A First-Out Alarm Detection Method via Association Rule Mining and Correlation Analysis
Abstract
:1. Introduction
2. Problem Description
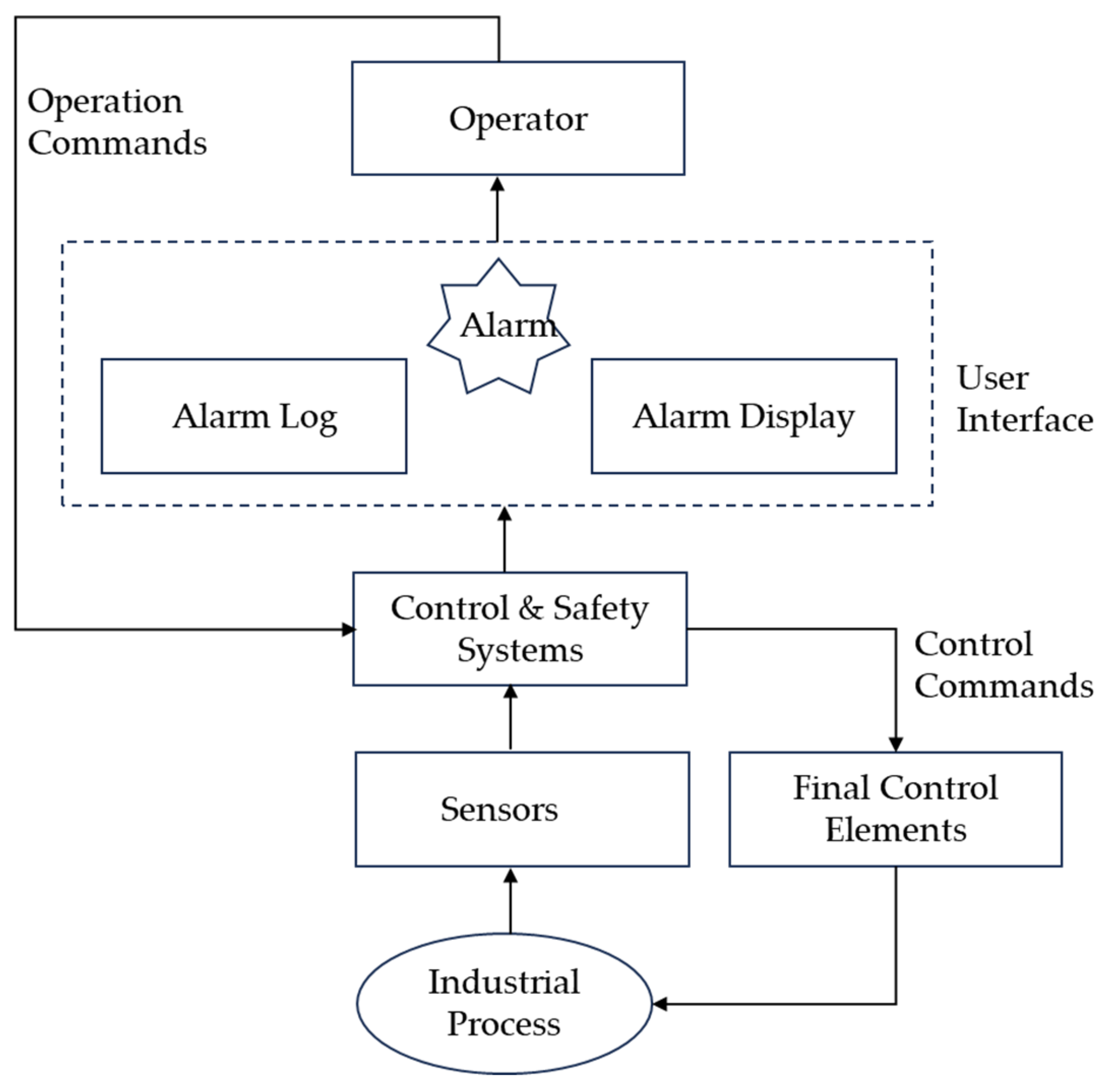
2.1. Preliminaries of Industrial Alarm System
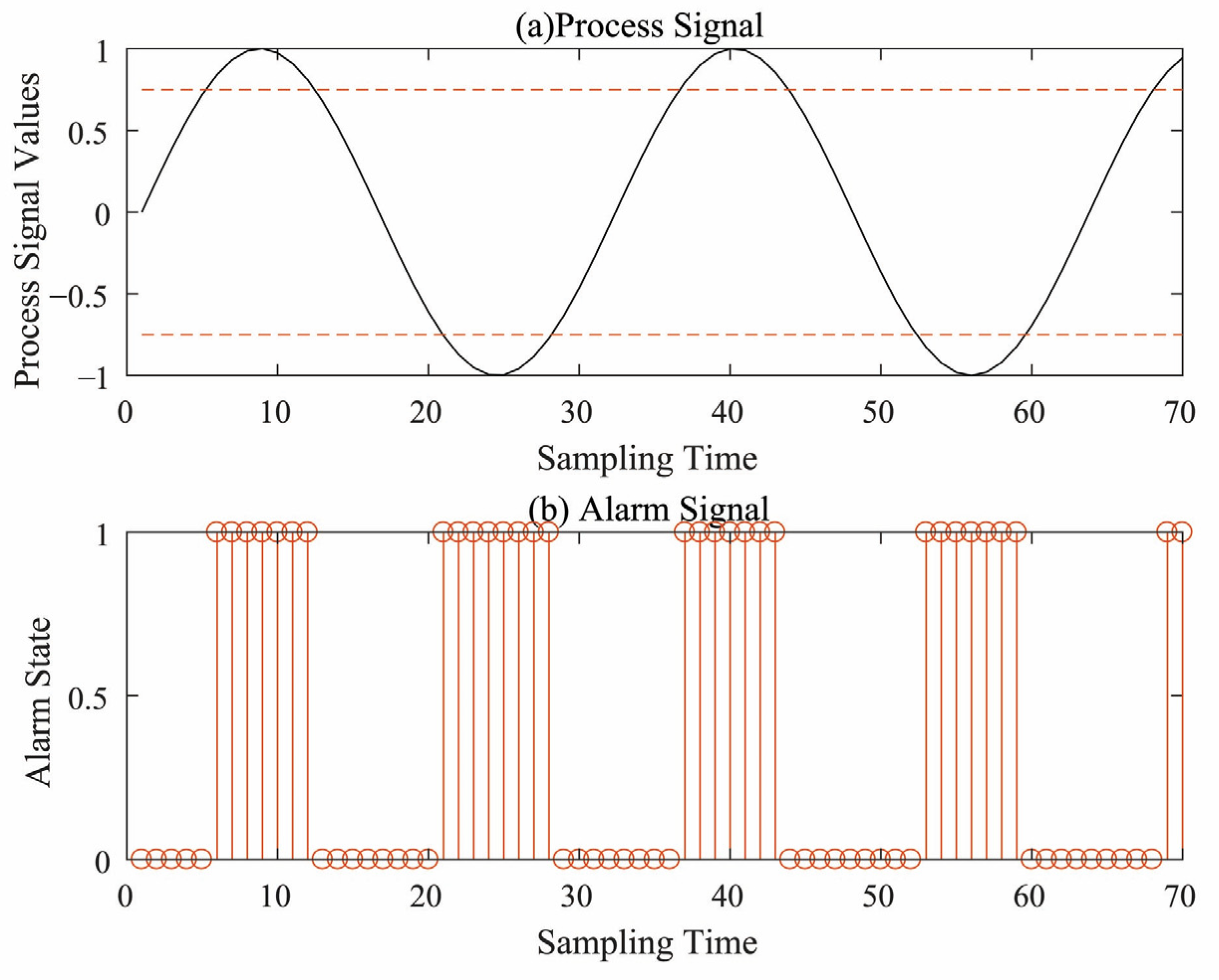
2.2. Introduction of Industrial Alarm Data
2.3. First-Out Alarm Detection Problem
3. Proposed Method for First-Out Alarm Detection
3.1. Alarm Association Rule Mining Based on FP-Growth and J-Measure
| Algorithm 1. FP-Growth algorithm to produce the set of frequent alarm itemsets |
| Input: Alarm database D; Support threshold s Output: Set of frequent alarm itemsets L |
|
- (1)
- In line 1, it scans the alarm database D once to generate a set of frequent items and calculate their supports, sort the items in a descending order based on their supports, and generate a list of frequent items .
- (2)
- In line 2, it creates the root node of FP-tree, labeled as “null”.
- (3)
- In lines 3–8, for each alarm sequence in the database D, conduct the following steps: ① Arrange the frequent items in the sequence according to the order in which they are listed, and denote the result of the arrangement as , where is the first item and is the list of remaining items; ② call insert_tree(, T); ③ if is not empty, recursively call insert_tree(B, N); procedure insert_tree([], T) is executed as follows: if T has children such that N.node-name = b; then the count of N is increased by 1; otherwise, a new node N is created with its node-name set to b, its node-count set to 1, and its node-parent linked to its parent node T, and link it to a node with the same node-name through the node-chain and node-link.
- (4)
- In line 9, all frequent itemsets are extracted from the alarm database D.
3.2. Determination of First-Out Alarm and Subsequent Alarms
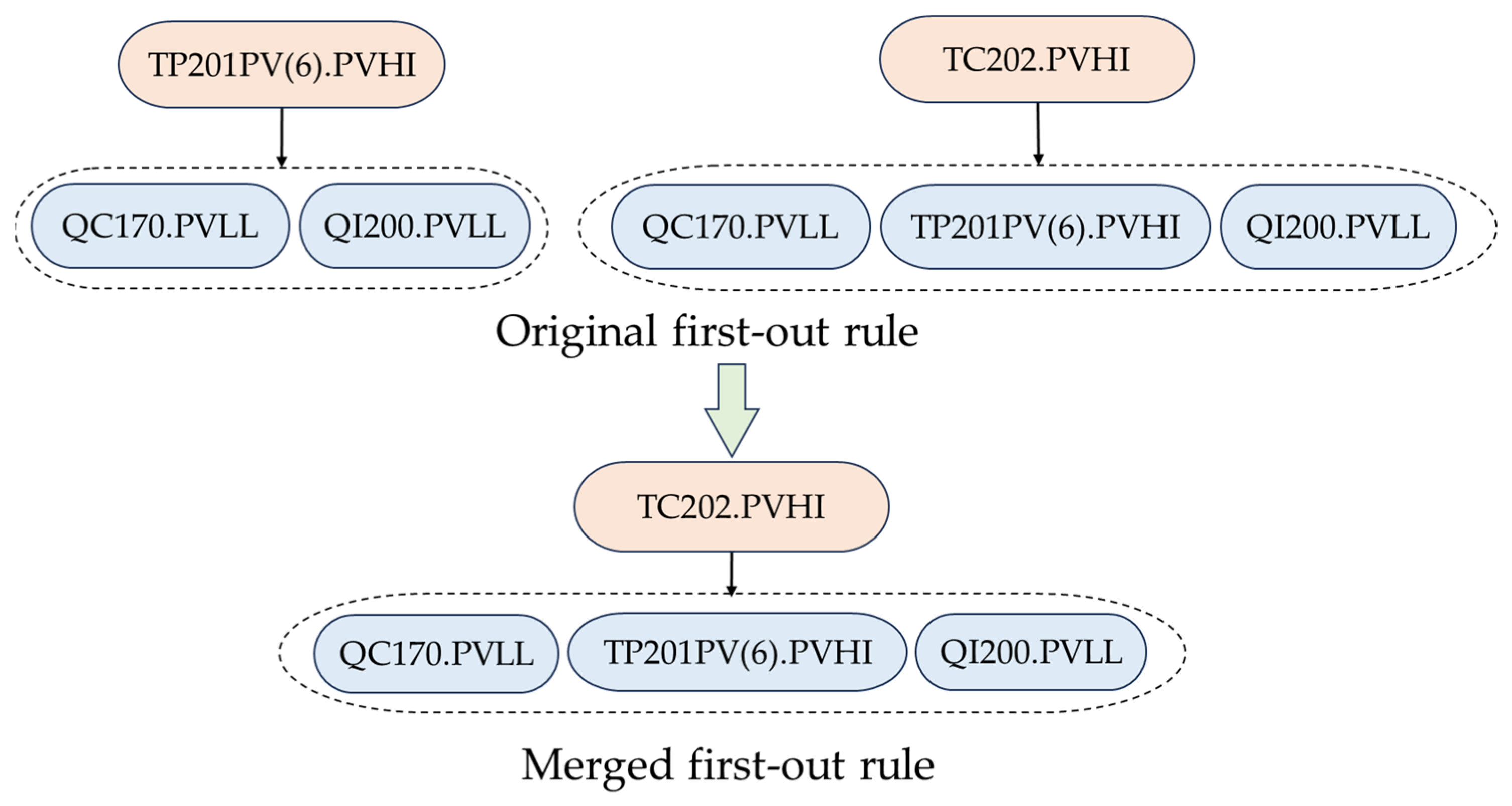
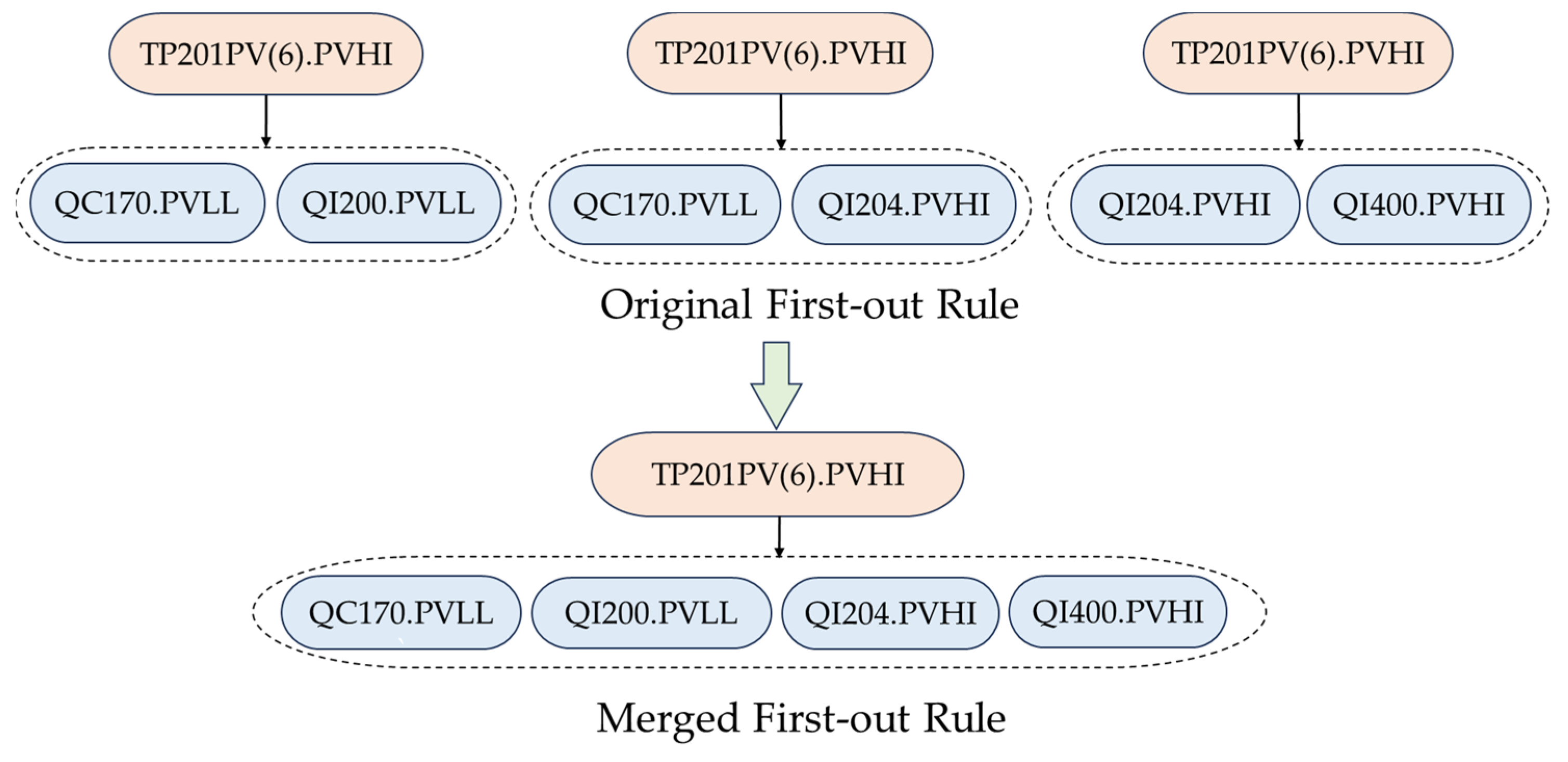
3.3. Screening and Consolidation of First-Out Rules
- (1)
- Scenario 1: Different alarms and are the first-out alarms of the same alarm set , i.e.,
- (2)
- Scenario 2: The first-out alarm is a subsequent alarm of another first-out alarm , i.e.,
- (3)
- Scenario 3: Alarm is the first alarm of different alarm sets and , but there exists an intersection of alarm sets and , i.e.,
- (1)
- In Scenario 1, it is known that , , , , . Thus, for , and . If implies and implies , then and are redundant, and only one rule should be retained. Otherwise, and are distinct rules, and should both be preserved. In this scenario, it should be checked whether and are redundant or not, which can be achieved through hypothesis test on .
- (2)
- In Scenario 2, it is known that , . Then, can be extended to , and thus we can obtain , and it needs to be determined whether to retain . If always occurs after , then one of the rules is duplicated and should be deleted. Otherwise, should be retained. In this scenario, it should be checked whether and hold a strong causal relation; as must follow as reflected by , , it is still necessary to check whether and are redundant.
- (3)
- In Scenario 3, it is known that , , . Let ; then it needs to be determined whether is valid. If occurs and also occurs, then the two first-out rules can be combined, i.e., . Otherwise, both and should be preserved. In this scenario, it should be checked whether all alarms in always appear together in historical sequences.
3.4. Discussions
- (1)
- The exploited data types are different. The data for alarm correlation analysis are binary alarm time series over a certain consecutive period. Regarding first-out alarm detection, the required data are essentially a collection of alarm sequences.
- (2)
- The objectives are different. The proposed method aims at identifying first-out alarms and exporting first-out rules, whereas existing alarm correlation analysis methods measure and export the correlations between alarms.
- (3)
- The principles are different. The detection of first-out alarms usually involves multiple alarms and requires alarm order information, while existing alarm correlation analysis methods only explore the correlation between two alarms and do not consider orders between alarm occurrences.
- (1)
- Time stamps of alarm events are key information. Inaccurate or inconsistent time stamps can lead to misinterpretations of the temporal order of alarms.
- (2)
- Noisy or incomplete historical data may hinder the ability to accurately assess and validate the first-out alarm detection method.
- (3)
- Transitioning the method from a testing environment to a real-time implementation may pose scalability challenges.
- (1)
- The data retrieval process can be optimized by using a database indexing system and leveraging efficient data structures such as hash tables or tree structures, to expedite the search for the earliest occurrences of each alarm.
- (2)
- Data pruning or filtering can be applied first to preprocess the alarm data and eliminate redundant information; thus the computational burden in the subsequent analysis can be reduced.
- (3)
- The detection task can be portioned into sub-tasks based on the units or groups that alarms belong to, and thus the proposed method can work efficiently for each sub-task.
4. Case Study
4.1. Experiment Preparation
- (1)
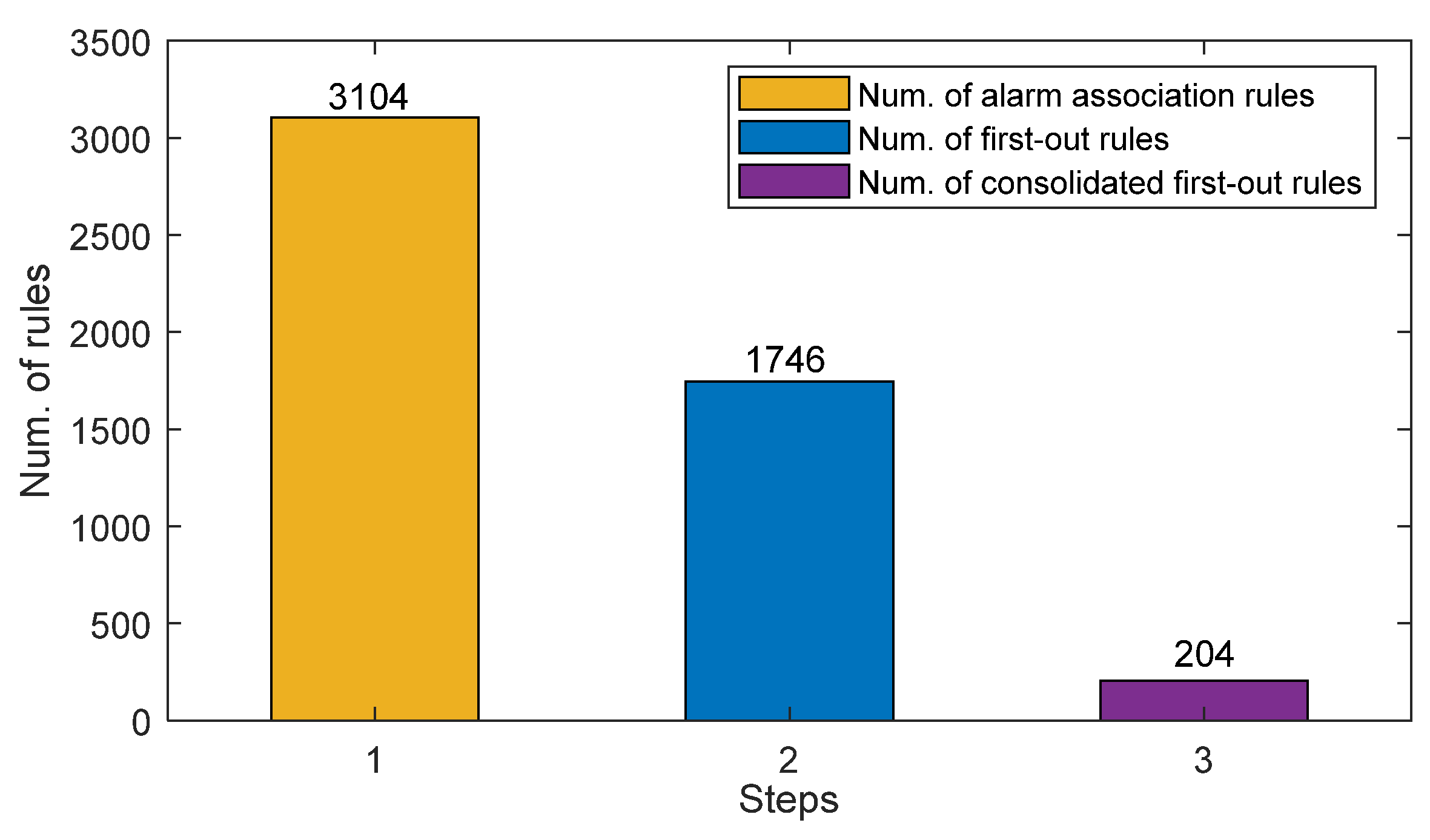
- The method in Section 3.1 was applied to extract alarm association rules. The minimum support degree and the minimum confidence level were set to 0.95 and 0.99, respectively. Initially, a total of 673,588 frequent patterns could be obtained. By keeping only closed alarm patterns and then identifying interesting association rules, 3104 rules were reserved from the historical alarm sequences.
- (2)
- The method in Section 3.2 was exploited to determine first-out rules. In the hypothesis test, the significance level was set to 0.05, and the corresponding threshold η was 3.84. The satisfaction rate threshold was set as 0.9. As a result, 1746 first-out rules were identified based on the interesting alarm association rules.
- (3)
- The method in Section 3.3 was utilized to screen and consolidate first-out rules, so as to reduce the redundancy in the results. Eventually, 204 consolidated first-out rules were received.
4.2. Scenario 1
4.3. Scenario 2
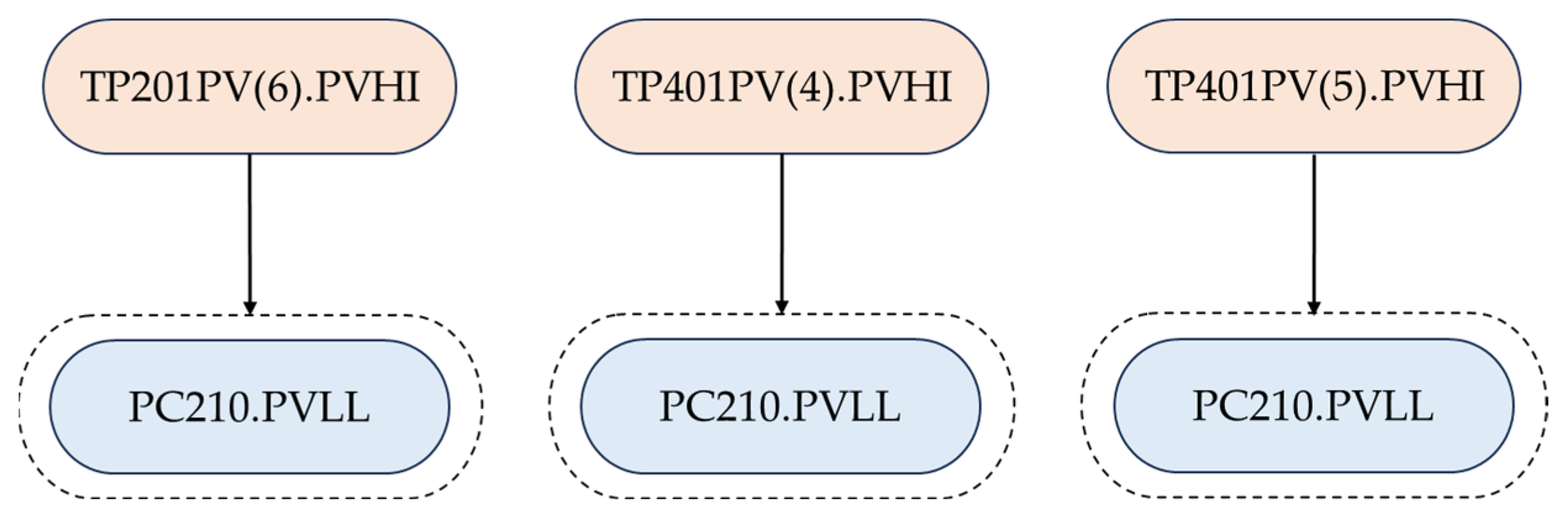
4.4. Scenario 3
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Goel, P.; Datta, A.; Mann, M.S. Industrial alarm systems: Challenges and opportunities. J. Loss Prev. Process Ind. 2017, 50, 23–36. [Google Scholar] [CrossRef]
- Wang, J.; Yang, F.; Chen, T. An overview of industrial alarm systems: Main causes for alarm overloading, research status, and open problems. IEEE Trans. Autom. Sci. Eng. 2016, 13, 1045–1061. [Google Scholar] [CrossRef]
- Rothenberg, D.H. Alarm Management for Process Control: A Best-Practice Guide for Design, Implementation, and Use of Industrial Alarm Systems; Momentum Press: New York, NY, USA, 2009. [Google Scholar]
- Noda, M.; Higuchi, F.; Takai, T.; Nishitani, H. Event correlation analysis for alarm system rationalization. Asia-Pac. J. Chem. Eng. 2011, 6, 497–502. [Google Scholar] [CrossRef]
- Yang, Z.; Wang, J.; Chen, T. Detection of correlated alarms based on similarity coefficients of binary data. IEEE Trans. Autom. Sci. Eng. 2013, 10, 1014–1025. [Google Scholar] [CrossRef]
- Kargaran, A.H.; Neshastegaran, A.; Izadi, I. Analytical derivation and comparison of alarm similarity analysis methods. IFAC-PapersOnLine 2021, 54, 360–365. [Google Scholar] [CrossRef]
- Yang, F.; Shah, S.L.; Xiao, D.; Chen, T. Improved correlation analysis and visualization of industrial alarm data. ISA Trans. 2012, 51, 499–506. [Google Scholar] [CrossRef]
- Hu, W.; Wang, J.; Chen, T. A new method to detect and quantify correlated alarms with occurrence delays. Comput. Chem. Eng. 2015, 80, 189–198. [Google Scholar] [CrossRef]
- Yang, B.; Li, J.; Li, H.; He, Y. Novel correlation analysis of alarms based on block matching similarities. Ind. Eng. Chem. Res. 2019, 58, 9465–9472. [Google Scholar] [CrossRef]
- Yang, B.; Wang, H.; Li, H.; He, Y. A novel detection of correlated alarms with delays based on improved block matching similarities. ISA Trans. 2020, 98, 393–402. [Google Scholar] [CrossRef]
- Li, T.; Tan, W.; Li, X. Data mining algorithm for correlation analysis of industrial alarms. Clust. Comput. 2019, 22, 10133–10143. [Google Scholar] [CrossRef]
- Yang, F.; Duan, P.; Shah, S.L.; Chen, T. Capturing Connectivity and Causality in Complex Industrial Processes; Springer Briefs in Applied Sciences and Technology; Springer: Berlin, Germany, 2014. [Google Scholar]
- Zhang, X.; Hu, W.; Yang, F. Detection of cause-effect relations based on information granulation and transfer entropy. Entropy 2022, 24, 212. [Google Scholar] [CrossRef] [PubMed]
- Hu, W.; Wang, J.; Chen, T.; Sirish, S. Cause-effect analysis of industrial alarm variables using transfer entropies. Control. Eng. Pract. 2017, 64, 205–214. [Google Scholar] [CrossRef]
- Su, J.; Wang, D.; Zhang, Y.; Yang, F.; Zhao, Y.; Pang, X. Capturing causality for fault diagnosis based on multi-valued alarm series using transfer entropy. Entropy 2017, 19, 663. [Google Scholar] [CrossRef]
- Otneim, H.; Berentsen, G.D.; Tjøstheim, D. Local lead–lag relationships and nonlinear granger causality: An empirical analysis. Entropy 2022, 24, 378. [Google Scholar] [CrossRef] [PubMed]
- Hu, W.; Wang, J.; Yang, F.; Han, B.; Wang, Z. Analysis of time-varying cause-effect relations based on qualitative trends and change amplitudes. Comput. Chem. Eng. 2022, 162, 107813. [Google Scholar] [CrossRef]
- Luo, Y.; Gopaluni, B.; Xu, Y.; Cao, L.; Zhu, Q.X. A novel approach to alarm causality analysis using active dynamic transfer entropy. Ind. Eng. Chem. Res. 2020, 59, 8661–8673. [Google Scholar] [CrossRef]
- de Abreu, R.S.; Nunes, Y.T.; Guede, L.A. A method for detecting causal relationships between industrial alarm variables using Transfer Entropy and K2 algorithm. J. Process Control 2021, 106, 142–154. [Google Scholar] [CrossRef]
- Folmer, J.; Schuricht, F.; Vogelheuser, B. Detection of temporal dependencies in alarm time series of industrial plants. IFAC Proc. Vol. 2014, 37, 7085–7090. [Google Scholar] [CrossRef]
- Wang, J.; Li, H.; Huang, J.; Su, C. A data similarity based analysis to consequential alarms of industrial processes. J. Loss Prev. Process Ind. 2015, 35, 29–34. [Google Scholar] [CrossRef]
- Wang, J.; Li, H.; Huang, J. Association rules mining based analysis of consequential alarm sequences in chemical processes. J. Loss Prev. Process Ind. 2016, 41, 178–185. [Google Scholar] [CrossRef]
- Hu, W.; Chen, T.; Shah, S.L. Discovering association rules of mode-dependent alarms from alarm and event logs. IEEE Trans. Control. Syst. Technol. 2018, 26, 971–983. [Google Scholar] [CrossRef]
- Zhou, B.; Hu, W.; Chen, T. Pattern extraction from industrial alarm flood sequences by a modified CloFAST algorithm. IEEE Trans. Ind. Inform. 2021, 18, 288–296. [Google Scholar] [CrossRef]
- ANSI/ISA-18.2; ANSI/ISA-18.2: Management of Alarm Systems for the Process Industries. ISA (International Society of Automation): Durham, NC, USA, 2016.
- Hu, W.; Chen, T. A data driven method to detect first-out alarms based on alarm occurrence events. In Proceedings of the 2019 CAA Symposium on Fault Detection, Supervision and Safety for Technical Processes (SAFEPROCESS), Xiamen, China, 5–7 July 2019; pp. 689–694. [Google Scholar]
- Gao, H.; Wei, C.; Huang, W.; Gao, X. Design of multivariate alarm trippoints for industrial processes based on causal model. Ind. Eng. Chem. Res. 2021, 60, 9128–9140. [Google Scholar] [CrossRef]
- Roohi, M.H.; Chen, T. Generalized moving variance filters for industrial alarm systems. J. Process Control 2020, 95, 75–85. [Google Scholar] [CrossRef]
- Kaced, R.; Kouadri, A.; Baiche, K. Designing alarm system using modified generalized delay-timer. J. Loss Prev. Process Ind. 2019, 61, 40–48. [Google Scholar] [CrossRef]
- Tulsyan, A.; Gopaluni, R.B. Univariate model-based deadband alarm design for nonlinear processes. Ind. Eng. Chem. Res. 2019, 58, 11295–11302. [Google Scholar] [CrossRef]
- Han, J.; Pei, J.; Yin, Y. Mining frequent patterns without candidate generation. ACM Sigmod Rec. 2000, 29, 1–12. [Google Scholar] [CrossRef]
- Wang, K.R.; Hu, W.; Chen, T. An efficient method to discover association rules of mode-dependent alarms based on the FP-growth algorithm. In Proceedings of the 2020 IEEE Electric Power and Energy Conference (EPEC), Edmonton, AB, Canada, 9–10 November 2020; pp. 1–5. [Google Scholar]
- Han, J.; Kamber, M.; Pei, J. Data Mining: Concepts and Techniques; No. 11082; Morgan Kaufmann Publishers: Burlington, MA, USA, 2012. [Google Scholar]
- Blanchard, J.; Guillet, F.; Gras, R.; Briand, H. Using information-theoretic measures to assess association rule interestingness. In Proceedings of the Fifth IEEE International Conference on Data Mining (ICDM’05), Houston, TX, USA, 27–30 November 2005; pp. 66–73. [Google Scholar]
- Smyth, P.; Goodman, R.M. An information theoretic approach to rule induction from databases. IEEE Trans. Knowl. Data Eng. 1992, 4, 301–316. [Google Scholar] [CrossRef]
- Machida, Y.; Ootakara, S.; Seki, H.; Hashimoto, Y.; Kano, M.; Miyake, Y.; Anzai, N.; Sawai, M.; Katsuno, T.; Omata, T. Vinyl Acetate Monomer (VAM) plant model: A new benchmark problem for control and operation study. IFAC-PapersOnLine 2016, 49, 533–538. [Google Scholar] [CrossRef]
- Zhu, L.; Cui, Y.; Takami, G.; Kanokogi, H.; Matsubara, T. Scalable reinforcement learning for plant-wide control of vinyl acetate monomer process. Control Eng. Pract. 2020, 97, 104331. [Google Scholar] [CrossRef]
- Yang, G.; Hu, W.; Cao, W.; Wu, M. Simulating industrial alarm systems by extending the public model of a vinyl acetate monomer process. In Proceedings of the 2020 39th Chinese Control Conference (CCC), Shenyang, China, 27–29 July 2020; pp. 6093–6098. [Google Scholar]
- Hu, W.; Yang, G.; Li, Y.; Cao, W.; Wu, M. Root cause identification of industrial alarm floods using word embedding and few-shot learning. IEEE Trans. Ind. Inform. 2023, 1–11. [Google Scholar] [CrossRef]




| No. | Alarm Tags | Time Stamps | Priority | Units |
|---|---|---|---|---|
| 1 | TC202.MVLO | 22 April 2022 10:37:04 | High | Reactor |
| 2 | TC202.SVHH | 22 April 2022 10:37:38 | Low | Reactor |
| 3 | TC150.MVLO | 22 April 2022 10:39:20 | High | Feedstock |
| 4 | TC150.MVLL | 22 April 2022 10:40:11 | Low | Feedstock |
| 5 | TP401PV(6).PVLO | 22 April 2022 10:40:34 | Low | Feedstock |
| 6 | TP401PV(6).PVHI | 22 April 2022 10:51:22 | Critical | Feedstock |
| 7 | TC410.PVHI | 22 April 2022 10:55:21 | Critical | Reactor |
| 8 | TP401PV(6).PVLO | 22 April 2022 11:03:34 | Low | Reactor |
| 9 | FC420.MVHH | 22 April 2022 11:06:31 | Low | Reactor |
| Method | Objective | Main Algorithms and Strategies | Type of Data Inputs | Detect Relations in Pair or Not | Consider Orders or Not |
|---|---|---|---|---|---|
| Proposed first-out alarm detection method | Identify first-out alarms and export first-out rules | Association rule mining, J-Measure, hypothesis test, and screening criteria | Sequences of alarm events | No | Yes |
| Alarm correlation analysis in [4,5] | Detect correlated alarms and calculate similarity coefficients | Cross-correlation function, Sorgenfrei and Jaccard coefficients | Binary valued alarm signals | Yes | No |
| Alarm correlation analysis in [7,8] | Detect correlated alarms and measure correlation levels | Gaussian kernel function, Pearson’s correlation coefficient, and estimation of correlation delay | Continuous valued pseudo alarm signals | Yes | No |
| Alarm correlation analysis in [9,10] | Detect correlated alarms and measure correlation levels | Cross-correlation function, partition of time sequences, matching of sequence blocks | Time-stamped alarm signals | Yes | No |
| Alarm correlation analysis in [11] | Detect correlated alarms and measure correlation levels | Calculation of conditional probabilities | Multi-alarm-state sequences | Yes | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, D.; Cheng, X. A First-Out Alarm Detection Method via Association Rule Mining and Correlation Analysis. Entropy 2024, 26, 30. https://doi.org/10.3390/e26010030
Li D, Cheng X. A First-Out Alarm Detection Method via Association Rule Mining and Correlation Analysis. Entropy. 2024; 26(1):30. https://doi.org/10.3390/e26010030
Chicago/Turabian StyleLi, Ding, and Xin Cheng. 2024. "A First-Out Alarm Detection Method via Association Rule Mining and Correlation Analysis" Entropy 26, no. 1: 30. https://doi.org/10.3390/e26010030
APA StyleLi, D., & Cheng, X. (2024). A First-Out Alarm Detection Method via Association Rule Mining and Correlation Analysis. Entropy, 26(1), 30. https://doi.org/10.3390/e26010030





