1. Introduction
Quantum cryptography, with its theoretically unconditional security feature, has gradually become an important research area in the field of cryptography. Unlike classical cryptography, the security of quantum cryptography is based on the quantum no-cloning theorem and Heisenberg’s uncertainty principle. As a result, it has attracted significant attention from researchers. Quantum cryptography includes several research areas, such as quantum key distribution (QKD) [
1,
2,
3,
4], quantum secret sharing (QSS) [
5,
6,
7], quantum secure direct communication (QSDC) [
8,
9,
10], quantum private query (QPQ) [
11,
12,
13,
14], and quantum key agreement (QKA). Among these, quantum key agreement (QKA) requires each participant to equally contribute to the generation of the negotiated key, ensuring that any non-trivial subset of participants cannot independently determine the key. In 2004, Zhou et al. [
15] innovatively applied quantum teleportation to key agreement, proposing the first quantum key agreement (QKA) protocol. However, Tsai et al. [
16] identified a significant flaw in Zhou’s protocol where a participant could independently determine the negotiated key. Subsequently, Hsueh et al. [
17] implemented a QKA protocol using maximally entangled states. Nevertheless, Hsueh et al.’s protocol was vulnerable to controlled-NOT attacks [
18]. In 2011, Chong et al. [
19] enhanced the security of Hsueh et al.’s protocol. In 2013, Shi et al. [
20] extended the two-party QKA to be multi-party and proposed the first multi-party QKA protocol, which utilizes the Bell state as the quantum resource state and employs entanglement swapping technology. On this basis, Sun et al. [
21] proposed an efficient quantum key agreement protocol based on commutative encryption. Wang et al. [
22] proposed a multi-party semiquantum key agreement without entanglement. In addition to these efforts, numerous QKA protocols have been proposed, such as the schemes based on a single particle [
23,
24,
25,
26], the Bell state [
27,
28,
29,
30,
31,
32], and a multi-particle entangled state [
33,
34,
35,
36,
37,
38,
39,
40].
Resently, Xu et al. [
41] proposed a single-state multi-party semiquantum key agreement protocol based on multi-particle entangled states which offers several key advantages: it uses only one kind of multi-particle entangled state as the initial quantum resource; it does not require pre-shared keys between different parties; and it eliminates the need for unitary operations or quantum entanglement swapping. Subsequently, Yang et al. [
42] proposed an efficient single-state multi-party quantum key agreement which retains most of the advantages of Xu et al.’s scheme while achieving significant improvements in the number of quantum state transmissions, the number of qubits consumed, and qubit efficiency.
In this paper, a single-state three-party quantum key agreement protocol utilizing single-particle measurements is proposed. We conduct a detailed analysis demonstrating that our scheme can resist potential internal and external attacks. Furthermore, we extend the proposed single-state three-party quantum key agreement protocol to be N-party by using N-particle entangled states instead of three-particle entangled states as the quantum resource states. Compared to previous multi-party QKA schemes, our protocol retains most of the advantages presented in references [
41,
42] while only requiring the use of the
X measurement basis and
Z measurement basis. Additionally, our protocol further reduces the number of qubits transmitted and consumed, and enhances qubit efficiency.
The rest of the paper is organized as follows: In
Section 2, we describe the single-state three-party quantum key agreement protocol in detail.
Section 3 provides a security analysis of the protocol. In
Section 4, we extend the proposed single-state three-party quantum key agreement protocol to be N-party.
Section 5 discusses the performance of our scheme.
Section 6 provides a conclusion.
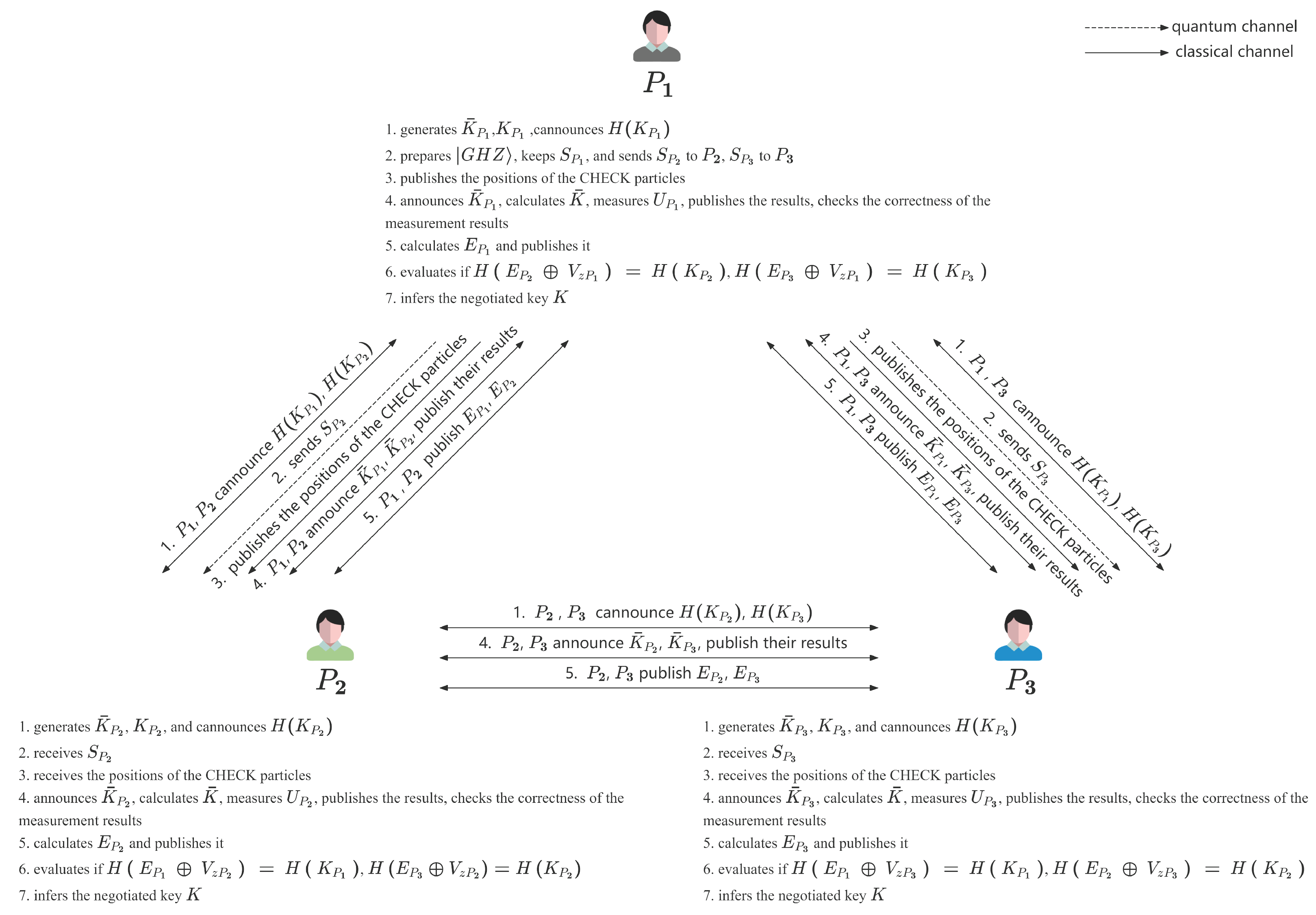
2. The Proposed Single-State Three-Party Quantum Key Agreement with Single-Particle Measurement
Suppose , , and seek to establish a private key over a quantum channel, ensuring that each participant contributes equally to the generation of the key and that the key cannot be fully determined by any non-trivial subset of them. In the negotiation phase, the utilization of a hash function outputting m bits is necessary.
Step 1:
,
, and
randomly generate the CHECK keys
and the INFO keys
Here, l represents the number of the CHECK particles, n represents the length of the negotiated key, and . They calculate the hash values corresponding to the keys and announce the values.
Step 2:
prepares
three-particle GHZ states
. For each GHZ state,
keeps the first particle, and sends the second particle to
and the third particle to
. We denote the first particle sequence as
, the second particle sequence as
, and the third particle sequence as
as follows:
Step 3: After
receives
and
receives
,
randomly selects
l particles as the CHECK particles, and informs
,
of the positions of the CHECK particles. Here, the CHECK particles held by
are denoted as
, respectively, as follows:
Then,
announce the CHECK keys
. They calculate
In this equation,
. For the
q-th CHECK particle, when the value of
is 0,
uses basis
Z to measure the particle
and publishes the results, where
. When the value of
is 1,
uses basis
X to measure the particle
and publishes the results, where
. Suppose that the measurement results in basis
Z are
, and in basis
X are
. According to the entanglement properties of the three-particle GHZ state and Equation (
14),
can check the correctness of the measurement results. When the chosen basis is Z, the measurement results must satisfy . When the chosen basis is X, the measurement results must satisfy . If the error exceeds the threshold, the protocol aborts. The remaining particles serve as INFO particles . measures the particles with basis Z.
Step 4: The measurement results are represented by . If the measurement result is , its value is taken as 0; if the measurement result is , its value is taken as 1. According to the entanglement properties of the three-particle GHZ state, we can obtain . calculates and sends it to , . calculates and sends it to , . calculates and sends it to , .
Step 5:
calculates
,
. If
and
,
will infer the final negotiated key
calculates
,
. If
and
,
will infer the final negotiated key
calculates
,
. If
and
,
will infer the final negotiated key
As shown in
Figure 1, the flowchart depicts the mechanism of the proposed MQKA protocol.
3. Security Analysis
This section will discuss the security of the proposed protocol. Without loss of generality, we analyze the security of the proposed three-party QKA protocol. The security analysis encompasses both internal attacks and external attacks.
3.1. External Attack
In the proposed three-party protocol, in order to obtain the negotiated key, an external attacker may launch typical attacks during the transmission of quantum states, including the Trojan horse attack, the intercept–resend attack, the entangle–measure attack, and the measure–resend attack.
3.1.1. The Trojan Horse Attack
In our scheme, since each particle is transmitted only once, our three-party QKA protocol is immune to the delay-photon Trojan horse attack [
43] and the invisible eavesdropping Trojan horse attack [
44].
3.1.2. The Intercept–Resend Attack
The external attacker may intercept the particles
transmitted and resend the fake states to
,
. Without loss of generality, suppose that Eve intercepts the particles
and sends the fake particles to
. Taking the
q-th fake CHECK particle
(
) as an example, the
q-th system state can be described as
Firstly, we consider the scenario where the measurement basis is Z. When the measurement results of are , we can obtain . Eve is capable of evading eavesdropping detection.
When the measurement results of are , we can obtain . Eve can be detected by the eavesdropping detection.
Secondly, we consider the scenario where the measurement basis is X. When the measurement results of in or , we can obtain . Eve is capable of evading eavesdropping detection.
When the measurement results of in or , we can obtain . Eve is unable to evade eavesdropping detection.
Therefore, for each CHECK particle, Eve is capable of evading eavesdropping detection with the probability of
For all l CHECK particles, Eve can be detected with the probability of .
3.1.3. The Entangle–Measure Attack
The external attacker may perform the entangle–measure attack. Without loss of generality, suppose that Eve intercepts the particles
transmitted to
(
), and performs unitary operation
on the intercepted particles. If this attack does not introduce any errors, the system state of Eve’s probe should be independent of the measurement results of
. The effect of
on
and
can be described as
In this equation,
,
,
, and
are the probe state of Eve on
, and
,
. The global state of the system can be described as
In this equation, the subscripts
,
, and
denote the particles from
,
, and
, respectively. If Eve does not introduce any errors during the eavesdropping check by participants, the measurement results of
,
, and
should be the same. Thereby, Eve’s attack
should be satisfied with the conditions
Based on Equation (
22), we can infer
Here, 0 represents a column zero vector. Then, we can obtain
Furthermore, we can obtain
Based on the aforementioned proof, in the absence of errors induced by Eve’s attack, the ultimate system state of Eve’s probe should be independent of the measurement results of the particles from , , and . Therefore, Eve is unable to obtain any useful information about the measured particles. Once Eve acquires any useful information, Eve’s attack will be detected with a nonzero probability.
3.1.4. The Measure–Resend Attack
The external attacker may intercept the particles transmitted, measure the particles, and resend the fake states to , . Without loss of generality, suppose that Eve intercepts the particles , measures the intercepted particles with Z basis, and sends the fake particles to . Clearly, the system state has a probability of for being and a probability of for being .
Firstly, we consider the scenario where the system state is . When the measurement basis is Z, the measurement results of , , are , and we can obtain . Eve is capable of evading eavesdropping detection.
When the measurement basis is X and the measurement results of , , in , , or , we can obtain . Eve is capable of evading eavesdropping detection.
When the measurement results of , , in , , or , we can obtain . Eve is unable to evade eavesdropping detection.
Secondly, we consider the scenario where the system state is . When the measurement basis is Z, the measurement results of , , are , and we can obtain . Eve is capable of evading eavesdropping detection.
When the measurement basis is X and the measurement results of , , in , , or , we can obtain . Eve is capable of evading eavesdropping detection.
When the measurement results of , , in , , or , we can obtain . Eve is unable to evade eavesdropping detection.
Therefore, for each CHECK particle, Eve is capable of evading eavesdropping detection with the probability of
For all l CHECK particles, Eve can be detected with the probability of .
3.2. Internal Attack
A secure quantum key agreement protocol is required to possess the fairness property, ensuring that all participants contribute equally to the negotiated key. In the proposed protocol, under the condition that all participants honestly execute the protocol prior to Step 4, they will be able to successfully obtain
. In Step 4,
calculates the value of
and publishes it to other participants, where
. However,
may announce the false value of
. Without loss of generality, suppose that
intends to determine the negotiated key
alone. In Step 4,
publishes the value of
, and
publishes the value of
. Based on the value of
and
,
can calculate the value of
and announce the false value of
to
,
, where
.
Based on the value of
,
can infer the false value of
can infer the false value of
Nevertheless, as the hash value,
The dishonest behavior of will be detected by , .
Similarly, in the event that two dishonest participants collude to execute the cheating behavior, their cheating behavior will be exposed through the utilization of the hash function’s properties.
4. The Extension of the Proposed Scheme
Suppose seek to establish a private key over a quantum channel, ensuring that each participant contributes equally to the generation of the key and that the key cannot be fully determined by any non-trivial subset of them. In the negotiation phase, the utilization of a hash function outputting m bits is necessary.
Step 1:
randomly generates the CHECK keys
and the INFO keys
Here, l represents the number of the CHECK particles, n represents the length of the negotiated key, and , . calculates the hash values and announces the values.
Step 2:
prepares
N-particle GHZ states
. For each GHZ state,
keeps the first particle, and sends the t-th particle to
, where
. We denote the
i-th particle sequence as
as follows:
Here, .
Step 3: After
receives
,
randomly selects
l particles as the CHECK particles and informs other participants of the positions of the CHECK particles. Here, the CHECK particles respectively held by
are denoted as
as follows:
Then,
announces the CHECK keys
and calculates
Here,
. For the
q-th CHECK particle, when the value of
is 0,
uses the
Z basis to measure the particle
and publishes the measurement results, where
. When the value of
is 1,
uses the
X basis to measure the particle
and publishes the measurement results, where
. Suppose that the measurement results in basis
Z are
and in basis
X are
. According to the entanglement properties of the N-particle GHZ state and Equation (
40),
In this equation, , , . can check the correctness of the measurement results. When the chosen basis is Z, the measurement results must satisfy . When the chosen basis is X, the measurement results must satisfy . If the error exceeds the threshold, the protocol aborts. The remaining particles serve as INFO particles . measures the particles with the Z basis.
Step 4: The measurement results are represented by . If the measurement result is , its value is taken as 0; if the measurement result is , its value is taken as 1. According to the entanglement properties of the N-particle GHZ state, we can obtain . calculates and sends it to other participants.
Step 5:
calculates
. If
,
will infer the final negotiated key
In this equation, , . If any participant refuses K as the negotiated key, the protocol will be terminated and restarted.
5. Discussions
Reference [
45] provides a definition of qubit efficiency,
In this equation, q is the number of transmitted qubits, c is the number of consumed classical bits, and f is the number of bits of the negotiated key. In the proposed protocol, prepares N-particle entangled states, and it has . For the consumed classical bits, in order to announce the hash , the CHECK keys , the measurement results of , and the ciphertext , needs to spend m, l, l, and n classical bits, respectively, where m is the length of the hash function . For N participants, the number of needed classical bits is . The length of the negotiated key is n; therefore, . Therefore, the qubit efficiency is . When l is the same as n, the qubit efficiency .
In comparison to the previous MQKA protocols, as illustrated in
Table 1, our protocol demonstrates great advantages. Our scheme retains most of the advantages of the schemes in [
41,
42] using one kind of multi-particle entangled state as the initial quantum resource, and eliminates the need for entanglement swapping techniques, unitary operations, or pre-shared keys between participants. In addition, our scheme uses only the X and Z bases for measurement, making it simpler and more practical than scheme [
41], which uses GHZ and Z bases, and scheme [
42], which uses X, Y, and Z bases. In terms of qubit transmission, our scheme and reference [
42] require only one transmission from participant P1 to P2 (P3), while scheme [
41] involves additional steps of reflecting or resending particles. Regarding qubit consumption, our scheme and reference [
42] consume
qubits, whereas reference [
41] consumes
qubits. Moreover, our scheme achieves a qubit efficiency of
, compared to
for reference [
41] and
for reference [
42]. These advantages make our scheme more efficient and practical for implementation.
6. Conclusions
In this paper, a single-state multi-party quantum key agreement (MQKA) protocol utilizing single-particle measurement is proposed. We introduce a single-state three-party quantum key agreement protocol with single-particle measurement followed by a comprehensive security analysis. Building on this foundation, we further extend this approach by employing multi-particle entangled states to develop a multi-party version of the single-state multi-party quantum key agreement with single-particle measurement. Specifically, it employs one kind of multi-particle entangled state as the quantum resource, eliminating the need for entanglement swapping techniques, unitary operations, or pre-shared keys between participants. Moreover, the protocol uses only the X measurement basis and Z measurement basis, which results in fewer qubits being transmitted and consumed, and higher qubit efficiency. While our method can be extended to a multi-party version, the preparation of multi-particle entangled states remains a significant challenge that warrants further investigation.