Function Computation under Privacy, Secrecy, Distortion, and Communication Constraints †
Abstract
1. Introduction
1.1. Models for Function Inputs and Outputs
1.2. Summary of Contributions
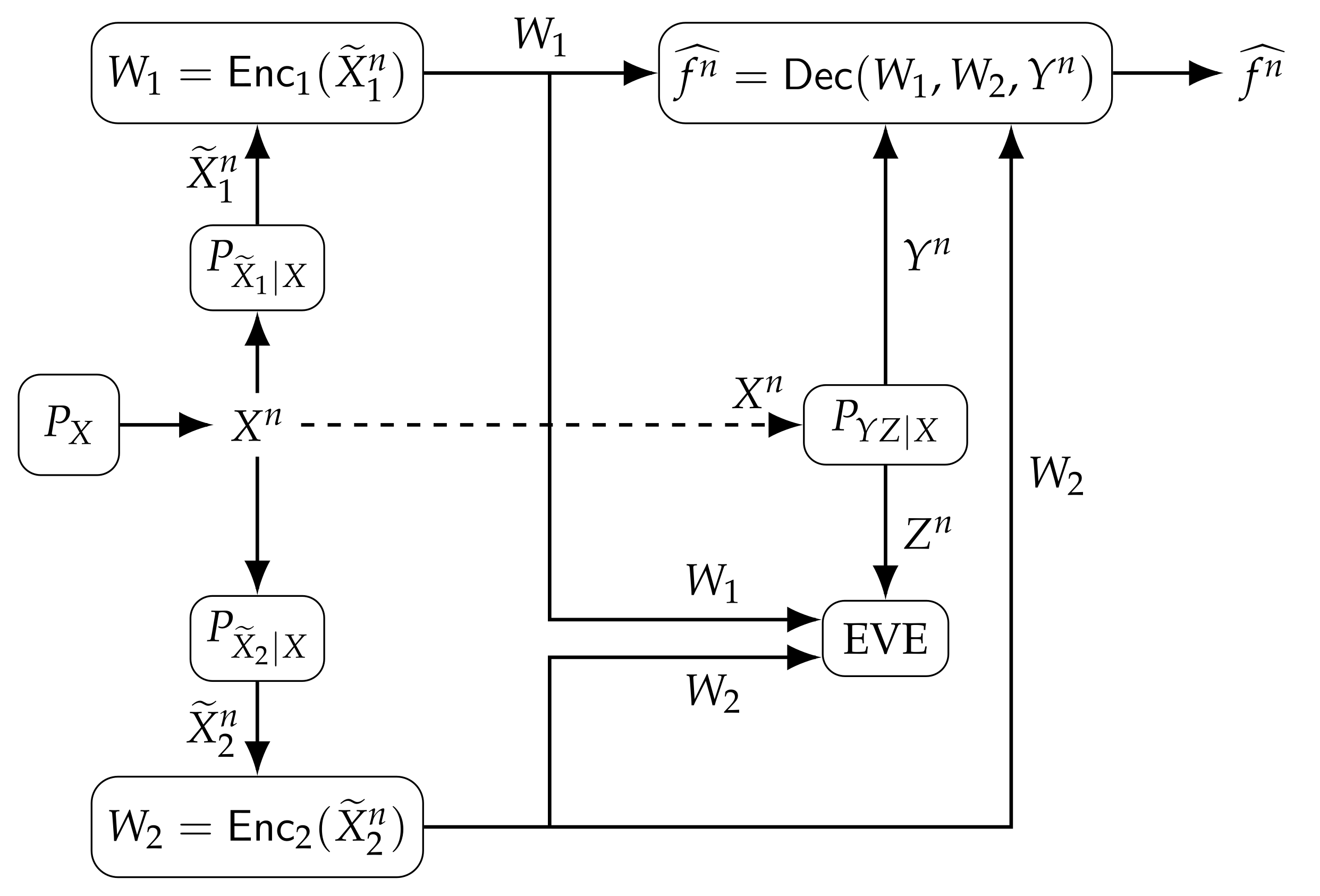
- The lossless single-function computation model with two transmitting nodes is considered, and an inner bound for the rate region that characterizes the optimal trade-off between secrecy, privacy, storage, and distortion constraints is established by using the output statistics of a random binning (OSRB) method [30,31]. An outer bound for the same rate region is also provided by using standard properties of Shannon entropy. Inner and outer bounds are shown to not match in general due to different Markov chains imposed.
- The proposed inner and outer bounds are extended for the lossy single-function computation model with two transmitting nodes by considering a distortion metric. Furthermore, effects of considering a distortion constraint, rather than a reliability constraint, on the function computation are discussed.
- For both partially invertible functions, which define a set that is a proper superset of the set of invertible functions, and invertible functions, we characterize simplified lossless and lossy rate regions.
- The simplified rate regions for invertible functions are further simplified when the eavesdropper’s measurement channel is physically degraded with respect to the fusion center’s channel or vice versa, which results in different bounds on the rates.
- We evaluate a simplified rate region for a physically degraded case with multiplicative Bernoulli noise components.
1.3. Organization
1.4. Notation
2. System Model
2.1. Lossless Single-Function Computation
2.2. Lossy Single-Function Computation
3. Inner and Outer Bounds
3.1. Lossless Single-Function Computation
3.2. Lossy Single-Function Computation
4. Rate Regions for Special Sets of Computed Functions and Measurement Channels
4.1. Partially Invertible Functions
4.2. Invertible Functions
4.3. Invertible Functions and Two Different Degraded Channels
4.3.1. Eve’s Channel Is Physically Degraded
4.3.2. Fusion Center’s Channel Is Physically Degraded
4.4. Lossless Rate Region Example
5. Proof of Theorem 1
5.1. Inner Bound
- observing , the decoder estimates as ;
- observing , the decoder estimates as ;
- observing , the decoder estimates as ;
- observing , the decoder estimates as .
5.2. Outer Bound
6. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Mijumbi, R.; Serrat, J.; Gorricho, J.L.; Bouten, N.; De Turck, F.; Boutaba, R. Network Function Virtualization: State-of-the-Art and Research Challenges. IEEE Commun. Surv. Tutor. 2016, 18, 236–262. [Google Scholar] [CrossRef]
- Predd, J.B.; Kulkarni, S.B.; Poor, H.V. Distributed learning in wireless sensor networks. IEEE Sign. Process. Mag. 2006, 23, 56–69. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science, Chicago, IL, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Yao, A.C. How to generate and exchange secrets. In Proceedings of the 27th Annual Symposium on Foundations of Computer Science, Toronto, ON, Canada, 27–29 October 1986; pp. 162–167. [Google Scholar]
- Tyagi, H.; Narayan, P.; Gupta, P. When Is a Function Securely Computable? IEEE Trans. Inf. Theory 2011, 57, 6337–6350. [Google Scholar] [CrossRef]
- Orlitsky, A.; Roche, J.R. Coding for computing. IEEE Trans. Inf. Theory 2001, 47, 903–917. [Google Scholar] [CrossRef]
- Bloch, M.; Günlü, O.; Yener, A.; Oggier, F.; Poor, H.V.; Sankar, L.; Schaefer, R.F. An Overview of Information-Theoretic Security and Privacy: Metrics, Limits and Applications. IEEE J. Sel. Areas Inf. Theory 2021, 2, 5–22. [Google Scholar] [CrossRef]
- Ma, N.; Ishwar, P. Some Results on Distributed Source Coding for Interactive Function Computation. IEEE Trans. Inf. Theory 2011, 57, 6180–6195. [Google Scholar] [CrossRef]
- Sefidgaran, M.; Tchamkerten, A. Computing a function of correlated Sources: A rate region. In Proceedings of the 2011 IEEE International Symposium on Information Theory, St. Petersburg, Russia, 31 July–5 August 2011; pp. 1856–1860. [Google Scholar]
- Nazer, B.; Gastpar, M. Computation Over Multiple-Access Channels. IEEE Trans. Inf. Theory 2007, 53, 3498–3516. [Google Scholar] [CrossRef]
- Kowshik, H.; Kumar, P.R. Optimal Function Computation in Directed and Undirected Graphs. IEEE Trans. Inf. Theory 2012, 58, 3407–3418. [Google Scholar] [CrossRef]
- Kannan, S.; Viswanath, P. Multi-Session Function Computation and Multicasting in Undirected Graphs. IEEE J. Sel. Areas Commun. 2013, 31, 702–713. [Google Scholar] [CrossRef]
- Slepian, D.; Wolf, J. Noiseless coding of correlated information sources. IEEE Trans. Inf. Theory 1973, 19, 471–480. [Google Scholar] [CrossRef]
- Wyner, A.D.; Ziv, J. The rate-distortion function for source coding with side information at the decoder. IEEE Trans. Inf. Theory 1976, 22, 1–10. [Google Scholar] [CrossRef]
- Goldenbaum, M.; Boche, H.; Poor, H.V. On secure computation over the binary modulo-2 adder multiple-access wiretap channel. In Proceedings of the 2016 IEEE Information Theory Workshop (ITW), Cambridge, UK, 11–14 September 2016; pp. 21–25. [Google Scholar]
- Tyagi, H.; Watanabe, S. Converses For Secret Key Agreement and Secure Computing. IEEE Trans. Inf. Theory 2015, 61, 4809–4827. [Google Scholar] [CrossRef]
- Prabhakaran, V.; Ramchandran, K. On Secure Distributed Source Coding. In Proceedings of the 2007 IEEE Information Theory Workshop, Lake Tahoe, CA, USA, 2–6 September 2007; pp. 442–447. [Google Scholar]
- Tu, W.; Lai, L. On Function Computation with Privacy and Secrecy Constraints. IEEE Trans. Inf. Theory 2019, 65, 6716–6733. [Google Scholar] [CrossRef]
- Günlü, O. Key Agreement with Physical Unclonable Functions and Biometric Identifiers. Ph.D. Thesis, Technische Universität München, Munich, Germany, 2018. [Google Scholar]
- Günlü, O.; Bloch, M.; Schaefer, R.F. Secure Multi-Function Computation with Private Remote Sources. arXiv 2021, arXiv:2106.09485. [Google Scholar]
- Wang, Y.; Rane, S.; Draper, S.C.; Ishwar, P. A Theoretical Analysis of Authentication, Privacy, and Reusability Across Secure Biometric Systems. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1825–1840. [Google Scholar] [CrossRef]
- Günlü, O.; Kittichokechai, K.; Schaefer, R.F.; Caire, G. Controllable Identifier Measurements for Private Authentication With Secret Keys. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1945–1959. [Google Scholar] [CrossRef]
- Li, N.; Zhang, Y.; Kuo, C.C.J. Explainable Machine Learning based Transform Coding for High Efficiency Intra Prediction. arXiv 2020, arXiv:2012.11152. [Google Scholar]
- Voloshynovskiy, S.; Koval, O.; Holotyak, T.; Beekhof, F. Privacy enhancement of common randomness based authentication: Key rate maximized case. In Proceedings of the 2009 First IEEE International Workshop on Information Forensics and Security (WIFS), London, UK, 6–9 December 2009; pp. 86–90. [Google Scholar]
- Wayman, J.; Jain, A.; Maltoni, D.; Maio, D. Biometric Systems: Technology, Design and Performance Evaluation; Springer: London, UK, 2005. [Google Scholar]
- De Groot, J.; Škoric, B.; De Vreede, N.; Linnartz, J.P. Information leakage of continuous-source zero secrecy leakage helper data schemes. Citeseer Gen 2012, 1, 1–16. [Google Scholar]
- Voloshynovskiy, S.; Koval, O.; Holotyak, T.; Beekhof, F.; Farhadzadeh, F. Privacy amplification of content identification systems based on fingerprint bit reliability. In Proceedings of the 2010 IEEE International Workshop on Information Forensics and Security, Seattle, WA, USA, 12–15 December 2010; pp. 1–6. [Google Scholar]
- Campisi, P. Security and Privacy in Biometrics; Springer: London, UK, 2013. [Google Scholar]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A. Communication-Efficient Learning of Deep Networks from Decentralized Data. Int. Conf. Artif. Intell. Statist. 2017, 54, 1273–1282. [Google Scholar]
- Yassaee, M.H.; Aref, M.R.; Gohari, A. Achievability Proof via Output Statistics of Random Binning. IEEE Trans. Inf. Theory 2014, 60, 6760–6786. [Google Scholar] [CrossRef]
- Holenstein, T.; Renner, R. On the Randomness of Independent Experiments. IEEE Trans. Inf. Theory 2011, 57, 1865–18716. [Google Scholar] [CrossRef]
- Günlü, O.; Bloch, M.; Schaefer, R.F. Secure Lossy Function Computation with Multiple Private Remote Source Observations. In Proceedings of the 25th International ITG Workshop on Smart Antennas (WSA 2021), French Riviera, France, 10–12 November 2021. [Google Scholar]
- Günlü, O.; Bloch, M.; Schaefer, R.F. Multiple Noisy Private Remote Source Observations for Secure Function Computation. In Proceedings of the Asilomar Conference on Signals, Systems & Computers, Pacific Grove, CA, USA, 31 October–3 November 2021. [Google Scholar]
- Gamal, A.E.; Kim, Y.H. Network Information Theory; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Ericson, T.; Körner, J. Successive encoding of correlated sources. IEEE Trans. Inf. Theory 1983, 29, 390–395. [Google Scholar] [CrossRef]
- Ahmadipour, M.; Wigger, M.; Kobayashi, M. Joint Sensing and Communication over Memoryless Broadcast Channels. In Proceedings of the IEEE Information Theory Workshop, Kanazawa, Japan, 17–21 October 2021; pp. 1–5. [Google Scholar]
- Bloch, M. Lecture Notes in Information-Theoretic Security; The Georgia Institute of Technology: Atlanta, GA, USA, 2018. [Google Scholar]
- Bloch, M.; Barros, J. Physical-Layer Security; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Günlü, O.; Schaefer, R.F.; Poor, H.V. Biometric and Physical Identifiers with Correlated Noise for Controllable Private Authentication. arXiv 2020, arXiv:2001.00847. [Google Scholar]
- Csiszár, I.; Körner, J. Information Theory: Coding Theorems for Discrete Memoryless Systems, 2nd ed.; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Günlü, O. Function Computation under Privacy, Secrecy, Distortion, and Communication Constraints. Entropy 2022, 24, 110. https://doi.org/10.3390/e24010110
Günlü O. Function Computation under Privacy, Secrecy, Distortion, and Communication Constraints. Entropy. 2022; 24(1):110. https://doi.org/10.3390/e24010110
Chicago/Turabian StyleGünlü, Onur. 2022. "Function Computation under Privacy, Secrecy, Distortion, and Communication Constraints" Entropy 24, no. 1: 110. https://doi.org/10.3390/e24010110
APA StyleGünlü, O. (2022). Function Computation under Privacy, Secrecy, Distortion, and Communication Constraints. Entropy, 24(1), 110. https://doi.org/10.3390/e24010110





