Revisiting Information Detection and Energy Harvesting: A Power Splitting-Based Approach
Abstract
1. Introduction
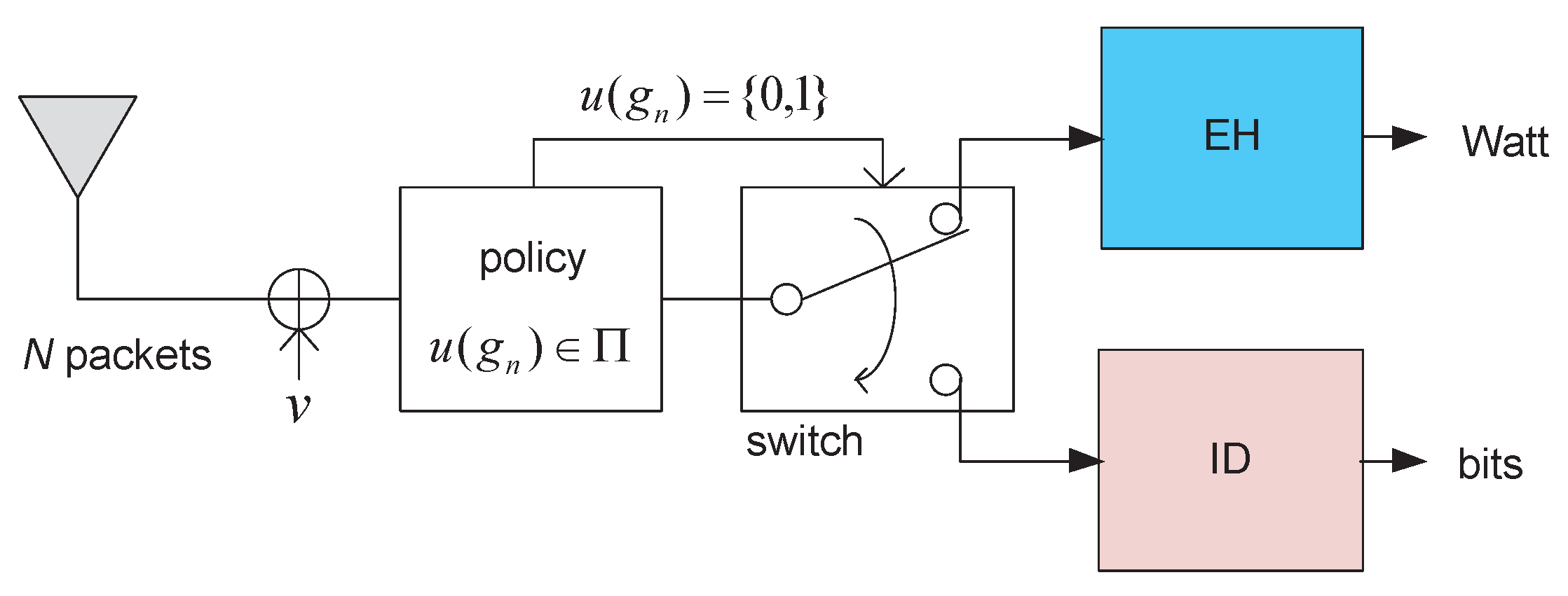
2. System and Signal Models
3. Optimal DPS Solution
- All N packets and their channels should be stored in a controller/buffer to determine the power splitting ratio . Note that τ is a function of λ, which is a function of all .
- Power splitting for each packet requires a high-speed and highly accurate power splitter.
- Computing λ may cause a significant delay and requires high computational complexity.
4. Optimal TPS Solutions
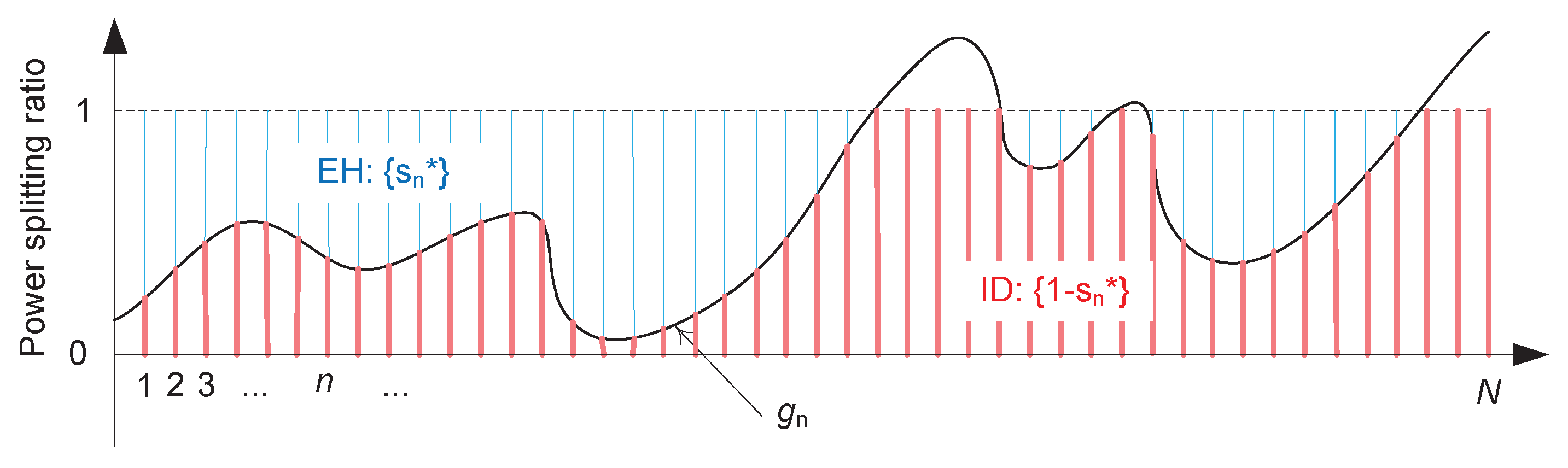
4.1. Problem Formulation
4.2. Class of TPS Policies
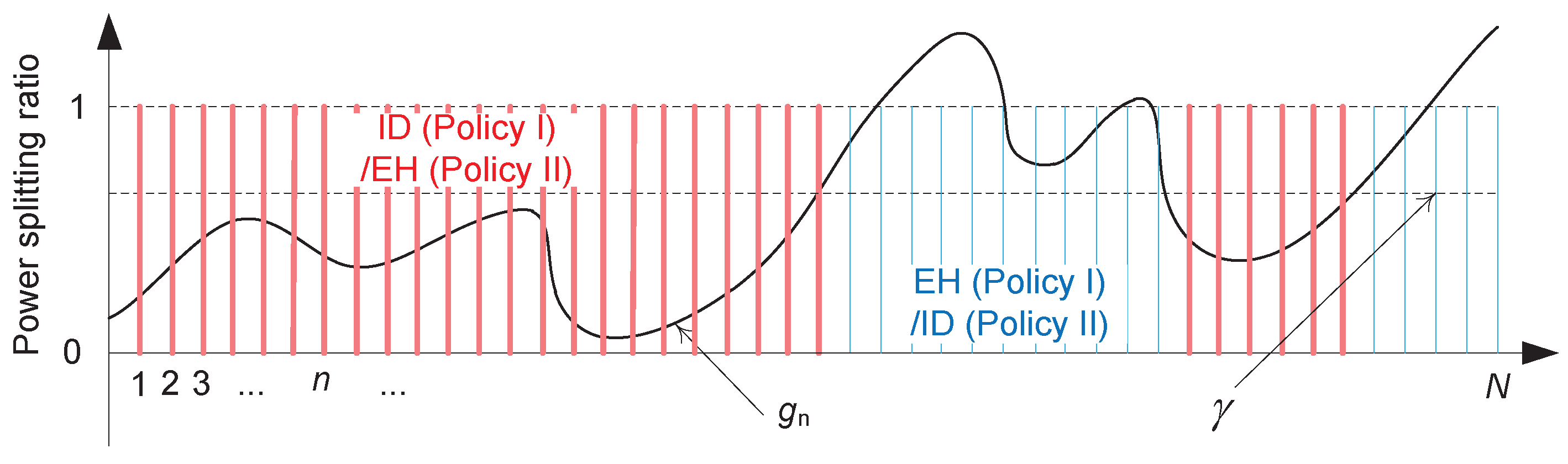
4.3. Two Single-Threshold Policies
4.4. Asymptotic Analysis
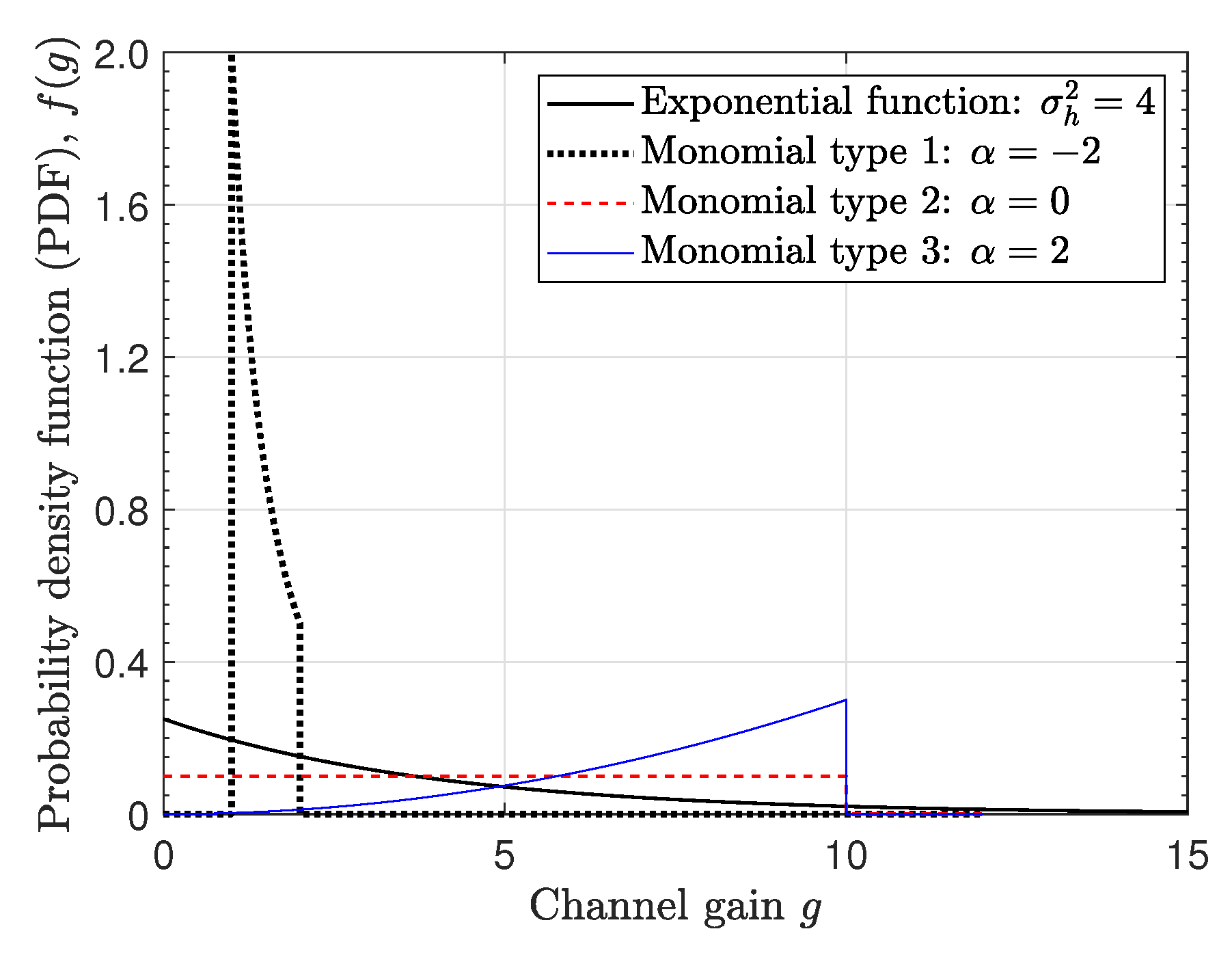
4.5. Statistics-Based Policies
5. Numerical Evaluation and Discussion
5.1. Simulation Environment
5.2. Numerical Results
6. Concluding Remarks
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| CSI | channel state information |
| DPS | dynamic power splitting |
| DTS | dynamic time sharing |
| EH | energy harvesting |
| ID | information decoding |
| MIMO | multiple-input multiple-output |
| MISO | multiple-input single-output |
| probability density function | |
| R–E | rate–energy |
| SIMO | single-input multiple-output |
| SISO | single-input single-output |
| SWIPT | simultaneous wireless information and power transfer |
| TPS | threshold-based power-splitting |
Appendix A. Proof of Theorem 1
Appendix B. Proof of Corollary 1
Appendix C. Proof of Theorem 2
Appendix D. Proof of Theorem 3
- (i)
- Case 1 (): Define . Because and , is a convex increasing function. From the CFC rule, it is evident that and are convex functions because and are convex functions owing to the non-negative . Because is convex, is convex if is an even integer. In contrast, because is a convex function if is convex with a positive integer, i.e., and , is also convex. Therefore, in general, is a convex function for all . Similarly, we can show that is convex. Consequently, in (A6) is convex because it denotes the sum of two convex functions if . Furthermore, because , we can show that if , which implies that Policy I is optimal if . Here, is the maximum achievable rate derived as
- (ii)
- Case 2 (): Because and , is a concave increasing function. Thus, is a convex decreasing function. From the CFC rule, and are convex as and are concave functions owing to the negative . Because is convex, is convex if is an odd number. If is convex when and , then is convex. Therefore, is also convex. Therefore, is convex for all . Similarly, we can show that is convex for all . Consequently, is convex for all as it denotes the sum of two convex functions. Furthermore, because , we can show that if , which implies that Policy I is optimal if .
- (iii)
- Case 3 (): is convex because it denotes the sum of two convex functions: and . Note that and are convex owing to the negative . Furthermore, because , we can show that if , which implies that Policy I is optimal if .
- (iv)
- Case 4 (): From (A5), we obtain the following equalities when :where are constant values. Because is a logarithmically increasing concave function, is a logarithmically convex function, i.e., is convex. In contrast, is an exponentially decreasing convex function; thus, is a decreasing logarithmically convex function, i.e., is convex. Therefore, in (A6) is convex. Considering that , we can show that if , which implies that policy I is optimal if .
References
- Raghunathan, V.; Chou, P.H. Design and Power Management of Energy Harvesting Embedded Systems. In Proceedings of the International Symposium on Low Power Electronics and Design, Tegernsee, Germany, 4–6 October 2006; pp. 369–374. [Google Scholar] [CrossRef]
- Lu, C.; Raghunathan, V.; Roy, K. Efficient Design of Micro-Scale Energy Harvesting Systems. IEEE J. Emerg. Sel. Top. Circuits Syst. 2011, 1, 254–266. [Google Scholar] [CrossRef]
- Prauzek, M.; Konecny, J.; Borova, M.; Janosova, K.; Hlavica, J.; Musilek, P. Energy Harvesting Sources, Storage Devices and System Topologies for Environmental Wireless Sensor Networks: A Review. Sensors 2018, 18, 2446. [Google Scholar] [CrossRef]
- Ho, C.K.; Zhang, R. Optimal Energy Allocation for Wireless Communications with Energy Harvesting Constraints. IEEE Trans. Signal Process. 2012, 60, 4808–4818. [Google Scholar] [CrossRef]
- Zhang, R.; Ho, C.K. MIMO Broadcasting for Simultaneous Wireless Information and Power Transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, R.; Ho, C.K. Wireless Information and Power Transfer: Architecture Design and Rate-Energy Tradeoff. IEEE Trans. Commun. 2013, 61, 4754–4767. [Google Scholar] [CrossRef]
- Huang, K.; Larsson, E.G. Simultaneous Information-and-Power Transfer for Broadcand Downlink Systems. IEEE Trans. Signal Process. 2013, 61, 5972–5986. [Google Scholar] [CrossRef]
- Luecken, H.; Steiner, C.; Wittneben, A. Location-aware UWB Communication with Generalized Energy Detection Receivers. IEEE Trans. Wirel. Commun. 2012, 11, 3068–3078. [Google Scholar] [CrossRef]
- Fouladgar, A.M.; Simeone, O. On the Transfer of Information and Energy in Multi-User Systems. IEEE Commun. Lett. 2012, 16, 1733–1736. [Google Scholar] [CrossRef]
- Krikidis, I.; Timotheou, S.; Sasaki, S. RF Energy Transfer for Cooperative Networks: Data Relaying or Energy Harvesting? IEEE Commun. Lett. 2012, 16, 1772–1775. [Google Scholar] [CrossRef]
- Nasir, A.A.; Zhou, X.; Durrani, S.; Kennedy, R.A. Relaying Protocols for Wireless Energy Harvesting and Information Processing. IEEE Trans. Wirel. Commun. 2013, 12, 3622–3636. [Google Scholar] [CrossRef]
- Do, D.-T.; Van Nguyen, M.-S. Device-to-Device Transmission Modes in NOMA Network with and without Wireless Power Transfer. Comput. Commun. 2019, 139, 67–77. [Google Scholar] [CrossRef]
- Dang, H.P.; Van Nguyen, M.-S.; Do, D.-T.; Pham, H.L.; Selim, B.; Kaddoum, G. Joint Relay Selection, Full-Duplex and Device-to-Device Transmission in Wireless Powered NOMA Networks. IEEE Access 2020, 8, 82442–82460. [Google Scholar] [CrossRef]
- Do, D.-T.; Van Nguyen, M.-S.; Nguyen, T.N.; Li, X.; Choi, K. Enabling Multiple Power Beacons for Uplink of NOMA-Enabled Mobile Edge Computing in Wirelessly Powered IoT. IEEE Access 2020, 8, 148892–148905. [Google Scholar] [CrossRef]
- Do, D.-T.; Le, C.-B.; Afghan, F. Enabling Full-Duplex and Energy Harvesting in Uplink and Downlink of Small-Cell Network Relying on Power Domain Based Multiple Access. IEEE Access 2020, 8, 142772–142784. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.-C. Wireless Information Transfer with Opportunistic Energy Harvesting. IEEE Trans. Wirel. Commun. 2012, 12, 288–300. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.-C. Wireless Information and Power Transfer: A Dynamic Power Splitting Approach. IEEE Trans. Commun. 2013, 61, 3990–4001. [Google Scholar] [CrossRef]
- Zhou, X. Training-based SWIPT: Optimal Power Splitting at the Receiver. IEEE Trans. Veh. Technol. 2015, 64, 4377–4382. [Google Scholar] [CrossRef]
- Perera, T.D.P.; Jayakody, D.N.K.; Sharma, S.K.; Chatzinotas, S.; Li, J. Simultaneous Wireless Information and Power Transfer (SWIPT): Recent Advances and Future Challenges. IEEE Commun. Surv. Tutor. 2017, 20, 264–302. [Google Scholar] [CrossRef]
- Bansal, S.; Kumar, D. IoT Ecosystem: A Survey on Devices, Gateways, Operating Systems, Middleware and Communication. Int. J. Wirel. Inf. Netw. 2020, 27, 340–364. [Google Scholar] [CrossRef]
- Gu, Q.; Wang, G.; Fan, R.; Zhong, Z.; Yang, K.; Jiang, H. Rate-Energy Tradeoff in Simultaneous Wireless Information and Power Transfer over Fading Channels with Uncertain Distribution. IEEE Trans. Veh. Technol. 2018, 67, 3663–3668. [Google Scholar] [CrossRef]
- Xiong, K.; Wang, B.; Liu, K.J.R. Rate-Energy Region of SWIPT for MIMO Broadcasting under Nonlinear Energy Harvesting Model. IEEE Trans. Wirel. Commun. 2017, 16, 5147–5161. [Google Scholar] [CrossRef]
- Li, L.; Wang, H.; Wang, Z.; Paulraj, A. Simultaneous Wireless Information and Power Transfer in Multi-User Interference SISO System. In Proceedings of the IEEE International Conference on Ubiquitous Wireless Broadband (ICUWB), Montreal, QC, Canada, 4–7 October 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Li, S.; Xu, W.; Liu, Z.; Lin, J. Independent Power Splitting for Interference-Corrupted SIMO SWIPT Systems. IEEE Commun. Lett. 2016, 20, 478–481. [Google Scholar] [CrossRef]
- Shi, Q.; Xu, W.; Chang, T.-H. Joint Beamforming and Power Splitting for MISO Interference Channel with SWIPT: An SOCP Relaxation and Decentralized Algorithm. IEEE Trans. Signal Process. 2014, 62, 6194–6208. [Google Scholar] [CrossRef]
- Zong, Z.; Feng, H.; Yu, F.R.; Zhao, N.; Yang, T.; Hu, B. Optimal Transceiver Design for SWIPT in K-User MIMO Interference Channels. IEEE Trans. Wirel. Commun. 2016, 15, 430–445. [Google Scholar] [CrossRef]
- Zhao, M.-M.; Cai, Y.; Shi, Q.; Hong, M.; Champagne, B. Joint Transceiver Designs for Full-Duplex K-Pair MIMO Interference Channel with SWIPT. IEEE Trans. Commun. 2017, 65, 890–905. [Google Scholar] [CrossRef]
- Dong, A.; Zhang, H.; Wu, D.; Yuan, D. QoS-Constrained Transceiver Design and Power Splitting for Downlink Multiuser MIMO SWIPT Systems. In Proceedings of the IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Pan, G.; Tang, C.; Li, T.; Chen, Y. Secrecy Performance Analysis for SIMO Simultaneous Wireless Information and Power Transfer Systems. IEEE Trans. Commun. 2015, 63, 3423–3433. [Google Scholar] [CrossRef]
- Saber, M.J.; Keshavarz, A.; Mazloum, J.; Sazdar, A.M.; Piran, M.J. Physical-Layer Security Analysis of Mixed SIMO SWIPT RF and FSO Fixed-Gain Relaying Systems. IEEE Syst. J. 2019, 13, 2851–2858. [Google Scholar] [CrossRef]
- Lee, H.; Lee, K.-J.; Kim, H.; Lee, I. Joint Transceiver Optimization for MISO SWIPT Systems with Time Switching. IEEE Trans. Wirel. Commun. 2018, 17, 3293–3312. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Sun, H.; Hu, R.Q.; Hanzo, L. Artificial Noise Aided Secure Cognitive Beamforming for Cooperative MISO-NOMA Using SWIPT. IEEE J. Sel. Areas Commun. 2018, 36, 918–931. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.C. Multi-Antenna Wireless Powered Communication with Energy Beamforming. IEEE Trans. Wirel. Commun. 2014, 62, 4349–4361. [Google Scholar] [CrossRef]
- Shi, Q.; Liu, L.; Xu, W.; Zhang, R. Joint Transmit Beamforming and Receive Power Splitting for MISO SWIPT Systems. IEEE Trans. Wirel. Commun. 2014, 18, 600–603. [Google Scholar] [CrossRef]
- Khandaker, M.R.A.; Wong, K.K. SWIPT in MISO Multicasting Systems. IEEE Wirel. Commun. Lett. 2014, 3, 277–280. [Google Scholar] [CrossRef]
- Zhu, Z.; Chu, Z.; Wang, N.; Huang, S.; Wang, Z.; Lee, I. Beamforming and Power Splitting Designs for AN-Aided Secure Multi-User MIMO SWIPT Systems. IEEE Trans. Inf. Forensic Secur. 2017, 12, 2861–2874. [Google Scholar] [CrossRef]
- Tang, J.; So, D.K.C.; Shojaeifard, A.; Wong, K.-K.; Wen, J. Joint Antenna Selection and Spatial Switching for Energy Efficient MIMO SWIPT System. IEEE Trans. Wirel. Commun. 2017, 16, 4754–4769. [Google Scholar] [CrossRef]
- Zhu, Z.; Chu, Z.; Zhou, F.; Niu, H.; Wang, Z.; Lee, I. Secure Beamforming Designs for Secrecy MIMO SWIPT Systems. IEEE Wirel. Commun. Lett. 2018, 7, 424–427. [Google Scholar] [CrossRef]
- Joung, J.; Ho, C.K.; Sun, S. Wireless Power Transfer and Communication for Sensors: Dynamic Frame-Switching (DFS) Policy. In Proceedings of the IEEE Online Conference on Green Communications, Online Conference, Tucson, AZ, USA, 12–14 November 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory, 2nd ed.; John Wiley & Sons: Hoboken, NJ, USA, 2006. [Google Scholar]
- Erez, U.; Trott, M.; Wornell, G.W. Rateless Coding for Gaussian Channels. IEEE Trans. Inf. Theory 2012, 58, 530–547. [Google Scholar] [CrossRef]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, J.; Shin, W.-Y.; Kang, X.; Lee, H.L.; Joung, J. Revisiting Information Detection and Energy Harvesting: A Power Splitting-Based Approach. Entropy 2020, 22, 1341. https://doi.org/10.3390/e22121341
Kim J, Shin W-Y, Kang X, Lee HL, Joung J. Revisiting Information Detection and Energy Harvesting: A Power Splitting-Based Approach. Entropy. 2020; 22(12):1341. https://doi.org/10.3390/e22121341
Chicago/Turabian StyleKim, Jaehong, Won-Yong Shin, Xin Kang, Han Lim Lee, and Jingon Joung. 2020. "Revisiting Information Detection and Energy Harvesting: A Power Splitting-Based Approach" Entropy 22, no. 12: 1341. https://doi.org/10.3390/e22121341
APA StyleKim, J., Shin, W.-Y., Kang, X., Lee, H. L., & Joung, J. (2020). Revisiting Information Detection and Energy Harvesting: A Power Splitting-Based Approach. Entropy, 22(12), 1341. https://doi.org/10.3390/e22121341







