Abstract
Due to the equivalent keys revealed by a chosen-plaintext attack or a chosen-ciphertext attack, most of the existing chaotic image encryption schemes are demonstrated to be insecure. In order to improve security performance, some scholars have recently proposed the plaintext-related chaotic image encryption scheme. Although the equivalent effect of a one-time pad is achieved, an additional secure channel is required to transmit the hash values or other parameters related to the plaintext before the ciphertext can be decrypted at the receiving end. Its main drawback is that an absolutely secure channel is needed to transmit the information related to the plaintext, which is not feasible in practical applications. To further solve this problem, this paper proposes a chaotic image encryption scheme based on global dynamic selection of a multi-parallel structure. First, a chaotic sequence is employed to dynamically select DNA encoding rules. Secondly, the permutation with a multi-parallel structure is performed on the DNA-encoded matrix, and the DNA decoding rules are dynamically selected according to another chaotic sequence. Finally, the diffusion rules obtained by the ciphertext feedback mechanism are introduced to determine the dynamic diffusion. Compared with the existing local dynamic encryption schemes, the main advantage of this scheme is that it can realize global dynamic selection, so as to ensure that there is no equivalent key, and it can resist the chosen-ciphertext attack or chosen-plaintext attack and does not need an additional secure channel to transmit parameters related to plaintext, which is practical. A theoretical analysis and numerical experiments demonstrate the feasibility of the method.
1. Introduction
With the development of today’s science and technology, all aspects of people’s lives have undergone informatization [1,2]. As a medium in the information age, images can directly convey the message that people want to express [3]. Information technology has an increasing impact on personal privacy, medicine, and social interaction. Once the important information in the image is intercepted or tampered with by the attackers, the damage caused cannot be ignored [4,5]. Therefore, it is very important to protect the safe transmission and reception of image data. In order to ensure the security of digital images, researchers have proposed many image encryption methods based on different technologies [6,7,8].
Generally speaking, image encryption algorithms are mainly divided into two operations: permutation and diffusion [9]. Permutation changes the position of pixels, and its main purpose is to break the correlation between the adjacent pixels of an image. Diffusion changes the pixel value of each pixel in a specific way to achieve the purpose of protecting image information. In essence, diffusion is the operation of changing the pixel value [10,11]. Chaotic systems have the characteristics of pseudo-randomness, initial value sensitivity, parameter sensitivity, and unpredictability [12], which can be applied in the field of image encryption [13,14]. The chaotic sequence generated by the chaotic system iteratively participates in the permutation and diffusion, so as to improve the security of the cryptographic system. Due to the characteristics of chaotic systems and the high adaptability of image encryption technology, chaotic image encryption technology has gradually attracted the attention of researchers [15,16].
With the deepening of research on chaotic image encryption technology, chaotic image encryption algorithms are mainly divided into three categories [17,18]. The first type is encryption by a self-synchronous stream cipher, which does not require an additional secure channel and is practical [19,20,21,22,23]. The second type is encryption related to plaintext; this scheme has no equivalent key, and it is difficult to crack, but the premise is that additional parameters, such as the hash value, need to be assumed to be transmitted through an additional secure channel, which is not practical. Although Chai et al. improved on this basis by embedding key parameters into the cipher image and transmitting it together with the latter cipher image, it can not resist cropping attacks well [24]. The third type is a hybrid encryption that combines other technologies, such as local dynamic encryption, which does not consider the equivalent key and other situations and has difficulty resisting chosen-plaintext or chosen-ciphertext attacks. For example, Xian proposed a fractal sorting matrix and its application in chaotic image encryption [25]. The pixel positions in each round of permutation are the same, and the diffusion is orderly, which reduces the dynamics and randomness of the scheme. These make the scheme less secure [26,27,28].
In order to make the chaotic image encryption scheme dynamic and flexible, some encryption links with parallel structures are considered in permutation and diffusion [29,30,31,32]. In 2018, Yin proposed a chaotic image encryption scheme based on a breadth-first search and dynamic diffusion [33]. In 2019, Li proposed a chaotic image encryption method with orbit perturbation and dynamic state variable selection mechanisms [34]. In the same year, Meysam proposed a chaotic image encryption scheme based on a polynomial combination of chaotic maps and dynamic function generation [35]. In 2021, Wu proposed a plaintext-related dynamic key chaotic image encryption method [36]. These schemes use local dynamic selection to improve flexibility and multi-selectivity in the encryption [37,38,39].
In order to further improve the flexibility of a chaotic image encryption scheme, this paper proposes a chaotic image encryption scheme based on global dynamic selection to realize the dynamic selection of bit-level, pixel-level, and image-level encryption by designing a multi-parallel structure. First, DNA encoding rules are dynamically selected according to the chaotic sequence. Then, the DNA-encoded matrix is dynamically permuted. Next, the DNA decoding rules are dynamically selected according to the chaotic sequence. Finally, dynamic diffusion is performed by the diffusion rules obtained by different locations. The main feature of this scheme is that it can realize global dynamic selection, so as to ensure that this scheme cannot crack the equivalent key and can resist chosen-plaintext attacks and chosen-ciphertext attacks. Our scheme does not need to use an additional secure channel to transmit parameters related to plaintext, so it is practical. The simulation results and the performance analysis show that the designed scheme has high security and good performance indicators.
The remainder of this research work is organized as follows. The overall framework of the scheme and the basic theory of 2D-LSM, DNA coding, dynamic permutation, and dynamic diffusion are given in Section 2, while the security of the scheme is analyzed theoretically in Section 3. Simulation experiments and performance analysis are detailed in the Section 4. This article ends with a Conclusion section in which the contributions are summarized (Section 5).
2. Chaotic Image Encryption Scheme
This paper proposes a chaotic image encryption scheme based on global dynamic selection. Its design idea is to build a multi-parallel structure, and its main feature is to realize dynamic selection through the multi-parallel structure design in encryption. First of all, all encryption processes in this scheme are called “global”. Secondly, for an image to be encrypted, the orders of magnitude of each encryption process are the bit level, pixel level, and image level, respectively, i.e., processing an image at the bit level, pixel level, and image level can also be called global. Dynamic means that when encrypting the same order of magnitude, the encryption rules executed on the same process will change instead of being fixed. Specifically, at the bit level, it is realized through the DNA encoding process and the DNA decoding process. For every two adjacent bits, their rules of DNA encoding and DNA decoding are different. The pixel level is completed by dynamic diffusion, and the diffusion equation performed by every two adjacent pixels is different. The image level is realized by dynamic permutation; for the same image, the first round and the second round of the permutation are determined by the calculated permutation rule value. The permutation rule value is not fixed, and each number corresponds to a rule. The so-called parallel structure means that within the same encryption process, there are multiple available encryption rules. For example, in dynamic diffusion, each pixel will have two diffusion methods, but the specific implementation of the diffusion method can only be known after the diffusion rules are determined. However, encryption with a non-parallel structure often has only one rule to perform encryption, and the encryption method has been fixed. By designing a parallel structure, each encryption process has multiple parallel encryption rules, and the specific process rules in encryption are selected by the chaotic sequence, permutation rule value, and diffusion rule value.
Different from the existing schemes, the main feature of this scheme is that, even if it is not related to the plaintext, the equivalent key cannot be cracked within a limited number of years. The existing dynamic encryption is mainly local dynamic encryption. Local dynamic encryption realizes dynamic selection in some processes of encryption. We propose an encryption scheme with global dynamic selection to achieve dynamic selection in all processes of encryption. At the same time, it also realizes dynamic selection from the three aspects of the bit level, pixel level and image level for the first time. In the process of DNA encoding and DNA decoding, DNA encoding and decoding rules are selected according to the chaotic sequence to realize dynamic selection at the bit level. In the dynamic permutation, according to the permutation rule value, the permutation method is dynamically selected to realize the dynamic permutation at the image level. In dynamic diffusion, the diffusion equation of each pixel is selected through the diffusion rule value to achieve dynamic selection at the pixel level.
As the number of encryption rounds increases, the permutation method and diffusion equation performed by the first round and the second round of encryption will change due to the permutation rule value and the diffusion rule value. The encryption rules executed in different rounds are different. This reflects the characteristics of dynamic selection. The global dynamic selection feature of the scheme is reflected in two aspects:
- 1.
- All elements of an image can be classified into bit level, pixel level, and image level. This scheme dynamically selects a specific encryption from these three levels to encrypt the image.
- 2.
- Using the chaotic sequence and the designed multi-parallel structure, the design concept of dynamic selection is reflected in the encryption rules that need to be selected and executed for each process.
2.1. Scheme Description
The block diagram of the proposed image encryption scheme is shown in Figure 1. Without loss of generality, an encrypted object can be reduced to an image P of size , represented by a two-dimensional (2D) eight-bit integer matrix ; the final cipher image obtained after encryption through this scheme is . Each piece of two-dimensional image data can also be written as a one-dimensional (1D) array scanned in raster order (left to right, top to bottom). For example, . In Figure 1, the single-throw switch is turned on first, and, after entering the plain image P, is disconnected, and the double-throw switch is connected to position one. The image, after the first round of encryption, is fed back to the input for the second round of encryption. Then, connecting to position two outputs the cipher image. In Figure 1, I, S, E, D, , and are the DNA-encoded matrix, permutation matrix, DNA-decoded matrix, diffusion matrix, permutation rule value, and diffusion rule value of the encrypted image.
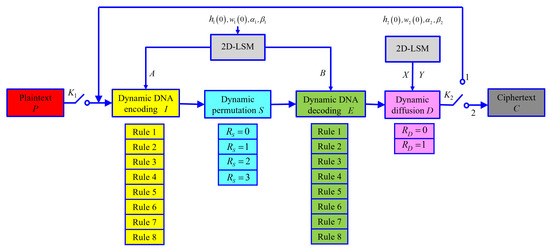
Figure 1.
Block diagram of global dynamic encryption.
In this scheme, the sub-block diagram of “2D-LSM” is a two-dimensional chaotic system proposed by Hua et al. [17], and the mathematical expression of the iteration function is:
where . The system is in a chaotic state when . This chaotic system has a total of four key parameters , The system is iterated by the first set of initial key parameters to obtain the chaotic sequences A and B. The system is iterated by the second set of initial key parameters to obtain X and Y.
This scheme realizes bit-level dynamic selection through sub-block diagrams of “Dynamic DNA encoding I” and “Dynamic DNA decoding E”. The process of DNA encoding is to divide each eight-bit binary pixel of image P into four two-bit binary bit pairs, according to the corresponding value in A. The DNA encoding rule to be executed is dynamically selected to realize the DNA encoding from the number matrix to the symbol matrix. The DNA-encoded matrix I is obtained. The process of DNA decoding is the opposite of that of DNA encoding. According to the corresponding value in B, the decoding rule is dynamically selected to decode each of the four symbols into an eight-bit binary pixel, and the DNA decoding matrix E is obtained.
The sub-block diagram of “Dynamic permutation S” realizes the dynamic selection of different permutation methods for the DNA-encoded matrix I and introduces the permutation rule value to select and execute four different permutation methods. is determined by the symbol values of the four corners of the matrix I, and the matrix after dynamic permutation is denoted as S.
Through the sub-block diagram “Dynamic diffusion D”, the dynamic diffusion of pixels in different positions of the DNA-decoded matrix E is realized. According to the diffusion rule value , select the specific execution rule from two different diffusion rules, and the image after diffusion is D. is obtained by feedback from the DNA-decoded matrix E, chaotic matrix X and diffusion matrix D. D is obtained by substituting the feedback of the DNA-decoded matrix E, the chaotic matrix Y, and the diffusion matrix D into the diffusion equation determined by .
is a single-throw switch, which is used to cut off or connect the plaintext input encryption system; is a double-throw switch, which is used to connect the feedback loop when is at one and to connect the ciphertext output branch when is at two. The ciphertext output branch is used to output the final encrypted cipher image.
2.2. The Encryption Process
This section will introduce the encryption process of this scheme, and the detailed process is as follows:
(1) Initialization: Iterate the 2D-LSM chaotic system 800 times from the initial conditions with the control parameters to avoid the transient effect in the initial iteration, and then iterate it more times to obtain the two state sequences and . Quantize them to two eight-bit integer sequences and via
where is the rounding down function, is the modulo operation, and .
Iterate the 2D-LSM chaotic system 800 times from the initial conditions with the control parameters to avoid the transient effect in the initial iteration, and then iterate it L more times to obtain two state sequences and . The one-dimensional arrays and can also be written as two-dimensional eight-bit integer matrices, and , by scanning them in raster order. Quantize them to two eight-bit integer sequences and via
where is the rounding down function, is the modulo operation, and .
(2) DNA encoding: The switch is closed, so that each pixel in P corresponds to four two-bit binary pairs. Then, use the column encoding rules in Table 1 to transform them into DNA symbols. Because one pixel corresponds to four symbols, the matrix P will be reshaped into a symbol matrix with M rows and columns, consisting only of “ATCG”.

Table 1.
Eight kinds of DNA coding rules.
(3) Dynamic permutation: Calculate the permutation rule value according to the pixel position value of the DNA-encoded matrix and perform the corresponding permutation to obtain the permutation image S. The expression of is
where the DNA symbol is converted into binary according to “A = 00, G = 01, C = 10, T = 11”. Then, the addition operation of Equation (4) is performed, and is the modulo operation.
Since the Modulo 4 operation is performed when calculating , satisfies . The matrix of illustrates the permutation according to .
When , transpose the symbol matrix I, as shown in Figure 2.
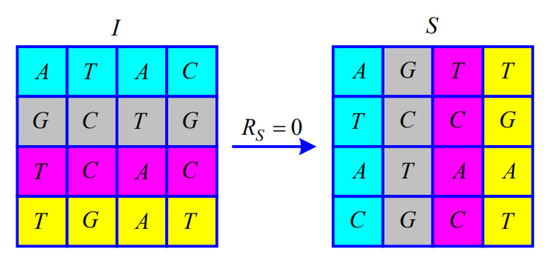
Figure 2.
Illustration of the permutation for .
When , from to , the i-th and -th of the symbol matrix I exchange the entire row, as shown in Figure 3.
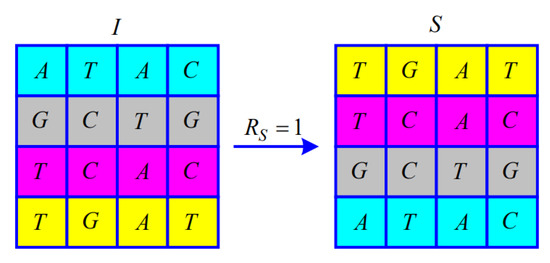
Figure 3.
Illustration of the permutation for .
When , from to , the i-th and -th of the symbol matrix I exchange the entire column, as shown in Figure 4.
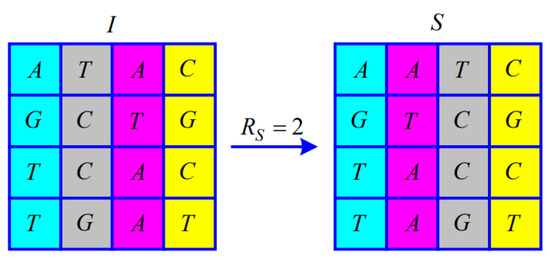
Figure 4.
Illustration of the permutation for .
When , from to , the i-th and -th of the symbol matrix I exchange the entire row, as shown in Figure 5.
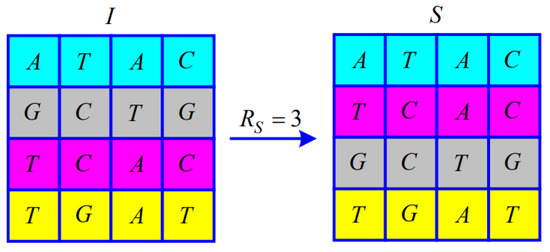
Figure 5.
Illustration of the permutation for .
(4) DNA decoding: Select the rules in Table 1 for dynamic DNA decoding of the permutation image S according to the corresponding values in sequence B, decode S in the raster scanning order, combine the four symbols into one pixel, and obtain a DNA-decoded matrix with M rows and N columns.
(5) Dynamic diffusion: According to the DNA-decoded matrix E, the chaotic matrix X, and the diffusion matrix D, dynamically calculate the diffusion rule value at different positions of E, where the mathematical expression of is
where , is the modulo operation, and ⊕ is the exclusive OR operation.
The diffusion rule value determines the diffusion rule performed by the pixel at different positions of E, and the diffusion image is .
Figure 6 shows how to obtain the diffusion rule value for an image of .
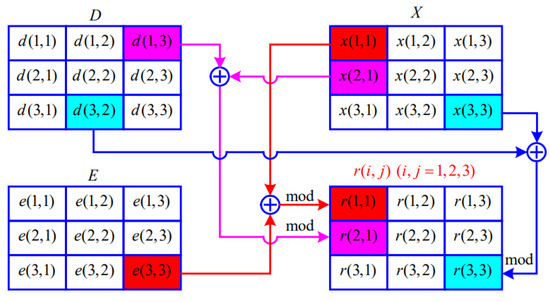
Figure 6.
A schematic diagram of acquisition of diffusion rules.
The diffusion image is obtained as follows:
where and . Figure 7 shows how to obtain the diffusion image .
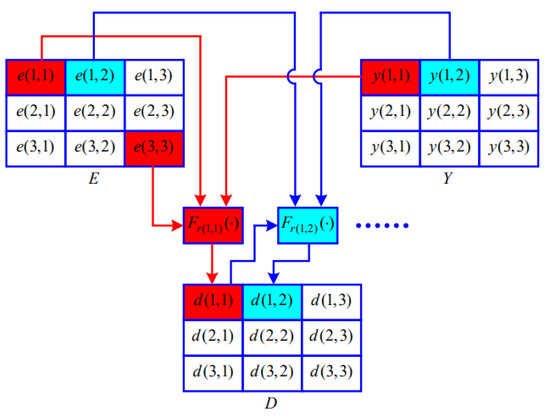
Figure 7.
A schematic diagram of acquisition of D.
(6) Disconnect , connect to position one, and use the diffusion image D as the input image for the next round of encryption.
(7) The second round of encryption: Repeat steps (3)–(6) to make connect to position two. Then, the final cipher image C can be obtained.
The decryption process is the inverse process of encryption, and decryption can be completed by operating the above steps in reverse order. The main steps of decryption are given here.
(1) Inverse dynamic diffusion: Record the inverse diffusion rule value as . According to the inverse diffusion rule value , choose the inverse diffusion equation at different positions to obtain E,
The matrix , before diffusion, is obtained as shown in Equation (7).
where and .
(2) Inverse DNA diffusion: The pixels in E are dynamically decoded according to the corresponding values in sequence B in the raster scanning order, and the corresponding four binary pairs are converted into the DNA symbol matrix S by the column coding rules in Table 1.
(3) Inverse permutation: is obtained to select the inverse permutation rule, and .
(4) Inverse DNA encoding: According to the corresponding value in sequence A, the DNA coding rule in Table 1 is dynamically selected to reverse encode I to obtain the DNA-decoded matrix P.
During encryption, both the permutation rule value and the diffusion rule value will change with the number of rounds to achieve the purpose of dynamic rule selection, so as to flexibly use different permutation rules and diffusion rules. When the image is encrypted, different permutation rules will be implemented for different encryption rounds, so as to realize dynamic permutation at the image level. In dynamic diffusion, the diffusion rule value of each pixel will also change dynamically with the pixel position, and the diffusion rule value of each round will also change dynamically with the number of encryption rounds, achieving dynamic diffusion from the pixel level. For different images to be encrypted, depends on the special location pixels of the input image to be encrypted after DNA encoding and the different images to be encrypted by different permutation rule values. The diffusion rule value is mainly determined by the image before diffusion E. The permutation image S and the chaotic matrix X, and the diffusion rule value will also change as the number of rounds of encryption changes the DNA-decoded matrix E and the permutation image S.
Setting the number of feedback rounds to one can not only reflect the characteristics of dynamic diffusion rules changing with the number of rounds but also reflect the dynamic selection and the multi-parallel structure. Too many rounds will definitely affect the encryption efficiency. In this scheme, as the number of rounds changes, fewer rounds can be used to achieve the core advantages of the scheme, namely the dynamic, parallel structure and the dynamic diffusion rule matrix . Through the global dynamic selection feature, the combination of encryption methods for any one-bit pair change is , and the combination of encryption methods for any pixel change is . This is the main difference between the parallel structure proposed in this paper and the existing non-parallel structure.
3. Security Analysis
3.1. Equivalent Key Analysis
The core of the scheme’s security lies in the ciphertext feedback mechanism and dynamic selection characteristics. Through these two characteristics, the cost of finding special plaintext pairs that are conducive to cracking is significantly higher. This section theoretically analyzes the ciphertext feedback mechanism and dynamic selection characteristics in this encryption scheme to illustrate the effect of the ciphertext feedback mechanism and the dynamic selection feature on the security of the scheme.
3.1.1. Analysis of Ciphertext Feedback Mechanism in Diffusion
The expression of the ciphertext feedback mechanism reflected in the diffusion is shown in Equation (6). In order to better study the effect of the ciphertext feedback mechanism, let the image before diffusion be , and the image after diffusion be .
Transform Equation (6) into
where is the diffusion-related factor, and .
Proposition 1.
If different images before diffusion and have at , then .
Proof.
For different images and , there are the diffusion-related factors
and
Respectively, the corresponding images are and .
The diffusion-related factor at is expressed as and . Then, . Proposition 1 is proved. □
From Proposition 1, , where and . According to Equation (9), it is found that the difference will be passed to the next pixel after the ciphertext feedback mechanism, making the value of unpredictable.
Supposing that the diffusion images in the first round are and , the diffusion images in the second round are and , and the final cipher images are and , respectively.
For the first round of encryption, is unpredictable at , but in the second round of encryption, and are used as the input images, and the unpredictability of and is transmitted to other positions of the image by DNA encoding, dynamic permutation, and DNA decoding, applying the unpredictability of a single pixel to all pixels in the image. In addition, the input images and in the second round are uncontrollable for the attacker, and it is difficult to directly select a special plaintext pair to obtain a partially controllable by chosen-plaintext attack, so that the equivalent key cannot be cracked.
3.1.2. Diffusion Rule Value Difference Analysis
The image after the first round of DNA decoding is . The image after the second round of DNA decoding is . The image after the first round of dynamic diffusion is , and the image after the second round of dynamic diffusion is the final cipher image .
For the ciphertext feedback mechanism of the first round of the diffusion rule , the expression is as follows:
The diffusion rule value difference can be simplified to , where
is the extracted ciphertext-related factor.
To better study the effect of ciphertext feedback mechanisms in this process, it is assumed that there are different
and
where the subscript 1 represents the first round of encryption, i.e., . . The diffusion rules corresponding to and are and , respectively, where there must be .
Specifically, suppose and exist, and , where and . After the ciphertext feedback mechanism, the unpredictability of is passed to the next pixel of , and so on, eventually making the value of unpredictable, meaning that and in the first round of diffusion rule expressions are unpredictable at . For and , since and in and are unmeasurable at , the number of diffusion rules that need to be exhausted are in the range of is .
In the second round of encryption, the ciphertext-related factors in the corresponding diffusion rules of and are
and
respectively. Since the unpredictability of and also makes and unpredictable, this makes the second round of the permutation rule more unpredictable. Based on this, and because of the dynamic nature of , in each location is unpredictable, the attacker needs to exhaust all cases. For a -size image, the second round of the diffusion rule value needs to be exhausted , and the total number of exhaustive times for and in the case of two rounds of encryption is .
According to the development of the limit of exhaustive attacks based on Moore’s Law, the limit of exhaustive attacks in 2022 is , and the limit of exhaustive attacks in 2050 will be [39]. For the existing effective image size, it is easy to satisfy that is larger than , and there are , , and , which are far greater than the required for the key space.
3.2. Key Space Analysis
Any chaotic image encryption scheme has a key space larger than to ensure that it can withstand brute force attacks. The key space mentioned here means that the chaotic digital image system uses a key with a specified length.
In this scheme, the 2D-LSM system is in a chaotic state within the parameter range from to . With a finite precision of , there are , , , and , and the calculation formula for a set of parameter key spaces is as follows:
Because two sets of key parameters are set, the overall key space of this scheme is , which is much larger than , which meets the key space requirements of the encryption scheme.
4. Simulation Experiments and Performance Analysis
The experimental hardware platform is a PC, and the processor is Ryzen 5 5600 G AMD, The benchmark frequency is 3.90 GHz, the memory size is 16G, the hard disk is a 128G SSD, and the HDD is 1 T. The software environment is the Windows 10 operating system and Matlab R2019a.
In this section, to demonstrate the security of our scheme, a grayscale image of the size is used as the plain image. The initial keys are
, , , , , , ,
.
The original plain image encrypted with the number of feedback rounds is one to illutrate the encryption performance indicators. The relevant experimental results are shown in Figure 8, where (a), (d), and (g) are the plain images of Lena, Peppers, and Cameraman, respectively; (b), (e), and (h) are the cipher images of Lena, Peppers, and Cameraman, respectively; and (c), (f), and (i) are the decrypted images of Lena, Peppers, and Cameraman, respectively.
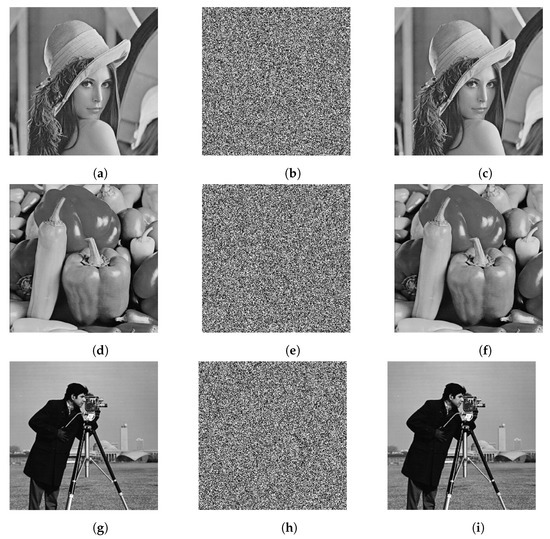
Figure 8.
Experimental results: (a) Lena original image, (b) Lena encrypted image, (c) Lena decrypted image, (d) Peppers original image, (e) Peppers encrypted image, (f) Peppers decrypted image, (g) Cameraman original image, (h) Cameraman encrypted image, (i) Cameraman decrypted image.
4.1. Histogram Analysis
An image histogram is a frequency statistic for each grayscale level in an image. The histogram shows the distribution of grayscale in the image. For the distribution of pixel intensity in the image, the histogram of the cipher image obtained by a secure encryption scheme should be as flat and uniform as possible. A more evenly distributed histogram means a better ability to resist statistical attacks, as shown in Figure 9. The plain images of Lena, Cameraman, and Peppers with their histograms and the ciphertexts with their corresponding histograms are shown in Figure 9. It can be seen that the grayscale distribution of their original image has many peaks and valleys, but, in the encrypted grayscale image, the grayscale distribution is very uniform. Therefore, it can be confirmed that the scheme we designed has the performance of resisting statistical attacks.
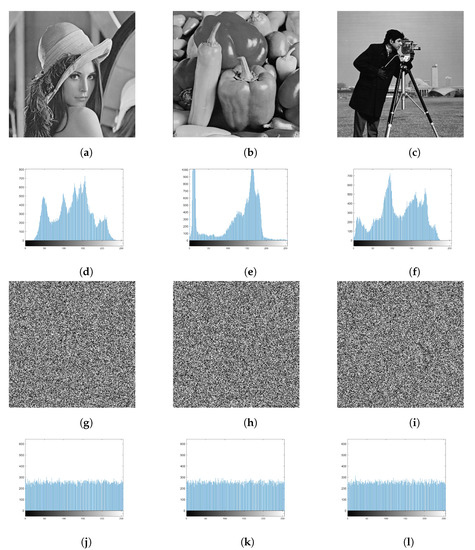
Figure 9.
Experimental result: (a) plain image of Lena, (b) plain image of Peppers, (c) plain image of Cameraman, (d) histogram of Lena plain image, (e) histogram of a Peppers plain image, (f) histogram of Cameraman plain image, (g) cipher image of Lena, (h) cipher image of Peppers, (i) cipher image of Cameraman, (j) histogram of Lena’s cipher image, (k) histogram of Peppers’ cipher image, (l) histogram of Cameraman’s cipher image.
4.2. Correlation Analysis
Since adjacent pixels of common images are highly correlated in horizontal, vertical, and diagonal directions, this indicates that adjacent pixels often have similar and predictable features. An ideal image encryption scheme should have sufficiently low correlation coefficients in the horizontal, vertical, and diagonal directions to resist statistical attacks.
To highlight the influence of the encryption scheme proposed in this paper on eliminating the high correlation of planar images, their correlation in the horizontal, vertical and diagonal directions was calculated by
where
and N is the number of randomly chosen adjacent pixel pairs along the horizontal direction, vertical direction, and diagonal direction in both the plain image and its cipher image. and are the i-th items of the two adjacent pixel sequences u and v.
Figure 10 demonstrates the adjacent pixel correlation plots of the arbitrarily chosen 2000 sets of nearby pixels in Lena, Cameraman, and Peppers along the horizontal, vertical, and diagonal orders. It can be observed that, in each figure, the X-axis indicates the three images, while the Y-Z plane plots the values of the adjacent pixels. The adjacent pixel pairs of the plain images are mostly on or close to the diagonal lines, indicating that these adjacent pixels exhibit strong correlations. However, the adjacent pixel pairs for all cipher images are distributed quite randomly across the Y-Z phase plane, demonstrating that they exhibit weak correlations. This indicates that our proposed scheme can efficiently decorrelate the high correlations of the plain images.
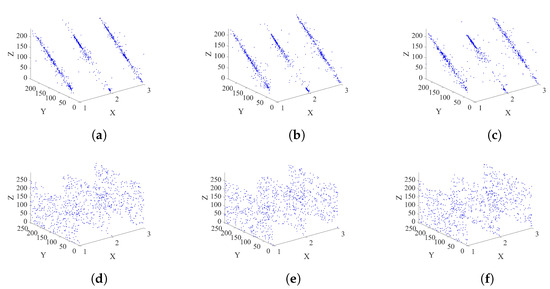
Figure 10.
Histograms of Lena, Cameraman, and Peppers: (a) horizontal adjacent pixel pairs of three plain images, (b) vertical adjacent pixel pairs of three plain images, (c) diagonal adjacent pixel pairs of three plain images, (d) horizontal adjacent pixel pairs of three cipher images, (e) vertical adjacent pixel pairs of three cipher images, (f) diagonal adjacent pixel pairs of three cipher images. In each figure, the X-axis denotes the index of the three images, while the Y-Z plane plots the pixel pairs.
The correlation distribution results are shown in Table 2, where we calculate the correlation coefficients of adjacent pixels in the horizontal, vertical, and diagonal directions of Lena, Cameraman, and Peppers and images 4.2.05, 4.2.06, and 4.2.07 with , and it can be clearly seen that the correlation coefficient of the original image is close to 1, while the correlation coefficient of the encrypted image is close to 0 in all directions.

Table 2.
Correlation coefficients of adjacent pixel pairs in the original images and their encrypted images.
4.3. NPCR and UACI Tests
A differential attack is a common security attack model. In the broadest sense, it refers to an attack for tracing how differences in information input can affect the resultant difference at the output and exploiting such properties to recover the secret key (cryptography key). An image encryption scheme exhibits high performance in resisting differential attacks if it possesses the characteristics of diffusion and the avalanche effect. The above characteristics indicate that a slight change in the plaintexts can spread over all of the data in the ciphertexts.
Therefore, the number of pixel change rates (NPCR) and a unified average changing intensity (UACI) are proposed to better measure the diffusion and avalanche effect characteristics in an encryption scheme. Security (resistance to differential attacks) is associated with high UACI/NPCR values. The calculation formula is as follows
where two images of the same size are denoted as and , the size of the image is , and are the pixel values of the corresponding coordinates in the images, and is the sign function as
Given the significance level , the critical NPCR score is obtained as
where G indicates the largest allowed pixel value, and is the inverse cumulative density function of the standard normal distribution . The critical scores with the given can be obtained using
where and .
An encryption algorithm can pass the test if the calculated UACI value is within the range .
Using Equation (19) to calculate the median value of the confidence interval, compare the average value of UACI calculated by different images of the the same size. The closer to , the more stable the UACI is
In Table 3, the NPCR and UACI values of multiple encrypted images of different sizes in our scheme are compared with those in other schemes. The numbers in bold indicate the best indicators in the comparison scheme, and the numbers with underlines indicate that they failed the test. We find that the average NPCR and UACI values of our encrypted images are 99.6084 and 33.4645, respectively. The NPCR value of reference [38] is 99.5818, which is the closest to the theoretical value, but its pass rate in the NPCR index is only 5/6. By giving priority to the pass rate, our NPCR value is closest to the theoretical value 99.5693 of the image in Table 3, and the corresponding UACI value is also closest to the median value of the confidence interval .

Table 3.
NPCR and UACI values of cipher images.
The average values of NPCR and UACI calculated by different images of are 99.6063 and 33.4653. Although the NPCR value in reference [38] is 99.5818, which is closest to the theoretical value, its pass rate in the NPCR index is only 16/18. By giving priority to the pass rate, our test value is closer to the theoretical NPCR value of 99.5893 for this size, and the corresponding UACI is also closest to the median of the confidence interval .
The average values of NPCR and UACI calculated by different images of are 99.6063 and 33.4602. Although the NPCR value in reference [38] is 99.6037, which the closest to the theoretical value, its pass rate in the NPCR index is only 3/4. By giving priority to the pass rate, our test value is closer to the theoretical NPCR value of 99.5994 for this size, and the corresponding UACI is also closest to the median of the confidence interval .
In summary, our scheme has a high pass rate for NPCR and UACI indicators when encrypting images of different sizes, and the average values of NPCR and UACI obtained under different sizes of images are closer to the theoretical values. It shows that our scheme has a strong ability to resist differential attacks. Therefore, it can be verified that this scheme can resist differential attacks, and it also has certain advantages compared to other schemes.
4.4. Global Shannon Entropy and Local Local Shannon Entropy
Global Shannon entropy is an important indicator that reflects the random characteristics of image information. It is generally believed that the larger the global Shannon entropy, the stronger the uncertainty of the image (the greater the amount of information) and the less visible information. It is used to measure the distribution of image pixels. Their global Shannon entropy can be calculated as
where G indicates the largest allowed pixel value, and represents the probability of the occurrence of the pixel value i.
The theoretical value of the global Shannon entropy H intended for an eight-bit grayscale random image is nearer to eight. Here, the images with sizes of , , and are selected, and the results are shown in Table 4.

Table 4.
Global Shannon entropy of plain images and cipher images.
For an image of the size , the best rates of [14,25] are 2/6 and 1/6; the best rate of our proposed scheme is 3/6. For an image of the size , the best rates of [14,25] are 1/18 and 11/18; the best rate of our proposed scheme is 13/18. For an image of the size , the best rates of [14,25] are 2/4 and 4/4; the best rate of our proposed scheme is 4/4. In total, [14] has a best rate of 5/28, [25] has a best rate of 16/28, and our scheme has a best rate of 21/28. The test results show that our proposed scheme has a better performance in the global Shannon entropy test, and the best rate is relatively good.
Local Shannon entropy is an important indicator to reflect the randomness of local regions [13]. It is generally believed that the confidence interval of a local Shannon entropy is . The local Shannon entropy in this interval indicates that the image shows strong randomness in the local area.
Here, we define the local Shannon entropy measure for 30 local image blocks with 1936 pixels as
where is one of the randomly select non-overlapping image blocks with 1936 pixels within the image S. is computed by Shannon entropy via Equation (20).
The image sizes images are , , and , respectively, and the results are shown in Table 5.

Table 5.
Comparison of local Shannon entropy.
It can be seen that the pass rates of [5,25] are both 2/6, and the pass rate of our proposed scheme is 5/6 for an image of the size . The pass rates of [5,25] are 13/18 and 18/18, and the pass rate of our proposed scheme is 17/18 for an image of the size . The pass rates of [5,25] are 3/4 and 4/4, and the pass rate of our proposed scheme is 4/4 for an image of the size . In total, ref. [5] has a pass rate of 20/28, ref. [25] has a pass rate of 24/28, and our scheme has a pass rate of 26/28.The comparison results show that our proposed scheme has a better overall performance in the local information entropy test, a relatively better pass rate, higher randomness, less visible information, and a better encryption performance.
4.5. Sensitivity Analysis
A cryptographic system with a good security performance must be key-sensitive, that is, a small change in the key will cause significant differences between the encrypted images and the decrypted images. Modify only minor changes to for key susceptibility testing.
During the encryption, the Lena image is encrypted using the original key and a slightly changed key, respectively. The original Lena image is shown in Figure 11a, the cipher image with the original key is shown in Figure 11b, the cipher image with a slightly changed key is shown in Figure 11c, and the difference between the two cipher images is shown in Figure 11d. It indicates that a slight change in the plain image can spread over all of the data in the cipher images.
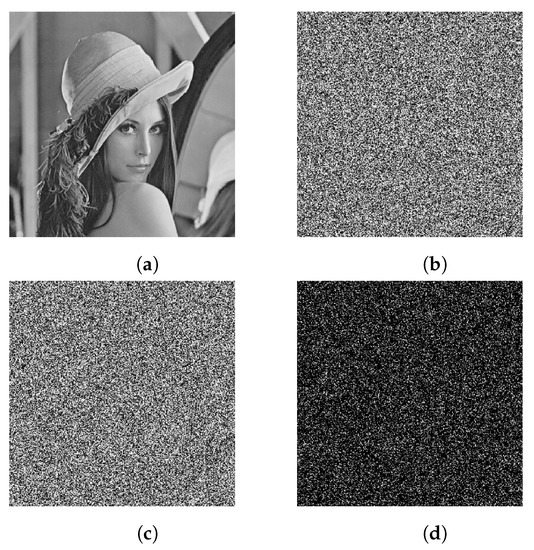
Figure 11.
Key sensitivity test for image encryption: (a) plain image of Lena, (b) encrypted image with the original key, (c) encrypted image with a slightly changed key, (d) cipher image with horizontal adjacent pixel distribution.
During the decryption, the same cipher image of Lena is decrypted with the correct key and with a slightly changed key, respectively. The original image is featured in Figure 12a, the encrypted image with the original key is featured in Figure 12b, the decrypted image with a slightly changed key is featured in Figure 12c, and the image decrypted by the original key is featured in Figure 12d.
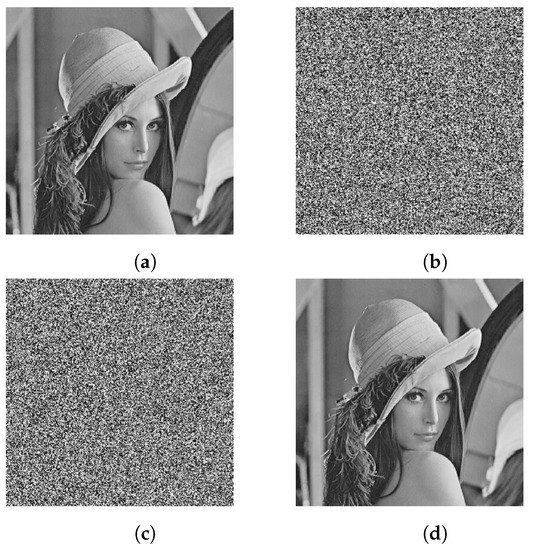
Figure 12.
Key sensitivity test for image decryption: (a) plain image of Lena, (b) encrypted image with original key, (c) decrypted image with a slightly changed key, (d) decrypted image with the correct key.
5. Conclusions
We propose an image chaos encryption scheme based on global dynamic selection, the main work of which includes the following aspects:
- 1.
- Design a multi-parallel structure to achieve dynamic selection.
- 2.
- Dynamic selection of DNA encoding rules using chaotic sequences.
- 3.
- Calculate the permutation rule according to the pixel position value of the DNA-encoded matrix and perform the corresponding permutation to obtain the permutation image.
- 4.
- The diffusion rule obtained by the ciphertext feedback mechanism is introduced to determine the dynamic diffusion performed, and the image after the diffusion is obtained.
Compared with the existing local dynamic selection, the main advantage of this scheme is that it can realize global dynamic selection. According to the results of Lenstra et al., under the condition of limited years, if the cracking difficulty of this scheme is greater than that of an exhaustive attack, it has no attack value, so the equivalent key cannot be cracked. A theoretical analysis and a numerical analysis verify the feasibility of the scheme.
Author Contributions
Methodology, X.C.; software, X.C.; validation, L.F.; writing—original draft preparation, X.C.; writing—review and editing, S.Y. and Q.W.; supervision, S.Y.; project administration, S.Y.; funding acquisition, Q.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Natural Science Foundation of China (No. 62271157) and the Natural Science Foundation of Guangdong Province (No. 2022A1515010005).
Institutional Review Board Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Hua, Z.; Zhou, Y.; Huang, H. Cosine-transform-based chaotic system for image encryption. Inf. Sci. 2019, 480, 403–419. [Google Scholar] [CrossRef]
- Talhaoui, M.Z.; Wang, X. A new fractional one dimensional chaotic map and its application in high-speed image encryption. Inf. Sci. 2021, 550, 13–26. [Google Scholar] [CrossRef]
- Wang, X.Y.; Zhang, Y.Q.; Bao, X.M. A novel chaotic image encryption scheme using DNA sequence operations. Opt. Lasers Eng. 2015, 73, 53–61. [Google Scholar] [CrossRef]
- Xu, L.; Gou, X.; Li, Z.; Li, J. A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt. Lasers Eng. 2017, 91, 41–52. [Google Scholar] [CrossRef]
- Alawida, M.; Teh, J.S.; Samsudin, A. An image encryption scheme based on hybridizing digital chaos and finite state machine. Signal Process. 2019, 164, 249–266. [Google Scholar] [CrossRef]
- Jain, K.; Aji, A.; Krishnan, P. Medical Image Encryption Scheme Using Multiple Chaotic Maps. Pattern Recognit. Lett. 2021, 152, 356–364. [Google Scholar] [CrossRef]
- Zhao, D.; Liu, L.; Yu, F.; Heidari, A.A.; Wang, M.; Liang, G.; Chen, H. Chaotic random spare ant colony optimization for multi-threshold image segmentation of 2D Kapur entropy. Knowl.-Based Syst. 2021, 216, 106510. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Feng, B.; Lü, J.; Hao, F. Cryptanalysis of a Chaotic Image Encryption Algorithm Based on Information Entropy. IEEE Access 2018, 6, 75834–75842. [Google Scholar] [CrossRef]
- Ye, G.; Zhao, H.; Chai, H. Chaotic image encryption algorithm using wave-line permutation and block diffusion. Nonlinear Dyn. 2016, 83, 2067–2077. [Google Scholar] [CrossRef]
- Farah, M.A.; Farah, A.; Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 2020, 99, 3041–3064. [Google Scholar] [CrossRef]
- Luo, Y.; Yu, J.; Lai, W.; Liu, L. A novel chaotic image encryption algorithm based on improved baker map and logistic map. Multimed. Tools Appl. 2019, 78, 22023–22043. [Google Scholar] [CrossRef]
- Wang, Q.; Yu, S.; Guyeux, C.; Wang, W. Constructing Higher-Dimensional Digital Chaotic Systems via Loop-State Contraction Algorithm. IEEE Trans. Circuits Syst. Regul. Pap. 2021, 68, 3794–3807. [Google Scholar] [CrossRef]
- Wu, Y.; Zhou, Y.; Saveriades, G.; Agaian, S.; Noonan, J.P.; Natarajan, P. Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci. 2013, 222, 323–342. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C.P. Image encryption using a new parametric switching chaotic system. Signal Process. 2013, 93, 3039–3052. [Google Scholar] [CrossRef]
- Solak, E.; Cokal, C.; Yildiz, O.T.; Biyikoğlu, T. Cryptanalysis of Fridrich’s chaotic image encryption. Int. J. Bifurc. Chaos 2012, 20, 1405–1413. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Yan, X.; Li, Q.; Wang, X. Image Encryption Based on Chaotic Sub-Block Scrambling and Chaotic Digit Selection Diffusion. Opt. Lasers Eng. 2020, 134, 106202. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Chen, Y.; Li, Y. Color image encryption using orthogonal Latin squares and a new 2D chaotic system. Nonlinear Dyn. 2021, 104, 4505–4522. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, J. A Multidimensional Chaotic Image Encryption Algorithm based on DNA Coding. Multimed. Tools Appl. 2020, 79, 21579–21601. [Google Scholar] [CrossRef]
- Chen, B.; Yu, S.; Chen, P.; Xiao, L.; Lü, J. Design and virtex-7-based implementation of video chaotic secure communications. Int. J. Bifurc. Chaos 2020, 30, 2050075. [Google Scholar] [CrossRef]
- Chen, B.; Yu, S.; Zhang, Z.; Li, D.D.U.; Lü, J. Design and smartphone implementation of chaotic duplex h. 264-codec video communications. Int. J. Bifurc. Chaos 2021, 31, 2150045. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Xu, C.; Zhang, X.; Iu, H.H. A memristive synapse control method to generate diversified multi-structure chaotic attractors. IEEE Trans.-Comput.-Aided Des. Integr. Circuits Syst. 2022, 42, 942–955. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Sun, Y.; Wang, T. Generating n-Scroll Chaotic Attractors From A Memristor-based Magnetized Hopfield Neural Network. IEEE Trans. Circuits Syst. II Express Briefs 2022, 70, 311–315. [Google Scholar] [CrossRef]
- Alawida, M.; Samsudin, A.; Teh, J.S.; Alkhawaldeh, R.S. A new hybrid digital chaotic system with applications in image encryption. Signal Process. 2019, 160, 45–58. [Google Scholar] [CrossRef]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X. Fractal sorting matrix and its application on chaotic image encryption. Inf. Sci. 2021, 547, 1154–1169. [Google Scholar] [CrossRef]
- Wang, X.; Chen, S.; Zhang, Y. A chaotic image encryption algorithm based on random dynamic mixing. Opt. Laser Technol. 2021, 138, 106837. [Google Scholar] [CrossRef]
- Wang, S.; Peng, Q.; Du, B. Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Opt. Laser Technol. 2022, 148, 107753. [Google Scholar] [CrossRef]
- Liu, W.; Sun, K.; Zhu, C. A fast image encryption algorithm based on chaotic map. Opt. Lasers Eng. 2016, 84, 26–36. [Google Scholar] [CrossRef]
- Gan, Z.H.; Chai, X.L.; Han, D.J.; Chen, Y.R. A chaotic image encryption algorithm based on 3-D bit-plane permutation. Neural Comput. Appl. 2019, 31, 7111–7130. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Cui, L.; Sun, Y.; Xu, C.; Yu, F. Brain-like initial-boosted hyperchaos and application in biomedical image encryption. IEEE Trans. Ind. Inform. 2022, 18, 839–8850. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Cui, L.; Sun, Y.; Zhang, X.; Yao, W. Hyperchaotic memristive ring neural network and application in medical image encryption. Nonlinear Dyn. 2022, 110, 841–855. [Google Scholar] [CrossRef]
- Zhu, Y.; Wang, C.; Sun, J.; Yu, F. A chaotic image encryption method based on the artificial fish swarms algorithm and the DNA coding. Mathematics 2023, 11, 767. [Google Scholar] [CrossRef]
- Yin, Q.; Wang, C. A New Chaotic Image Encryption Scheme Using Breadth-First Search and Dynamic Diffusion. Int. J. Bifurc. Chaos 2018, 28, 1850047. [Google Scholar] [CrossRef]
- Li, H.; Wang, Y.; Zuo, Z. Chaos-based image encryption algorithm with orbit perturbation and dynamic state variable selection mechanisms. Opt. Lasers Eng. 2019, 115, 197–207. [Google Scholar] [CrossRef]
- Asgari-Chenaghlu, M.; Balafar, M.A.; Feizi-Derakhshi, M.R. A novel image encryption algorithm based on polynomial combination of chaotic maps and dynamic function generation. Signal Process. 2019, 157, 1–13. [Google Scholar] [CrossRef]
- Wu, Z.; Pan, P.; Sun, C.; Zhao, B. Plaintext-Related Dynamic Key Chaotic Image Encryption Algorithm. Entropy 2021, 23, 1159. [Google Scholar] [CrossRef]
- Khan, M.; Masood, F. A novel chaotic image encryption technique based on multiple discrete dynamical maps. Multimed. Tools Appl. 2019, 78, 26203–26222. [Google Scholar] [CrossRef]
- Himeur, Y.; Boukabou, A. A robust and secure key-frames based video watermarking system using chaotic encryption. Multimed. Tools Appl. 2018, 77, 8603–8627. [Google Scholar] [CrossRef]
- Lenstra, A.K.; Verheul, E.R. Selecting cryptographic key sizes. J. Cryptol. 2001, 14, 255–293. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).