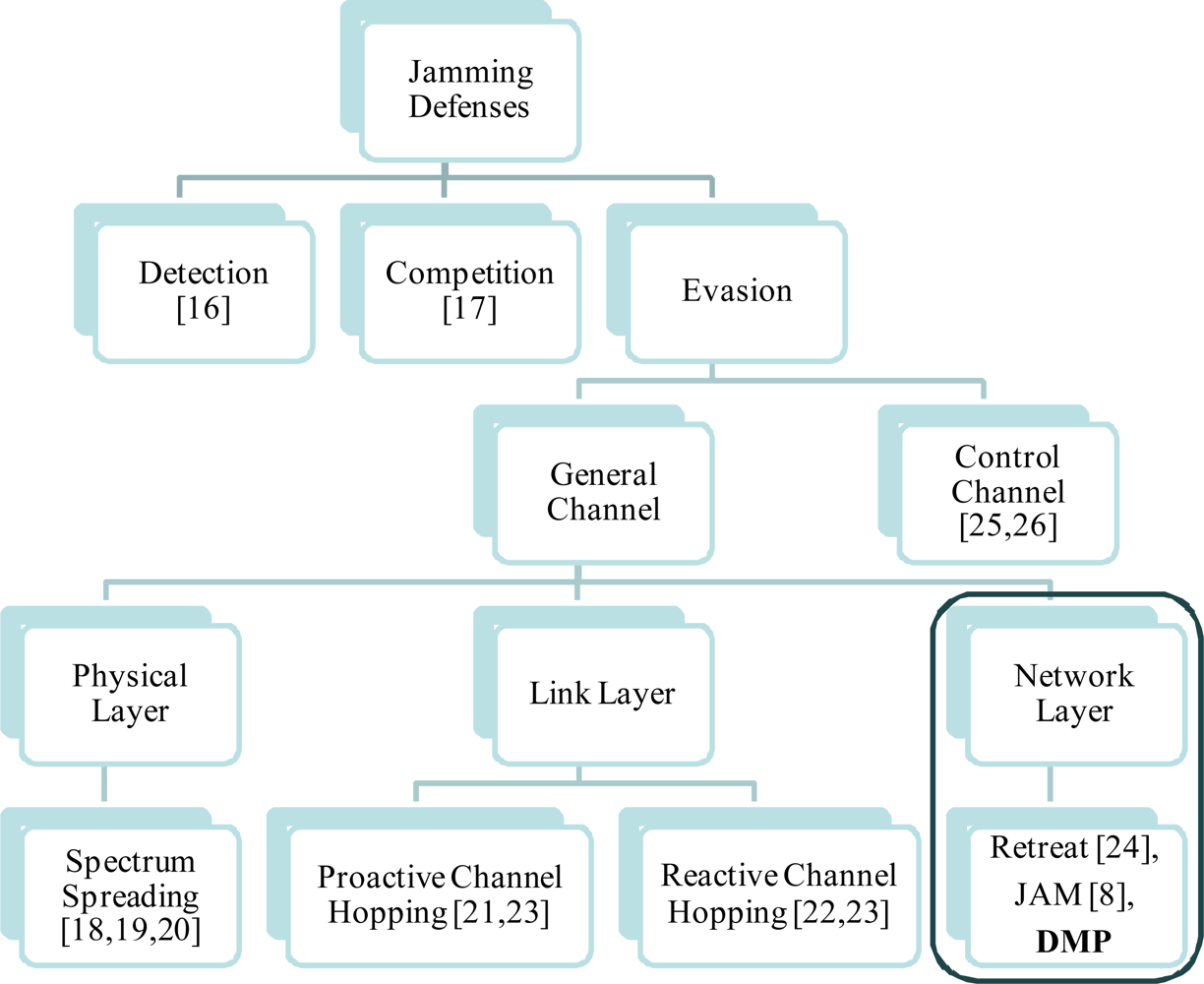
| Type | Layer | Characteristics |
|---|---|---|
| Spectrum Spreading [18,19,20] | Physical Layer | It is too energy-consuming to be widely deployed in resource-constrained sensors. |
| Channel Hopping [21,22,23] | Link Layer | The jammer can also change the jamming channel continuously and then it enlarges the channel switching overhead on nodes on the entire network. |
| Retreat [24] | Network Layer | It is limit to mobile environment. |
| JAM [8] | Network Layer | It simply focused on a mapping service for the jamming area, thus the best single route detouring the jamming zone can easily become congested again. |
| DMP | Network Layer | As a general approach irrelative with specific protocols on physical and link layer, it can enhance the robustness against jamming on existing routing protocols. |
| 1: | IF (nnext-hop ∈ Njamming) |
| 2: | Zforward = Nforward = Φ |
| 3: | FOR(each z in Zneighbor) |
| 4: | IF((fn in z ∉ Njamming) AND (czDist >= zDist) AND (z ≠ dz)) |
| 5: | add z to Zforward |
| 6: | ENDIF |
| 7: | ENDFOR |
| 8: | sort fn in Zforward according to the distance value |
| 9: | |
| 10: | WHILE(|Nforward| == α) |
| 11: | pop the first node fn in the sorted list |
| 12: | add fn to Nforward |
| 13: | ENDWHILE |
| 14: | detour normal traffic evenly to fn in Nforward |
| 15: | |
| 16: | ELSE IF (nnext-hop ∉ Njamming) |
| 17: | route the traffic according to the general routing protocol |
| 18: | ENDIF |
© 2010 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open-access article distributed under the terms and conditions of the Creative Commons Attribution license ( http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Kim, M.; Chae, K. DMP: Detouring Using Multiple Paths against Jamming Attack for Ubiquitous Networking System. Sensors 2010, 10, 3626-3640. https://doi.org/10.3390/s100403626
Kim M, Chae K. DMP: Detouring Using Multiple Paths against Jamming Attack for Ubiquitous Networking System. Sensors. 2010; 10(4):3626-3640. https://doi.org/10.3390/s100403626
Chicago/Turabian StyleKim, Mihui, and Kijoon Chae. 2010. "DMP: Detouring Using Multiple Paths against Jamming Attack for Ubiquitous Networking System" Sensors 10, no. 4: 3626-3640. https://doi.org/10.3390/s100403626
APA StyleKim, M., & Chae, K. (2010). DMP: Detouring Using Multiple Paths against Jamming Attack for Ubiquitous Networking System. Sensors, 10(4), 3626-3640. https://doi.org/10.3390/s100403626