Abstract
With the rapid advancement of hyperspectral remote sensing technology, the security of hyperspectral images (HSIs) has become a critical concern. However, traditional image encryption methods—designed primarily for grayscale or RGB images—fail to address the high dimensionality, large data volume, and spectral-domain characteristics inherent to HSIs. Existing chaotic encryption schemes often suffer from limited chaotic performance, narrow parameter ranges, and inadequate spectral protection, leaving HSIs vulnerable to spectral feature extraction and statistical attacks. To overcome these limitations, this paper proposes a novel hyperspectral image encryption algorithm based on a newly designed two-dimensional cross-coupled hyperchaotic map (2D-CSCM), which synergistically integrates Cubic, Sinusoidal, and Chebyshev maps. The 2D-CSCM exhibits superior hyperchaotic behavior, including a wider hyperchaotic parameter range, enhanced randomness, and higher complexity, as validated by Lyapunov exponents, sample entropy, and NIST tests. Building on this, a layered encryption framework is introduced: spectral-band scrambling to conceal spectral curves while preserving spatial structure, spatial pixel permutation to disrupt correlation, and a bit-level diffusion mechanism based on dynamic DNA encoding, specifically designed to secure high bit-depth digital number (DN) values (typically >8 bits). Experimental results on multiple HSI datasets demonstrate that the proposed algorithm achieves near-ideal information entropy (up to 15.8107 for 16-bit data), negligible adjacent-pixel correlation (below 0.01), and strong resistance to statistical, cropping, and differential attacks (NPCR ≈ 99.998%, UACI ≈ 33.30%). The algorithm not only ensures comprehensive encryption of both spectral and spatial information but also supports lossless decryption, offering a robust and practical solution for secure storage and transmission of hyperspectral remote sensing imagery.
1. Introduction
With the rapid advancement of remote sensing technology, hyperspectral images have found extensive applications in fields such as land mapping, disaster detection, environmental monitoring, agricultural monitoring, and military reconnaissance, owing to their unique advantages of high spatial resolution (sub-meter level), high spectral resolution (less than 10 nm), and high temporal resolution (hourly response) [1,2]. However, hyperspectral remote sensing images contain not only spatial texture features but also spectral information characterized by continuous bands [3]. This type of geospatial data faces significant security threats during storage, transmission, and sharing. If such data is intercepted, critical information could be extracted through spectral feature inversion, posing substantial risks to the security of hyperspectral remote sensing images. Therefore, establishing a robust security protection framework for hyperspectral remote sensing imagery is of great importance. To safeguard image information, researchers have developed various techniques, including image encryption [4,5,6,7] and watermarking [8,9,10,11]. Among these, image encryption stands out as one of the most direct and effective methods for ensuring image security [12]. It transforms a plain image into a highly secure, completely indiscernible cipher image. Only with the correct key can the original image be fully restored.
Chaos theory is one of the most widely applied and effective methods in the field of image cryptography [13,14,15,16]. Chaotic systems are characterized by sensitivity to initial conditions, ergodicity, pseudo-randomness, and unpredictability [17], features that share many common attributes with the principles of image encryption. Chaotic systems can be broadly categorized into continuous-time chaotic systems, typically described by differential equations, and discrete-time chaotic maps, which generate sequences through iterative computations. Discrete chaotic maps, such as Logistic, Tent, Cubic, Chebyshev, and their various coupled or transformed forms, are particularly favored in image encryption due to their computational efficiency and ease of implementation. Compared to one-dimensional (1D) chaotic maps, high-dimensional maps typically possess more complex structures and offer superior chaotic performance. Hyperchaotic systems, a subset of chaotic systems characterized by at least two positive Lyapunov exponents, exhibit more complex dynamical behaviors, higher randomness, and stronger unpredictability, making them highly suitable for high-security image encryption applications.
In recent years, researchers have proposed various novel 2D chaotic maps and applied them to image encryption algorithms. Hua et al. [18] introduced a new 2D Sine-Logistic modulation map (2D-SLMM), derived from the Logistic and Sine maps, and applied it in a chaotic magic transform (CMT) to efficiently alter image pixel positions. Zhu et al. [19] proposed a 2D Logistic-modulated-sine-coupling-logistic chaotic map (2D-LSMCL), which modulates the Sine map using a Logistic map and couples the modulated result with another Sine map. Teng et al. [20] proposed a 2D cross-coupled hyperchaotic map based on Logistic and Sine maps (2D-CLSS). Their results demonstrated that the system exhibits good ergodicity and a wide range of hyperchaotic phenomena, and it was applied to a new IES. Hu et al. [21] proposed a novel cross-coupled 2D chaotic map combining Sine and Logistic systems, which achieves a hyperchaotic state compared to traditional Sine and Logistic systems.
Concurrently, continuous-time chaotic systems, particularly those based on memristors, have also shown significant potential in image encryption. For instance, studies on bursting firings in memristive Hopfield neural networks, novel 4D discrete hyperchaotic maps based on parallel and cascade memristors, and 6D multistable memristive chaotic systems with a wide range of hyperchaotic states have demonstrated complex dynamics suitable for cryptographic applications [22,23,24]. While these continuous systems offer rich dynamical behaviors, their implementation often requires solving differential equations, leading to higher computational complexity compared to discrete maps. This computational overhead becomes a critical concern when encrypting large-volume hyperspectral remote sensing images, which often reach gigabyte (GB) levels. Therefore, this work focuses on designing a discrete hyperchaotic map that balances superior performance with computational efficiency.
The security of these chaos-based image encryption algorithms depends on both the structure of the encryption algorithm and the chaotic performance of the underlying chaotic map. On the one hand, if the encryption structure is inadequately designed, it may be successfully breached by various cryptanalytic attack methods [25]. Furthermore, statistical security evaluations are necessary but not sufficient conditions for proving cryptographic strength. A comprehensive security analysis must also consider resistance against known cryptanalytic techniques. Recent cryptanalysis works have revealed vulnerabilities in several chaos-based image encryption schemes, highlighting the importance of designing algorithms that can withstand chosen-plaintext and known-plaintext attacks [26,27,28]. On the other hand, with the rapid development of chaos analysis techniques, researchers have found that some existing chaotic maps possess security vulnerabilities due to weak chaotic performance [29,30,31], which consequently leads to security issues in the dependent encryption algorithms [32]. Therefore, designing encryption algorithms with higher security strength and developing chaotic systems with better performance are crucial for advancing chaos-based image encryption technology. Accordingly, this paper proposes a new 2D chaotic map named 2D-CSCM. Its chaotic performance will be rigorously tested and analyzed through various methods, including scatter plots, bifurcation diagrams, Lyapunov exponents, and sample entropy.
In 1998, Fridrich J. first proposed a digital image encryption algorithm based on a chaotic system, which divided the encryption process into two stages: scrambling and diffusion [33]. Subsequently, numerous researchers have continued to propose a multitude of image encryption schemes based on chaotic systems. Wang et al. [34] investigated an image encryption algorithm based on multi-objective particle swarm optimization (MOPSO), DNA encoding sequences, and a 1D Logistic map. Liu et al. [35] proposed a Sin-Arcsin-Arnold multi-dynamic random non-adjacent coupled map lattice (SAMCML) model and utilized it to design an encryption scheme for protecting medical multi-images. Through designed 3D-Fisher transformations and DNA operations, the scheme achieves random cross-plane scrambling and efficient diffusion. Wang et al. [36] proposed a color image encryption algorithm based on a two-dimensional (2D) hyperchaotic system, a three-dimensional (3D) L-shaped transformation, and DNA crossover and mutation. This method constructs an image cube and performs scrambling and diffusion operations on it using chaotic sequences. Sharma et al. [37] proposed an adaptive image encryption algorithm based on the Harris Hawk Optimization (HHO). The image is first decomposed into four sub-images of the same dimension via HVD decomposition for block-based pixel disruption. In the diffusion stage, bit-level XOR operations are performed with a random image generated by the Lorenz equations. Although mainstream research, including the aforementioned work, has achieved considerable results, its focus has predominantly been on the encryption of conventional digital images (e.g., RGB images, grayscale images).
Hyperspectral remote sensing images differ significantly from conventional digital images. The underlying data structure of conventional digital images (e.g., RGB or grayscale images) typically consists of a single-layer or three-layer pixel matrix. In contrast, hyperspectral remote sensing images are composed of dozens to hundreds of continuous spectral bands, each containing its corresponding Digital Number (DN) values. These DN values represent not only brightness but also physical properties such as reflectance and temperature of ground objects. Furthermore, the bit depth of DN values in hyperspectral images often exceeds 8 bits (0–255). More critically, hyperspectral images contain continuous spectral-dimensional information [38] absent in conventional images, forming unique spectral curve characteristics. Existing encryption algorithms designed for conventional digital images lack specialized mechanisms to address these hyperspectral data attributes. Consequently, to achieve effective chaotic encryption for hyperspectral remote sensing images, there is a pressing need for an encryption algorithm capable of handling their multi-dimensional data structure, high bit-depth DN values, and spectral domain features. Moreover, the single-scene data volume of hyperspectral imagery is enormous, often reaching gigabyte (GB) levels, which imposes higher demands on the security of the encryption algorithm, necessitating chaotic systems with superior performance. To address the challenges outlined above, this paper proposes a hyperspectral remote sensing image encryption algorithm based on the 2D-CSCM hyperchaotic map. Targeting the underlying data structure and spectral domain characteristics of hyperspectral data, the algorithm employs a layered processing strategy—comprising spectral dimension encryption, spatial pixel scrambling, and bit-level diffusion based on DNA encoding rules—to protect the spectral curve profiles and achieve comprehensive encryption of the entire image’s information.
In summary, the main contributions of this study are as follows:
- (1)
- A novel 2D hyperchaotic map (2D-CSCM) is proposed, integrating Cubic, Sinusoidal, and Chebyshev maps. It demonstrates superior hyperchaotic behavior, including a wider hyperchaotic parameter range and enhanced randomness, as validated by Lyapunov exponents, sample entropy, and NIST tests.
- (2)
- A dedicated spectral domain encryption method is designed, effectively concealing critical spectral curve features while preserving spatial readability—a crucial requirement for hyperspectral image processing.
- (3)
- A comprehensive encryption framework is developed, incorporating the proposed hyperchaotic map, spectral scrambling, spatial permutation, and a bit-level DNA diffusion mechanism tailored for high bit-depth DN values, ensuring robust security for hyperspectral imagery.
The remainder of this paper is organized as follows. Section 2 introduces the 2D-CSCM chaotic map and its chaotic performance. Section 3 describes the framework and details of the proposed hyperspectral remote sensing image encryption method based on 2D-CSCM. Section 4 provides a comprehensive security analysis of the proposed encryption algorithm. Finally, Section 5 and Section 6 present the discussion and conclusions.
2. 2D-CSCM Hyperchaotic Map
Chaotic maps are commonly employed in cryptography to generate pseudo-random sequences, forming the foundation of chaos-based image encryption methods. Therefore, this section will first introduce the proposed 2D-CSCM (2D Cubic–Sinusoidal–Chebyshev Map) hyperchaotic map. Its performance will then be evaluated through a series of metrics to demonstrate superior chaotic behavior, justifying its application in the encryption algorithm proposed in this paper.
2.1. Definition of the 2D-CSCM Hyperchaotic Map
This paper proposes a two-dimensional hyperchaotic map named 2D-CSCM, which integrates the cubic map, sinusoidal map, and Chebyshev map. The map accepts two input states, and , and produces two output states, and . The mathematical formulation of this cross-coupled map is given by Equation (1), where and are typically chaotic maps, and the output states are derived from computations using these functions applied to the input states:
In this work, we enhance the cross-coupled structure by incorporating the cubic map, sinusoidal map, and Chebyshev map, along with trigonometric sine and cosine functions, to propose the 2D-CSCM hyperchaotic map. The specific mathematical expression is provided in Equation (2):
where denotes the control parameter, and , represent the subsequent states of the current inputs and , respectively.
The rationale for selecting this specific combination of maps lies in their complementary chaotic properties. The cubic map serves as the core nonlinear component providing robust chaotic dynamics. The sinusoidal map introduces a periodic element that, when nonlinearly coupled, helps in disrupting periodic patterns and enhances sensitivity. The Chebyshev map contributes its distinct orthogonal and ergodic characteristics, which diversify the algebraic structure of the system and aid in achieving a more uniform distribution of output sequences. This synergistic design aims to create a hyperchaotic map with superior performance.
Furthermore, the constants 2.595 and 2.3 in Equation (2) were determined through a numerical optimization process. We performed a parameter sweep, evaluating the chaotic strength using the Lyapunov exponent as the key metric. These specific values were identified as optimal for maximizing the Lyapunov exponents and ensuring a wide hyperchaotic parameter range for , thereby guaranteeing the map operates at its peak chaotic performance for cryptographic applications.
The map exhibits chaotic behavior over a broad parameter range . The use of sine and cosine functions ensures that the map states remain bounded within .
2.2. Performance Evaluation of the 2D-CSCM Hyperchaotic Map
The comprehensive comparative analysis presented in this section aims to transcend mere performance benchmarking and delve into the mechanistic advantages of the proposed 2D-CSCM. While many recent 2D chaotic maps, such as 2D-SLMM [18] and 2D-CLSS [21], are constructed by coupling variants of the Logistic and Sine maps, our 2D-CSCM introduces a fundamental architectural innovation by cross-integrating three distinct families of maps: the Cubic, Sinusoidal, and Chebyshev. This synergistic design is hypothesized to be the root cause of its superior dynamics. The Cubic map provides a stronger nonlinear driving force compared to the Logistic map. The incorporation of the Chebyshev polynomial, with its inherent orthogonality and ergodicity, diversifies the algebraic structure and enhances output uniformity. Finally, the nested trigonometric coupling amplifies sensitivity and disrupts periodic patterns. The following quantitative comparisons serve to validate that this structural novelty directly translates into observable performance advantages.
To validate the chaotic effectiveness of the proposed 2D-CSCM, this section conducts a comprehensive evaluation using a series of standard chaotic metrics, including: attractor phase diagrams, bifurcation diagrams, Lyapunov exponents, value distribution histograms, sensitivity to initial conditions, sample entropy, 0–1 test, and the NIST SP 800-22 statistical test suite. For objective comparison, the performance of 2D-CSCM will be benchmarked against several classical and recently proposed chaotic maps, namely the Henon map, 2D-SLMM [18], 2D-LSMCL [19], and 2D-CLSS [21], in order to highlight its advantages in terms of chaotic complexity, randomness, and stability (reliability).
This section presents a comprehensive evaluation of the 2D-CSCM map’s chaotic performance through a series of standard metrics. A key distinction of a hyperchaotic map, as proposed, is the presence of at least two positive Lyapunov exponents. This property, coupled with complex dynamical behaviors like a wide chaotic parameter range and high entropy, makes hyperchaotic maps particularly suitable for high-security cryptography. The following analyses not only validate the hyperchaotic nature of 2D-CSCM but also benchmark its performance against several classical and recent 2D chaotic maps through direct, fair comparisons under identical conditions. The specific parameter settings used for the comparative maps in the following figures are provided in Appendix A for completeness.
2.2.1. Phase Diagram
The trajectory of a chaotic attractor directly reflects the nonlinearity and complexity of the system [39]. For periodic behavior, the trajectory typically appears as a fixed or repetitive curve. In contrast, a bounded chaotic system exhibits trajectories confined to a certain range, yet never repeating or converging. Ideally, a chaotic trajectory should show no fixed pattern and be uniformly distributed throughout the phase space, indicating high randomness in the generated sequences. A uniform phase space distribution suggests that the chaotic map can output well-randomized values.
Figure 1 illustrates the attractor phase diagrams of different chaotic maps. Figure 1a–d show the attractor distributions of the compared chaotic maps, while Figure 1e–h present the attractor distributions of the proposed 2D-CSCM with initial values under , , , and , respectively. The attractor phase diagrams of the comparison maps exhibit clearly fixed trajectories and uneven distributions. In contrast, the trajectory of the 2D-CSCM attractor shows no obvious pattern under chaotic states, with a more uniform distribution overall. Moreover, as the parameter μ increases, the distribution becomes even more homogeneous. These results demonstrate that the 2D-CSCM possesses more complex dynamic behavior and enhanced chaotic properties.
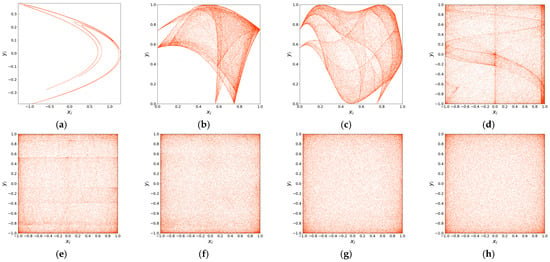
Figure 1.
Attractor Phase Diagram. (a) Attractor Phase Diagram of the Henon Chaotic Map; (b) Attractor Phase Diagram of the 2D-SLMM; (c) Attractor Phase Diagram of the 2D-LSMCL; (d) Attractor Phase Diagram of the 2D-CLSS; (e–h) Attractor phase diagrams of 2D-CSCM at μ = 0, μ = 0.1, μ = 2.5, and μ = 200, respectively.
2.2.2. Bifurcation Diagram
The bifurcation diagram reveals how the qualitative behavior of a chaotic map evolves with a control parameter. By discarding initial transients and plotting the long-term states, it provides a powerful and intuitive visualization of global dynamics, including period-doubling routes to chaos and the existence of periodic windows [40]. Figure 2 shows the bifurcation diagrams of the 2D-CSCM and several comparative chaotic maps. The diagrams reveal that the other maps exhibit chaotic behavior only within limited parameter intervals, and their state values do not fully cover the entire value range. In contrast, the 2D-CSCM maintains chaotic behavior throughout , with values entirely distributed within the interval [−1, 1]. The bifurcation diagram of 2D-CSCM demonstrates a more uniform and continuous distribution, indicating higher dynamic complexity and stronger chaotic characteristics. Moreover, 2D-CSCM remains chaotic over an even broader parameter range .
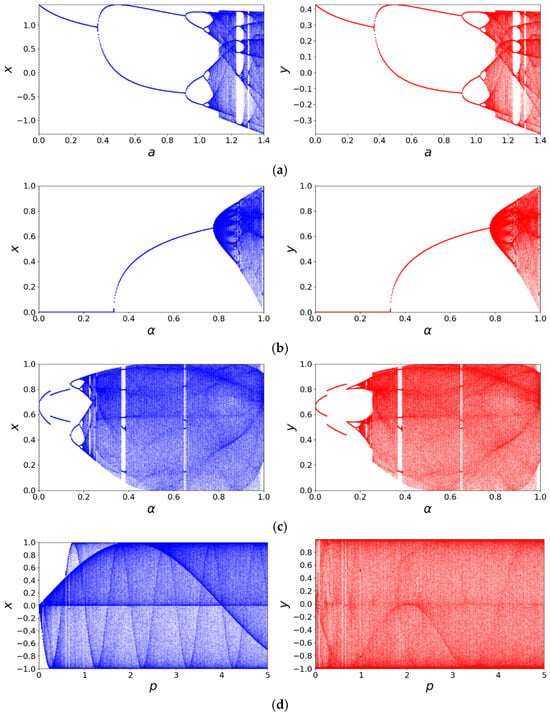
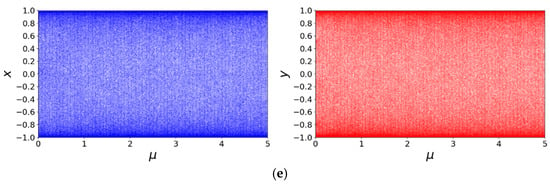
Figure 2.
Bifurcation diagram comparison. (a) Bifurcation diagram of the Henon Chaotic Map; (b) Bifurcation diagram of the 2D-SLMM; (c) Bifurcation diagram of the 2D-LSMCL; (d) Bifurcation diagram of the 2D-CLSS; (e) Bifurcation diagram of 2D-CSCM.
2.2.3. Lyapunov Exponent
The Lyapunov exponent is a powerful measure for quantifying the degree of chaos in a dynamical system, evaluating the unpredictability and complexity of chaotic sequences it generates [41]. It measures the rate of divergence of nearby trajectories, reflecting the system’s sensitivity to initial conditions. A positive Lyapunov exponent indicates chaotic behavior, high sensitivity to minute changes in initial conditions, and thus unpredictability. In contrast, a negative Lyapunov exponent suggests convergence toward a fixed point or limit cycle, implying stability and predictability. A system with multiple positive Lyapunov exponents is considered hyperchaotic. Hyperchaotic maps generally exhibit more complex and richer dynamic behavior than standard chaotic maps, making them highly suitable for image encryption, as they produce intensely scrambled outputs that are difficult to predict or decrypt without the correct key and algorithm.
The presence of multiple positive Lyapunov exponents is a definitive marker of hyperchaos. From a cryptographic standpoint, such systems offer superior properties. First, multiple positive LEs indicate exponential divergence in more than one direction within the phase space [42], leading to more rapid and complex mixing of state variables. This directly translates to enhanced sensitivity and higher unpredictability in the generated sequences—a crucial property for confounding statistical analysis. Furthermore, the magnitude of the Lyapunov exponents is of critical importance. A larger positive LE signifies a faster average rate of divergence [43], meaning the system loses correlation with its initial state more rapidly, thereby increasing its short-term unpredictability and resistance to prediction attacks. As evidenced by our results (Figure 3 and Figure 4), the 2D-CSCM not only possesses two positive LEs across a wide parameter range but also maintains large values for these exponents, confirming its superior hyperchaotic strength for cryptographic applications.
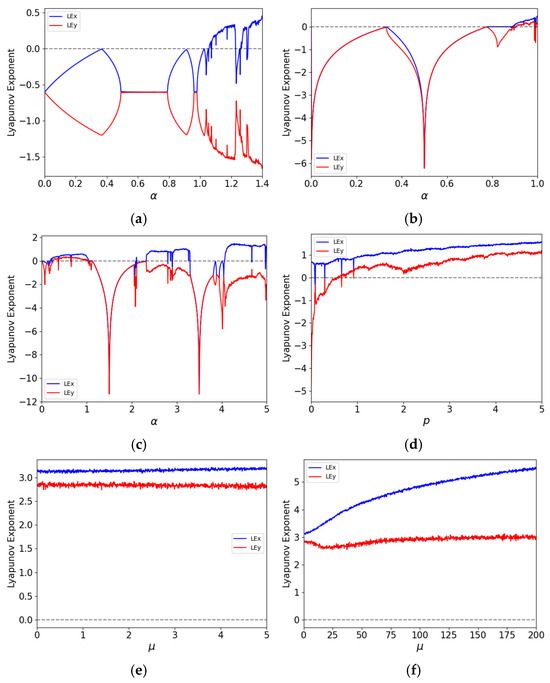
Figure 3.
Distribution of Lyapunov exponents. (a) Distribution of Lyapunov exponents of the Henon Chaotic Map; (b) Distribution of Lyapunov exponents of the 2D-SLMM; (c) Distribution of Lyapunov exponents of the 2D-LSMCL; (d) Distribution of Lyapunov exponents of the 2D-CLSS; (e,f) Distributions of Lyapunov exponents of 2D-CSCM under and , respectively.
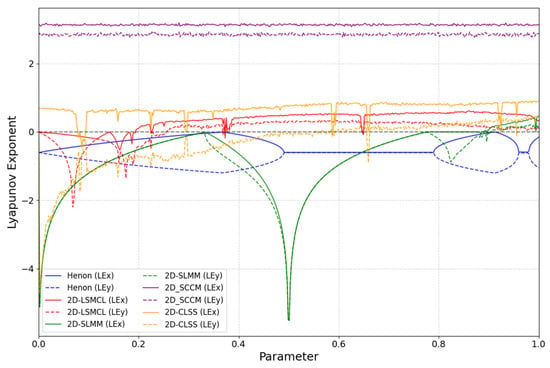
Figure 4.
Comparison of Lyapunov exponent curves (Parameter ranging from 0 to 1).
In this study, the Lyapunov exponents are computed using the QR decomposition method [44]. The distributions of Lyapunov exponents for 2D-CSCM and other comparative chaotic maps are shown in Figure 3, where Figure 3e,f represent the performance of 2D-CSCM over and , respectively. The results demonstrate that 2D-CSCM has two positive Lyapunov exponents across both intervals, proving that it exhibits not only chaotic but also hyperchaotic behavior. In contrast, the other chaotic maps show chaotic characteristics only within limited portions of their parameter intervals. Compared to these maps, 2D-CSCM exhibits larger Lyapunov exponents that remain positive throughout the parameter range, attesting to its stronger chaotic nature. Figure 4 provides a detailed comparison of Lyapunov exponent curves over the interval . Moreover, 2D-CSCM maintains its hyperchaotic behavior over the entire range .
2.2.4. Sensitivity to Initial Conditions
This section focuses on evaluating the sensitivity of the 2D-CSCM to initial conditions. By introducing a minute perturbation to the initial values and comparing the chaotic trajectories of the original and perturbed systems over the same time range, the dependence of the system on initial conditions can be visually assessed [45]. The initial state of the system is set as , and a perturbation of magnitude is applied to and , respectively. Figure 5a shows a comparison between the original trajectory (, ) and the trajectory after perturbing (, ); Figure 5b displays the original trajectory and the trajectory after perturbing (, ). It is clearly observed that even under extremely small initial disturbances, the system trajectories diverge significantly, demonstrating the high sensitivity of 2D-CSCM to initial conditions.
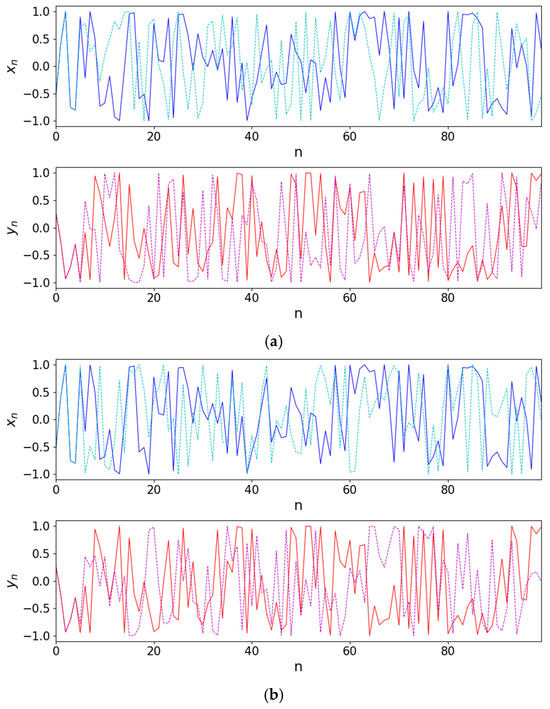
Figure 5.
Sensitive dependence on initial conditions is illustrated in the control and parallel runs with initial conditions (a) , (solid line) and , (dashed line); (b) , (solid line) and , (dashed line).
2.2.5. Sample Entropy
Sample entropy [46] is used to quantify the oscillation patterns in a time series and is proportional to the complexity of the sequence. It can be calculated using Equation (3):
where is the embedding dimension, is the tolerance value, and is the length of the time series. and denote the number of template vector matches using the Chebyshev distance between and . For two-dimensional chaotic sequences, the sample entropy typically falls between 0 and 2. A higher sample entropy value generally indicates stronger nonlinearity and complexity in the sequence.
Figure 6 shows the sample entropy performance of the 2D-CSCM and other comparative chaotic maps. The other maps struggle to achieve the ideal value of 2 within their chaotic parameter ranges. In contrast, the sample entropy of 2D-CSCM remains close to 2 across different values of the control parameter . Compared to the other maps, 2D-CSCM exhibits sample entropy values much closer to the ideal value throughout the parameter range, indicating superior sequence complexity.
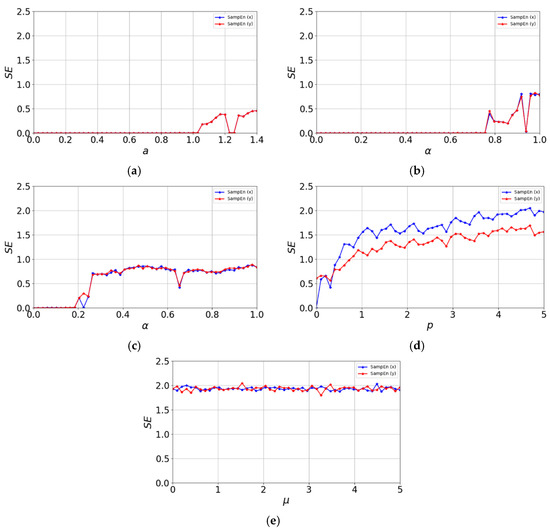
Figure 6.
Sample entropy distribution. (a) Sample entropy distribution of the Henon Chaotic Map; (b) Sample entropy distribution of the 2D-SLMM; (c) Sample entropy distribution of the 2D-LSMCL; (d) Sample entropy distribution of the 2D-CLSS; (e) Sample entropy distribution of 2D-CSCM.
2.2.6. 0–1 Test
The 0–1 test is an important method for evaluating the expansion behavior of chaotic map trajectories, used to identify chaotic dynamics in a time series [47]. For a given time series , , the test is conducted as follows:
where is a random constant, and , . The mean square displacement is computed as:
If and exhibit Brownian motion, grows linearly with time; if the trajectory is bounded, so is . The asymptotic growth rate is defined as:
A value of close to 1 indicates chaotic behavior in the time series.
We performed the 0–1 test for the control parameter ranging from 0 to 5, uniformly sampled at 100 points. As shown in Figure 7, the values of the sequences generated by the 2D-CSCM in both the and directions are all close to 1. Specifically, the mean values for the and sequences reach 0.9987 and 0.9991, with variances of 0.0021 and 0.0015, respectively. Since displaying all 100 data points is impractical, we provide these statistical measures which robustly confirm the chaotic nature of the map’s output.
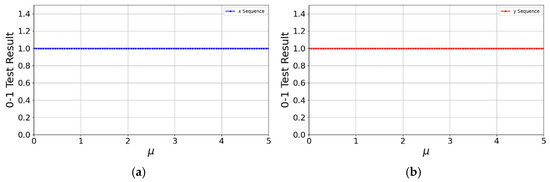
Figure 7.
0–1 Test. (a) Performance of x sequence in 0–1 test; (b) Performance of y sequence in 0–1 test.
2.2.7. NIST SP 800-22 Test
The NIST SP 800-22 test is a comprehensive statistical suite provided by the National Institute of Standards and Technology (NIST) for evaluating the randomness and statistical properties of binary sequences [48]. It consists of 15 distinct tests. The p-value is a statistical measure indicating the probability of observing the data under the null hypothesis. A sequence is considered random for a given test if the p-value exceeds the threshold α = 0.01. Table 1 presents the NIST test results for the output sequences of the 2D-CSCM. As shown, the binary streams generated by 2D-CSCM passed all subtests. These results demonstrate that 2D-CSCM can produce long, aperiodic chaotic sequences suitable for image encryption.

Table 1.
NIST SP 800-22 Test Results.
3. Hyperspectral Remote Sensing Image Encryption Algorithm Based on the 2D-CSCM Hyperchaotic Map
This section introduces a novel encryption algorithm for hyperspectral remote sensing images, founded on the 2D-CSCM hyperchaotic map. The algorithm enables spectral-domain encryption, full-image spatial encryption, and lossless decryption. The process consists of four key stages: key generation, spectral dimension encryption, pixel scrambling, and DN value diffusion. The flowchart of the proposed encryption algorithm is shown in Figure 8.
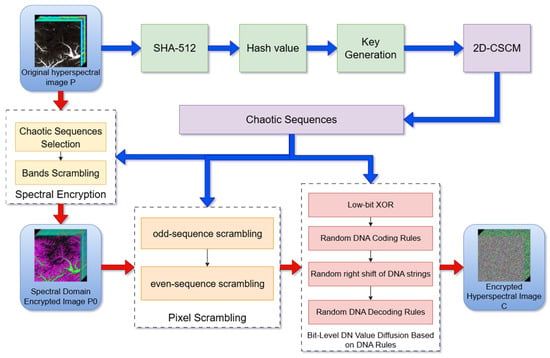
Figure 8.
Encryption Algorithm Process.
The proposed algorithm is a symmetric encryption scheme. For each hyperspectral image to be encrypted, the entire process, including the key generation and the iteration of the 2D-CSCM, is executed once. The initial conditions and parameters (, , ) for the 2D-CSCM are derived from the plaintext image via the SHA-512 hash function as described in Section 3.1. These values (, , ) constitute the secret key.
This secret key must be securely transmitted to the authorized receiver through a separate channel (e.g., encrypted using the receiver’s public key via an algorithm like RSA). Upon receiving the key, the decryption process is initiated.
The 2D-CSCM is a deterministic mathematical function. Given the same initial key , it will generate an identical sequence of chaotic values regardless of the hardware or software platform (e.g., Intel x86-64, ARM-based systems, Windows, and Linux), provided that the floating-point arithmetic conforms to the IEEE 754 standard. This determinism is a fundamental property of chaotic maps and ensures lossless decryption. Our experiments conducted on different computing environments have confirmed this reproducibility.
3.1. Key Generation
As a symmetric image encryption algorithm, the same key must be used for both encryption and decryption. This key is transmitted to the receiver via a network or other communication method. In this algorithm, the encryption key is generated using the SHA-512 hash function. The specific steps are as follows:
Step 1: Input the original image into the SHA-512 hash function to obtain a 512-bit hash value . This hash value is inherently a binary sequence but is typically represented as a 128-character hexadecimal string for readability. For subsequent computations, we treat directly as a binary sequence of length 512.
Step 2: Divide sequence into 8 subsequences denoted as to , each 64 bits long.
Step 3: Convert into 64-bit floating-point numbers, and into 64-bit integers.
Step 4: Extract the fractional parts of to obtain . Then, compute the initial state parameters and using Equations (11) and (12):
Step 5: Calculate the intermediate value using Equation (13), convert it into a 64-bit floating-point number, and take its absolute value to obtain the final parameter :
As a result, is a positive number, while and fall within the range . The values , , and are used as the control parameter and initial states of the 2D-CSCM, respectively, to generate the chaotic sequences required in the subsequent encryption process.
The key generation mechanism is plaintext-dependent, as the hash is derived from the original image. This design provides a desirable property of being resistant to known-plaintext attacks for a single image, as each image has a unique key. However, we acknowledge that under a chosen-plaintext attack (CPA) model, where an adversary can obtain the ciphertext for a chosen plaintext, this dependency could be exploited to analyze the relationship between the plaintext and the key. Nevertheless, for the specific application scenario of securing hyperspectral remote sensing images—which are typically large, unique datasets not subject to arbitrary manipulation by an adversary—the practical risk of a successful CPA is considered low. The primary security guarantees rely on the robustness of the SHA-512 hash function and the hyperchaotic map.
The SHA-512 hash function was selected over SHA-256 for two primary reasons: (1) It produces a longer 512-bit digest, which facilitates the derivation of a more complex and higher-entropy set of initial conditions and parameters (, , ) for the 2D-CSCM map, thereby strengthening the key space. (2) SHA-512 is optimized for 64-bit processors, and given the large data volume of hyperspectral images, its computational efficiency on modern computing platforms is comparable to, if not better than, SHA-256 for such sizable inputs.
3.2. Spectral Encryption Process
Hyperspectral remote sensing images cover a broad spectral range with high resolution, and their spectral domain often contains crucial information, particularly the spectral curve shapes that reflect material properties. Therefore, encrypting the spectral domain is essential for protecting hyperspectral image data. This subsection describes the spectral encryption process based on the 2D-CSCM. The specific steps are as follows:
Step 1: For a hyperspectral image of size , generate two chaotic sequences and of length using the 2D-CSCM, where is the number of rows, N the number of columns, and the number of spectral bands.
Step 2: Determine whether is even or odd. If is even, select sequence as the encryption sequence; otherwise, select sequence .
Step 3: Sort the values of the selected encryption sequence in ascending order and generate the corresponding index sequence.
Step 4: Use this index sequence to permute all bands of the image, resulting in the spectrally encrypted image .
At this stage, the spectral encryption of the hyperspectral image is complete. This process operates solely on the spectral dimension without altering spatial information, thereby encrypting spectral features while fully preserving the spatial texture and structural content of the image.
3.3. Pixel Scrambling Process
The spatial information of a hyperspectral remote sensing image is represented by a pixel matrix. To enhance security in the spatial domain, pixel positions are scrambled. This section describes the pixel scrambling process based on the 2D-CSCM. The specific steps are as follows:
Step 1: For the spectrally encrypted hyperspectral image of size , generate two chaotic sequences and of length using the 2D-CSCM for subsequent scrambling;
Step 2: Read all pixels of in a snake-like pattern and flatten them into a one-dimensional pixel sequence ;
Step 3: Sort the sequences and in ascending order to generate index sequences and , where will be used to scramble the odd-indexed group, and the even-indexed group;
Step 4: Divide the one-dimensional sequence into an odd group and an even group based on pixel order;
Step 5: Use X1 to reorder the odd group, obtaining the scrambled odd group ; similarly, use to scramble the even group, yielding ;
Step 6: Concatenate after to form a fully scrambled pixel sequence ;
Step 7: Repeat Steps 5–6 for all spectral bands to accomplish pixel scrambling across the entire dataset;
Step 8: Reshape back into an three-dimensional matrix, resulting in the pixel-scrambled image .
3.4. Bit-Level DN Value Diffusion Process Based on DNA Rules
Unlike conventional grayscale images, the pixel values in hyperspectral remote sensing images are represented as Digital Numbers (DNs), which may indicate brightness, reflectance, radiance, or other physical quantities, with possible bit depths of 8, 16, or 32 bits. To accommodate the encryption of high bit-depth DN values, this paper proposes a bit-level diffusion method based on DNA encoding rules. The specific steps are as follows:
Step 1: For the pixel-scrambled image of size , generate two chaotic sequences and of length using the 2D-CSCM for subsequent diffusion;
Step 2: Read the DN values of and convert them into an unsigned integer sequence with the original bit depth;
Step 3: Convert the floating-point values of chaotic sequence into binary form, truncate the lower bits corresponding to the DN bit-length, and perform a bitwise XOR operation with to obtain the binary sequence ;
Step 4: Compute the DNA encoding rule sequence from chaotic sequence using Equation (14), which determines the DNA encoding mode for each value in , yielding the DNA-encoded string sequence :
The result of (an integer between 0 and 7) dynamically selects one of the 8 possible DNA encoding rules for each pixel or data block. The standard set of DNA coding rules employed in this study is defined in Table A1 in Appendix A. For example, if , rule ‘A’ might be used where 00 encodes to A, 11 to T, 10 to C, and 01 to G. Our algorithm does not rely on a single fixed rule but pseudo-randomly selects from all 8 rules based on the chaotic sequence, significantly enhancing the diffusion effect and resistance to analysis.
Step 5: Reverse each DNA string in to obtain the reversed sequence ;
Step 6: Perform a right circular shift on each string in . The shift amount is calculated using Equation (15):
where denotes the current index;
Step 7: Compute the DNA decoding rule sequence from chaotic sequence using Equation (16), and decode the shifted DNA strings to obtain the diffused binary sequence :
Step 8: Convert the binary values in back into unsigned integers with the original DN bit depth, resulting in the final encrypted image .
While DNA-based operations provide a novel and complex layer for diffusion, it is recognized that certain implementations can be vulnerable to specific attacks if the encoding/decoding rules are static or poorly chosen. The primary vulnerabilities often lie in the predictability of the rules. Our scheme mitigates this by (1) dynamically selecting the encoding and decoding rules using the hyperchaotic sequences and , making them plaintext- and key-dependent, and (2) incorporating non-linear operations like bit reversal and circular shifting within the DNA domain. This dynamic and integrated approach strengthens the algorithm against cryptanalysis that targets static DNA coding rules.
This completes the overall encryption of the hyperspectral remote sensing image.
3.5. Decryption Process
As a symmetric encryption scheme, the decryption process is the inverse of the encryption procedure. The deterministic nature of the 2D-CSCM ensures that, given the same secret key (, , ), identical chaotic sequences are generated for decryption, regardless of computing platform, provided IEEE 754 floating-point standard is followed. This determinism guarantees lossless decryption, as experimentally validated in subsequent sections.
In the proposed method, both the spectral encryption and pixel scrambling stages alter only the positional arrangement of the data without modifying the original pixel values. Meanwhile, the DN value diffusion process based on DNA rules is a reversible bit-level operation that incurs no loss of information. Therefore, the proposed hyperspectral image encryption algorithm supports lossless decryption.
The 2D-CSCM is a deterministic function, yet its hyperchaotic sensitivity means that even minor floating-point discrepancies across different IEEE 754-compliant systems could, in theory, cause trajectory divergence after many iterations. A pivotal design choice in our algorithm inherently mitigates this risk: the entire process—from key generation through all chaotic sequence iterations required for encryption—is executed as a single, continuous computational workflow on the encryption machine. Consequently, only the final ciphertext and the initial key (kx, ky, ku) are shared. The decryption process does not resume from an intermediate state; it independently regenerates the entire chaotic sequence from the shared initial key. This approach ensures that any platform-specific numerical behavior originates from the same starting point, preventing the accumulation of divergent errors that could occur if intermediate states were transferred.
To empirically validate this design, we conducted a cross-platform test. A ZY1E hyperspectral image was encrypted on a local workstation (Intel i9, Windows 11). The ciphertext and key were then decrypted on Google Colab (cloud environment) and a Linux server (Ubuntu 22.04). The decrypted images on both platforms were bit-for-bit identical to the original (MSE = 0, SSIM = 1.0), confirming the practical robustness of our design for lossless decryption across heterogeneous environments.
4. Experimental Results and Performance Evaluation
This section presents the experimental results and performance evaluations of the proposed hyperspectral remote sensing image encryption algorithm. The first subsection demonstrates the effect and quantitative metrics of spectral-domain encryption, evaluating the encryption performance of the spectrally encrypted image . Subsections 2 to 9 present the overall encryption effect of the complete algorithm and report various performance metrics commonly used in chaotic image encryption.
Experiments were conducted on four hyperspectral remote sensing images:
ZY1E ASHI Subset: A subset of images acquired by the ASHI sensor onboard the ZY-1-02D satellite. Size: [, , ] = [512, 512, 76]. Data Type: 16-bit unsigned integer (DN values).
Botswana: Captured by NASA’s EO-1 satellite. Size: [200, 200, 145]. Data Type: 16-bit unsigned integer. (Source: GIC Website).
PaviaU: Collected by the ROSIS sensor. Size: [610, 340, 103]. Data Type: 16-bit unsigned integer. (Source: GIC Website).
Indian Pines: Acquired by the AVIRIS sensor. Size: [145, 145, 200]. Data Type: 16-bit unsigned integer. (Source: GIC Website).
(Hyperspectral Remote Sensing Scenes—Grupo de Inteligencia Computacional (GIC)).
All experiments were conducted on a computer with the following configuration: Intel Core i9-13900H CPU @ 2.20 GHz, 16 GB RAM, and the Windows 11 operating system. The algorithm was implemented in Python 3.7.
4.1. Spectral Domain Information Encryption Capability
4.1.1. Encrypted Spectral Profile Comparison
Hyperspectral remote sensing images possess high spectral resolution, enabling the extraction of intensity values across all bands at any pixel to form an approximately continuous spectral curve. To evaluate the effectiveness of spectral encryption, a specific pixel at location (100, 100) was selected, and its spectral profiles were extracted from the original, encrypted, and decrypted image data blocks. Figure 9 displays the spectral curves from the original, encrypted, and decrypted images for four hyperspectral datasets. The encrypted spectral profiles differ significantly from the original ones, effectively concealing the initial spectral characteristics, while the decrypted spectra are fully restored to their original forms, demonstrating that the proposed algorithm achieves efficient encryption and lossless decryption in the spectral domain.
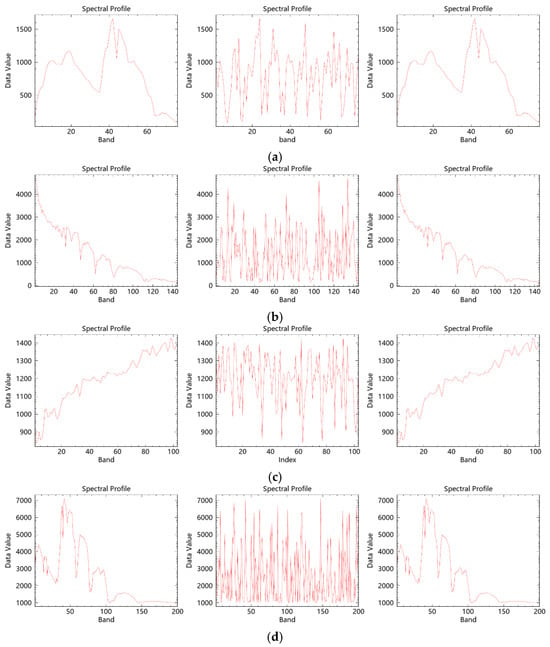
Figure 9.
Comparison of original, encrypted, and decrypted spectral profiles of hyperspectral remote sensing images. (a) Performance of ZY1E Satellite Hyperspectral Images at (100, 100); (b) Performance of Botswana at (100, 100); (c) Performance of PaviaU at (100, 100); (d) Performance of Indian Pines at (100, 100).
Furthermore, the encryption algorithm independently encrypts spectral profiles without altering spatial information. Figure 10 shows the image cubes of the original, spectrally encrypted, and decrypted images. The spectral cross-sections of the encrypted image cubes are substantially altered, whereas the spatial information remains unchanged. The decrypted image cubes revert entirely to their original state. These results confirm that the proposed algorithm securely encrypts spectral information while fully preserving spatial content.
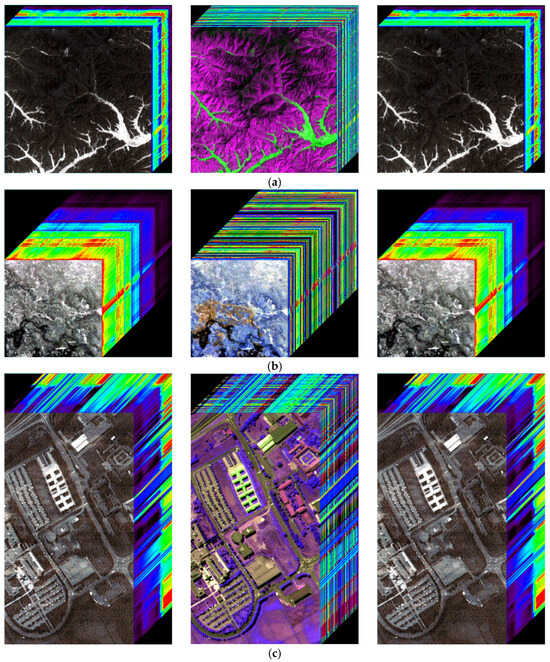
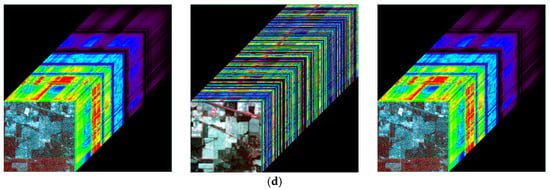
Figure 10.
Image cubes before encryption, after spectral encryption, and after decryption. (a) Performance of ZY1E Satellite Hyperspectral Images; (b) Performance of Botswana; (c) Performance of PaviaU; (d) Performance of Indian Pines.
4.1.2. Quantitative Evaluation
To quantitatively evaluate the similarity between the original spectral curves and the encrypted/decrypted ones, this study employs two metrics: the Spectral Angle Mapper (SAM) and the Spectral Information Divergence (SID) [49].
SAM measures the similarity between two spectral vectors by calculating the angle between them. For two spectral curves and of length L, the SAM value is computed as:
where , and .
SID treats spectral curves as random variables and measures their similarity through the divergence of their probability distributions. Let and be two spectral pixel vectors. Their probability distributions are obtained by normalization: , .Then the SID is defined as:
where:
Smaller SAM and SID values indicate higher similarity. As shown in Table 2, the SAM and SID values increase significantly after encryption, but both drop to zero after decryption, demonstrating that the encryption effectively disrupts the original spectral features while allowing perfect recovery, thus confirming the algorithm’s effectiveness and reversibility in spectral encryption.

Table 2.
SAM and SID Quantitative Results.
4.2. Visual Effects
The visual effects of the proposed encryption algorithm are illustrated in Figure 11 and Figure 12. Figure 11 compares the original, encrypted, and decrypted images in three selected spectral bands, while Figure 12 shows the corresponding image cubes before encryption, after encryption, and after decryption. It can be observed that the encrypted images and image cubes completely conceal the visual information of the originals, exhibiting a noise-like random distribution. Meanwhile, the decrypted images are visually identical to the original ones without any distortion or loss of information. These results demonstrate that the proposed encryption algorithm effectively protects the visual content of hyperspectral remote sensing images while achieving lossless decryption.
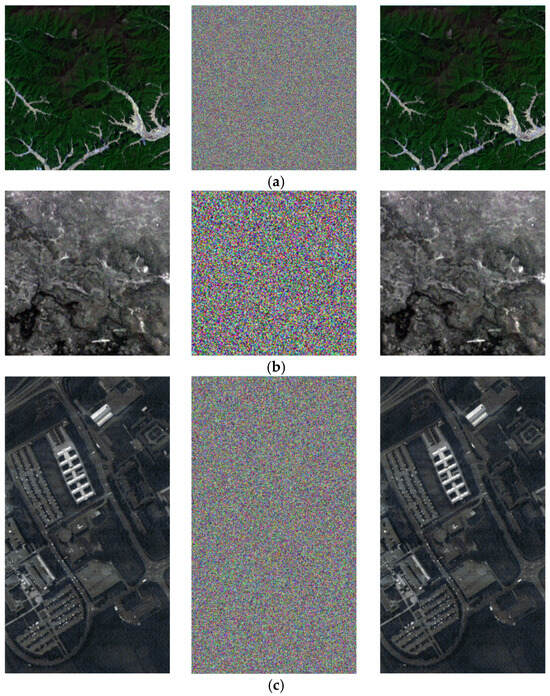
Figure 11.
Visual comparison of hyperspectral remote sensing images before encryption, after encryption, and after decryption. (a) Performance of ZY1E Satellite Hyperspectral Images (Band selection: R = 32, G = 21, B = 11); (b) Performance of Botswana (Band selection: R = 3, G = 2, B = 1); (c) Performance of PaviaU (Band selection: R = 3, G = 2, B = 1); (d) Performance of Indian Pines (Band selection: R = 3, G = 2, B = 1).
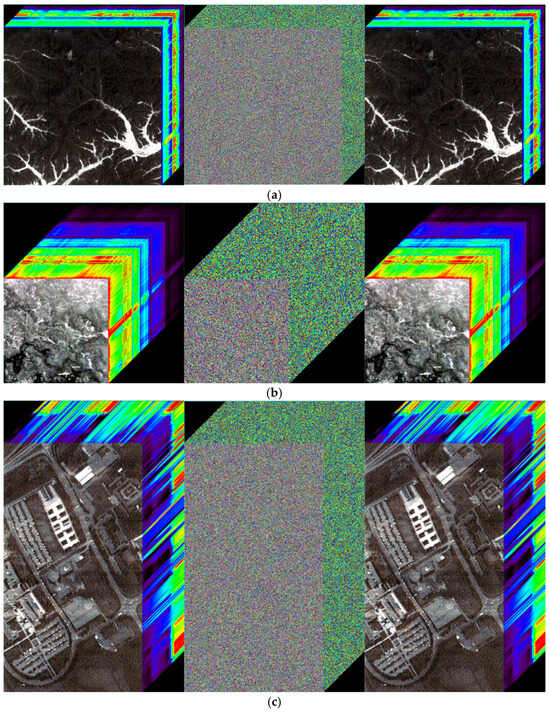
Figure 12.
Image cubes before encryption, after encryption, and after decryption. (a) Performance of ZY1E Satellite Hyperspectral Images; (b) Performance of Botswana; (c) Performance of PaviaU; (d) Performance of Indian Pines.
4.3. Key Space Analysis
In encryption systems, a key space larger than 2100 is generally considered sufficient to resist brute-force attacks, meeting common security standards [50]. In the proposed algorithm, the effective secret key comprises the three floating-point numbers , and . In digital computers, the precision of these floating-point numbers is finite. According to the IEEE 754 double-precision standard, each double-precision floating-point number has a precision of about , effectively providing approximately distinct representable values within a given range.
Therefore, the conservative lower bound for the key space can be calculated as: () × () × () = . This key space of not only far exceeds the common security threshold of but is also fully compliant with the key space sizes achieved in state-of-the-art chaotic image encryption schemes. This demonstrates that the proposed algorithm possesses a sufficiently large key space to effectively resist brute-force attacks.
4.4. Key Sensitivity Analysis
Key sensitivity refers to the property that even a minor modification to the key should make it impossible to decrypt the ciphertext correctly. A secure image encryption algorithm must exhibit high key sensitivity [51]. This section evaluates the key sensitivity of the proposed algorithm. A slight perturbation Δ = 10−15 was introduced to the original key components , , and individually to generate incorrect keys. Figure 13a shows the original Band 7 image of the ZY1E satellite hyperspectral dataset, and Figure 13b displays the image decrypted with the correct key. Figure 14 presents the decryption results using , , and , respectively. It is evident that decryption with slightly altered keys fails to recover any recognizable information. Figure 15 illustrates the DN value differences between the incorrectly decrypted images and the original image, while Figure 16 provides heatmaps of these differences. The differences are significant and irregular, confirming the complete decryption failure. These results demonstrate the high key sensitivity of the proposed encryption algorithm, highlighting its security against key-based attacks.
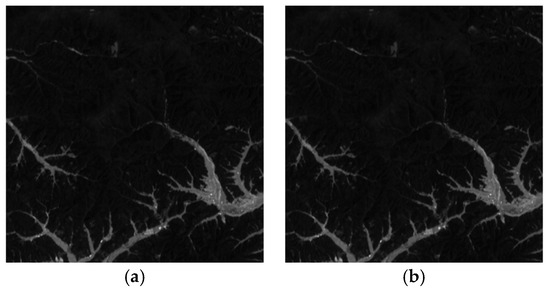
Figure 13.
Original Band 7 image of ZY1E dataset and decryption result with correct key. (a) Original image; (b) Image decrypted with the correct key.
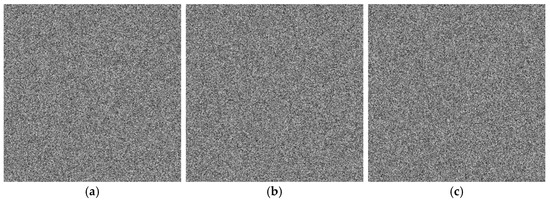
Figure 14.
Decrypted images with perturbed keys: , , and . (a) Image decrypted using ; (b) Image decrypted using ; (c) Image decrypted using .
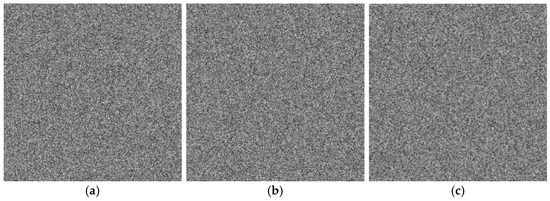
Figure 15.
DN value differences between original and decrypted images using perturbed keys. (a) ; (b) ; (c) .
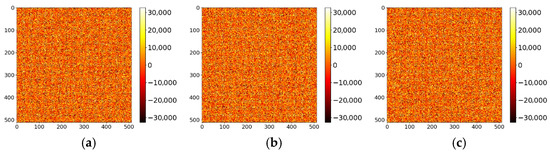
Figure 16.
Heatmaps of DN value differences for decryptions with perturbed keys. (a) ; (b) ; (c) .
4.5. Statistical Analysis
In cryptanalysis of image encryption algorithms, a common approach is to exploit statistical features of the ciphertext image. These characteristics can also be analyzed through their histograms, which reflect the distribution patterns of pixel values. A flatter histogram indicates weaker correlation between pixel values and their frequencies, making it more difficult to decode the original image information [52]. As the encryption target in this paper is hyperspectral remote sensing images whose pixel values are Digital Number (DN) values, histogram tests are performed on the DN values.
The histogram test results of the proposed encryption algorithm are shown in Figure 17. Figure 17a,b show the DN value histograms of the ZY1E satellite hyperspectral image before and after encryption, respectively; Figure 17c,d show those of the PaviaU image before and after encryption. The original images exhibit distinct statistical characteristics in their DN value distributions. After encryption, the histograms of the encrypted images become uniform across the entire DN value range. This indicates that the proposed encryption algorithm successfully conceals the statistical features of the images, making the encrypted images resistant to statistical analysis and histogram-based attacks.
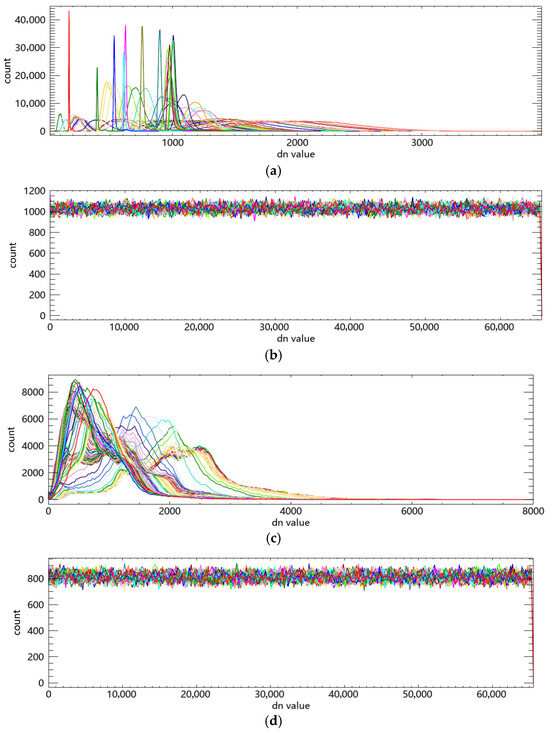
Figure 17.
Comparison of DN value histograms before and after encryption. (a) DN value histogram of ZY1E hyperspectral image before encryption; (b) DN value histogram of ZY1E hyperspectral image after encryption; (c) DN value histogram of PaviaU image before encryption; (d) DN value histogram of PaviaU image after encryption.
4.6. Correlation Analysis
Correlation analysis is another statistical method used to examine the relationships between adjacent pixels in an image, which could be exploited by attackers [53]. Therefore, an image encryption algorithm should enhance data security by disrupting the correlation between neighboring pixels. To evaluate the security of the proposed algorithm, we randomly selected 10,000 pixels from the image and calculated the correlation coefficients between adjacent pixels in the horizontal (H), vertical (V), and diagonal (D) directions. The correlation coefficient is computed using the following formula:
where and represent the values of two adjacent pixels, is the number of selected pixels, denotes the covariance, is the variance, and is the mean value. A value of close to 1 indicates high correlation, while a value near 0 suggests low correlation.
Figure 18 illustrates the correlation distributions of the original and encrypted images in three directions. The pixel points of the original image are clustered near the diagonal, indicating high correlation, whereas those of the encrypted image are uniformly scattered across the plane, showing significantly reduced correlation. Table 3 provides the specific correlation coefficients: before encryption, the coefficients in all directions are close to 1; after encryption, they are all near 0. These results demonstrate that the proposed encryption algorithm effectively disrupts the correlation between adjacent DN values, thereby resisting statistical attacks based on pixel relationships and enhancing overall security.
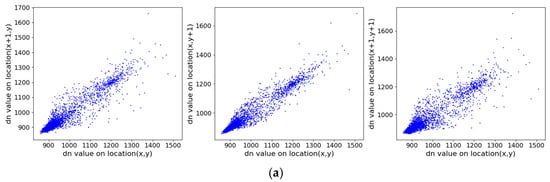
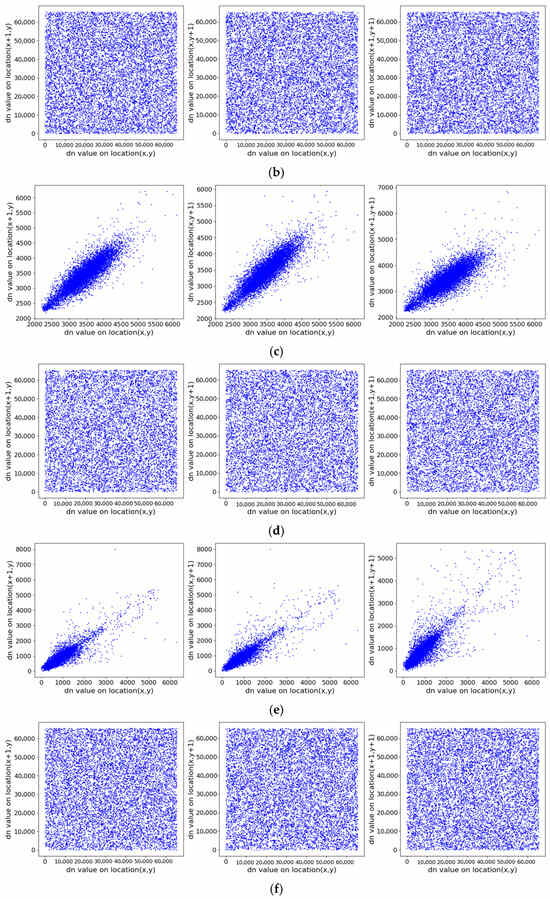
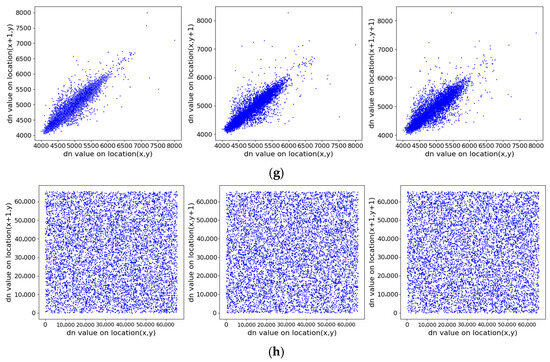
Figure 18.
Correlation distributions of adjacent pixels in original and encrypted images on three directions (horizontal, vertical, diagonal). (a) ZY1E before encryption; (b) ZY1E after encryption; (c) Botswana before encryption; (d) Botswana after encryption; (e) PaviaU before encryption; (f) PaviaU after encryption; (g) Indian Pines before encryption; (h) Indian Pines after encryption.

Table 3.
Correlation coefficients of image adjacent pixels.
4.7. Information Entropy
The degree of randomness of an information source can be measured and quantified using information entropy [54]. According to Shannon’s principle, the entropy of a source mm is calculated as:
where is the number of possible intensity levels, and is the probability of a particular intensity value appearing in the image. For a grayscale image with , the ideal entropy is 8. Since the encrypted objects in this paper are hyperspectral remote sensing images with a bit depth of 16 bits, , and the ideal entropy value is 16. A ciphertext entropy close to the ideal value indicates higher randomness and better encryption performance.
Table 4 lists the information entropy values of the original and encrypted images, alongside the ideal value for 16-bit data. The entropy of the original images is considerably lower than 16, confirming that their DN value distributions are far from random, a common characteristic of real-world hyperspectral scenes. After encryption, the entropy increases significantly and approaches the ideal value, demonstrating that the encrypted images exhibit high randomness. It is noted that the encrypted entropy for the ‘Botswana’ and ‘Indian Pines’ datasets is slightly lower than the ideal maximum. This is not a limitation of the encryption algorithm but stems from the inherent data characteristics of the original images, which contain large homogeneous areas (e.g., shadows, uniform vegetation) that do not utilize the full 16-bit dynamic range. The algorithm successfully maximizes the randomness to a level very close to the theoretical ceiling permitted by the source data. These results confirm the effectiveness of the proposed algorithm in enhancing randomness and resisting entropy-based attacks.

Table 4.
Information Entropy Comparison.
4.8. Resistance to Cropping Attacks
Robustness is a crucial metric for evaluating the ability of an image encryption algorithm to withstand disturbances or attacks, with resistance to cropping attacks being particularly important. During data transmission, images may suffer from partial information loss due to channel noise or malicious interventions [55]. To assess the algorithm’s resilience against such disturbances, this experiment simulates cropping attacks by intentionally removing portions of the encrypted image and examining whether the original image can still be recovered recognizably.
Figure 19a shows the original ZY1E satellite hyperspectral image in a band combination (R:32, G:21, B:11); Figure 19b–d present the decryption results after cropping 1/64, 1/16, and 1/4 of the encrypted image, respectively. The results demonstrate that despite varying degrees of data loss, the algorithm successfully decrypts the images, with primary geographic information preserved in the reconstructed images. These findings indicate that the proposed encryption algorithm exhibits strong robustness against cropping attacks, making it suitable for practical scenarios where partial data corruption may occur during transmission.
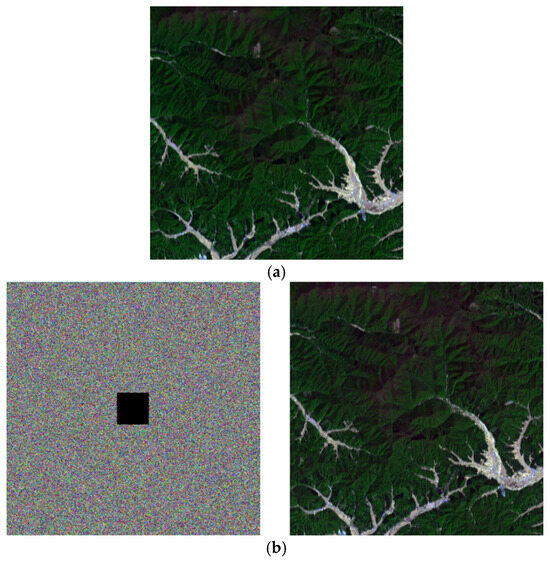
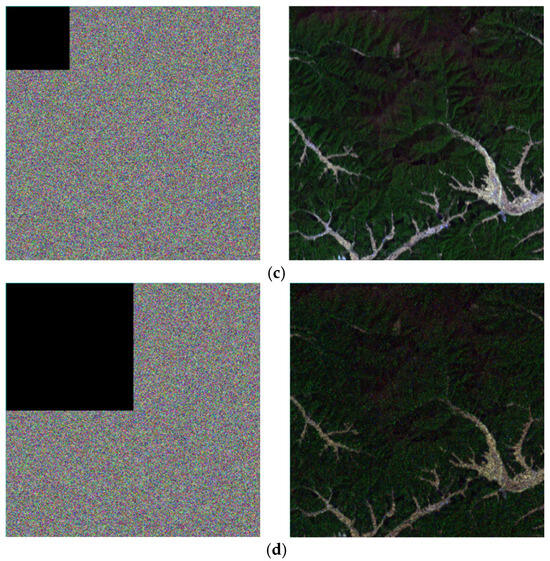
Figure 19.
Experimental results of resistance to cropping attacks. (a) Original image (Band selection: R = 32, G = 21, B = 11); (b) Cropped 1/64 region and decrypted image; (c) Cropped 1/16 region and decrypted image; (d) Cropped 1/4 region and decrypted image.
4.9. Resistance to Differential Attacks
Differential attacks are a type of chosen-plaintext attack. The core idea is to analyze the impact of differences in specially chosen plaintext pairs on the resulting ciphertext differences, thereby inferring the most probable key [56]. An algorithm resistant to differential attacks should ensure that a minor change in the plaintext leads to significant alterations in the ciphertext. The Number of Pixels Change Rate (NPCR) and the Unified Average Changing Intensity (UACI) are two primary metrics for evaluating this property [57]. The corresponding formulas are as follows:
where and are the number of rows and columns of the image, and are two ciphertext images whose original plaintexts differ by only one pixel value, is an indicator function (1 if , else 0), and is the pixel value range (for 16-bit DN values, ).
The acceptable intervals for NPCR and UACI at a significance level are given by:
where and .
Due to the different value range of DN values in hyperspectral images () compared to ordinary grayscale images, the confidence intervals differ accordingly. Table 5 and Table 6 list the NPCR and UACI values of the test images, along with their confidence intervals and test results. The results show that all NPCR and UACI values fall within the theoretically acceptable ranges, indicating that the proposed algorithm effectively resists differential attacks.

Table 5.
NPCR Test Results for Differential Attack Analysis.

Table 6.
UACI Test Results for Differential Attack Analysis.
4.10. Computational Efficiency Analysis
While the primary focus of this work is on achieving high security for hyperspectral images, we acknowledge the importance of computational efficiency given the large data volume. Experimental results showed that the average encryption times for the ZY1E, Botswana, PaviaU, and Indian Pines datasets were approximately 85.3 s, 23.6 s, 89.1 s, and 19.4 s, respectively.
The results indicate that the encryption time is approximately proportional to the total number of pixels (). The proposed algorithm provides a feasible solution for the secure offline storage and transmission of hyperspectral data. Future work will focus on optimizing the algorithm’s speed through parallel computing (e.g., GPU acceleration) to meet real-time requirements.
5. Discussion
Although the algorithm performs excellently in security and functional implementation, it still has certain limitations. The computational complexity is relatively high, which may restrict its use in large-scale scenarios with stringent real-time requirements; the current algorithm focuses only on full-image encryption without considering the sensitivity weight of different content within hyperspectral images; furthermore, hyperspectral data possess more underlying features—such as floating-point DN values and internal correlations within the image cube—that could be leveraged to further enhance encryption performance.
Future research efforts could be directed toward the following areas:
To improve computational efficiency, parallel computing and hardware acceleration strategies could be explored. By utilizing parallel computing architectures such as GPUs to parallelize spectral scrambling and DNA diffusion operations, the algorithm’s throughput could be significantly enhanced, meeting the demands of real-time encryption for large-scale hyperspectral data. The proposed method shows notable potential for parallelization, enabling a substantial increase in encryption efficiency while maintaining security through computational architecture optimization.
To enhance algorithm adaptability, novel encryption mechanisms integrating deep learning should be thoroughly investigated. Employing convolutional neural networks to automatically extract image texture features and adaptively adjust encryption strength can improve the algorithm’s intelligence and generalization capability without compromising security.
To broaden the application scope, the algorithm’s use in encrypting multidimensional remote sensing data should be actively explored. Extending the encryption framework to multispectral images, remote sensing video streams, and other geospatial data types will address key technical challenges in integrated security protection for multi-source remote sensing data and provide technical support for building an integrated space-air-ground secure transmission system.
To promote practical deployment, the implementation and optimization of the algorithm on dedicated hardware platforms should be emphasized. Designing hard-ware accelerators for the encryption algorithm using FPGAs or ASICs can meet the application requirements of resource-constrained scenarios such as onboard real-time processing and edge computing, facilitating the translation of research achievements into practical applications.
In summary, the proposed encryption algorithm demonstrates strong performance in protecting hyperspectral remote sensing images, yet there remains room for further optimization. Future research may focus on developing adaptive encryption mechanisms, exploring chaotic map parameters that dynamically evolve with image statistics, and extending the encryption framework to a wider range of geospatial data types. These research directions not only hold significant theoretical value but are also crucial for advancing the practical application of remote sensing data security protection.
6. Conclusions
This paper proposes a hyperspectral remote sensing image encryption algorithm based on a 2D-CSCM hyperchaotic map, effectively addressing the encryption challenges posed by the multidimensionality, large volume, and spectral characteristics of hyperspectral data. Experimental results demonstrate that the algorithm achieves efficient encryption of the spectral domain while fully preserving spatial information integrity. It also incorporates an adapted encryption mechanism tailored to the unique data structure and high bit-depth DN values of hyperspectral images, accomplishing comprehensive encryption of hyperspectral remote sensing images.
First, the 2D-CSCM hyperchaotic map was designed and validated through multiple analytical methods, including Lyapunov exponents, sample entropy, and NIST tests, confirming its excellent randomness and complex dynamic behavior, making it highly suitable for high-security image encryption applications. For key generation, the algorithm employs the SHA-512 hash function to derive keys from the original image, ensuring strong correlation between the keys and plaintext. During encryption, the algorithm first performs spectral dimension scrambling to conceal spectral curve features while maintaining the readability of spatial textures in individual bands. It then applies spatial pixel scrambling and DNA encoding-based bit-level diffusion to protect overall spatial texture information, thereby achieving encryption of the entire hyperspectral image. Experiments on real remote sensing images verify the security and effectiveness of the algorithm. The comprehensive experimental results indicate that the algorithm offers a large key space (2^512), significantly increased information entropy close to the ideal value after encryption, very low adjacent pixel correlation, and strong resistance against statistical analysis, cropping attacks, and differential attacks, fully demonstrating its superior security performance and practical value.
In terms of application value, the proposed 2D-CSCM chaotic map exhibits significantly better chaotic performance than existing maps, making it applicable not only to hyperspectral image encryption but also to other image encryption algorithms. By addressing the characteristics of hyperspectral remote sensing images and achieving both spectral and full-image encryption, the algorithm holds considerable application potential in the storage, transmission, and utilization of hyperspectral images.
Author Contributions
Conceptualization, Z.B.; methodology, Q.Z.; funding acquisition, Q.Z.; software, Z.B.; validation, Z.B.; formal analysis, Z.B.; investigation, Z.B.; resources, W.T., Y.W. and J.L.; data curation, Z.B.; writing—original draft preparation, Z.B.; writing—review and editing, Z.B., W.T. and X.W.; visualization, Z.B.; supervision, Q.Z.; project administration, Q.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Natural Science Support Program Project of the Xinjiang Production and Construction Corps, grant number 2025DB024.
Data Availability Statement
The hyperspectral remote sensing image data used in this study were partly obtained from the public dataset available at: https://www.ehu.eus/ccwintco/index.php/Hyperspectral_Remote_Sensing_Scenes, accessed on 3 October 2025 (including scenes such as Pavia Centre and University). The remaining portion of the data is subject to confidentiality agreements and institutional policies, and thus is not publicly available or shared in any form as part of this study.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
To ensure reproducibility and a fair comparison in Section 2.2, the parameters for the compared chaotic maps were set as follows, based on their original publications or standard chaotic regions:
Henon Map: a = 1.4, b = 0.3
2D-SLMM [18]: a = 1, b = 3
2D-LSMCL [19]: α = 0.75, β = 3
2D-CLSS [21]: p = 2.5
All maps were evaluated with initial conditions (0.4, 0.6) unless otherwise specified for a particular test.

Table A1.
Eight kinds of DNA coding rules.
Table A1.
Eight kinds of DNA coding rules.
| Rules | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
|---|---|---|---|---|---|---|---|---|
| A | 00 | 00 | 01 | 01 | 10 | 10 | 11 | 11 |
| T | 11 | 11 | 10 | 10 | 01 | 01 | 00 | 00 |
| G | 01 | 10 | 00 | 11 | 00 | 11 | 01 | 10 |
| C | 10 | 01 | 11 | 00 | 11 | 00 | 10 | 01 |
References
- Zhang, Z.; Huang, L.; Wang, Q.; Jiang, L.; Qi, Y.; Wang, S.; Shen, T.; Tang, B.-H.; Gu, Y. UAV Hyperspectral Remote Sensing Image Classification: A Systematic Review. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2025, 18, 3099–3124. [Google Scholar] [CrossRef]
- Kumar, V.; Singh, R.S.; Rambabu, M.; Dua, Y. Deep learning for hyperspectral image classification: A survey. Comput. Sci. Rev. 2024, 53, 100658. [Google Scholar] [CrossRef]
- He, L.; Li, J.; Liu, C.; Li, S. Recent Advances on Spectral–Spatial Hyperspectral Image Classification: An Overview and New Guidelines. IEEE Trans. Geosci. Remote Sens. 2018, 56, 1579–1597. [Google Scholar] [CrossRef]
- Vijayakumar, M.; Ahilan, A. An optimized chaotic S-box for real-time image encryption scheme based on 4-dimensional memristive hyperchaotic map. Ain Shams Eng. J. 2024, 15, 102620. [Google Scholar] [CrossRef]
- Ur Rehman, M. Quantum-enhanced Chaotic Image Encryption: Strengthening Digital Data Security With 1-D Sine-based Chaotic Maps and Quantum Coding. J. King Saud Univ. Comput. Inf. Sci. 2024, 36, 101980. [Google Scholar] [CrossRef]
- Alsubaei, F.S.; Alneil, A.A.; Mohamed, A.; Mustafa Hilal, A. Block-Scrambling-Based Encryption with Deep-Learning-Driven Remote Sensing Image Classification. Remote Sens. 2023, 15, 1022. [Google Scholar] [CrossRef]
- Li, Y.-M.; Jiang, M.; Wei, D.; Deng, Y. A Novel Image Encryption Algorithm Based on Compressive Sensing and a Two-Dimensional Linear Canonical Transform. Fractal Fract. 2024, 8, 92. [Google Scholar] [CrossRef]
- Su, Q.; Sun, Y.; Xia, Y.; Wang, Z. A robust color image watermarking scheme in the fusion domain based on LU factorization. Opt. Laser Technol. 2024, 174, 110726. [Google Scholar] [CrossRef]
- Jyothsna Devi, K.; Singh, P.; Bilal, M.; Nayyar, A. Enabling secure image transmission in unmanned aerial vehicle using digital image watermarking with H-Grey optimization. Expert Syst. Appl. 2024, 236, 121190. [Google Scholar] [CrossRef]
- Zhou, Q.; Sun, H.; Pang, X.; Ai, C.; Zhu, X.; Zhu, C.; Ren, N. Watermarking Algorithm for Remote Sensing Images Based on Ring-Shaped Template Watermark and Multiscale LCM. Remote Sens. 2024, 16, 2535. [Google Scholar] [CrossRef]
- Ye, C.; Tan, S.; Wang, J.; Shi, L.; Zuo, Q.; Feng, W. Social Image Security with Encryption and Watermarking in Hybrid Domains. Entropy 2025, 27, 276. [Google Scholar] [CrossRef]
- Kaur, M.; Kumar, V. A Comprehensive Review on Image Encryption Techniques. Arch. Comput. Methods Eng. 2020, 27, 15–43. [Google Scholar] [CrossRef]
- Wang, X.; Li, Y.; Jin, J. A new one-dimensional chaotic system with applications in image encryption. Chaos Solitons Fractals 2020, 139, 110102. [Google Scholar] [CrossRef]
- Huang, H.; Yang, S.; Ye, R. Efficient symmetric image encryption by using a novel 2D chaotic system. IET Image Process. 2020, 14, 1157–1163. [Google Scholar] [CrossRef]
- Singh, D.; Kaur, H.; Verma, C.; Kumar, N.; Illés, Z. A novel 3-D image encryption algorithm based on SHA-256 and chaos theory. Alex. Eng. J. 2025, 122, 564–577. [Google Scholar] [CrossRef]
- Higazy, M.; Almalki, N.; Muhammad, S.; Al-Ghamdi, A. A new fractional order 6D chaotic model: Study of model dynamics, system structure graph, electronic circuit realization and fractional control. J. Ocean Eng. Sci. 2024, 9, 112–125. [Google Scholar] [CrossRef]
- Gao, X.; Liu, X. CLSM-IEA: A novel cosine-logistic-sine map and its application in a new image encryption scheme. Signal Image Video Process. 2024, 18, 3063–3077. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.-M.; Chen, C.L.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Zhu, H.; Zhao, Y.; Song, Y. 2D Logistic-Modulated-Sine-Coupling-Logistic Chaotic Map for Image Encryption. IEEE Access 2019, 7, 14081–14098. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Xian, Y. Image encryption algorithm based on a 2D-CLSS hyperchaotic map using simultaneous permutation and diffusion. Inf. Sci. 2022, 605, 71–85. [Google Scholar] [CrossRef]
- Hu, M.; Li, J.; Di, X. Quantum image encryption scheme based on 2D chaotic map. Nonlinear Dyn. 2023, 111, 2815–2839. [Google Scholar] [CrossRef]
- Yu, F.; He, S.; Yao, W.; Cai, S.; Xu, Q. Bursting Firings in Memristive Hopfield Neural Network with Image Encryption and Hardware Implementation. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2025. [Google Scholar] [CrossRef]
- Yu, F.; Wang, X.; Guo, R.; Ying, Z.; Cai, S.; Jin, J. Dynamical Analysis, Hardware Implementation, and Image Encryption Application of New 4D Discrete Hyperchaotic Maps Based on Parallel and Cascade Memristors. Integration 2025, 104, 102475. [Google Scholar] [CrossRef]
- Yu, F.; Gracia, Y.M.; Guo, R.; Ying, Z.; Xu, J.; Yao, W.; Jin, J.; Lin, H. Dynamic Analysis and Application of 6D Multistable Memristive Chaotic System with Wide Range of Hyperchaotic States. Axioms 2025, 14, 638. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, K.; Zhang, J.; Zhao, X.; Chen, Y.; Cai, B.; Zhu, Z.; Wen, H.; Ye, C. Integrating Fractional-Order Hopfield Neural Network with Differentiated Encryption: Achieving High-Performance Privacy Protection for Medical Images. Fractal Fract. 2025, 9, 426. [Google Scholar] [CrossRef]
- Chen, L.; Li, C.; Li, C. Security Measurement of a Medical Communication Scheme Based on Chaos and DNA Coding. J. Vis. Commun. Image Represent. 2022, 83, 103424. [Google Scholar] [CrossRef]
- Feng, W.; He, Y.; Li, H.; Li, C. Cryptanalysis and Improvement of the Image Encryption Scheme Based on 2D Logistic-Adjusted-Sine Map. IEEE Access 2019, 7, 12584–12597. [Google Scholar] [CrossRef]
- Feng, W.; Qin, Z.; Zhang, J.; Ahmad, M. Cryptanalysis and Improvement of the Image Encryption Scheme Based on Feistel Network and Dynamic DNA Encoding. IEEE Access 2021, 9, 145459–145470. [Google Scholar] [CrossRef]
- Liu, M.; Zhang, S.; Fan, Z.; Qiu, M. H∞ state estimation for discrete-time chaotic systems based on a unified model. IEEE Trans. Syst. Man Cybern. Part B (Cybern.) 2012, 42, 1053–1063. [Google Scholar]
- Lin, L.; Shen, M.; So, H.C.; Chang, C. Convergence analysis for initial condition estimation in coupled map lattice systems. IEEE Trans. Signal Process. 2012, 60, 4426–4432. [Google Scholar] [CrossRef]
- Srivastava, A.N.; Das, S. Detection and prognostics on low-dimensional systems. IEEE Trans. Syst. Man Cybern. Part C (Appl. Rev.) 2009, 39, 44–54. [Google Scholar] [CrossRef]
- Li, H.; Yu, S.; Feng, W.; Chen, Y.; Zhang, J.; Qin, Z.; Zhu, Z.; Wozniak, M. Exploiting Dynamic Vector-Level Operations and a 2D-Enhanced Logistic Modular Map for Efficient Chaotic Image Encryption. Entropy 2023, 25, 1147. [Google Scholar] [CrossRef]
- Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar] [CrossRef]
- Wang, X.; Li, Y. Chaotic image encryption algorithm based on hybrid multi-objective particle swarm optimization and DNA sequence. Opt. Lasers Eng. 2021, 137, 106393. [Google Scholar] [CrossRef]
- Liu, H.; Teng, L.; Zhang, Y.; Si, R.; Liu, P. Mutil-medical image encryption by a new spatiotemporal chaos model and DNA new computing for information security. Expert Syst. Appl. 2024, 235, 121090. [Google Scholar] [CrossRef]
- Wang, Q.; Zhang, X.; Zhao, X. Color image encryption algorithm based on novel 2D hyper-chaotic system and DNA crossover and mutation. Nonlinear Dyn. 2023, 111, 22679–22705. [Google Scholar] [CrossRef]
- Sharma, V.K.; Sharma, J.B. Harris Hawk optimization driven adaptive image encryption integrating Hilbert vibrational decomposition and chaos. Appl. Soft Comput. 2024, 164, 112016. [Google Scholar] [CrossRef]
- Adão, T.; Hruška, J.; Pádua, L.; Bessa, J.; Peres, E.; Morais, R.; Sousa, J.J. Hyperspectral Imaging: A Review on UAV-Based Sensors, Data Processing and Applications for Agriculture and Forestry. Remote Sens. 2017, 9, 1110. [Google Scholar] [CrossRef]
- Toktas, F.; Erkan, U.; Yetgin, Z. Cross-channel color image encryption through 2D hyperchaotic hybrid map of optimization test functions. Expert Syst. Appl. 2024, 249, 123583. [Google Scholar] [CrossRef]
- Erkan, U.; Toktas, A.; Lai, Q. 2D hyperchaotic system based on Schaffer function for image encryption. Expert Syst. Appl. 2023, 213, 119076. [Google Scholar] [CrossRef]
- Qiu, H.; Xu, X.; Jiang, Z.; Sun, K.; Xiao, C. A color image encryption algorithm based on hyperchaotic map and Rubik’s Cube scrambling. Nonlinear Dyn. 2022, 110, 2869–2887. [Google Scholar] [CrossRef]
- Rong, X.; Chedjou, J.C.; Yu, X.; Makhkamov, B.S.; Jiang, D.; Kengne, J. A Special Memristive Diode-Bridge-Based Hyperchaotic Hyperjerk Autonomous Circuit with Three Positive Lyapunov Exponents. Chaos Solitons Fract. 2024, 189, 115704. [Google Scholar] [CrossRef]
- Feng, W.; Wang, Q.; Liu, H.; Ren, Y.; Zhang, J.; Zhang, S.; Qian, K.; Wen, H. Exploiting Newly Designed Fractional-Order 3D Lorenz Chaotic System and 2D Discrete Polynomial Hyper-Chaotic Map for High-Performance Multi-Image Encryption. Fractal Fract. 2023, 7, 887. [Google Scholar] [CrossRef]
- von Bremen, H.F.; Udwadia, F.E.; Proskurowski, W. An efficient QR based method for the computation of Lyapunov exponents. Phys. D Nonlinear Phenom. 1997, 101, 1–16. [Google Scholar] [CrossRef]
- Murillo-Escobar, D.; Murillo-Escobar, M.Á.; Cruz-Hernández, C.; Arellano-Delgado, A.; López-Gutiérrez, R.M. Pseudorandom number generator based on novel 2D Hénon-Sine hyperchaotic map with microcontroller implementation. Nonlinear Dyn. 2023, 111, 6773–6789. [Google Scholar] [CrossRef]
- Richman, J.S.; Moorman, J.R. Physiological time-series analysis using approximate entropy and sample entropy. Am. J. Physiol. Heart Circ. Physiol. 2000, 278, H2039–H2049. [Google Scholar]
- Wang, M.; Wang, X.; Wang, C.; Zhou, S.; Xia, Z.; Li, Q. Color image encryption based on 2D enhanced hyperchaotic logistic-sine map and two-way Josephus traversing. Digit. Signal Process. 2023, 132, 103818. [Google Scholar] [CrossRef]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, N.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; NIST Special Publication 800-22; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2010. [Google Scholar]
- Du, Y.; Chang, C.-I.; Ren, H.; Chang, C.-C.; Jensen, J.O.; D’Amico, F.M. New hyperspectral discrimination measure for spectral characterization. Opt. Eng. 2004, 43, 1777–1786. [Google Scholar] [CrossRef]
- Mao, N.; Tong, X.; Zhang, M.; Wang, Z. Real-time image encryption algorithm based on combined chaotic map and optimized lifting wavelet transform. J. Real-Time Image Process. 2023, 20, 35. [Google Scholar] [CrossRef]
- Liu, P.; Wang, X.; Su, Y.; Liu, H.; Unar, S. Globally Coupled Private Image Encryption Algorithm Based on Infinite Interval Spatiotemporal Chaotic System. IEEE Trans. Circuits Syst. I Regul. Pap. 2023, 70, 2511–2522. [Google Scholar] [CrossRef]
- Rani, N.; Sharma, S.R.; Mishra, V. Grayscale and colored image encryption model using a novel fused magic cube. Nonlinear Dyn. 2022, 108, 1773–1796. [Google Scholar] [CrossRef]
- Wang, X.; Xue, W.; An, J. Image encryption algorithm based on Tent-Dynamics coupled map lattices and diffusion of Household. Chaos Solitons Fractals 2020, 141, 110309. [Google Scholar] [CrossRef]
- Yu, J.; Xie, W.; Zhong, Z.; Wang, H. Image encryption algorithm based on hyperchaotic system and a new DNA sequence operation. Chaos Solitons Fractals 2022, 162, 112456. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, R.; Liu, J. Partial-privacy image encryption algorithm based on time-varying delayed exponentially controlled chaotic system. Nonlinear Dyn. 2024, 112, 10633–10659. [Google Scholar] [CrossRef]
- Khan, J.S.; Kayhan, S.K. Chaos and compressive sensing based novel image encryption scheme. J. Inf. Secur. Appl. 2021, 58, 102711. [Google Scholar] [CrossRef]
- Wu, Y.; Noonan, J.P.; Agaian, S. NPCR and UACI randomness tests for image encryption. Cybern. J. Multidiscip. J. Sci. Technol. J. Sel. Areas Telecommun. 2011, 1, 31–38. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).