1. Introduction
With the deep integration of wireless communication technology and intelligent sensing, integrated sensing and communication (ISAC) has become one of the core technologies for sixth generation (6G) communication systems [
1,
2]. By sharing resources such as spectrum and hardware, ISAC can achieve collaborative optimization of communication and sensing, significantly improving spectrum efficiency and system performance [
3]. In recent years, unmanned aerial vehicles (UAVs) have demonstrated extensive potential in ISAC systems due to their flexible deployment, wide coverage, and line-of-sight (LoS) communication links [
4]. Integrating ISAC modules onto UAVs can not only enhance resource utilization but also provide communication and sensing services for ground users simultaneously [
5,
6].
In a UAV-assisted ISAC system, UAV trajectory design, user scheduling, and resource allocation are crucial factors affecting system performance. Currently, numerous studies focus on utilizing a single UAV to provide ISAC services for users [
7,
8,
9,
10,
11,
12]. For instance, Liu et al. [
7] proposed a joint optimization problem of user scheduling, transmit power, and UAV trajectory, aiming to maximize energy efficiency and minimize radar mutual information (MI) under the premise of satisfying user sensing fairness. Deng et al. [
8] studied the UAV-assisted integrated periodic sensing and communication (IPSAC) mechanism. Under the premise of satisfying sensing frequency and beam pattern gain requirement, the authors jointly optimized UAV trajectory, user association, target sensing selection, and transmit beamforming to maximize system communication rate. Zhou et al. [
9] proposed a joint optimization problem of UAV CPU frequency, UAV radar sensing power, user transmit power, and UAV trajectory, aiming to minimize the total energy consumption of the UAV and users. Liu et al. [
10] jointly optimized UAV trajectory, task scheduling, and power allocation. Under the constraint of communication rate, they maximized the radar estimation rate. Zhu et al. [
11] proposed a reconfigurable intelligent surface (RIS)-assisted ISAC system operating in the millimeter-wave band, which configures the radio propagation environment by altering the phase of radio signals to enhance communication transmission rates. Zhu et al. [
12] investigated a simultaneous transmitting and reflecting reconfigurable intelligent surface (STAR-RIS)-assisted ISAC dual secure communication system. By jointly designing the base station’s transmit beamforming and receive filter, along with the STAR-RIS’s transmission and reflection coefficients, the system maximizes the long-term average secrecy rate of users while ensuring the echo signal-to-noise ratio threshold and user rate constraints.
However, constrained by size and power, a single UAV has limited service capability and coverage range, making it difficult to handle scenarios where the geographical locations of communication users or targets are widely distributed. This has driven in-depth research on multi-UAV-assisted ISAC systems [
13,
14,
15,
16]. For example, Zhang et al. [
13] investigated the resource allocation problem in multi-UAV-assisted ISAC systems. By jointly optimizing the UAV trajectory, user association, and beamforming design, the sum of weighted bit rates of all ground users was maximized while ensuring the sensing signal gain of targets. Qin et al. [
14] proposed a joint optimization problem of user association, UAV trajectory planning, and power allocation, aiming to maximize the minimum weighted spectral efficiency among UAVs. Then, the authors introduced centralized and distributed schemes for solving the optimization problem. Wang et al. [
15] considered a scenario where multiple UAVs collaboratively detect targets and transmit the collected data to a central UAV. Regarding the communication and sensing scheduling problem, the authors formulated it into two optimization problems, with the objectives of maximizing the average utility function (MAUF) and minimizing the completion time (MCT), respectively. Liu et al. [
16] introduced radar MI to measure the sensing performance of ISAC from the perspective of information entropy. To achieve fair communication, the authors maximized the minimum communication rate of each Internet of Things (IoT) node through joint optimization of node scheduling, transmit power, and the three-dimensional (3D) trajectory of UAVs.
Although the aforementioned studies have made significant progress in UAV-assisted ISAC systems, most of them assume that users are in a stationary state and do not fully consider the impact of user mobility on system performance. In fact, some work has begun to focus on ISAC systems in dynamic scenarios. For example, Al-habob et al. [
17] investigated a downlink multi-user ISAC system with multiple mobile eavesdropping UAVs, aiming to maximize user secrecy rates and ensure sensing quality by designing predictive beamforming schemes. However, this work did not consider user mobility and employed only a single base station to provide ISAC services. Pan et al. [
18] explored a multi-UAV cooperative ISAC dynamic system, which maximizes the positioning accuracy of moving targets while ensuring communication service quality by jointly optimizing trajectories, base station association, spectrum, and power resources. Nevertheless, these studies still do not address the realistic threat of malicious jamming.
As an active attacker, malicious jamming aims to weaken and disrupt the normal communication activities of communication parties through various means (e.g., signal interference, electromagnetic attacks, etc.), thereby degrading communication performance. Jammers use advanced electronic jamming equipment to emit noise signals that are similar to or within the same frequency band as the communication signals, severely reducing the signal-to-noise ratio at the receiver and leading to degraded or even interrupted communication quality. In ISAC systems, malicious jamming not only disrupts communication links but also indirectly affects sensing accuracy and exacerbates power allocation conflicts.
Currently, limited work has focused on UAV-assisted ISAC systems in malicious jamming environments. Liu et al. [
19] studied a UAV-enabled ISAC system under malicious jamming attacks, which maximizes the minimum transmission rate of users by optimizing transmit beamforming while meeting sensing constraints. However, this work only considered a simple scenario with a single fixed UAV deployment, lacking an analysis of multi-UAV dynamic trajectory optimization and user mobility. Mei et al. [
20] explored the minimization of age of information (AoI) in scenarios with malicious jamming UAVs, reducing AoI by jointly designing the trajectories and power of legitimate UAVs, but similarly without considering multi-UAV cooperation and user mobility. Therefore, under multiple constraints such as mobility, sensing requirements, communication guarantees, and malicious jamming, achieving efficient, robust, and dynamic trajectory planning and resource allocation for UAVs has become a critical problem that urgently needs to be addressed.
Unlike existing studies, the innovation of this paper lies in being the first to thoroughly investigate the joint optimization of user association, UAV trajectory design, and power allocation in multi-UAV-assisted ISAC systems under the complex scenario of coexisting dynamic users and malicious jamming attacks. This paper designs a multi-UAV-assisted ISAC system in a malicious jamming environment, where multiple UAVs provide downlink communication services while sensing environmental information around ground users and dynamically optimizing their trajectories to mitigate the impact of malicious jamming. Additionally, we introduce a long short-term memory (LSTM) network to predict user positions, thereby addressing the challenges posed by mobility. The main contributions of this paper are summarized as follows:
A joint optimization problem is built to jointly optimize user association, UAV trajectory, and transmit power, aiming to maximize the total communication rate of all users under the constraint of sensing accuracy. Due to the non-convexity of the problem, an effective alternating optimization-based predictive scheduling algorithm (AOPSA) is put forward to solve it.
We decompose the optimization problem into three subproblems, which are solved using the improved auction algorithm (IAA), dream optimization algorithm (DOA), and rapidly-exploring random trees-based optimizer algorithm (RRTOA).
An LSTM network is introduced to capture the temporal characteristics of user positions, and it is combined with AOPSA to enhance the system’s real-time performance and optimization efficiency.
A series of simulations are conducted to evaluate the performance of AOPSA. Simulation results demonstrate that LSTM can effectively predict user positions. Moreover, AOPSA outperforms four benchmarks with diverse parameter settings.
The remainder of this paper is organized as follows.
Section 2 describes the multi-UAV-assisted ISAC system model under malicious jamming environments. In
Section 3, we propose the joint optimization problem of user association, UAV trajectory, and UAV transmit power.
Section 4 provides a detailed introduction to the proposed optimization algorithms.
Section 5 presents the simulation results of the proposed algorithms and discusses these results. Finally,
Section 6 concludes the paper.
2. System Model
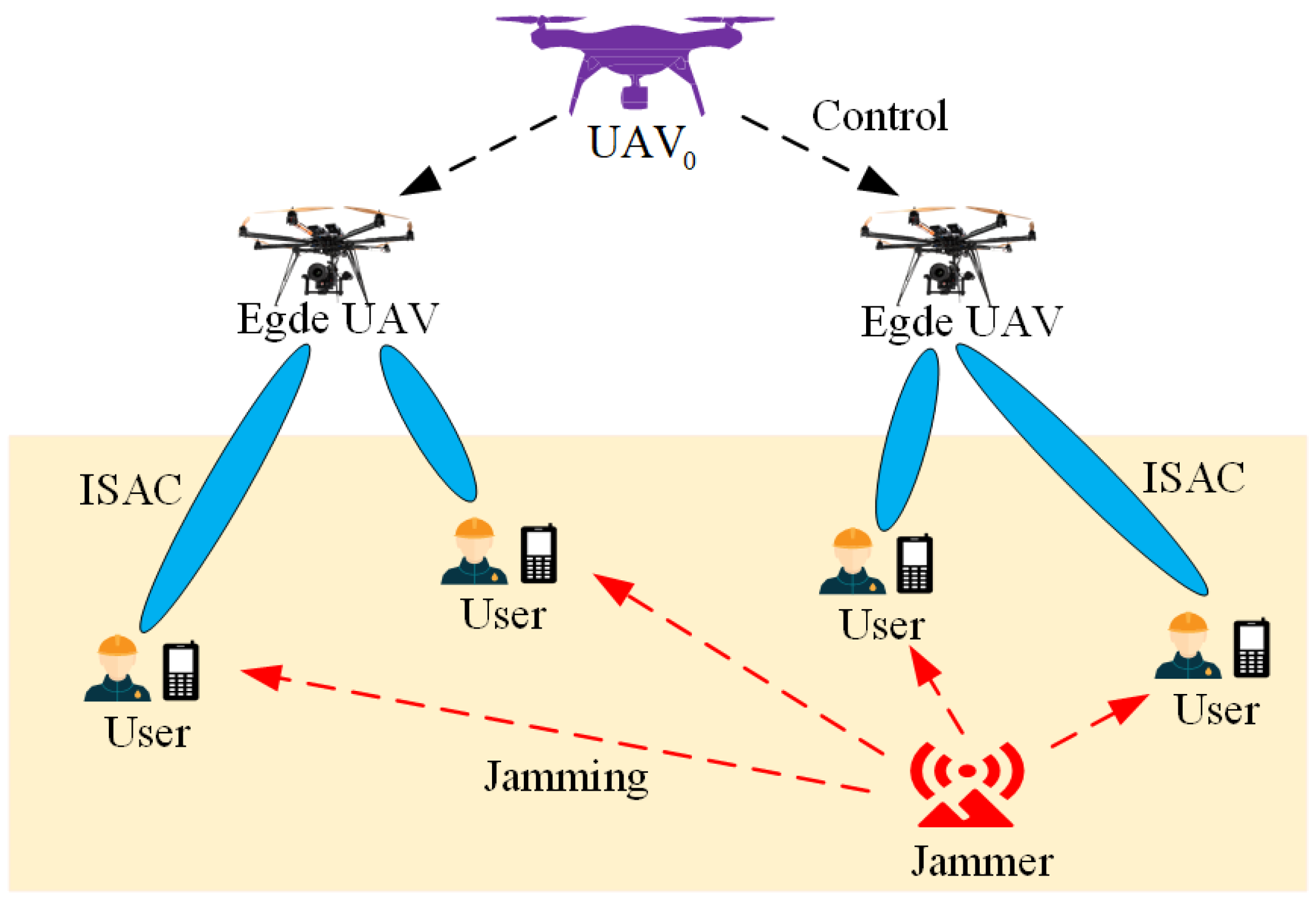
We consider a multi-UAV-assisted ISAC system under malicious jamming environments as shown in
Figure 1. The system model includes the following: a central UAV, denoted as
;
M edge UAVs equipped with communication and sensing modules, denoted as
;
K ground mobile users, denoted as
; and a static malicious jammer. In this system,
provides global management and control, edge UAVs perform ISAC service for the users by sensing the environmental information around the users and sending the sensing information back to the users [
16]. The jammer operates in a fixed-frequency mode, continuously emitting jamming signals within the primary communication frequency band (e.g., the ISAC shared band) to disrupt the communication link between edge UAVs and users. Such jammers are typically stationary (e.g., ground-based fixed jamming stations) and transmit at a constant power, generating strong interference via high-gain antennas. Due to the distance-dependent attenuation characteristics of wireless signal propagation, the jamming intensity experienced by user nodes is negatively correlated with their distance from the jammer. Based on feedback regarding the jamming intensity received by ground users, the UAV can perform radar detection scans over suspected jammer locations to estimate its approximate position [
21,
22].
Assume
hovers directly above the center of the area at a fixed altitude of
. Edge UAVs fly at a fixed altitude
H, with flying time
divided into
T time slots of length
.
should be sufficiently small to ensure sensing and communication channel state information (CSI) remain nearly constant. We consider a 3D Cartesian coordinate system. At each time slot
, the coordinates of
can be expressed as
, the coordinates of
can be expressed as
, and the jammer’s coordinates can be expressed as
. The motion constraints of
can be expressed as
where
denotes the
norm,
is the maximum flying speed of edge UAVs, and
represents the minimum collision avoidance distance between edge UAVs.
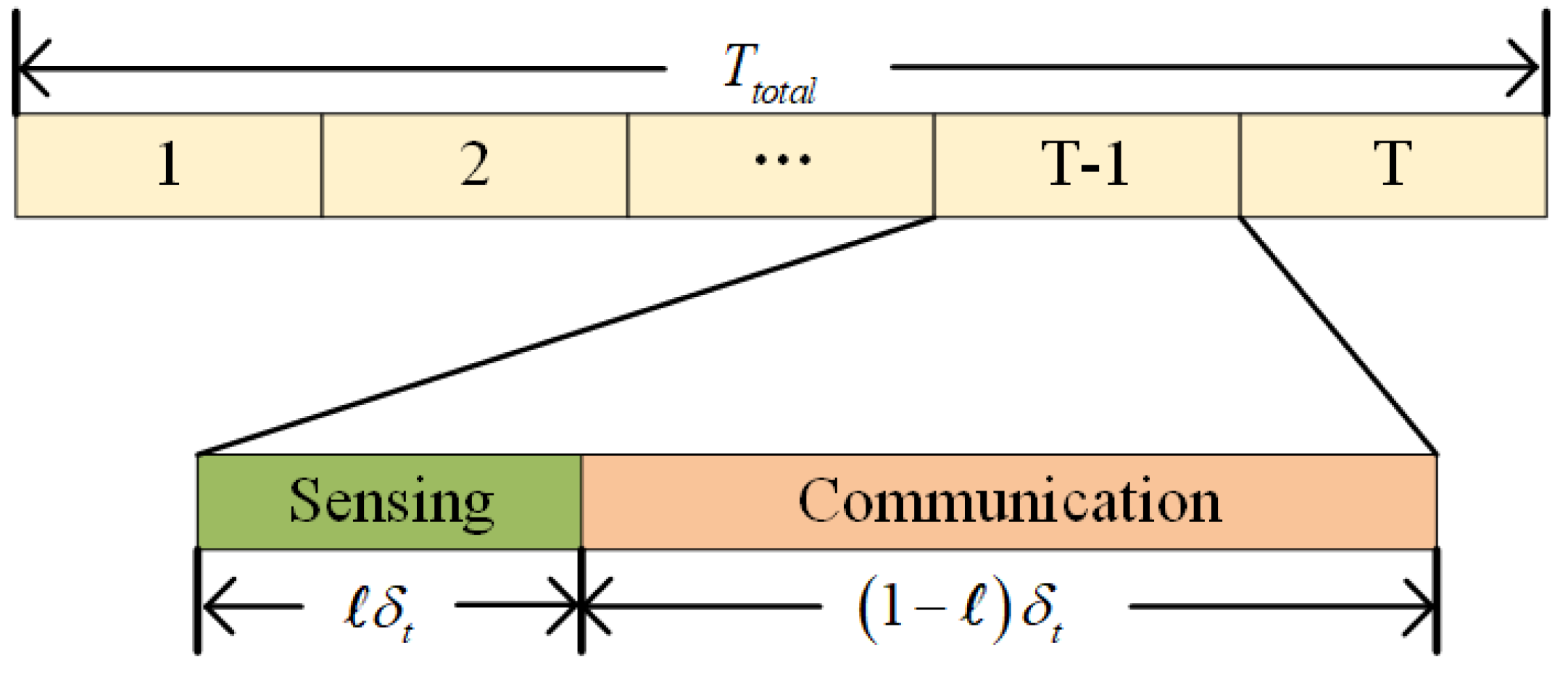
To prevent mutual interference between radar signals and communication signals, the UAVs employ the time-division multiplexing (TDM) technique for radar detection and communication [
16]. As depicted in
Figure 2, each time slot is divided into two subtime slots by the allocation weight parameter
ℓ. One subtime slot is allocated for the sensing task, while the other subtime slot is designated for the communication task.
We consider the air-to-ground communication channel mainly experiences Nakagami-m fading. Therefore, the communication channel gain from
to
at time slot
t can be expressed as [
16,
23]
where
represents the small-scale fading coefficient following the Nakagami-m distribution,
denotes the antenna gain of the transmitter of
,
denotes the antenna gain of the receiver of
,
represents the distance between
and
,
is the signal wavelength, and
. Considering the transmit and return links of the radar signal, the channel power gain of the radar detection link
and
can be expressed as
where
denotes the antenna gain of the radar receiver of
,
represents the radar cross section (RCS) of the target, and
. Considering that the ground-to-ground communication channel mainly experiences Rayleigh fading, the jamming channel gain from the malicious jammer to
can be expressed as [
24]
where
denotes the antenna gain of the transmitter of the jammer,
represents the distance between the jammer and
,
is a random variable following the exponential distribution with unit mean, and
.
In this work, the UAVs communicate with users via orthogonal frequency division multiple access (OFDMA). At time slot
t, the signal-to-interference-plus-noise ratio (SINR) of the communication link between
and
can be expressed as
where
denotes the transmit power of
and satisfies
, and
is the maximum transmit power of edge UAVs.
is the additive white Gaussian noise (AWGN) power, and
represents the transmit power of the jammer. The SINR of the sensing link between
and
can be expressed as
To ensure the sensing accuracy of edge UAVs, the SINR of the sensing link needs to satisfy the constraint
[
25], where
represents the minimum SINR for accurate radar sensing.
We introduce a binary integer variable
to represent user association. If
, it indicates that
and
are associated at time slot
t, otherwise
. Assuming that each user can associate with at most one UAV at each time slot, it can be expressed as
At time slot
t, the communication rate from
to
can be expressed as
Therefore, the total communication rate of
can be expressed as
The total communication rate of all users can be expressed as
4. Algorithm Design
It is evident that problem is a typical non-convex mixed integer nonlinear programming (MINLP) problem, which is challenging to solve directly. On one hand, the user association optimization variable is a binary integer. On the other hand, even with fixed user association, the problem remains non-convex with respect to UAV trajectory and transmit power . Therefore, to solve problem , we decompose the original optimization problem into three subproblems: user association optimization, UAV trajectory optimization, and UAV transmit power optimization. Then, we solve these three subproblems through alternating iterations to obtain the solution of the original problem. Before introducing the algorithms, we first present the specific mechanism of LSTM for predicting user positions.
4.1. LSTM Predicting User Positions
Assuming ground users follow a random walk model and their current position information can be obtained through a global positioning system. The position information of
K users over the past
S time slots can be represented as
Based on
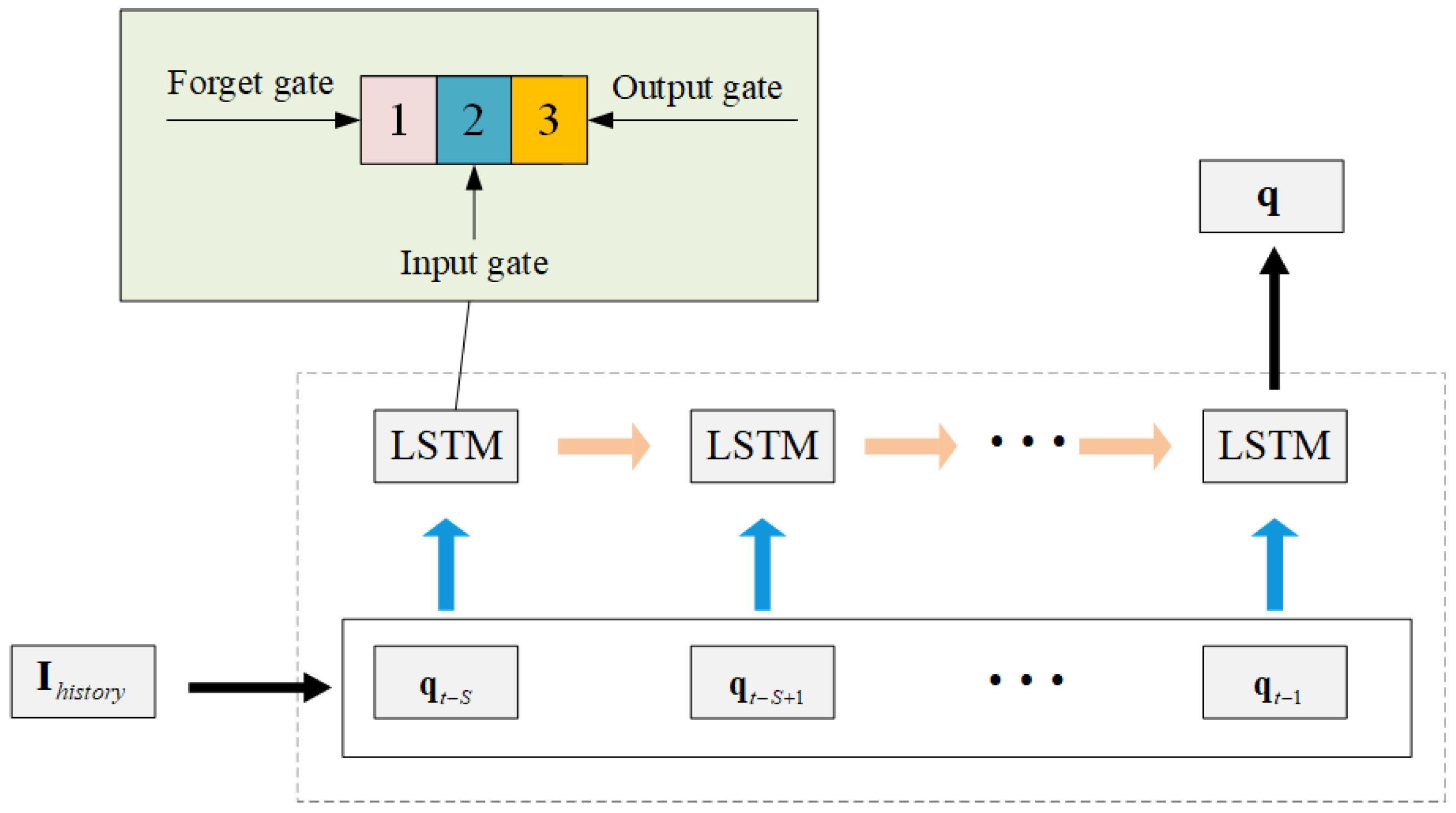
, we utilize LSTM to predict future user positions. The LSTM network is a type of time-recurrent neural network, suitable for processing and predicting sequential data or time series. Take
Figure 3 as an example to introduce the composition and functions of the LSTM network unit.
The first part is generally referred to as the forget gate, which is used to determine whether the information from the past time step needs to be forgotten; the second part is called the input gate, through which new information is input into the network; the third part is called the output gate, which is used to pass the information to the next unit. As an excellent perceptron, the LSTM network can fully perceive the relevant features of the time series, such as the temporal correlation between the user’s position information and service changes within a certain period of time, thereby predicting the user’s position at the next moment. The dataset is generated by simulating the random walk trajectories of K users within the task area. In each time slot, users move according to a random direction with inertia. The initial direction of users is uniformly distributed within , with the turning angle per step constrained to . Boundary reflection is implemented to ensure users remain within the task area.
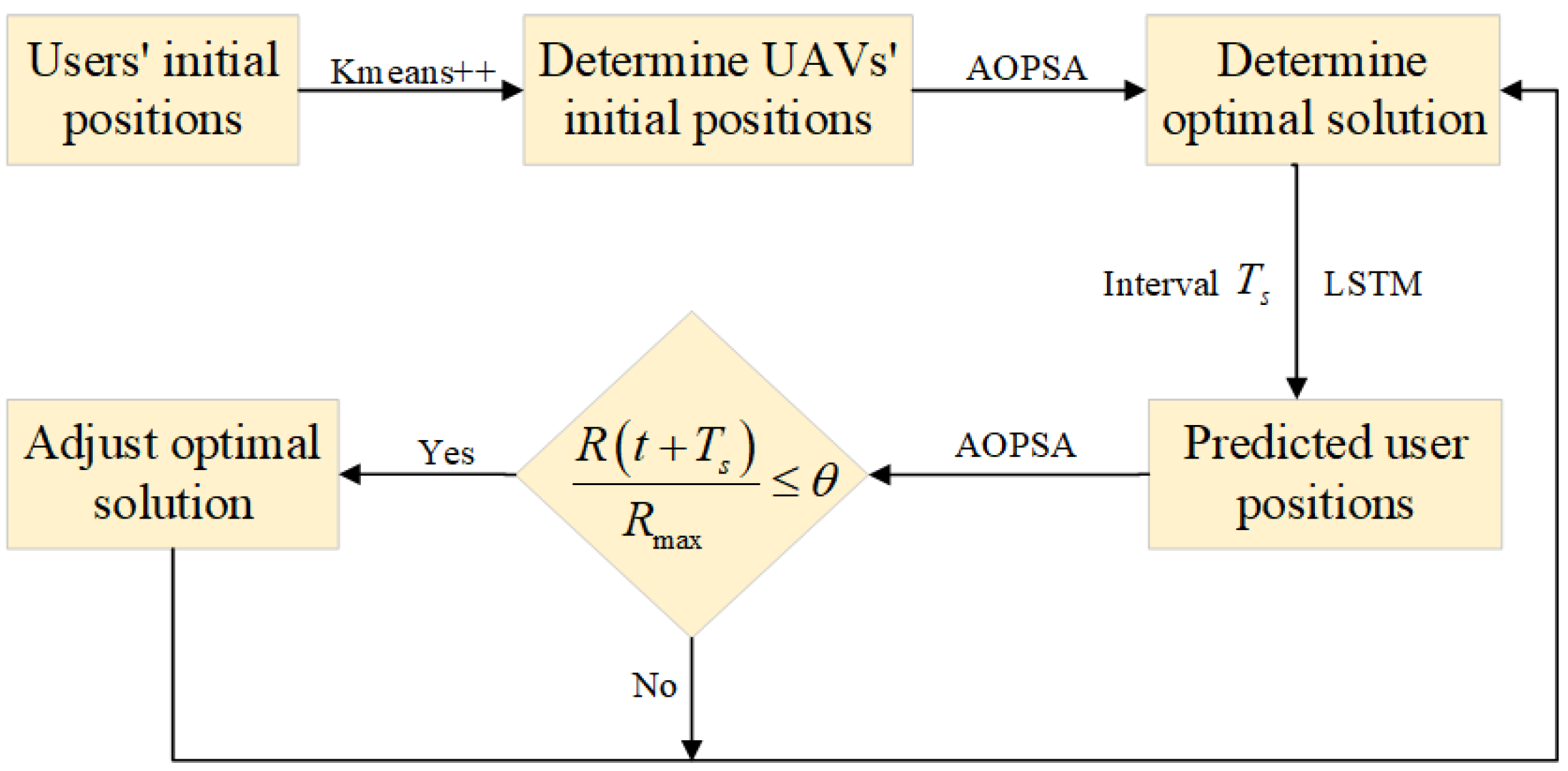
Setting the time interval
as the cycle for adjusting the optimization scheme, the flowchart of alternating optimization schemes based on user position prediction is shown in
Figure 4.
In this figure, represents the objective function value obtained using the optimal optimization scheme for time slot , represents the objective function value obtained, still using the optimal optimization scheme for time slot t, and is the adjustment threshold, for example 95%.
For the LSTM prediction model, the input size is
. Let
denote the output size and
h denote the number of units in the hidden layer of the network. According to the connection relationships between neurons, the computational complexity of LSTM can be expressed as
[
26]. We train the LSTM prediction model offline, and then use the trained model for solving the optimization problem to ensure real-time performance.
4.2. Determine the Initial Positions of UAVs with Kmeans++
Based on the positions of all users at the initial time slot, we use the Kmeans++ algorithm [
27] to determine the initial positions of the UAVs, as shown in Algorithm 1.
| Algorithm 1 Kmeans++ Algorithm |
Input: Users’ initial positions
Output: UAVs’ initial positions
- 1:
Randomly select a user as the first center ; - 2:
Calculate the shortest distance from to the selected center set ; - 3:
Select a new user as the next center with probability ; - 4:
Repeat steps 2–3 until ; - 5:
Assign each user to the nearest center, forming M clusters; - 6:
Calculate the average position of users in each cluster as the new center; - 7:
Repeat steps 5–6 until the cluster centers are stable.
|
4.3. User Association Optimization
For given
and
, the user association optimization subproblem can be formulated as
The traditional auction algorithm is difficult to adapt to many-to-many association requirements. Therefore, we propose an IAA based on the dynamic pricing mechanism to solve , maximizing user rates while ensuring sensing service quality. The process of solving with IAA is described as follows:
We define the price of as , initialize the prices of all UAVs as , and the set of unassigned users .
For each unassigned :
Select the set of valid UAVs that satisfy the sensing constraint
Calculate the net benefit for
to
Select the UAV with the maximum net benefit
Update the price of
, with the update mechanism as follows
where
is the suboptimal net benefit,
is the price increment,
is the basic step size, and
prevents division by zero.
The detailed process of solving
with IAA is shown in Algorithm 2. The computational complexity of IAA is mainly related to the number of UAVs and users. Therefore, the total computational complexity of IAA is
. This algorithm coordinates resource competition among multiple UAVs by introducing dynamic price adjustment increment
, providing an effective solution paradigm for joint optimization problems in dynamic environments. Its distributed characteristics and low computational complexity make it particularly suitable for real-time resource scheduling scenarios in large-scale multi-UAV networks.
| Algorithm 2 Improved Auction Algorithm (IAA) |
Input: , , , , ,
Output:
Initialize: , - 1:
while do - 2:
Randomly select , filter based on Equation ( 16); - 3:
if then - 4:
Update ; - 5:
else - 6:
Select UAV based on Equations ( 17) and ( 18); - 7:
Update ; - 8:
Update the price of UAV based on Equations ( 19) and ( 20); - 9:
end if - 10:
end while - 11:
return .
|
4.4. UAV Trajectory Optimization
For given
and
, the UAV trajectory optimization subproblem can be formulated as
We use the DOA [
28] to solve
. DOA is a novel meta-heuristic algorithm inspired by human dream behavior, which simulates the processes of memory retention, forgetting, and self-organization in dreams. By integrating memory, forgetting, and supplementary strategies, it effectively balances global exploration and local exploitation. The memory strategy serves as the foundation of the algorithm, resetting individuals to the previous optimal values within the group or population. This is followed by the forgetting supplement, which facilitates a gradual shift from exploration to exploitation. In the exploration stage, global optimization is enhanced through grouping, while in the exploitation stage, the entire population collaborates to improve local optimization. Reference [
28] demonstrates that compared to algorithms such as particle swarm optimization (PSO) and successive convex approximation (SCA), DOA performs superiorly in terms of convergence, stability, and overall performance. The process of solving
with DOA is described as follows.
4.4.1. Optimization Algorithm Assumptions
Based on the characteristics of human dreams and knowledge of optimization algorithms, we summarize the following four hypotheses:
The quality of dreams can be evaluated using fitness values.
The initiation of dreams is closely related to the foundation of existing memories.
Humans partially forget existing memories and supplement the forgotten parts with logically self-organized information.
Memory ability varies among individuals or groups and exhibits a certain degree of randomness.
These hypotheses help us better understand the principles of the algorithm. The workflow, exploration phase, and various strategies in the development phase of the algorithm are concrete embodiments of these four hypotheses.
4.4.2. Initialization
Based on the optimal UAV positions obtained from the last alternating optimization
, initialize the population
and ensure that each individual in
satisfies constraints (
21a)–(
21f). Population
can be expressed as
where
is the number of individuals and
represents the
ith individual in
. Each individual represents the horizontal coordinates of all UAVs, i.e.,
represents the horizontal coordinates of the
mth UAV in the
ith individual. The initialization population is formulated as follows
where
r is a random number between 0 and 1.
4.4.3. Fitness Function
Transforming constraints (
21a)–(
21f) into penalty function terms, the fitness function can be expressed as
where
is the constraint violation indicator function,
is the penalty coefficient, and
is the set of constraints (
21a)–(
21f).
4.4.4. Exploration Phase
We divide the population into five groups based on the the difference in memory ability, the number of forgetting dimension
for each group can be expressed as
where
represents the group number,
represents a random integer selected from
a to
b, and
represents the number of dimensions.
Memory Strategy: Each iteration is regarded as a dream behavior. Before each iteration, individuals in each group reset their positions to the best individual from the previous iteration within the group. The update formula can be expressed as
where
represents the
ith individual at iteration
, and
represents the best individual in group
F at iteration
u.
Forgetting and supplementary strategy: Individuals in each group randomly forget information in certain dimensions while dreaming. The forgetting and supplementary strategy follows the memory strategy, allowing individuals to forget and self-supplement position information in the forgotten dimensions. The update formula can be expressed as
where
and
represent the x and y coordinates of the
mth UAV of the
ith individual at iteration
, respectively.
and
represent the x and y coordinates of the
mth UAV of the best individual in group
F at iteration
u, respectively.
is the maximum number of iterations,
is the maximum number of iterations in the exploration phase, and
.
4.4.5. Exploitation Phase
Memory strategy: This phase does not perform grouping. Before each dream, all individuals reset their positions to the best individual from the previous iteration in the entire population. The update formula can be expressed as
where
represents the best individual in the entire population at iteration
u. The number of forgetting dimensions for all individuals in the population is the same, expressed as
Forgetting and supplementary strategy: The position update formula can be expressed as
where
and
represent the x and y coordinates of the
mth UAV of the best individual in the entire population at iteration
u, respectively.
The detailed process of solving
with DOA is shown in Algorithm 3. The computational complexity of DOA is mainly concentrated in the exploration phase and exploitation phase. The computational complexity of the exploration phase can be expressed as
, and the computational complexity of the exploitation phase can be expressed as
. Therefore, the total computational complexity of DOA is
.
| Algorithm 3 Dream Optimization Algorithm (DOA) |
Input:
, , , , , ,
Output:
,
Initialize:
, Generate initial population based on Equations (22)–(24)
- 1:
while
do - 2:
for do - 3:
Update and ; - 4:
Update based on Equation ( 26); - 5:
Update based on Equation ( 27); - 6:
for each individual do - 7:
Randomly select dimensions to forget; - 8:
for each forgotten dimension m do - 9:
Update and based on Equations ( 28) and ( 29); - 10:
Check and repair constraints ( 21a)–( 21f) for and ; - 11:
end for - 12:
end for - 13:
end for - 14:
Update and based on Equation ( 25); - 15:
Update ; - 16:
end while - 17:
while
do - 18:
Update based on Equation ( 30); - 19:
Update f based on Equation ( 31); - 20:
for each individual i do - 21:
Randomly select f dimensions to forget; - 22:
for each forgotten dimension m do - 23:
Update and based on Equations ( 32) and ( 33); - 24:
Check and repair constraints ( 21a)–( 21f) for and ; - 25:
end for - 26:
end for - 27:
Update and based on Equation ( 25); - 28:
Update ; - 29:
end while - 30:
return
and .
|
4.5. UAV Transmit Power Optimization
For given
and
, the UAV transmit power optimization subproblem can be expressed as
We use RRTOA [
29] to solve
. RRTOA is a novel meta-heuristic algorithm inspired by the search mechanism of rapidly-exploring random trees in robot path planning. The rapidly-exploring random trees algorithm effectively explores the search space by incrementally expanding a tree structure, demonstrating strong adaptability to complex constraints and high-dimensional planning requirements. However, traditional rapidly-exploring random trees algorithms suffer from issues such as slow convergence rates and undesirable path quality. Particularly in regions near the goal, the tree expansion becomes sparse, leading to reduced computational efficiency. To address these limitations, RRTOA has been effectively improved. RRTOA utilizes the adaptive step size wandering strategy, absolute difference-based adaptive step size strategy, and boundary-based adaptive step size strategy, which can effectively search the solution space while guiding the population to find high-quality solutions. Reference [
29] shows that compared to similar meta-heuristic algorithms, RRTOA achieves competitive results across various problems. The process of solving
with RRTOA is described as follows.
4.5.1. Initialization
Based on the optimal UAV power allocation scheme from the last alternating optimization
, initialize population
and ensure individuals in the population satisfy constraints (
34a)–(
34c). Population
can be expressed as
where
is the number of individuals, each individual
represents a UAV power allocation scheme. The initialization formula for the population is as follows
where
represents the power of the
mth UAV in the
jth individual, and
is a random number between 0 and 1.
4.5.2. Fitness Function
Transforming constraints (
34a)–(
34c) into penalty function terms, the fitness function is expressed as
where
is the constraint violation indicator function,
is the penalty coefficient, and
is the set of constraints (
34a)–(
34c).
4.5.3. Adaptive Step Size Wandering Strategy
To address the issue of low exploration efficiency caused by a fixed step size, RRTOA models the random sampling mechanism as an adaptive step size wandering strategy to enhance the algorithm’s search capability. The adaptive step size wandering strategy greatly improves the effectiveness of the global search by combining global random initialization methods, effectively preventing the algorithm from falling into local optima. We define monotonic functions
and
that vary with the iteration number
to control the dynamic adjustment of the step size, which can be expressed as
where
is the maximum number of iterations, and
is the current iteration number.
When
, the update formula is as follows
where
represents the power of the
mth UAV in the
jth individual at iteration
,
represents the power of the
mth UAV in the
jth individual at iteration
,
is the adaptive step size of this strategy, and
is the step size penalty factor.
4.5.4. Absolute Difference-Based Adaptive Step Size Strategy
RRTOA introduces an absolute difference-based adaptive step size strategy. This strategy dynamically adjusts the step size by calculating the absolute difference between the current particle position and the current best position, achieving a dynamic balance between large-scale exploration and local fine-tuning of the search space. Consequently, it enhances the algorithm’s global optimization capability and efficiency.
When
, the update formula is as follows
where
represents the power of the
mth UAV in the best individual at iteration
,
is the adaptive step size of this strategy,
is a random number between 0 and 1, and
is the adaptive step size adjustment coefficient of this strategy, which can be expressed as
where
is the random disturbance factor, with
.
4.5.5. Boundary-Based Adaptive Step Size Strategy
To achieve more precise optimization, a boundary-based adaptive step size strategy is introduced. The core of this strategy involves exploring with very small random steps, which enables RRTOA agents to conduct meticulous searches in the surrounding area. This not only ensures localized searching around the current best solution but also prevents convergence to local minima.
When
, the update formula is as follows
where
is the adaptive step size of this strategy,
is a random number between 0 and 1, and
is the adaptive step size adjustment coefficient of this strategy, which can be expressed as
The detailed process of solving
with RRTOA is shown in Algorithm 4. The computational complexity of RRTOA is mainly affected by population size, number of iterations, and problem dimension. Therefore, the total computational complexity of RRTOA is
.
| Algorithm 4 RRT-Based Optimizer Algorithm (RRTOA) |
Input:
, , , , , ,
Output:
,
Initialize:
, generate initial population based on Equations (35) and (36)
- 1:
while
do - 2:
if then - 3:
Update based on Equations ( 39) and ( 40); - 4:
end if - 5:
if then - 6:
Update based on Equations ( 41)–( 43); - 7:
end if - 8:
if then - 9:
Update based on Equations ( 44)–( 46); - 10:
end if - 11:
Update and based on Equation ( 37); - 12:
Update ; - 13:
end while - 14:
return
and .
|
4.6. Alternating Optimization-Based Predictive Scheduling Algorithm
We define the relevant variables in AOPSA:
is the maximum number of iterations,
is the convergence threshold, and
represents the objective function value at iteration
. The detailed process of solving
with AOPSA is shown in Algorithm 5. The computational complexity of AOPSA is
.
| Algorithm 5 Alternating Optimization-based Predictive Scheduling Algorithm (AOPSA) |
Input:
M, K, , , , , , ,
Output:
, , ,
Initialize: UAV initial positions, , , - 1:
for
: do - 2:
Optimize user association using Algorithm 2; - 3:
Optimize UAV trajectory using Algorithm 3; - 4:
Optimize UAV transmit power using Algorithm 4; - 5:
Calculate ; - 6:
if then - 7:
break; - 8:
else - 9:
Update ; - 10:
end if - 11:
end for - 12:
return
, , , .
|
5. Simulation Results
This section evaluates the performance of AOPSA through simulation. Regarding the frequency selection, we adopt the millimeter-wave frequency band (28 GHz). This frequency band has abundant spectrum resources and can meet the system’s requirements for high-speed data transmission and high-precision sensing. The initial positions of ground users are randomly distributed within a 2D area of 800 m × 800 m. The main simulation parameters are shown in
Table 1, and the settings of the values mainly refer to [
16,
25].
To demonstrate the effectiveness of AOPSA, we compare AOPSA with three other schemes as well as the joint optimization scheme in [
30]. The details are as follows:
Scheme 1: UAVs are uniformly distributed throughout the area and remain stationary at altitude H. Only user association optimization and UAV power optimization are performed.
Scheme 2: UAV power is fixed at . Only user association optimization and UAV trajectory optimization are performed.
Scheme 3: UAVs are uniformly distributed throughout the area and remain stationary at altitude H. UAV power is fixed at , and only user association optimization is performed.
Reference [30]: Adopt spectral clustering, coalition game, and SCA to sequentially solve the three subproblems of UAV position optimization, user association optimization, and transmit power optimization.
We compare and analyze the computational complexity of AOPSA and the reference [
30] algorithm as shown in
Table 2. The complexity analysis for AOPSA has been presented in
Section 4 and will not be reiterated here. The reference [
30] algorithm employs coalition game, spectral clustering, and SCA to sequentially solve three subproblems: user association optimization, UAV position optimization, and transmit power optimization. In the user association optimization subproblem, the coalition game requires traversing all possible user–UAV combinations in the worst case, resulting in exponential computational complexity
for solving subproblem
. The UAV trajectory optimization subproblem involves three components: similarity matrix construction
, eigen decomposition
, and initial clustering
. For the power optimization subproblem, the computational complexity reaches
. This analysis reveals that AOPSA significantly reduces the computational complexity and is suited for large scale scenarios.
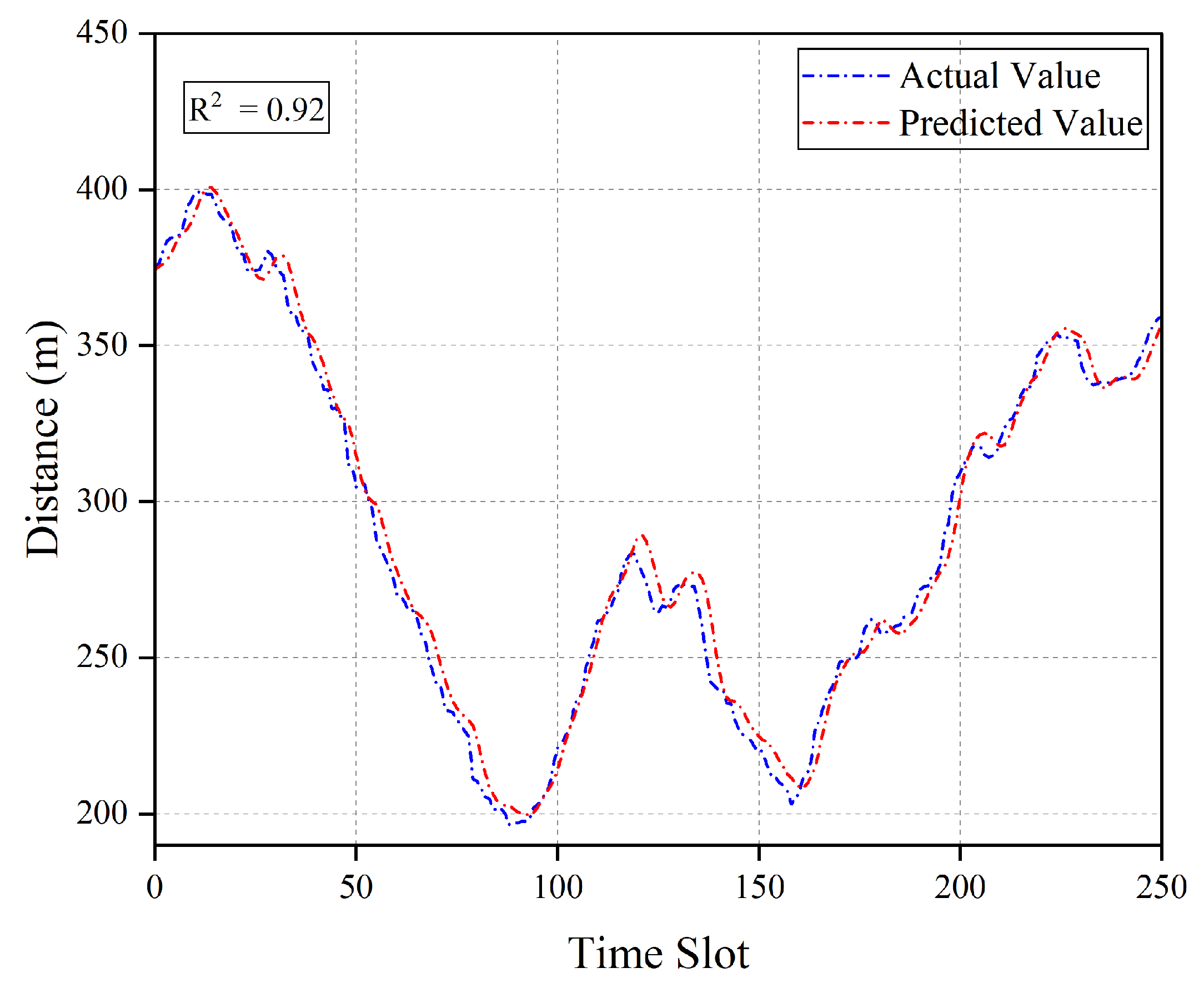
Figure 5 describes the comparison result of the LSTM-predicted values and actual values for a single user position. To more intuitively present the user position at each time slot, we further convert the user coordinates into the distance between the user and the jammer. As shown in
Figure 5, the two curves of predicted values and actual values achieve good fitting (coefficient of determination
). This indicates that the LSTM model can effectively capture the temporal features of user position changes and achieve relatively accurate predictions.
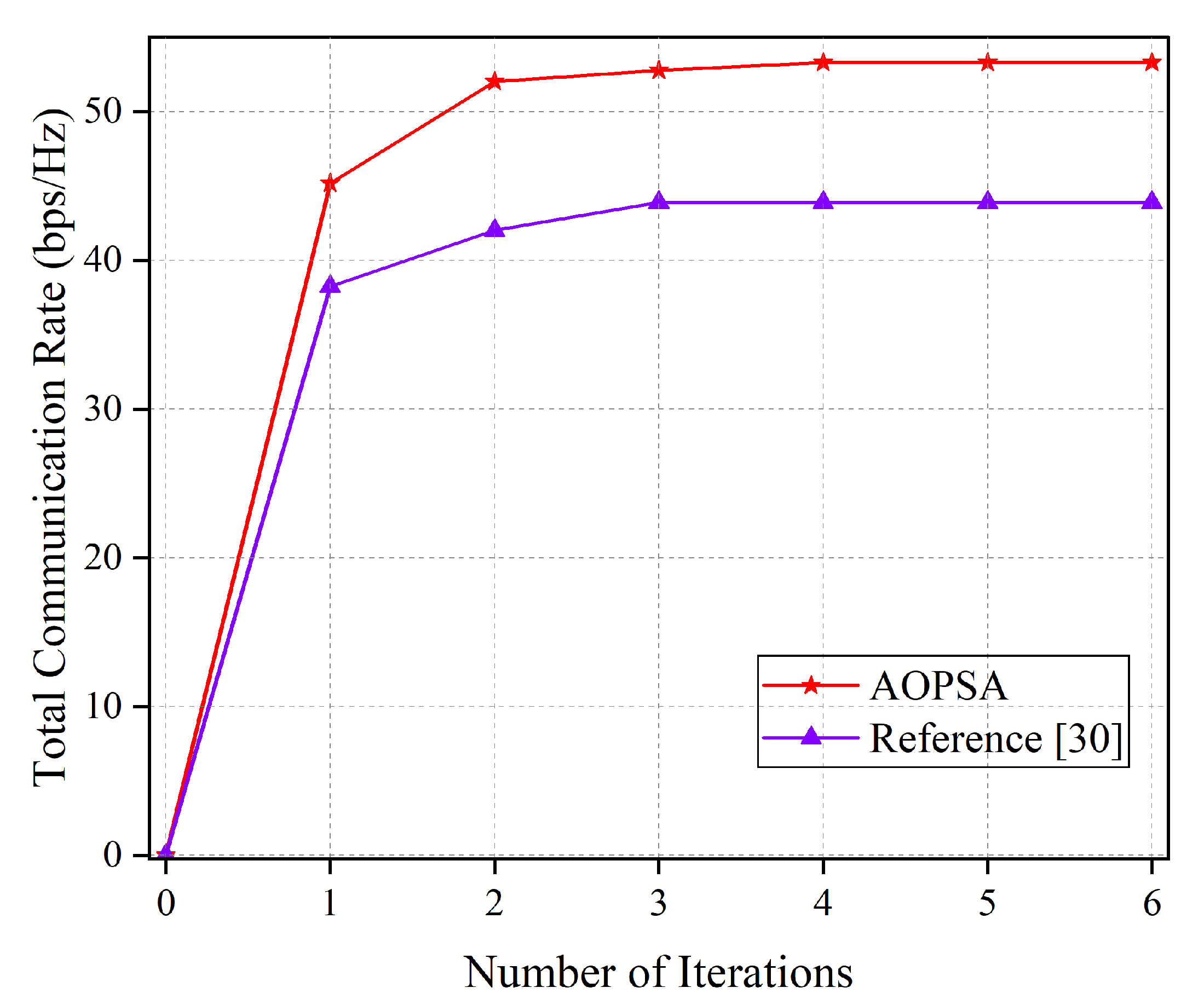
Before comparing the performance of different schemes, we validate the convergence behavior of the AOPSA. As illustrated in
Figure 6, we compare the total communication rate of AOPSA (per single time slot) with that of the algorithm in reference [
30] as a function of iteration numbers. The results demonstrate that AOPSA rapidly increases the communication rate to 53 bps/Hz within the first four iterations and maintains stable performance thereafter. Compared to reference [
30], our proposed algorithm achieves approximately 23.2% performance improvement, demonstrating favorable convergence behavior and effectiveness.
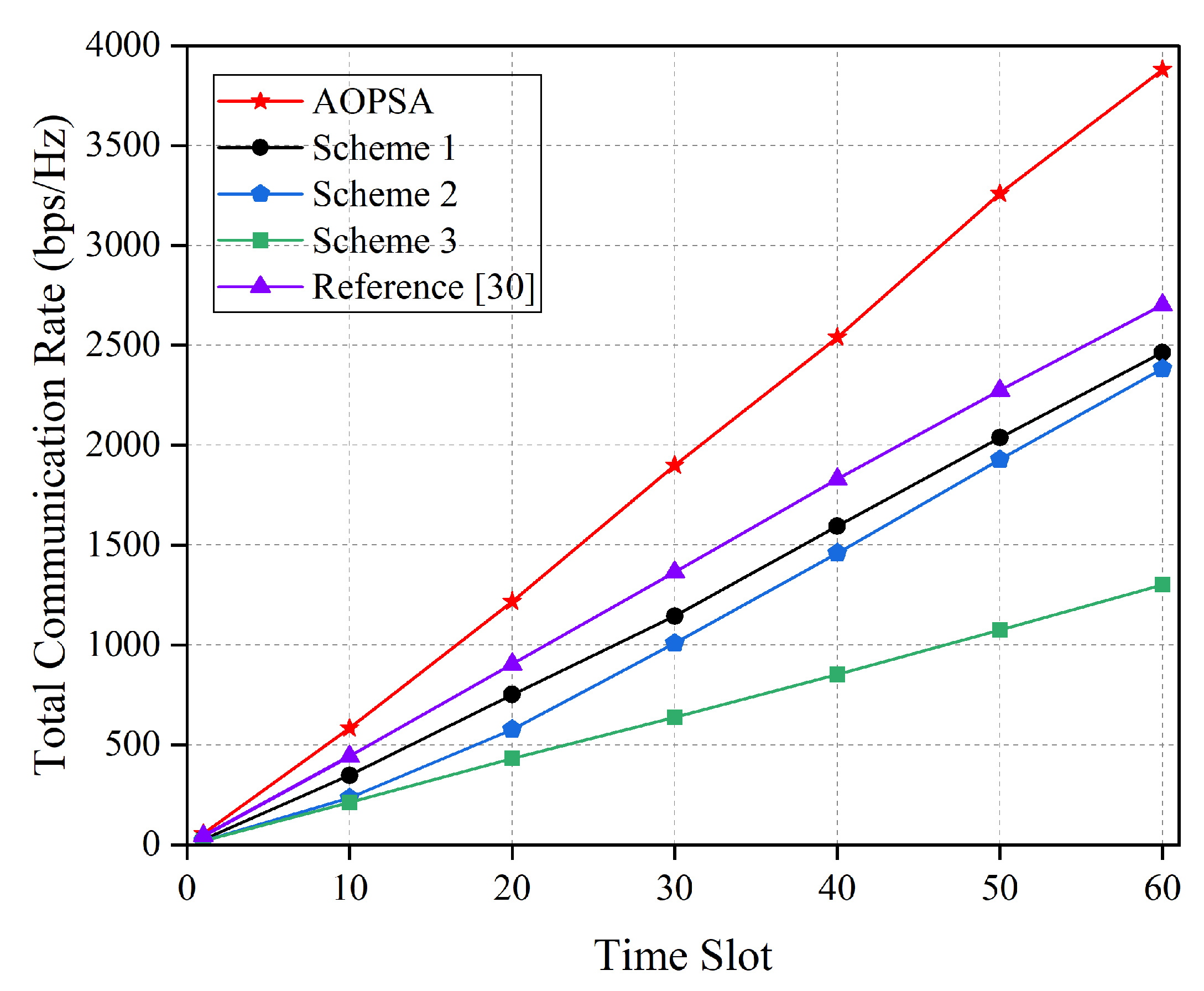
Figure 7 shows the comparison of total communication rate for five optimization schemes over the entire flight time. It can be observed that as the number of time slots increases, the total communication rates of all schemes show an upward trend. The best performance is achieved by AOPSA, which reaches approximately 3750 bps/Hz at 60th time slot. Reference [
30] reaches 2650 bps/Hz, while baseline scheme 3 is only around 1300 bps/Hz. Compared with [
30], AOPSA achieves a 41.5% performance improvement, and compared with baseline scheme 3, the performance improvement reaches up to 188%. This result fully demonstrates AOPSA’s effectiveness in solving the joint optimization problem of user association, UAV trajectory optimization, and power allocation.
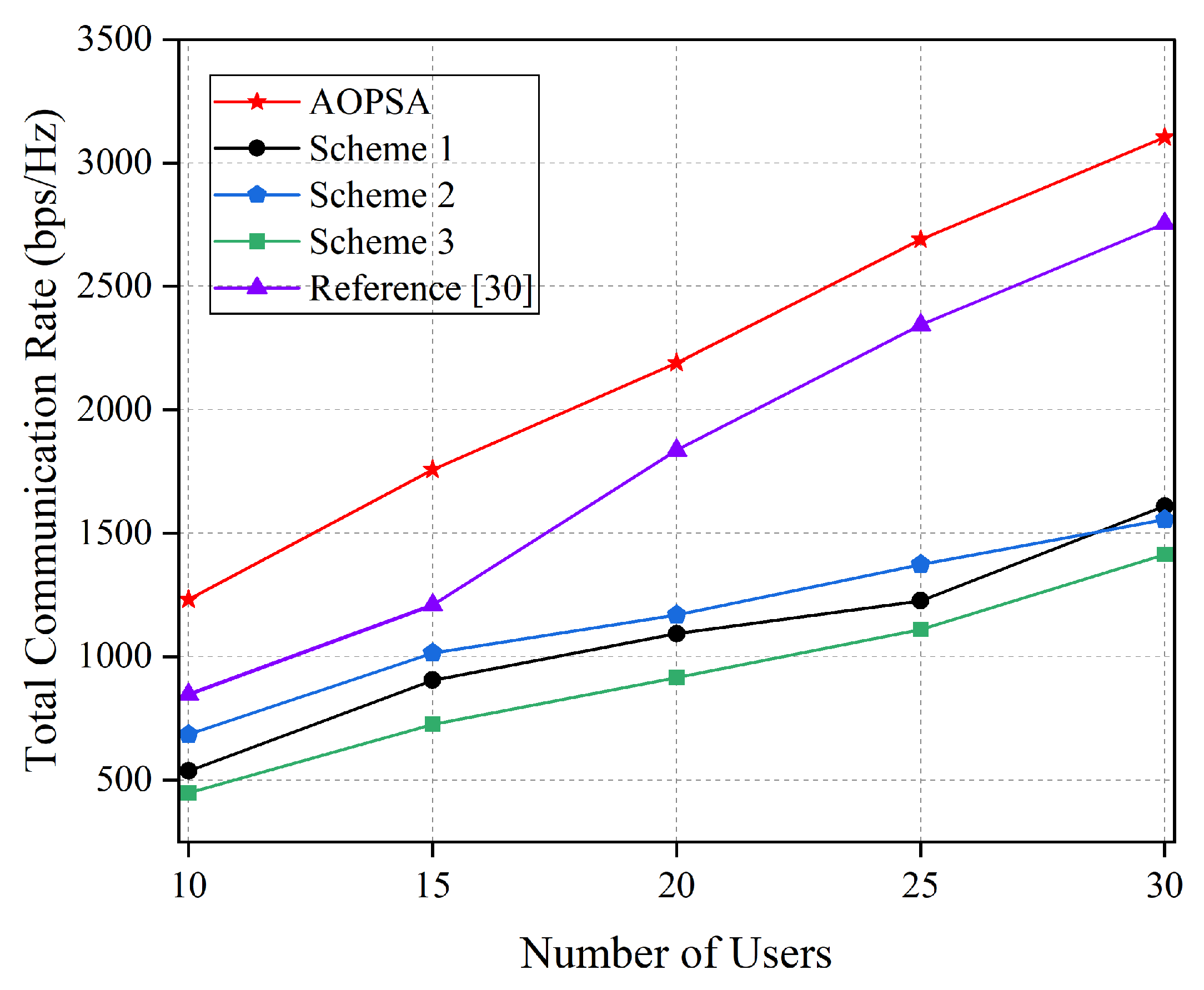
Figure 8 compares the variation trend of the total communication rate for five optimization schemes under different numbers of users. It can be seen that with the increase in the number of users, the total communication rates of all schemes show an upward trend. AOPSA consistently maintains the best performance, demonstrating higher scalability. This indicates that AOPSA has stronger resource optimization and scheduling capabilities when dealing with multiple scenarios, and can effectively cope with challenges brought by changes in the number of users, providing a reliable performance guarantee for practical deployments.
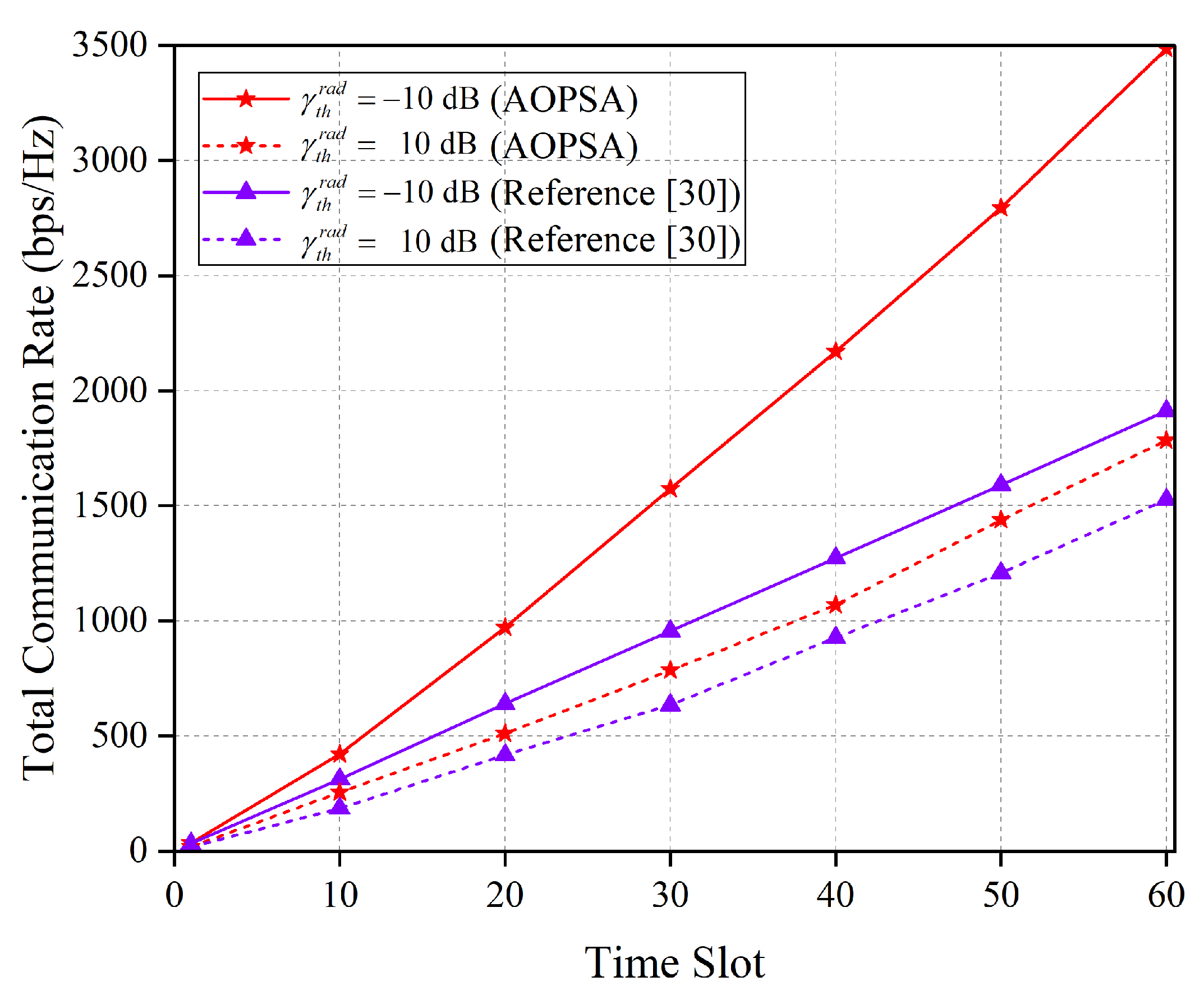
Figure 9 illustrates the performance comparison between the AOPSA and the reference [
30] algorithm in terms of the total communication rate over all time slots under different
. It can be observed that under the same
constraint, the total communication rate of AOPSA is significantly higher than that of the reference [
30] algorithm. As the
value increases, the total communication rates of both algorithms exhibit a decreasing trend. This result indicates that a higher
value requires more resources to meet the sensing performance requirements, thereby leading to a degradation in communication performance. Nevertheless, AOPSA still demonstrates superior performance, achieving an effective balance between communication and sensing.
As shown in
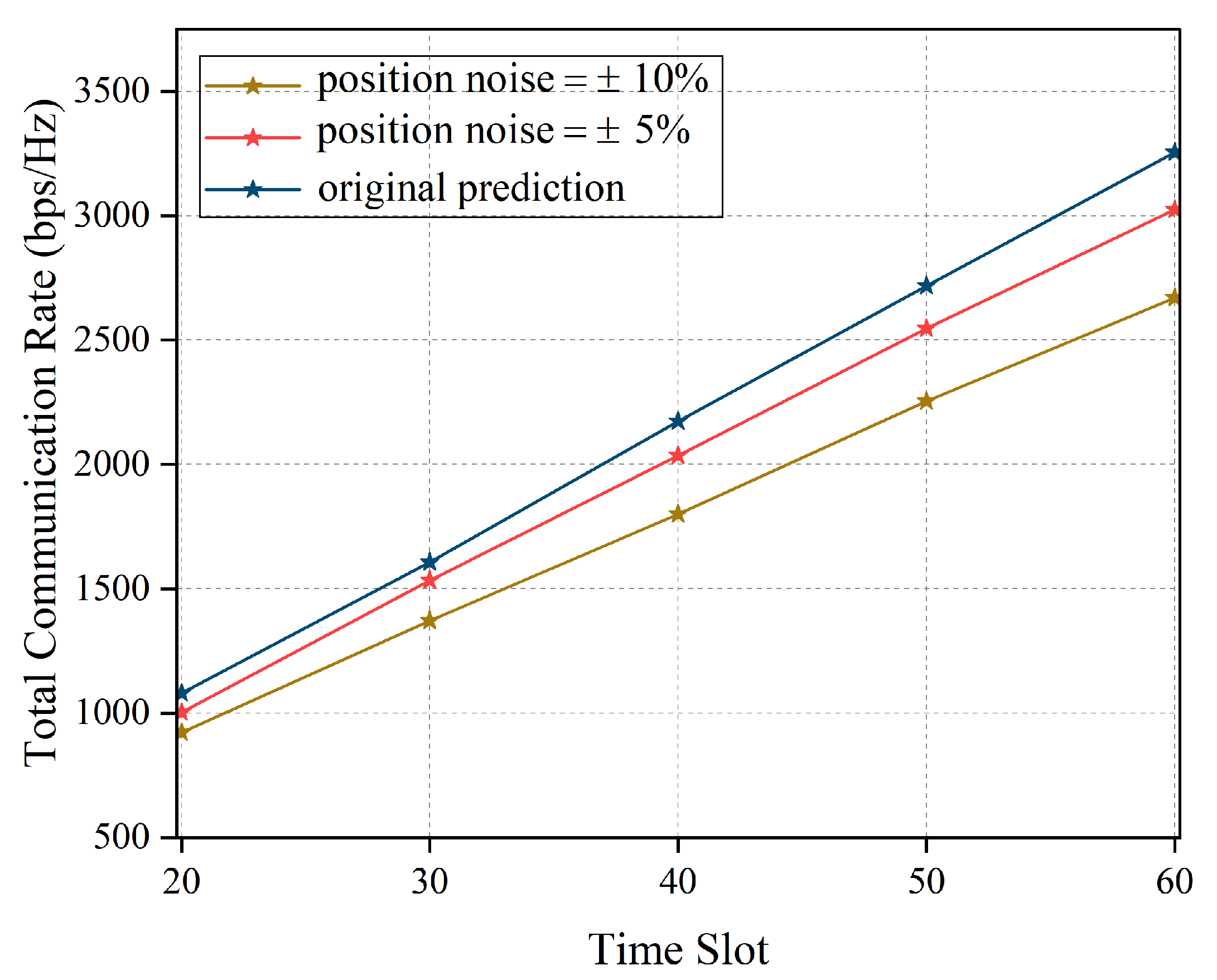
Figure 10, we compare the total communication rate of AOPSA under different prediction position noise conditions across time slots. It can be observed that the blue curve represents performance under ideal prediction conditions, with the communication rate increasing from approximately 1100 bps/Hz to 3300 bps/Hz while maintaining the highest transmission efficiency. In practical scenarios with prediction position noise, system performance decreases to varying degrees: the red curve (position noise ±5%) shows communication rates ranging from 1000 bps/Hz to 3000 bps/Hz; the yellow curve (position noise ±10%) exhibits the lowest performance, with rates increasing from 900 bps/Hz to 2600 bps/Hz. This demonstrates that position prediction accuracy significantly impacts system communication performance. As position noise increases, the deviation between system performance and ideal prediction gradually enlarges, further emphasizing the importance of adopting robust prediction algorithms in practical applications.
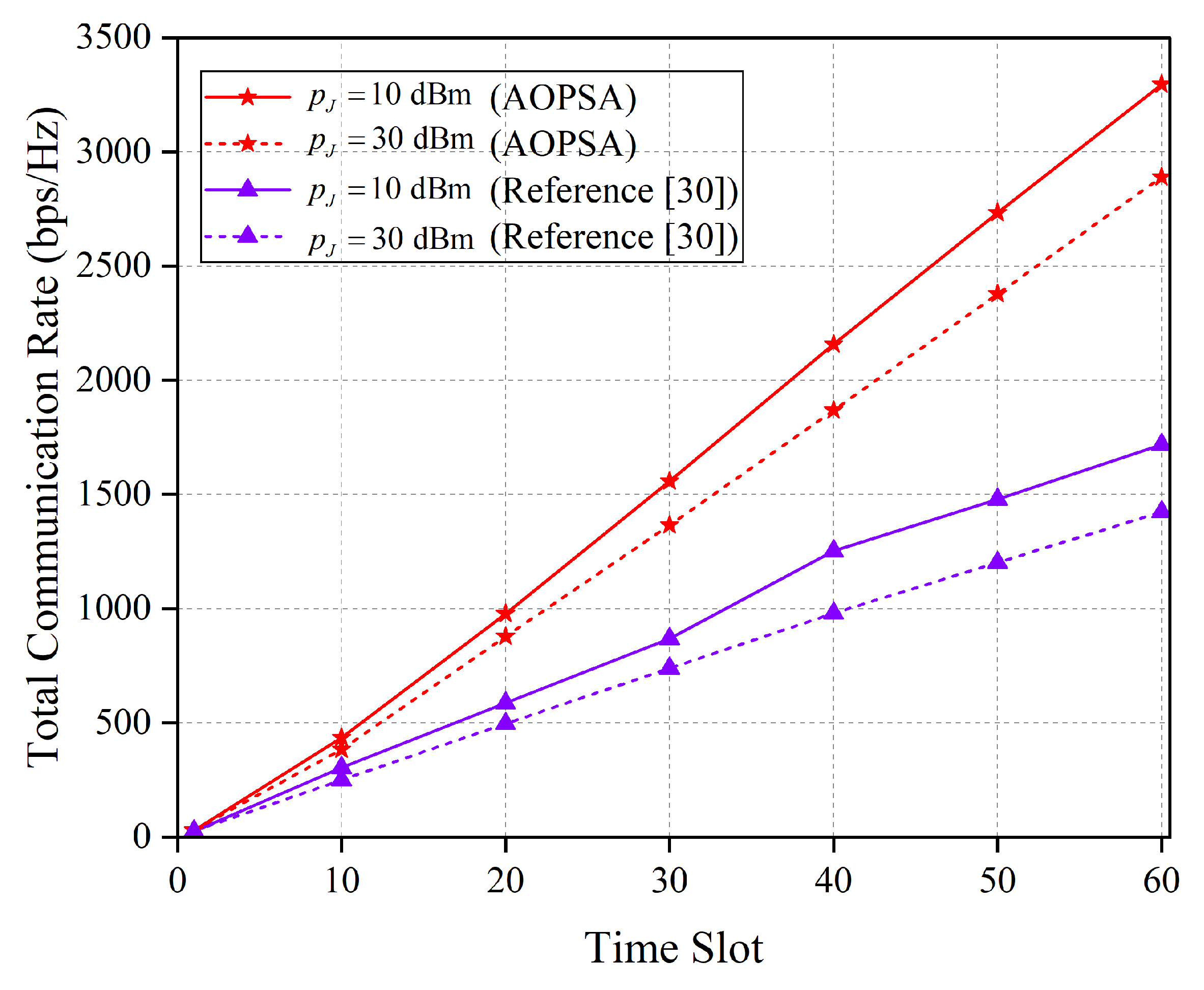
As shown in
Figure 11, the total communication rate of the AOPSA and the algorithm in reference [
30] is compared across all time slots under different
values. The results demonstrate that as
increases, the performance of both algorithms declines. Nevertheless, AOPSA consistently outperforms the reference [
30] algorithm. This indicates that the jamming power
directly affects the SINR of the communication link. Specifically, an increase in
intensifies the jamming imposed by the jammer on the user, leading to a reduction in the communication SINR and a consequent significant decrease in the communication rate.
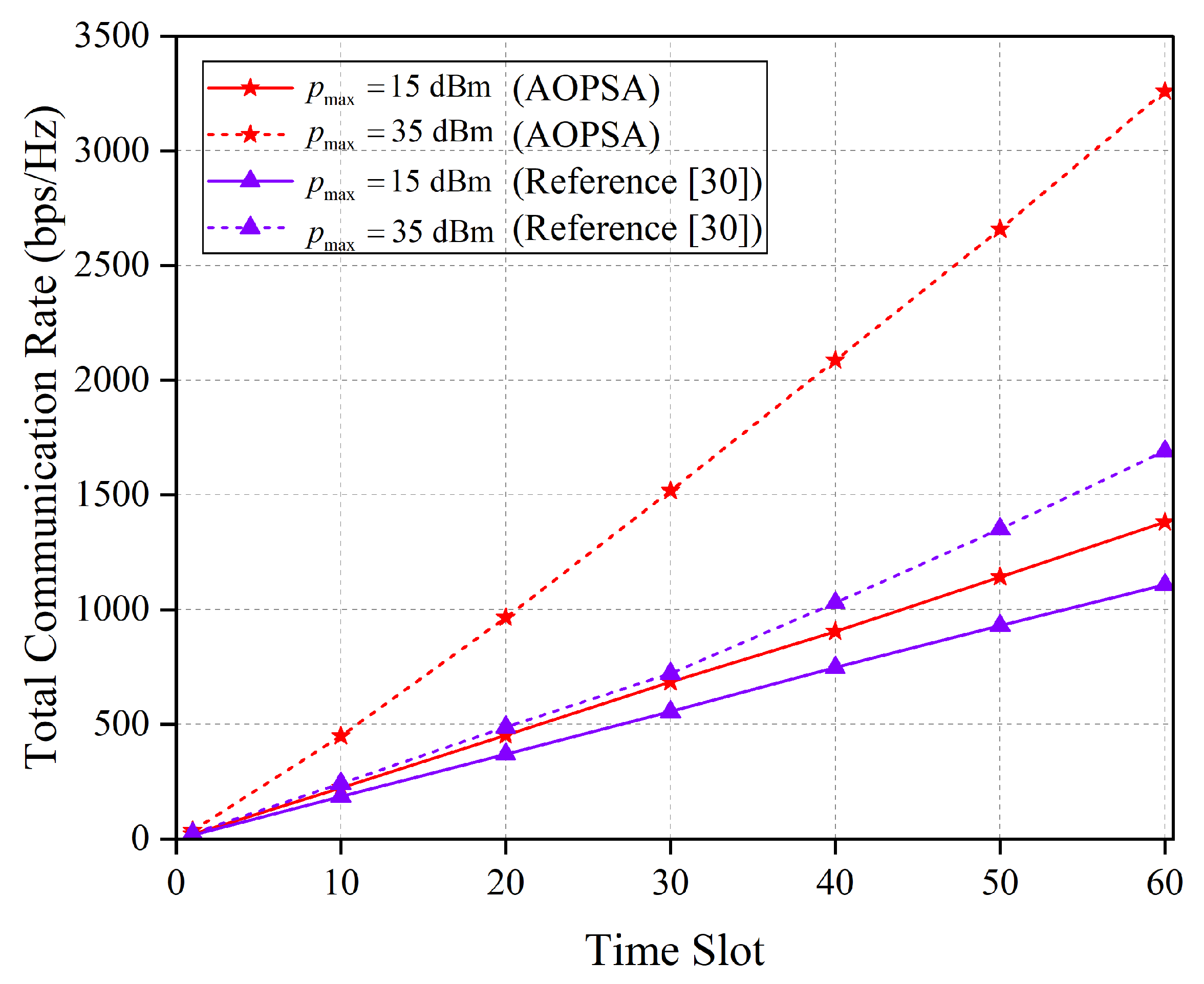
Figure 12 presents a comparison of the total communication rate between AOPSA and the algorithm in reference [
30] across all time slots under different
values. As shown in the figure, the performance of both algorithms improves as
increases, with AOPSA consistently outperforming the reference [
30] algorithm. This result indicates that a higher
value expands the feasible region for optimizing the UAV transmit power, allowing the algorithm to more flexibly adjust the power allocation within the extended constraint, thereby achieving significant performance enhancement.
6. Conclusions
This paper focuses on the multi-UAV-assisted ISAC system under malicious jamming environments, studying the joint optimization problem of user association, UAV trajectory planning, and transmit power allocation. To address the impact of user mobility and enhance system real-time performance, this paper proposes a user position prediction model based on LSTM to achieve accurate prediction of user positions in future time slots. To reduce the impact of malicious jamming and maximize the total communication rate of users, this paper adopts IAA, DOA, and RRTOA to optimize user association, UAV trajectory, and UAV transmit power, respectively. On this basis, the AOPSA is proposed to achieve joint optimization of the three variables. Simulation results demonstrate that the proposed algorithms can significantly improve the system’s total communication rate under malicious jamming environments, providing reliable technical support for practical deployment.
However, this paper primarily focuses on the analysis and discussion of stationary jammers. In practical scenarios, jammers are often mobile and possess a certain level of intelligence, enabling them to dynamically adjust their jamming methods and positions based on the countermeasures adopted by the communication system. This significantly enhances jamming efficiency and concealment. Such dynamic and intelligent jamming behaviors pose more severe challenges to existing anti-jamming schemes. Therefore, in future work, we will further investigate the underlying mechanisms of dynamic intelligent jamming scenarios and, on this basis, develop corresponding intelligent anti-jamming and collaborative communication strategies to improve the robustness of the system in such dynamic and intelligent jamming environments.