Multi-Sensor Scheduling Method Based on Joint Risk Assessment with Variable Weight
Abstract
1. Introduction
- (1)
- Joint risk assessment model containing target loss risk and target threat risk with variable weight is proposed. The traditional risk assessment methods only consider single risk (for example, target threat risk), while the proposed joint risk assessment model may be suitable for describing discrete risk and continuous risk, satisfying diversity of risk assessment models.
- (2)
- A multi-step joint risk prediction model is introduced to smooth the vibration of risk assessment, thus frequently switching the work mode of the sensor induced by time-varying risk can be avoided, and improve the optimization solution of sensor scheduling.
- (3)
- Convex relaxation is introduced to handle the NP-hard problem of sensor scheduling, leading to a suboptimal scheduling scheme with relatively minor computational complexity, which rapidity improves the algorithm.
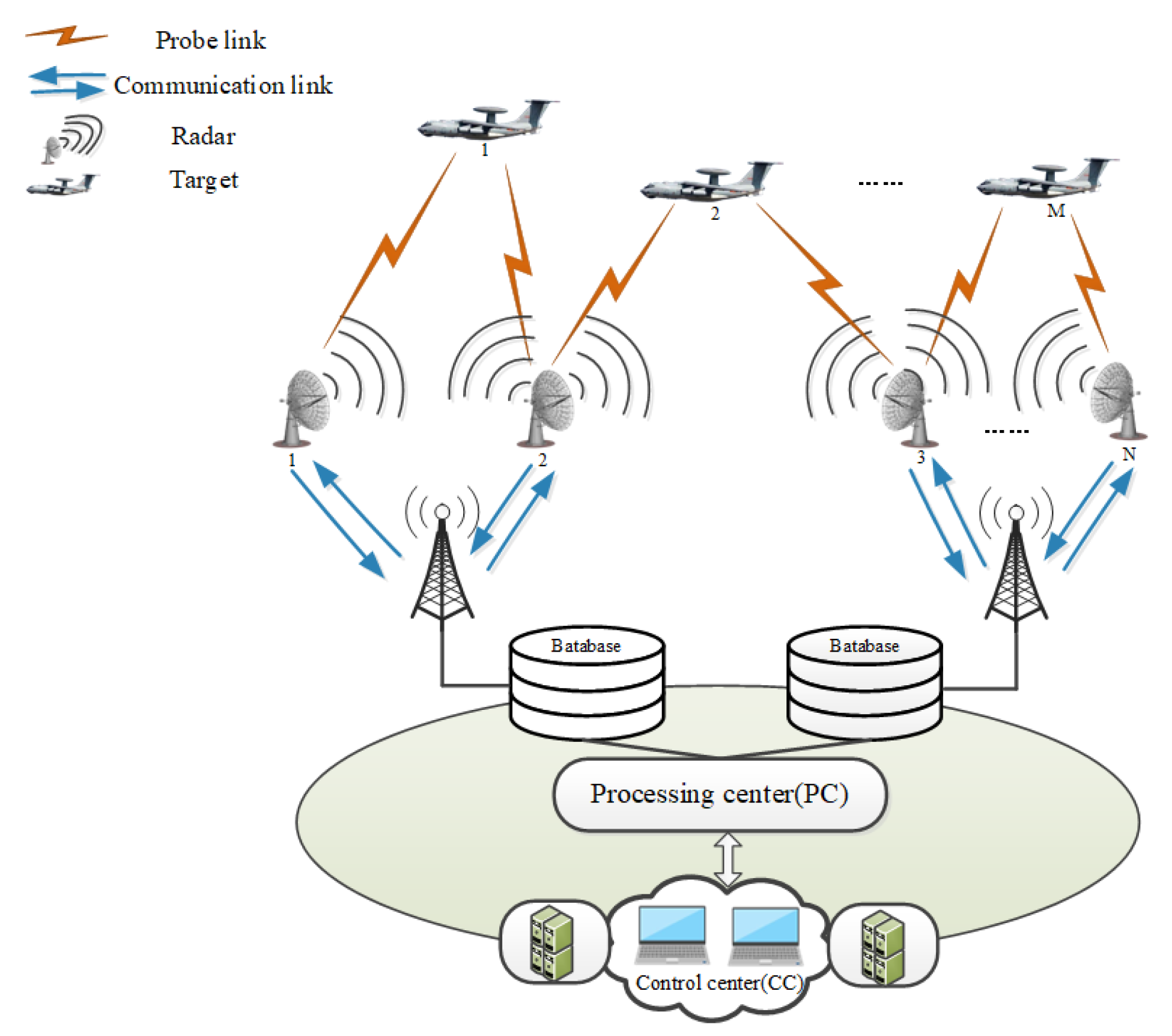
2. Problem Description
- (1)
- The number N of sensors used to detect targets is greater than the number M of targets, i.e., .
- (2)
- One target can be tracked by at least one sensor.
3. Target Loss Risk and Target Threat Risk
3.1. Target Loss Risk
- (1)
- Detection probability of target
3.2. Target Threat Risk
- (1)
- The target threat value U
- (2)
- Probability of target threat risk
- (3)
- Loss relating to target threat risk
4. Multi-Sensor Scheduling Based on Joint Risk Assessment
4.1. Flow Chart of Proposed Method
4.2. Joint Risk Assessment with Variable Weight
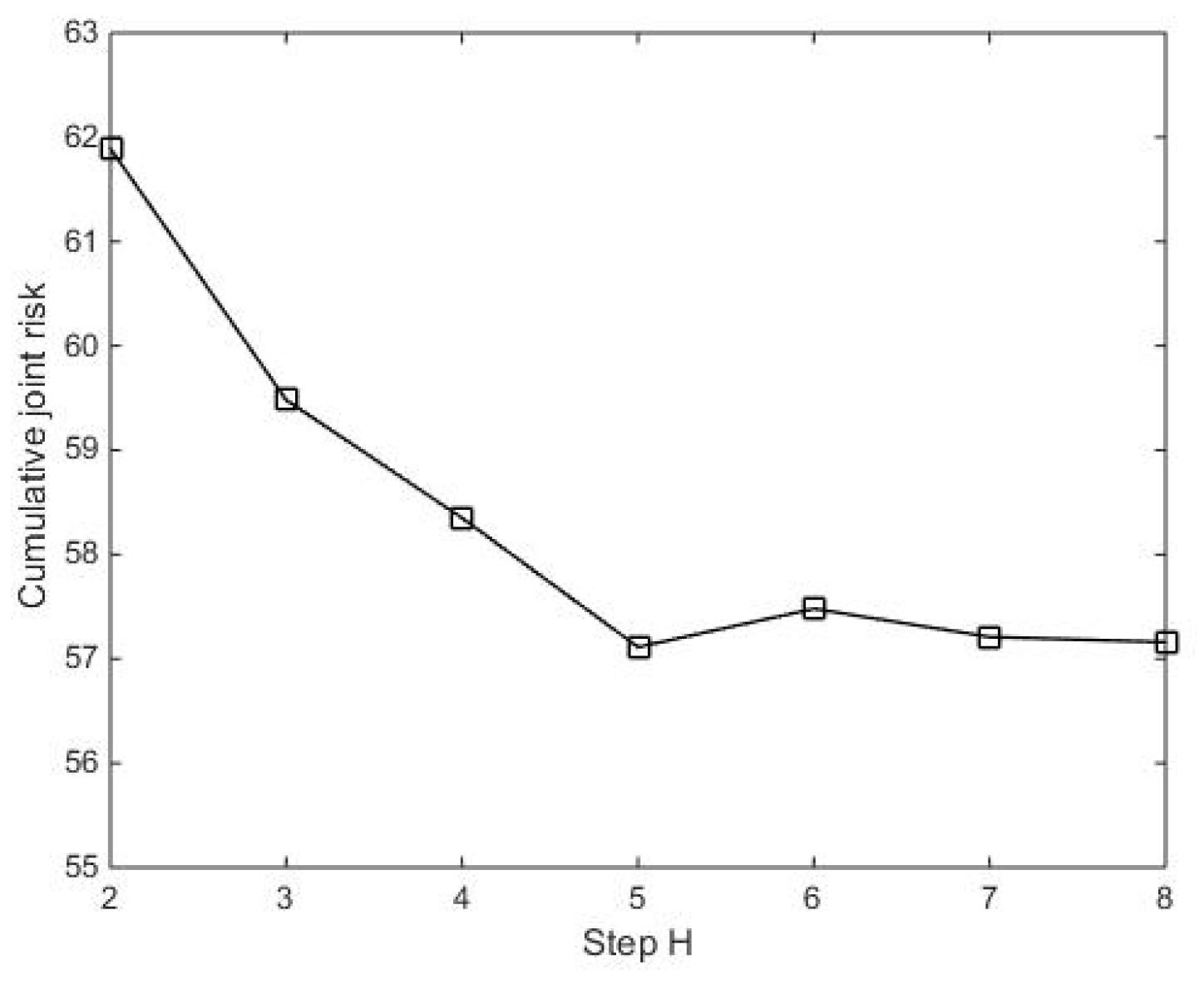
4.3. Multi-Step Prediction Model of Joint Risk Assessment
4.4. Multi-Sensor Scheduling Optimization
4.5. Algorithm Implementation
5. Simulation and Analysis
5.1. Scene and Parameters
- (1)
- The random scheduling approach (RMA) [14]: it randomly assigns sensors to detect and track targets, leading to its main application in the case where unknown variables cannot be solved immediately.
- (2)
- The closest scheduling approach (CMA) [15]: it selects sensors closer to the target to detect and track targets. Therefore, the better estimation accuracy of the target state can be obtained.
- (3)
- The myopic scheduling approach (MMA) [16]: it regards minimization of one-step joint risk prediction as the optimization rule of multi-sensor scheduling, in which schemes of sensor scheduling are obtained according ahead of time.
5.2. Results and Analysis
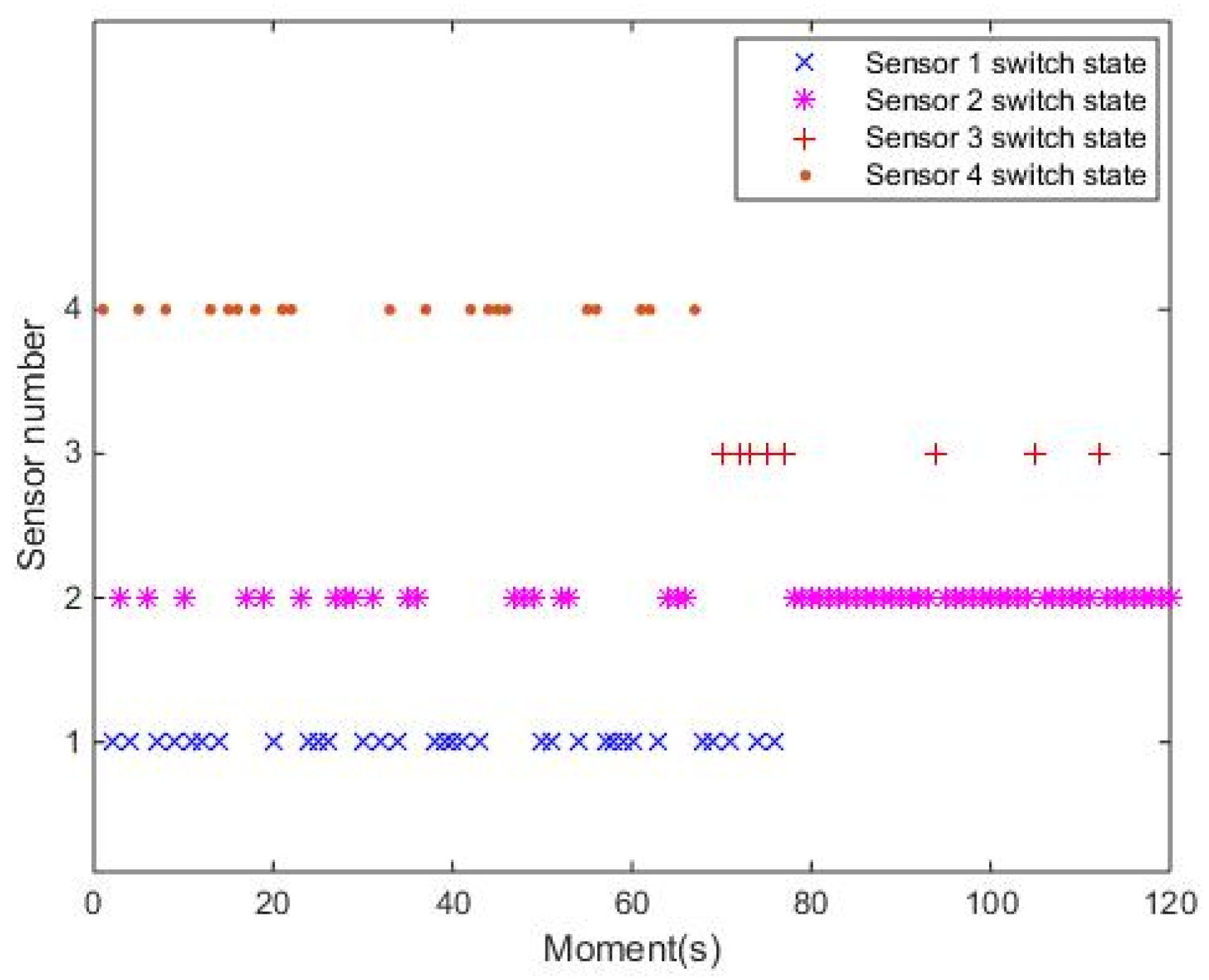
5.2.1. Simulation of PMA
- (2)
- Solution of joint risk
- (3)
- Scheme of sensor scheduling
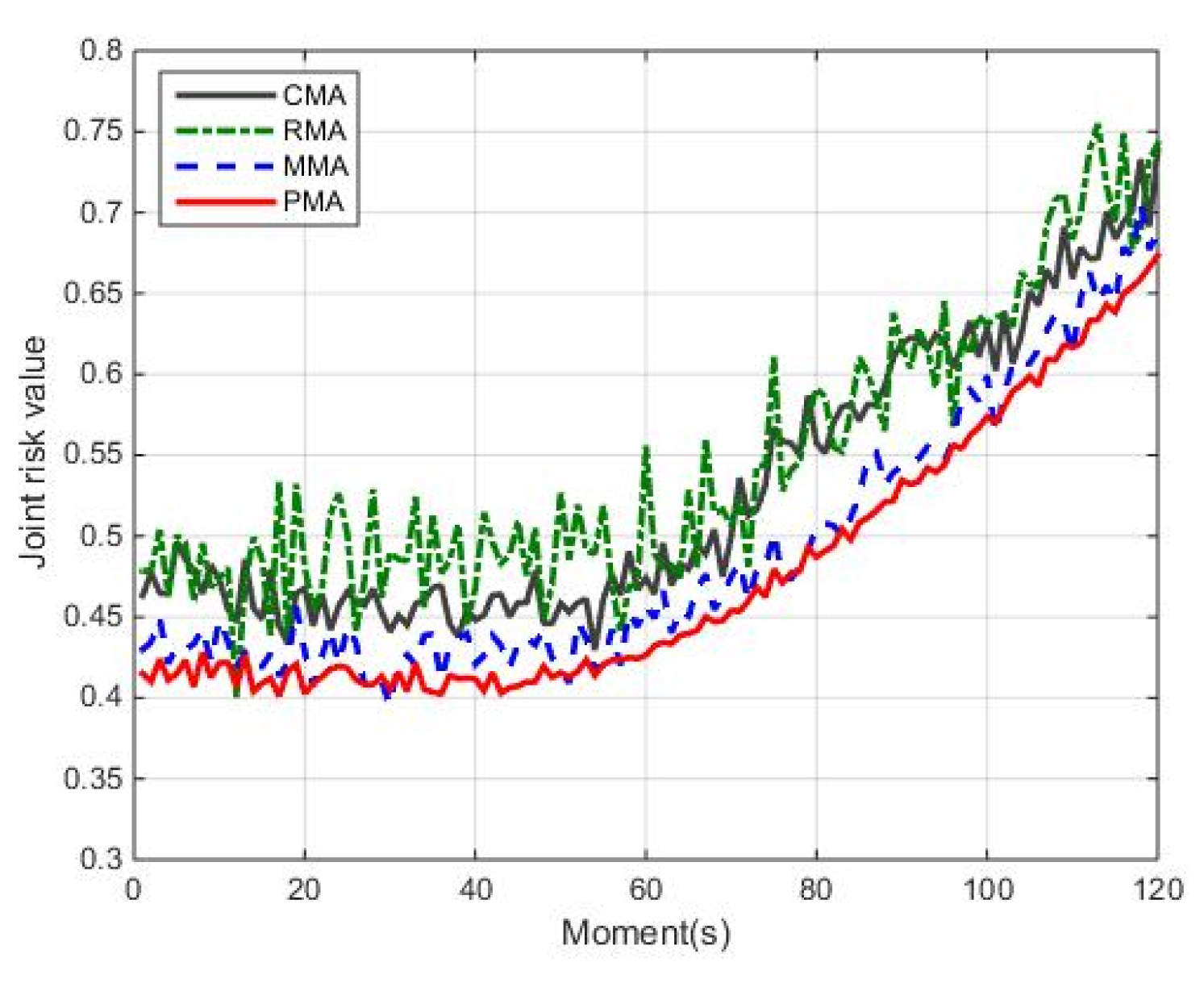
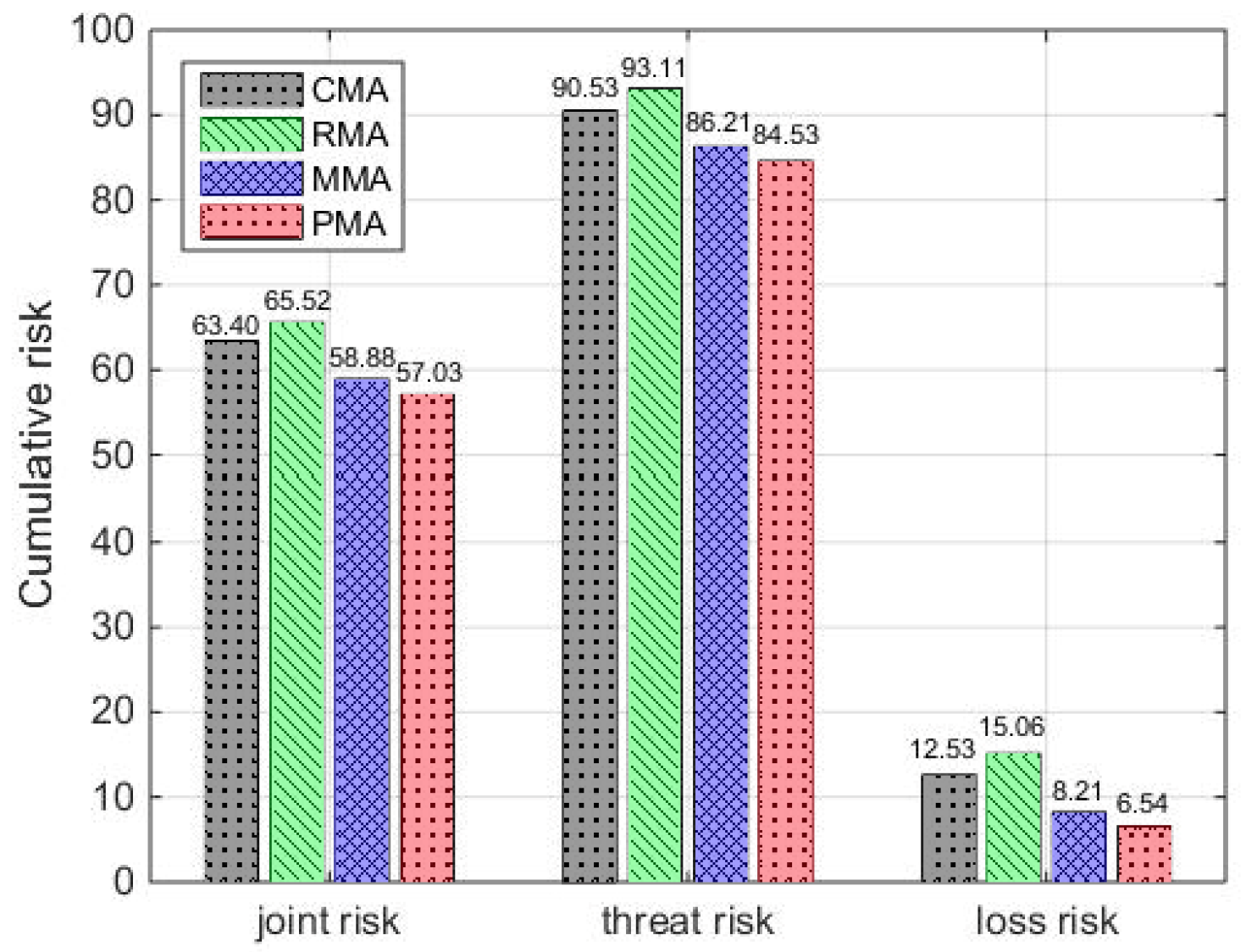
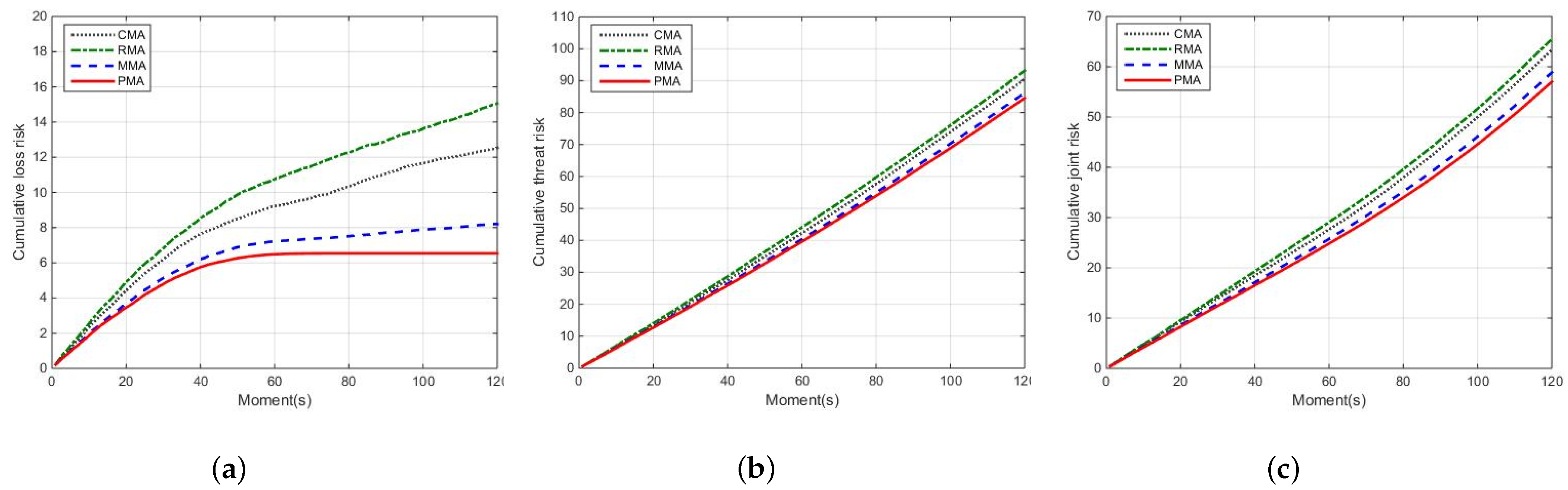
5.2.2. Comparison of Different Methods
- (1)
- Joint risk comparison
- (2)
- Tracking error comparison
- (3)
- Complexity analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhang, C.; Hwang, I. Multi-target identity management with decentralized optimal sensor scheduling. Eur. J. Control. 2020, 56, 10–37. [Google Scholar]
- Shi, Y.; Choi, J.W.; Xu, L.; Kim, H.J.; Ullah, I.; Khan, U. Distributed target tracking in challenging environments using multiple asynchronous bearing-only sensors. Sensors 2021, 20, 2671. [Google Scholar] [CrossRef] [PubMed]
- Anvaripour, M.; Saif, M.; Ahmadi, M. A novel approach to reliable sensor selection and target tracking in sensor networks. IEEE Trans. Ind. Inform. 2020, 16, 171–182. [Google Scholar] [CrossRef]
- Pang, C.; Shan, G. The prediction formula and a risk-based sensor scheduling method in target detection with guiding information. Def. Technol. 2020, 16, 447–452. [Google Scholar] [CrossRef]
- Shen, X.; Varshney, P.K. Sensor selection based on generalized information gain for target tracking in large sensor networks. IEEE Trans. Signal Process. 2014, 62, 363–375. [Google Scholar] [CrossRef]
- Wang, H.; Ge, J.; Zhang, D.; Liu, G. Sensor selection for target tracking based on single dimension information gain. J. Eng. 2019, 2019, 6562–6565. [Google Scholar] [CrossRef]
- Wang, N.; Xu, Y.S. The sensors’ spatial-temporal allocation by linear programming in multi-fighter cooperative detection. In Proceedings of the 2018 IEEE 4th International Conference on Control Science and Systems Engineering, Wuhan, China, 21–23 August 2018; pp. 183–187. [Google Scholar]
- Xu, G.; Pang, C.; Duan, X.; Shan, G. Multi-sensor optimization scheduling for target tracking based on PCRLB and a novel intercept probability factor. Electronics 2019, 8, 140. [Google Scholar] [CrossRef]
- Luo, R.; Huang, S.; Zhao, Y.; Song, Y. Threat Assessment Method of Low Altitude Slow Small (LSS) Targets Based on Information Entropy and AHP. Entropy 2021, 23, 1292. [Google Scholar] [CrossRef] [PubMed]
- Dong, Q.; Pang, C. Risk-Based Non-Myopic Sensor Scheduling in Target Threat Level Assessment. IEEE Access 2021, 9, 76379–76394. [Google Scholar] [CrossRef]
- Lan, Y.; Liang, J. Threat-based sensor management for multi-target tracking. In Proceedings of the International Conference in Communications, Signal Processing, and Systems, Singapore, 4–6 April 2019; pp. 2147–2154. [Google Scholar]
- Pang, C.; Shan, G. Risk-based sensor scheduling for target detection. Comput. Electr. Eng. 2019, 77, 179–190. [Google Scholar] [CrossRef]
- Mou, Z.; Tang, S.; Du, Q.; Wang, S.; Wang, N. Airborne sensor management algorithm based on targets threat evaluation. In Proceedings of the 2017 13th IEEE International Conference on Electronic Measurement & Instruments, Yangzhou, China, 20–23 October 2017; pp. 163–167. [Google Scholar]
- Ebenezer, S.P.; Papandreou-Suppappola, A. Generalized recursive track-before-detect with proposal partitioning for tracking varying number of multiple targets in low SNR. IEEE Trans. Signal Process. 2016, 64, 2819–2834. [Google Scholar] [CrossRef]
- Zhang, Z.; Shan, G. UTS-based foresight optimization of sensor scheduling for low interception risk tracking. Int. J. Adapt. Control. Signal Process. 2014, 28, 921–931. [Google Scholar] [CrossRef]
- Gomes-Borges, M.; Maltese, D.; Vanheeghe, P.; Sella, G.; Duflos, E. Sensor management using expected risk reduction approach. In Proceedings of the 2016 19th International Conference on Information Fusion, Heidelberg, Germany, 5–8 July 2016; pp. 2050–2058. [Google Scholar]
- Shan, G.; Pang, C. Distributed Sensor management Based on Target Losing Probability for Maneuvering Multi-Target Tracking. IEEE Access 2020, 8, 113610–113623. [Google Scholar] [CrossRef]
- Fotios, K.; Hans, D.; Alexander, Y. Threat-based sensor management for target tracking. IEEE Trans. Aerosp. Electron. Syst. 2015, 51, 2772–2785. [Google Scholar]
- Li, W.; Jia, Y. An information theoretic approach to interacting multiple model estimation. IEEE Trans. Aerosp. Electron. Syst. 2015, 51, 1811–1825. [Google Scholar] [CrossRef]
- Pang, C.; Shan, G.; Duan, X.; Xu, G. A multi-mode sensor management approach in the missions of target detecting and tracking. Electronics 2019, 8, 71. [Google Scholar] [CrossRef]
- Xu, G.; Shan, G.; Duan, X. Non-myopic scheduling method of mobile sensors for maneuvering target tracking. IET Radar Sonar Navig. 2019, 13, 1899–1908. [Google Scholar]



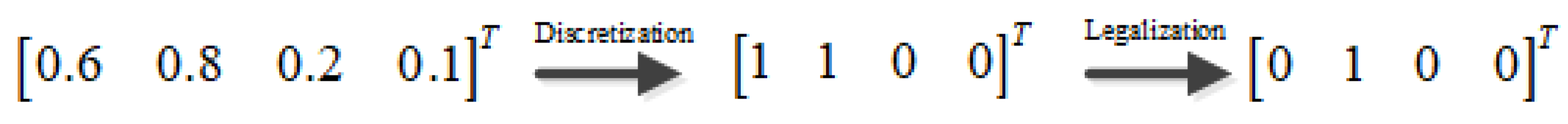
| Continuous Variables | Normalized Functions | Domain |
|---|---|---|
| Heading angle | ||
| Height | ||
| Speed | ||
| Distance |
| Input Multi-step risk prediction |
| Output Scheme of sensor scheduling |
| (1) Initializing parameters; |
| (2) Constructing multi-sensor scheduling optimization problem based on joint risk prediction is |
| according to (20); |
| (3) Relaxing into , then getting (21); |
| (4) Calculating according to (21); |
| (5) Computing by using D-L method and getting suboptimal scheduling scheme of (20). |
| Input Sensors measurements , target threat capability |
| Output Scheme of sensor scheduling |
| (1) Initializing parameters; |
| (2) For do |
| (3) Calculating the target loss risk according to (3); |
| (4) Calculating the target threat risk according to (10); |
| (5) Calculating the adaptive weight of target loss risk and target threat risk based on (17) and (18); |
| (6) Calculating the joint risk according to (16); |
| (7) Calculating the multi-step prediction of joint risk by using (19); |
| (8) Constructing the optimization problem of joint risk-based multi-sensor scheduling according to (20); |
| (9) Using SMBRP to solve the optimization problem (21), and getting the scheme of sensor scheduling ; |
| (10) End for |
| Sensors | Position/km | Detection Power | Sampling period/s | Measurement noise/km | False Alarm Probability |
|---|---|---|---|---|---|
| (0,0,0) | 24.4 | 10 | 0.61 | ||
| (0.1,0,0) | 25.4 | 10 | 0.60 | ||
| (0,0.1,0) | 24.8 | 10 | 0.59 | ||
| (0.1,0.1,0) | 26.1 | 10 | 0.60 |
| Method | MTE (km) | ATE (km) | The Percentage Reduction of RMA in ATE |
|---|---|---|---|
| CMA | 0.50 | 0.29 | 29.3% |
| MMA | 0.61 | 0.33 | 19.5% |
| RMA | 0.69 | 0.41 | - |
| PMA | 0.52 | 0.27 | 34.1% |
| Method | Complexity in General |
|---|---|
| CMA | |
| MMA | |
| RMA | |
| PMA |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, L.; Wu, J.; Wei, Q.; Shi, W.; Jin, Y. Multi-Sensor Scheduling Method Based on Joint Risk Assessment with Variable Weight. Entropy 2022, 24, 1315. https://doi.org/10.3390/e24091315
Zhou L, Wu J, Wei Q, Shi W, Jin Y. Multi-Sensor Scheduling Method Based on Joint Risk Assessment with Variable Weight. Entropy. 2022; 24(9):1315. https://doi.org/10.3390/e24091315
Chicago/Turabian StyleZhou, Lin, Jiawei Wu, Qian Wei, Wentao Shi, and Yong Jin. 2022. "Multi-Sensor Scheduling Method Based on Joint Risk Assessment with Variable Weight" Entropy 24, no. 9: 1315. https://doi.org/10.3390/e24091315
APA StyleZhou, L., Wu, J., Wei, Q., Shi, W., & Jin, Y. (2022). Multi-Sensor Scheduling Method Based on Joint Risk Assessment with Variable Weight. Entropy, 24(9), 1315. https://doi.org/10.3390/e24091315







