Abstract
Multi-party quantum private comparison (MQPC) assumes responsibility for overseeing the flow of data and communication among diverse entities, wherein it boasts powerful security capabilities that have garnered substantial attention. Most current MQPC protocols rely on difficult-to-prepare quantum states and are inefficient in their use of resources. In this paper, we propose a novel MQPC protocol without entanglement swapping, thereby building upon the assumption of an ideal channel. This protocol is based on Bell states, which simplifies implementation and addresses the challenges associated with using complex quantum states; it also enables the comparison of secret information by having a trusted party prepare and transmit encoded quantum sequences to participants, thereby facilitating efficient equality comparison among all parties. Our MQPC protocol showcased remarkable efficiency in comparison to existing protocols for quantum private comparison. Furthermore, the incorporation of decoy photon and shared key technologies made external and internal attacks ineffective, thereby ensuring the utmost security and integrity of the protocol.
1. Introduction
Secure multi-party computing (SMC) holds significant prominence within the realm of classical cryptography, with its origins in the millionaire problem that was first ever introduced by Yao [1] in 1982. This fascinating problem revolves around securely comparing the wealth of two wealthy individuals without revealing their actual fortunes. SMC assumes a pivotal role in preserving secrecy in diverse domains, thus encompassing clandestine bidding and auctions, confidential ballot elections, e-commerce, and private data analysis.
Nevertheless, the advent of quantum information processing technology in recent years has introduced vulnerabilities to classical SMC, which relies on complex mathematical puzzles. As a result, efforts have been made to extend SMC to the quantum realm, thereby aiming to address the security limitations inherent in classical SMC. In 1984, Bennett and Brassard [2] amalgamated the principles of quantum mechanics with classical cryptography, thus presenting the pioneering quantum cryptography protocol. Subsequently, a multitude of quantum cryptography protocols have been put forward, which encompass quantum secret sharing (QSS) [3,4], quantum key distribution (QKD) [2,5,6,7,8,9,10], quantum private query (QPQ) [11,12], quantum-secure direct communication (QSDC) [13,14], and various others.
QKD is a quantum communication protocol that is used for key distribution, where the quantum states of qubits are employed to transmit the keys. It can detect any eavesdropping or interference in the key transmission to ensure the security of the keys. To detect the presence of eavesdroppers, QKD introduces the concept of decoy states [15,16,17]. This is a special quantum bit state that is injected into the communication channel during transmission and is mixed with the transmitted key bits. If an eavesdropper attempts to interfere with the communication and measures the transmitted quantum bits, they inevitably affect the state of the decoy state. Therefore, decoy photon technology is often used to ensure the security of key distribution.
By employing QKD for secure quantum key distribution, quantum secure multi-party computing (QSMC) enables confidential communication among multiple users while providing efficient multi-plexing capabilities.
The quantum privacy comparison protocol (QPC), which is a prominent component of the QSMC protocol, has garnered significant interest. Its primary goal is to determine the equality of confidential values among participants while preserving the secrecy of the information. The groundbreaking QPC protocol introduced by Yang and Wen [18] has greatly facilitated various QPC protocols that utilize different quantum states as resources, including protocols based on single photons [19], Bell states [20,21,22], GHZ states [23,24], and multi-particle entangled states [25,26,27], among others. However, it is always necessary to perform the protocol several times when comparing the secret information of multiple participants when using two-party QPC protocols. To address this limitation, Chang et al. [28] proposed the original Multi-Party Quantum Private Comparison Protocol (MQPC) in 2013, thereby enabling the comparison of several secret information in a single execution. This protocol employed an n-particle GHZ state and facilitated the comparison of secret information among n participants. Since then, significant research efforts have been dedicated to advancing the MQPC.
In 2016, Ye [29] introduced an MQPC protocol that utilized the entanglement swapping of Bell-entangled states. The following year, Ji and Ye [30] proposed another MQPC protocol that employed the entanglement swapping of d-level cat states and d-level Bell states. Later in 2019, Ye [31] presented an MQPC protocol that utilizes single-particle states with multiple levels. It is evident from this analysis that most existing MQPC protocols rely on entangled states of n particles or d-level systems. However, the preparation and measurement of d-level systems and n-particle-entangled states remain challenging within current quantum technologies. These proposed solutions are currently only theoretically feasible and require significant advancements in quantum technology for their practical implementation. Another issue arises from the inefficiency of the existing MQPC protocols, thus resulting in sub-optimal utilization of the quantum resources and significant wastage.
To address the aforementioned concerns, we have developed an MQPC protocol that utilizes the Bell state as the foundational quantum resource. This protocol effectively simplifies the implementation process by tackling the challenge of using complex quantum states to achieve the comparisons across n participants. Additionally, it demonstrated superior quantum efficiency when compared to most existing MQPC protocols.
The remaining portion of this manuscript is well-structured, with the proposed protocol as the central focus. In Section 2, the fundamental concepts involved are introduced. Section 3 provides a detailed description of the protocol, including an analysis of its accuracy, and, in Section 4, the security of it is analyzed. In Section 5, a comparison is made between the proposed protocol and several other protocols that utilize the TP. Ultimately, Section 6 provides a summary and concludes the paper.
2. Background
The Bell states, as denoted in Equation (1):
The given values constitute a pair of entangled states involving two particles exhibiting maximal entanglement. Furthermore, they serve as a comprehensive and mutually perpendicular basis within a four-dimensional Hilbert space. In this paper, the Bell state was adopted as a quantum carrier.
The entanglement of the two particles in the Bell state signifies that the application of a unitary operation on an individual particle within the Bell state will invariably bring about a modification in the other particle. We have four unitary operations available—X, Y, Z, and I—which are defined as follows:
When any one of the operations I, X, Y, or Z is applied to the first particle of a given Bell state, it induces a transformation that manifests in two Bell states. The inter-relationship governing this transformation is elucidated in Table 1.

Table 1.
Transformation relation.
Using the above Equation (2), the iterative results of the unitary operations and I are shown in Table 2.

Table 2.
Unitary operation rule.
3. The Proposed Scheme
3.1. Prerequisites
The proposed protocol was conducted under the ideal condition of noiselessness. Prior to presenting this protocol, it is necessary to outline its prerequisites in the following:
- Let represent n parties holding different private information , respectively, where . Being aided by a semi-honest TP, their primary aim is to determine if their respective secrets bear resemblance. The TP is allowed to exert effort in recognizing the content of the participants’ secrets, but it is prohibited from colluding with others.
- is divided into sets in which each consists of two bits: . In the case where L mod , the last set is padded with 0 for completeness.
- Through the implementation of a multi-party QKD [32], two types of key sequences, denoted as and , are generated. In particular, serves as the secret key shared among all participants , while signifies the key that is mutually shared between the TP and :where, , .
- In this paper, the quantum carrier is taken as Bell state
3.2. Protocol Steps
The proposed MQPC protocol will be comprehensively explained in this section.
Step 1
The TP prepares a total of quantum states by selecting from the set . These states are used to construct n sequences of quantum states denoted that are as . can be expressed as follows:
in which the superscripts indicate the position of the Bell state in the . Furthermore, the indices distinguish the different particles within each Bell state.
Subsequently, two new sequences are formed by extracting out the first and second particles of each Bell state, respectively:
For each , one advances in a sequential manner by executing Step 2, Step 3, and Step 4 successively.
Step 2
The TP generates n decoy sets, each consisting of elements from a basis set , where:
These decoy sets are then inserted randomly by the TP into the sequence , thereby resulting in a new sequence that is identified as the . The TP subsequently transmits the modified sequence to the participant in order to effectively detect any potential eavesdropping.
Once it is verified that the has received all the particles of the , the TP continues to verify that the transmissions from the to the were secure through several steps. Firstly, the TP informs the about the location and preparation basis of the decoy photons in the . The then measures the decoy photons and feeds back the results to the TP. Finally, the TP compares the measurements with the initial state to calculate the error ratio. If the error ratio is above a predefined threshold level, the communication will be halted, and the protocol procedure will be reset. Otherwise, the will discard the decoy photons in the to resume the , and the protocol advances to the next step.
Step 3
The utilizes the shared keys and to encrypt the confidential information through an exclusive OR operation, thereby yielding .
In adherence to the coding regulations outlined in Table 3, the chooses a unitary operation based on the value of the , which is denoted as , which is applied on the jth particles of the . This modification affects the states of the particles in the , thereby resulting in a transformed sequence that is labeled as .

Table 3.
The coding rule.
Subsequently, the inserts a collection of decoy photons, each belonging to the basis sets , into various positions of the transformed sequence . This construction forms a novel sequence that is identified as .
Finally, the transmits the sequence to , with particular emphasis on the fact that will be sending to .
Step 4
Upon confirming ’s reception of all the particles, the proceeds to verify the security of transmitting to through a procedure that is similar to Step 2. If the ratio surpasses the pre-determined threshold level, the communication will be terminated, and the protocol procedure will be restarted. Otherwise, the communication will continue.
The then removes the decoy photons in the to restore the original form of the . Subsequently, the unitary operation , which is determined by and the mapping rules in Table 3, is applied to the jth particles of the , thereby transforming into .
For utmost security, the prepares a set of decoy photons consisting of elements from the basis sets randomly. These decoy photons are then inserted randomly into the , thereby creating a new sequence called . Finally, the transmits the to the TP.
Step 5
Upon authenticating the TP’s reception of all the particles, the verifies the security of transmitting the to the TP, thus following a similar procedure as the describe in Step 2. If the ratio surpasses a pre-defined threshold, the transmission will be halted, and the protocol procedure will be reset. Otherwise, the communication will persist uninterrupted.
The TP discards the decoy photons within the and restores the sequence as . Next, it selects the unitary operation that is determined by the value of and the rules presented in Table 3, and applies it to the jth particles of the . Consequently, the sequence undergoes transformation into .
Subsequently, the particles in both the and sequences are subjected to Bell basis measurement. By comparing the measurement results of each Bell state to the initially prepared states, the TP can verify if any changes have occurred: if the measurements align perfectly with the primary states, the TP will declare that are all equal; if those results differ from the initial states, the TP will announce that are not all equal.
For the sake of clarity, a flowchart representing the entire protocol can be found in Figure 1.
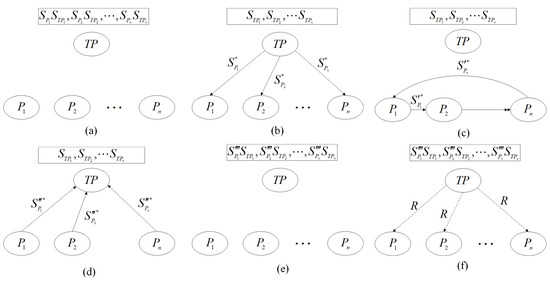
Figure 1.
The proposed protocol process is depicted in a simple flow chart, where quantum channels are represented by solid arrow lines, classical channels by dashed arrow lines, and multiple transmissions by double arrows. To maintain clarity, we exclude any considerations regarding external eavesdropping and eavesdropping inspection steps. (a) TP-prepared n sets of quantum states sequences and each separated into two sequences and . (b) TP transmits the sequence to while retaining the sequence . (c) delivers the unitary operation sequences to . (d) delivers the unitary operation sequences to TP. (e) The TP performs a unitary operation on the sequence , thus resulting in a modified sequence denoted as . (f) Bell basis measurement is employed to measure the sequences and , followed by the comparison of the obtained measurements against the to determine the comparative result R. R is then declared.
3.3. Correctness
In the aforementioned steps, all the examine the equality of their private information with the cooperation of the TP. During Step 5, the TP scrutinizes the measurements in relation to the original records to determine if the secrets are indeed identical. The confirmation of their identity takes place when the measurements align, whereas any disparities in the measurements indicate non-identity.
We present the validity of the proposed protocol through the following details. Let us consider the jth particle in . After all the parties of the complete the unitary operations of the presented protocol on the initial particle , its state is transformed to the following form:
Upon referring to Table 2 and Table 3, we observe that the unitary operations and adhere to the commutative law:
By substituting and into Equation (5), we conclude the following:
In Step 5, the TP performs the unitary operation on the jth particle. According to Equation (6),
is derived, thereby confirming the validity of Equation (4). It allows the TP to determine the participants’ secret equality by comparing measurements with the initial state. If , the initial state matches the measured state, thereby indicating correctness, while a disparity signifies a difference. Thus, the presented protocol functions correctly in enabling the TP to easily ascertain the equality of all the participants’ secrets.
4. Security Analysis
We undertake an analysis of the security aspects pertaining to the proposed protocol in this section. Firstly, we state that any external attacks directed at the protocol are rendered ineffectual. Secondly, it becomes evident that participants, whether individually or in a group of , are unaware of the confidential information held by other parties. Finally, the TP has the authority to disclose comparison outcomes, but it cannot access to any confidential information from other participants. As a result, this protocol guarantees privacy while facilitating the comparison of the secret equality among participants.
4.1. Outsider Attack
The potential of an external eavesdropper named Eve to gain the confidential information of n parties is the central focus of this comprehensive analysis. It is worth noting that the assumed security in our QKD technique effectively prevents Eve from accessing the shared keys.
Our protocol effectively eliminates Eve’s opportunity to launch an attack in Step 1, which does not involve any qubit transmissions. However, Steps 2, 3, and 4 comprise qubit transmission over the quantum channel that Eve could take advantage of to gather the secrets of n parties. Such attacks might involve the intercept-resend attack, the measure-resend attack, the entangle-measure attack, or related standard methods. Nevertheless, our proposed protocol incorporates the use of decoy photon technology, thereby guaranteeing the security of the quantum transmission. This technique is a variation of the eavesdropping detection method employed in the BB84 quantum key distribution protocol [2], which has been mathematically proven to have unconditional security [33].
In Step 5, our protocol effectively neutralizes Eve’s ability to launch any attacks while processing the information locally. As a result, the external eavesdropper can only acquire knowledge of the comparison result, thereby making her pursuit to acquire the secrets of the entirely futile.
While this protocol is formulated based on the ideal scenario, noise remains an inevitable factor in quantum systems. In practical quantum noise channels, the noise present in the quantum channels may potentially affect the particles, thus leading to quantum bit errors. Error suppression techniques, such as dynamic decoherence suppression, can effectively alleviate the impact of noise on the quantum bits, thereby reducing the overall transmission error rate. Additionally, quantum error-correcting codes are beneficial for detecting and correcting errors in the quantum bits during transmission. Hence, by integrating error suppression techniques and quantum error-correcting codes, we can ensure the robustness and security of this protocol in noisy environments.
To conclude, we confidently assert that the presented protocol has undergone a thorough analysis and incorporates measures at each step to mitigate vulnerabilities, thereby ensuring its resilience to external attacks.
4.2. Insider Attack
In their 2007 study, Gao et al. [34] proposed that attacks originating from participants who are actively engaged in implementing a protocol could pose a substantial threat regarding security. This raises the crucial question of whether the protocol under scrutiny possesses the ability to withstand internal attacks.
Case 1: Individual Attacks of Participants
Considering the possibility of a malicious participant, denoted as , who aims to access others’ secrets, it is imperative to contemplate any potential attacks that may transpire during the transmission of the particles across the quantum channel. Nevertheless, any efforts by the to intercept these particles will undoubtedly trigger detection by the eavesdropping check processes, as such attacks are bound to leave discernible traces on the decoy photons.
Another avenue through which the could attempt to obtain confidential information is by analyzing the sequence of the quantum states within his or her possession. Although the may possess knowledge of the during Step 4, this knowledge alone is inadequate for extracting the ’s secret. This limitation arises from the fact that the lacks access to the shared key or the initial Bell state that is prepared by the TP.
Therefore, the evidence suggests that dishonest participants, such as the , are effectively prevented from acquiring the secrets of others.
Case 2: Conspiracy Attack Among Participants
Our primary focus is directed toward the most extreme scenario, where a group of dishonest parties conspires to obtain the secret held by a single user, thus excluding all other participants. This specific case represents the greatest threat to the overall agreement.
To provide clarity, let us consider a hypothetical situation where the dishonest parties, which are referred to as , collaborate with the intention of stealing the secret belonging to the user .
In order to access the secret information, these parties would need to obtain two separate values: and . While the serves as a shared key among all participants, dishonest parties may be aware of its existence. However, their knowledge is restricted to the alone, as they do not have access to the specific key that is exclusively shared between the user and the TP; thus a trusted third party is renowned for its impartiality and non-collusion with other participants.
Consequently, we can confidently assert that the malevolent parties, comprising , are rendered futile in their attempt to pilfer the secret belonging to the user .
Case 3: Attacks From the TP
The initial requirement of our protocol mandates the TP to act as a semi-honest third party. The TP’s role is to make every effort to gain access to the participants’ confidential data while ensuring that they do not engage in any collusion with either party.
Suppose a suppositional scenario where the TP covertly attempts to obtain a ’s secret with hidden motives and surprisingly manages to acquire the from the undetected. Nevertheless, despite having access to the obtained by measuring the , the TP lacks the necessary knowledge to deduce the true secret belonging to the due to the encryption method utilized for the , which is encrypted by both the and . Moreover, any bold attempt by the TP to intercept the particles transmitted via the quantum channel would promptly trigger a vigilant array of detection mechanisms, thereby definitively revealing the TP as an external attacker.
Consequently, the proposed protocol successfully foils the TP’s malicious intentions, thus ensuring the unwavering integrity and security of the system.
5. Comparison
Currently, a few protocols exist that intend to bolster security and broaden the functionalities of multi-party quantum computation by diminishing or eliminating reliance on the trusted TP. Nevertheless, in most MQPC protocols, the TP is still employed, especially when a dependable quantum-secure communication channel is unavailable or unworkable. Consequently, our comparison is constrained to protocols that incorporate the involvement of the TP in the latter scenario.
A comparative analysis was conducted on various existing MQPC protocols that employ quantum carriers such as Bell states and other quantum states. The comprehensive findings of this analysis are available in Table 4 and Table 5. In this evaluation, the efficiency of the qubits is denoted as and shown in Equation (7):
where represents the classical bits consumed in comparison, and denotes the total particles consumed during each comparison phase. Notably, our assessment did not consider the decoy photons and keys produced by QKD.

Table 4.
Comparison with the other protocols based on Bell states.

Table 5.
The comparison of the presented protocol with respect to the other protocols.
The proposed protocol demonstrates several advantages compared to the existing MQPC protocols. By incorporating the protocols listed in Table 4, our approach utilizes the Bell state as quantum carriers and presents significant enhancements over the current MQPC protocols. One notable advantage is its superior quantum efficiency, which becomes evident upon examining Table 4. Our protocol achieves twice the qubit efficiency of Refs. [35,36], and achieves three times the efficiency of Ref. [30]. Moreover, our protocol surpasses the quantum resources and measurement capabilities of Refs. [30,36]. This superiority stems from the simplicity with respect to preparing and measuring two-level Bell states, as opposed to the more intricate procedures involved in preparing and measuring d-level Bell-entangled states. Additionally, it is worth noting that the comparison between the MQPC protocols relies on different quantum technologies. While both Refs. [30,36] utilized quantum entanglement swapping and unitary operations, our protocol exclusively relies on unitary operations.
We also compared our presented protocol with protocols involving multi-particle entangled states [37,38] and d-level systems [31,39]. The comparison results are shown in Table 5. It can be inferred that using Bell states as quantum resources to some extent makes the MQPC protocol feasible. These quantum states can be generated without expensive equipment and complex methods, thereby allowing for a high efficiency and low cost. On the other hand, the preparation and measurement of n-particle-entangled states and d-level systems may still be challenging with current quantum technologies. Fortunately, our proposed protocol only requires Bell-entangled states and unitary operations on single particles, and these techniques have been successfully demonstrated in experiments [40,41]. In contrast to Refs. [30,31,36,37,38,39], our protocol is based on two-dimensional photons instead of d-dimensional photons and n-particle-entangled states. This fundamental difference makes our protocol more feasible and practical.
6. Conclusions
In conclusion, based on the noiseless conditions, we have devised an innovative MQPC protocol that leverages Bell states, thereby eliminating the need for entanglement swapping. This groundbreaking protocol allows for the secure comparison of secrets among multiple participants within a single execution. By using decoy photons to prevent eavesdropping, encrypting the secrets of participants with shared keys, and employing a sequence of four unitary operations to encode the information into quantum states, our protocol guarantees robust security.
Extensive analysis and scrutiny have unequivocally validated the impervious nature of this protocol against both external and internal attacks. Moreover, our protocol presents noteworthy advantages over its predecessors in the realm of MQPC protocols, particularly concerning the quantum state preparation and overall efficiency. Another salient aspect worth mentioning is that the proposed protocol can be readily implemented by employing existing quantum technologies.
Author Contributions
Conceptualization, J.W. and L.G.; methodology, W.W.; validation, J.W., L.G. and W.W.; formal analysis J.W.; investigation, L.G.; resources, J.W. and L.G.; data curation, W.W. and J.W.; writing—original draft preparation, J.W.; writing—review and editing, W.W., L.G. and W.W.; visualization, L.G.; supervision, W.W.; project administration, W.W.; funding acquisition, W.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Science and Technology Research Project of Hebei Higher Education No. ZD2021011.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The manuscript has no associated data.
Conflicts of Interest
All authors have no conflict of interest—neither financial or otherwise.
References
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (sfcs 1982), Chicago, IL, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. arXiv 2020, arXiv:2003.06557. [Google Scholar] [CrossRef]
- Liao, Q.; Liu, H.; Zhu, L.; Guo, Y. Quantum secret sharing using discretely modulated coherent states. Phys. Rev. A 2021, 103, 032410. [Google Scholar] [CrossRef]
- Zhou, Y.; Yu, J.; Yan, Z.; Jia, X.; Zhang, J.; Xie, C.; Peng, K. Quantum secret sharing among four players using multipartite bound entanglement of an optical field. Phys. Rev. Lett. 2018, 121, 150502. [Google Scholar] [CrossRef] [PubMed]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Wang, X.B.; Yu, Z.W.; Hu, X.L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 2018, 98, 062323. [Google Scholar] [CrossRef]
- Chen, J.P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.; Hu, X.L.; Guan, J.Y.; Yu, Z.W.; Xu, H.; Lin, J.; et al. Sending-or-not-sending with independent lasers: Secure twin-field quantum key distribution over 509 km. Phys. Rev. Lett. 2020, 124, 070501. [Google Scholar] [CrossRef]
- Lu, Y.F.; Wang, Y.; Jiang, M.S.; Zhang, X.X.; Liu, F.; Li, H.W.; Zhou, C.; Tang, S.B.; Wang, J.Y.; Bao, W.S. Sending or Not-Sending Twin-Field Quantum Key Distribution with Flawed and Leaky Sources. Entropy 2021, 23, 1103. [Google Scholar] [CrossRef]
- Jiang, C.; Yu, Z.W.; Hu, X.L.; Wang, X.B. Robust twin-field quantum key distribution through sending or not sending. Natl. Sci. Rev. 2023, 10, nwac186. [Google Scholar] [CrossRef]
- Gao, F.; Qin, S.; Huang, W.; Wen, Q. Quantum private query: A new kind of practical quantum cryptographic protocol. Sci. China Phys. Mech. Astron. 2019, 62, 70301. [Google Scholar] [CrossRef]
- Liu, B.; Gao, F.; Huang, W.; Wen, Q. QKD-based quantum private query without a failure probability. Sci. China Phys. Mech. Astron. 2015, 58, 100301. [Google Scholar] [CrossRef]
- Qi, R.; Sun, Z.; Lin, Z.; Niu, P.; Hao, W.; Song, L.; Huang, Q.; Gao, J.; Yin, L.; Long, G.L. Implementation and security analysis of practical quantum secure direct communication. Light Sci. Appl. 2019, 8, 22. [Google Scholar] [CrossRef] [PubMed]
- Wang, C.; Deng, F.G.; Li, Y.S.; Liu, X.S.; Long, G.L. Quantum secure direct communication with high-dimension quantum superdense coding. Phys. Rev. A 2005, 71, 044305. [Google Scholar] [CrossRef]
- Lo, H.K.; Ma, X.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhao, Q.; Razavi, M.; Ma, X. Improved key-rate bounds for practical decoy-state quantum-key-distribution systems. Phys. Rev. A 2017, 95, 012333. [Google Scholar] [CrossRef]
- Liu, B.; Xia, S.; Xiao, D.; Huang, W.; Xu, B.; Li, Y. Decoy-state method for quantum-key-distribution-based quantum private query. Sci. China Phys. Mech. Astron. 2022, 65, 240312. [Google Scholar] [CrossRef]
- Yang, Y.G.; Wen, Q.Y. An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 2009, 42, 055305. [Google Scholar] [CrossRef]
- Wu, W.; Zhou, G.; Zhao, Y.; Zhang, H. New quantum private comparison protocol without a third Party. Int. J. Theor. Phys. 2020, 59, 1866–1875. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.B.; Chang, Y.; Hou, M.; Cheng, W. Efficient Quantum Private Comparison Based on Entanglement Swapping of Bell States. Int. J. Theor. Phys. 2021, 60, 3783–3796. [Google Scholar] [CrossRef]
- Wu, W.; Zhang, H. Cryptanalysis of Zhang et al’s Quantum Private Comparison and the Improvement. Int. J. Theor. Phys. 2019, 58, 1892–1900. [Google Scholar] [CrossRef]
- Wu, W.; Ma, X. Quantum private comparison protocol without a third party. Int. J. Theor. Phys. 2020, 59, 1854–1865. [Google Scholar] [CrossRef]
- Lang, Y.F. Quantum private comparison without classical computation. Int. J. Theor. Phys. 2020, 59, 2984–2992. [Google Scholar] [CrossRef]
- Xu, Q.D.; Chen, H.Y.; Gong, L.H.; Zhou, N.R. Quantum private comparison protocol based on Four-Particle GHZ States. Int. J. Theor. Phys. 2020, 59, 1798–1806. [Google Scholar] [CrossRef]
- Ji, Z.; Zhang, H.; Wang, H. Quantum private comparison protocols with a number of multi-particle entangled states. IEEE Access 2019, 7, 44613–44621. [Google Scholar] [CrossRef]
- Ji, Z.X.; Ye, T.Y. Quantum private comparison of equal information based on highly entangled six-qubit genuine state. Commun. Theor. Phys. 2016, 65, 711. [Google Scholar] [CrossRef]
- Ye, T.Y.; Ji, Z.X. Two-party quantum private comparison with five-qubit entangled states. Int. J. Theor. Phys. 2017, 56, 1517–1529. [Google Scholar] [CrossRef]
- Chang, Y.J.; Tsai, C.W.; Hwang, T. Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 2013, 12, 1077–1088. [Google Scholar] [CrossRef]
- Ye, T.Y. Multi-party quantum private comparison protocol based on entanglement swapping of Bell entangled states. Commun. Theor. Phys. 2016, 66, 280. [Google Scholar] [CrossRef]
- Ji, Z.-X.; Ye, T.-Y. Multi-party quantum private comparison based on the entanglement swapping of d-level cat states and d-level Bell states. Quantum Inf. Process. 2017, 16, 177. [Google Scholar]
- Ye, C.-Q.; Ye, T.-Y. Circular multi-party quantum private comparison with n-level single-particle states. Int. J. Theor. Phys. 2019, 58, 1282–1294. [Google Scholar]
- Zhang, Z.J.; Man, Z.X.; Shi, S.H. An efficient multiparty quantum key distribution scheme. Int. J. Quantum Inf. 2005, 3, 555–560. [Google Scholar] [CrossRef]
- Shor, P.W.; Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 2000, 85, 441. [Google Scholar] [CrossRef] [PubMed]
- Gao, F.; Qin, S.J.; Wen, Q.Y.; Zhu, F.C. A simple participant attack on the brádler-dušek protocol. Quantum Inf. Comput. 2007, 7, 329–334. [Google Scholar] [CrossRef]
- Ye, T.; Ji, Z. Multi-user quantum private comparison with scattered preparation and one-way convergent transmission of quantum states. Sci. China Phys. Mech. Astron. 2017, 60, 090312. [Google Scholar] [CrossRef]
- Ye, T.Y.; Hu, J.L. Multi-Party Quantum Private Comparison Based on Entanglement Swapping of Bell Entangled States within d-Level Quantum System. Int. J. Theor. Phys. 2021, 60, 1471–1480. [Google Scholar] [CrossRef]
- Huang, S.L.; Hwang, T.; Gope, P. Multi-party quantum private comparison protocol with an almost-dishonest third party using GHZ states. Int. J. Theor. Phys. 2016, 55, 2969–2976. [Google Scholar] [CrossRef]
- Zhou, M.K. Robust multi-party quantum private comparison protocols against the collective noise based on three-qubit entangled states. Int. J. Theor. Phys. 2018, 57, 2931–2937. [Google Scholar] [CrossRef]
- Du, G.; Zhang, F.; Ma, C. A new multi-party quantum private comparison protocol based on circle model. Int. J. Theor. Phys. 2019, 58, 3225–3233. [Google Scholar] [CrossRef]
- Kwiat, P.G.; Mattle, K.; Weinfurter, H.; Zeilinger, A.; Sergienko, A.V.; Shih, Y. New high-intensity source of polarization-entangled photon pairs. Phys. Rev. Lett. 1995, 75, 4337. [Google Scholar] [CrossRef]
- Dong, D.; Yan, F.-L. Quantum nondemolition measurement of two-photon Bell-state and three-photon Greenberger-Horne-Zeilinger-state based on weak nonlinearities. Acta Phys. Sin. 2013, 62, 100304. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).