Abstract
With the advancement of technology worldwide, security is essential for online information and data. This research work proposes a novel image encryption method based on combined chaotic maps, Halton sequence, five-dimension (5D) Hyper-Chaotic System and Deoxyribonucleic Acid (DNA) encoding. Halton sequence is a known low-discrepancy sequence having uniform distribution in space for application in numerical methods. In the proposed work, we derived a new chaotic map (HaLT map) by combining chaotic maps and Halton sequence to scramble images for cryptography applications. First level scrambling was done by using the HaLT map along with a modified quantization unit. In addition, the scrambled image underwent inter- and intra-bit scrambling for enhanced security. Hash values of the original and scrambled image were used for initial conditions to generate a 5D hyper-chaotic map. Since a 5D chaotic map has complex dynamic behavior, it could be used to generate random sequences for image diffusion. Further, DNA level permutation and pixel diffusion was applied. Seven DNA operators, i.e., ADD, SUB, MUL, XOR, XNOR, Right-Shift and Left-Shift, were used for pixel diffusion. The simulation results showed that the proposed image encryption method was fast and provided better encryption compared to ‘state of the art’ techniques. Furthermore, it resisted various attacks.
1. Introduction
In the past few decades, use of technology has grown rapidly. Transmission and reception of text, voice, image or video is possible due to growth in the field of communication. Large amounts of data are transferred from one point to another every second, which gives rise to security concerns regarding private information. Digital images are relevant and contain large amounts of information. Therefore, lots of research has been done in order to prevent unauthorized access to malicious nodes. Many techniques, like image encryption, steganography and watermarking, are used to protect images from attackers [1]. Image encryption is a method whereby the input image is converted to an unreadable format, which cannot be decrypted without a key. There are two main methods through which a meaningful image can be converted into an unreadable format: confusion and diffusion. Confusion is a process whereby the position of the pixels is changed in such a manner that, visually, it becomes impossible to predict the original image. On the other hand, diffusion is a process whereby the pixel values are changed to encrypt the image. AES (Advanced Encryption Standard) and DES (Data Encryption Standard) entail some of the very first algorithms designed for cryptography. Due to new advancements in communication systems these methods are now found to be dated, have many defects and are more suitable for text encryption [2]. In order to overcome these problems, modern research has focused more on chaos theory, encoding techniques and artificial intelligence. Chaotic maps are extremely sensitive to initial conditions, and are nonlinear, highly random and unpredictable in nature. These characteristics are used in cryptography applications in order to provide better security in the channel [3,4]. The main motivation of the proposed research work was to prevent multimedia threats in the communication channel. Traditional encryption schemes use chaotic maps to confuse and diffuse the pixels. The initial and control parameters used in these algorithms are fixed throughout the encryption process for all input images; which makes the image vulnerable to attack. Higher dimensional maps show more randomness and complex dynamic behavior, compared to traditional one-dimensional chaotic systems.
In general, image encryption methods contain two phases: image scrambling, using chaotic maps, and pixel diffusion, using XOR operation. Various encryption algorithms have been developed by researchers. In [5], a chaos-based cryptosystem was proposed, composed of several rounds of diffusion and substitution. Chaotic maps were used to shuffle the pixels of the image and values were sequentially altered to achieve diffusion. The pixel confusion algorithms included new sorting methods literature, like the quantization unit [6], matrix semi-tensor product theory [7,8], zigzag permutation, graph-theory and fractal sorting matrix [9], to correctly decrypt the image at the receiver’s end. Authors in [10] proposed a color image encryption scheme, based on one-time keys and chaotic maps. This algorithm generated keys by means of the MD5 algorithm of the mouse position, which makes the algorithm robust to chosen-plaintext attack. Color image encryption algorithm, using multi dimension systems with bit-level permutation, was proposed in [11]. For the scrambling and diffusion process, a piece-wise linear chaotic map and Chen multi-dimensional system were used, respectively. In [12], the initial keys for the chaotic maps were generated by MD5 algorithm with input image pixels. This method ensured a different key for every input image. The research discussed above were based on the traditional one-dimensional chaotic map, which is also well known to hackers. Therefore, there is a need to design a new robust chaotic map and an efficient encryption algorithm for secured communication. Multidimensional chaotic maps are a new subject of research as they provide better hyper-chaotic behavior than the one-dimensional chaos system. In 1963, the first chaotic attractor was found which led to development of chaos theory in many fields [13]. The hyper-chaotic system enhances randomness and indefiniteness; therefore, it is more popular in engineering applications. In [14], a 5D hyper-chaotic map was used to generate pseudorandom sequences. The obtained sequences were recombined for confusion and diffusion of image pixels. The two popular hyper-chaotic systems are Rössler [15] and Chua’s circuit [16]. Chen’s hyper-chaotic system [17] is also a popular technique to generate pseudorandom sequences and it is widely used by researchers for image encryption [18]. Authors in [19] used a 5Dhyper-chaotic system for secure communication, based on a microcontroller unit. New multidimensional chaotic systems were obtained in order to achieve better randomness and complex dynamical behavior [20,21,22,23]. High-dimensional systems, combined with neural networks, also provide high security and resistance against various attacks [24]. Recent research has been based on compressive sensing, where the input image is compressed to a smaller size which is, then, further embedded with secret data and encrypted to achieve highly secured image communication [25]. This method has an extra advantage of reserving less bandwidth while the data is transmitted to the receiver. Mathematical characteristics of chaotic attractors are rigorously studied. Sequences like the Halton sequence [26], which shows uniform behavior in space, cannot be used in cryptography. These sequences need to be scrambled to obtain non-uniform behavior for security applications. Research in [27], evaluated some pre-existing scrambling techniques of the Halton sequence and also proposed simple techniques, like increasing the number of points between the bases, in order to generate a random Halton sequence. In [28], a survey of randomized quasi-Monte Carlo methods was conducted to study the transformation of uniformly distributed sequences after applying scrambling methods. For better security, bit-level operators were applied on the shuffled image [29,30]. DNA-based pixel diffusion algorithms mainly focus on changing the gray pixel value to DNA base streams. Further, various DNA operations, like compliment or XOR, were applied among the base values to diffuse the pixels. Finally, the pixels were converted back to gray level values. DNA-fused chaos theory is a very popular and successful method for image pixel diffusion. These approaches are very sensitive to initial conditions and are resistant to various brute attacks. DNA-based encryption technique is blended with chaotic maps, hash functions and other methods to provide better security [31,32,33,34]. Authors in [35] generated random sequence, using coupled map lattice and chaotic map, which are then combined with the DNA method for image encryption. DNA encoding was also used for medical image encryption combined with chaotic maps in the frequency domain to achieve robustness in the proposed algorithm [36,37,38,39,40,41].
The proposed work focused on building a new chaotic map (HaLT map) by combining Logistic Tent map and the Halton sequence. This map can be used in many engineering applications where a system with high chaotic nature is required. In the proposed algorithm, a new HaLT map was used in multimedia security applications to provide better privacy from unauthorized users. In this work, two levels of scrambling process were applied to achieve high randomness among image pixels. The use of a HaLT map and inter–intra bit-level permutation was done to confuse the pixels in the first and second levels of the scrambling process, respectively. Further, a 5D hyper-chaotic map and DNA computations with seven operations were used in the diffusion stage. The initial and control parameters for the 5D chaotic map were generated using MD5 and SHA256 hash functions. The initial seed to the hash functions were pixels of the input image. This method generated a new key for every input image, making the algorithm resistant to cryptography attacks.
The main contributions of the proposed scheme are as follows,
- ➢
- A novel random sequence (HaLT map) generator is proposed, which combines a CLT map (Combined Logistic Tent map) and the Halton sequence.
- ➢
- A modified quantization unit is developed to sort the generated HaLT sequence for first level scrambling.
- ➢
- For second level scrambling, bit-level operations are performed for enhanced security.
- ➢
- MD5 and SHA256 hash functions are obtained from an original and scrambled image, respectively, and they are used to calculate the initial seeds for a 5D hyper-chaotic map.
- ➢
- A five-dimension chaotic map is used for DNA computing in order to provide great confidentiality and high security.
- ➢
- Pixel permutation is performed by double sorting in the quantization unit to efficiently change the pixel position of the matrix.
- ➢
- Seven DNA operations, namely ADD, SUB, MUL, XOR, XNOR, Right-Shift and Left-Shift, are performed to efficiently diffuse the pixels of the permutated image.
- ➢
- The selection of DNA rules and seven operations are carried out using the five chaotic sequences obtained from the 5D hyper-chaotic map.
2. Preliminaries
2.1. Halton Sequence
In statistics, Halton sequence is a standard low-discrepancy sequence which seems random but is deterministic in nature. This sequence generates points in space which cover the domain uniformly [26]. It is very popular among researchers because of its ease of implementation, due to its definition via the radical inverse function. Halton sequence is highly correlated between the inverse function and the base used for different dimensions, which results in poor randomization of the points in space. This sequence is generated using co-prime numbers as its base. If is an integer, then it can be expressed in terms of base as shown in Equation (1),
where, is the sequence of digits , is the number of points. The number in the Halton sequence is given in radical inverse of Equation (2), where all the digits are in the interval 0 to 1.
Consider, base the interval 0 to 1 is divided into half, then into a fourth, then eighth, and so on. Notice that the Halton sequence is basically filling the gaps between the intervals. This behavior is similar to uniform distribution. Therefore, to overcome this phenomenon, Halton sequences are randomized. Instead of using a traditional chaotic method for image scrambling, we proposed an algorithm to scramble Halton sequences using combined chaotic map to obtain a nondeterministic sequence for better pixel scrambling for image encryption applications.
2.2. Cryptographic Hashing
A cryptographic hash function is an algorithm that converts input data (message) into a fixed length of bit array (hash, digest, hash value). This function has many information security applications as it is able to withstand all known cryptanalytic attacks [1]. Using a dedicated algorithm [10,12,25,41], any input data can be converted to a secret hash value. The two hash functions used in the proposed work are:
2.2.1. MD5
Message Digest 5 is a hash function which gives 128 bits of hash value. It has a one-way function which converts any input data to fixed length, hexadecimal, output bits, in order to authenticate the original message.
2.2.2. SHA256
Secure Hash Algorithm-256 is a modified version of the MD5 algorithm, providing more security and authenticity to the original data. The hash value obtained by SHA can take years or decades to break, thus making it unbreakable. Another advantage of this function is its uniqueness, i.e., there are likely to be few, or no, collisions between the two hash values.
The detailed explanation of how these hash functions were used in the proposed work is discussed in Section 3.1.3.
2.3. Chaotic Maps
Chaotic maps are mathematical functions that exhibit chaotic behavior. These maps are used for generating random sequences for various engineering applications [6]. The two chaotic maps used in the proposed algorithm are:
2.3.1. Logistic Map
A logistic map is a member of the chaos family, represented in Equation (3),
where, µ is a positive number with range (3.5, 4). It is also known as biotic potential, which has a maximum capacity to generate chaotic values. and are the outputs in the range (0, 1) for and iteration, respectively. A bifurcation diagram of the logistic map is shown in Figure 1.
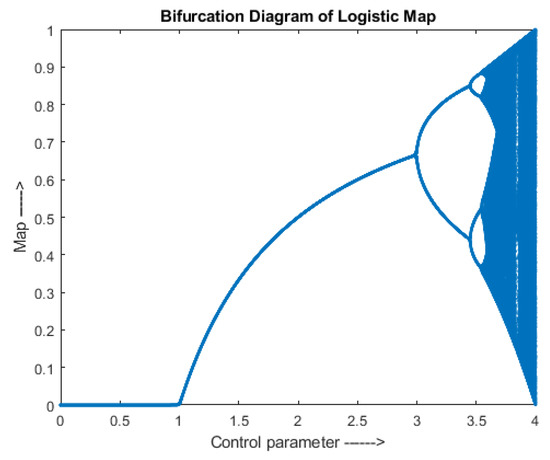
Figure 1.
Logistic Map-Bifurcation Diagram.
2.3.2. Tent Map
A tent map is a member of the chaos family, represented in Equation (4),
where, α is a positive number with range (2, 4), and are the outputs in the range (0, 1) for and iteration, respectively. A bifurcation diagram of a tent map is given in Figure 2.
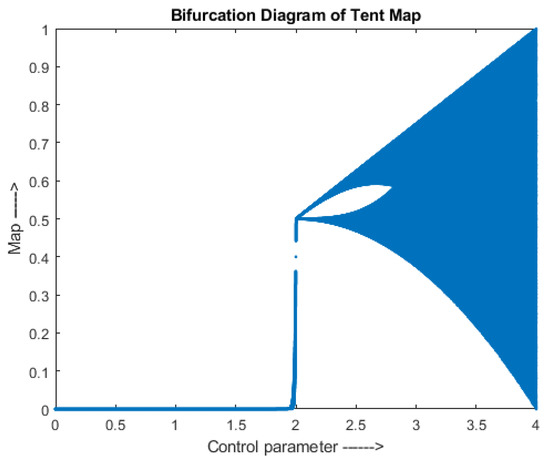
Figure 2.
Tent Map-Bifurcation Diagram.
2.3.3. Combined Chaotic Map: Combined Logistic-Tent (CLT) Map
The combined maps are obtained using Equation (5),
where, and are the two maps to be combined, is the initial value and is the control parameter of the maps. gives outputs in the range (0, 1) for iteration. A combined Logistic-Tent map was generated as per Equation (5) and it is represented in Equation (6), where is the logistic map, is the tent map, = (,) are the initial values of the logistic and tent maps, respectively, and = (,) are the control parameters of the logistic and tent maps.
and are in the range 3.5 to 4 and 2 to 4, respectively. The outputs and are in the range (0, 1) for and iteration, respectively. The bifurcation diagram is shown in Figure 3 which verifies that the map is chaotic in the range (0, 4).
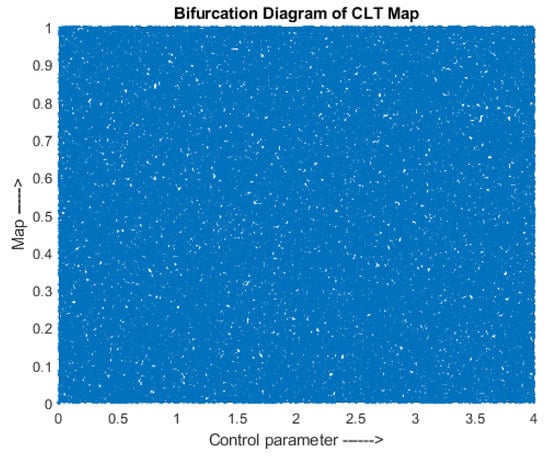
Figure 3.
Combined Logistic Tent map—Bifurcation diagram.
2.3.4. Hyper-Chaos System: 5D Hyper-Chaotic Map
Chaos theory is used in many fields, such as secured communication and mathematics. The logistic map discussed above is a one-dimensional chaotic map, used to generate random sequences for various applications. When hyper-chaotic systems are compared with lower dimension chaotic systems, they provide strong confidentiality, high randomness, more complex dynamic behavior, large key space and unpredictability with at least two positive Lyapunov exponents [22]. For any -dimensional Hyper-Chaotic map consisting of Lyapunov exponents, the following two conditions should be satisfied: firstly, the phase space, where the Hyper-Chaotic map exists, should be at least , which means the number of coupled first-order differential equations required are . Secondly, at least two terms should be present in the differential equations which provide dynamic instability, and at least one should be nonlinear in nature. In the proposed research, the following 5D Hyper-Chaotic attractor was used, which is shown in Equation (7). This system was derived from a 3D modified Lorenz system, by adding a coupling and a nonlinear feedback controller, which gave rise to two quadratic nonlinearities.
where, , > 0, > −, ≠ 0, , , , and are constant parameters, is the coupling coefficient and , are control parameters. The 3D and 2D projection of the 5D hyper-chaotic system is shown in Figure 4.
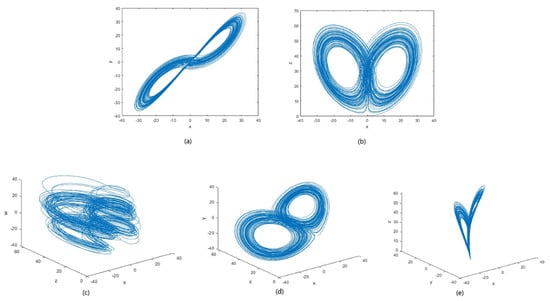
Figure 4.
Phase diagram of 5D Hyper−chaotic system with parameters (, , , , , , , ) = (35, 7, 35, −5, 10.6, 1, 5, 0.05). (a,b) 2D projection −, respectively. (c–e) 3D projection − − , − − , − − respectively.
2.4. DNA Computing for Cryptography
Genetic code in a living cell is a term used for the set of instructions that translates DNA information within genetic material into amino acid sequences of proteins. This encoding technique is a vast area of research, not only in the field of biology, but also in other branches, like science and engineering. A DNA sequence contains four types of proteins: namely, Adenine (A), Thymine (T), Cytosine (C), Guanine (G). The bases A and T are complementary, and G and C are complementary to each other. Similarly, in the binary system, 1 and 0 are complementary; therefore, 00 and 11 are also complementary, as are 10 and 01complementary to each other. Using DNA to encode a binary system 00, 11, 10 and 01, there are 4! = 24 combinations possible. Among these 24 combinations, only 8 kinds of bases satisfy the complementary rule, shown in Table 1 [38,39].

Table 1.
DNA Rules.
Randomly, a rule is chosen among eight rules in order to DNA encode image pixels. For example, consider a pixel value 156 in decimal is converted to binary value ‘10011100’. This binary sequence can be encoded to 8 kinds of amino acid strands, ‘GCTA’, ‘CGTA’, ’GCAT’, ‘CGAT’, ‘TAGC’, ‘ATGC’, ‘TACG’, ‘ATCG’, using the rules in Table 1. Among these 8 DNA sequences, any one rule is chosen for a particular pixel value. The seven possible DNA operations used in this work are: ADD, SUB, MUL, XOR, XNOR, Right Circular Shift and Left Circular Shift. These operations were derived based on fusing mathematics and biological operators, which are shown in Figure 5. The seven DNA operations were performed according to the binary ADD, SUB, MUL, XOR, XNOR operations. In right and left circular shift, the binary value of the image pixels was circularly shifted and the DNA encoded according to the rules given in Figure 5f,g. These operations were used to fuse the plain image pixels with key image pixels. In order to provide good security to the input images, a different operation was used for every pixel value.
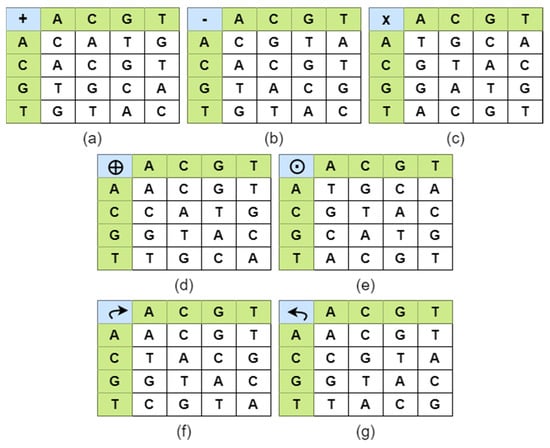
Figure 5.
DNA algebraic operations (a) ADD, (b) SUB, (c) MUL, (d) XOR, (e) XNOR, (f) Right circular shift, (g) Left circular shift.
3. Proposed Image Encryption Methodology
The proposed image encryption methodology consisted of two phases which are explained in the following subsections. Figure 6 gives the proposed block diagram.
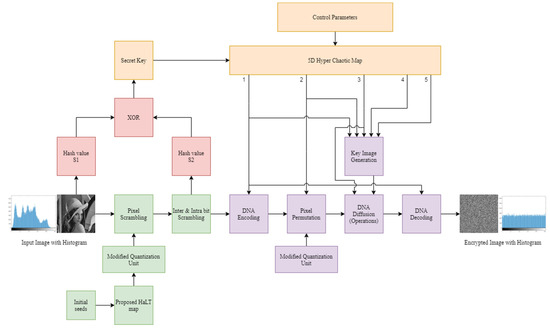
Figure 6.
Block Diagram of Proposed Image Encryption Method; 1–5 are the five sequences of 5D Hyper−chaotic map.
3.1. Phase 1
The encryption steps in this phase contain first level scrambling, with the proposed HaLT map, second level scrambling with bit-level operations, and seed generation, using hash functions for the diffusion process.
3.1.1. Proposed HaLT Map
As discussed earlier, Halton sequences are deterministic in nature and show uniform distribution in space. Therefore, there is a need to scramble the Halton sequence to use it in information security applications. In this research, the CLT chaotic map was used to efficiently scramble the Halton sequence.
The idea behind combining any two chaotic maps is given in Equation (5) and it is used in this method. Consider a Halton sequence obtained using Equation (2) with base , the 1000 points generated are given in Figure 7a. To generate a scrambled sequence, the combined chaotic-CLT map was used. As discussed earlier, the CLT map was obtained by combining logistic and tent chaotic maps, which showed high randomness in the range 0 to 1. Similarly, using Equation (5), the Halton sequence and CLT map were combined to get a new HaLT map for input image scrambling. The 1000 random points of the HaLT map in the interval 0 to 1 are shown in Figure 7b. Figure 7c shows 65,536 random points of the generated map for the application in [256 × 256] size image encryption.
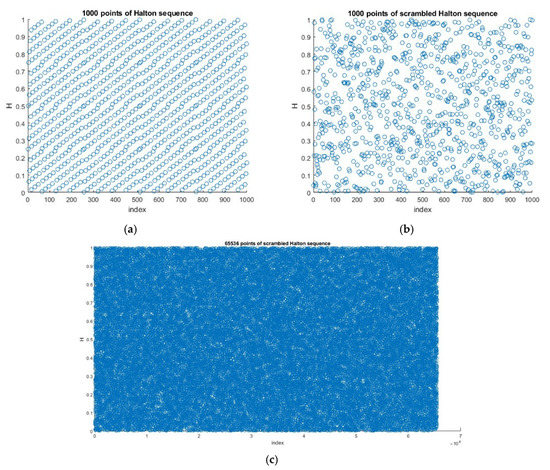
Figure 7.
(a) 1000 Halton sequence points for base = 4, (b) 1000 HaLT map points, (c) 65,536 HaLT map points.
In [6], the quantization unit was used for pixel scrambling, where the input image was mapped with the sorted chaotic map. Here, the HaLT map was double sorted, which was then mapped with the input image. Consider the generated HaLT sequence shown in Figure 8a. This sequence was sorted and the sorting order recorded as shown in Figure 8b. In the modified quantization unit, was arranged in ascending order to obtain as shown in Figure 8c. This sorted sequence was used to map the input image pixels given in Figure 8d. Finally, the first level of scrambled image was obtained, as shown in Figure 8e.
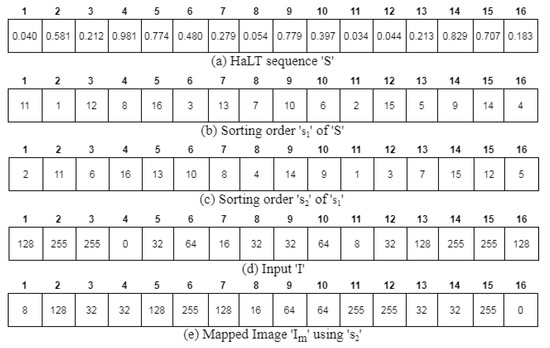
Figure 8.
Modified Quantization Unit; 1–16 are the number of pixels.
3.1.2. Bit-Level Operations
The next step in the first phase of the proposed methodology is inter- and intra-bit scrambling. The proposed bit scrambling algorithm scrambles the bits of the image pixels and the planes of the image. After the first level of image scrambling, bit plane slicing was done to extract the eight planes of the matrix. Now the odd and even number of planes were swapped among each other, as shown in Figure 9. In inter-bit scrambling, the even bit plane pixels were flipped up to down, using Equation (8), where and were the new and old bit plane arrays, respectively, is the function in MATLAB which flips the array up to down, and is the index for bit plane varying from 1 to 8. The image arrays were then converted from binary to decimal values and reshaped to the size of the original image to obtain a final scrambled image .
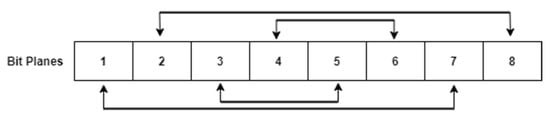
Figure 9.
Intra-bit scrambling; 1–8 are the eight planes of the image.
3.1.3. Seed Generation Using Hash Functions
The last step of the first phase was to generate initial seeds for the 5D hyper-chaotic map. In this method, SHA-256 and MD5 hash functions were used. Two hashes were obtained, one from the original image and another from the scrambled image, which were then XOR to create the seed for the chaotic map. Hash functions play a vital role in cryptography, because they are irreversible in nature and they can resist many attacks. Since SHA-256 and MD5 can generate 256 and 128 bits, respectively, they were used in the proposed algorithm to provide better security and prevent various attacks. The number of rows and columns of the original image were considered as .
A pixel value at a particular location can be represented as , where is the original image and is the row and column. Three vectors of size , of size and of size [] were generated from the original image. Here was the sum of all the pixels in the row, was the sum of all the pixels in the column and was the sum of all the pixels across diagonal of image . The MD5 algorithm was applied on all the three vectors using Equation (9), and then SHA-256 function was applied on the resultant hash value obtained from the previous MD5 algorithm to get a 32-bit hash value, using Equation (10). The above hash value generation algorithm was also applied on the scrambled image to get another 32-bit value. The two hash values obtained were further XOR, as given in Equation (11); the resultant initial seed was used as initial seed for the Hyper-Chaotic map in the next phase, where, and are the MD5 hash values obtained from the original image and the scrambled image, respectively. Then, . and were the SHA-256 hash values obtained from and respectively. was the final 32-bit key used as initial seed in the further steps of proposed algorithm.
3.2. Phase 2
The encryption steps in this phase contained the 5D hyper-chaotic map, key image generation and, finally, DNA computing.
3.2.1. D Hyper-Chaotic Map
The generated 32-bit key in the first phase was given as an input for the initial seed of the 5D hyper-chaotic map defined in Equation (7). The control parameters used were (, , , , , , , ) = (35, 7, 35, −5, 10.6, 1, 5, 0.05). Map values and were initialized using key as shown in Equation (12), where was obtained by XOR the first six values of key . Similarly, the remaining values and were calculated by applying XOR operation on the consecutive six values in the key. After initializing the values, the 5D system was pre-iterated for [] times to remove any transition effect. Then, the map was iterated for [] times to obtain five chaotic sequences. These sequences were normalized from 0 to 1 using Equation (13), in order to be utilized for key image generation and DNA computing. Where, was the five sequences , the was floor value.
3.2.2. Key Image Generation
The map obtained after [] times iteration was normalized from 0 to 255, using Equation (14). The key image of size [] was obtained from Equation (15), where ‘’ was the key image, and were the normalized sequences and was the index position.
3.2.3. DNA Computing
The steps used in DNA computing were DNA first level encoding, DNA diffusion (operations) and DNA second level encoding.
- DNA Encoding
The scrambled image and the key image were first-level encoded with the help of the 8 DNA rules, shown in Table 1. To randomly choose any one rule among eight DNA rules, sequence was normalized in the range 1 to 8, using Equation (16), where was a vector containing values from 1 to 8.
The scrambled image and key image were DNA encoded to get and , where each pixel value used a different rule which was randomly chosen by the vector . Modified quantization unit was applied on the sequence and mapped with the encoded image to obtain a permutated image .
- DNA Diffusion
As mentioned in earlier sections, seven DNA operations were used in order to diffuse the DNA encoded scrambled image. For every pixel a different operation was used from the seven operations, namely ADD, SUB, MUL, XOR, XNOR, Right Circular Shift and Left Circular Shift, as shown in Figure 5. To randomly choose one operation among the seven, chaotic sequence was normalized in the range 1 to 7, using Equation (17), where was a vector containing values from 1 to 7, was the index value.
DNA operations were selected as follows:
The above operations were applied on the permutated image and encoded key image to get a diffused image . For every pixel value a different operation was used to ensure better security in the algorithm. The vector randomly chose an operation for a particular pixel to be diffused.
- DNA Encoding
In order to obtain the final encrypted image, , the diffused matrix obtained from the above step was second level DNA encoded. The vector was used to select a rule from the eight DNA rules to encode every pixel.
3.3. Proposed Algorithm Steps
This section gives the step-by-step explanation of the encryption Algorithm 1.
| Algorithm 1. Proposed Image Encryption Algorithm |
| Input—Gray Image of size , control parameters for hyper-chaotic map, (,, , , , , , ) = (35, 7, 35, −5, 10.6, 1, 5, 0.05), parameters for logistic map , parameters for tent map , parameters for Halton sequence . Output—Encrypted Gray Image of size . Step 1:-Input gray scale image of size . Step 2:-Initialize CLT map shown in Equation (6) with control parameters and initial condition, . Iterate it for finite number of times to remove transient effect. Continue iterating the map for times. This process created a chaotic sequence of size . Step 3:-Generate Halton sequence using Equations (1) and (2) of size . Step 4:-Combine the CLT map and Halton sequence, using Equation (5), to form a new chaotic sequence (HaLT map) of size . Where is the CLT map and is the Halton sequence. Step 5:-As shown in Figure 9 (Modified Quantization Unit), double sort the HaLT sequence and map it with the input image to get scrambled image . Step 6:-Using bit plane slicing technique extract the eight planes of the image . Step 7:-Intra-bit scrambling—Swap odd and even number of planes, as shown in Figure 9. Step 8:-Inter-bit scrambling—Flip all the even plane pixels up to down, using Equation (8). Step 9:-Convert the values from binary to decimal and reshape the matrix to size to obtain a final scrambled image . Step 10:-Generate three vectors (sum of all rows), (sum of all columns) and (sum of all pixels across diagonal) of both original image and scrambled image . Step 11:-Apply MD5 hash function on , and using Equation (9). Further apply SHA256 hash function, as given in Equation (10), to generate two 32-bit hash values and . Using Equation (11), XOR and to obtain . Step 12:-Using for initial seed calculation, as given in Equation (12), and control parameters as (,, , , , , , ) = (35, 7, 35, −5, 10.6, 1, 5, 0.05) generate 5D Hyper-Chaotic map given in Equation (7). Iterate the map for finite number of times to remove transient effect. Continue iterating the map for times. This process created a chaotic sequence of size . Step 13:-Key Image Generation—Normalize all five chaotic sequences in the range 0 to 255, using Equation (14). Key Image of size [] was formed, using Equation (15). Step 14:-The sequences obtained from Step 12 were normalized in the range 0 to 1, using Equation (13). Step 15:-DNA Encoding (level 1)—To randomly choose the eight DNA rules for encoding the scrambled image and key image , the sequence was normalized into values from 1 to 8, using Equation (16). The normalized sequence randomly chose a rule and encoded and to obtain and . Step 16:-Pixel permutation—Modified quantization unit was applied on the sequence and mapped with the encoded image to obtain a permutated image . Step 17:-DNA Diffusion—To randomly choose the seven DNA operations to apply between and , sequence was normalized in the range 1 to 7, using Equation (17). The normalized sequence randomly chose an operation to be performed between and to obtain a diffused image . Step 18:-DNA Encoding (level 2)—Vector was used to encode the diffused image to get the final encrypted image . |
The decryption process was the reverse of the proposed encryption algorithm.
4. Results and Discussion
The results and detailed discussions on the generated HaLT map and proposed image encryption technique are demonstrated in this section. Various tests and security analyses were performed to estimate the efficiency and robustness of the proposed work. Experiments were performed by MATLAB2020a on Windows 7 OS, Intel(R) Core(TM) i5-4570U CPU 3.20GHz, 4 GB RAM.
4.1. Simulation Results of Proposed HaLT Map
NIST test, correlation analysis, Lyapunov exponent spectrum and spectral entropy complexity analysis were performed on the HaLT map, described in the subsections below.
4.1.1. NIST Test
The National Institute of Standards and Technology (NIST) is an important document used to analyze the strength of randomness in a sequence. A total of 15 tests were performed on the generated sequence and on the final encrypted image. Table 2 tabulates the results obtained to check whether the generated values are suitable for cryptographic applications. The generated HaLT map was normalized in the range 0 to 255, using Equation (14) to get , then converted to binary values, using Equation (18) for the NIST test. The encrypted image pixels were also converted to binary values, using Equation (18), for the NIST test. Figure 10 shows the 1000 generated HaLT random sequence. The test results show that the proposed HaLT map passed all 15 NIST randomness tests.

Table 2.
NIST Test Result of Generated Random Sequence of Size 256 × 256 = 65,536 and on seven encrypted images.
Figure 10.
Generated HaLT Sequence.
4.1.2. Correlation
Figure 11 shows the correlation analysis of the generated sequence. The auto-correlation of the sequence is given in Figure 11a. Figure 11b shows the cross-correlation of the two sequences when one of the bits was changed in the initial condition of the CLT map. The correlation plot showed the sensitivity towards initial conditions of the generated HaLT map.
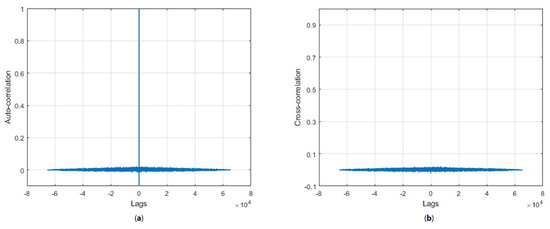
Figure 11.
Correlation analysis of the generated sequence (a) auto correlation plot, (b) cross correlation plot.
4.1.3. Lyapunov Exponent Spectrum
In mathematics, Lyapunov exponents are the measure of a dynamic system’s sensitivity to change in its initial conditions. It is an essential method to determine the rate of exponential separation of close trajectories. The separation rate can be different for different initial conditions. Therefore, to determine convergence or divergence of the system in phase space, the Lyapunov exponent spectrum was plotted [42]. The positive maximal Lyapunov exponent determined that the dynamic system was chaotic in nature.
If the Lyapunov exponent was negative, the behavior of the system would be non-chaotic. The evolution equation of a dynamic system, defined by Equation (19), and the spectrum of Lyapunov exponents were given by Equation (20),
Figure 12 is the plot of the Lyapunov exponent spectrum for the logistic map, tent map, CLT map and proposed HaLT map. The spectrum plot shows that the HaLT map provided positive maximal Lyapunov exponents for a larger range, as compared to other standard chaotic maps. Therefore, the derived HaLT map had chaotic behavior and it was more suitable for cryptographic applications.
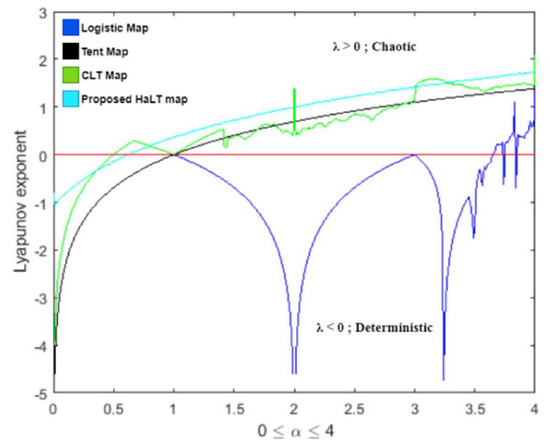
Figure 12.
Lyapunov exponent spectrum of logistic map, tent map, CLT map and proposed HaLT map.
4.1.4. Information Spectral Entropy Analysis
The generated HaLT sequence dynamic complexity was determined by Spectral Entropy (SE) analysis. In this paper, the spectral entropy complexity algorithm [43] was used to calculate the behavior complexity of the generated sequence. The SE value was normalized in the range 0 to 1. A greater SE value determined the stronger chaotic nature of the system. Using such random systems for communication purposes gives high information security. The smaller SE value corresponded to lesser complexity in the system, otherwise complexity was high. Figure 13a plots the bifurcation diagram of the generated chaotic sequence, where the map was chaotic in the entire parameter range. Change in system control parameters influenced SE, with r (0, 4), as shown in Figure 13b. This plot showed that the SE value was large, with negligible fluctuation, depicting the chaotic nature of the system throughout the parameter range. Figure 13c denotes the chaotic characteristics distribution of the generated sequence versus the system control parameter, r (0, 4), and the Halton sequence base value b (2, 10). To observe the SE distribution more clearly, the color range of the contour plot was taken from 0.5 (white) to 1 (black). The main color on the contour plot was brown, depicting a larger SE value in the range 0.8971 to 0.9459, showing the chaotic nature of the generated system in the entire parameter range. Therefore, the proposed HaLT map is spectrally efficient and it is more suitable for image encryption applications.
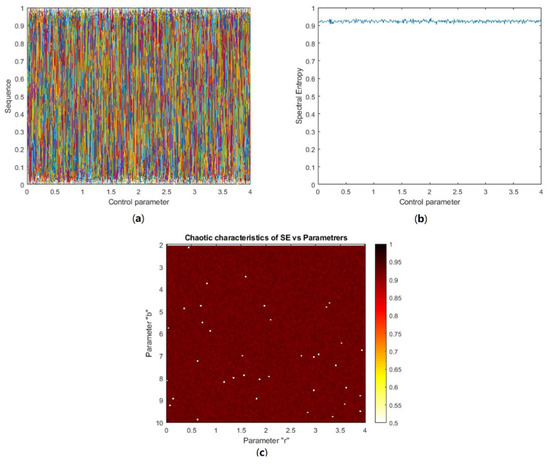
Figure 13.
(a) Bifurcation diagram of HaLT map; different colors show the results for different initial values and control parameters, (b) SE vs. control parameter (0 ≤ r ≥ 4) plot, (c) Chaotic characteristics of SE verses parameters of the system, with 0 ≤ r ≥ 4 and 2 ≤ b ≥ 10.
4.2. Simulation Results of Proposed Image Encryption Algorithm
In this section, various simulations and tests were performed on five test images [44], which are displayed in Figure 14: namely, Lena, Baboon, Goldhill, Cameraman and Bridge of size []. The simulation results were compared with the ‘state of the art’ techniques [18,35,36,38,41,45,46,47,48,49], on the basis of correlation, information entropy, NPCR, UACI, cropping attack and noise attack. The subsections below show the various tests performed on the proposed method.

Figure 14.
Test Images (a) Lena, (b) Baboon, (c) Goldhill, (d) Cameraman, (e) Bridge.
4.2.1. Statistical Attacks
The statistical analyses performed on the proposed algorithm were histogram analysis, correlation analysis, chi-square test, information entropy and deviation from ideality.
- Histogram Analysis
A histogram is basically a graphical plot of gray intensity levels and pixel distribution in an image. For a secure and robust encryption algorithm, the cipher image was validated on the basis of a uniformly distributed, flat histogram plot for all gray level values. For all five input images, histogram analysis is given in Figure 15, where the cipher images exhibited a uniformly distributed flat histogram plot.
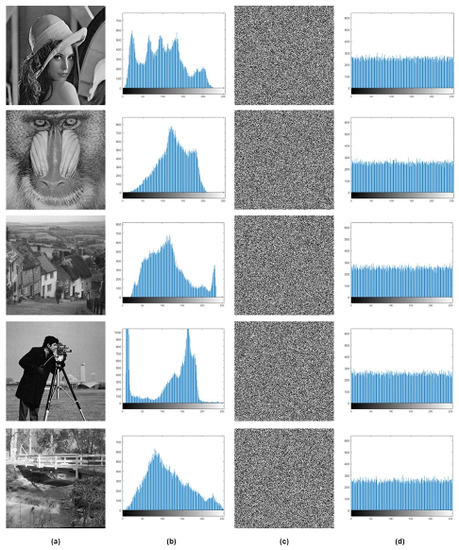
Figure 15.
Histogram analysis, x-axis in histogram plot represents gray level values and y-axis represents number of pixels (a) Test Images, (b) Test images histogram plot, (c) Cipher Images, (d) Cipher images histogram plot.
For histogram quantity analysis, a variance of five cipher images is tabulated in Table 3. Most importantly, there were five secret keys (b, µ, α, p(0) and S) used in the proposed encryption algorithm. We also calculated the variance of the same cipher image when any of the five secret keys were changed. Table 1 also shows the % change in the variance value compared with the encrypted image when one of the keys was changed. It was observed that the algorithm was very sensitive to the initial conditions. A lower value of variance indicated higher uniformity in the cipher image histogram [50]. The variance of the Lena plain image was 632100. As shown in the table, the proposed method was very sensitive to the hash key ‘S’. Even one bit change in the hash value gave around 10% difference in variance. The % variance difference in the cipher image showed that the algorithm was extremely sensitive to initial conditions and also depended on the input plain image. Therefore, the proposed work was robust to any statistical attacks. The histogram variance was calculated, using Equation (21), where was the number of gray level values, and were the number of pixels at and graylevel and the vector of histogram values .

Table 3.
Histogram variance analysis of encrypted images.
- Correlation Coefficient
The correlation analysis is a test to check the connection between the pixels. Usually, pixels in plain images have high correlation among themselves in all directions. However, for cipher images, this correlation coefficient should be near to zero. Table 4 tabulates the correlation analysis done on all the test images, and the results obtained were compared with the existing techniques [18,35,36,38,41,45]. The correlation values for the test images were very close to the ideal value 0, and also better than many ‘state of the art’ techniques. The comparison showed that the algorithm broke the correlation between the adjacent pixels and could resist statistical attacks. The left and right column of Figure 16 show the pixel distribution of two adjacent horizontally, vertically and diagonally arranged pixels in the original image and encrypted image, respectively. It was observed that the correlation of input image was very close to 1. Whereas, after applying the proposed algorithm on the plain image, the strong correlation among pixels broke and it was scattered throughout the plane. The equations to calculate correlation analysis are shown in Equations (22)–(24), where and represent gray level intensity of the two adjacent pixels, is the number of pixel pairs, is variance, is covariance and is the correlation coefficient.

Table 4.
Correlation Analysis.
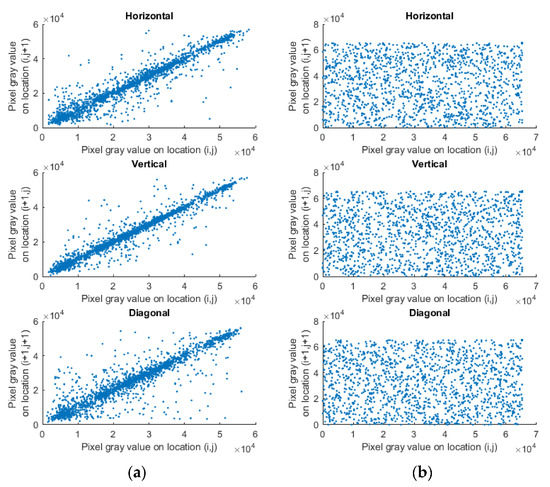
Figure 16.
Correlation plot in all three directions (a) Input image, (b) Cipher image.
- Chi-square Analysis
Unlike histogram analysis, which gives a visual representation of pixel distribution, the chi-square test delivers the statistical representation of the pixel uniformity across the gray scale intensities. The test performed on cipher images is given in Table 5, which tabulates the chi-square value and p-value. The values obtained were compared with the 5% and 1% probabilities for d = 255 degrees of freedom and passed all the tests, showing uniform distribution of pixel values. Equation (25) gives the chi-square test formula, where is the gray scale values expected to be 256 for image size, is the observed value and is the expected value.

Table 5.
Chi-Square Analysis.
- Information Entropy
Entropy measures the uncertainty of a message in an image. This value for cipher images having highest uncertainty was expected to be approximately equal to 8. The entropy for the original image and resultant cipher image of the proposed algorithm are tabulated in Table 6; the results obtained were compared with the existing techniques [18,35,36,38,41,45,51]. The values of encrypted images were almost equal to 8 showing high randomness of information in the image and were also better than many ‘state of the art’ techniques. The formula of entropy is given in Equation (26), where is the length of pixel value in bits, is the probability of symbol in message .

Table 6.
Information entropy analysis.
- Deviation from Ideality
It is a property which measures the deviation of a resultant encrypted image from an ideal cipher image. The formula to obtain an ideal cipher image is given in Equation (27) and the deviation formula is given in Equation (28), where is the deviation, and represents the histogram of the encrypted image and of the original image, respectively. To generate a cipher image of size , the number of pixels for all the gray level should be equal to 256, is the intensity level from 0 to 255. The results obtained for all test images are tabulated in Table 7 and showed a lot less deviation from the resultant encrypted images than from the ideal cipher images.

Table 7.
Deviation from Ideality.
4.2.2. Differential Attacks
The differential analyses of Number of Pixel Change Rate (NPCR) and Unified Average Change in Intensity (UACI) were performed on the proposed algorithm which showed the performance of proposed work when a random pixel is changed in the original image. Table 8 tabulates NPCR and UACI values of the obtained encrypted images when a single bit is randomly changed in the input image. The expected values were: NPCR = 99.6094% and UACI = 33.4635% [52]. The results obtained were near to the expected values and compared with the ‘state of art’ techniques [18,35,38,41,45,53]. The values of encrypted images were all in the critical range, showing high sensitivity towards input image and were also better than many ‘state of the art’ techniques. The analysis performed on the proposed method showed that it could resist various differential attacks as it passed all the critical values. Differential analysis was performed on 100 test images of size . The obtained results are in Figure 17, which shows that all the test images were near to the expected value of NPCR and UACI.

Table 8.
Differential Attack Analysis.
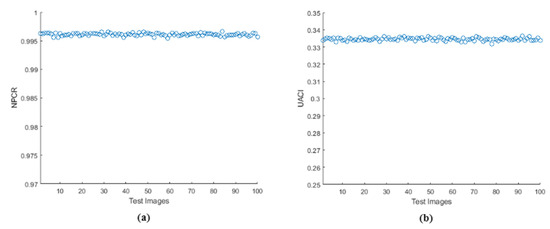
Figure 17.
Differential analysis for 100 test images (a) NPCR, (b) UACI.
- NPCR
This metric calculates the percentage change which occurred in the cipher image when one bit of the input image was changed. The NPCR formula is stated in Equation (29), where and are the encrypted images before and after randomly changing one bit at index position of the input image.
- UACI
This metric calculates the average intensity change in pixels when one bit is randomly replaced in the original image. UACI formula is stated in Equation (31),
4.2.3. Key Space and Key Sensitivity Analysis
The most important aspect in an image encryption algorithm is key security analysis. Key space is the maximum possible keys used to encrypt the image. Larger key space will provide more security to an image [54]. In the proposed technique, for generating the HaLT map, two keys for initial condition with 10−2 precision, two keys for control parameter with 10−1 precision and one key for base parameter were used. For generation of the 5D hyper-chaotic map two 256-bit hash keys and seven control parameters with 10−2 precision were required. Hence, an approximately 608-bit key (each key had 8 bits), i.e., 76 Bytes of key, is required to decrypt the image. The key space required was more than 2608, which is large enough to maintain a high security level to resist against brute force attack.
The decryption algorithm, which is extremely sensitive to the initial secret keys used in the encryption algorithm, is considered to be a good method. Even a single bit modification in the encryption key should result in the decryption algorithm failing. The key sensitivity test was performed on test image Lena, illustrated in Figure 18, where Figure 18a is the input image; Figure 18b had single bit change in the initial secret key of the HaLT map generator and Figure 18c had a single bit change in the hash value; showing approximately 99.3% change from the correctly decrypted image, shown in Figure 18d.
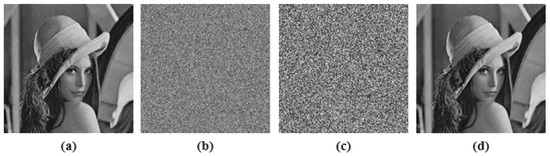
Figure 18.
Key sensitivity analysis; (a) Input image, (b) Decrypted image when single bit changed in HaLT map key, (c) Decrypted image when single bit changed in hash key, (d) Correctly decrypted image.
4.2.4. Robustness Analysis
This is the measure to test the strength of the proposed image encryption algorithm to withstand adverse conditions. Cropping attack and noise attack is performed in order to test the algorithm. The Peak Signal to Noise Ratio (PSNR) was calculated for all the input images and their corresponding decrypted images to tabulate the quality of the decryption algorithm, given in Table 9. The tabulation also compared the proposed work with ‘state of the art; techniques [41,45,46,47], and shows that the values obtained were approximately equal to the existing methods. Figure 19 shows the 6.25%, 25% and 50% cropping attack analysis on the Lena test image. The results show that even after 50% cropping of the encrypted image, the decryption algorithm was able to decode the original image, which makes the algorithm robust against cropping attack. For noise attack analysis, salt and pepper noise, with 0.005, 0.05 and 0.1 densities, were used, as demonstrated in Figure 20. The decrypted image showed that the proposed work was robust against noise attack.

Table 9.
Robustness analysis.
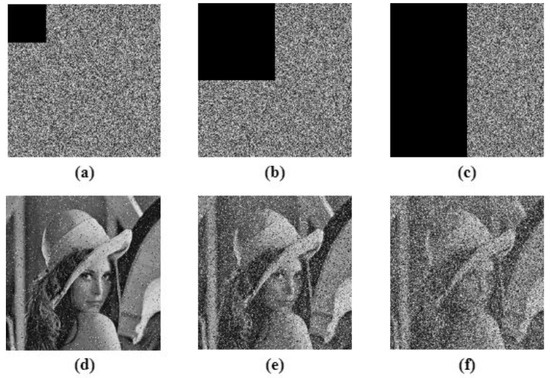
Figure 19.
Cropping attack analysis, (a–c) are 6.25%, 25% and 50% cropping of cipher images respectively, (d–f) are the corresponding decrypted image.
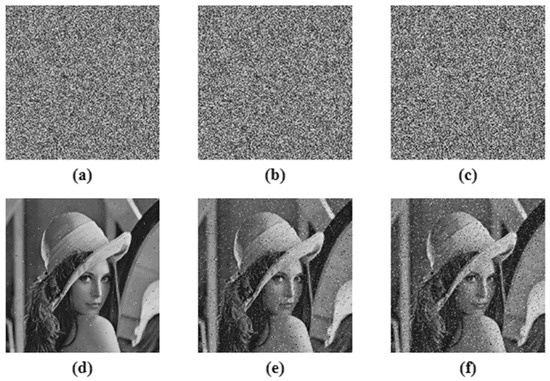
Figure 20.
Noise attack analysis, (a–c) are 0.005, 0.05 and 0.1 noise density cipher images respectively, (d–f) are the corresponding decrypted image.
4.2.5. Cryptanalytic Attacks
Cryptanalysis is a study in cryptology which helps to find flaws or imperfections in encryption algorithms. In order to find fault in the method we have to attack and then analyze the system with the following [55]:
- Ciphertext Only Analysis (COA): In this type of attack, the attacker knows some ciphertext and tries to find the encryption key and plain text.
- Chosen Plaintext Analysis (CPA): In this, the attacker knows the encryption algorithm, chooses a random plaintext and generates a cipher text to find the encryption key.
- Known Plaintext Analysis (KPA): In this, the attacker maps the known plain text and cipher text to figure out the encryption key.
- Chosen Ciphertext Analysis (CCA): Here the attacker knows the decryption algorithm and tries to find the plain text by using a random cipher text.
Among the cryptanalytic attacks discussed above, CPA is the most common and a powerful attack. This attack analysis is done for encryption algorithms where, in particular, XOR operation is performed for diffusing image pixels. The equation used is given in Equation (32), where and are the two test images, Lena and Baboon, and and are the two corresponding to cipher images. Figure 21 shows that the proposed algorithm did not justify Equation (32); therefore, it could resist chosen plain text attack.
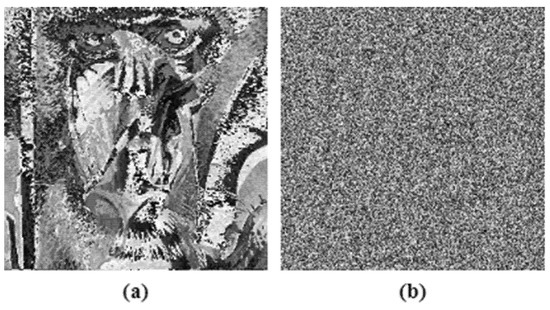
Figure 21.
Chosen plain text analysis (a) , (b) .
If the proposed system can pass the CPA test, then it is resistible to other types of attacks. As discussed in Section 4.2.3, the encryption algorithm is extremely sensitive to initial conditions. The encryption key depends on the plain image itself, which makes it difficult for the attacker to predict the key because it keeps changing with the input plain image.
4.2.6. Execution Time Analysis
In today’s world of internet and big data, time analysis plays an important role for encryption algorithms. The execution time for encryption and decryption algorithms on test images are tabulated in Table 10, and compared with exciting techniques [45,46,48,49,56]. All the references used 256 × 256 image size, 4 GB or more RAM size and i5+ core processor. The results obtained showed that the proposed method ran faster than other algorithms and also provided better security.

Table 10.
Execution Time Analysis.
5. Conclusions
In this research work, we proposed a two-phase image encryption method for secure communication. In the first phase, three methods were used: HaLT map generator, bit-level operation and double sorting quantization unit for pixel scrambling. A method was proposed to generate a random sequence by combining CLT map and Halton sequence to derive a HaLT map for cryptographic applications. Hash values were obtained individually from the original image and the scrambled image using a combination of MD5 and SHA-256 hash function algorithms. The obtained two hash values were then XOR which was fed to the next phase. The new hash value obtained after XOR was used as seed for a 5D hyper-chaotic map in the second phase. The five pseudorandom sequences generated by the 5D map were used for DNA first level encoding, key image generation, DNA operations and DNA second level encoding. Firstly, the scrambled image obtained from the first phase of the proposed algorithm was DNA encoded. Then, pixel permutation was done by applying the quantization unit on the encoded image. Random sequences obtained from the hyper-chaotic map were used to generate the key image. The permutated image and the key image were diffused using seven DNA operations, namely ADD, SUB, MUL, XOR, XNOR, Right-Shift and Left-Shift. DNA second phase encoding was done on the diffused image to get the final cipher image. The simulation results showed that the proposed HaLT map generator and image encryption algorithm provide high security as they resist various cryptography attacks and are fast for practical applications.
Author Contributions
S.P. and T.V. conceptualization, S.P. and T.V. formal analysis, T.V. funding acquisition, S.P. and T.V. investigation, S.P. and T.V. methodology, T.V. supervision, S.P. and T.V. validation, S.P. writing-original draft, T.V. writing-review and editing. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by SENSE School, Vellore Institute of Technology, Vellore, India.
Institutional Review Board Statement
The study was not involving humans or animals.
Informed Consent Statement
Not applicable.
Data Availability Statement
http://sipi.usc.edu/database/database.php?volume=misc (accessed on 20 February 2022).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Stallings, W. Cryptography and Network Security: Principles and Practice, 5th ed.; Prentice Hall Press: Upper Saddle River, NJ, USA, 2010. [Google Scholar]
- Wang, X.; Feng, L.; Zhao, H. Fast image encryption algorithm based on parallel computing system. Inf. Sci. 2019, 486, 340–358. [Google Scholar] [CrossRef]
- Wang, X.; Yang, J. A privacy image encryption algorithm based on piecewise coupled map lattice with multi dynamic coupling coefficient. Inf. Sci. 2021, 569, 217–240. [Google Scholar] [CrossRef]
- Wang, X.; Liu, P. A New Full Chaos Coupled Mapping Lattice and Its Application in Privacy Image Encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2022, 69, 1291–1301. [Google Scholar] [CrossRef]
- Wong, K.W. Image Encryption Using Chaotic Maps. In Intelligent Computing Based on Chaos; Springer: Berlin/Heidelberg, Germany, 2009; Volume 184, pp. 333–354. [Google Scholar]
- Patel, S.; Thanikaiselvan, V.; Pelusi, D.; Nagaraj, B.; Arunkumar, R.; Amirtharajan, R. Colour image encryption based on customized neural network and DNA encoding. Neural Comput. Appl. 2021, 33, 14533–14550. [Google Scholar] [CrossRef]
- Wang, X.; Gao, S. Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Inf. Sci. 2020, 539, 195–214. [Google Scholar] [CrossRef]
- Wang, X.; Gao, S. Image encryption algorithm for synchronously updating Boolean networks based on matrix semi-tensor product theory. Inf. Sci. 2020, 507, 16–36. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X. Fractal sorting matrix and its application on chaotic image encryption. Inf. Sci. 2021, 547, 1154–1169. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X. Color image encryption based on one-time keys and robust chaotic maps. Comput. Math. Appl. 2010, 59, 3320–3327. [Google Scholar] [CrossRef] [Green Version]
- Liu, H.; Wang, X. Color image encryption using spatial bit-level permutation and high-dimension chaotic system. Opt. Commun. 2011, 284, 3895–3903. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X.; Kadir, A. Image encryption using DNA complementary rule and chaotic maps. Appl. Soft Comput. 2012, 12, 1457–1466. [Google Scholar] [CrossRef]
- Lorenz, E.N. Deterministic nonperiodic flow. J. Atmos. Sci. 1963, 20, 130–141. [Google Scholar] [CrossRef] [Green Version]
- Fang, D.; Sun, S. A new secure image encryption algorithm based on a 5D hyperchaotic map. PLoS ONE 2020, 15, e0242110. [Google Scholar] [CrossRef]
- Rossler, O. An equation for hyperchaos. Phys. Lett. A 1979, 71, 155–157. [Google Scholar] [CrossRef]
- Kapitaniak, T.; Chua, L.O. Hyperchaotic Attractors of Unidirectionally-Coupled Chua’s Circuits. Int. J. Bifurc. Chaos 1994, 4, 477–482. [Google Scholar] [CrossRef]
- Tong, X.; Chen, P. A joint image lossless compression and encryption method based on chaotic map. Multimed. Tools Appl. 2017, 76, 13995–14020. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, X. A fast image encryption scheme based on integer wavelet and hyper-chaotic system. In Proceedings of the IEEE International Conference on Artificial Intelligence and Big Data (ICAIBD), Chengdu, China, 26–28 May 2018; pp. 139–143. [Google Scholar]
- Peng, Z.; Yu, W.; Wang, J.; Zhou, Z.; Chen, J.; Zhong, G. Secure Communication Based on Microcontroller Unit with a Novel Five-Dimensional Hyperchaotic System. Arab. J. Sci. Eng. 2022, 47, 813–828. [Google Scholar] [CrossRef]
- Yang, Q.; Bai, M. A new 5D hyperchaotic system based on modified generalized Lorenz system. Nonlinear Dyn. 2017, 88, 189–221. [Google Scholar] [CrossRef]
- Wolf, A.; Swift, J.B.; Swinney, H.L.; Vastano, J.A. Determining Lyapunov exponents from a time series. Phys. D Nonlinear Phenom. 1985, 16, 285–317. [Google Scholar] [CrossRef] [Green Version]
- Yang, Q.; Chen, C. A 5D Hyperchaotic System with Three Positive Lyapunov Exponents Coined. Int. J. Bifurc. Chaos 2013, 23, 1350109. [Google Scholar] [CrossRef]
- Hu, G. Generating Hyperchaotic Attractors with Three Positive Lyapunov Exponents via State Feedback control. Int. J. Bifurc. Chaos 2009, 19, 651–660. [Google Scholar] [CrossRef]
- Wang, X.-Y.; Yang, L.; Liu, R.; Kadir, A. A chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn. 2010, 62, 615–621. [Google Scholar] [CrossRef]
- Wang, X.; Liu, C.; Jiang, D. A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3D DCT. Inf. Sci. 2021, 574, 505–527. [Google Scholar] [CrossRef]
- Halton, J.H. On the efficiency of certain quasi-random sequences of points in evaluating multi-dimensional integrals. Numer. Math. 1960, 2, 84–90. [Google Scholar] [CrossRef]
- Ostadkalayeh, A.M.; Vajargah, B.F. The scrambles of Halton sequence and thier weaknesses. J. Hyperstruct. 2021, 9, 40–53. [Google Scholar]
- Ökten, G.; Liu, Y. Randomized quasi-Monte Carlo methods in global sensitivity analysis. Reliab. Eng. Syst. Saf. 2021, 210, 107520. [Google Scholar] [CrossRef]
- Es-Sabry, M.; El Akkad, N.; Merras, M.; Saaidi, A.; Satori, K. A new image encryption algorithm using random numbers generation of two matrices and bit-shift operators. Soft Comput. 2020, 24, 3829–3848. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, X. Multiple-image encryption algorithm based on bit planes and chaos. Multimed. Tools Appl. 2020, 79, 20753–20771. [Google Scholar] [CrossRef]
- Barik, R.C.; Changder, S. A novel and efficient amino acid codon based medical image encryption scheme colligating multiple chaotic maps. Multimed. Tools Appl. 2021, 80, 10723–10760. [Google Scholar] [CrossRef]
- Zhou, S.; Wang, B.; Zheng, X.; Zhou, C. An Image Encryption Scheme Based on DNA Computing and Cellular Automata. Discret. Dyn. Nat. Soc. 2016, 2016, 5408529. [Google Scholar] [CrossRef] [Green Version]
- Nandy, N.; Banerjee, D.; Pradhan, C. Color image encryption using DNA based cryptography. Int. J. Inf. Technol. 2021, 13, 533–540. [Google Scholar] [CrossRef]
- Chai, X.; Fu, X.; Gan, Z.; Lu, Y.; Chen, Y. A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Processing 2019, 155, 44–62. [Google Scholar] [CrossRef]
- Tian, J.; Lu, Y.; Zuo, X.; Liu, Y.; Qiao, B.; Fan, M.; Ge, Q.; Fan, S. A novel image encryption algorithm using PWLCM map-based CML chaotic system and dynamic DNA encryption. Multimed. Tools Appl. 2021, 80, 32841–32861. [Google Scholar] [CrossRef]
- Banu, S.A.; Amirtharajan, R. A robust medical image encryption in dual domain: Chaos-DNA-IWT combined approach. Med. Biol. Eng. Comput. 2020, 58, 1445–1458. [Google Scholar] [CrossRef] [PubMed]
- Ravichandran, D.; Banu, S.A.; Murthy, B.K.; Balasubramanian, V.; Fathima, S.; Amirtharajan, R. An efficient medical image encryption using hybrid DNA computing and chaos in transform domain. Med. Biol. Eng. Comput. 2021, 59, 589–605. [Google Scholar] [CrossRef]
- Guan, M.; Yang, X.; Hu, W. Chaotic image encryption algorithm using frequency-domain DNA encoding. IET Image Processing 2019, 13, 1535–1539. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Lu, Y.; Chen, Y.; Han, D. A novel image encryption algorithm based on the chaotic system and DNA computing. Int. J. Mod. Phys. C 2017, 28, 1750069. [Google Scholar] [CrossRef]
- Li, T.; Yang, M.; Wu, J.; Jing, X. A Novel Image Encryption Algorithm Based on a Fractional-Order Hyperchaotic System and DNA Computing. Complexity 2017, 2017, 9010251. [Google Scholar] [CrossRef] [Green Version]
- Zefreh, E.Z. An image encryption scheme based on a hybrid model of DNA computing, chaotic systems and hash functions. Multimed. Tools Appl. 2020, 79, 24993–25022. [Google Scholar] [CrossRef]
- Vulpiani, A.; Cecconi, F.; Cencini, M. Chaos: From Simple Models to Complex Systems; Series on Advances in Statistical Mechanics; World Scientific Publishing Co. Pte. Ltd.: Singapore, 2009; Volume 17. [Google Scholar]
- Liu, L.; Du, C.; Zhang, X.; Li, J.; Shi, S. Dynamics and Entropy Analysis for a New 4-D Hyperchaotic System with Coexisting Hidden Attractors. Entropy 2019, 21, 287. [Google Scholar] [CrossRef] [Green Version]
- SIPI Image Database—Misc. Available online: http://sipi.usc.edu/database/database.php?volume=misc (accessed on 20 February 2022).
- Hu, T.; Liu, Y.; Gong, L.-H.; Ouyang, C.-J. An image encryption scheme combining chaos with cycle operation for DNA sequences. Nonlinear Dyn. 2016, 87, 51–66. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Yuan, K.; Chen, Y.; Liu, X. A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput. Appl. 2019, 31, 219–237. [Google Scholar] [CrossRef]
- Hosny, K.; Kamal, S.; Darwish, M.; Papakostas, G. New Image Encryption Algorithm Using Hyperchaotic System and Fibonacci Q-Matrix. Electronics 2021, 10, 1066. [Google Scholar] [CrossRef]
- Girdhar, A.; Kapur, H.; Kumar, V. A novel grayscale image encryption approach based on chaotic maps and image blocks. Appl. Phys. A 2021, 127, 39. [Google Scholar] [CrossRef]
- Yan, X.; Wang, X.; Xian, Y. Chaotic image encryption algorithm based on arithmetic sequence scrambling model and DNA encoding operation. Multimed. Tools Appl. 2021, 80, 10949–10983. [Google Scholar] [CrossRef]
- Zhang, Y.-Q.; Wang, X.-Y. A symmetric image encryption algorithm based on mixed linear–nonlinear coupled map lattice. Inf. Sci. 2014, 273, 329–351. [Google Scholar] [CrossRef]
- Wang, X.-Y.; Zhang, Y.-Q.; Bao, X.-M. A novel chaotic image encryption scheme using DNA sequence operations. Opt. Lasers Eng. 2015, 73, 53–61. [Google Scholar] [CrossRef]
- Ping, P.; Fan, J.; Mao, Y.; Xu, F.; Gao, J. A Chaos Based Image Encryption Scheme Using Digit-Level Permutation and Block Diffusion. IEEE Access 2018, 6, 67581–67593. [Google Scholar] [CrossRef]
- Wang, X.; Liu, L.; Zhang, Y. A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt. Lasers Eng. 2015, 66, 10–18. [Google Scholar] [CrossRef]
- Zhang, Y.-Q.; Wang, X.-Y. A new image encryption algorithm based on non-adjacent coupled map lattices. Appl. Soft Comput. 2015, 26, 10–20. [Google Scholar] [CrossRef]
- Wang, X.; Teng, L.; Qin, X. A novel colour image encryption algorithm based on chaos. Signal Processing 2012, 92, 1101–1108. [Google Scholar] [CrossRef]
- Ping, P.; Xu, F.; Mao, Y.; Wang, Z. Designing permutation–substitution image encryption networks with Henon map. Neurocomputing 2018, 283, 53–63. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).