Time Delay Complex Chen Chaotic System and Secure Communication Scheme for Wireless Body Area Networks
Abstract
1. Introduction
2. Characteristics of Time Delay Complex Chen System
2.1. Chaos Attractor
2.2. Symmetry and Initial Value Sensitivity
2.3. Lyapunov Exponent and Bifurcation Diagram
3. Communication Scheme Based on CMPS
3.1. Design of CMPS Controller
3.2. Communication Scheme for Wireless Body Area Network
4. Controller Design
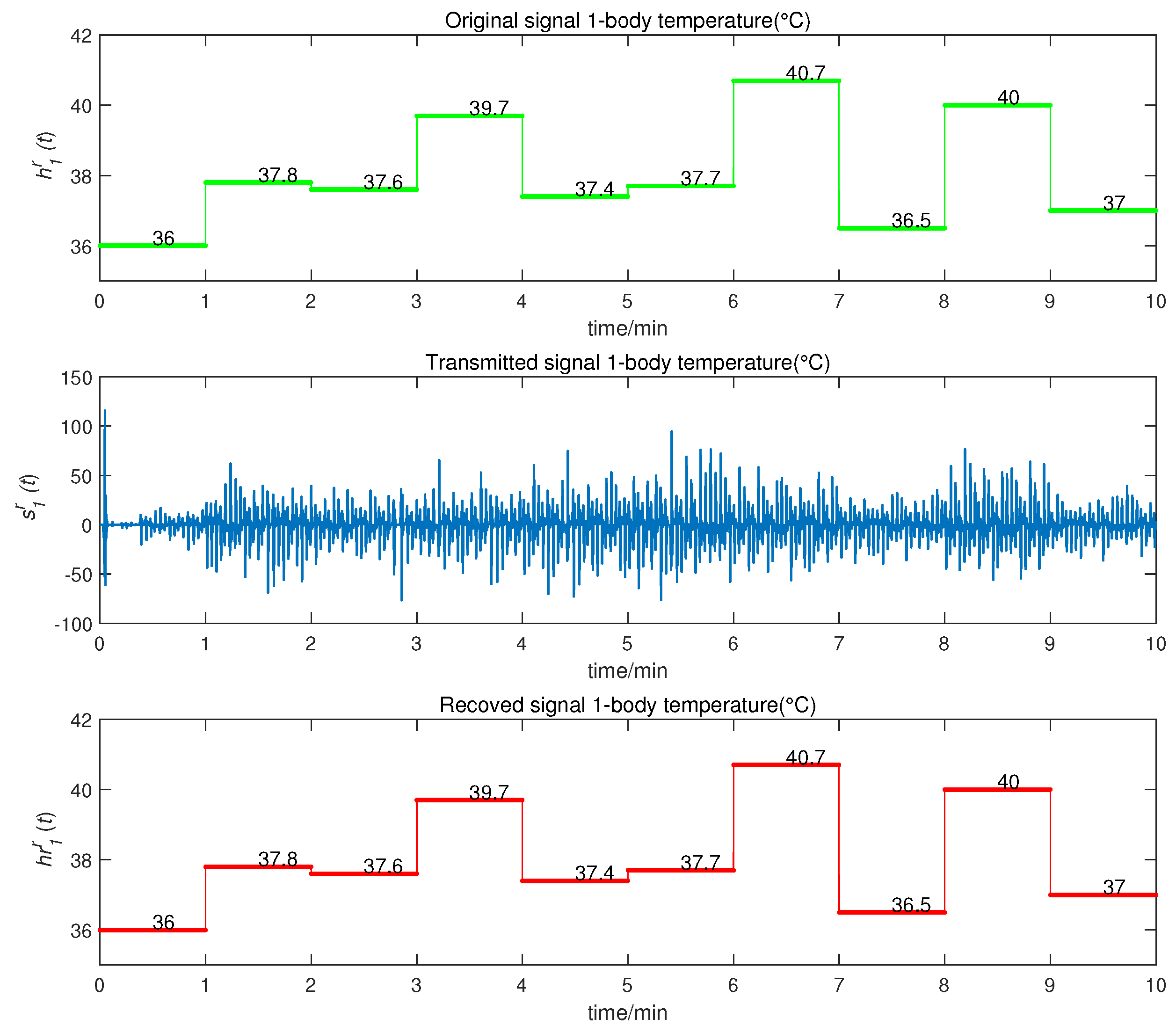
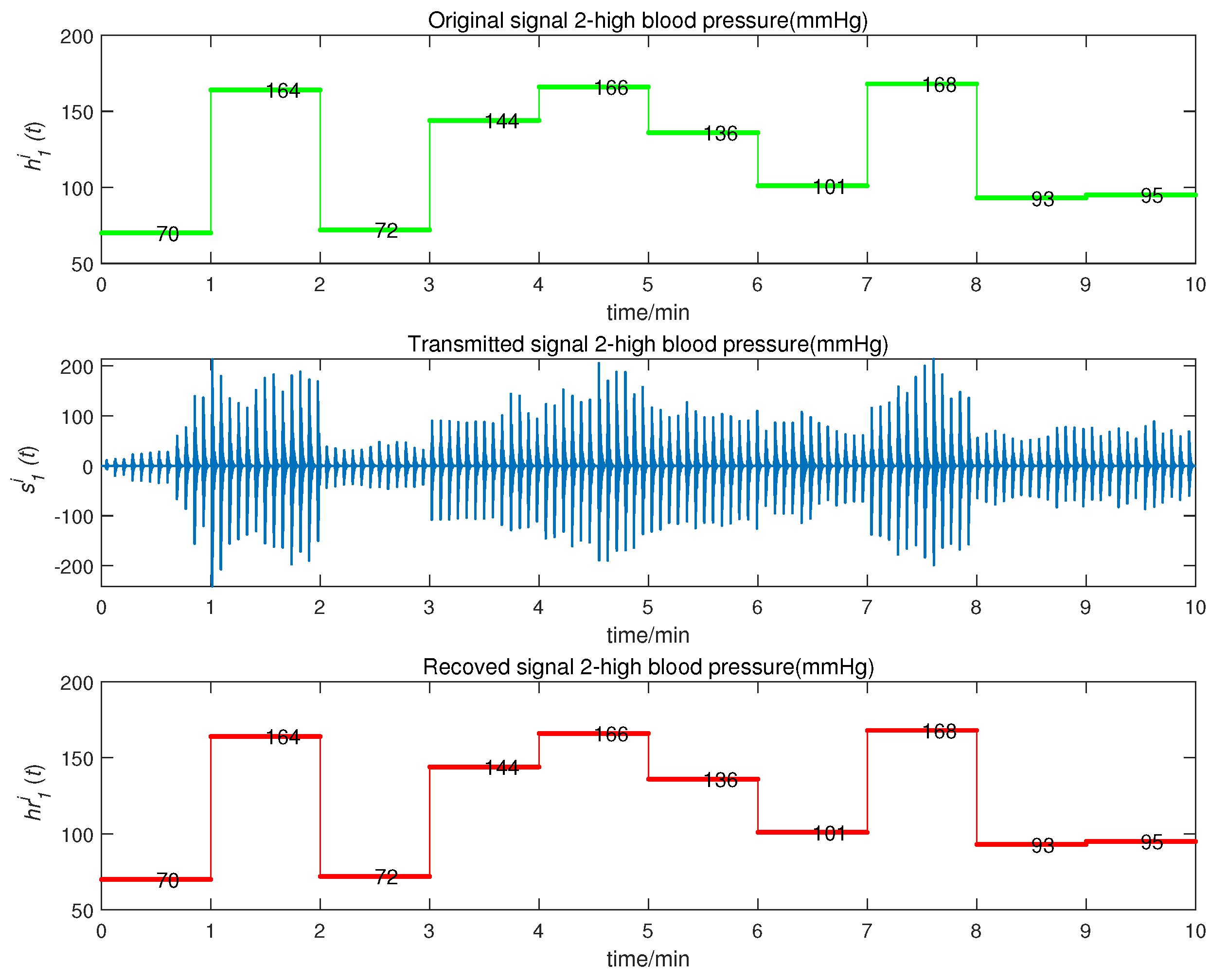
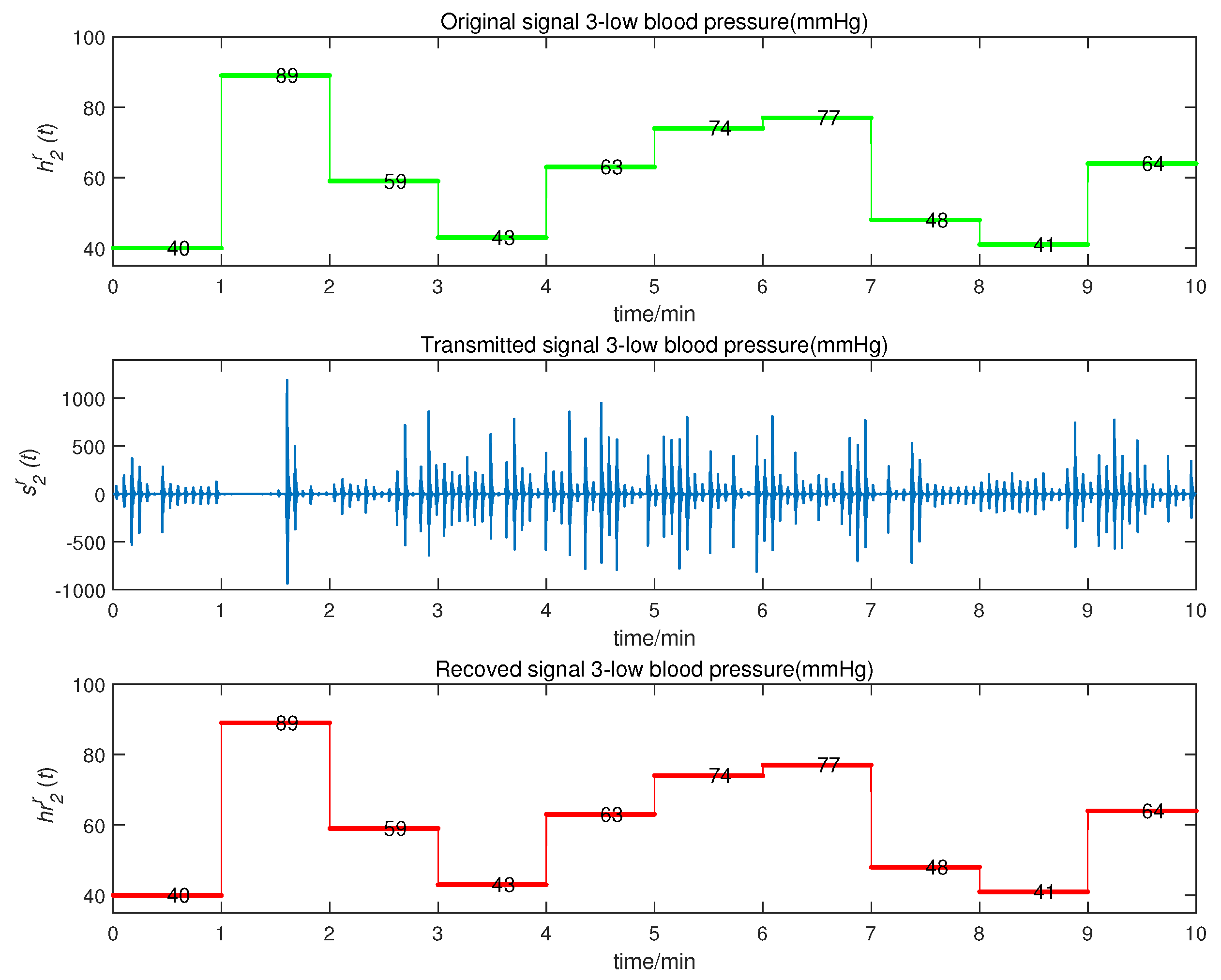
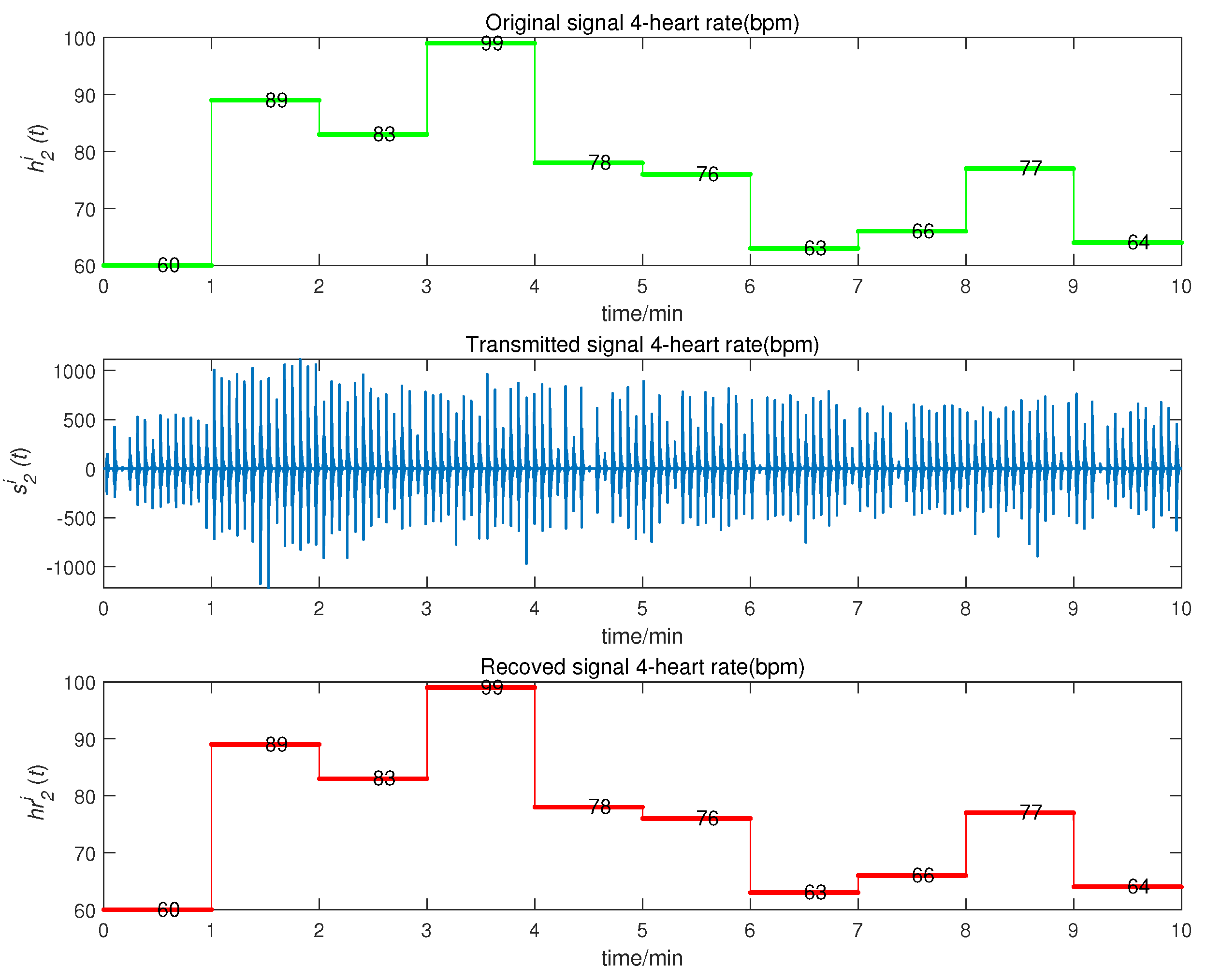
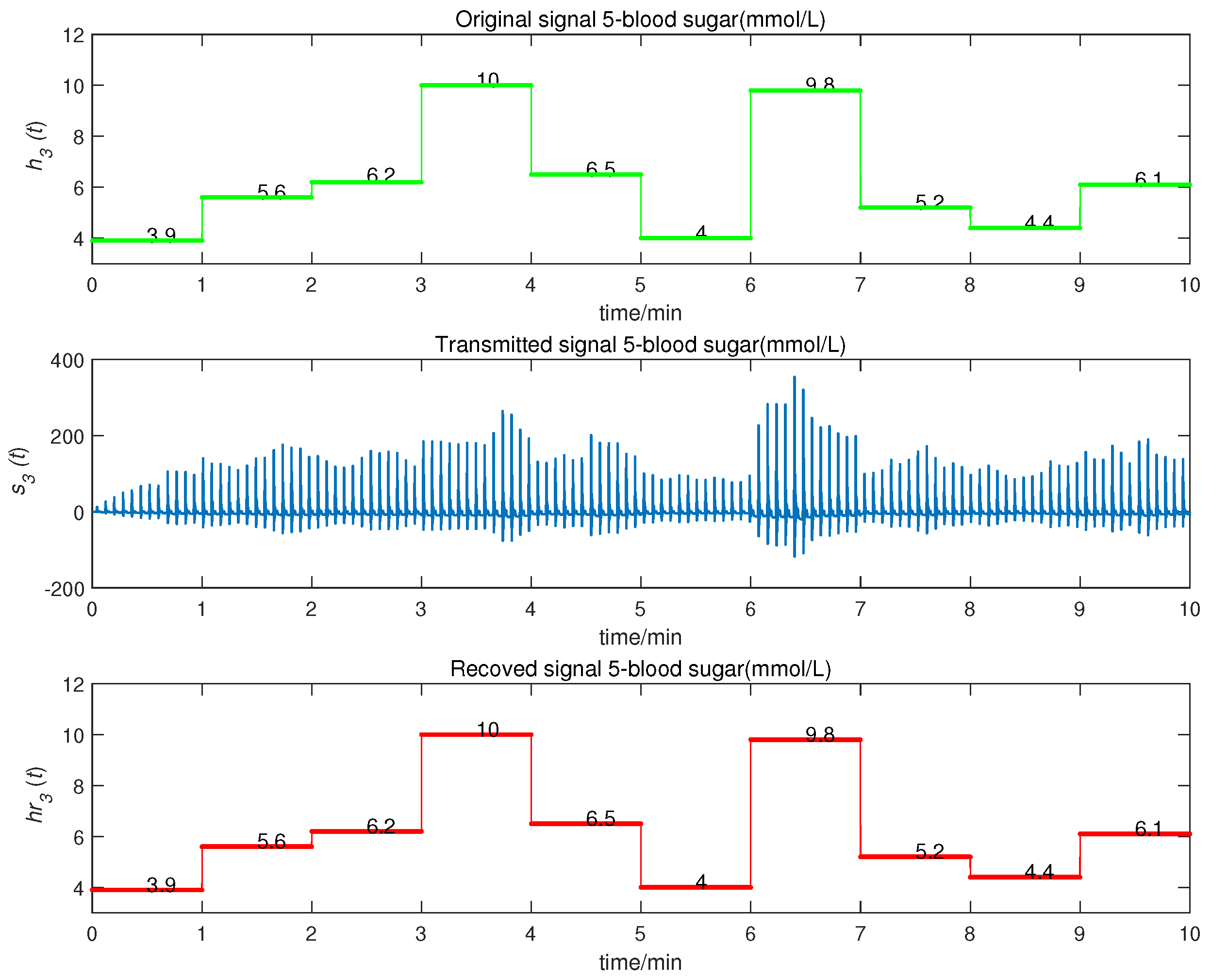
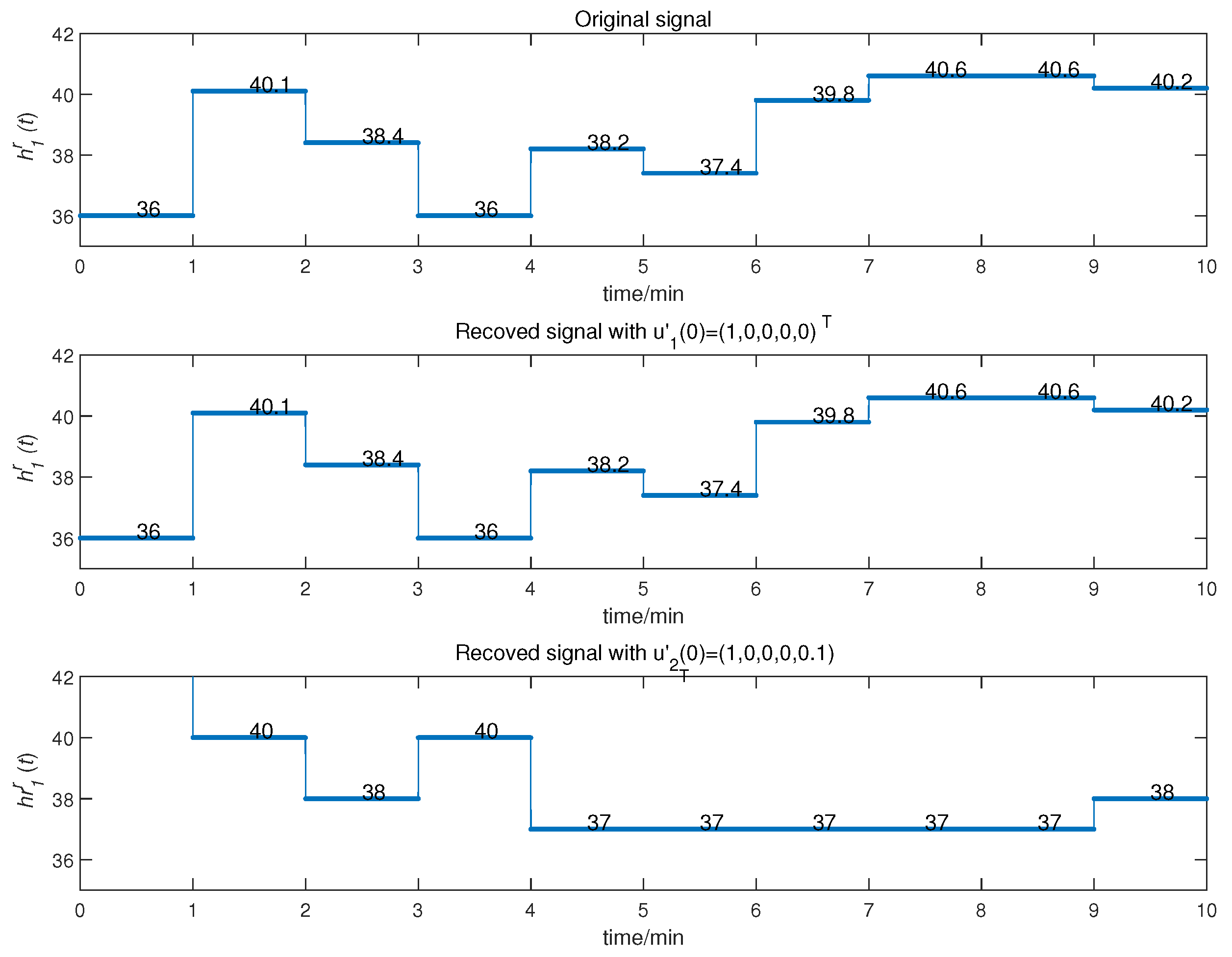
5. Application and Simulation
- as the temperature, within the range of [35, 40] (°C);
- to stand for the high blood pressure value, within the range of [70, 200] (mmHg);
- to stand for the low blood pressure value, within the range of [40, 100] (mmHg);
- as the heart rate, within the range of [60, 100] (beats per minute, bpm); and
- as blood sugar, within the range of [3.9, 10] (mmol/L).
6. Security Analysis
6.1. Key Space Analysis
6.2. Key Sensitivity Analysis
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| CMPS | complex modified projection synchronization |
| WBAN | wireless body area network |
| PS | projection synchronization |
| MPS | modified projection synchronization |
| CS | complete synchronization |
| AS | anti synchronization |
| CCS | complex complete synchronization |
| BER | bit error rate |
References
- Mackey, M.C.; Glass, L. Oscillation and chaos in physiological control systems. Int. J. Bifurc. Chaos 1977, 197, 287–289. [Google Scholar] [CrossRef]
- Fowler, A.C.; Gibbon, J.D.; McGuinness, M.J. The complex Lorenz equations. Phys. D 1982, 4, 139–163. [Google Scholar] [CrossRef]
- Zhao, X.; Liu, J.; Liu, H.; Zhang, F. Dynamic analysis of a one-parameter chaotic system in complex field. IEEE Access 2020, 8, 28774–28781. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, Y.; Kadir, A.; Xu, Y. mage encryption using complex hyper chaotic system by injecting impulse into parameters. Appl. Math. Comput. 2019, 1, 83–93. [Google Scholar]
- Zhang, R.; Liu, Y.; Yang, S. Adaptive synchronization of fractional-order complex chaotic system with unknown complex parameters. Entropy 2019, 21, 207. [Google Scholar] [CrossRef] [PubMed]
- Zhao, X.; Liu, J.; Liu, H.; Zhang, F. A theoretical implementation for a Proposed Hyper-Complex Chaotic System. J. Intell. Fuzzy Syst. 2020, 38, 2585–2590. [Google Scholar]
- Yang, F.; Mou, J.; Ma, C.; Cao, Y. Dynamic analysis of an improper fractional-order laser chaotic system and its image encryption application. Opt. Lasers Eng. 2020, 129, 106031. [Google Scholar] [CrossRef]
- Sahin, E.; Ayas, M.S. Fractional High-Order Differential Estimator and Feedback Controller Design for a Single-Input–Single-Output Affine Chaotic System. J. Comput. Nonlinear Dyn. 2020, 15, 011006. [Google Scholar] [CrossRef]
- Zhang, F.; Liu, S.; Yu, W. Characteristics of complex Lorenz chaotic System with Delay and its self-delay synchronization. Acta Phys. Sin. 2013, 62, 505–762. [Google Scholar]
- Zhang, F. Complete synchronization of coupled multiple-time delay complex chaotic system with applications to secure communication. Acta Phys. Pol. B 2015, 46, 1473–1486. [Google Scholar] [CrossRef]
- Sun, B.; Li, M.; Zhang, F.; Wang, H.; Liu, J. The characteristics and self-time delay synchronization of two-time delay complex Lorenz system. J. Frankl. Inst. 2015, 356, 334–350. [Google Scholar] [CrossRef]
- Matsumoto, T. A chaotic attractor from Chua’s circuit. IEEE Trans. Circuits Syst. 1984, 31, 1055–1058. [Google Scholar] [CrossRef]
- Terry, J.; Van Wiggeren, G.D. Chaotic communication using generalized synchronization. Chaos Solitons Fractals 2001, 12, 145–152. [Google Scholar] [CrossRef]
- Kiani-B, A.; Fallahi, K.; Pariz, N.; Leung, H. A chaotic secure communication scheme using fractional chaotic systems based on an extended fractional Kalman filter. Commun. Nonlinear Sci. Numer. Simul. 2009, 14, 863–879. [Google Scholar] [CrossRef]
- Trejo-Guerra, R.; Tlelo-Cuautle, E.; Cruz-Herández, C.; Sánchez-López, C. Chaotic communication system using Chua’s oscillators realized with CCII+ s. Int. J. Bifurc. Chaos 2009, 19, 4217–4226. [Google Scholar] [CrossRef]
- Cheng, C.; Lin, Y.; Wu, S. Design of adaptive sliding mode tracking controllers for chaotic synchronization and application to secure communications. J. Frankl. Inst. 2012, 349, 2626–2649. [Google Scholar] [CrossRef]
- Pisarchik, A.; Jaimes-Reátegui, R.; Sevilla-Escoboza, J.R.; Ruiz-Oliveras, F.R.; García-López, J.H. Two-channel opto-electronic chaotic communication system. J. Frankl. Inst. 2012, 349, 3194–3202. [Google Scholar] [CrossRef]
- Chee, C.; Xu, D. Chaos-based M-ary digital communication technique using controlled projective synchronisation. IEE Proc. Circuits Devices Syst. 2006, 153, 357–360. [Google Scholar] [CrossRef]
- Mahmoud, G.M.; Mahmoud, E.E.; Arafa, A.A. On projective synchronization of hyperchaotic complex nonlinear systems based on passive theory for secure communications. Phys. Scr. 2006, 87, 055002. [Google Scholar] [CrossRef]
- Mainieri, R.; Rehacek, J. Projective Synchronization in Three-Dimensional Chaotic Systems. Phys. Rev. Lett. 1999, 82, 3042. [Google Scholar] [CrossRef]
- Guo, L.; Xu, Z.; Hu, M. Projective synchronization in drive—Response networks via impulsive control. Chin. Phys. Lett. 2008, 25, 2816. [Google Scholar]
- Zhang, F.; Liu, S.; Yu, W. Modified projective synchronization with complex scaling factors of uncertain real chaos and complex chaos. Chin. Phys. B 2013, 22, 120505. [Google Scholar] [CrossRef]
- Mahmoud, G.M.; Mahmoud, E.E. Complex modified projective synchronization of two chaotic complex nonlinear systems. Nonlinear Dyn. 2013, 73, 2231–2240. [Google Scholar] [CrossRef]
- Zhang, F.; Liu, S. Full state hybrid projective synchronization and parameters identification for uncertain chaotic (hyperchaotic) complex systems. J. Comput. Nonlinear Dyn. 2014, 9, 021009. [Google Scholar] [CrossRef]
- Liu, S.; Zhang, F. Complex function projective synchronization of complex chaotic system and its applications in secure communication. Nonlinear Dyn. 2014, 76, 1087–1097. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X.; Zhu, Q. Asynchronization anti-noise hyper chaotic secure communication system based on dynamic delay and state variables switching. Phys. Lett. A 2011, 375, 2828–2835. [Google Scholar] [CrossRef]
- Azzaz, M.S.; Tanougast, C.; Sadoudi, S. Synchronized hybrid chaotic generators: Application to real-time wireless speech encryption. Commun. Nonlinear Sci. 2013, 18, 2035–2047. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, L.; An, X. Adaptive coupled synchronization among three coupled chaos systems and its application to secure communications. EURASIP J. Wirel. Commun. Netw. 2016, 2016, 1–15. [Google Scholar] [CrossRef]
- Li, R.; Wu, H. Secure communication on fractional-order chaotic systems via adaptive sliding mode control with teaching–learning–feedback-based optimization. Nonlinear Dyn. 2019, 95, 1221–1243. [Google Scholar] [CrossRef]
- Nwachioma, C.; Pérez-Cruz, J.H. New Chaotic Oscillator—Properties, Analog Implementation, and Secure Communication Application. IEEE Access 2019, 17, 7510–7521. [Google Scholar] [CrossRef]
- Sathiyamurthi, P.; Ramakrishnan, S. Speech encryption algorithm using FFT and 3D-Lorenz–logistic chaotic map. Multimed. Tools Appl. 2020, 79, 17817–17835. [Google Scholar] [CrossRef]
- Elsafty, A.H.; Tolba, M.F.; Said, L.A. Enhanced hardware implementation of a mixed-order nonlinear chaotic system and speech encryption application. AEU-Int. J. Electron. Commun. 2020, 125, 153347. [Google Scholar] [CrossRef]
- Moskalenko, O.I.; Koronovskii, A.A.; Hramov, A.E. Generalized synchronization of chaos for secure communication: Remarkable stability to noise. Phys. Lett. A 2010, 374, 2925–2931. [Google Scholar] [CrossRef]
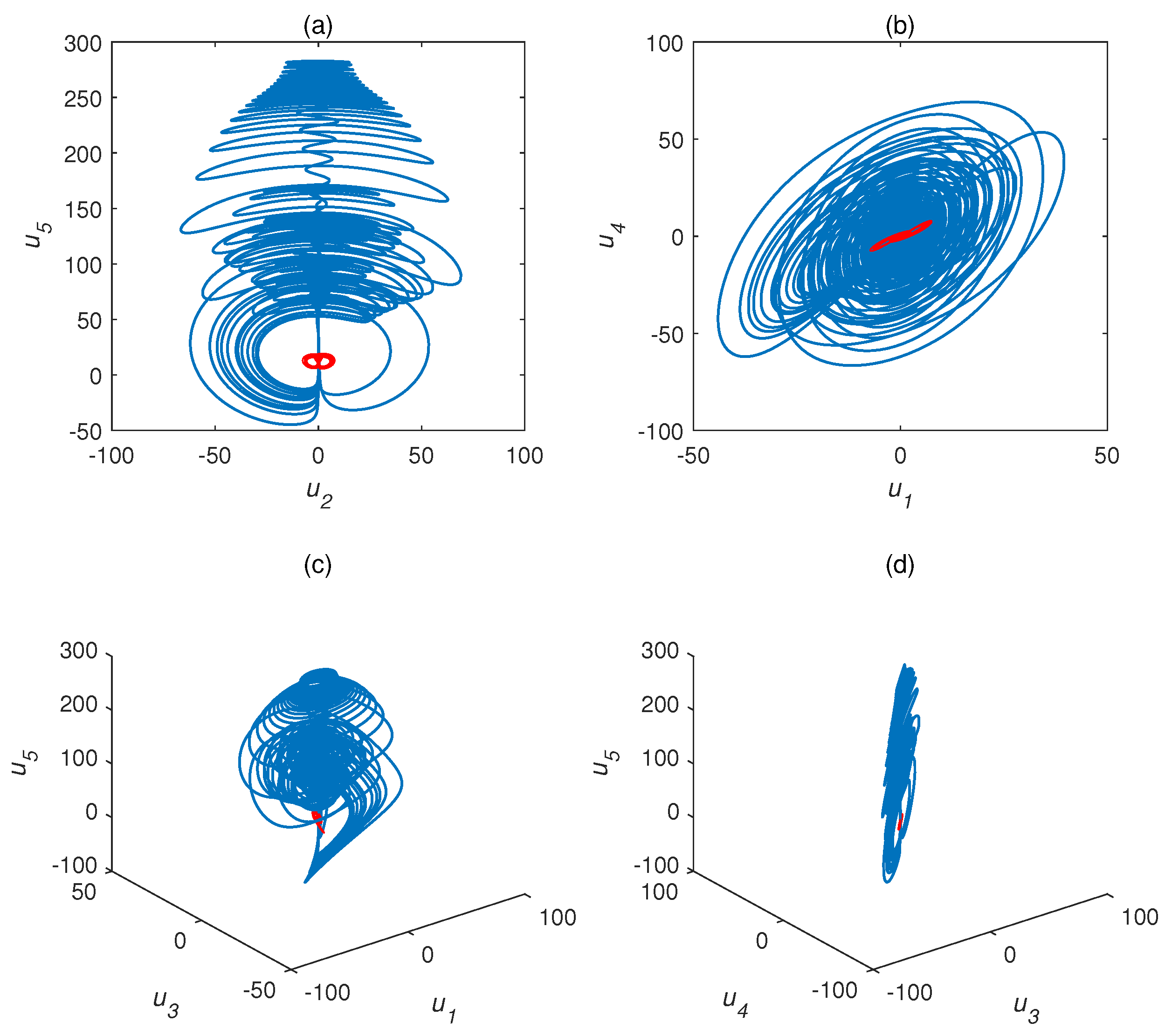

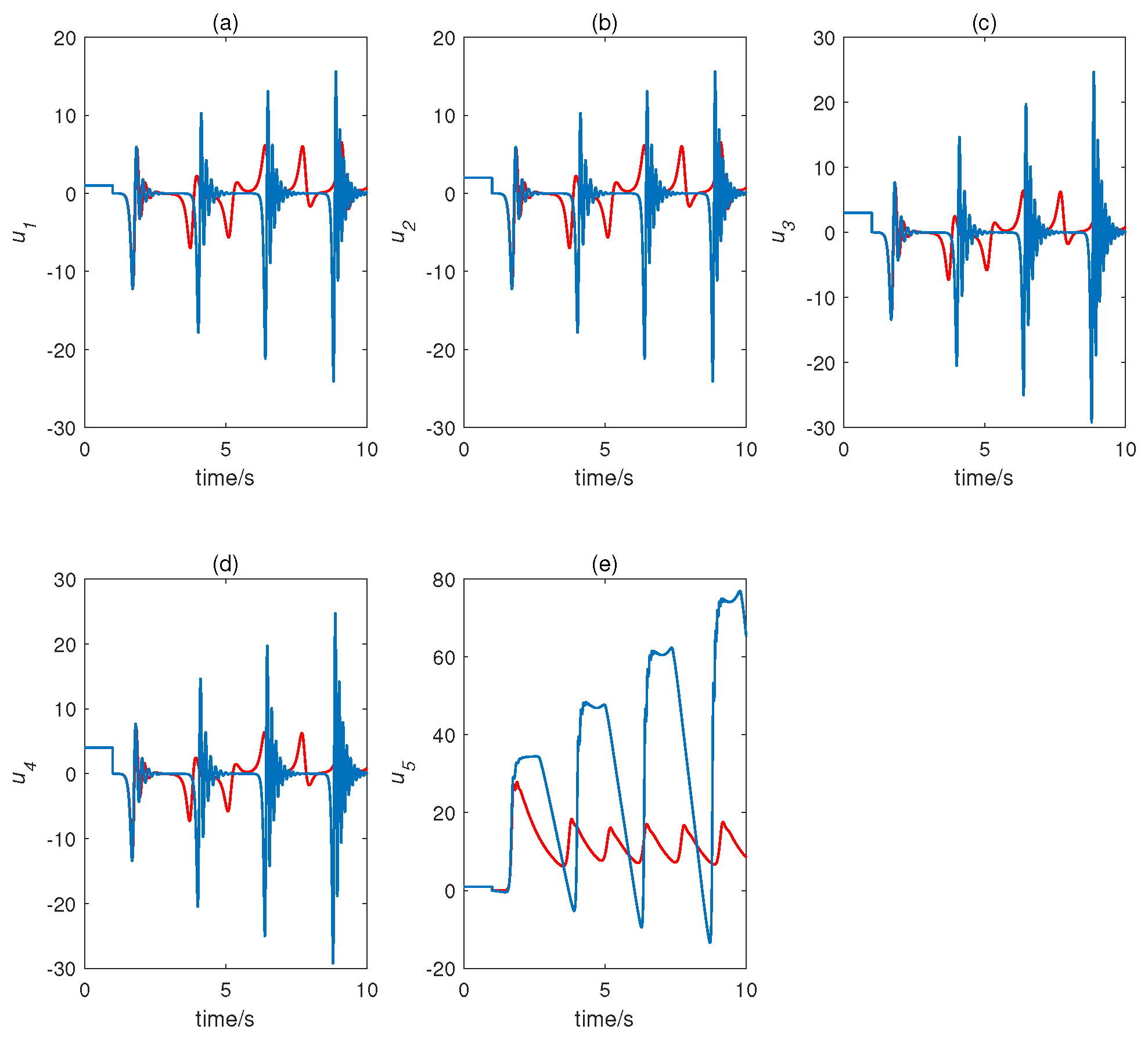

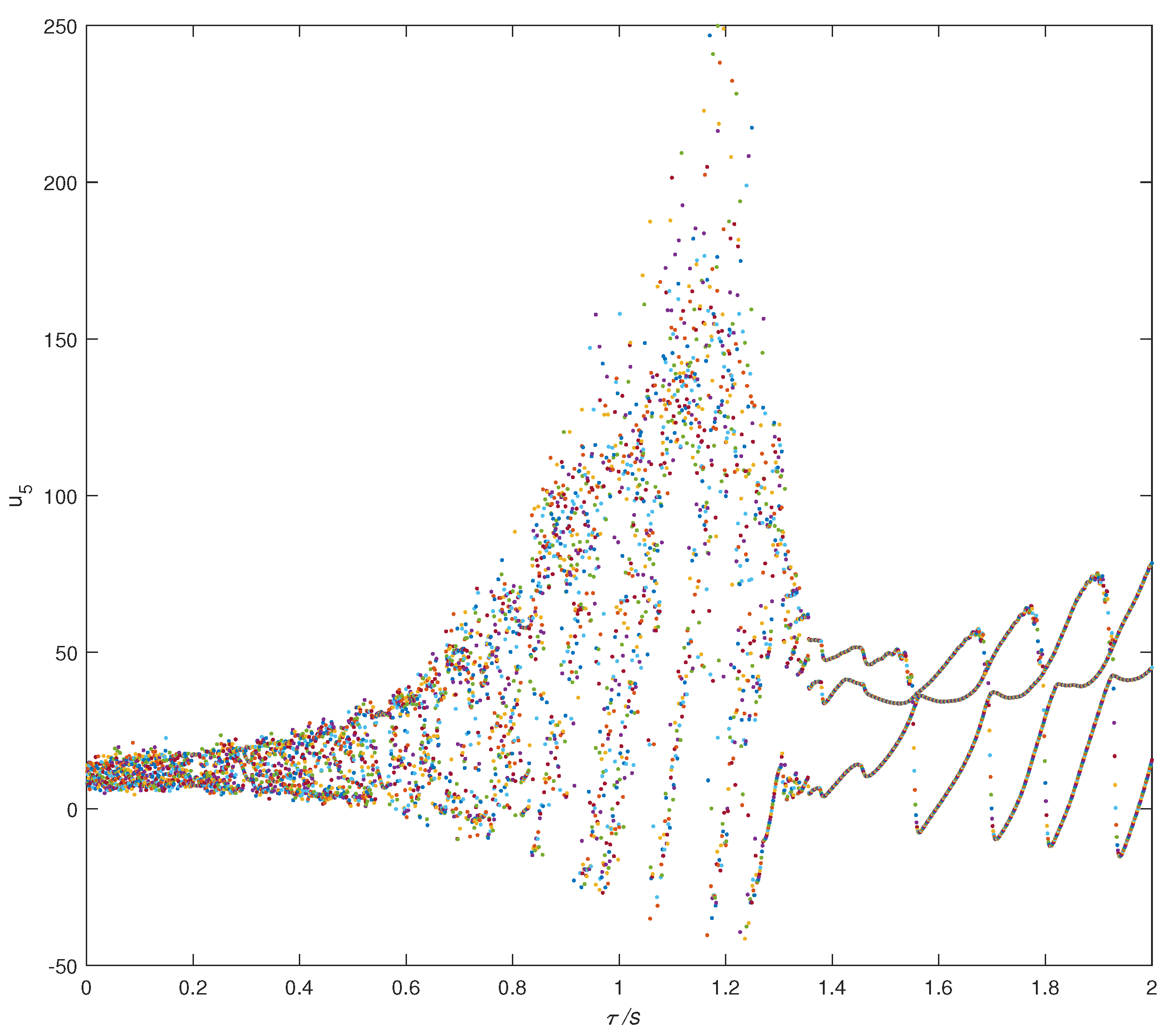


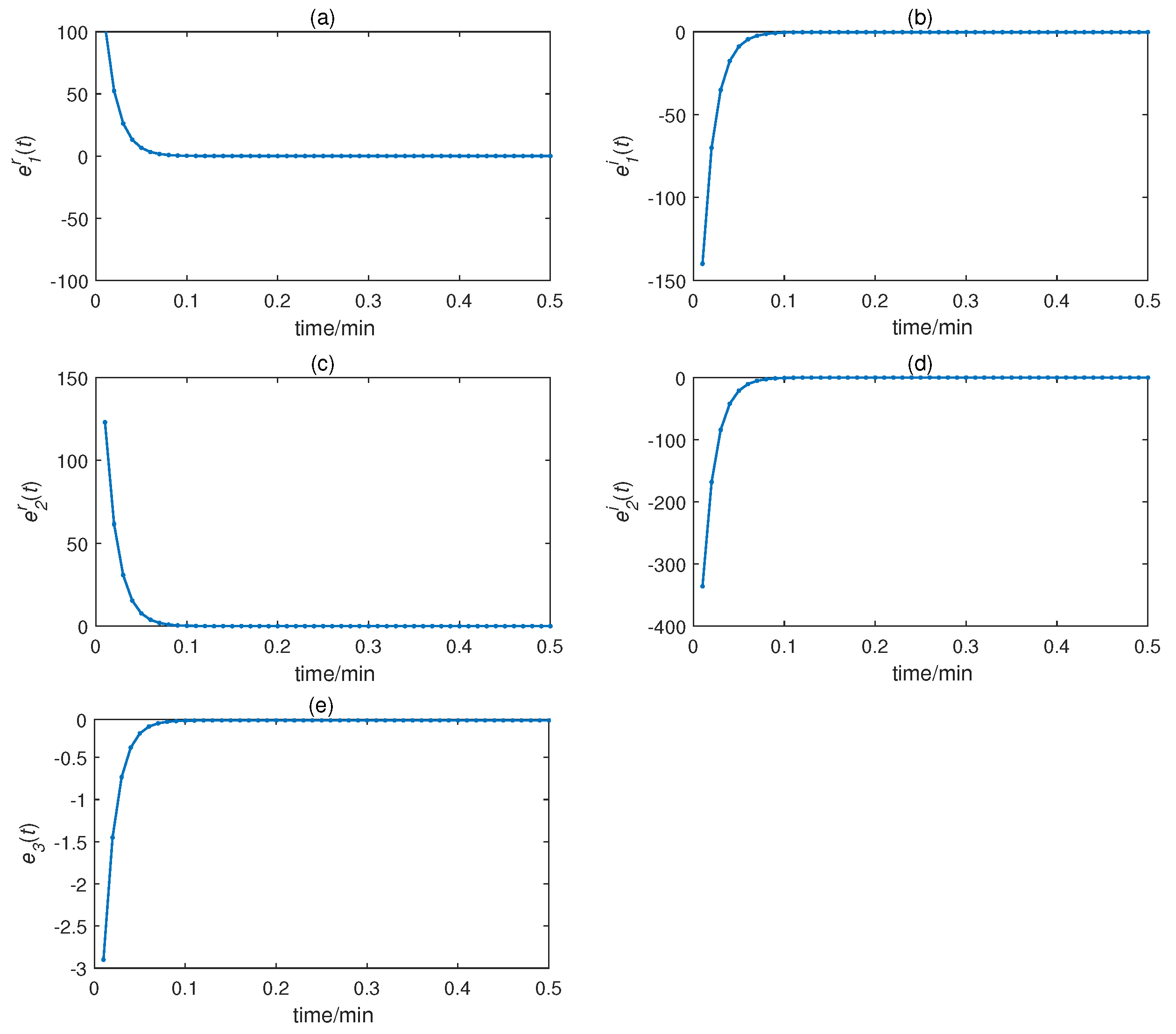
| Variable | Symbol | Types | |||||
|---|---|---|---|---|---|---|---|
| s | 2.2260 | −0.0857 | −0.7402 | −0.5030 | −1.1583 | (+,0,−,−,−) | Chaos |
| s | 2.2837 | 0.7366 | −0.0176 | −0.5226 | −1.4729 | (+,+,0,−,−) | Hyperchaos |
| s | 0.4680 | 0.4676 | −0.0298 | −0.8371 | −0.8366 | (0,0,0,−,−) | Limit cycle |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, F.; Leng, S.; Li, Z.; Jiang, C. Time Delay Complex Chen Chaotic System and Secure Communication Scheme for Wireless Body Area Networks. Entropy 2020, 22, 1420. https://doi.org/10.3390/e22121420
Zhang F, Leng S, Li Z, Jiang C. Time Delay Complex Chen Chaotic System and Secure Communication Scheme for Wireless Body Area Networks. Entropy. 2020; 22(12):1420. https://doi.org/10.3390/e22121420
Chicago/Turabian StyleZhang, Fangfang, Sen Leng, Zhengfeng Li, and Cuimei Jiang. 2020. "Time Delay Complex Chen Chaotic System and Secure Communication Scheme for Wireless Body Area Networks" Entropy 22, no. 12: 1420. https://doi.org/10.3390/e22121420
APA StyleZhang, F., Leng, S., Li, Z., & Jiang, C. (2020). Time Delay Complex Chen Chaotic System and Secure Communication Scheme for Wireless Body Area Networks. Entropy, 22(12), 1420. https://doi.org/10.3390/e22121420





