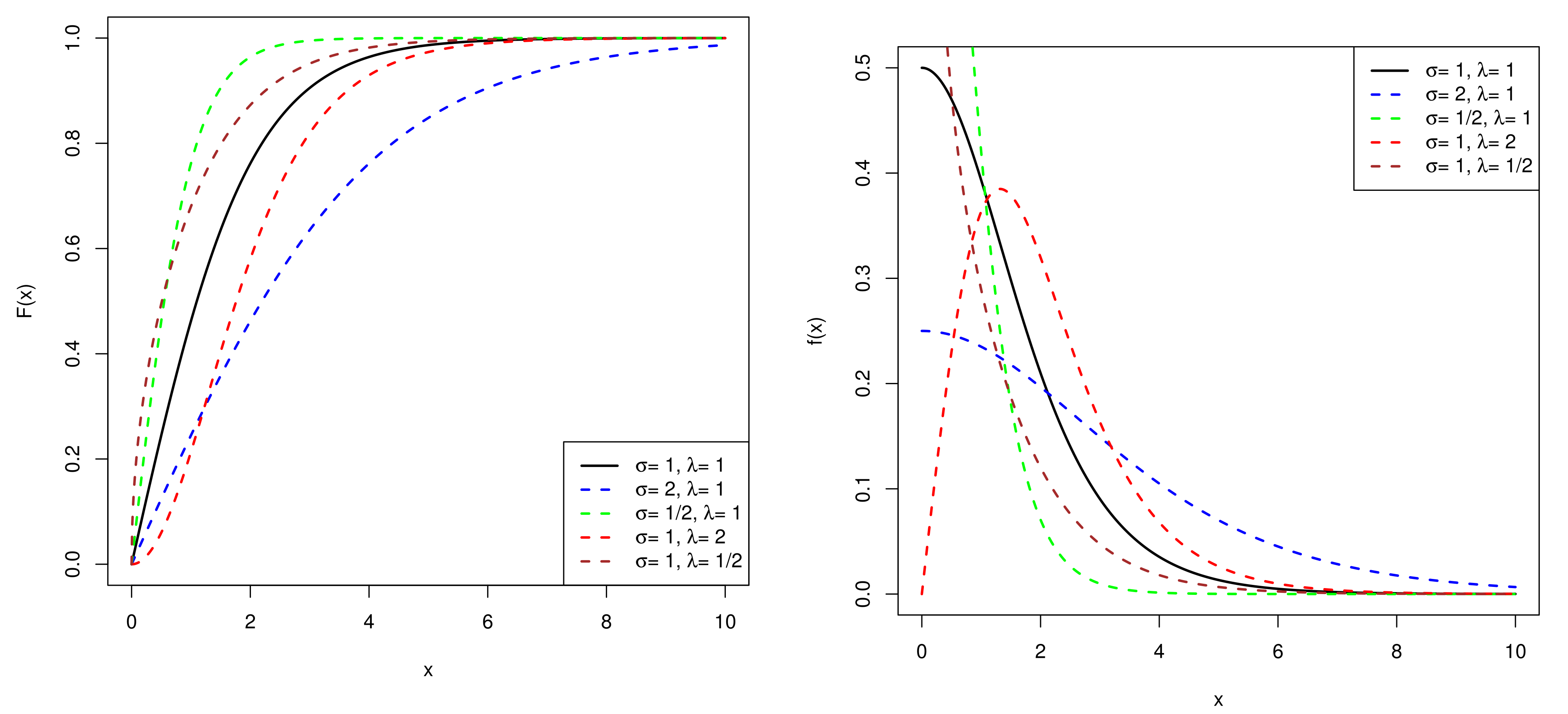
4. Bayesian Estimation
In this section, we compute the Bayesian estimates of the quantities by using the Lindley method and the importance sampling procedure. Unlike classical statistics, Bayesian statistics treat quantities as random variables, which combines the prior information with observed information.
The option of prior distribution is a pivotal problem. Generally speaking, the conjugate prior distribution is the first choice due to its algebraic simplicity. However, it is very difficult to find such prior when both quantities
and
are unknown. The prior distribution is reasonable to keep the same form as (
6). Suppose that
and
and that these two priors are independent. The PDFs of their prior distributions correspond to
The corresponding joint distribution is
Given the sample
, the posterior distribution
can be written as
4.1. Symmetric and Asymmetric Loss Functions
The loss function is employed to appraise the intensity of inconsistency between the estimation of the parameter and the true value. The squared error loss function is a symmetric loss function, which is applied in many areas. However, on the condition that overestimation causes greater loss compared with underestimation or vice versa, using a symmetric loss function is not suitable. Instead, the asymmetric loss function is employed to fix the problem. Therefore, we consider the Bayesian estimations under one symmetric loss function, namely the squared error loss function (SELF) as well as two asymmetric loss functions, namely the Linex Loss Function (LLF) and the General Entropy Loss Function (GELF) in this subsection.
4.1.1. Squared Error Loss Function (SELF)
The squared error loss function is a symmetric loss function, which puts the overestimate and underestimate on the same level. It is the sum of squared distances between the target variable and the predicted value. The function corresponds to
where
is the estimation of
.
The Bayesian estimation of
under SELF is given by
Then, for the unknown parameters
and
, the Bayesian estimates under SELF can be given directly as
4.1.2. Linex Loss Function (LLF)
The Linex function is a well-known asymmetric loss function. It is defined as
The size of p denotes the level of asymmetry and its sign represents the direction of asymmetry. For , LLF alters exponentially in the negative direction and linearly in the positive direction, thus a negative bias has a more serious impact—while, for , the positive error will be punished heavily. The larger the dimension of p is, the larger the punishment intensity is. When approaches 0, LLF is almost symmetric.
The Bayesian estimation of
under LLF is written as
Then, for unknown parameters
and
, the Bayesian estimates under LLF are
4.1.3. General Entropy Loss Function (GELF)
The General Entropy loss function (GELF) is another noted asymmetric loss function, which is
For
, the overestimation has a more serious impact compared with the underestimation, and vice versa. The Bayesian estimation of
under GELF is derived:
Notably, when
, the Bayesian estimation under GELF has the same value as that under SELF. The Bayesian estimates of
and
under GELF correspond to
We can know that the Bayesian estimates of and are in the modality of a ratio of two complicated integrals and the specific and explicit forms cannot be represented without trouble. Thus, the Lindley method is employed to solve this problem.
4.2. Lindley Approximation Method
In this subsection, in order to compute the Bayesian estimates, we apply the Lindley approximation method. Let
denote any function about
and
,
l denote the log-likelihood function and
. According to the [
19], the Bayesian estimates can be expressed by the posterior expectation of
where
Here, and denotes the -th component of the covariance matrix. Then, the Bayesian estimates under three loss functions SELF, LLF, and GELF are derived.
4.2.1. Squared Error Loss Function (SELF)
For
, let
; therefore,
Then, the Bayesian estimate of
under SELF is
Similarly, for parameter
, it is clear that
, hence
Then, the Bayesian estimate of
under SELF can be written as
4.2.2. Linex Loss Function (LLF)
For
, we take
, hence
The Bayesian estimate of
under LLF is derived as
Similarly, for the parameter
, let
, hence
The Bayesian estimate of
under LLF can be written as
4.2.3. General Entropy Loss Function (GELF)
For parameter
, let
, hence
The Bayesian estimate of
under GELF can be written as
Similarly, for parameter
, , it is clear that
, hence
The Bayesian estimate of
under GELF can be written as
Though the Lindley approximation is effective to obtain point estimations by estimating the ratio of integrals, it can not provide credible intervals of the unknown parameters. Therefore, the importance sampling method is adopted to gain not only point estimation but also credible intervals.
4.3. Importance Sampling Procedure
The importance sampling procedure is an extension to the Monte Carlo method, which can greatly reduce the number of sample points drawn in the simulation, and is widely used in the reliability analysis of various models. From (
6) and (
21), the joint posterior distribution is derived by
where
It is clear that is the PDF of an inverse Gamma distribution while is the PDF of a Gamma distribution.
Therefore, the Bayesian estimation of is acquired by the following steps:
Generate from .
On the basis of step 1, generate from .
Repeat step 1 and step 2 M times and produce a series of samples.
The Bayesian estimate of
is calculated by
Therefore, the Bayesian estimate of the unknown parameter
and
is derived by
For the sake of simplicity,
is denoted as
. Then, we sort
in ascending order as
. In addition, we combine
and
together as
. The HPD credible interval is established based on the estimate
, where
is an integer that satisfies
Hence, the credible interval can be represented as , . Therefore, the HPD credible for is obtained by . Note that for all .
5. Simulation
Plenty of simulation experiments are carried out to appraise the performance of our estimations by Monte Carlo simulations. Here, the R software is employed for all the simulations. The point estimation is evaluated by the mean square error (MSE) and estimation value (VALUE), while the interval estimation is assessed based on the coverage rate (CR) and interval mean length (ML). For point estimation, smaller mean square error and closer estimation value suggest better performance of estimation. In addition, for interval estimation, the higher the coverage rate is and the narrower the interval mean length is, the better the estimation is.
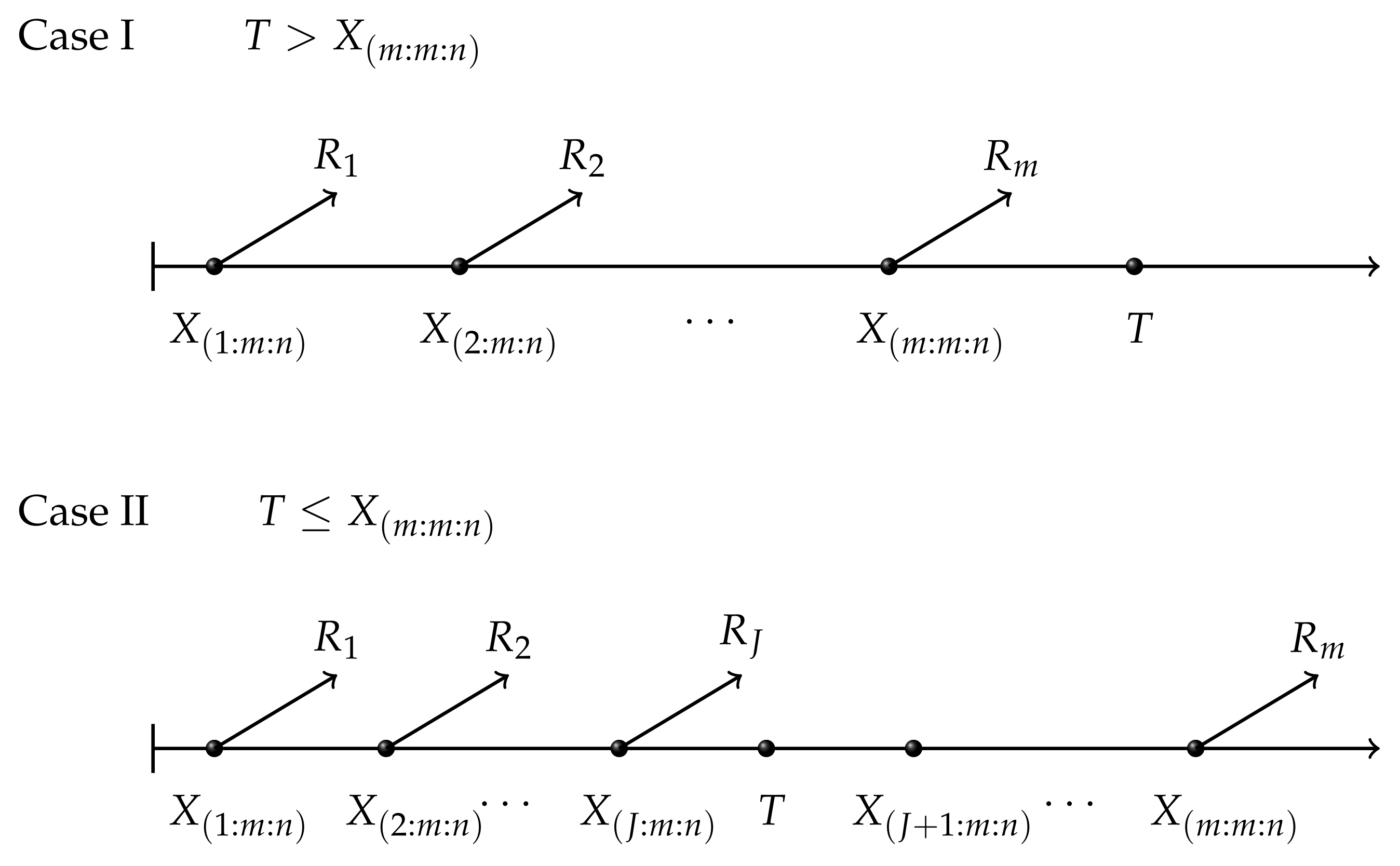
First of all, adaptive type II progressive censored data from an exponentiated half-logistic distribution should be generated. The algorithm for generating adaptive Type II progressive censored data from a general distribution can be obtained in [
3]. The algorithm to generate the censored data is listed in Algorithm 3.
| Algorithm 3: Generating adaptive type II progressive censored data from EHL(). |
- 1.
Generate a Type II progressive censored sample from an exponentiated half-logistic distribution EHL() with initial values of and : - (a)
generate independent random variables from the uniform distribution . - (b)
Let , . - (c)
Let , . - (d)
For certain and , let . Then, is the Type II progressive censored sample from EHL().
- 2.
Confirm the value of J, and abandon the sample . - 3.
Generate the first order statistics from a truncated distribution with sample size as .
|
In order to carry out simulations, we set and . For comparison purposes, we consider and . For all the combinations of sample size and time T, two different censoring schemes (CS) are chosen:
Scheme I (Sch I): .
Scheme II (Sch II): .
In addition, the specific diverse censoring schemes conceived for the simulation are listed in
Table 1.
For simplicity, we abbreviate the censoring schemes. For example, (1, 1, 1, 0, 0, 0, 0) is represented as (1*3, 0*4). In each case, the simulation is repeated 3000 times. Then, the associated MSEs and VALUEs with the point estimation and the related coverage rates and mean lengths with the interval estimation can be acquired through Monte Carlo simulations using R software.
For maximum likelihood estimation, the L-BFGS-B method is used and the simulation results are put into
Table A1. In Bayesian estimation, we employ not only non-informative priors (non-infor) but also informative priors (infor). For the non-informative priors, we set
. Then, for the informative priors, we should first determine the hyper-parameters for Bayesian estimation. Generally speaking, the actual value of the parameter is usually considered as the expectation of the prior distribution. However, due to the complexity and interactive influence of the two prior distributions, the optimal value can not be found directly. Thus, we adopt a genetic algorithm and simulated annealing algorithm to determine the optimal hyper-parameters and the results are:
. To get Bayesian point estimation, the Lindley method and the importance sampling method are employed. Three loss functions are adopted separately for comparison purposes. The parameter
p of LLF is set to 0.5 and 1 and the parameter
q of GELF is set to
and 0.5.
The informative Bayes method uses minimization of loss functions, and such minimizations can only be performed if the true parameter values are known. Hence, informative Bayes can only be seen as a reference, or an oracle method.
The results are presented in
Table A2,
Table A3,
Table A4,
Table A5,
Table A6,
Table A7,
Table A8 and
Table A9. In addition, the mean length and coverage rate of asymptotic confidence intervals, boot-t intervals, boot-p intervals, and HPD intervals at 95% confidence/credible level are also shown in
Table A10 and
Table A11.
Due to the excessive amount of tables, it is not easy for readers to find rules of the estimation. Therefore, some figures which present the most representative simulation results are made to show the rules more intuitively.
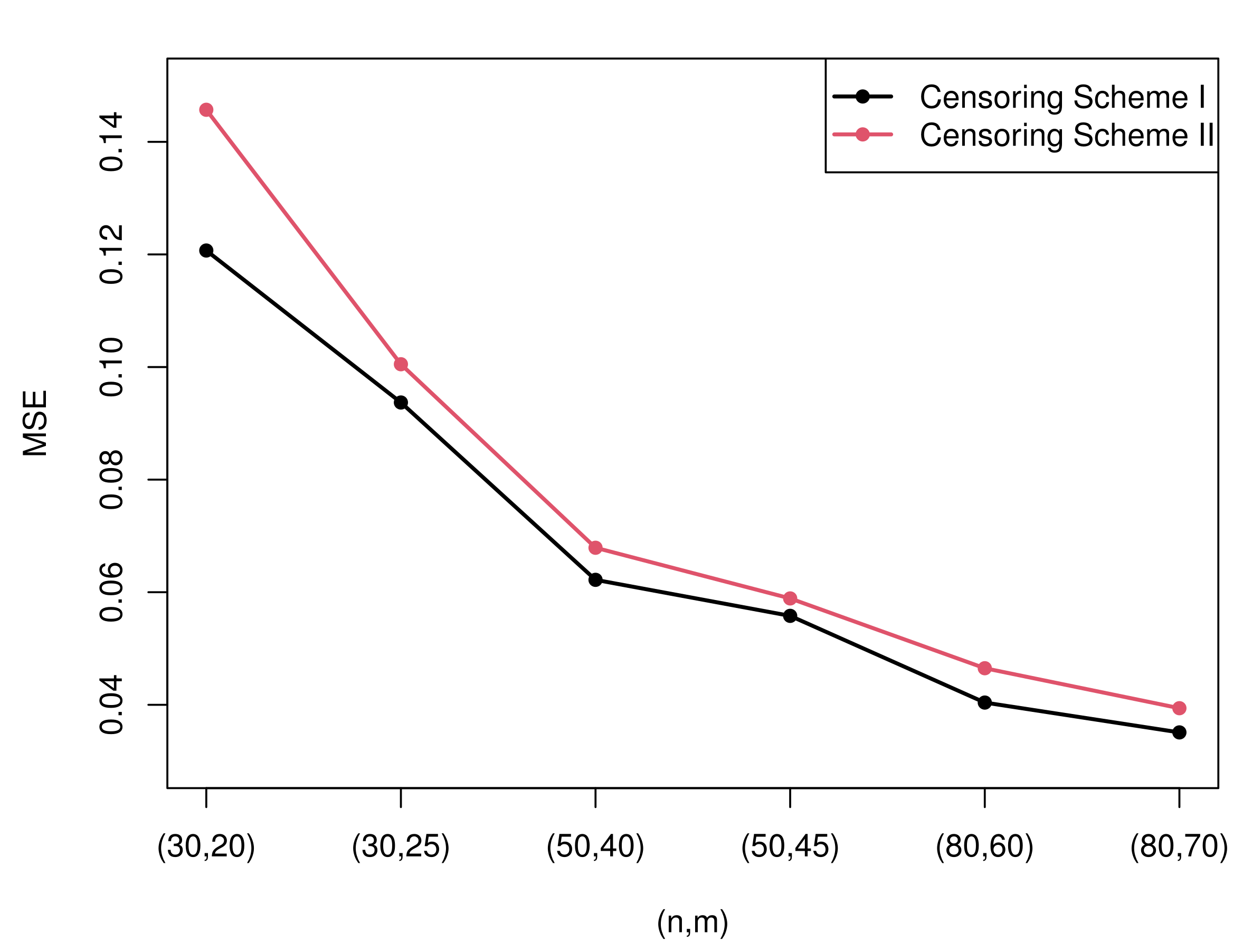
Figure 3 and
Figure 4 present the MSEs of the maximum likelihood estimates of the two parameters under censoring scheme I and censoring scheme II when
.
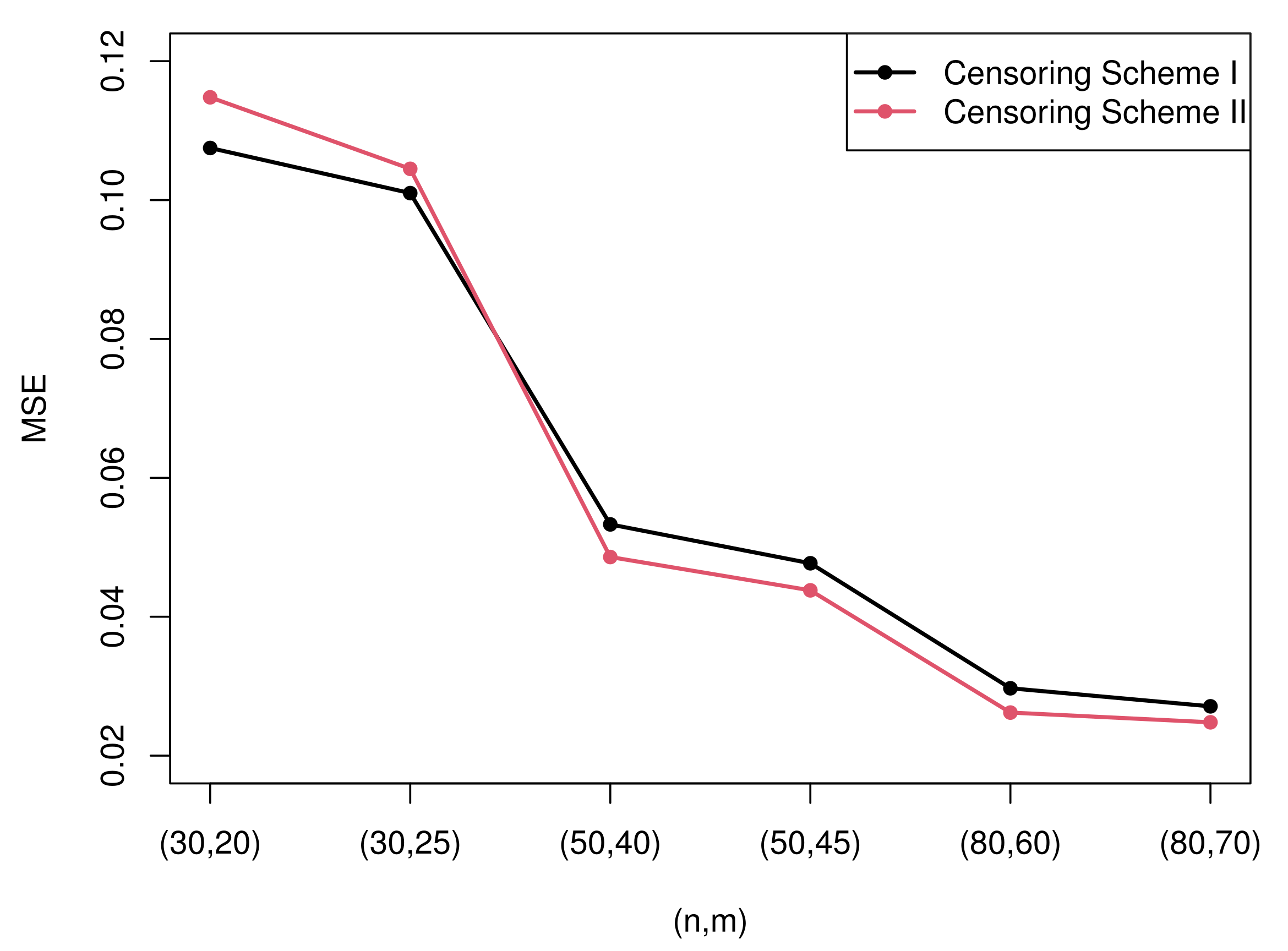
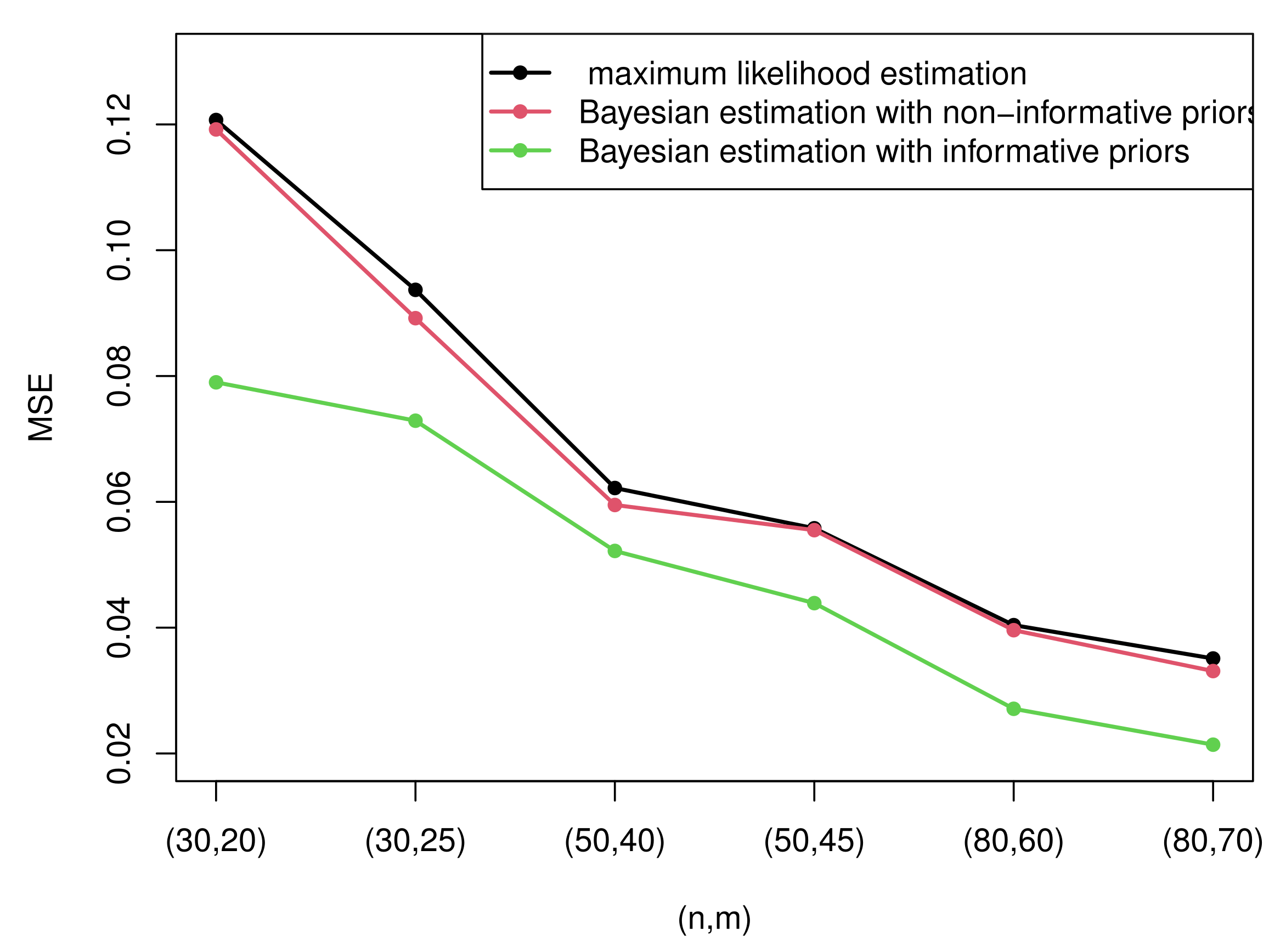
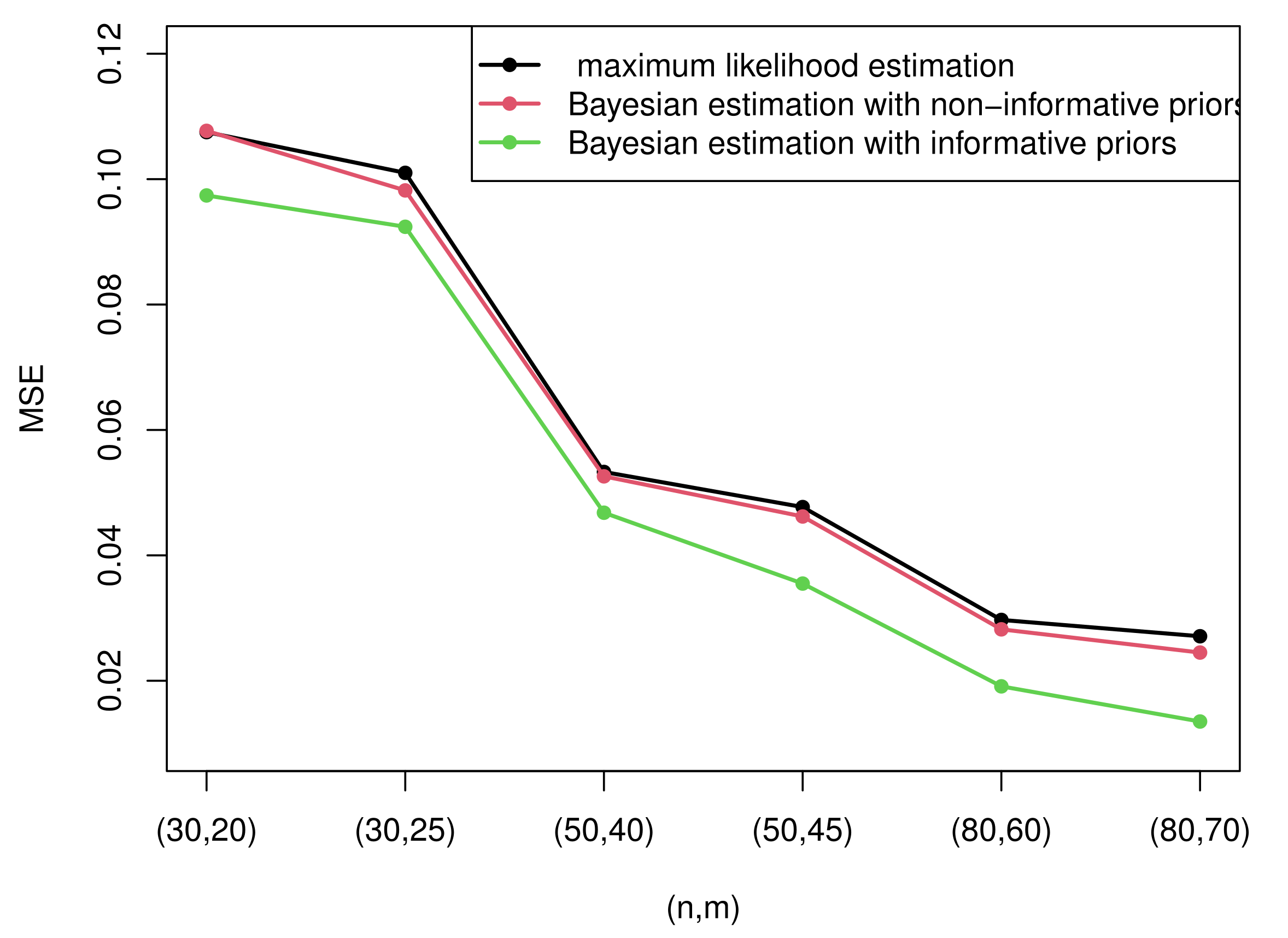
Figure 5 and
Figure 6 compare the MSEs of maximum likelihood estimates with the Bayesian estimates with non-informative and informative priors obtained by importance sampling under censoring scheme I and
.
- (1)
All the estimation values are generally inclined to approach the true value, and MSEs tend to decrease as the sample size
n or observed numbers
m or the value of
increases. The rules of the MSEs can be easily obtained from
Figure 3 and
Figure 4.
- (2)
The MLEs of perform better than the MLEs of according to the MSE. However, the estimation values of are closer to the true value compared with those of .
- (3)
Diverse censoring schemes show a regular mode in terms of MSE. From the
Figure 3 and
Figure 4, we can know that, when
is considered, Sch I performs better than Sch II in all cases, yet when
is considered, Sch II is more effective than Sch I except the case of
.
- (4)
There is no observed specific pattern with the change of T. It is apprehensible because the observed data may remain unaltered when T changes.
- (1)
Generally, the Bayesian estimates under three loss functions with informative priors are more accurate contrasted with MLEs in terms of MSE in all cases. This rule can be intuitively summarized from
Figure 5 and
Figure 6. This is because the Bayesian method not only considers the data but also takes the prior information of unknown parameters into account. In addition, the importance sampling procedure outperforms the Lindley method.
- (2)
From
Figure 5 and
Figure 6, it is clear that the performance of the Bayesian estimates with non-informative priors is almost similar to MLEs under all circumstances. This is because we have no information with respect to the unknown parameters. In other words, it only takes the data into account. Thus, it is reasonable that the results are analogous to MLEs.
- (3)
The Bayesian estimates under GELF are superior compared with those under SELF and LLF. For LLF, Bayesian estimates under are better than those under for the parameter , while choosing is better than for the estimate of . For GELF, take the fact that both and are satisfactory and perform well. On the whole, the Bayesian estimates under GELF using the importance sampling procedure are the most effective as they possess the minimal MSEs and the closest estimation values.
- (4)
When is considered, Sch I performs better than Sch II except when , yet when is taken into account, Sch II is superior compared with Sch I in most cases.
- (1)
The mean lengths of all the intervals become narrower as n and m increase, and this pattern holds for both and . In addition, the coverage rate of intervals of is higher while the coverage rate of intervals of is stable with the increase of m and n.
- (2)
The HPD credible intervals and boot-t intervals perform better contrasted by asymptotic confidence intervals due to narrower mean length and higher coverage rate. In addition, the HPD credible intervals possess the narrowest mean length while the boot-t intervals have the highest coverage rate.
- (3)
The results of the two parameters’ intervals have no obvious connection with different censoring schemes.
6. Real Data Analysis
An authentic dataset is analyzed for expository intention by employing the methods mentioned above in this section. The dataset was initially from [
20] and further employed by [
21,
22]. The complete data set describes log times to the breakdown of an insulating fluid testing experiment and is presented in
Table 2.
At the beginning, we should consider the problem whether the distribution EHL
fits the data set well. The fitting effect of exponentiated half-logistic distribution and Half Logistic distribution with the CDF
is compared. The criteria employed for examining the goodness of fit include the negative log-likelihood function (
), Kolmogorov–Smirnov (K-S) statistics with its
p-value, Bayesian Information Criterion (BIC), and Akaike Information Criterion (AIC). The definitions are:
where
d is the number of parameters,
L is the maximized value of the likelihood function, and
n denotes the total number of observed values.
The results of the K-S,
p-value, AIC, BIC, and
of the two distributions are listed in
Table 3. Obviously, exponentiated half-logistic distribution fits the model better since it has lower K-S, AIC, BIC,
statistics, and higher
p-value. Then, we can analyze this data on the basis of our model.
We set
and
2. The two different censoring schemes are
and
.
Table 4 presents the specific adaptive type II censoring data under different schemes based on the data set.
The point estimations for
and
are presented in
Table 5 and
Table 6. For Bayesian estimation, since we have no informative prior, a non-informative prior is applied, namely
. Three loss functions are considered, and we still use the parameters in the previous simulation. At the same time, 95% ACIs, boot-p, boot-t, and HPD intervals are established, while
Table 7 and
Table 8 display the corresponding results. Let Lower denote the lower bound and Upper denote the upper bound.
- (1)
The estimates of parameter using the Lindley method generally tend to be larger than those gained by the importance sampling procedure.
- (2)
The estimates under the first censoring scheme are closer to the MLEs under the full sample, and the estimations using the Lindley method are more effective than those obtained by the importance sampling.
- (3)
The results are relatively close between and when using the first censoring scheme because the observed data remain unaltered when the T is increasing.
- (4)
The HPD credible intervals have the narrowest mean length among all the intervals while the ACIs possess the longest mean length.
- (5)
The results of the two parameters’ intervals have no obvious connection with different censoring schemes.
7. Conclusions
In this manuscript, classical and Bayesian inference for exponentiated half-logistic distribution under adaptive Type II progressive censoring is considered. The maximum likelihood estimates are derived through the Newton–Raphson algorithm. Bayesian estimation under three loss functions is also considered and the estimates are derived through importance sampling and the Lindley method. Meanwhile, we establish the confidence and credible intervals of and and contrast them with each other. Asymptotic confidence intervals are constructed based on observed and expected Fisher information matrices. In order to tackle the problem of small sample size, boot-p and boot-t intervals are computed.
In the simulation section, estimation values and mean squared values are calculated to test the performance of the point estimation while mean lengths and coverage rates are considered for the interval estimation. According to the simulation results, it is clear that the Bayesian estimation which possesses suitable informative priors performs better than MLEs under all circumstances. In more detail, the Bayesian estimations under GELF perform best among all the estimations and the importance sampling procedure makes more sense than Lindley approximation. In addition, when it comes to interval estimation, boot-t and boot-p intervals perform better in the case of a small sample size than asymptotic confidence intervals. In addition, HPD credible intervals generally possess the shortest mean length while boot-t intervals have the highest coverage rate compared with other intervals.
Exponentiated half-logistic distribution under adaptive Type II progressive censoring is significant and practical due to the flexibility of the censoring scheme and the superior features of distribution. Furthermore, the competing risks and accelerated life test can be explored in the research field. In brief, carrying out further research on this model has great potential for survival and reliability analysis.