Abstract
Virtual networks have emerged as a promising solution for enabling diverse users to efficiently share bandwidth resources over optical network infrastructures. Despite the invention of various schemes aimed at ensuring secure isolation among virtual networks, the security of data transfer in virtual networks remains a challenging problem. To address this challenge, the concept of evolving traditional optical networks into key programmable optical networks (KPONs) has been proposed. Inspired by this, this paper delves into the establishment of secure virtual networks over KPONs, in which the information-theoretically secure keys can be supplied for ensuring the information-theoretic security of data transfer within virtual networks. A layered architecture for secure virtual network provisioning over KPONs is proposed, which leverages software-defined networking to realize the programmable control of optical-layer resources. With this architecture, a heuristic algorithm, i.e., the key adaptation-based secure virtual network provisioning (KA-SVNP) algorithm, is designed to dynamically allocate key resources based on the adaption between the key supply and key demand. To evaluate the proposed solutions, an emulation testbed is established, achieving millisecond latencies for secure virtual network establishment and deletion. Moreover, numerical simulations indicate that the designed KA-SVNP algorithm performs superior to the benchmark algorithm in terms of the success probability of secure virtual network requests.
1. Introduction
The exponential growth of network traffic driven by Internet-based applications (e.g., cloud computing, augmented reality and e-banking) has led to an increased focus on the need for sensitive data secrecy. Optical networks have been widely deployed around the world and have become one of the most important underlying telecommunication facilities for data transfer nowadays. However, a variety of sophisticated and diverse attacks (e.g., eavesdropping, jamming and interception [1]) have emerged in optical networks, posing a significant threat to the optical network security.
Encryption is an effective method for diminishing the adverse effects of the aforementioned attacks and enhancing the security of data transmission through optical networks. It is exceedingly difficult for an eavesdropper to decrypt the ciphertext without knowledge of the encryption key. In order to ensure the adaptability and compatibility with high-speed optical networks, a variety of optical domain encryption strategies have been proposed [2,3,4,5,6,7], with the aim of improving the security of optical networks. Nevertheless, the enhanced computational capabilities and the invention of advanced algorithms [8,9] may compromise the security of numerous traditional secrecy techniques for optical networks in the near future.
The physical layer security (PLS) based methods have been proposed as effective means to augment the security of optical networks. One such method is the quantum noise stream cipher (QNSC) [10,11,12,13], which has been suggested as a method of masking the signal states with intrinsic quantum noise, thereby directly encrypting the data across optical networks. Furthermore, quantum key distribution (QKD) [14,15,16,17], in combination with optical networks, can provide complementary capacity and security, where the information-theoretically secure keys can be produced. The produced secure keys can be further combined with the one-time pad algorithm to guarantee the information-theoretic security of data encryption. Obviously, the secure keys are of paramount importance in providing enhanced security for future optical networks. In particular, the concept and architecture of key programmable optical networks (KPONs) have been proposed in [18], enabling the flexible generation and distribution of the secure keys using PLS-based approaches under the programmable techniques.
Currently, the virtual networks are being developed and constructed on top of the substrate optical network infrastructure with the objective of sharing valuable network resources (e.g., computing, switching and spectrum resources) [19,20,21,22]. This approach offers the advantage of improving the utilization of optical-layer resources and is, therefore, an essential component of the future optical network architecture. As the volume of confidential data transferred daily by the virtual networks continues to grow, the credibility of optical networks will become increasingly important. Hence, it is anticipated that the KPON will evolve to serve as the substrate optical network for the realization of secure virtual networks, in which the information-theoretically secure keys can be supplied for ensuring the information-theoretic security of data transfer within virtual networks. Accordingly, how to efficiently realize the provisioning of numerous secure virtual networks over a KPON becomes an essential problem.
Targeting at this problem, this work proposes a layered architecture for secure virtual network provisioning over KPONs, in which a software-defined networking (SDN) controller is deployed in the middle layer for efficient resource management, and the programmable agent is developed to enable the flexible configuration of KPONs. In addition, a key adaptation-based secure virtual network provisioning (KA-SVNP) algorithm is devised, where the information-theoretically secure key resources and the key requirements are specially taken into account in the construction of multiple secure virtual optical networks. Further, an emulation testbed is established, while the total latency for secure virtual network establishment and deletion, as well as the average control latency for a single node, are evaluated. The success probability of secure virtual network requests is evaluated through numerical simulations, demonstrating the superior performance of the devised KA-SVNP algorithm in comparison to the benchmark algorithm.
The rest of this paper is organized as follows. Section 2 presents the network architecture for secure virtual network provisioning over KPONs. The network model and the KA-SVNP algorithm are proposed in Section 3. Section 4 demonstrates the emulation results and analyzes the simulation results. Finally, Section 5 concludes this paper.
2. Network Architecture
2.1. Securing Virtual Networks with PLS-Based Keys
The PLS techniques for key generation and distribution in optical networks allow for the production of information-theoretically secure keys between any pair of optical nodes. These optical nodes are situated within the substrate nodes of the KPON. Figure 1 illustrates the process of securing virtual networks with PLS-based keys from the KPON. The key server is situated in the same physical location as the optical node, in order to manage the entire lifetime of keys with information-theoretic security, including key generation, distribution, allocation, destruction, and so on. To elaborate a little further, the key generation and distribution are implemented based on the PLS module (e.g., QKD module) embedded within the key server. Furthermore, the specific implementation details of key management (e.g., key storage, allocation, updating, and destruction) are not the focus of this paper. Specifically, we adopt the standard key management operations specified in ITU-T Recommendation Y.3803 [23]. For further details of the operations of key management, please refer to [23]. Notably, the forward security is supported since the generated keys can ensure information-theoretic security based on PLS-based approaches (e.g., QKD). In light of the fact that PLS-based keys are generated in a distributed manner, it is necessary to place the key server in a distributed manner. This entails equipping each optical node with a key server. Multiple virtual networks can be constructed over the same KPON. Each virtual network is constituted of several virtual nodes interconnected by virtual links. The transfer of data across the virtual network can be secured by obtaining the requisite secure keys from the key server. The key server is tasked with realizing the virtualization of PLS-based key resources, thereby facilitating the allocation of secure keys for data encryption and decryption between each pair of virtual nodes. The virtual nodes and virtual links are abstracted from the optical nodes and optical links in the KPON, respectively. The key requirements for different pairs of virtual nodes may be different. Hence, the construction of a secure virtual network has to consider not only the bandwidth resource requirements of the virtual links, but also the key requirements between each pair of virtual nodes.
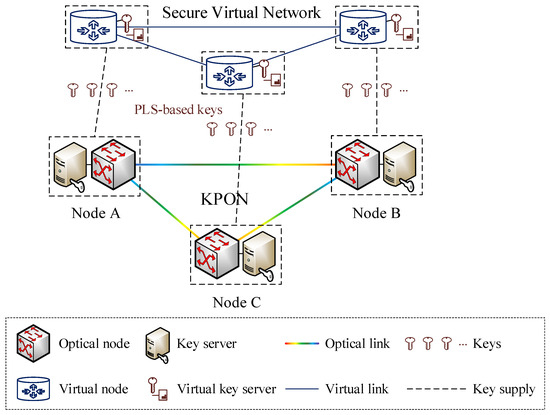
Figure 1.
Illustration of securing virtual networks with PLS-based keys from the KPON.
As exemplified in Figure 1, in the event that the information-theoretically secure keys shared between any pair of optical nodes (e.g., Nodes A and B) are symmetric keys, a proportion of these keys should be symmetrically virtualized into virtual key servers situated between virtual nodes A and B, in order to satisfy the key requirements of the secure virtual network. In particular, the security requirements of the virtual network are specific to each pair of virtual nodes. Moreover, the virtual link A-B is abstracted from the optical link A-B by occupying a portion of the bandwidth resources. In consequence of the aforementioned process, the virtual network is able to use bandwidth resources and information-theoretically secure key resources for secure communications among its virtual nodes, without concerning itself with the specifics of the underlying KPON infrastructure.
2.2. Layered Architecture for Secure Virtual Network Provisioning over KPONs
In order to ensure the effective implementation of the aforementioned process for securing virtual networks with information-theoretically secure keys from the KPON, it is advisable to introduce the SDN technique, which allows for the centralized management of the KPON via a logical control approach. The feasibility of introducing the SDN technique with an efficient global control capability for virtual network construction has been confirmed in previous studies [24,25]. Accordingly, the implementation of secure virtual network provisioning over KPONs can rely on the SDN-based layered architecture shown in Figure 2. This layered architecture comprises three layers, arranged in a top-down sequence, i.e., the secure virtual network layer, the control layer and the substrate KPON layer. The substrate KPON layer is constituted of a number of substrate nodes interconnected by substrate fiber links. Each substrate node comprises an optical node and a key server. The keys with information-theoretic security are generated between each pair of optical nodes and their life cycles are managed by the corresponding key servers. In addition, each substrate node is linked to a programmable agent to facilitate its adaptive configuration.
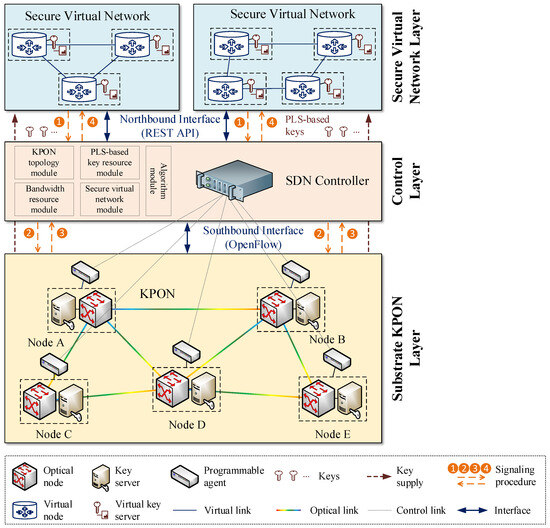
Figure 2.
Illustration of the layered architecture for secure virtual network provisioning over KPONs.
The secure virtual network layer is constituted by a number of secure virtual networks, which are abstracted from the substrate KPON layer. A secure virtual network consists of several virtual nodes interconnected by virtual links, where the virtual key servers present in each virtual node are abstracted from the corresponding key servers. Specifically, a subset of keys with information-theoretic security is virtualized from the key server and stored in the virtual key server, in order to satisfy the corresponding security requirements of each virtual network. In reality, multiple secure virtual networks can share the bandwidth and key resources over the same KPON.
In the control layer, a centralized SDN controller is deployed with the objective of performing flexible secure virtual network provisioning over the KPON. The SDN controller comprises a number of modules, each of which implements a specific control function for the KPON. These include the KPON topology module, the bandwidth resource module, the PLS-based key resource module, the secure virtual network module, and the algorithm module. As the control layer represents a middle layer within this layered architecture, it also serves as a bridge between the secure virtual network layer and the substrate KPON layer. The northbound interface is employed for the intercommunication between the control layer and the secure virtual network layer, with the REST API serving as the implementation. Conversely, the southbound interface is implemented by OpenFlow [26,27], which facilitates communication between the control layer and the substrate KPON layer. The simplified control and configuration signaling procedures for secure virtual network provisioning are indicated by orange dashed lines and numbered from 1 to 4. Furthermore, the security of these control and configuration signaling messages can be augmented through the use of keys with information-theoretic security.
3. Heuristic Algorithm Design
3.1. Network Model
The network model entails the mathematical representation of the substrate KPON and the secure virtual network request. A KPON is modelled as , where and represent the substrate node set and the substrate fiber link set, respectively. Additionally, a substrate node is denoted by . In accordance with the aforementioned description, the optical nodes and the key servers also correspond to . On each substrate link , the total bandwidth resources and the total information-theoretically secure key resources are denoted by and , respectively. It is important to note that the bandwidth resources are reflected by the number of wavelength channels, while the information-theoretically secure key resources are reflected by the PLS-based key rates.
The set of incoming secure virtual network requests is modelled as . Each secure virtual network request is represented by , where and represent the virtual node set and the virtual link set, respectively. In addition, a virtual node of request is denoted by , while a virtual link of request is denoted by . Furthermore, each secure virtual network request is associated with specific bandwidth requirements and key requirements for the implementation of secure communications among its virtual nodes. In this section, for each secure virtual network request, it is assumed that the bandwidth requirement for each virtual link is the same and the key requirement between each pair of virtual nodes is the same. The bandwidth requirements and key requirements of request are represented by and , respectively.
Given that the bandwidth resources and the information-theoretically secure key resources can be employed dynamically, the real-time available bandwidth resources and the information-theoretically secure key resources for link at time step are represented by and , respectively. These can be expressed as follows:
where represents the set of online secure virtual networks successfully configured over the KPON that occupy link at time step .
In this paper, we focus on enhancing the security of virtual networks. Consequently, the information-theoretically secure key resources are the primary resources considered for the construction of secure virtual networks. For each virtual link, it may be abstracted from a physical path on the substrate KPON, given that the substrate nodes corresponding to the virtual nodes may not be directly connected. The set of physical paths available for virtual link is denoted by , where each physical path is denoted by . Then, the set of substrate links on path is represented by . The real-time available information-theoretically secure key resources for the physical path at time step is denoted by , which is characterized by the minimum available information-theoretically secure key resources on the substrate links along the path . A key adaption metric is defined for the path as follows:
In the event that the value of is negative, it becomes impossible to satisfy the key requirements of the corresponding secure virtual network request. In practice, the path with the maximum value of is the better option in for implementing the virtual link of this request, since the achievable information-theoretically secure key resources are more sufficient and the number of hops is lower in this case, thus contributing to the saving of information-theoretically secure key resources.
3.2. KA-SVNP Algorithm
A dynamic key adaptation-based secure virtual network provisioning (KA-SVNP) algorithm is devised to map each incoming secure virtual network request over the KPON, as shown in Algorithm 1. This can be expressed as the secure virtual network mapping for each request , involving two primary steps: firstly, node mapping for each virtual node, i.e., can be mapped onto a set of candidate substrate nodes (i.e., ); secondly, link mapping for each virtual link, i.e., can be mapped onto a set of candidate physical paths (i.e., ). In this context, a deterministic relationship is established between the virtual node and the substrate node for a secure virtual network request. The virtual link is mapped into one of the alternative physical paths , where the bandwidth resource constraint and the information-theoretically secure key resource constraint are considered. It is important to note that the allocation of key resources takes precedence over that of bandwidth resources, given the necessity for securing the virtual network prior to communication between its virtual nodes. The K-shortest-path approach is utilized for computing alternative physical paths for each node pair. It employs edge weights calculated based on hop counts and does not involve key resources. Subsequently, the final path is selected based on the adaption between the key supply and key demand (i.e., the path with the maximum value of is selected). The final assignment also depends on the ordering of virtual links, which is based on the number of hops in their corresponding final physical paths, arranged in ascending order. Furthermore, the first-fit approach is adopted for the allocation of bandwidth and information-theoretically secure key resources, which has been extensively utilized for resource allocation in secure optical networks [28,29]. The failure of secure virtual network requests typically stems from insufficient bandwidth or key resources, while the search strategy for resource allocation (e.g., the first-fit approach used in this paper) can also contribute to such failures. Hence, the search strategy for resource allocation can be further optimized in future studies. It is important to note that existing solutions (including the designed KA-SVNP algorithm) to the virtual network provisioning problem are difficult to achieve optimality in dynamic scenarios, which has been proven to be an NP-hard problem [21].
| Algorithm 1: KA-SVNP algorithm | |
| Input: , , , , , | |
| Output: , , | |
| 1: | initialize ; |
| 2: | for each incoming secure virtual network request do |
| 3: | for each virtual node do |
| 4: | perform deterministic node mapping to map the virtual node from the secure virtual network request onto a substrate node, where the assignment is realized for the virtual node with the same location as the substrate node; |
| 5: | end for |
| 6: | for each virtual link do |
| 7: | compute the alternative physical paths with the K-shortest-path approach; |
| 8: | record the alternative physical paths in ; |
| 9: | for each alternative physical path do |
| 10: | search the substrate links on path and record them in ; |
| 11: | search the real-time available information-theoretically secure key resources for each substrate link along the physical path ; |
| 12: | search the real-time available bandwidth resources for each substrate link along the physical path ; |
| 13: | compute the real-time available information-theoretically secure key resources for the physical path ; |
| 14: | ; |
| 15: | if do |
| 16: | remove this physical path from ; |
| 17: | end if |
| 18: | if the bandwidth requirement cannot be satisfied do |
| 19: | remove this physical path from ; |
| 20: | end if |
| 21: | end for |
| 22: | if do |
| 23: | mark ; |
| 24: | select the alternative physical path with the maximum value of in as the final physical path for ; |
| 25: | else |
| 26: | mark ; |
| 27: | break; |
| 28: | end if |
| 29: | end for |
| 30: | if do |
| 31: | record the secure virtual network request in ; |
| 32: | allocate the information-theoretically secure key resources and the bandwidth resources with the first-fit approach; |
| 33: | update the status of information-theoretically secure key resources and bandwidth resources; |
| 34: | else |
| 35: | the secure virtual network request is failed; |
| 36: | end if |
| 37: | end for |
| 38: | estimate the success probability: ; |
| 39: | return , , . |
The success probability () of secure virtual network requests is estimated based on the ratio of the number of successfully provisioned secure virtual network requests to the total number of incoming secure virtual network requests, which can be expressed as:
where represents the set of secure virtual network requests that are successfully provisioned over the KPON.
4. Evaluation and Analysis
4.1. Emulation Results for the Latency
In order to verify the proposed layered architecture for secure virtual network provisioning over KPONs, an emulation testbed is established, following the KPON topology shown in Figure 3. The REST API is developed based on the HTTP/JSON, while the OpenFlow protocol is implemented for the intercommunication between the SDN controller and programmable agents. The SDN controller is developed based on the OpenDayLight platform. Moreover, the Open vSwitch is developed to implement the function of the programmable agent, which also emulates the functions of optical nodes and key servers.
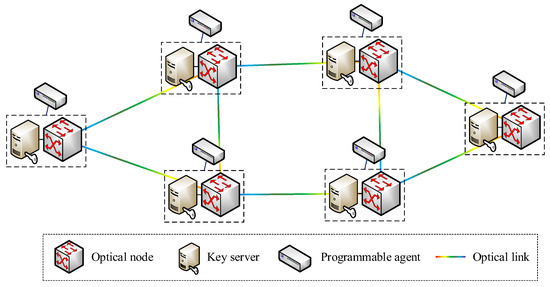
Figure 3.
The KPON topology used in the emulation.
Figure 4 displays the establishment and deletion latencies for secure virtual networks. The number of virtual nodes for each virtual network is set to 3, while the PLS-based key requirement and bandwidth requirement are set to 100 bps and 50 GHz (i.e., a wavelength channel), respectively. The total latency represents the time interval between the arrival of the secure virtual network establishment/deletion request and the reception of the establishment/deletion response. It can be observed that the total latencies exhibit variability across different secure virtual networks. In the case of the emulated eight requests, the minimum and maximum total latencies for the establishment of the secure virtual network are 300.5 ms and 589.9 ms, respectively. In addition, the minimum and maximum total latencies for the deletion of the secure virtual network are 142.6 ms and 584.8 ms, respectively. Hence, even though the total latency may fluctuate, the millisecond latency for the establishment/deletion of a secure virtual network over the KPON can be achieved.
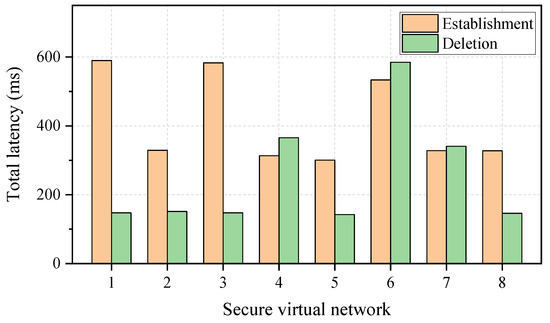
Figure 4.
The total latency for the establishment/deletion of secure virtual networks.
The emulation results of the average control latency for the intercommunication between the SDN controller and a single node are illustrated in Figure 5. It can be observed that the average control latency is lower than 2 ms for a once-only intercommunication, demonstrating the benefits of the KPON in supporting the low-latency configuration of secure virtual networks. In addition, the virtual nodes/links for a secure virtual network are processed individually in the emulation testbed, hence the latency will increase in proportion to the scale of the virtual network.
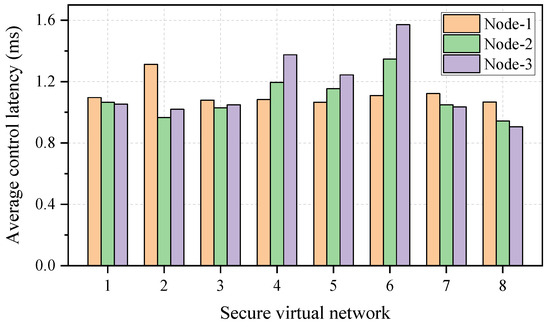
Figure 5.
The average control latency for the intercommunication between the SDN controller and a single node.
4.2. Simulation Results for the Success Probability of Secure Virtual Network Requests
In order to evaluate the performance of the proposed KA-SVNP algorithm in a high-load environment, numerical simulations are carried out using the 14-node NSFNET topology, as shown in Figure 6. The secure virtual network requests arrive following a Poisson process. The value of K is set to 5 in the K-shortest-path approach. The number of virtual nodes for a secure virtual network request is randomly selected from the interval [2,3].
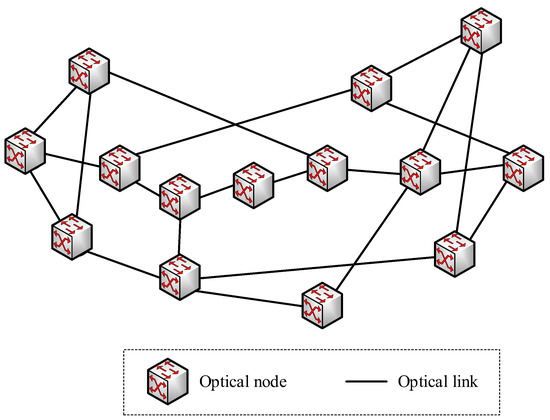
Figure 6.
The NSFNET topology used in the numerical simulation.
Figure 7 presents a comparative analysis of the proposed KA-SVNP algorithm and the benchmark algorithm in terms of the success probability of secure virtual network requests, where the scenarios without bandwidth limitation and with bandwidth limitation are considered in Figure 7a,b, respectively. The benchmark algorithm is the traditional virtual network provisioning algorithm with stochastic available path selection, which does not take into account the key adaption. The key requirement for each secure virtual network request is randomly selected from the interval [1,4] kbps, while the information-theoretically secure key resources (i.e., key rates) for each substrate link are 50 kbps. In Figure 7a, the number of bandwidth resources is sufficient. In Figure 7b, each substrate link provides 40 wavelength channels (each at 50 GHz) of bandwidth resources, while each secure virtual network request requires one wavelength channel at 50 GHz. From Figure 7 we can see that the proposed KA-SVNP algorithm demonstrably outperforms the benchmark algorithm in both scenarios. For example, when the traffic load is 170 Erlangs, the improvement in the success probability of secure virtual network requests for the KA-SVNP algorithm relative to the benchmark algorithm can reach 8.7% and 10.8% in the scenarios without bandwidth limitation and with bandwidth limitation, respectively, thereby demonstrating the efficiency of the proposed KA-SVNP algorithm. Hence, the key supply (i.e., the information-theoretically secure key resources for each substrate link) and key demand (i.e., the key requirement of the secure virtual network request) can be adaptive by the selection of the physical path with the maximum value of in the proposed KA-SVNP algorithm.
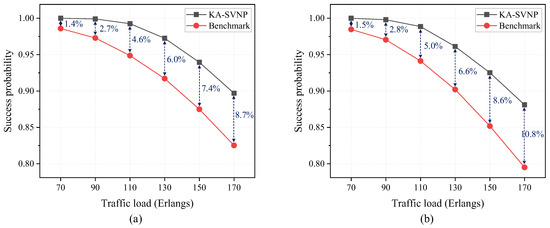
Figure 7.
Success probability of secure virtual network requests versus traffic load for the proposed KA-SVNP algorithm and the benchmark algorithm in two scenarios: (a) without bandwidth limitation; (b) with bandwidth limitation.
The results of the success probability of secure virtual network requests as a function of traffic load are plotted in Figure 8, where the scenario without bandwidth limitation is considered. In Figure 8a, the comparative analysis of different information-theoretically secure key resources is presented, where the key requirement for each secure virtual network request is randomly selected from the interval [1,4] kbps. In addition, Figure 8b illustrates the comparison of different key requirements, with the PLS-based key rate for each substrate link set at 50 kbps. It can be seen that the success probability of secure virtual network requests declines progressively as the traffic load rises. This is due to either an increase in the arrival rate or a decrease in the departure rate. As shown in Figure 8a, an increase in the PLS-based key rate results in a corresponding rise in the success probability of secure virtual network requests, due to the expansion of the total available key resources. As illustrated in Figure 8b, the success probability of secure virtual network requests declines in conjunction with an increase in key requirements. This is due to an increase in the total key requirements. Consequently, in order to accommodate a larger number of secure virtual network requests, it may be necessary to either increase the value of or reduce the range of . However, this may result in a trade-off between cost and flexibility.
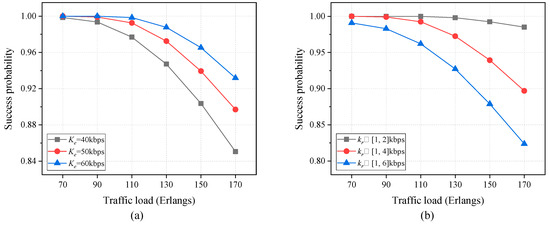
Figure 8.
Success probability of secure virtual network requests versus traffic load for different PLS-based (a) key resources and (b) key requirements.
5. Conclusions
This paper presents an investigation of the secure virtual network provisioning over KPONs. The information-theoretically secure keys are generated via the PLS-based method to ensure the information-theoretic security of data transfer within virtual networks. A layered architecture for enabling efficient configuration of secure virtual networks over the KPON is illustrated. Furthermore, the network model is formulated and the key adaption metric is defined. A KA-SVNP algorithm is designed relying on the dynamic adaptation of the key supply and key demand, where the physical path for each virtual link of the secure virtual network request is specifically selected based on the value of . The emulation testbed is established, and the emulation results for the latency are analyzed. In particular, the millisecond latency for the establishment/deletion of a secure virtual network over the KPON can be achieved. Furthermore, numerical simulations are performed, and the simulation results for the success probability of secure virtual network requests versus the traffic load are analyzed. With regard to the success probability of secure virtual network requests, the proposed KA-SVNP algorithm is observed to outperform the benchmark algorithm by 8.7% under a traffic load of 170 Erlangs. Moreover, in order to increase the success probability of secure virtual network requests, it is possible to either increase the value of or reduce the range of . In future work, we will further conduct simulation experiments on large-scale carrier-grade topologies to verify the generalization ability of the proposed algorithm in real network scenarios. Furthermore, machine learning methods are expected to be utilized to enhance the performance of secure virtual network provisioning.
Author Contributions
Conceptualization, X.W. and H.J.; Methodology, J.L. and Z.L.; Validation, X.W., J.L. and Z.L.; Writing—Original Draft Preparation, X.W. and H.J.; Writing—Review & Editing, X.W., J.L. and Z.L.; Funding Acquisition, X.W., H.J., J.L. and Z.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Key Research and Development Program of China (2023YFF0612900).
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Skorin-Kapov, N.; Furdek, M.; Zsigmond, S.; Wosinska, L. Physical-layer security in evolving optical networks. IEEE Commun. Mag. 2016, 54, 110–117. [Google Scholar] [CrossRef]
- Kitayama, K.-I.; Sasaki, M.; Araki, S.; Tsubokawa, M.; Tomita, A.; Inoue, K.; Harasawa, K.; Nagasako, Y.; Takada, A. Security in photonic networks: Threats and security enhancement. J. Light. Technol. 2011, 29, 3210–3222. [Google Scholar] [CrossRef]
- Li, Y.; Hua, N.; Li, J.; Zhong, Z.; Li, S.; Zhao, C.; Xue, X.; Zheng, X. Optical spectrum feature analysis and recognition for optical network security with machine learning. Opt. Express 2019, 27, 24808–24827. [Google Scholar] [CrossRef]
- Engelmann, A.; Jukan, A. Toward all-optical layered encryption: A feasibility analysis of optical stream cipher. IEEE Trans. Inf. Foren. Sec. 2019, 14, 2689–2704. [Google Scholar] [CrossRef]
- Chen, F.; Song, M.; Zhou, F.; Zhu, Z. Security-aware planning of packet-over-optical networks in consideration of OTN encryption. IEEE Trans. Netw. Service Manag. 2021, 18, 3209–3220. [Google Scholar] [CrossRef]
- Zhao, A.; Jiang, N.; Liu, S.; Zhang, Y.; Qiu, K. Physical layer encryption for WDM optical communication systems using private chaotic phase scrambling. J. Light. Technol. 2021, 39, 2288–2295. [Google Scholar] [CrossRef]
- Lv, Q.; Zhu, Z. On the multilayer planning of filterless optical networks with OTN encryption. IEEE/ACM Trans. Netw. 2023, 31, 2529–2544. [Google Scholar] [CrossRef]
- Gill, S.S.; Kumar, A.; Singh, H.; Singh, M.; Kaur, K.; Usman, M.; Buyya, R. Quantum computing: A taxonomy, systematic review and future directions. Softw.-Pract. Exp. 2022, 52, 66–114. [Google Scholar] [CrossRef]
- Yang, Z.; Zolanvari, M.; Jain, R. A survey of important issues in quantum computing and communications. IEEE Commun. Surv. Tutor. 2023, 25, 1059–1094. [Google Scholar] [CrossRef]
- Yoshida, M.; Kan, T.; Kasai, K.; Hirooka, T.; Nakazawa, M. 10 Tbit/s QAM quantum noise stream cipher coherent transmission over 160 km. J. Light. Technol. 2021, 39, 1056–1063. [Google Scholar] [CrossRef]
- Tanizawa, K.; Futami, F. IF-over-fiber transmission of OFDM quantum-noise randomized PSK cipher for physical layer encryption of wireless signals. J. Light. Technol. 2022, 40, 1698–1704. [Google Scholar] [CrossRef]
- Sun, J.; Jiang, L.; Yi, A.; Feng, J.; Deng, X.; Pan, W.; Luo, B.; Yan, L. Experimental demonstration of 201.6-Gbit/s coherent probabilistic shaping QAM transmission with quantum noise stream cipher over a 1200-km standard single mode fiber. Opt. Express 2023, 31, 11344–11353. [Google Scholar] [CrossRef]
- Li, Y.; Li, Y.; Zhu, K.; Wang, W.; Zhao, Y.; Zhang, J. Analysis of the encryption penalty in a QAM-based quantum noise stream cipher. Opt. Express 2023, 31, 19006–19020. [Google Scholar] [CrossRef]
- Lo, H.-K.; Curty, M.; Tamaki, K. Secure quantum key distribution. Nat. Photonics 2014, 8, 595–604. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.-K.; Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The evolution of quantum key distribution networks: On the road to the Qinternet. IEEE Commun. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhang, H.; Zhang, J. Key programmable optical networks (KPON) with OpenFlow-based key distribution. In Proceedings of the Asia Communications and Photonics Conference, Wuhan, China, 2–5 November 2016; AF2A.139. [Google Scholar]
- Fischer, A.; Botero, J.F.; Beck, M.T.; de Meer, H.; Hesselbach, X. Virtual network embedding: A survey. IEEE Commun. Surv. Tutor. 2013, 15, 1888–1906. [Google Scholar] [CrossRef]
- Gong, L.; Zhu, Z. Virtual optical network embedding (VONE) over elastic optical networks. J. Light. Technol. 2014, 32, 450–460. [Google Scholar] [CrossRef]
- Gong, L.; Jiang, H.; Wang, Y.; Zhu, Z. Novel location-constrained virtual network embedding LC-VNE algorithms towards integrated node and link mapping. IEEE/ACM Trans. Netw. 2016, 24, 3648–3661. [Google Scholar] [CrossRef]
- Fan, W.; Xiao, F.; Chen, X.; Cui, L.; Yu, S. Efficient virtual network embedding of cloud-based data center networks into optical networks. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 2793–2808. [Google Scholar] [CrossRef]
- International Telecommunication Union. Quantum Key Distribution Networks—Key Management; ITU-T Recommendation Y.3803; International Telecommunication Union: Geneva, Switzerland, 2020. [Google Scholar]
- Aguado, A.; Davis, M.; Peng, S.; Álvarez, M.V.; López, V.; Szyrkowiec, T.; Autenrieth, A.; Vilalta, R.; Mayoral, A.; Muñoz, R.; et al. Dynamic virtual network reconfiguration over SDN orchestrated multitechnology optical transport domains. J. Light. Technol. 2016, 34, 1933–1938. [Google Scholar] [CrossRef]
- Li, H.; Ota, K.; Dong, M. Virtual network recognition and optimization in SDN-enabled cloud environment. IEEE Trans. Cloud Comput. 2021, 9, 834–843. [Google Scholar] [CrossRef]
- Channegowda, M.; Nejabati, R.; Fard, M.R.; Peng, S.; Amaya, N.; Zervas, G.; Simeonidou, D.; Vilalta, R.; Casellas, R.; Martínez, R.; et al. Experimental demonstration of an OpenFlow based software-defined optical network employing packet, fixed and flexible DWDM grid technologies on an international multi-domain testbed. Opt. Express 2013, 21, 5487–5498. [Google Scholar] [CrossRef]
- Cvijetic, N.; Tanaka, A.; Ji, P.N.; Sethuraman, K.; Murakami, S.; Wang, T. SDN and OpenFlow for dynamic flex-grid optical access and aggregation networks. J. Light. Technol. 2014, 32, 864–870. [Google Scholar] [CrossRef]
- Zhao, Y.; Cao, Y.; Wang, W.; Wang, H.; Yu, X.; Zhang, J.; Tornatore, M.; Wu, Y.; Mukherjee, B. Resource allocation in optical networks secured by quantum key distribution. IEEE Commun. Mag. 2018, 56, 130–137. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Li, J.; Lin, R.; Zhang, J.; Chen, J. Hybrid trusted/untrusted relay-based quantum key distribution over optical backbone networks. IEEE J. Sel. Areas Commun. 2021, 39, 2701–2718. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).