A Quantum Proxy Signature Scheme Without Restrictions on the Identity and Number of Verifiers
Abstract
1. Introduction
2. The Construction of Quantum One-Way Function
3. The Proposed Scheme
- Original signer: This participant has the original signing authority. They share the key with the proxy signatory through quantum key distribution and delegate the signing authority to the proxy signatory.
- Proxy signer: After this participant shares a key with the original signer through quantum key distribution, they sign on behalf of the original signer.
- Trusted center: An advanced trusted node, possessing control over the entire scheme.
3.1. The Initialization Stage
| Algorithm 1: Initialization Stage |
1 Key Distribution via QKD; 2 ; 3 ; 4 ; 5 Entanglement Establishment; 6 ; 7 State Preparation and Teleportation; 8 ; 9 ; 10 Public Parameter Publication; 11 ; 12 ; 13 ; 14 return
; |
3.2. The Authorization Stage
| Algorithm 2: Authorization Stage |
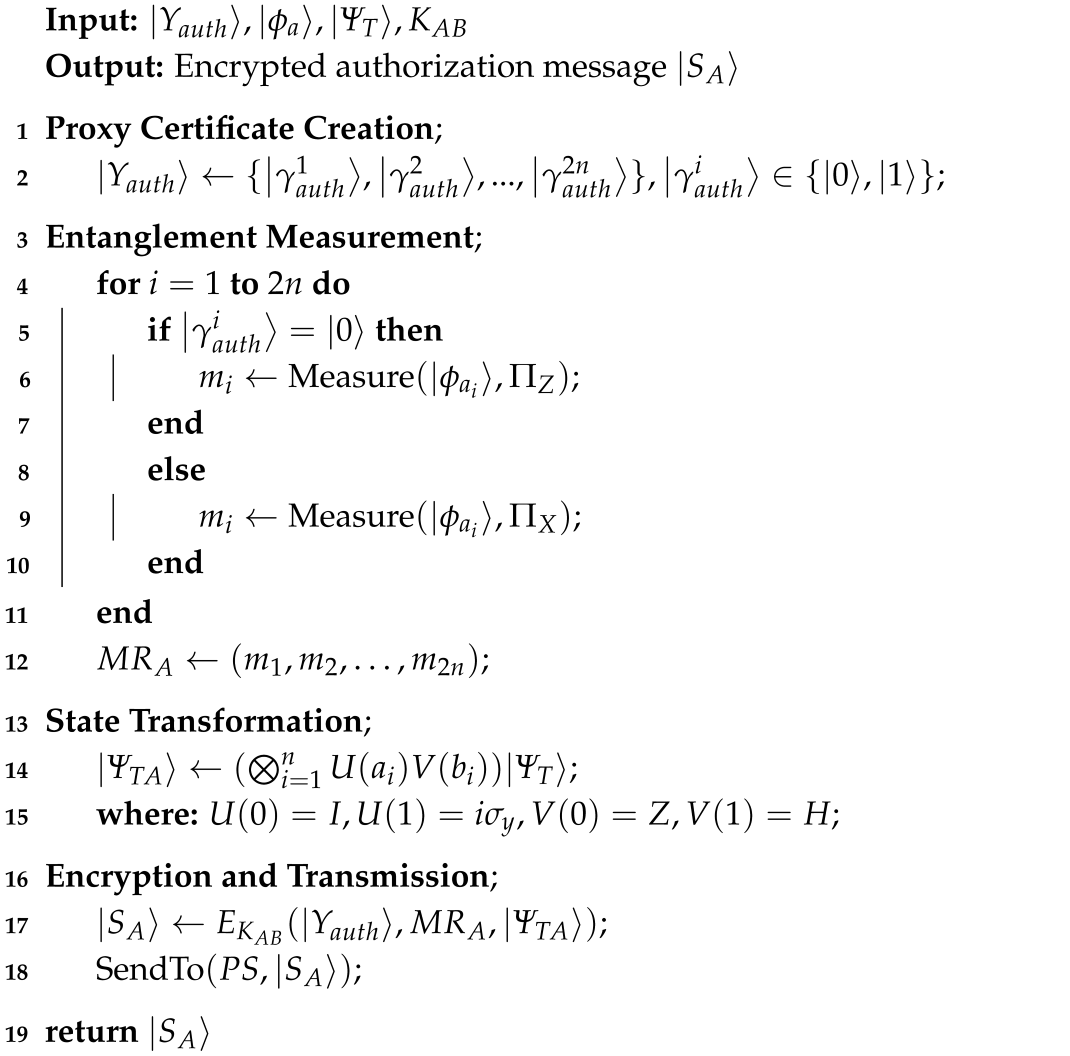 |
3.3. The Signature Stage
| Algorithm 3: Signature Stage |
 |
3.4. The Verification Stage
| Algorithm 4: Verification Stage |
 |
4. Security Analysis
4.1. Anti-Honesty Termination
4.2. Anti-Repudiation Attack
4.3. Anti-Forgery Attack
5. Summary
Funding
Data Availability Statement
Conflicts of Interest
References
- Rivest, R.L.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic Curve Cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for Quantum Computation: Discrete Logarithms and Factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Grover, L.K. A Fast Quantum Mechanical Algorithm for Database Search. In Proceedings of the 28th Annual ACM Symposium on the Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Pedernales, J.S.; Di Candia, R.; Egusquiza, I.L.; Casanova, J.; Solano, E. Efficient Quantum Algorithm for Computing n-time Correlation Functions. Phys. Rev. Lett. 2014, 113, 020505. [Google Scholar] [CrossRef] [PubMed]
- Sato, Y.; Tezuka, H.; Kondo, R.; Yamamoto, N. Quantum Algorithm for Partial Differential Equations of Nonconservative Systems with Spatially Varying Parameters. Phys. Rev. Appl. 2025, 23, 014063. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Lange, T. Post-Quantum Cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef]
- Singh, M.; Sood, S.K.; Bhatia, M. Post-Quantum Cryptography: A Review on Cryptographic Solutions for the Era of Quantum Computing. Arch. Comput. Methods Eng. 2025. [Google Scholar] [CrossRef]
- Cherkaoui, D.K.; Tasic, I.; Cano, M.D. Exploring Post-Quantum Cryptography: Review and Directions for the Transition Process. Technologies 2024, 12, 241. [Google Scholar] [CrossRef]
- Liu, Y.K.; Dustin, M. Post-quantum cryptography and the quantum future of cybersecurity. Phys. Rev. Appl. 2024, 21, 040501. [Google Scholar] [CrossRef]
- Kim, M.S.; Rehman, S.; Khan, M.F.; Kim, S. Mem-Transistor-Based Gaussian Error–Generating Hardware for Post-Quantum Cryptography Applications. Adv. Quantum Technol. 2025, 8, 2400394. [Google Scholar] [CrossRef]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Wang, X.; Zhang, S.; Khan, M.K. QF2PM: Quantum-Secure Fine-Grained Privacy-Preserving Profile Matching for Mobile Social Networks. IEEE Trans. Netw. Sci. Eng. 2025. early access. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Zhang, S. Quantum multi-party private set intersection using single photons. Phys. A Stat. Mech. Its Appl. 2024, 649, 129974. [Google Scholar] [CrossRef]
- Guo, H. Quantum Cryptography, 1st ed.; Science Press: Beijing, China, 2023; pp. 45–89. [Google Scholar]
- Huang, X.; Zhang, W.; Zhang, S. Practical quantum protocols for blind millionaires’ problem based on rotation encryption and swap test. Phys. A Stat. Mech. Its Appl. 2024, 637, 129614. [Google Scholar] [CrossRef]
- Gottesman, D.; Chuang, I. Quantum digital signatures. arXiv 2001, arXiv:quant-ph/0105032. [Google Scholar] [CrossRef]
- Zhan, L.; Zhang, C.-H.; Lu, N.; Qian, X.-R.; Ding, H.-J.; Liu, J.-Y.; Zhou, X.-Y.; Wang, Q. Experimental quantum digital signature based on heralded single-photon sources. Quantum Inf. Process. 2024, 23, 25. [Google Scholar] [CrossRef]
- Chapman, J.C.; Alshowkan, M.; Qi, B.; Peters, N.A. Entanglement-based quantum digital signatures over a deployed campus network. Opt. Express 2024, 32, 7521. [Google Scholar] [CrossRef]
- Clarke, P.J.; Collins, R.J.; Dunjko, V.; Andersson, E.; Jeffers, J.; Buller, G.S. Experimental demonstration of quantum digital signatures using phase-encoded coherent states of light. Nat. Commun. 2012, 3, 1174. [Google Scholar] [CrossRef]
- Yin, H.-L.; Wang, W.-L.; Tang, Y.-L.; Zhao, Q.; Liu, H.; Sun, X.-X.; Zhang, W.-J.; Li, H.; Puthoor, I.V.; You, L.-X.; et al. Experimental measurement-device-independent quantum digital signatures over a metropolitan network. Phys. Rev. A 2017, 95, 042338. [Google Scholar] [CrossRef]
- Puthoor, I.V.; Amiri, R.; Wallden, P.; Curty, M.; Andersson, E. Measurement-device-independent quantum digital signatures. Phys. Rev. A 2016, 94, 022328. [Google Scholar] [CrossRef]
- Du, Y.; Li, B.-H.; Hua, X.; Cao, X.-Y.; Zhao, Z.; Xie, F.; Zhang, Z.; Yin, H.-L.; Xiao, X.; Wei, K. Chip-integrated quantum signature network over 200 km. Light Sci. Appl. 2025, 14, 108. [Google Scholar] [CrossRef]
- Tian, Y.-L.; Feng, T.-F.; Zhou, X.-Q. Collaborative quantum computation with redundant graph state. Acta Phys. Sinaca 2019, 68, 110302. [Google Scholar] [CrossRef]
- Krishnaswamy, D. Quantum blockchain networks. In Proceedings of the Twenty-First International Symposium on Theory, Algorithmic Foundations, and Protocol Design for Mobile Networks and Mobile Computing, Virtual, 11–14 October 2020; Association for Computing Machinery: New York, NY, USA, 2020; Volume 6, pp. 327–332. [Google Scholar]
- Chawla, D.; Kumari, S.; Rathore, R.S.; Mehra, P.S.; Das, A.K.; Kumar, N. Quantum Blockchain for Internet of Things: A systematic review, proposed solutions and challenges. Comput. Electr. Eng. 2025, 126, 110524. [Google Scholar] [CrossRef]
- Hillery, M.; Bužek, V.; Berthiaume, A. Quantum secret sharing. Phys. Rev. A 1999, 59, 1829–1834. [Google Scholar] [CrossRef]
- Yang, Y.; Wen, Q. Threshold proxy quantum signature scheme with threshold shared verification. Sci. China Ser. G Phys. Mech. Astron. 2008, 51, 1079–1088. [Google Scholar] [CrossRef]
- Wang, Z.; Li, J.; Chen, X.B.; Ye, C. Quantum multi-proxy strong blind signature based on block blind coding. Quantum Inf. Process. 2022, 21, 386. [Google Scholar] [CrossRef]
- Lou, X.; Zan, H.; Xu, X. Quantum circuit-based proxy blind signatures: A novel approach and experimental evaluation on the IBM quantum cloud platform. Chin. Phys. B 2024, 33, 050307. [Google Scholar] [CrossRef]
- Prajapat, S.; Obaidat, M.S.; Bharmaik, V.; Thakur, G.; Kumar, P. Quantum Safe Proxy Blind Signature Protocol Based on 3D Entangled GHZ-Type States. Trans. Emerg. Telecommun. Technol. 2025, 36, e70140. [Google Scholar] [CrossRef]
- Niu, X.F.; Zhang, J.Z.; Xie, S.C. A Quantum multi-proxy blind signature scheme based on entangled four-qubit cluster state. Commun. Theor. Phys. 2018, 70, 043. [Google Scholar] [CrossRef]
- Wang, T.Y.; Wang, X.X.; Cai, X.Q.; Zhang, R.L. Analysis of efficient quantum multi-proxy signature. Quantum Inf. Process. 2020, 19, 8. [Google Scholar] [CrossRef]
- Chen, J.J.; You, F.C.; Li, Z.Z. Quantum multi-proxy blind signature based on cluster state. Quantum Inf. Process. 2022, 21, 104. [Google Scholar] [CrossRef]
- Yu, J.; Zhang, J. Quantum proxy threshold multiple signature scheme. Int. J. Theor. Phys. 2021, 60, 2709–2721. [Google Scholar] [CrossRef]
- Lu, Z.; Xue, Q.; Zhang, T.; Cai, J.; Han, J.; He, Y.; Li, Y. Locally verifiable approximate multi-member quantum threshold aggregation digital signature scheme. Comput. Commun. 2024, 228, 107934. [Google Scholar] [CrossRef]
- Jin-jing, S.; Rong-hua, S.; Ying, T. A multiparty quantum proxy group signature scheme for the entangled-state message with quantum Fourier transform. Quantum Inf. Process. 2011, 10, 653–670. [Google Scholar] [CrossRef]
- Şahin, M.S.; Akleylek, S. A survey of quantum secure group signature schemes: Lattice-based approach. J. Inf. Secur. Appl. 2023, 73, 103432. [Google Scholar] [CrossRef]
- Lan, L.; Lu, R.; Zhong, J.; Shi, Y. A Secure Quantum Proxy Group Signature Scheme Based on Three-qubit Entangled States. Int. J. Theor. Phys. 2024, 63, 59. [Google Scholar] [CrossRef]
- Xiong, S.; Tang, B.; Han, H.; Huang, J.; Bai, M.; Li, F.; Yu, W.; Mo, Z.; Liu, B. Efficient arbitrated quantum digital signature with multi-Receiver verification. Adv. Quantum Technol. 2024, 7, 2400110. [Google Scholar] [CrossRef]
- Zeng, G.; Keitel, C.H. Arbitrated quantum-signature scheme. Phys. Rev. A 2002, 65, 042312. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiong, S. A Quantum Proxy Signature Scheme Without Restrictions on the Identity and Number of Verifiers. Entropy 2025, 27, 1171. https://doi.org/10.3390/e27111171
Xiong S. A Quantum Proxy Signature Scheme Without Restrictions on the Identity and Number of Verifiers. Entropy. 2025; 27(11):1171. https://doi.org/10.3390/e27111171
Chicago/Turabian StyleXiong, Siyu. 2025. "A Quantum Proxy Signature Scheme Without Restrictions on the Identity and Number of Verifiers" Entropy 27, no. 11: 1171. https://doi.org/10.3390/e27111171
APA StyleXiong, S. (2025). A Quantum Proxy Signature Scheme Without Restrictions on the Identity and Number of Verifiers. Entropy, 27(11), 1171. https://doi.org/10.3390/e27111171





